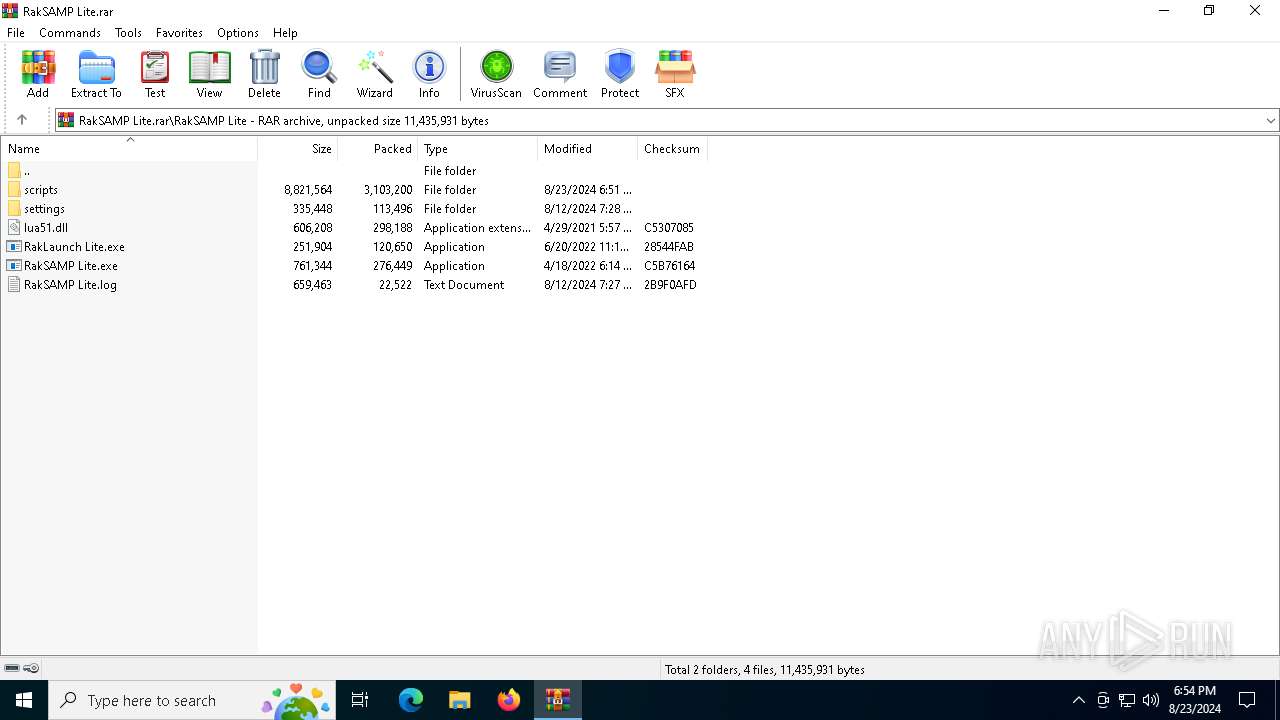
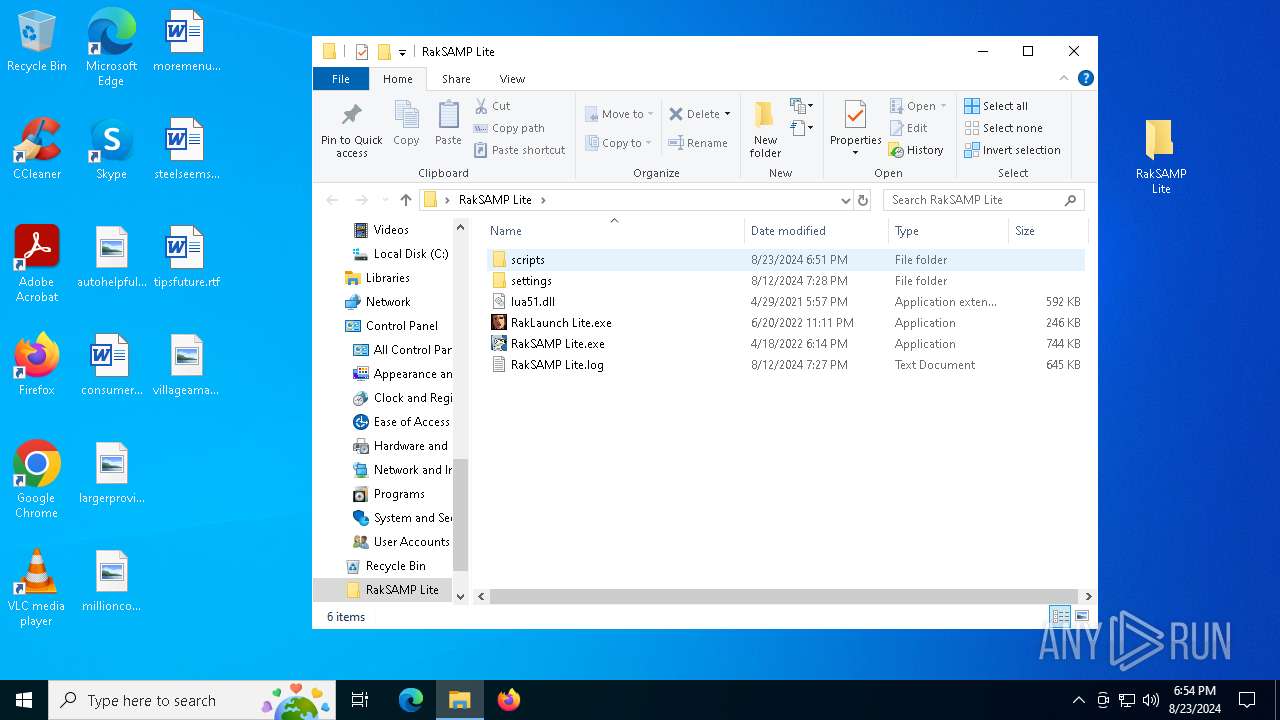
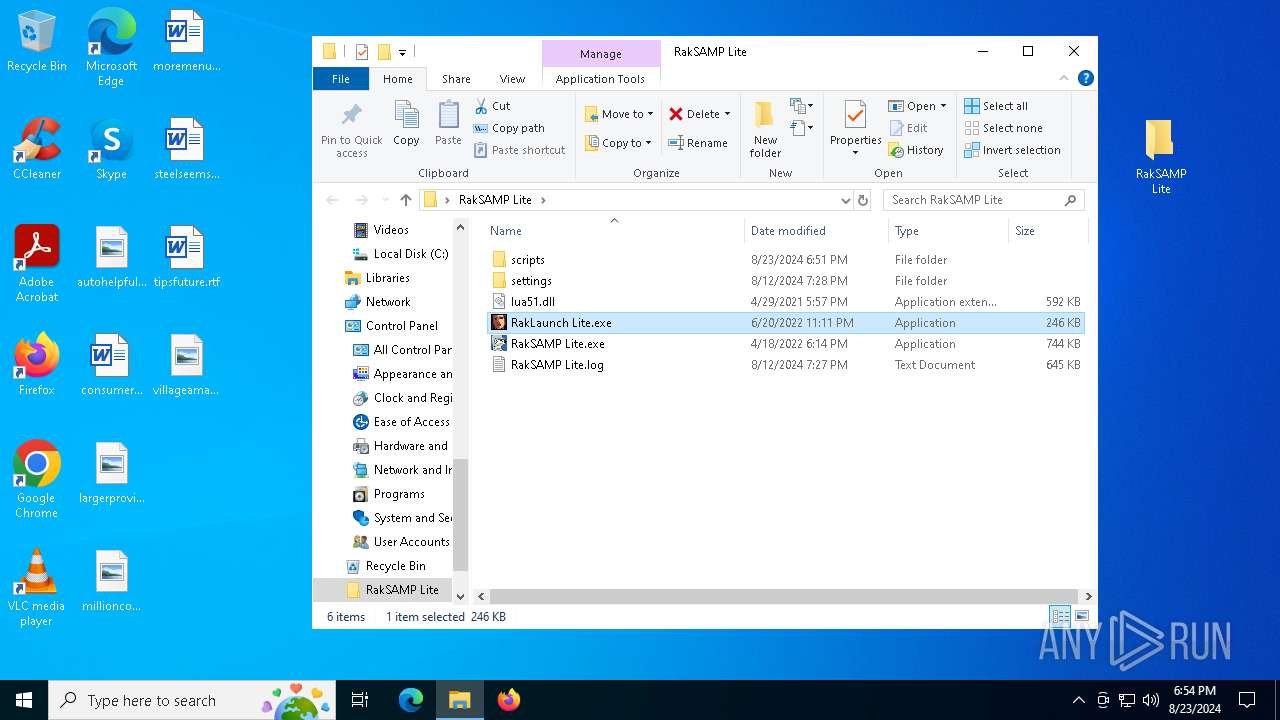
| File name: | RakSAMP Lite.rar |
| Full analysis: | https://app.any.run/tasks/3a4f8a58-b834-4e71-8709-4ca15576b76c |
| Verdict: | Malicious activity |
| Analysis date: | August 23, 2024, 18:53:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 811E03C940278C5CE0F499E28FA101B5 |
| SHA1: | 59DDA3E1550DB96181B9CF552E45E3BA2CC0425E |
| SHA256: | 7B8358BEF78109E14EDA409CACBF4EE6C2E0204D0DF9340C5BB732331A5357AA |
| SSDEEP: | 98304:FhkkQM+CXmDRPSdvRzDNo7LC+QbL0LtdUF+JijCE1nFdVulf75PfI0yxH2Qc0cLV:WVkxXA |
MALICIOUS
No malicious indicators.SUSPICIOUS
Potential Corporate Privacy Violation
- RakSAMP Lite.exe (PID: 7068)
Reads security settings of Internet Explorer
- RakLaunch Lite.exe (PID: 5464)
Reads the date of Windows installation
- RakLaunch Lite.exe (PID: 5464)
INFO
Checks supported languages
- RakLaunch Lite.exe (PID: 5464)
- RakSAMP Lite.exe (PID: 7068)
Reads the computer name
- RakLaunch Lite.exe (PID: 5464)
- RakSAMP Lite.exe (PID: 7068)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6660)
Manual execution by a user
- RakLaunch Lite.exe (PID: 5464)
Process checks computer location settings
- RakLaunch Lite.exe (PID: 5464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
135
Monitored processes
5
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5464 | "C:\Users\admin\Desktop\RakSAMP Lite\RakLaunch Lite.exe" | C:\Users\admin\Desktop\RakSAMP Lite\RakLaunch Lite.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5552 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6660 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\RakSAMP Lite.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
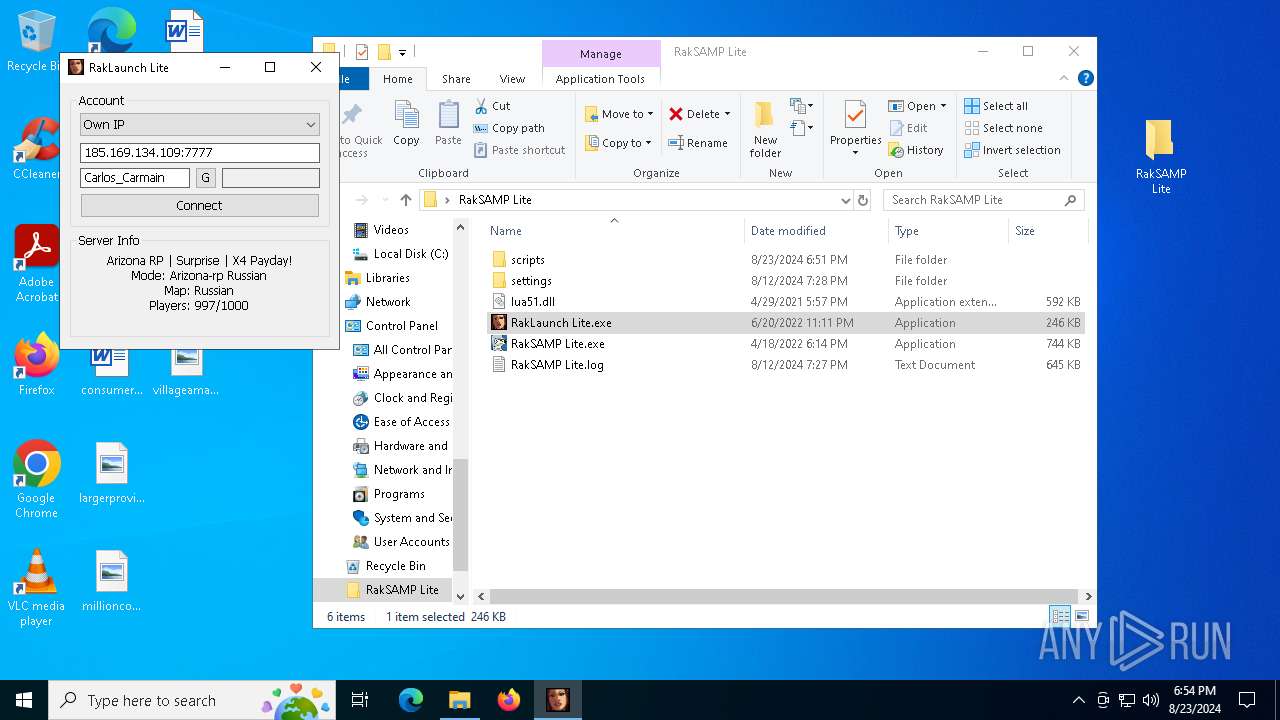
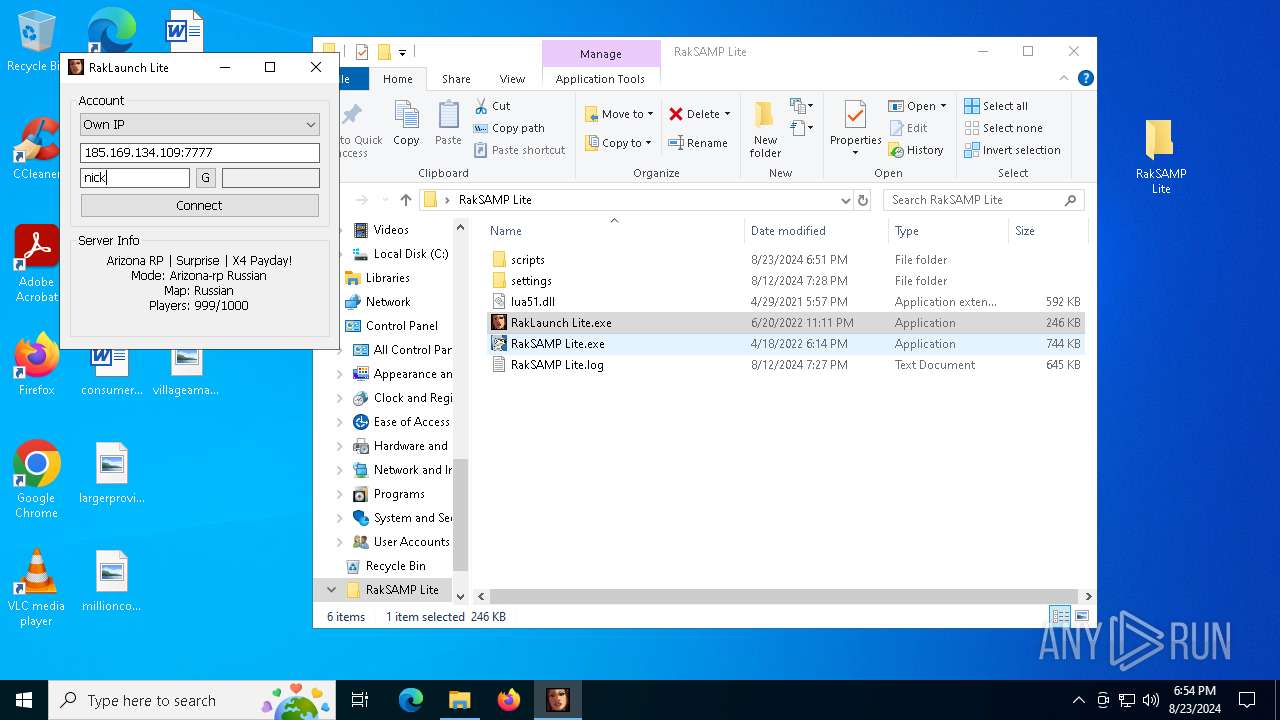
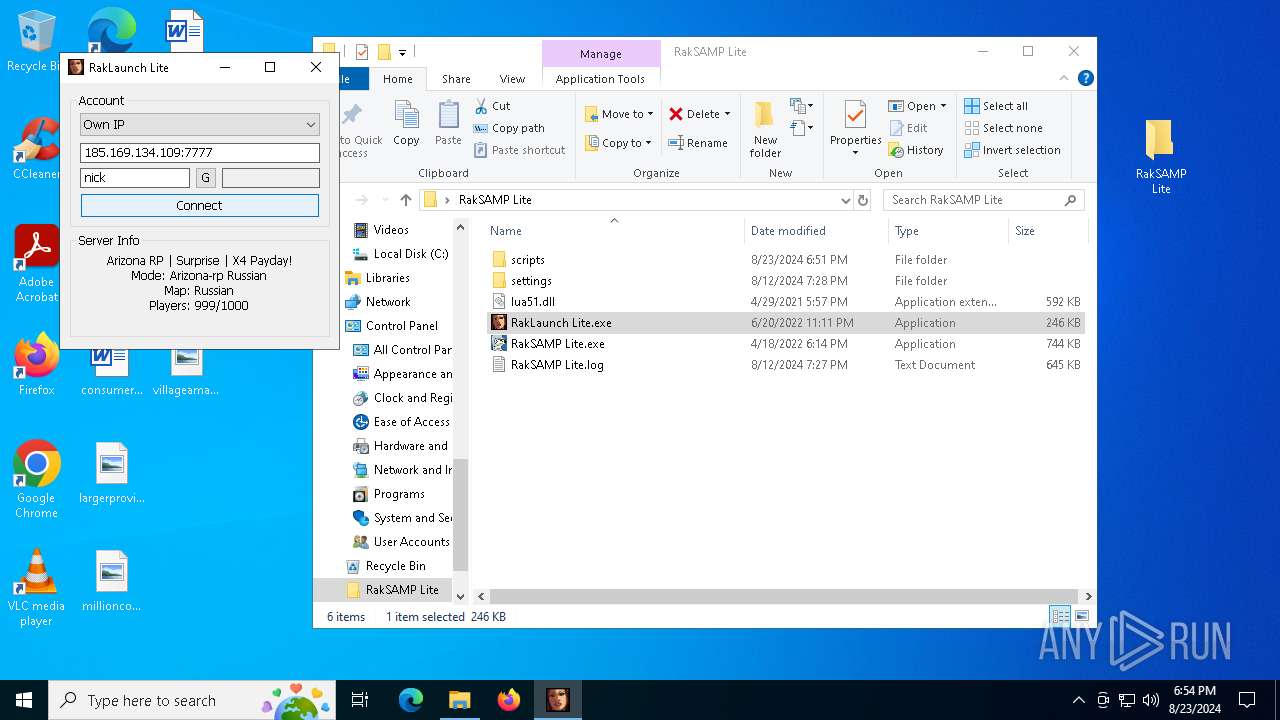
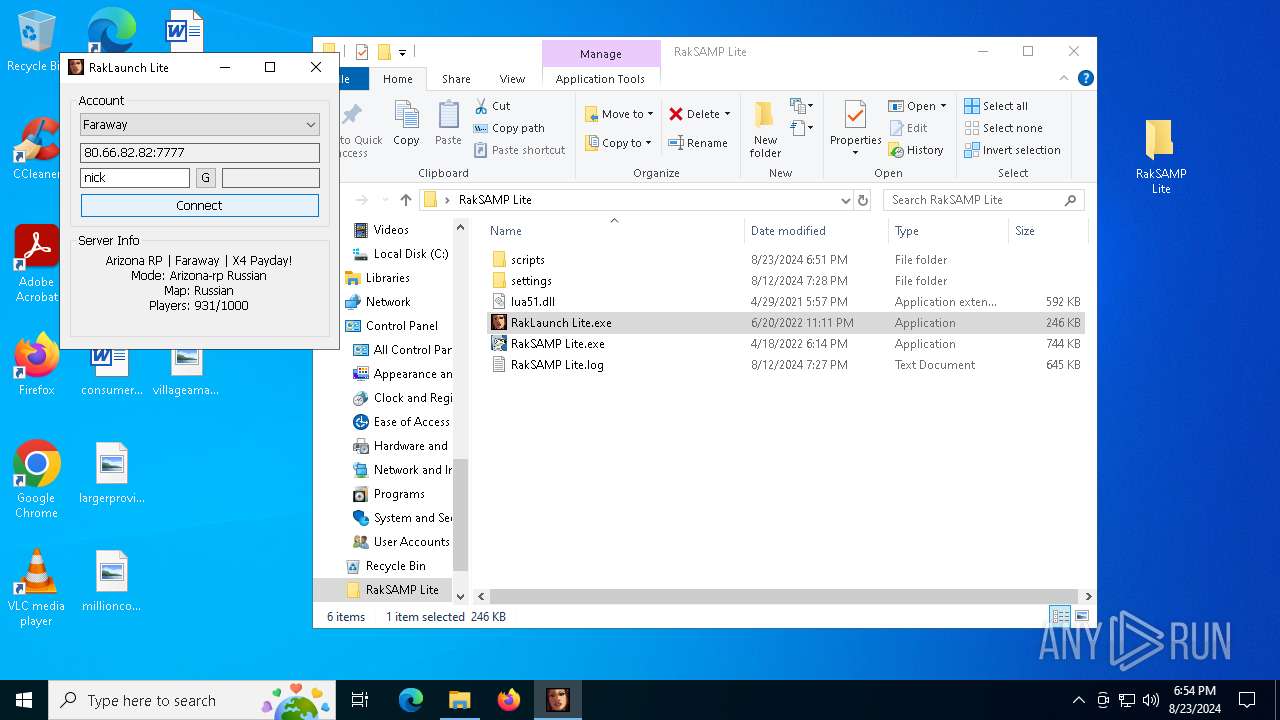
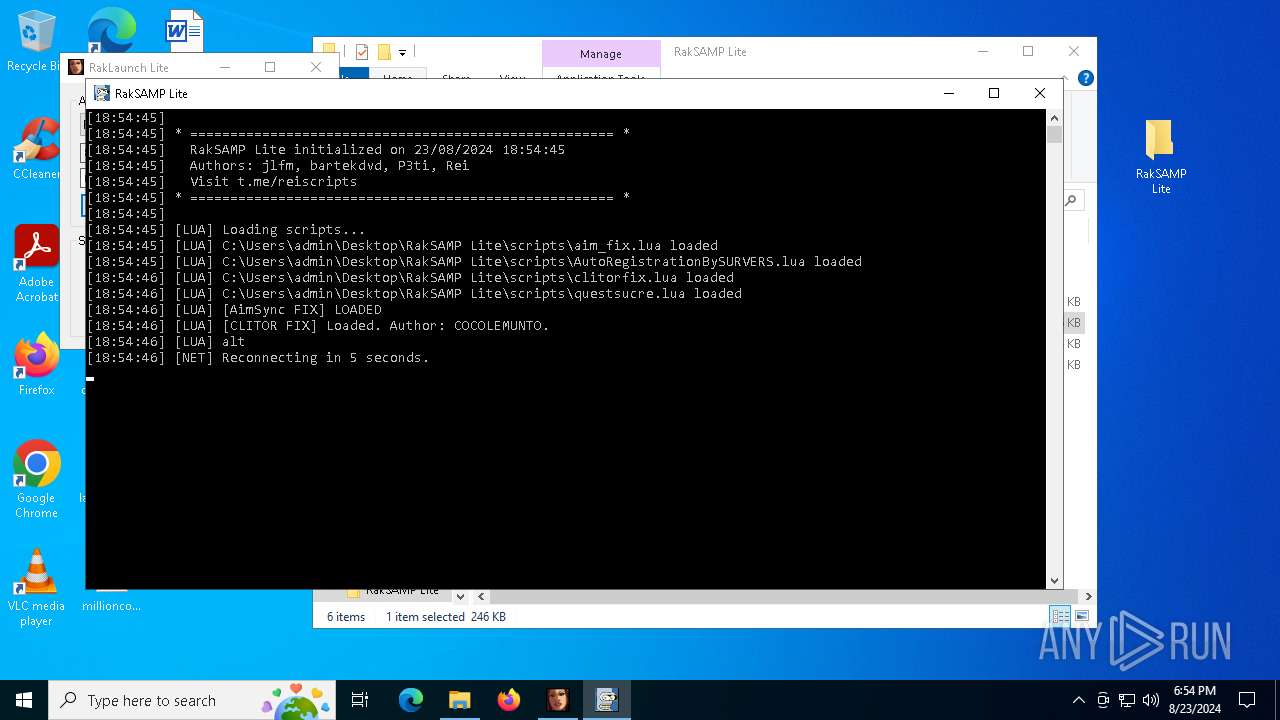
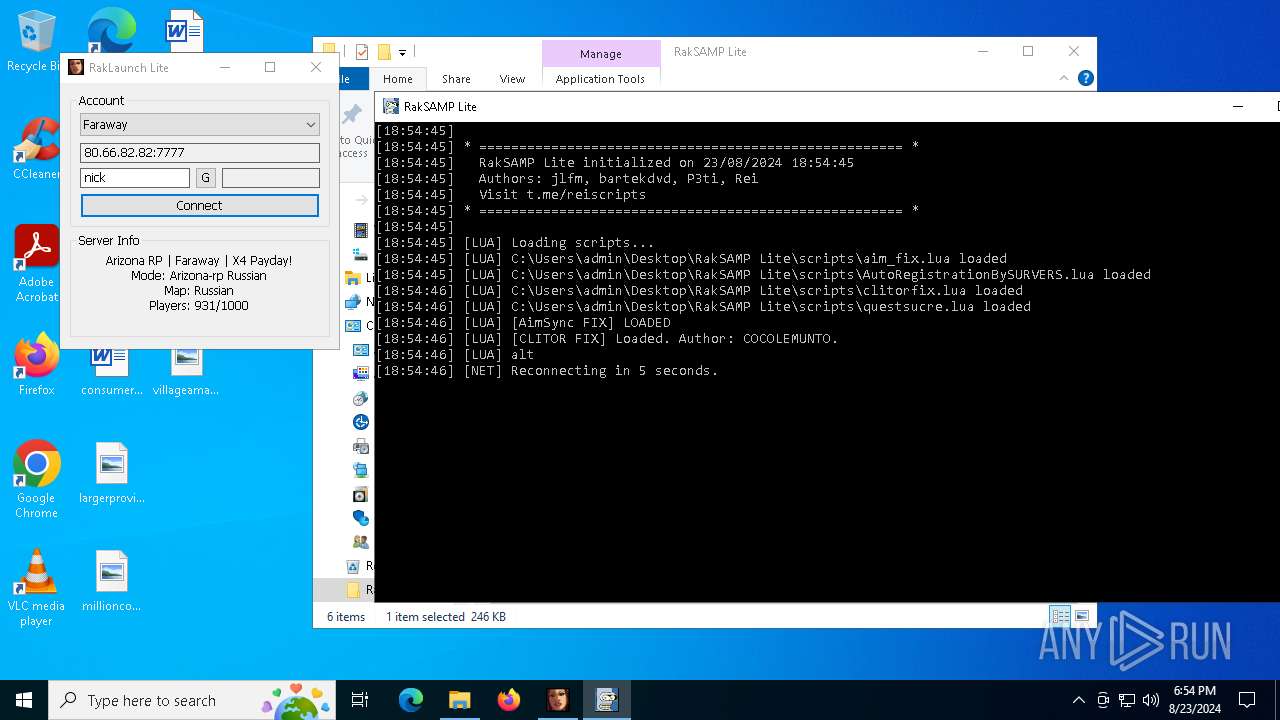
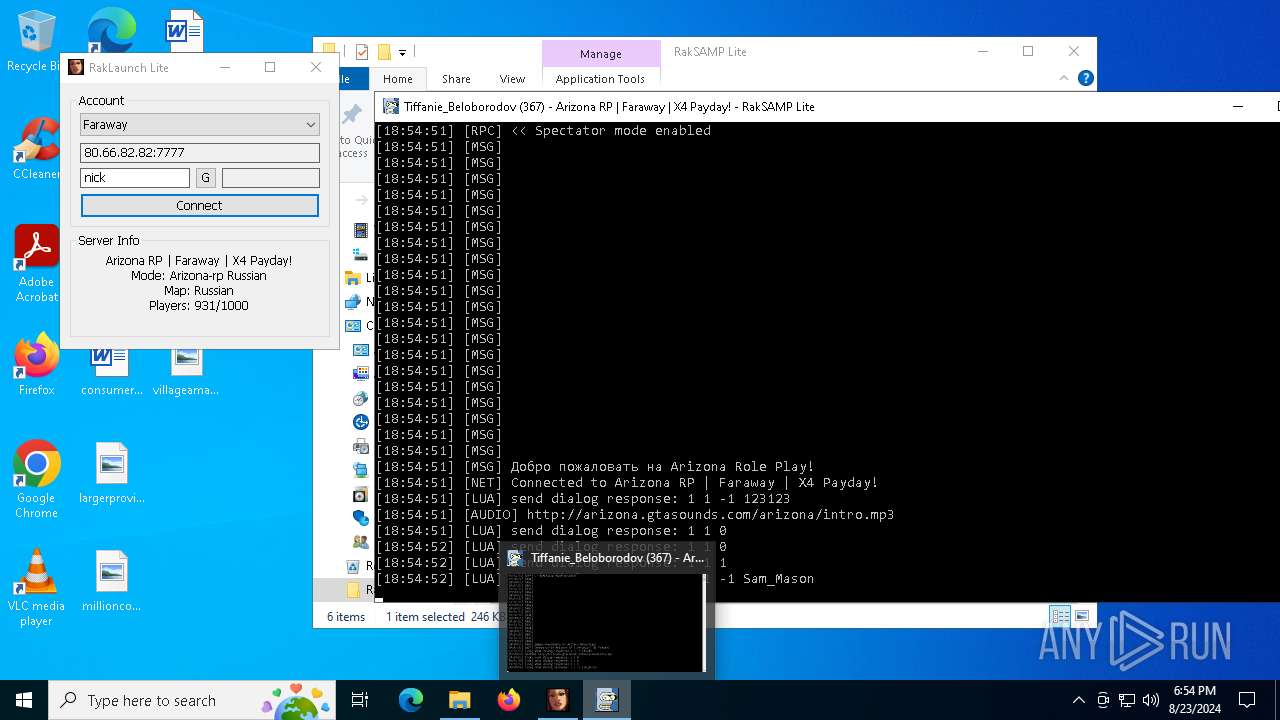
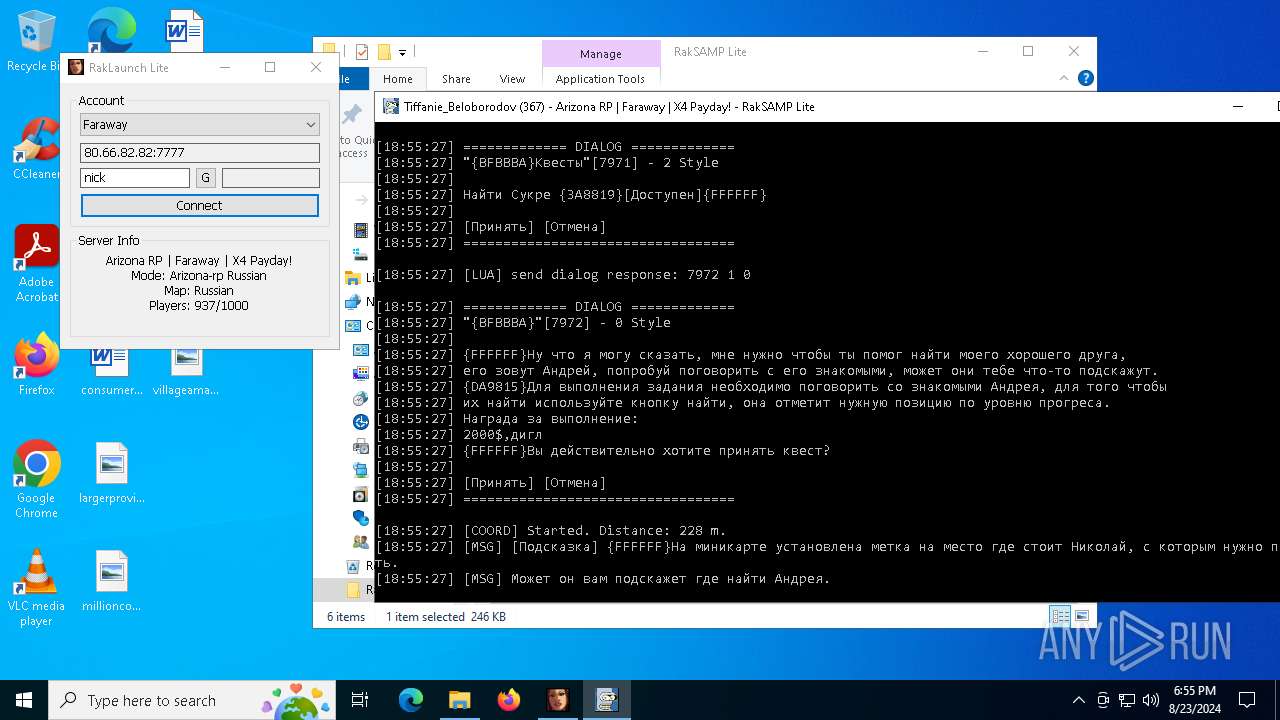
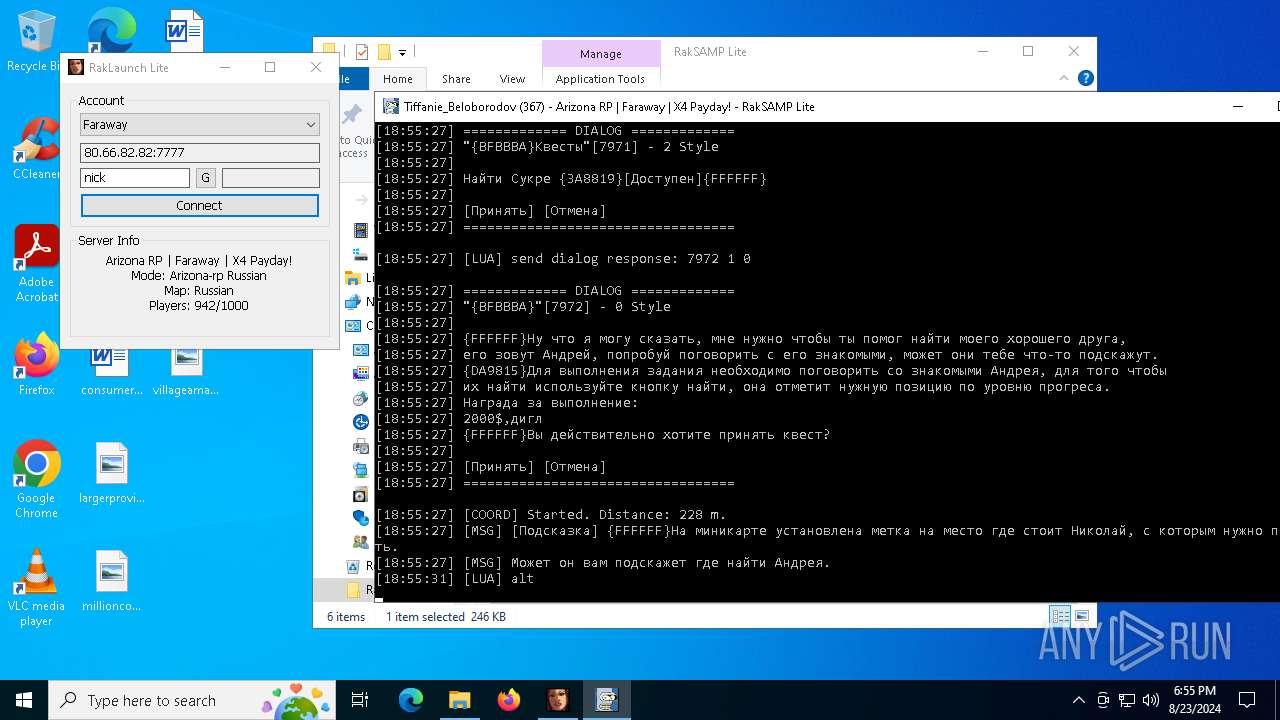
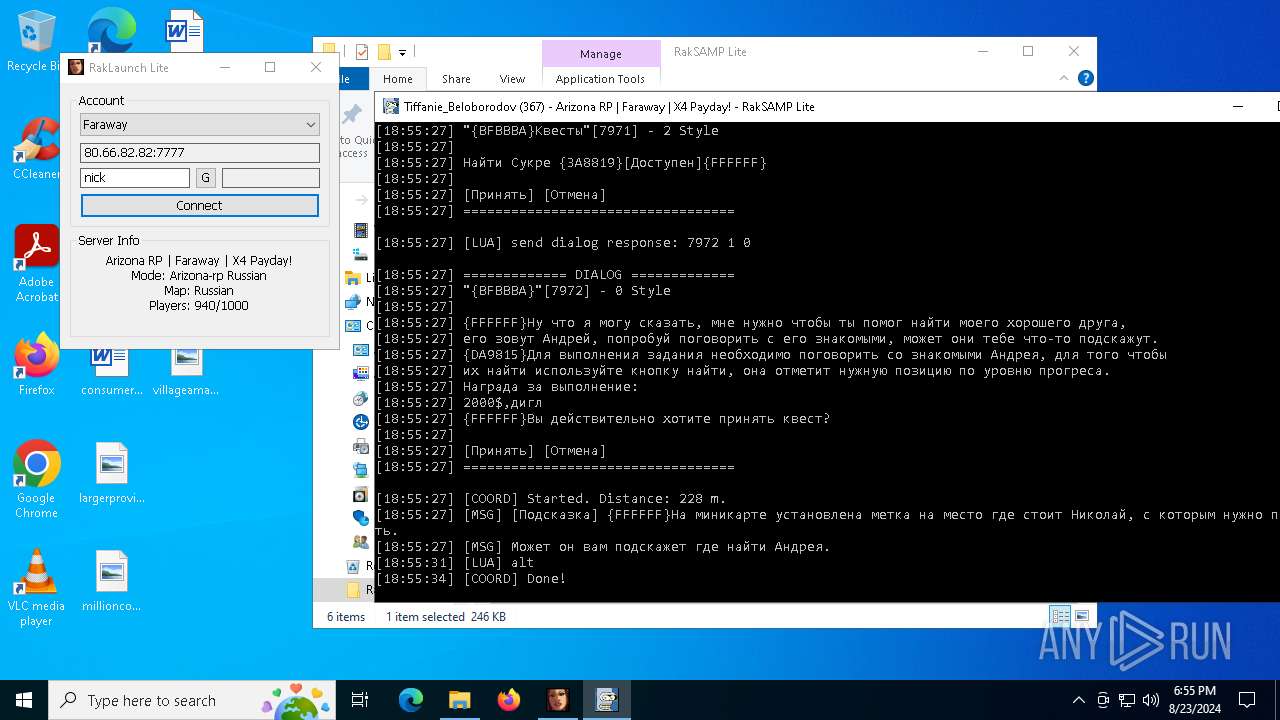
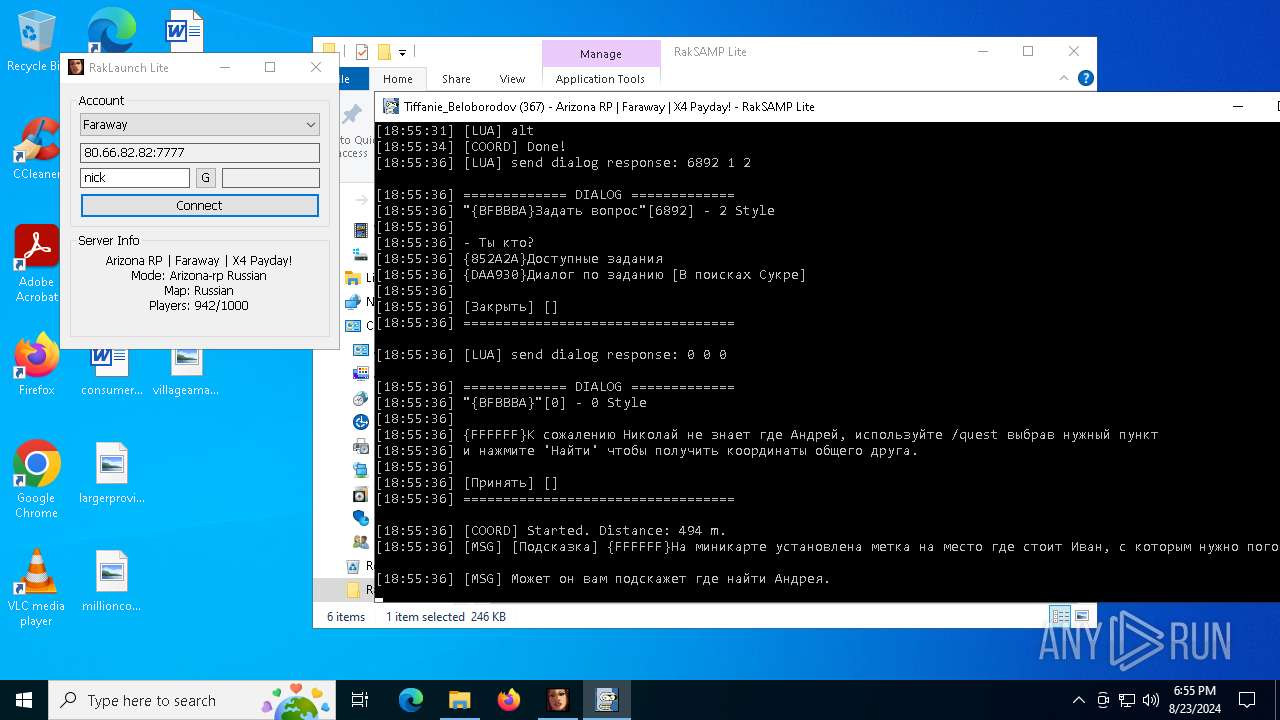
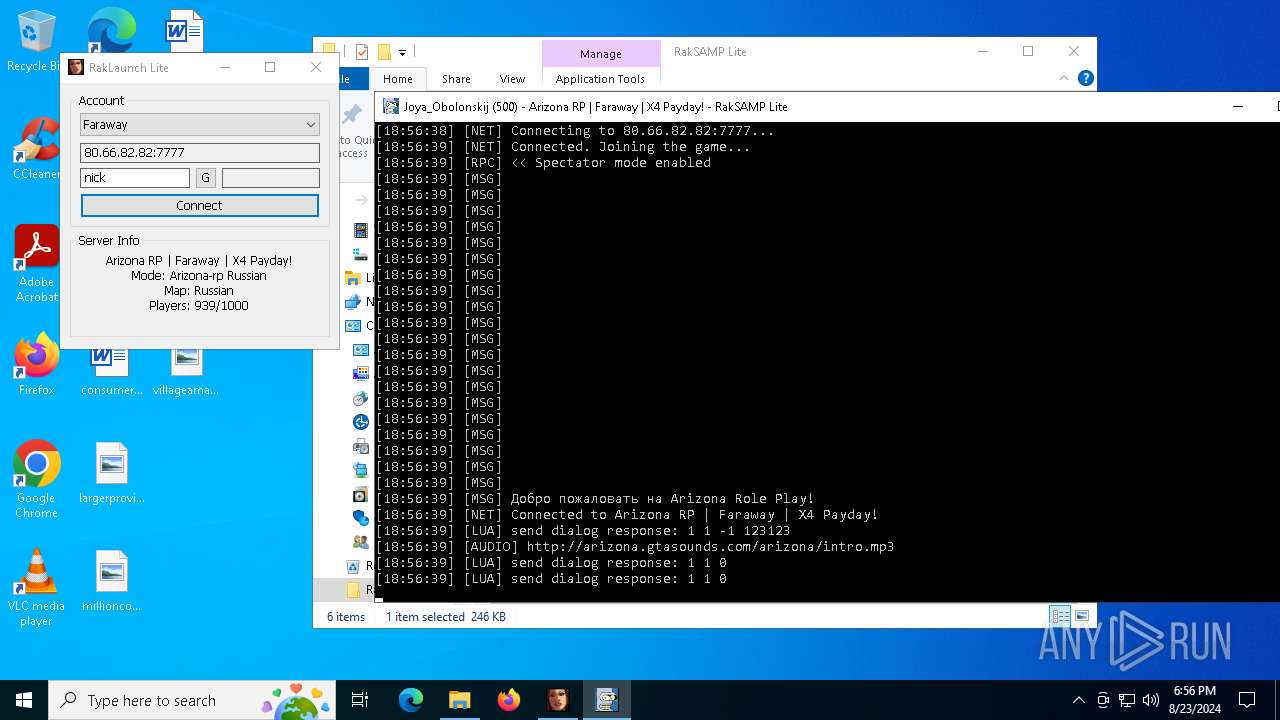
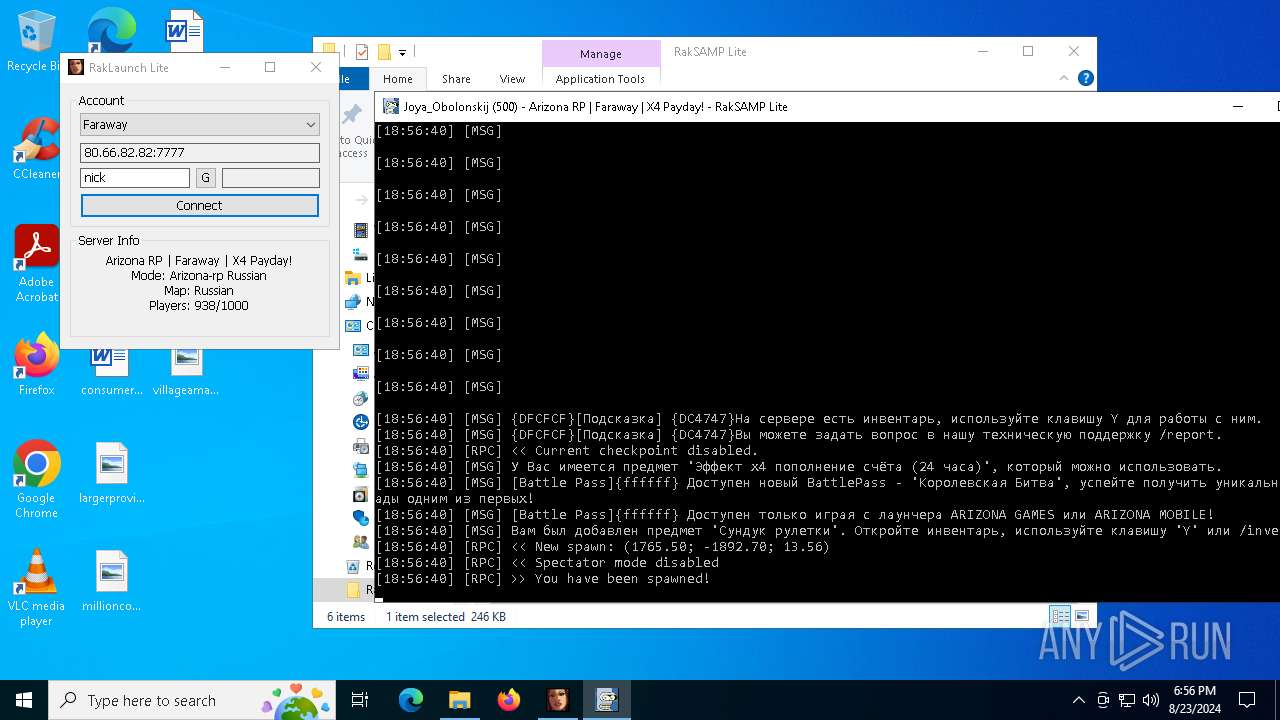
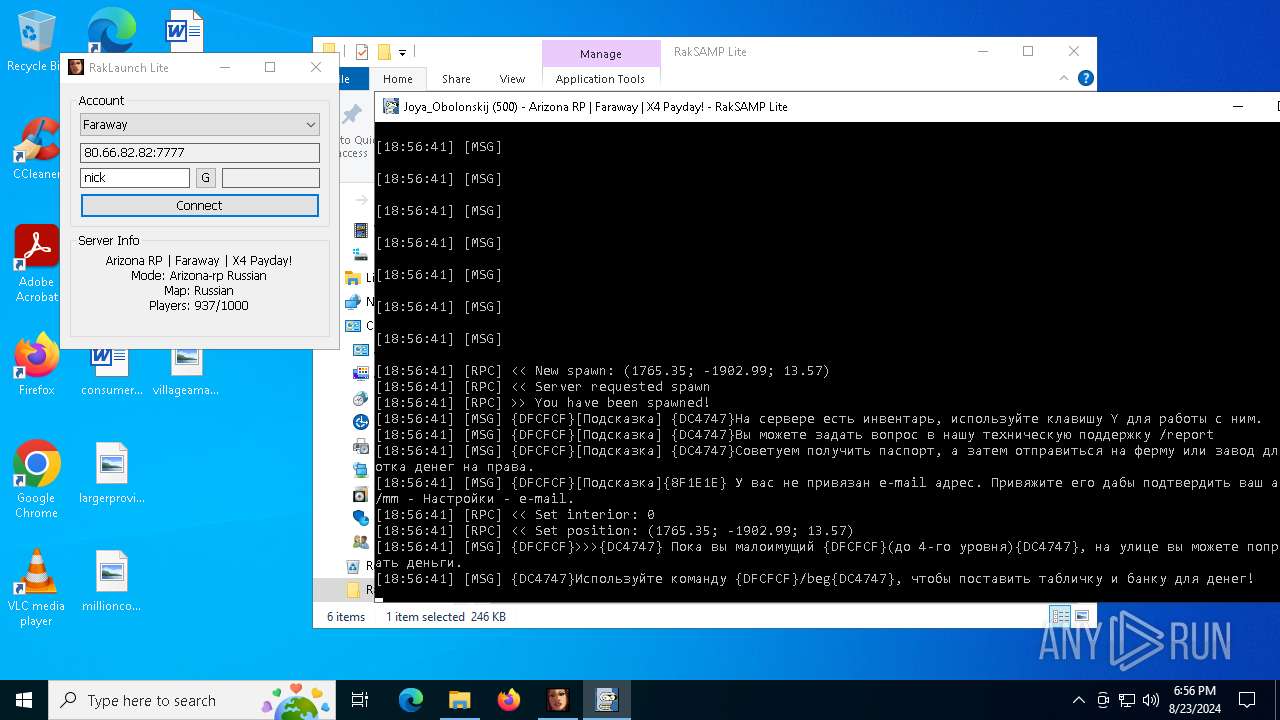
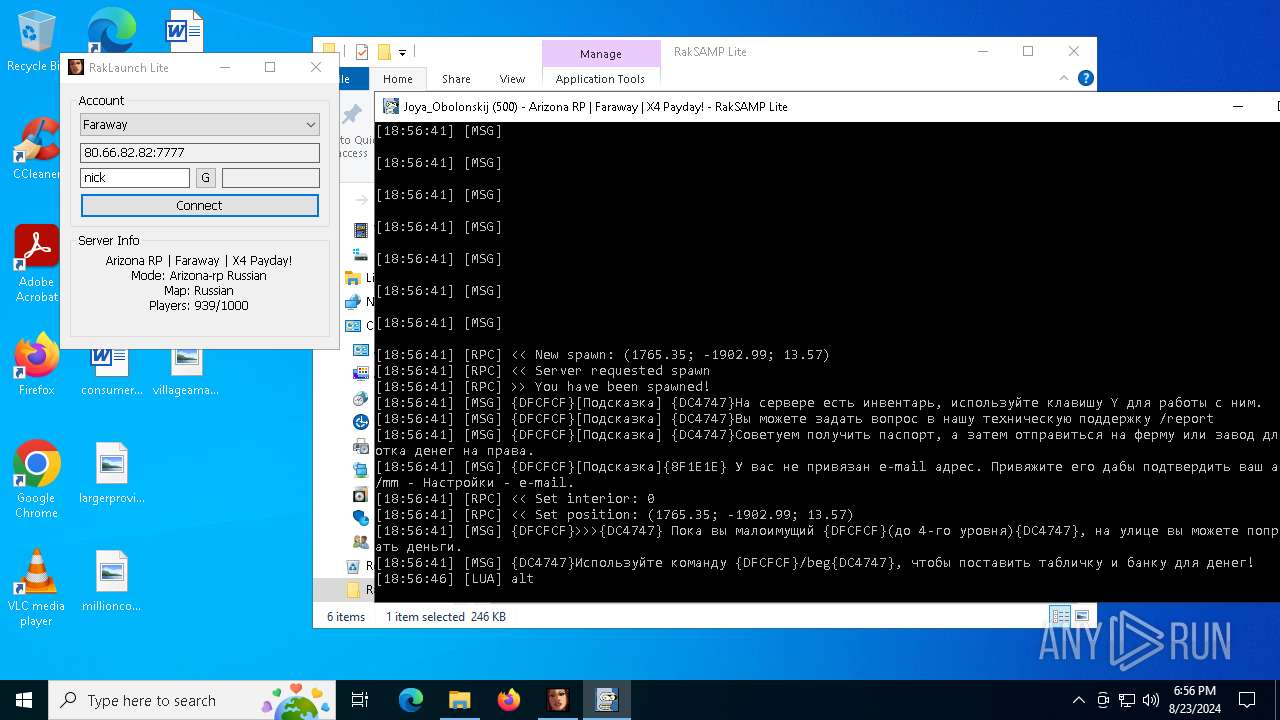
| 7068 | "C:\Users\admin\Desktop\RakSAMP Lite\RakSAMP Lite.exe" -h 80.66.82.82 -p 7777 -n nick -z | C:\Users\admin\Desktop\RakSAMP Lite\RakSAMP Lite.exe | RakLaunch Lite.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RakSAMP Lite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 800
Read events
6 773
Write events
27
Delete events
0
Modification events
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RakSAMP Lite.rar | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6660) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
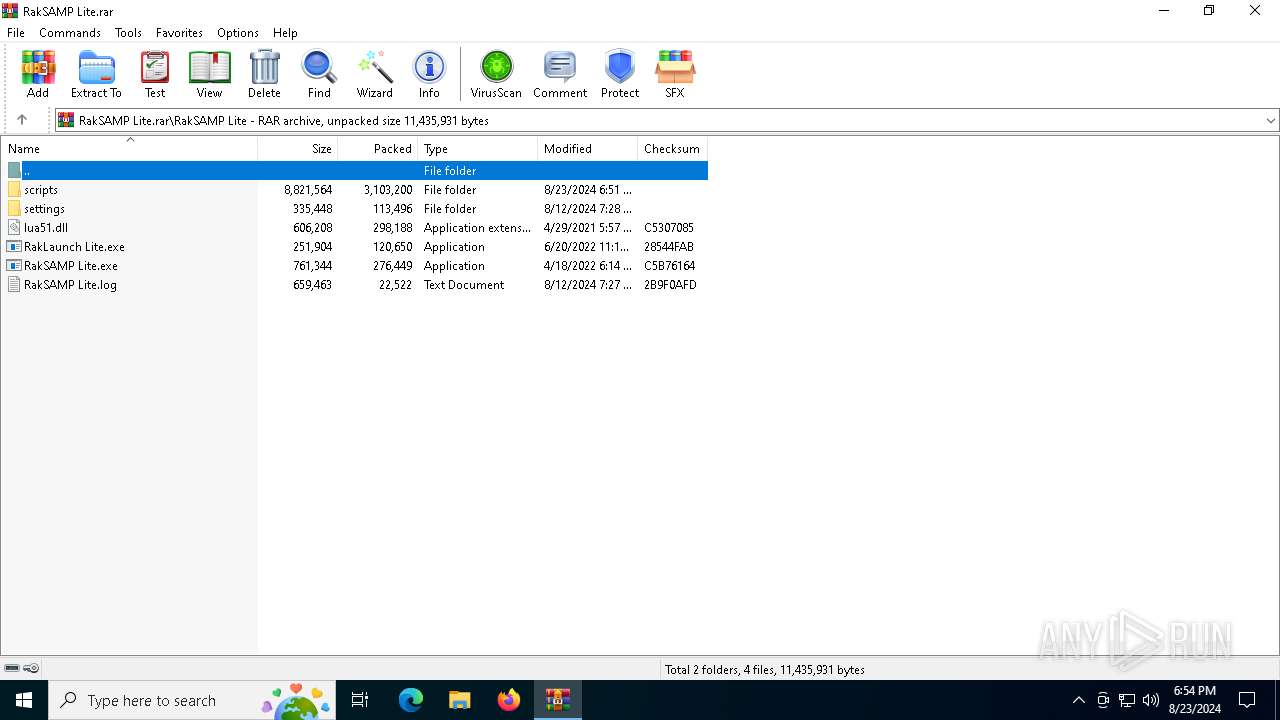
Executable files
17
Suspicious files
17
Text files
66
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6660.7253\RakSAMP Lite\lua51.dll | executable | |
MD5:3DFF7448B43FCFB4DC65E0040B0FFB88 | SHA256:FF976F6E965E3793E278FA9BF5E80B9B226A0B3932B9DA764BFFC8E41E6CDB60 | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6660.7253\RakSAMP Lite\scripts\libs\cjson.dll | executable | |
MD5:A8EEC61368EE2351305E60885C548B61 | SHA256:9FA1F6C66644A3E14A7D0E8D2937512963773FD047FA6826482CAA304ECF964C | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6660.7253\RakSAMP Lite\scripts\libs\config.ld | text | |
MD5:511280DD4B2302E2ABD75B491D842F63 | SHA256:8AF159F04A37A25112D6A6235C812233DAD1883DAC524F4744167E712BD9EF4F | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6660.7253\RakSAMP Lite\RakLaunch Lite.exe | executable | |
MD5:7D53985DBCDBED7E32F22934EC1F7B94 | SHA256:7AE2A1E9F328110BAE84CD82158041DE56DD5FCC0A8F5BB3E9378419A3BBEFCB | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6660.7253\RakSAMP Lite\scripts\aim_fix.lua | binary | |
MD5:DE2C0E4F9ACECD6BD2C1819B0874EC6C | SHA256:9C61CC4F3F87C92696989450230C5046DACCE96FB3CDA16B33F70BCC3B220362 | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6660.7253\RakSAMP Lite\scripts\libs\base64.dll | executable | |
MD5:A7B7CE324277FF19D9BA081C4DFDCB1D | SHA256:4E19BAC2A3E0A3E854143ED9259B82A4F405409B0D2928E10A27DB672BF346BE | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6660.7253\RakSAMP Lite\RakSAMP Lite.exe | executable | |
MD5:9802AC594BD6245E31C5E640A23F1652 | SHA256:0C1AEEAB9ADCF23318A04837CCB1D4EA1210DA2943AC1AF4A9D94A450F733D87 | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6660.7253\RakSAMP Lite\scripts\libs\autobus.lua | text | |
MD5:EB9032303580667E2D4ACD66F32FE313 | SHA256:D7EB520D3D500C3C6EC2BC4606F11A95B3341C92276BAFC8558CACFD3B3FFE6C | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6660.7253\RakSAMP Lite\scripts\libs\cjson\cjson\util.lua | text | |
MD5:D9187071B6C2CAE70AC95CFF4170BF36 | SHA256:0F9C82E5BA2779ECF5C4016E944213524549E8EA0C91FD7F00B2C6BB0441EE4A | |||
| 6660 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6660.7253\RakSAMP Lite\scripts\libs\copas\limit.lua | binary | |
MD5:0FC68F97B07313F95CF6DED6D685575D | SHA256:AE7229C8F1B9744B4D83B644492AC549CE7727FB163530E4B2A1FF5BBBB41179 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
36
DNS requests
15
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5400 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6828 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5400 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6344 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
608 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
400 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
608 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5400 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5400 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7068 | RakSAMP Lite.exe | Potential Corporate Privacy Violation | ET P2P Edonkey Publicize File ACK |
7068 | RakSAMP Lite.exe | Potential Corporate Privacy Violation | ET P2P Edonkey Publicize File ACK |
7068 | RakSAMP Lite.exe | Potential Corporate Privacy Violation | ET P2P Edonkey Publicize File ACK |
7068 | RakSAMP Lite.exe | Potential Corporate Privacy Violation | ET P2P Edonkey Publicize File ACK |