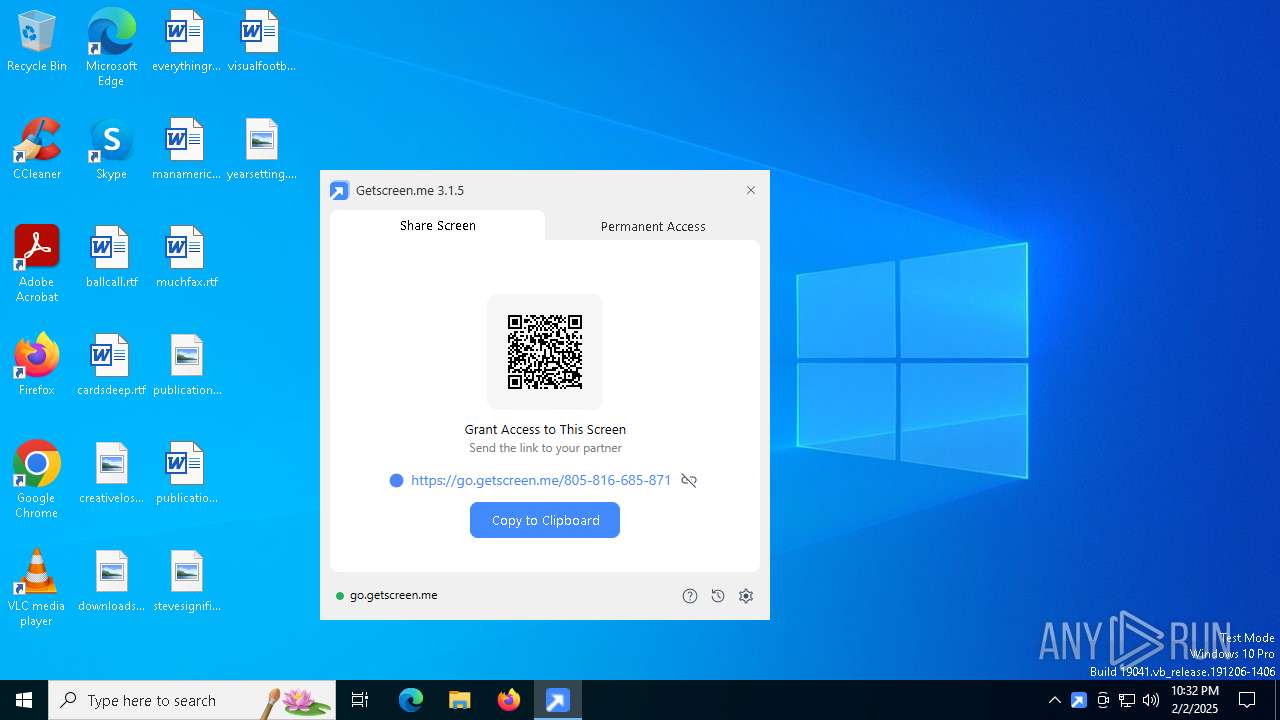
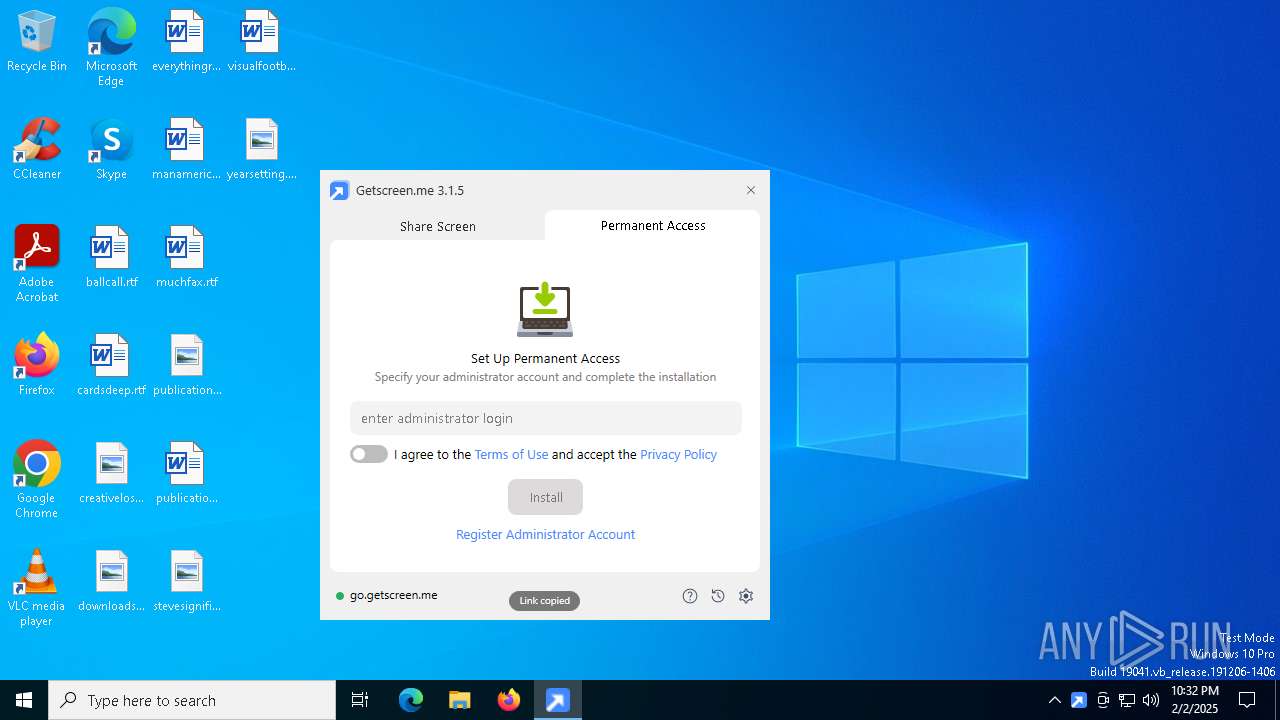
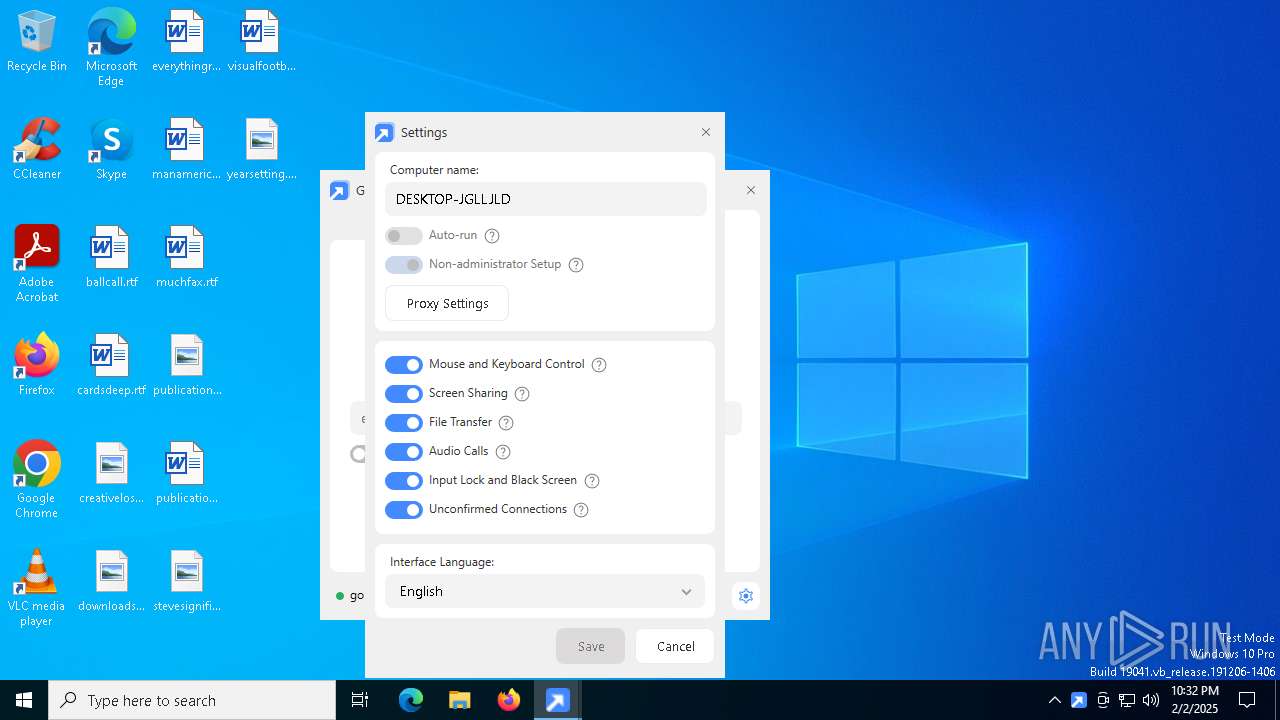
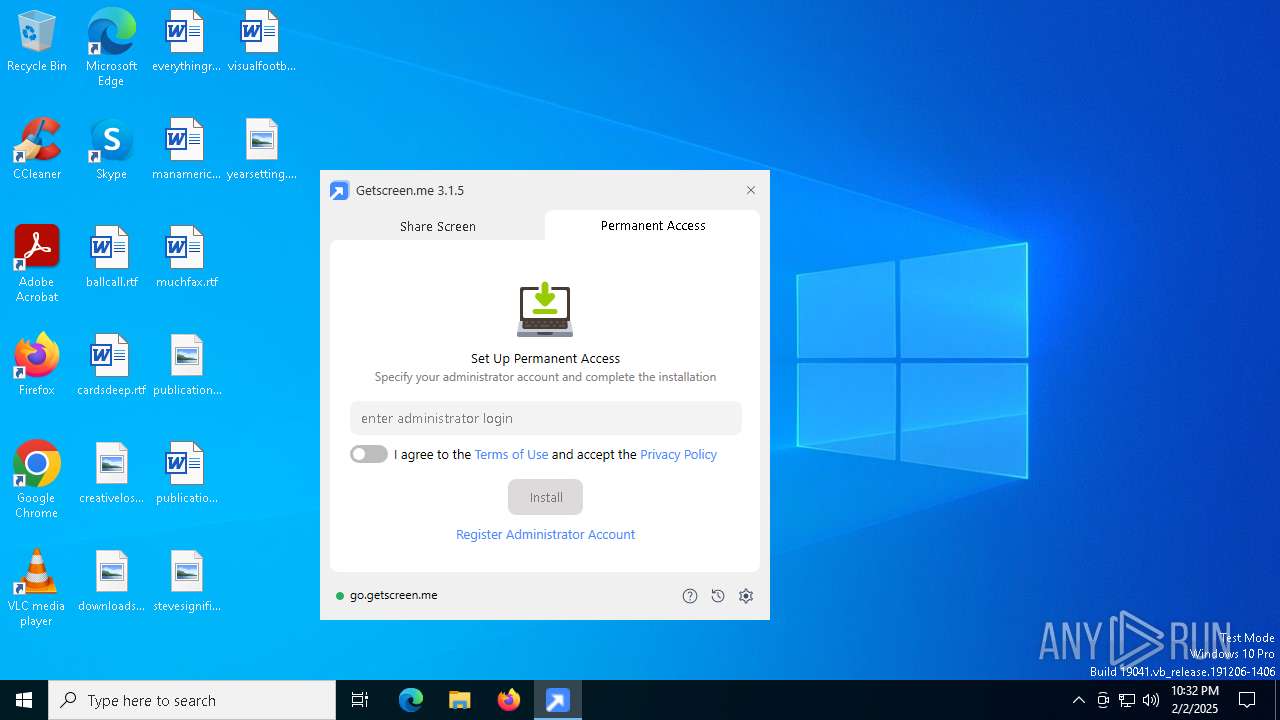
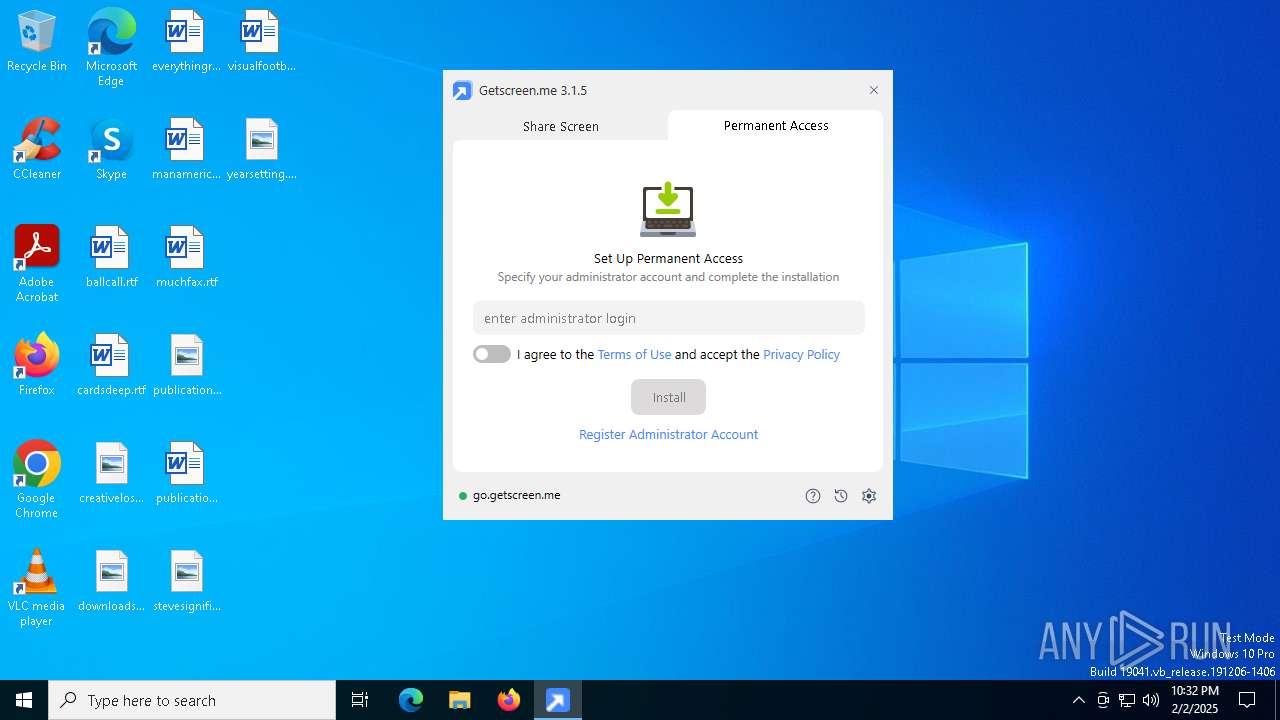
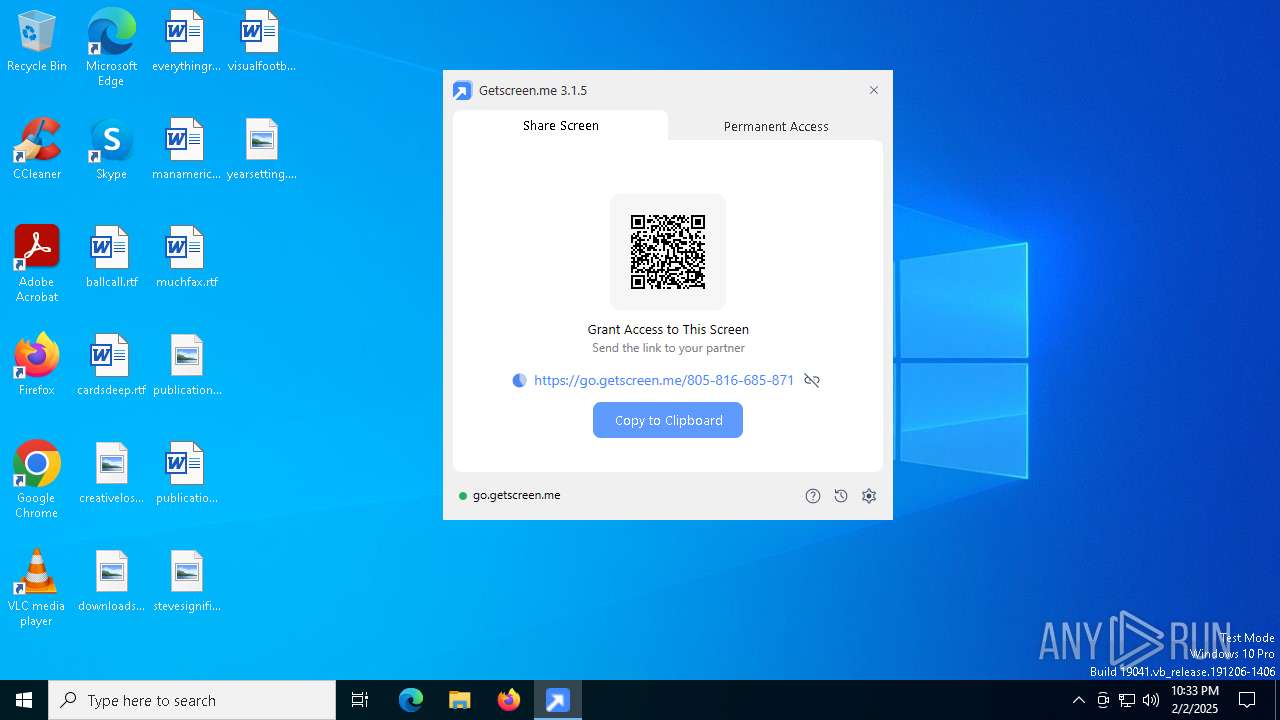
| download: | /download/getscreen.exe |
| Full analysis: | https://app.any.run/tasks/d2cd1fb8-3352-4f10-97f9-d112cd31f2a7 |
| Verdict: | Malicious activity |
| Analysis date: | February 02, 2025, 22:31:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 3 sections |
| MD5: | D8F4AC49C046E29F1368DCEB7D7733A8 |
| SHA1: | E84D8A3DED5B2405973955ACF2C24D5B83DA86C2 |
| SHA256: | 7B8B59710B254A3EB01C02E1B7279781372FE08453227906CC28709C607C2F1F |
| SSDEEP: | 98304:iqOQ9I4d9VOc0JbI8UQjYgwmZKJ711vtqCFEA5yy2jJ0BER7rWR9+kCQEa0wWifS:DInfVUDblSErpU |
MALICIOUS
GETMESCREEN has been detected (SURICATA)
- getscreen.exe (PID: 6176)
SUSPICIOUS
Reads security settings of Internet Explorer
- getscreen.exe (PID: 3220)
Reads the date of Windows installation
- getscreen.exe (PID: 3220)
Application launched itself
- getscreen.exe (PID: 3220)
- getscreen.exe (PID: 6176)
Connects to unusual port
- getscreen.exe (PID: 6176)
There is functionality for taking screenshot (YARA)
- getscreen.exe (PID: 6176)
Executable content was dropped or overwritten
- getscreen.exe (PID: 6176)
Executes as Windows Service
- kbvlduskxeobhyhwxuurbeldsservuf-elevate.exe (PID: 6220)
INFO
Reads the computer name
- getscreen.exe (PID: 3220)
- getscreen.exe (PID: 6492)
- kbvlduskxeobhyhwxuurbeldsservuf-elevate.exe (PID: 6220)
- getscreen.exe (PID: 6176)
- getscreen.exe (PID: 6376)
Process checks computer location settings
- getscreen.exe (PID: 3220)
Checks supported languages
- getscreen.exe (PID: 3220)
- getscreen.exe (PID: 6376)
- getscreen.exe (PID: 6492)
- kbvlduskxeobhyhwxuurbeldsservuf-elevate.exe (PID: 6220)
- getscreen.exe (PID: 6176)
Creates files in the program directory
- getscreen.exe (PID: 3220)
- getscreen.exe (PID: 6376)
- getscreen.exe (PID: 6492)
- getscreen.exe (PID: 6176)
Creates files or folders in the user directory
- getscreen.exe (PID: 6176)
Checks proxy server information
- getscreen.exe (PID: 6176)
UPX packer has been detected
- getscreen.exe (PID: 6176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (87.1) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.4) |
| .exe | | | DOS Executable Generic (6.4) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:10:22 11:11:46+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 7606272 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | 27553792 |
| EntryPoint: | 0x21879d0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.1.5.0 |
| ProductVersionNumber: | 3.1.5.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Unknown (0009) |
| CharacterSet: | Unicode |
| CompanyName: | Getscreen.me |
| InternalName: | Getscreen.me |
| OriginalFileName: | getscreen.exe |
| ProductName: | Getscreen.me |
| FileVersion: | 3.1.5 |
| LegalCopyright: | Copyright (C) 2024 |
| ProductVersion: | 3.1.5 |
Total processes
131
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3220 | "C:\Users\admin\AppData\Local\Temp\getscreen.exe" | C:\Users\admin\AppData\Local\Temp\getscreen.exe | — | explorer.exe | |||||||||||
User: admin Company: Getscreen.me Integrity Level: MEDIUM Exit code: 0 Version: 3.1.5 Modules
| |||||||||||||||
| 6176 | "C:\Users\admin\AppData\Local\Temp\getscreen.exe" | C:\Users\admin\AppData\Local\Temp\getscreen.exe | getscreen.exe | ||||||||||||
User: admin Company: Getscreen.me Integrity Level: HIGH Version: 3.1.5 Modules
| |||||||||||||||
| 6220 | "C:\ProgramData\Getscreen.me\kbvlduskxeobhyhwxuurbeldsservuf-elevate.exe" -elevate \\.\pipe\elevateGS512kbvlduskxeobhyhwxuurbeldsservuf | C:\ProgramData\Getscreen.me\kbvlduskxeobhyhwxuurbeldsservuf-elevate.exe | — | services.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 1 Modules
| |||||||||||||||
| 6376 | "C:\Users\admin\AppData\Local\Temp\getscreen.exe" -cpipe \\.\pipe\PCommand96Getscreen.me -cmem 0000pipe0PCommand96Getscreen0mepco244uqvhv1aad -child | C:\Users\admin\AppData\Local\Temp\getscreen.exe | getscreen.exe | ||||||||||||
User: SYSTEM Company: Getscreen.me Integrity Level: SYSTEM Exit code: 1 Version: 3.1.5 Modules
| |||||||||||||||
| 6492 | "C:\Users\admin\AppData\Local\Temp\getscreen.exe" -gpipe \\.\pipe\PCommand97Getscreen.me -gui | C:\Users\admin\AppData\Local\Temp\getscreen.exe | getscreen.exe | ||||||||||||
User: SYSTEM Company: Getscreen.me Integrity Level: SYSTEM Version: 3.1.5 Modules
| |||||||||||||||
Total events
2 122
Read events
2 121
Write events
1
Delete events
0
Modification events
| (PID) Process: | (6492) getscreen.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\GetScreen\Getscreen.me |
| Operation: | write | Name: | Language |
Value: en | |||
Executable files
1
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6376 | getscreen.exe | C:\ProgramData\Getscreen.me\memory\0000pipe0PCommand96Getscreen0mepco244uqvhv1aad | — | |
MD5:— | SHA256:— | |||
| 6176 | getscreen.exe | C:\ProgramData\Getscreen.me\settings.dat | binary | |
MD5:ABA97805681BFD7A98E98557385F135C | SHA256:D804CA8BC2EC3856118040D18BBD788D1FA9C601D016D77946AF0E66278FBA14 | |||
| 6492 | getscreen.exe | C:\ProgramData\Getscreen.me\logs\20250202.capture.log | text | |
MD5:7456F8E47B73BDCF1696CDDE05E9439C | SHA256:07611FE1D95236620C5A142F9634C906063F74B0DBDA15CA4304E6808AD872E6 | |||
| 6176 | getscreen.exe | C:\Users\admin\AppData\Local\Getscreen.me\settings.dat | binary | |
MD5:ABA97805681BFD7A98E98557385F135C | SHA256:D804CA8BC2EC3856118040D18BBD788D1FA9C601D016D77946AF0E66278FBA14 | |||
| 6376 | getscreen.exe | C:\ProgramData\Getscreen.me\logs\20250202.gui.log | text | |
MD5:6206D9690636F117504032AACD4B5EF5 | SHA256:E13A1D4589A17EB7D27B332A2203DCA87060376DDA815BF21A800D2049FACC6F | |||
| 3220 | getscreen.exe | C:\ProgramData\Getscreen.me\logs\20250202.log | text | |
MD5:79B80350C3B0249FDC8BD49D13C7D331 | SHA256:29CAA932C1A49B405AA6B342E80A7F83DE4367B09A792D678C6299DF49000436 | |||
| 6176 | getscreen.exe | C:\ProgramData\Getscreen.me\kbvlduskxeobhyhwxuurbeldsservuf-elevate.exe | executable | |
MD5:D8F4AC49C046E29F1368DCEB7D7733A8 | SHA256:7B8B59710B254A3EB01C02E1B7279781372FE08453227906CC28709C607C2F1F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
55
DNS requests
25
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4128 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4128 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7020 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.112:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.21.65.154:443 | — | Akamai International B.V. | NL | unknown |
6176 | getscreen.exe | 64.176.173.218:3478 | px-il1.getscreen.me | — | — | unknown |
6176 | getscreen.exe | 162.55.165.163:3478 | px-eu1.getscreen.me | — | — | unknown |
6176 | getscreen.exe | 103.43.75.192:3478 | px-au1.getscreen.me | — | — | unknown |
6176 | getscreen.exe | 139.59.27.133:3478 | px-in1.getscreen.me | — | — | unknown |
6176 | getscreen.exe | 144.202.110.36:3478 | px-us1.getscreen.me | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
getscreen.me |
| unknown |
image.getscreen.me |
| unknown |
px-eu1.getscreen.me |
| unknown |
px-in1.getscreen.me |
| unknown |
px-il1.getscreen.me |
| unknown |
px-br1.getscreen.me |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6176 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6176 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6176 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6176 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6176 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6176 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6176 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
6176 | getscreen.exe | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
— | — | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
— | — | Misc activity | REMOTE [ANY.RUN] GetMeScreen Remote Desktop Software |
Process | Message |
|---|---|
getscreen.exe | unrecognized css selector at (this://app/main.htm(1))
|
getscreen.exe | unrecognized css selector at (this://app/settings.htm(1))
|