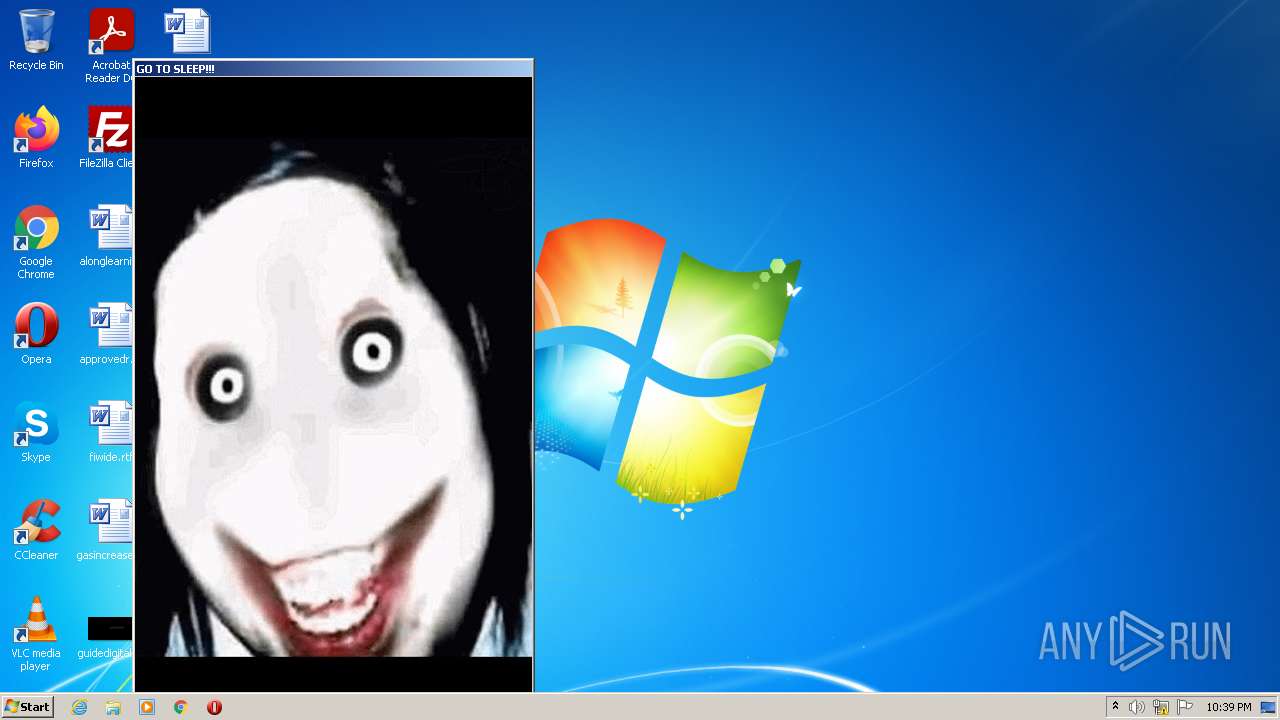
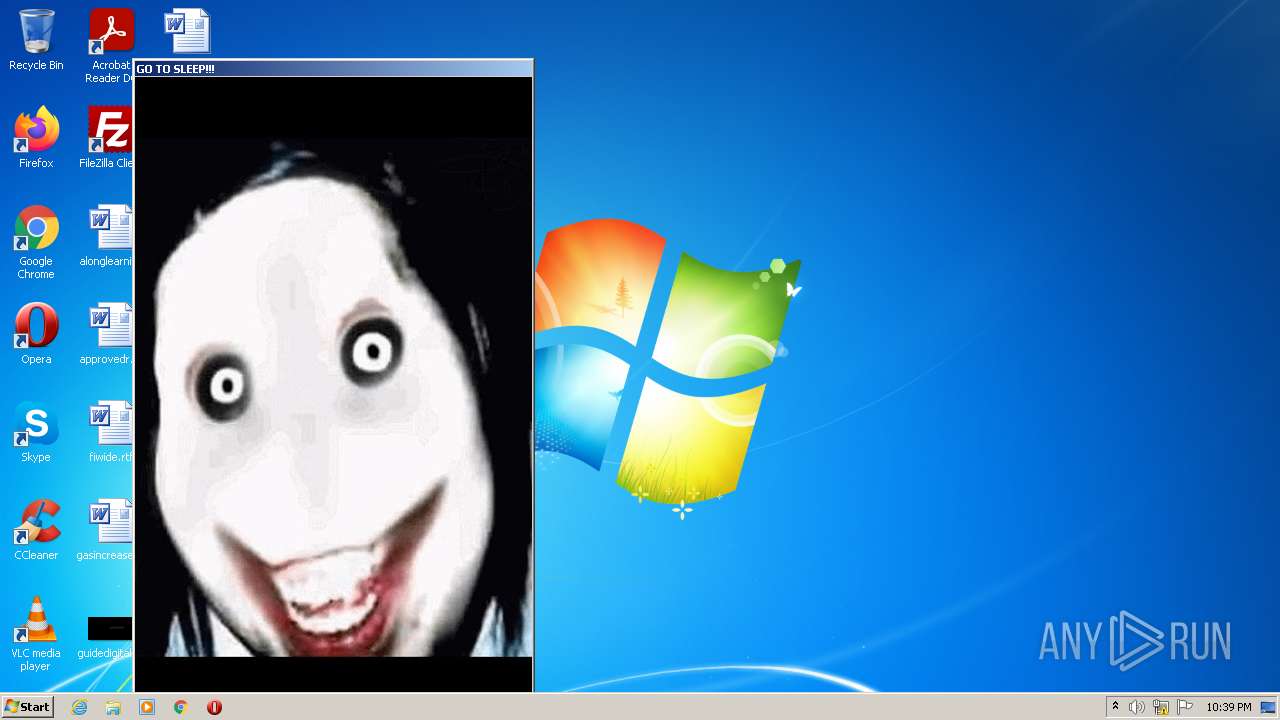
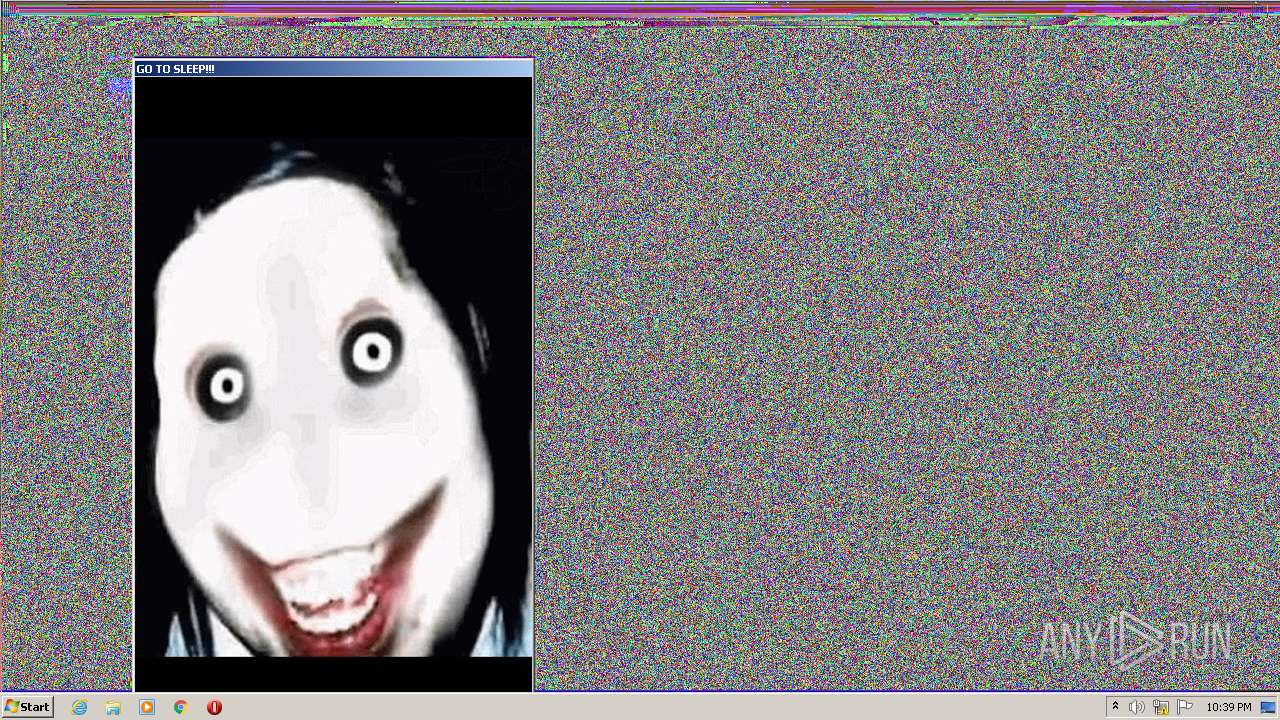
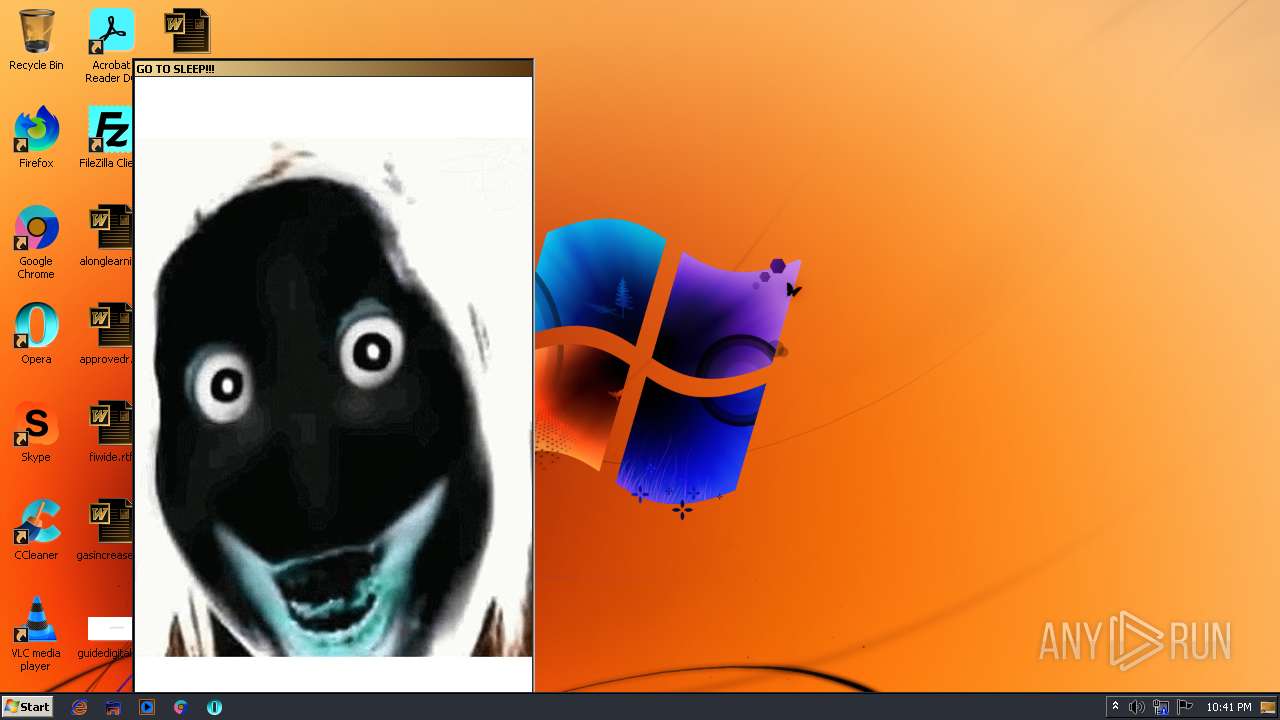
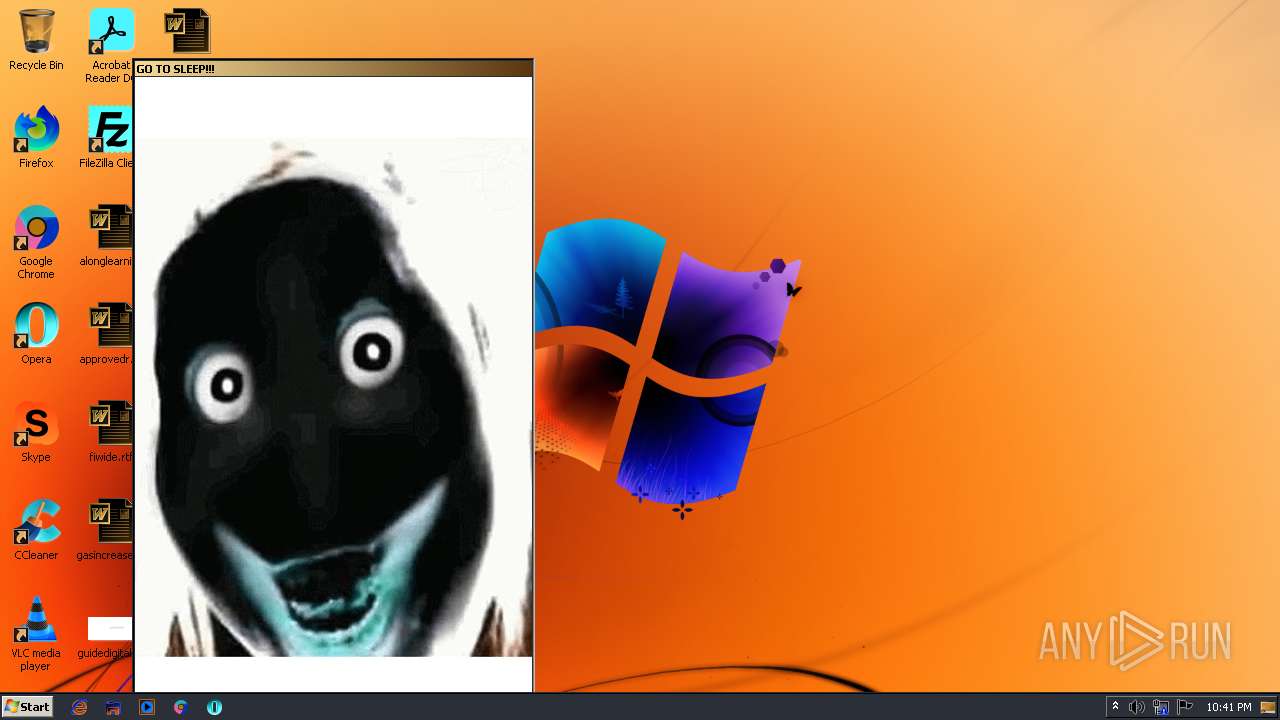
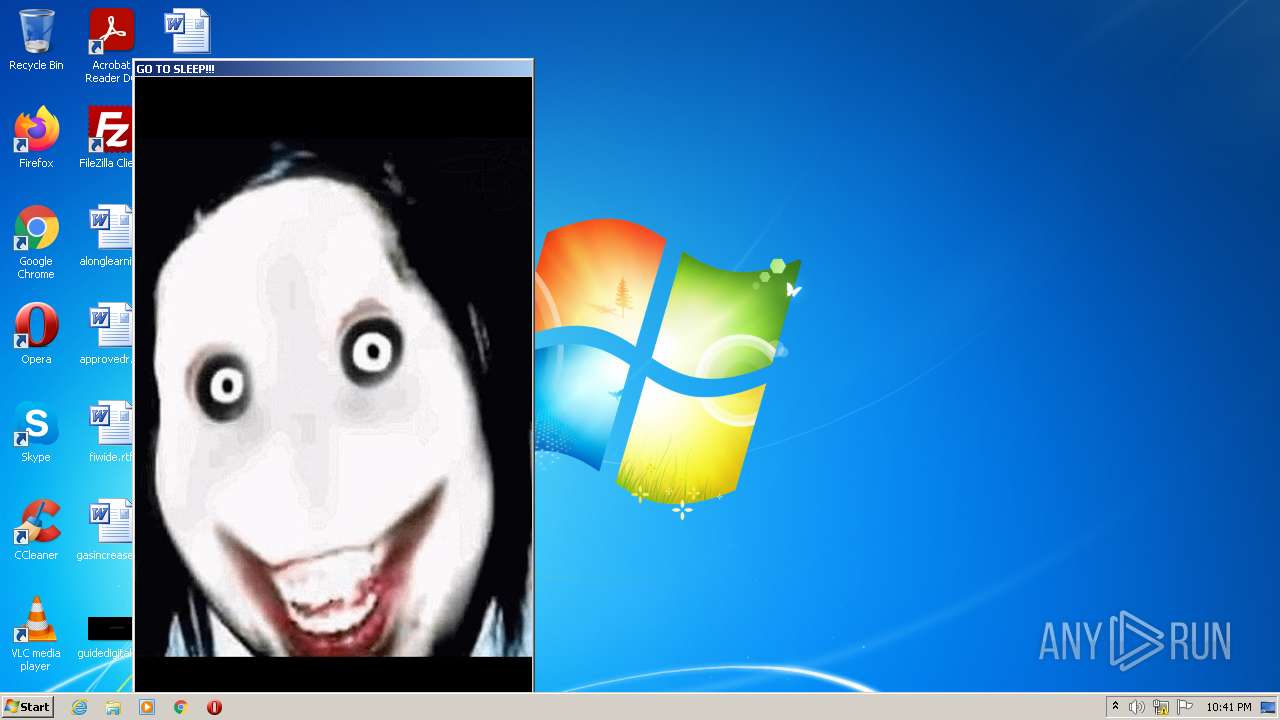
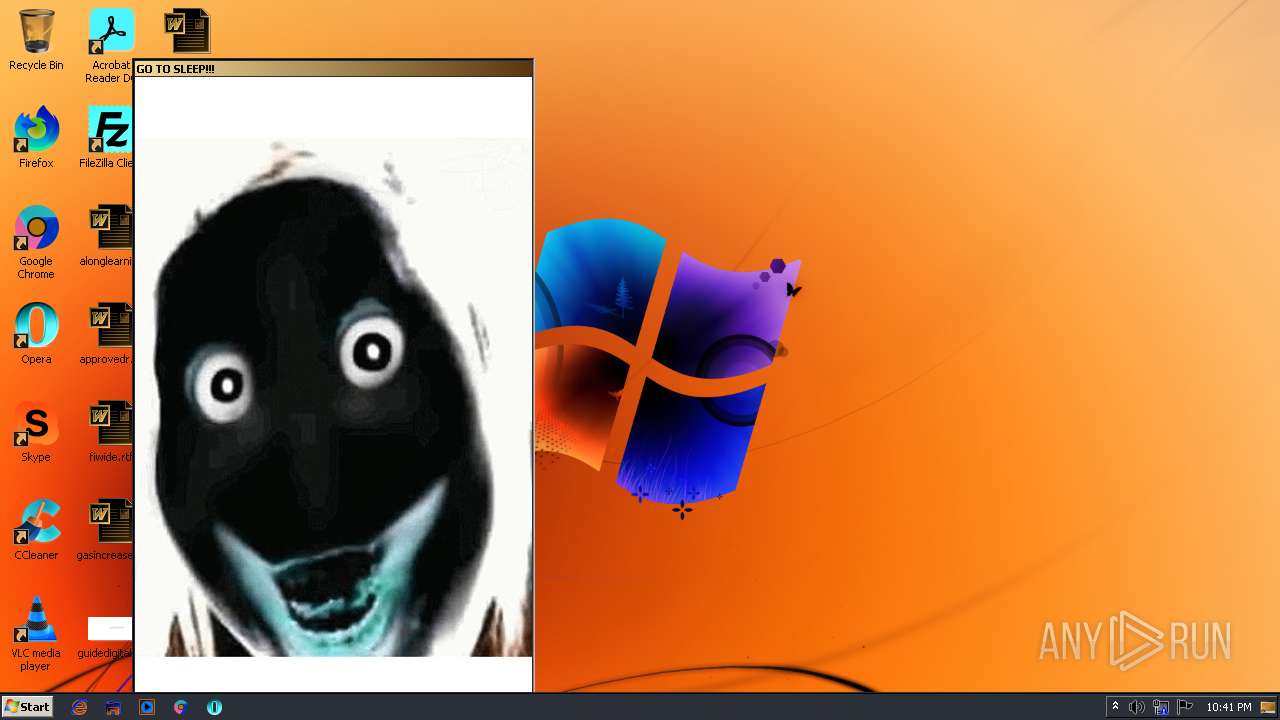
| File name: | WISEA J171227.81-232210.7.exe |
| Full analysis: | https://app.any.run/tasks/ad125100-a800-4c44-8030-3e4ae01b48bd |
| Verdict: | Malicious activity |
| Analysis date: | January 28, 2022, 22:39:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 1A2C5145B217E1DF1DA776BE54758B4C |
| SHA1: | BDC088A007C1E2BE1D814702CC513D9CE9A2A20C |
| SHA256: | 7B9DA8CDE71455485279766FED3F3477B2A86A3B292AC9A07875F28F5C59C519 |
| SSDEEP: | 49152:9rB9lq48gkFtXRKkV2BbFvjNDe6oMGFdGlX:ffq2kFtXR9UBRvjNDe6vGFdu |
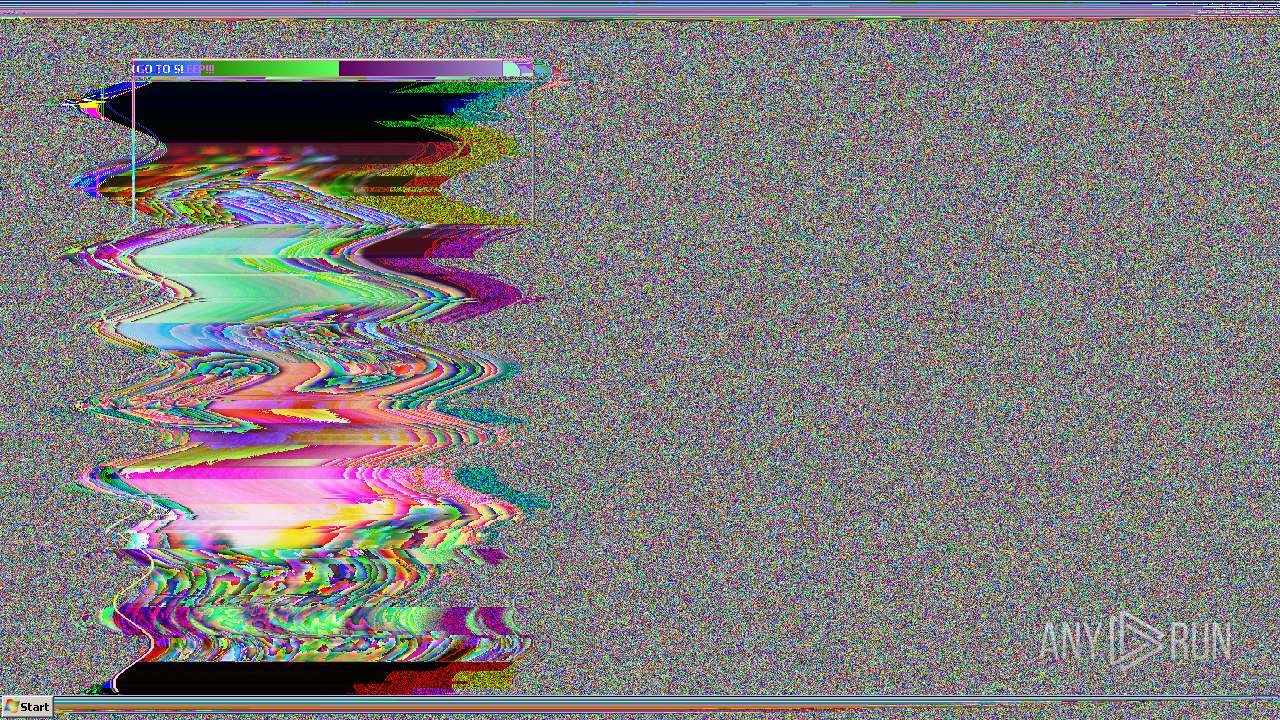
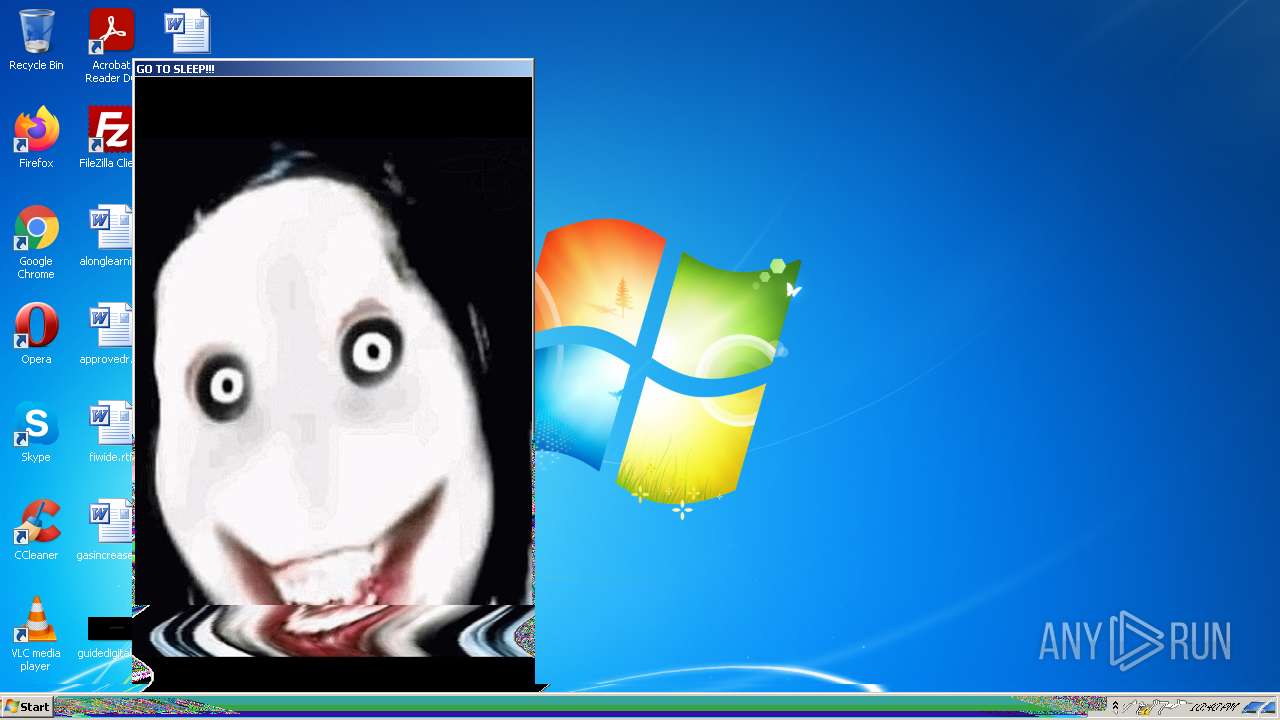
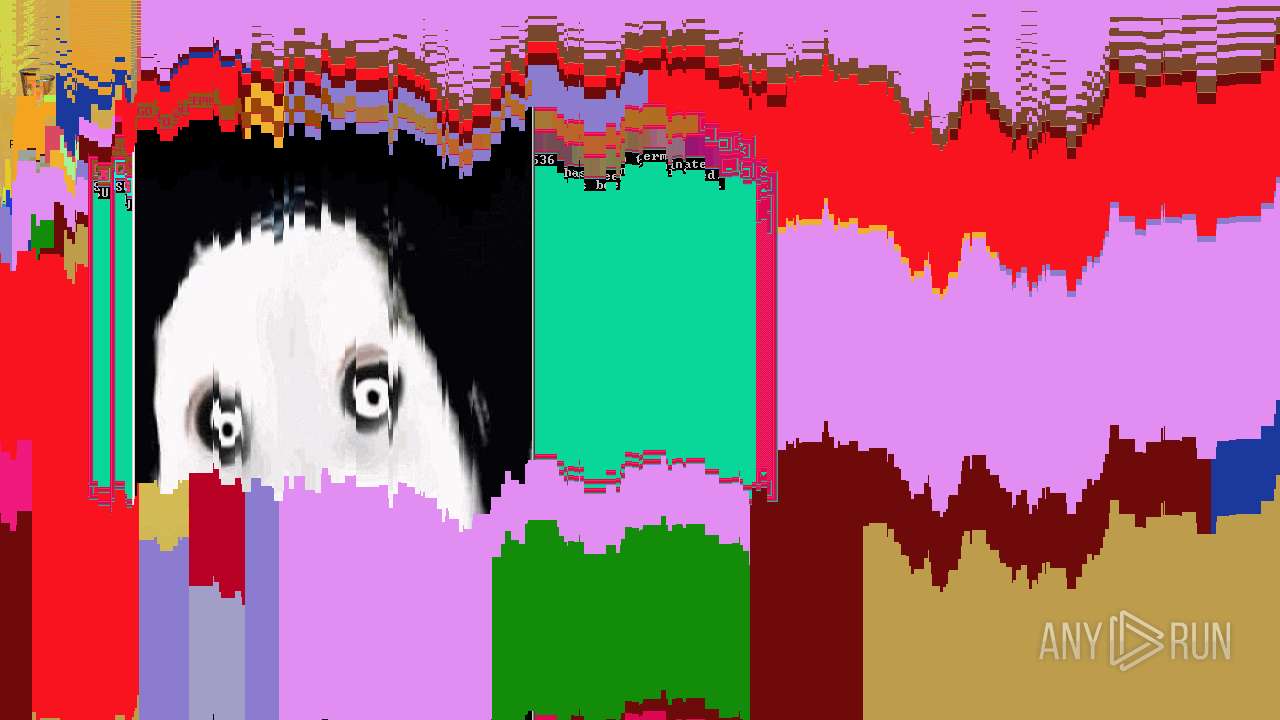
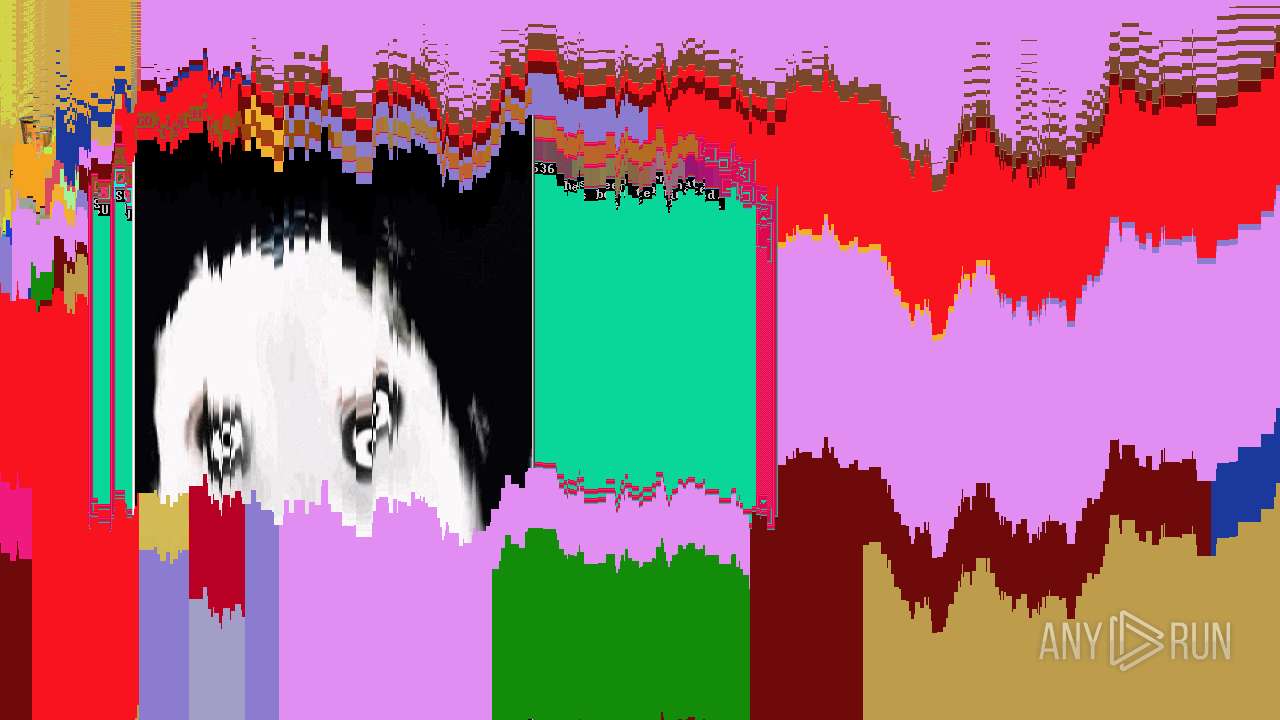
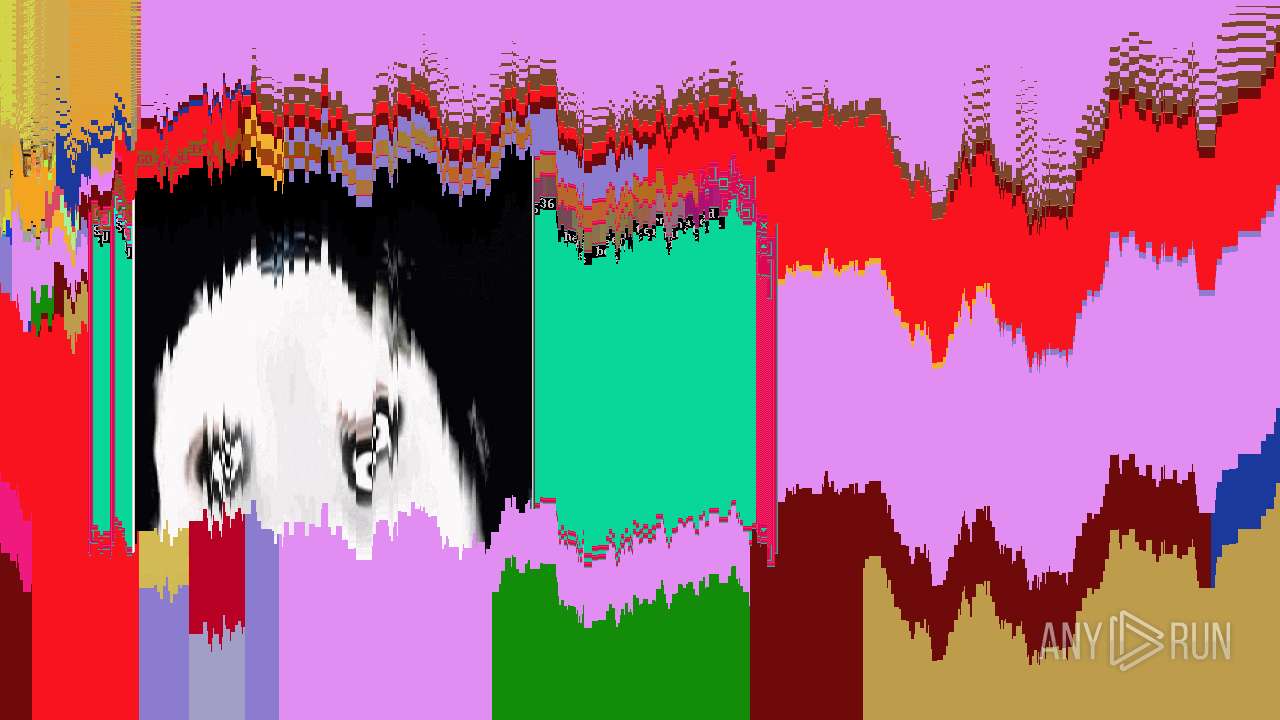
MALICIOUS
Application was dropped or rewritten from another process
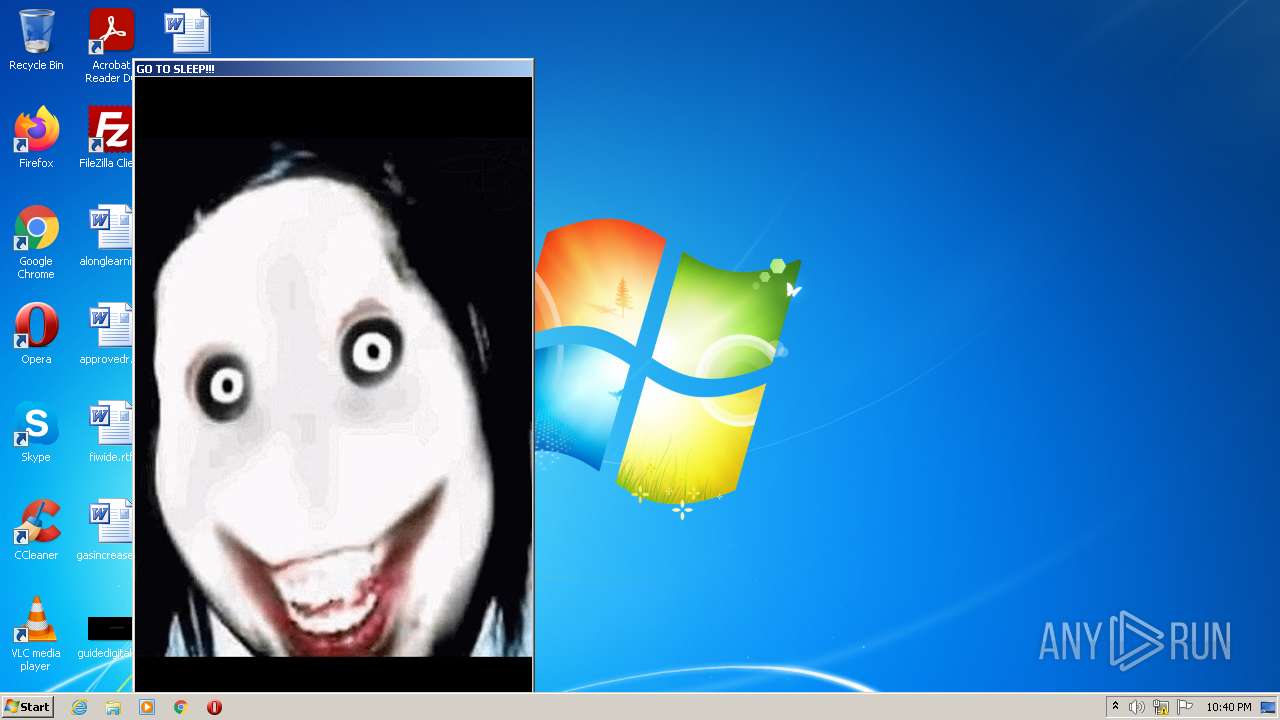
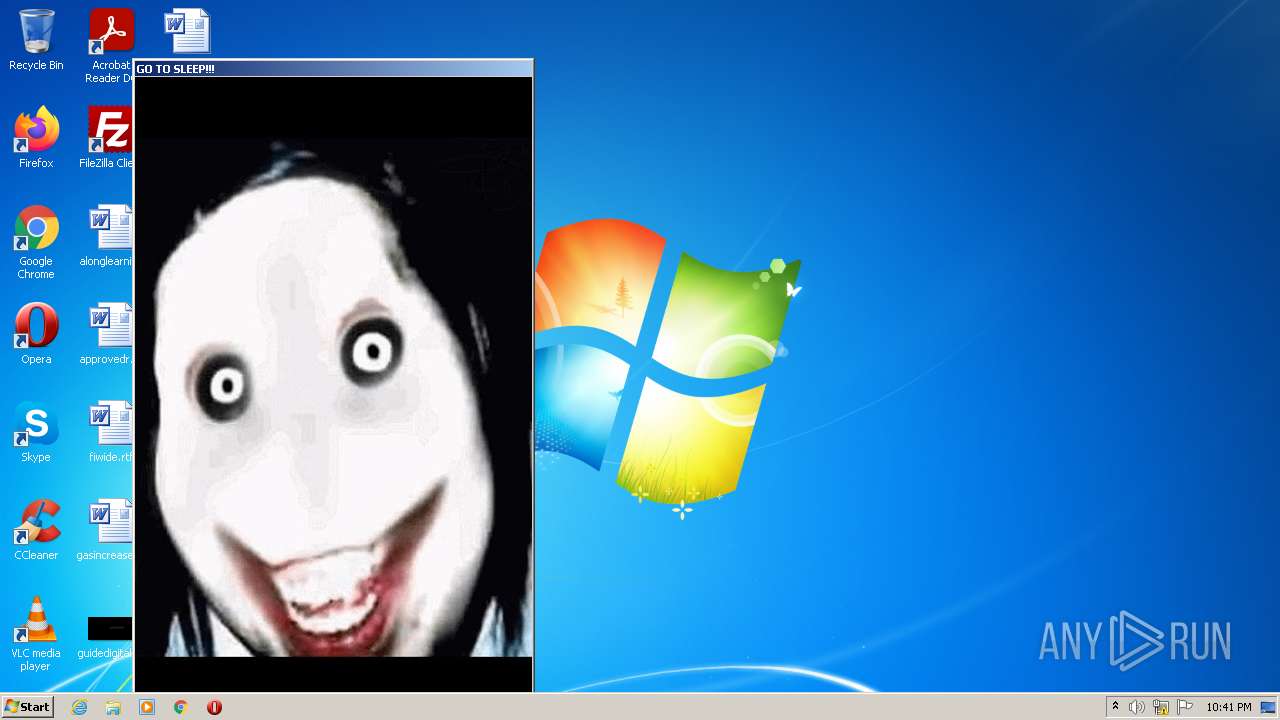
- jeffscream.exe (PID: 308)
- mlt.exe (PID: 2692)
- snd1.exe (PID: 1252)
- ColorA.exe (PID: 452)
- sw.exe (PID: 2972)
- mlt.exe (PID: 3048)
- TransparentBlt.exe (PID: 1536)
- mlt.exe (PID: 864)
- PatBlt3.exe (PID: 3800)
- PatBlt.exe (PID: 3892)
- reds.exe (PID: 2724)
- gl2.exe (PID: 3872)
- bsod.exe (PID: 1992)
- mbr.exe (PID: 1712)
Drops executable file immediately after starts
- WISEA J171227.81-232210.7.exe (PID: 1972)
SUSPICIOUS
Checks supported languages
- WISEA J171227.81-232210.7.exe (PID: 1972)
- mlt.exe (PID: 2692)
- wscript.exe (PID: 2664)
- jeffscream.exe (PID: 308)
- sw.exe (PID: 2972)
- ColorA.exe (PID: 452)
- snd1.exe (PID: 1252)
- mlt.exe (PID: 3048)
- PatBlt3.exe (PID: 3800)
- TransparentBlt.exe (PID: 1536)
- mlt.exe (PID: 864)
- PatBlt.exe (PID: 3892)
- reds.exe (PID: 2724)
- gl2.exe (PID: 3872)
- bsod.exe (PID: 1992)
- mbr.exe (PID: 1712)
Executable content was dropped or overwritten
- WISEA J171227.81-232210.7.exe (PID: 1972)
Drops a file that was compiled in debug mode
- WISEA J171227.81-232210.7.exe (PID: 1972)
Executes scripts
- WISEA J171227.81-232210.7.exe (PID: 1972)
Drops a file with a compile date too recent
- WISEA J171227.81-232210.7.exe (PID: 1972)
Reads the computer name
- wscript.exe (PID: 2664)
- snd1.exe (PID: 1252)
- WISEA J171227.81-232210.7.exe (PID: 1972)
Uses TASKKILL.EXE to kill process
- wscript.exe (PID: 2664)
INFO
Checks supported languages
- taskkill.exe (PID: 3212)
- taskkill.exe (PID: 2864)
- taskkill.exe (PID: 3300)
- taskkill.exe (PID: 2448)
- taskkill.exe (PID: 2236)
- taskkill.exe (PID: 484)
- taskkill.exe (PID: 3304)
- taskkill.exe (PID: 3344)
- taskkill.exe (PID: 4044)
Reads the computer name
- taskkill.exe (PID: 3212)
- taskkill.exe (PID: 2864)
- taskkill.exe (PID: 2448)
- taskkill.exe (PID: 2236)
- taskkill.exe (PID: 3300)
- taskkill.exe (PID: 3344)
- taskkill.exe (PID: 3304)
- taskkill.exe (PID: 4044)
- taskkill.exe (PID: 484)
Checks Windows Trust Settings
- wscript.exe (PID: 2664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (64.1) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.5) |
| .exe | | | Win32 Executable (generic) (10.6) |
| .exe | | | Generic Win/DOS Executable (4.7) |
| .exe | | | DOS Executable Generic (4.7) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x21f950 |
| UninitializedDataSize: | 315392 |
| InitializedDataSize: | 258048 |
| CodeSize: | 1912832 |
| LinkerVersion: | 2.5 |
| PEType: | PE32 |
| TimeStamp: | 2018:02:01 21:46:09+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 01-Feb-2018 20:46:09 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 01-Feb-2018 20:46:09 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x0004D000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x0004E000 | 0x001D3000 | 0x001D2600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99989 |
.rsrc | 0x00221000 | 0x0003F000 | 0x0003E600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.58451 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.08821 | 672 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
2 | 5.26116 | 67624 | Latin 1 / Western European | UNKNOWN | RT_ICON |
3 | 5.48477 | 38056 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 5.46325 | 21640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 5.39077 | 16936 | Latin 1 / Western European | UNKNOWN | RT_ICON |
6 | 5.61214 | 9640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
7 | 5.65808 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
8 | 5.86741 | 2440 | Latin 1 / Western European | UNKNOWN | RT_ICON |
9 | 5.76169 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
0E4D90C0EBD3C3AE9C2F57CA3DF16F89B99346BC | 7.99534 | 35084 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
Imports
COMCTL32.DLL |
GDI32.DLL |
KERNEL32.DLL |
MSVCRT.dll |
OLE32.DLL |
SHELL32.DLL |
SHLWAPI.DLL |
USER32.DLL |
WINMM.DLL |
Total processes
74
Monitored processes
26
Malicious processes
4
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Users\admin\AppData\Local\Temp\CDD7.tmp\jeffscream.exe" | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\jeffscream.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 6.06.0006 Modules
| |||||||||||||||
| 452 | "C:\Users\admin\AppData\Local\Temp\CDD7.tmp\ColorA.exe" | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\ColorA.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 484 | "C:\Windows\System32\taskkill.exe" /f /im TransparentBlt.exe | C:\Windows\System32\taskkill.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 864 | "C:\Users\admin\AppData\Local\Temp\CDD7.tmp\mlt.exe" | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\mlt.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1252 | "C:\Users\admin\AppData\Local\Temp\CDD7.tmp\snd1.exe" | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\snd1.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1536 | "C:\Users\admin\AppData\Local\Temp\CDD7.tmp\TransparentBlt.exe" | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\TransparentBlt.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1712 | "C:\Users\admin\AppData\Local\Temp\CDD7.tmp\mbr.exe" | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\mbr.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1972 | "C:\Users\admin\AppData\Local\Temp\WISEA J171227.81-232210.7.exe" | C:\Users\admin\AppData\Local\Temp\WISEA J171227.81-232210.7.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1992 | "C:\Users\admin\AppData\Local\Temp\CDD7.tmp\bsod.exe" | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\bsod.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2236 | "C:\Windows\System32\taskkill.exe" /f /im PatBlt3.exe | C:\Windows\System32\taskkill.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 599
Read events
1 583
Write events
16
Delete events
0
Modification events
| (PID) Process: | (1972) WISEA J171227.81-232210.7.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1972) WISEA J171227.81-232210.7.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1972) WISEA J171227.81-232210.7.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1972) WISEA J171227.81-232210.7.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2664) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2664) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2664) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2664) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
12
Suspicious files
1
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1972 | WISEA J171227.81-232210.7.exe | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\mbr.exe | executable | |
MD5:751C94891803E5C4C46DB04C25AAA5E1 | SHA256:7E2528E49ED6DC71CB8ACE28E6C4D11D8F5DF9E518992221A2A53D259E3910F3 | |||
| 1972 | WISEA J171227.81-232210.7.exe | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\jeffscream.exe | executable | |
MD5:AE532CA673CE29CAD72FE09C7B2390C0 | SHA256:FC6B50B29FD5DB6C62B2143E55A317C50682DE7FEBF4EB60DB39E1AF00E822F5 | |||
| 1972 | WISEA J171227.81-232210.7.exe | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\CDD8.tmp\CDD9.vbs | binary | |
MD5:71C0265C199A52C5879135819236232B | SHA256:DD49EDC7CD2930A9E9A9DE141637EF560EB5BD96EFF56F8FF48EAC958116C270 | |||
| 1972 | WISEA J171227.81-232210.7.exe | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\mlt.exe | executable | |
MD5:BC183F5854488A0774969EC19B492153 | SHA256:4B97506AE7118DEA78E251492166888732815F5CDC90B9C56DE2F9EE3862B20F | |||
| 1972 | WISEA J171227.81-232210.7.exe | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\snd1.exe | executable | |
MD5:C59DBF876BF5AB5F7073E38B382F2686 | SHA256:85C6416337E28D1CA1C5DAC316CDB36B967E6ABF18F4D19CC85B1471FF382C28 | |||
| 1972 | WISEA J171227.81-232210.7.exe | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\bsod.exe | executable | |
MD5:6CA54B7AD61F828445B49B0B5D66E291 | SHA256:7CDB69DD054F13CCAAC87AFCA4F6EF75A7415A2EB5EBBA6A49BB8C2861C8D516 | |||
| 1972 | WISEA J171227.81-232210.7.exe | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\ColorA.exe | executable | |
MD5:90C7241B937FF484C32271C9FDE1BC25 | SHA256:6F68804118352C0BE4D0AA84DECB4958B50BA570F481D6351E9D852312B7A2BD | |||
| 1972 | WISEA J171227.81-232210.7.exe | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\gl2.exe | executable | |
MD5:CEEE61C4A9EBD36707D83AA048C17E89 | SHA256:453FDAFD5AB832BE209A2ECBAC9D7A04DF14549A533E2D498BF7CD70931759C4 | |||
| 1972 | WISEA J171227.81-232210.7.exe | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\PatBlt3.exe | executable | |
MD5:08E74E5F077F0337D0C0D15DDE94F8BE | SHA256:B41D36F67E147133F8C3AA054B52275F68D7E2735A65EB3ABCDCD08BEDE1100B | |||
| 1972 | WISEA J171227.81-232210.7.exe | C:\Users\admin\AppData\Local\Temp\CDD7.tmp\PatBlt.exe | executable | |
MD5:5DB9E58F4A0275540361FA0B5E847708 | SHA256:361B92A974678B4C920C992CD5DC1B26E3E14114A7525B3133545080BB19C007 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report