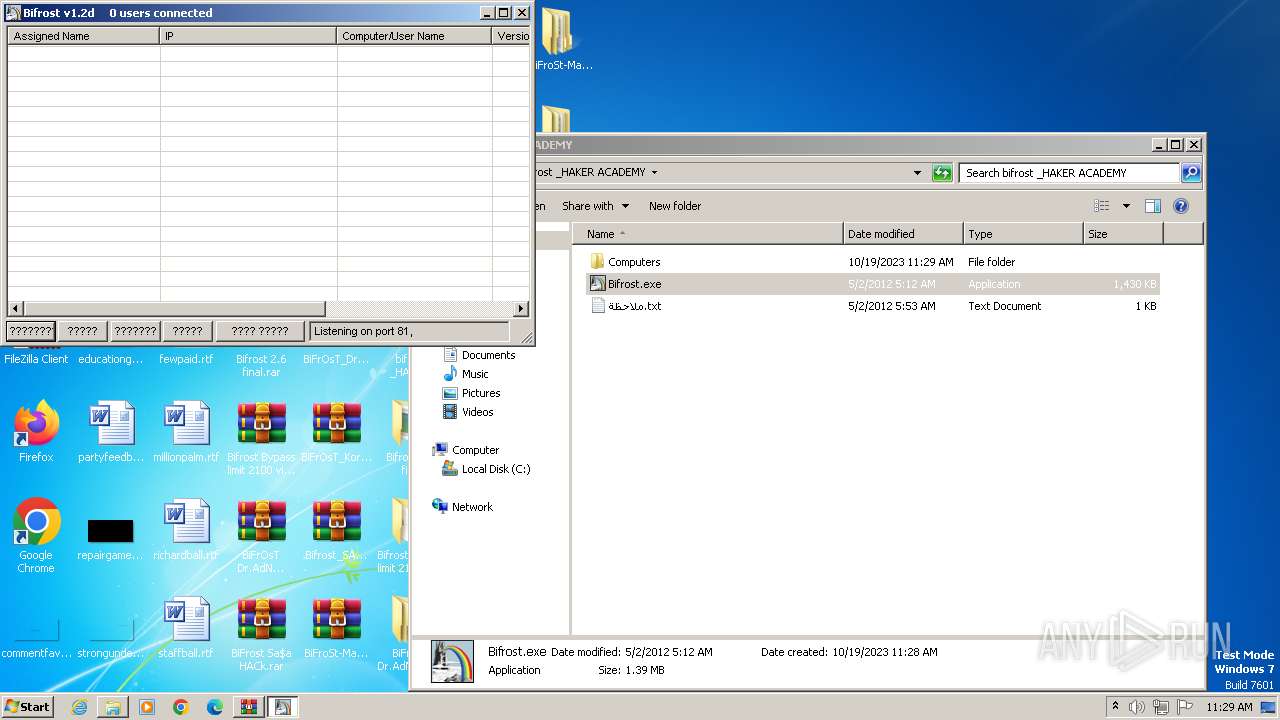
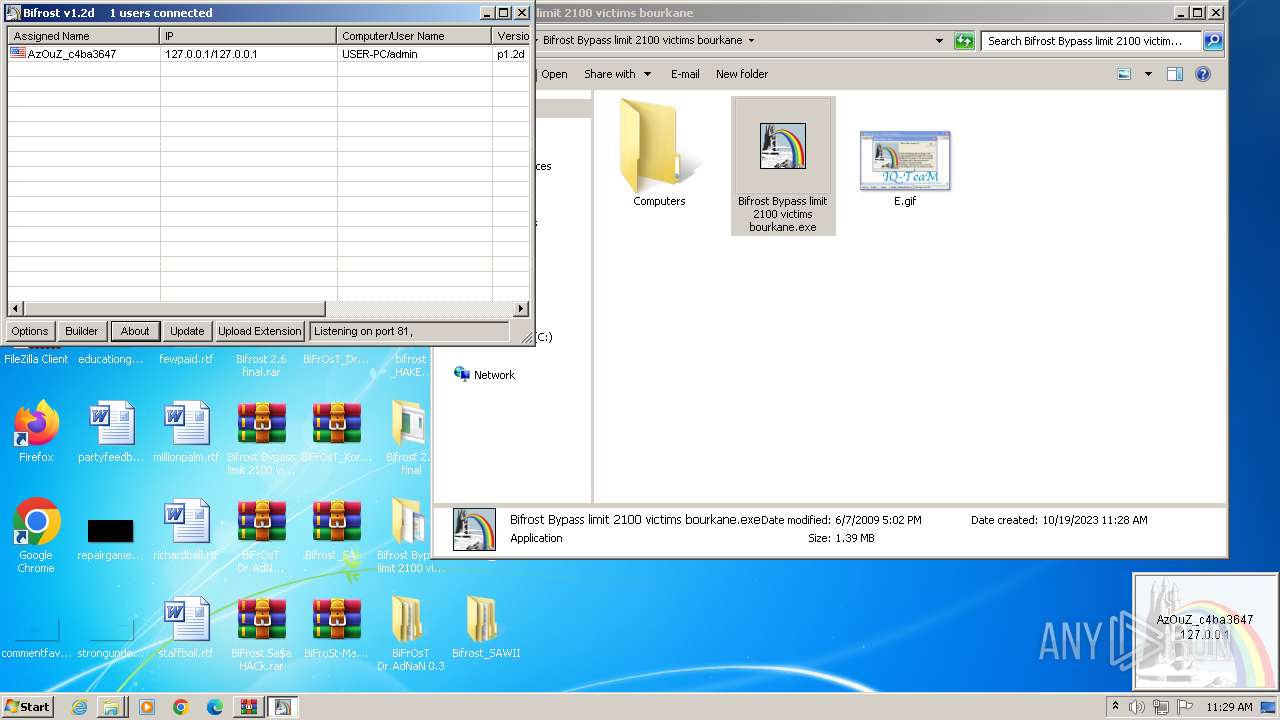
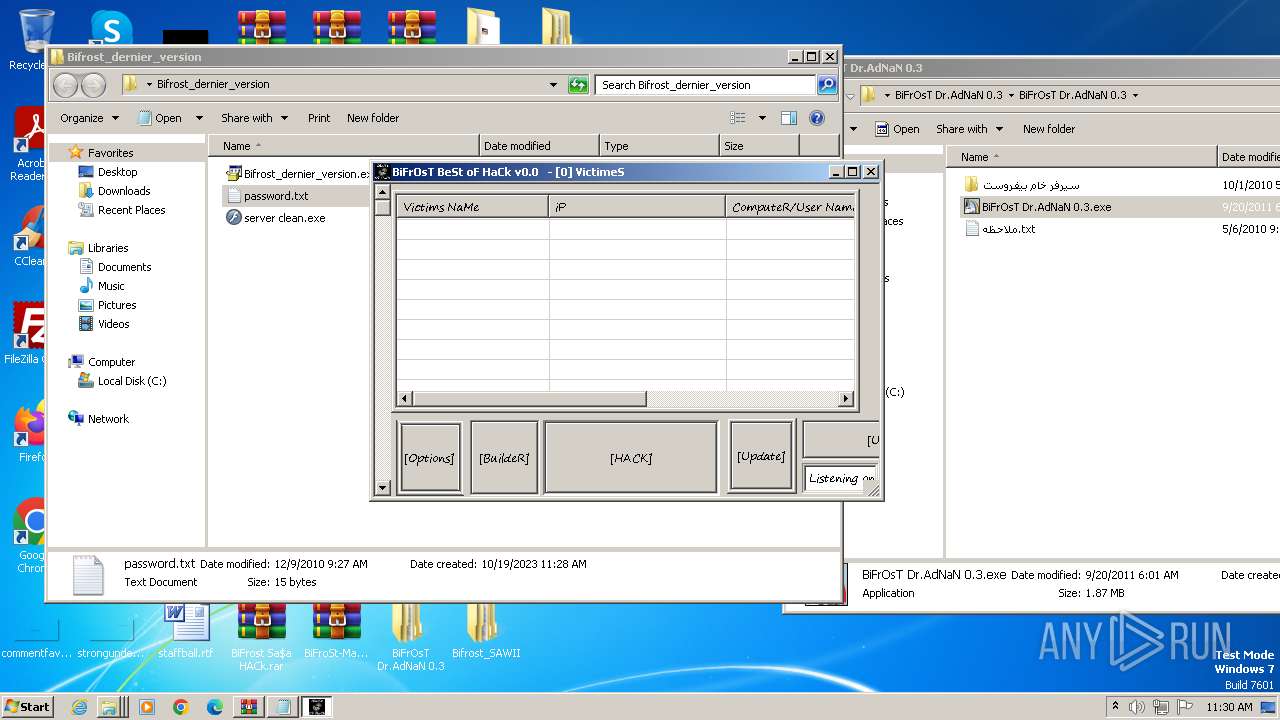
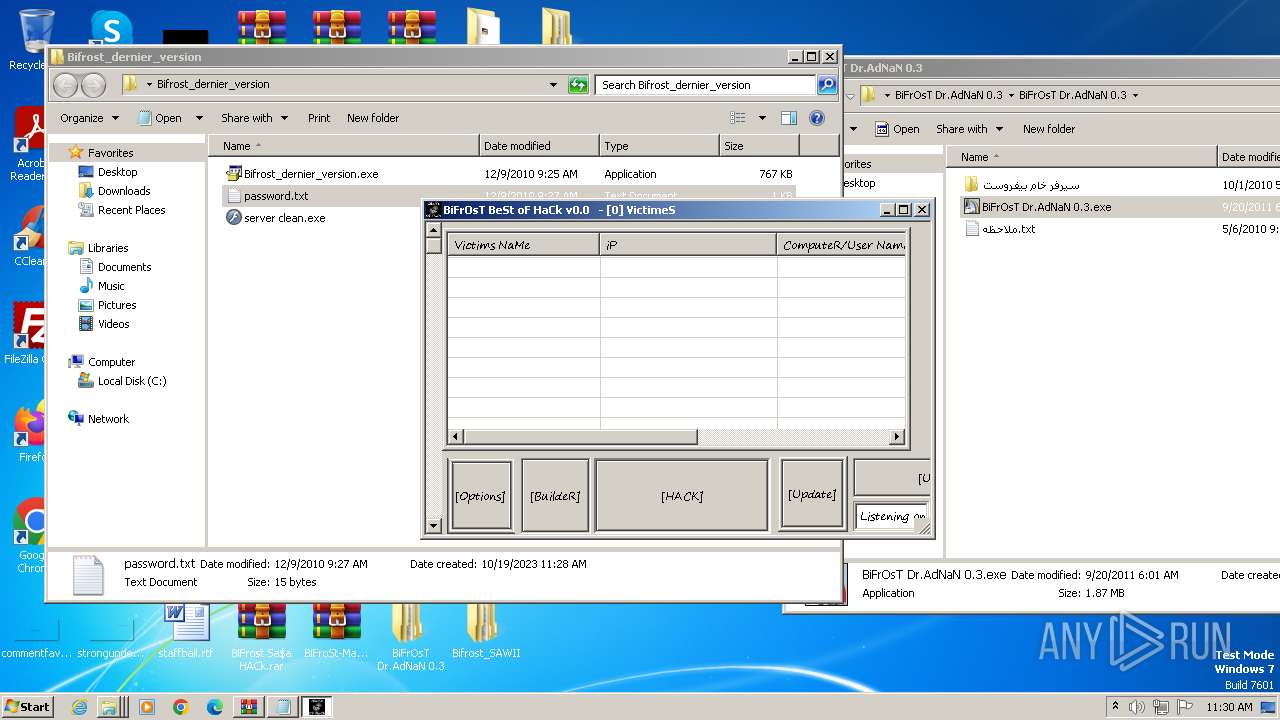
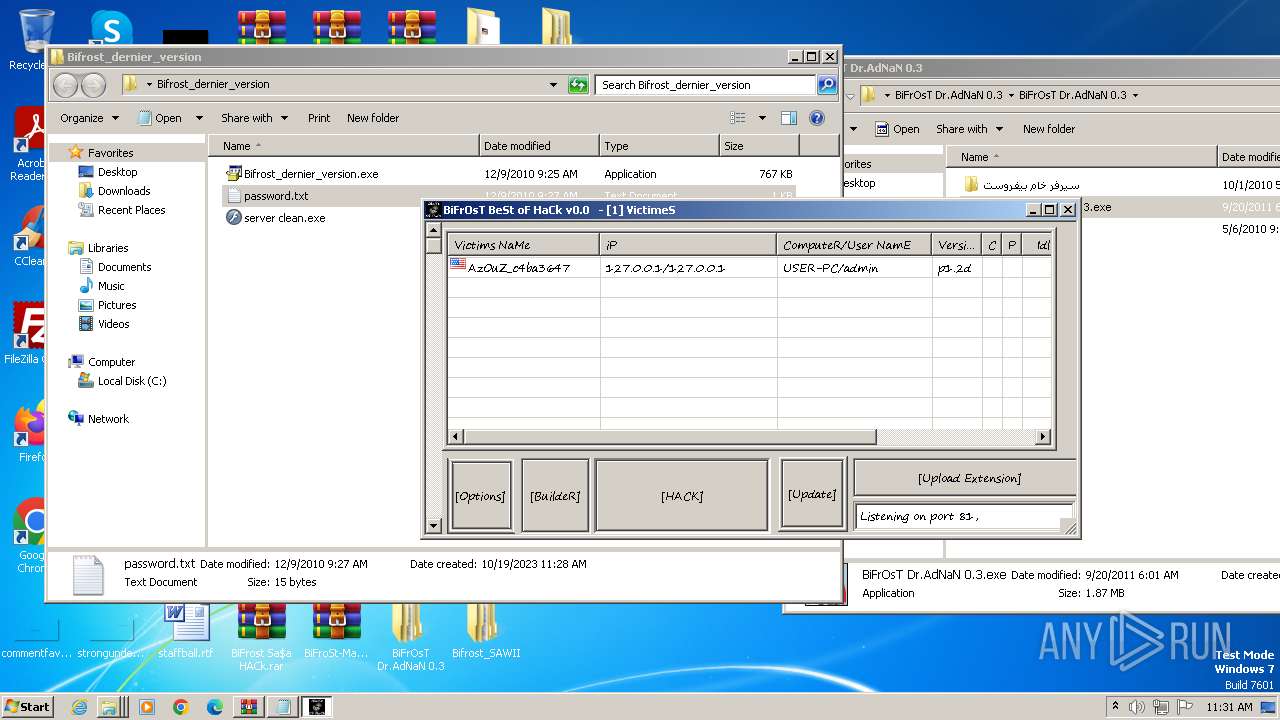
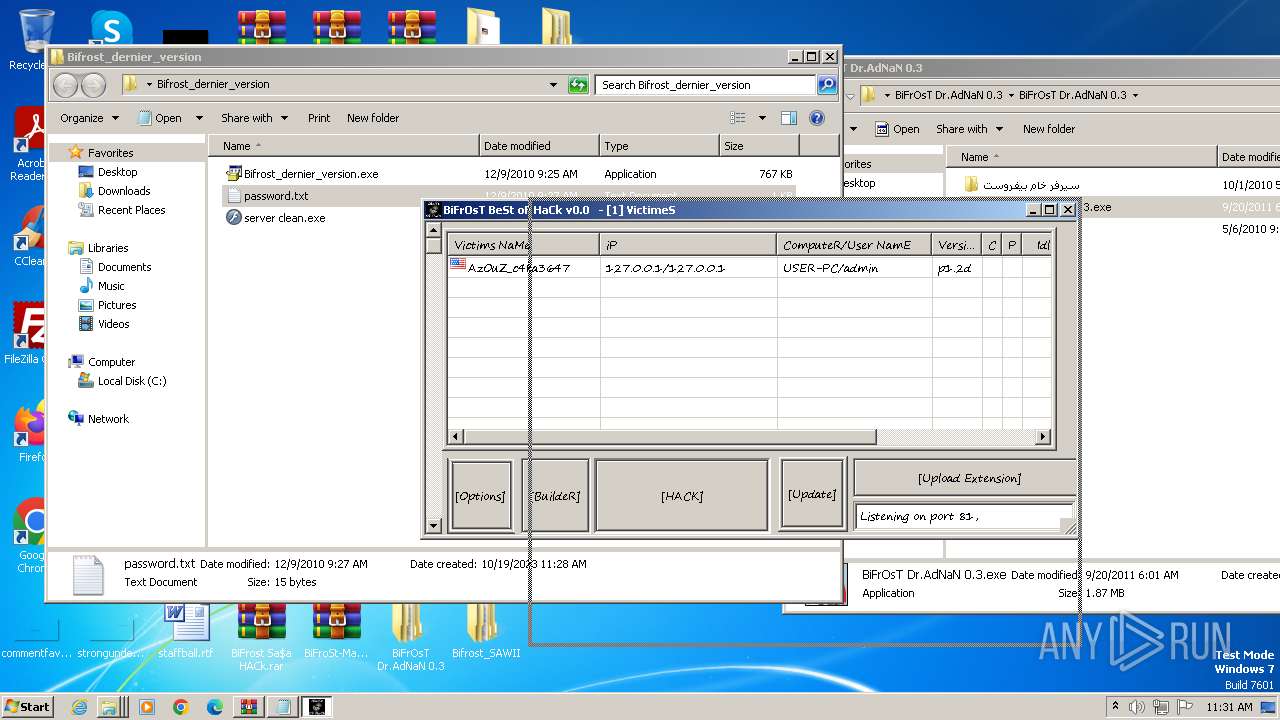
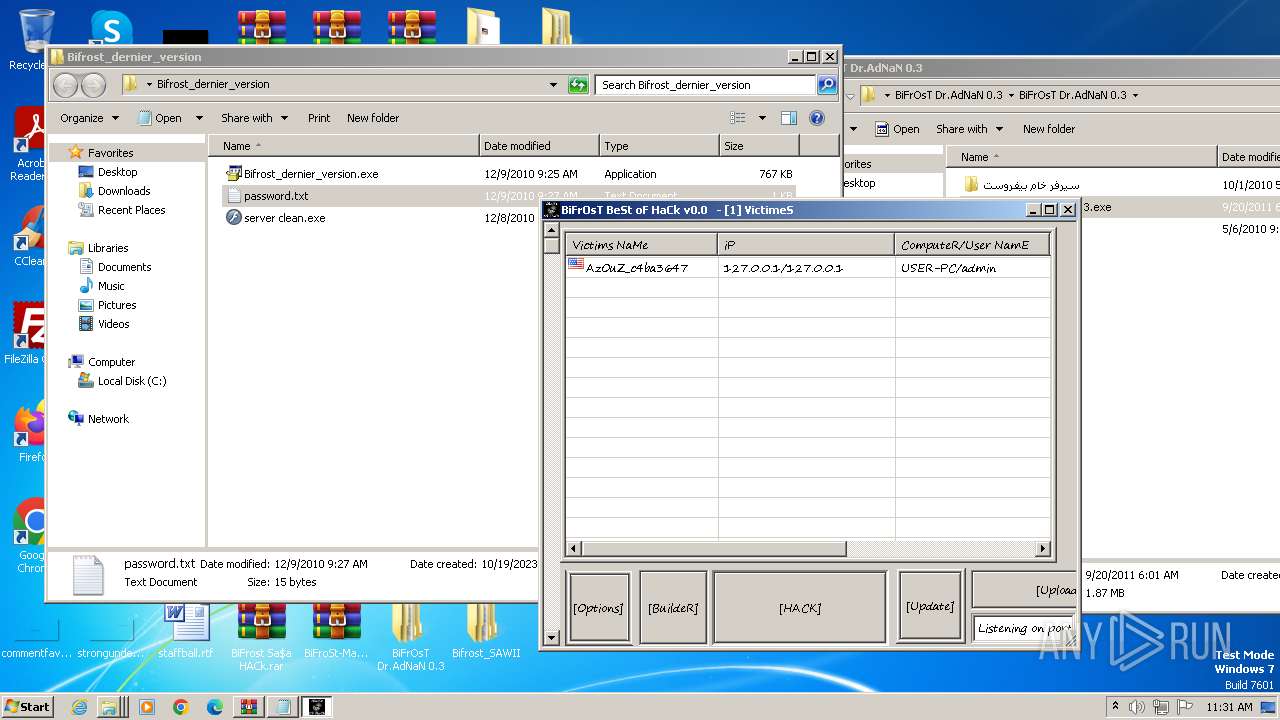
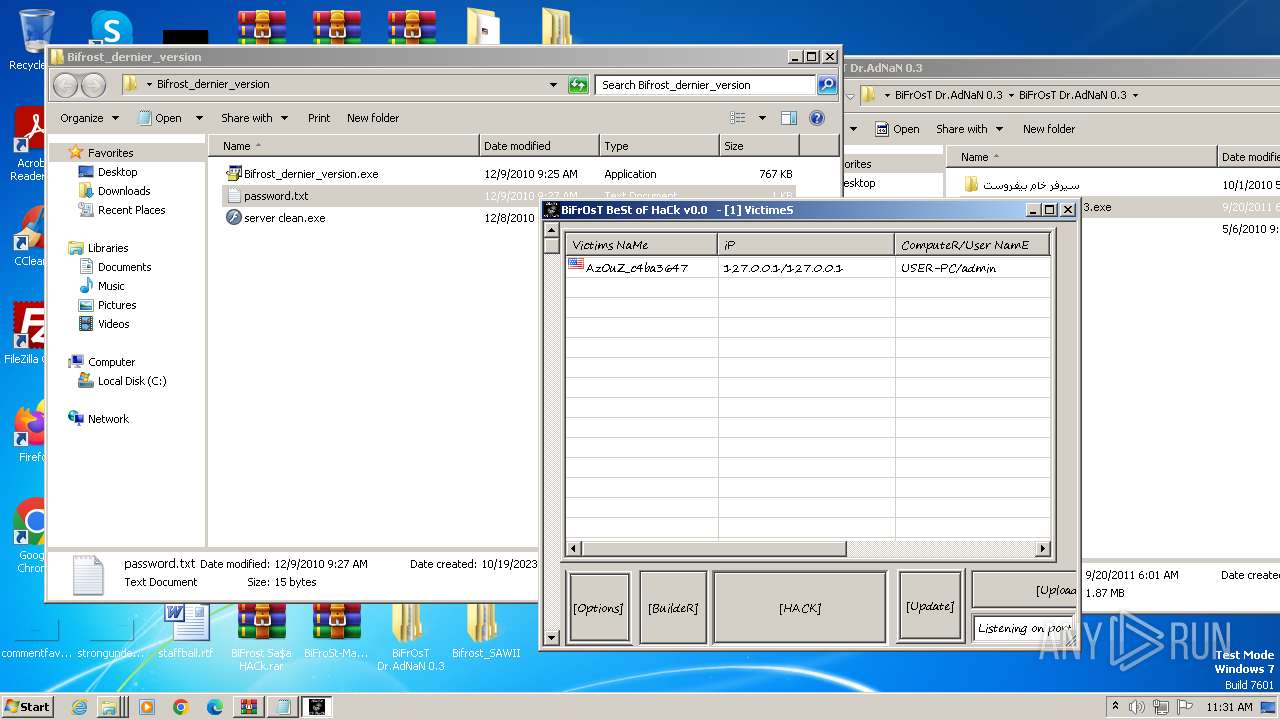
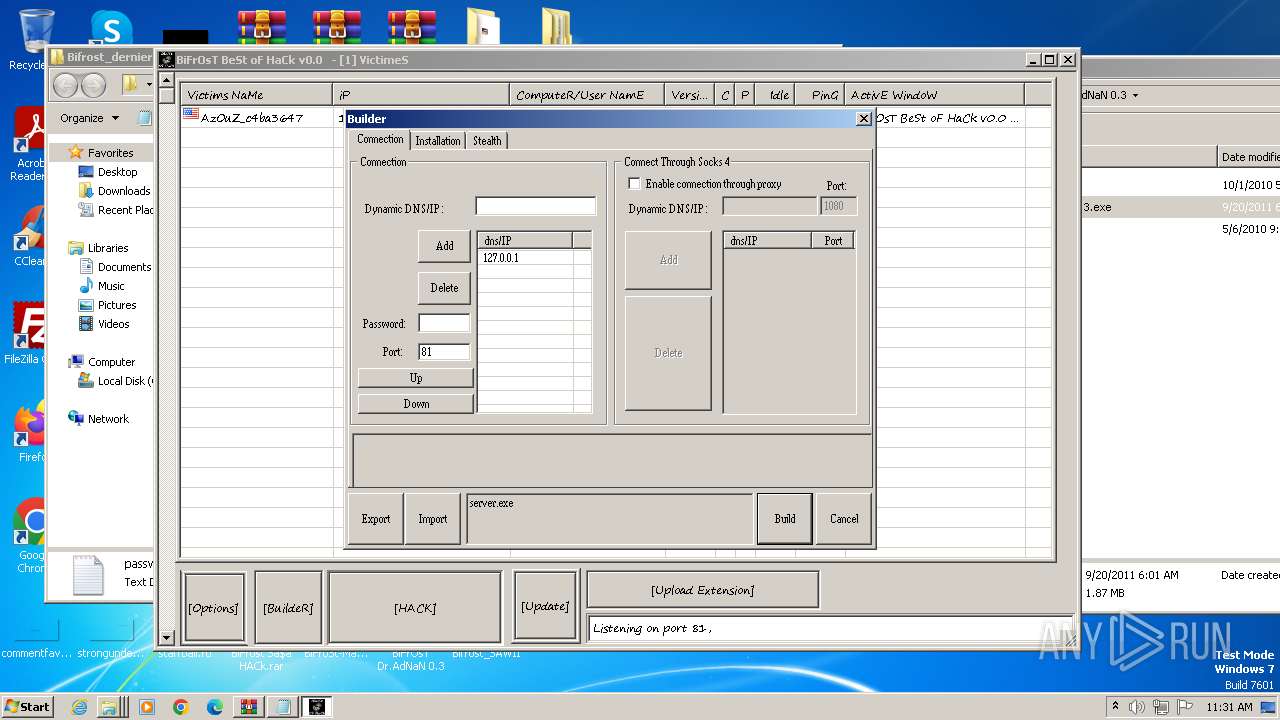
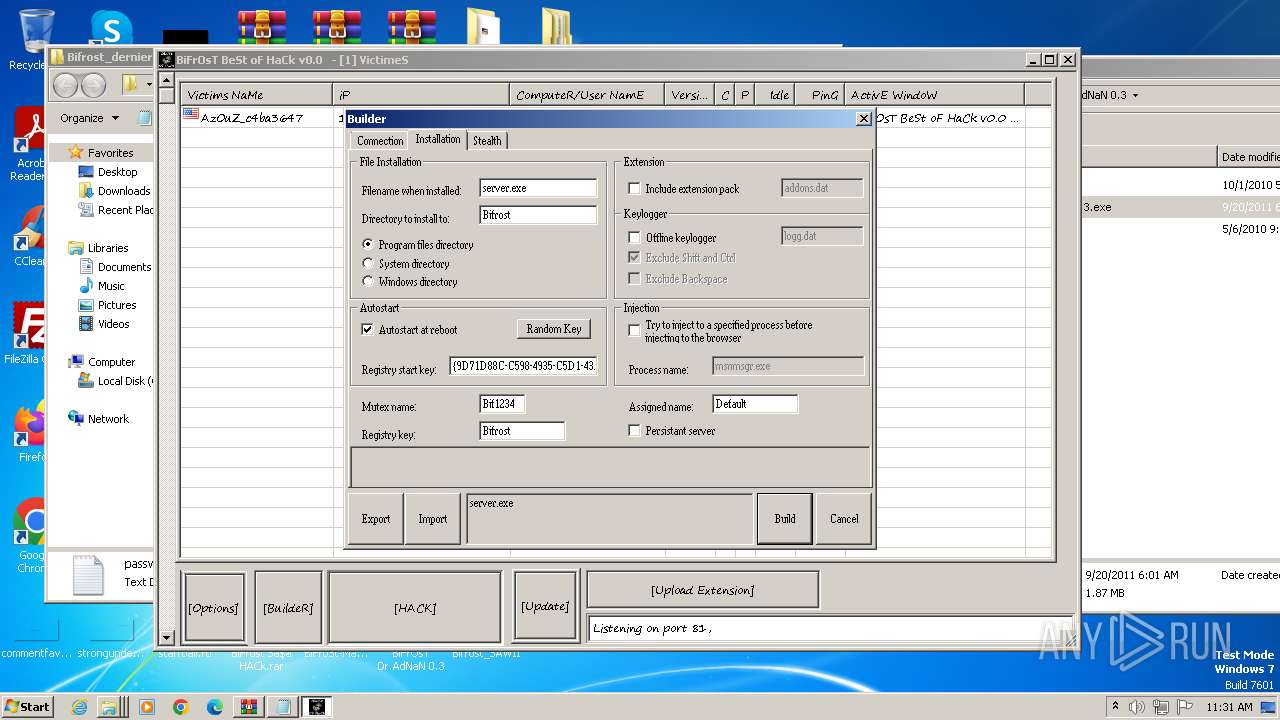
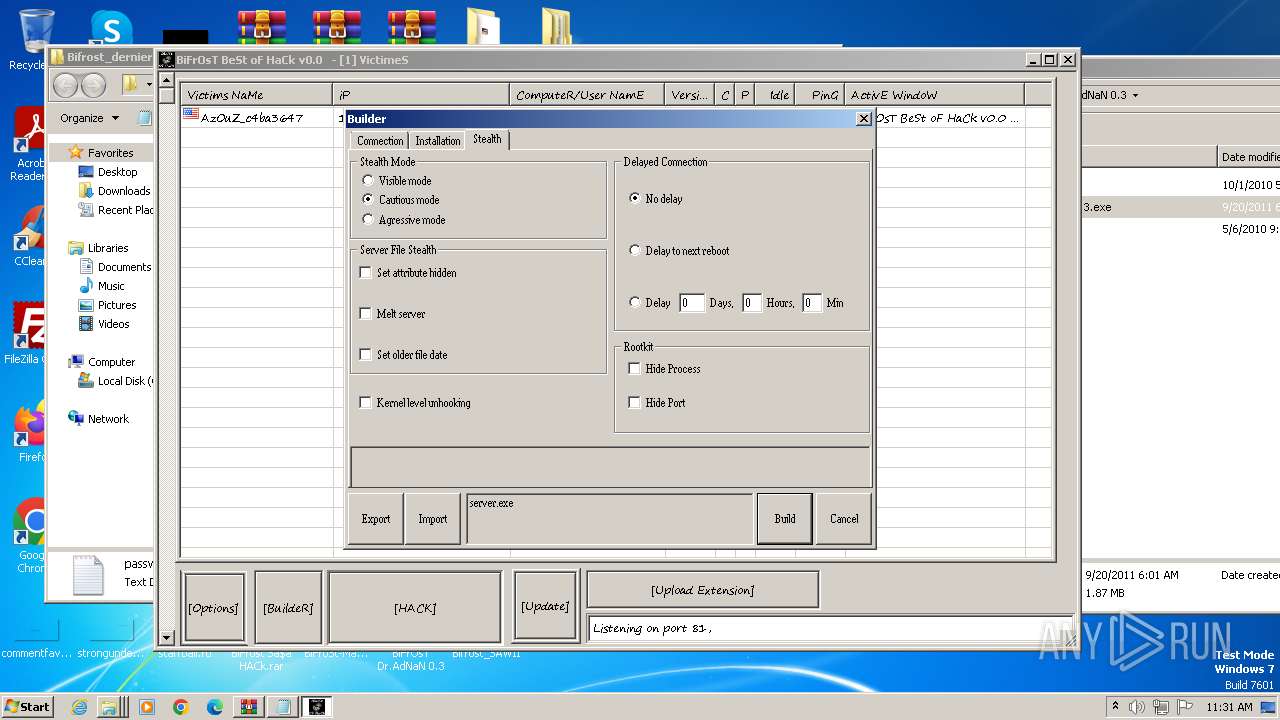
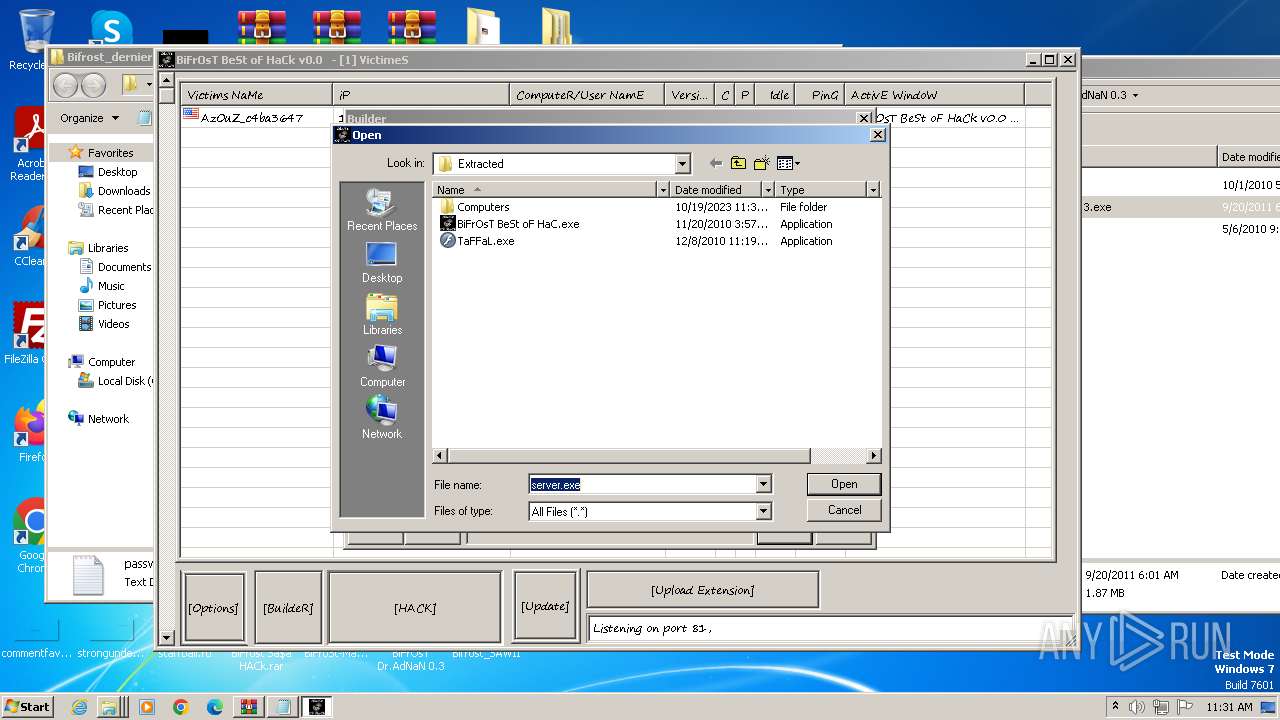
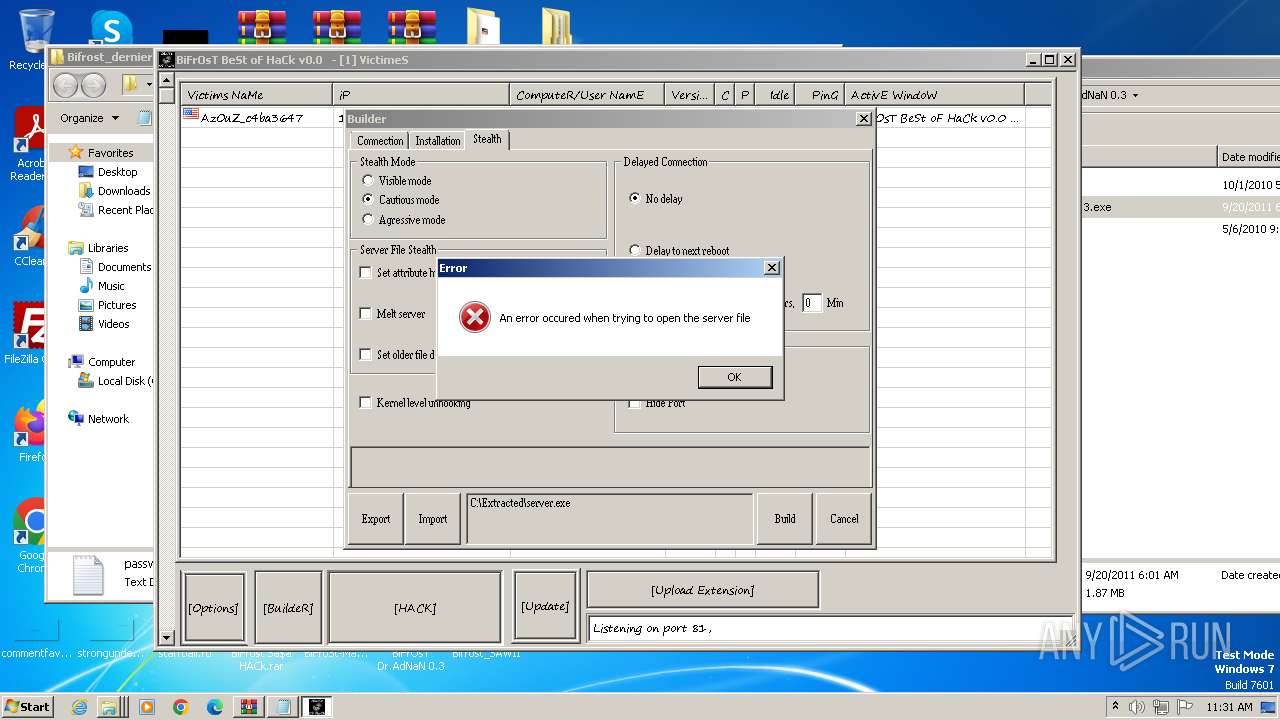
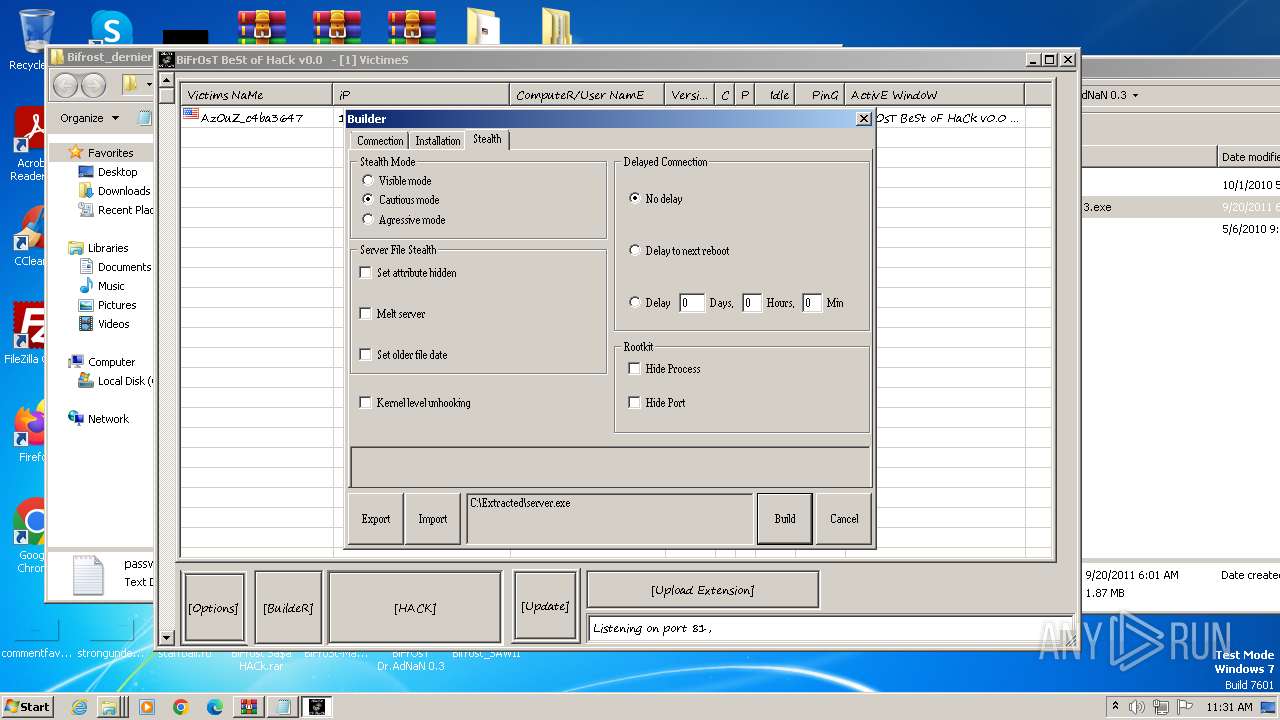
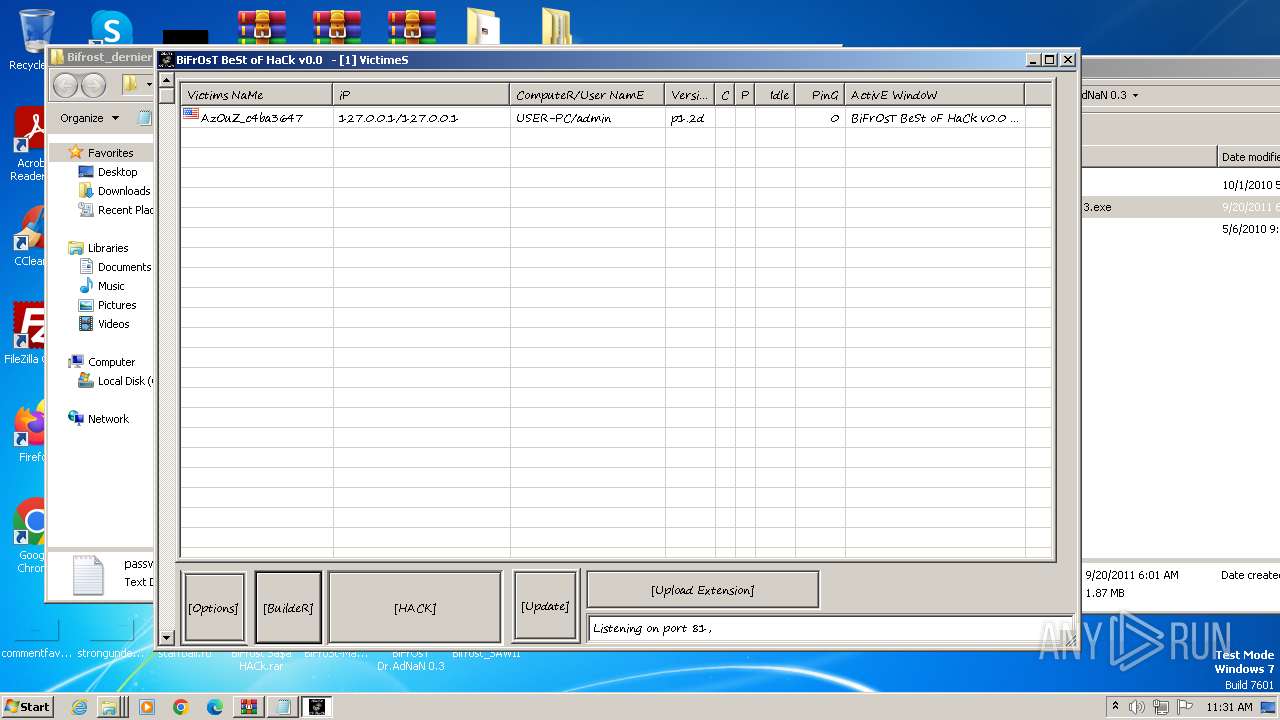
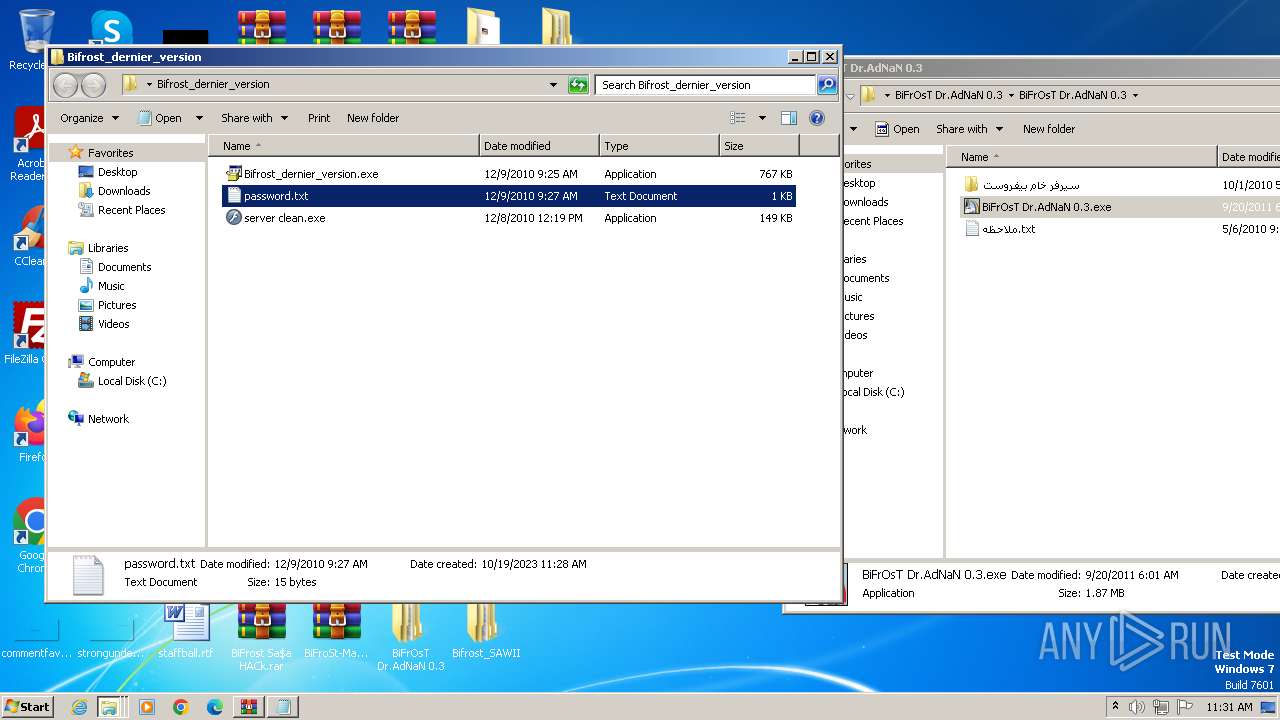
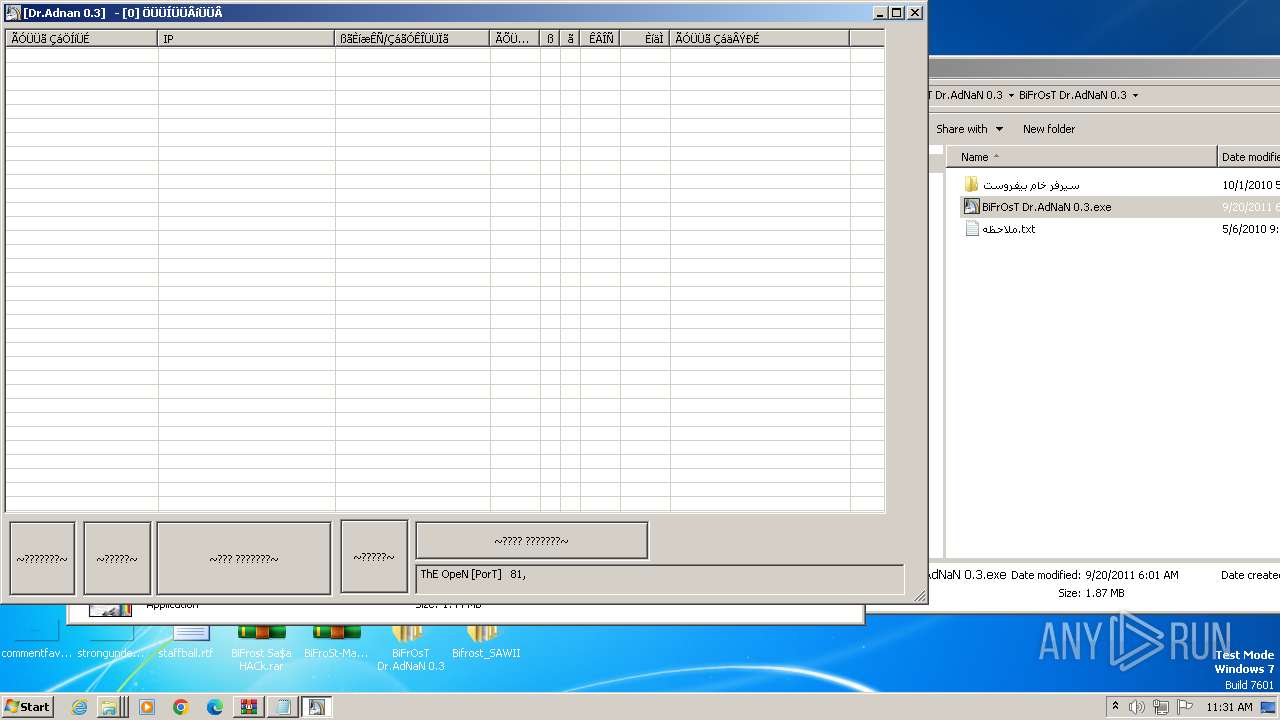
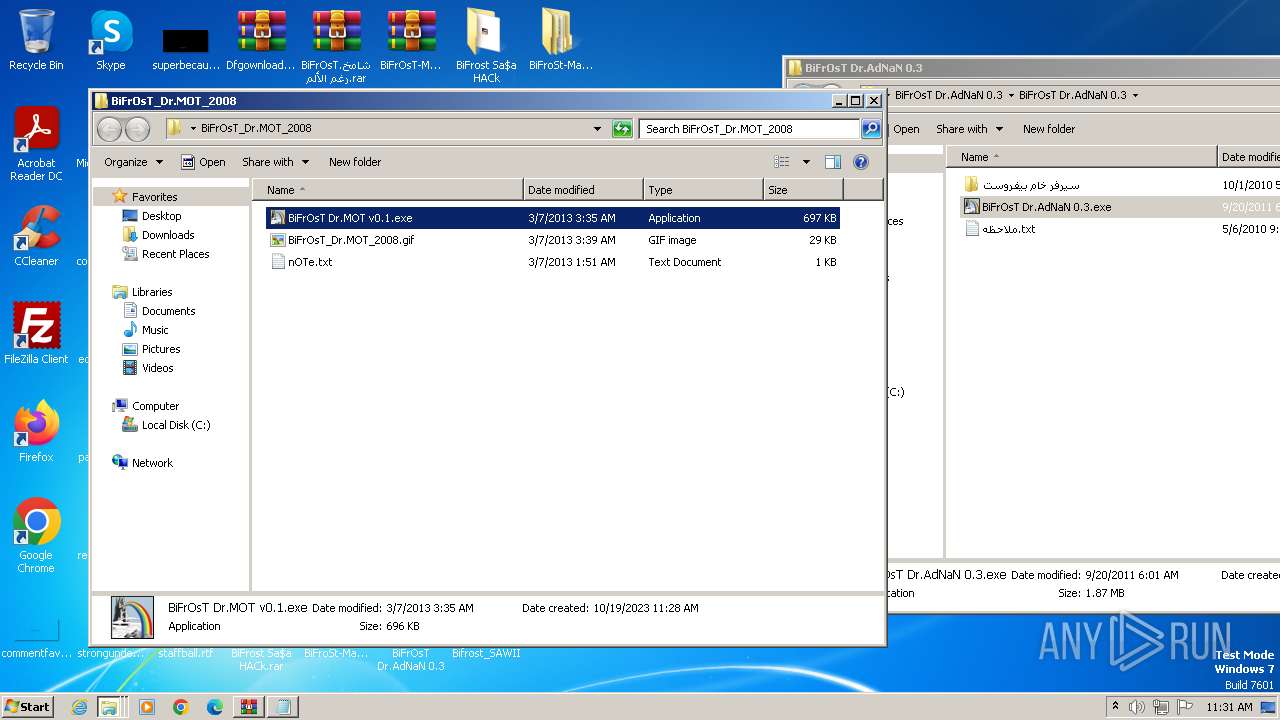
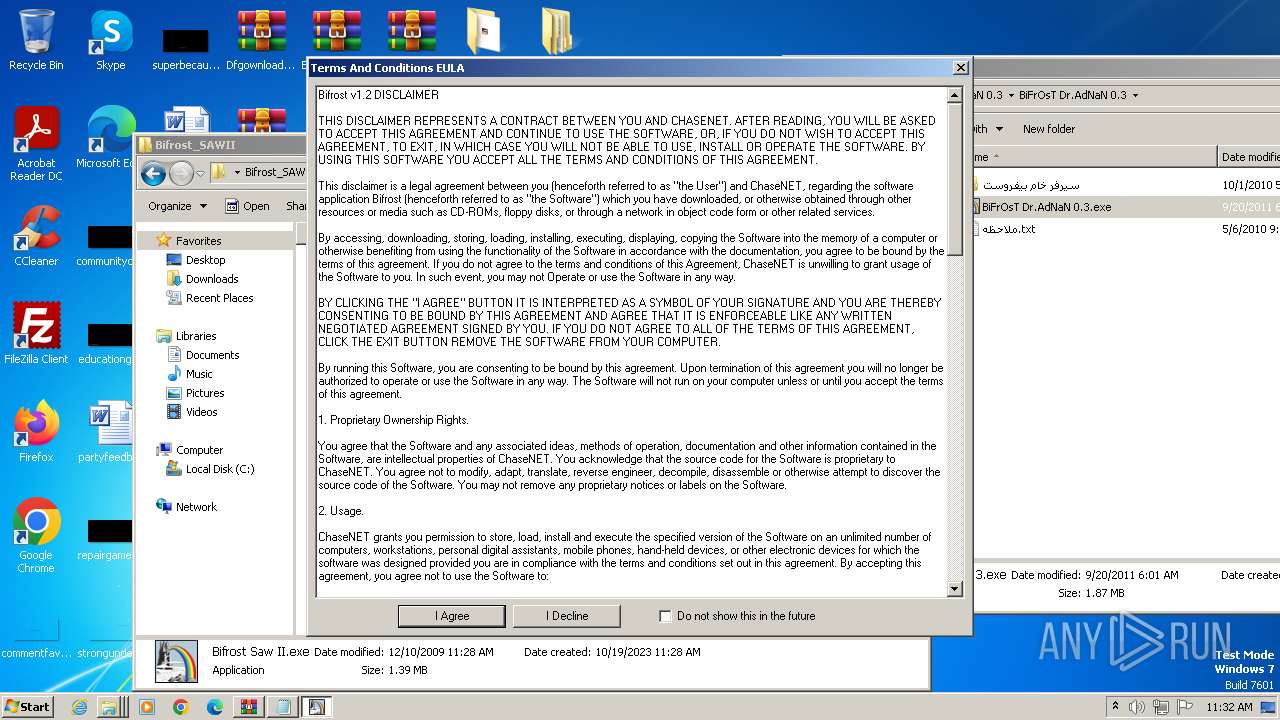
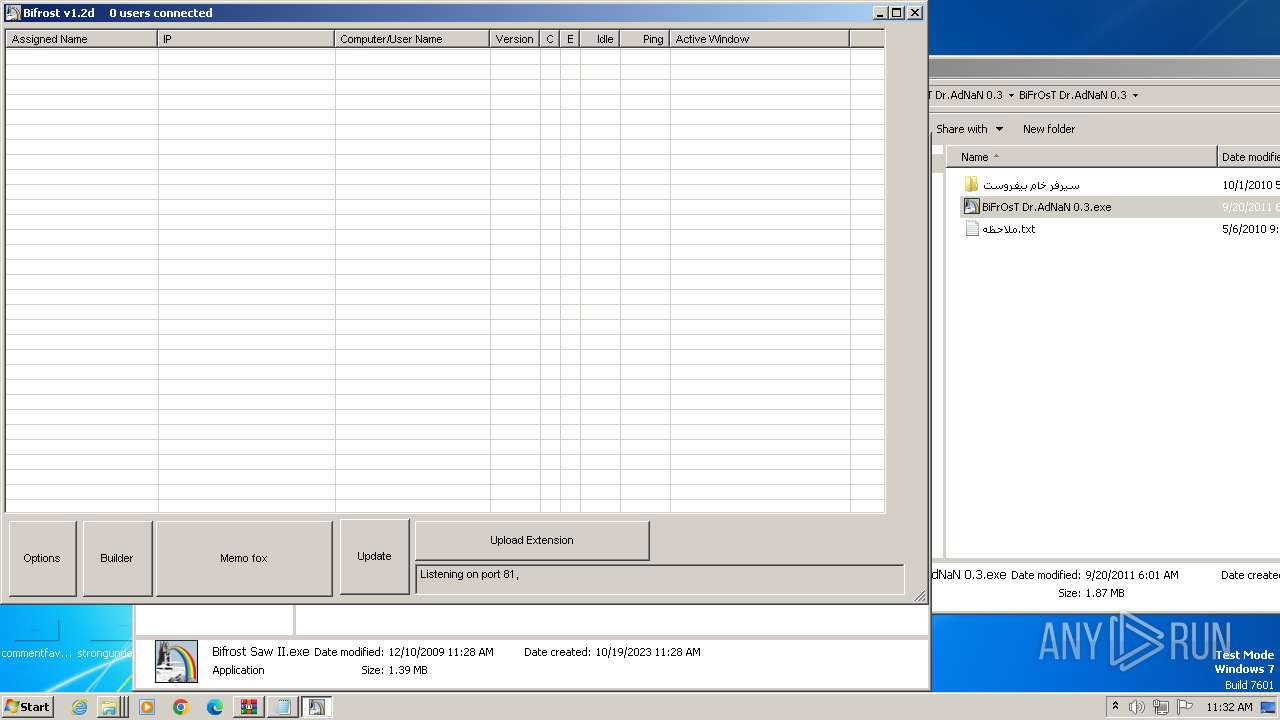
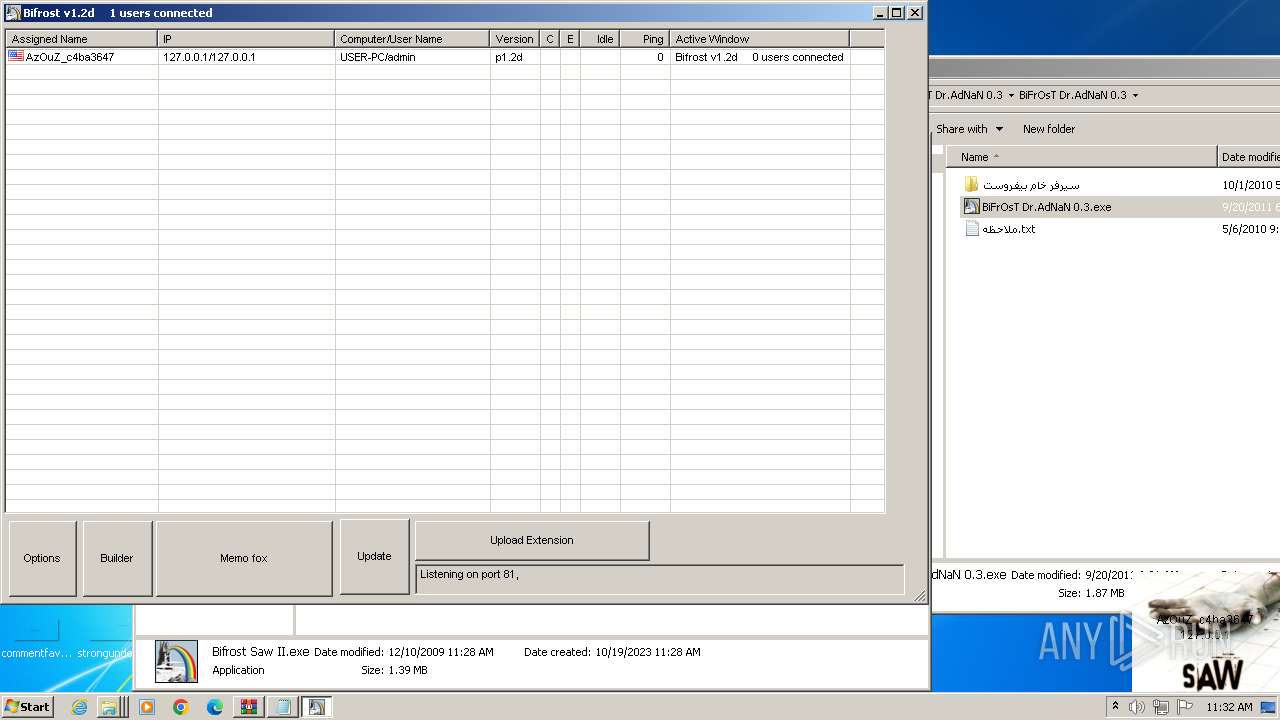
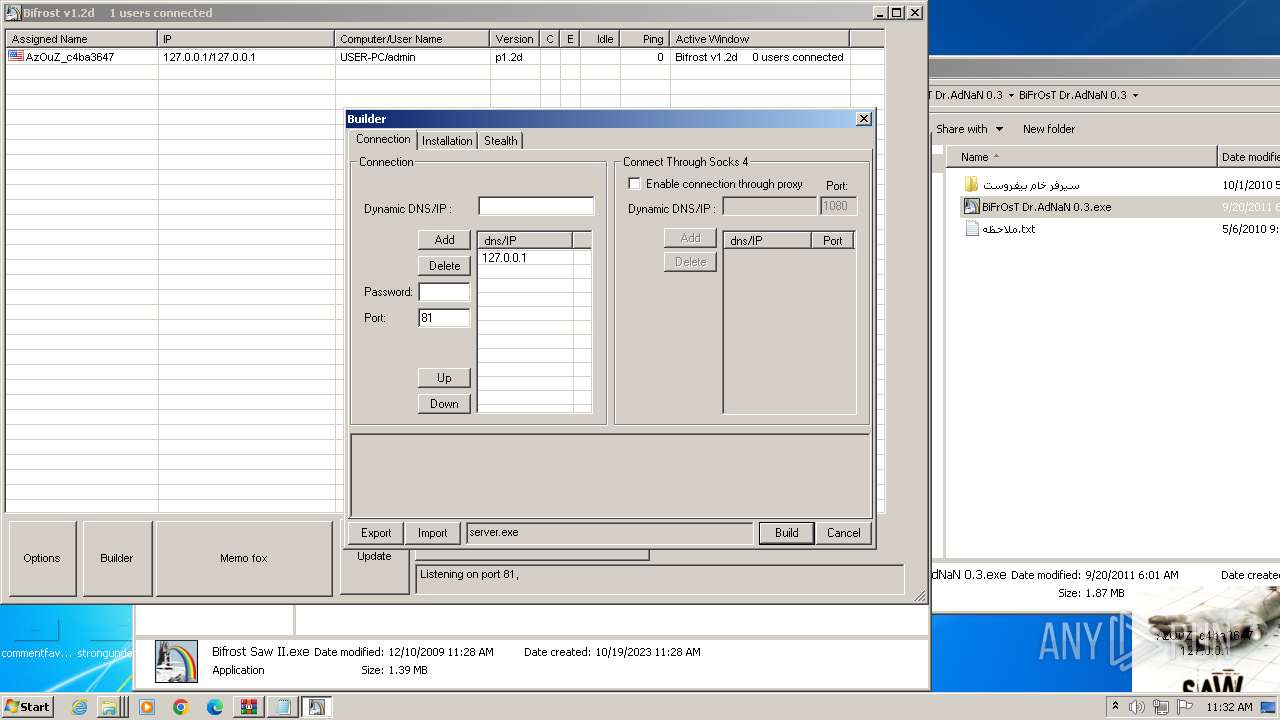
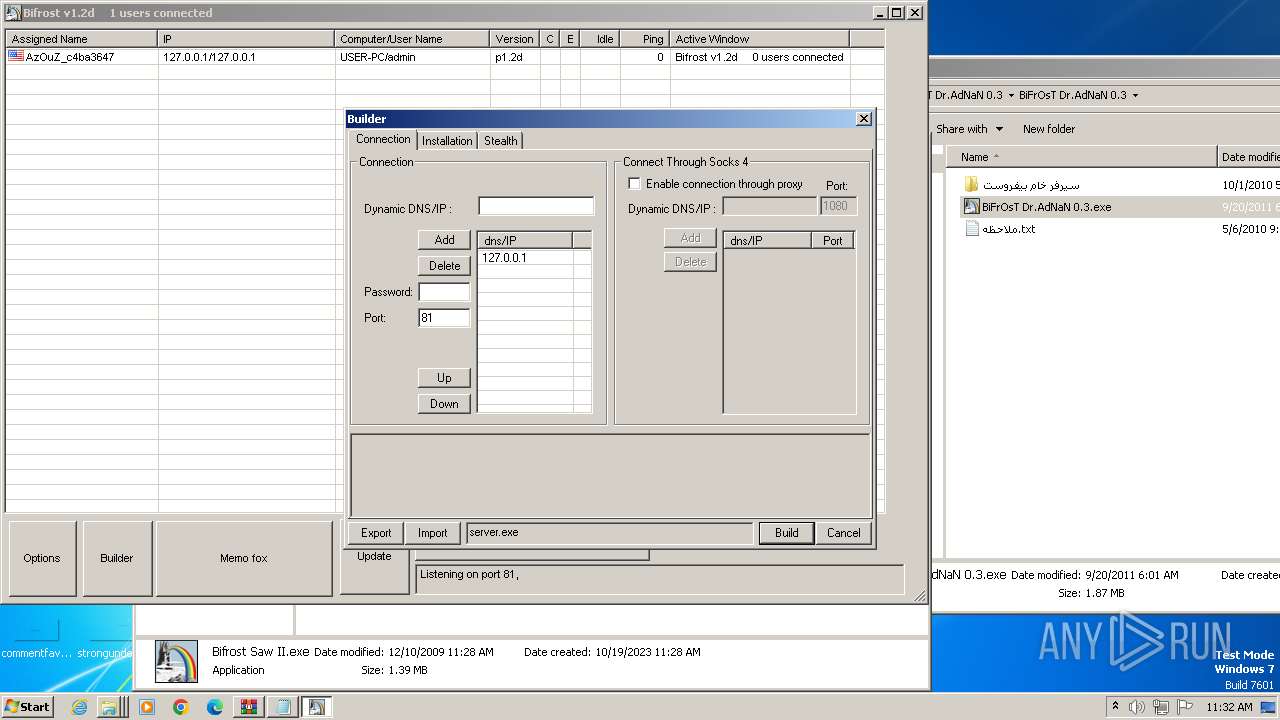
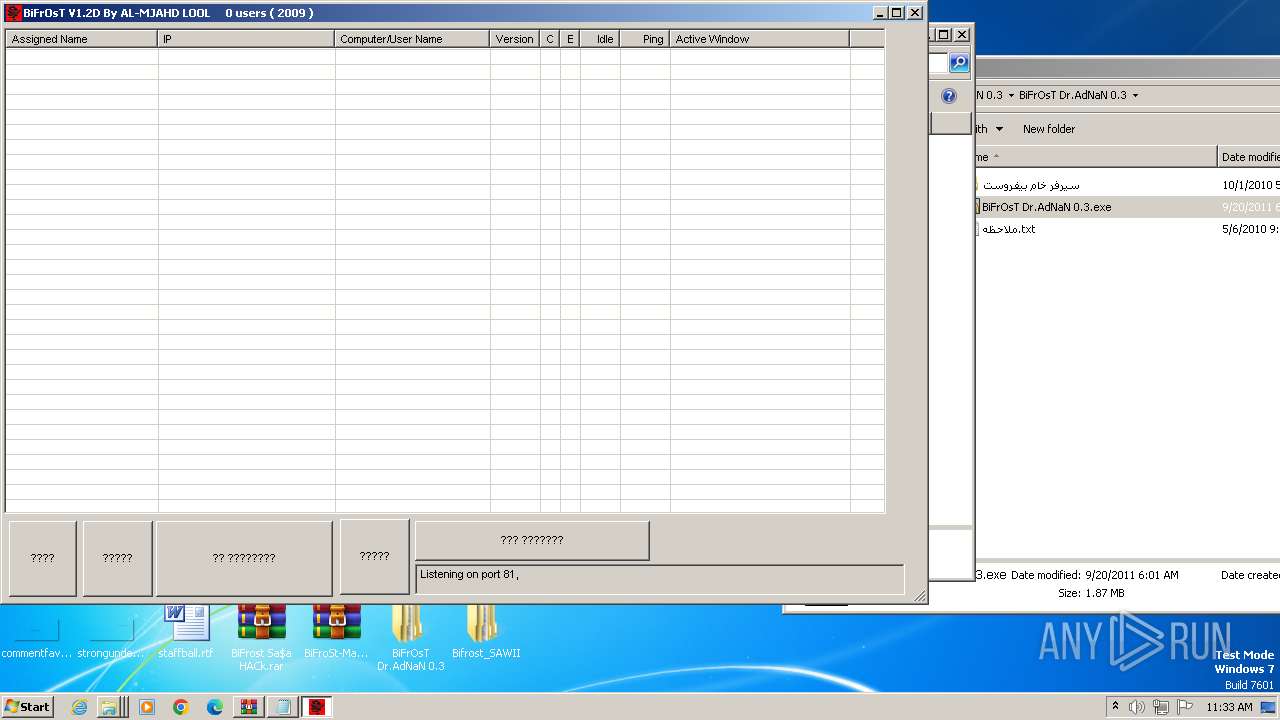
| File name: | Dfgownloads.rar |
| Full analysis: | https://app.any.run/tasks/1e0acd0c-2acd-41c5-9ddb-03c113ed6465 |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2023, 10:28:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | BB4C399E02EE90EFE868AFAC1A7D4E9B |
| SHA1: | 44B4D1C297EA627AFD566DE84EFF1A9DAAD234EF |
| SHA256: | 7B821449D8A58E32F8607626BC8A7F2DE8F727C76231A42C5F3DE56B771AE620 |
| SSDEEP: | 393216:CalJ6jv61hz03ePtUq01E8dFFZOtVx+G8DOgeyOtcrvJUXmOkp8E:PJ6e1qq09dZOtffBgctAnOU8E |
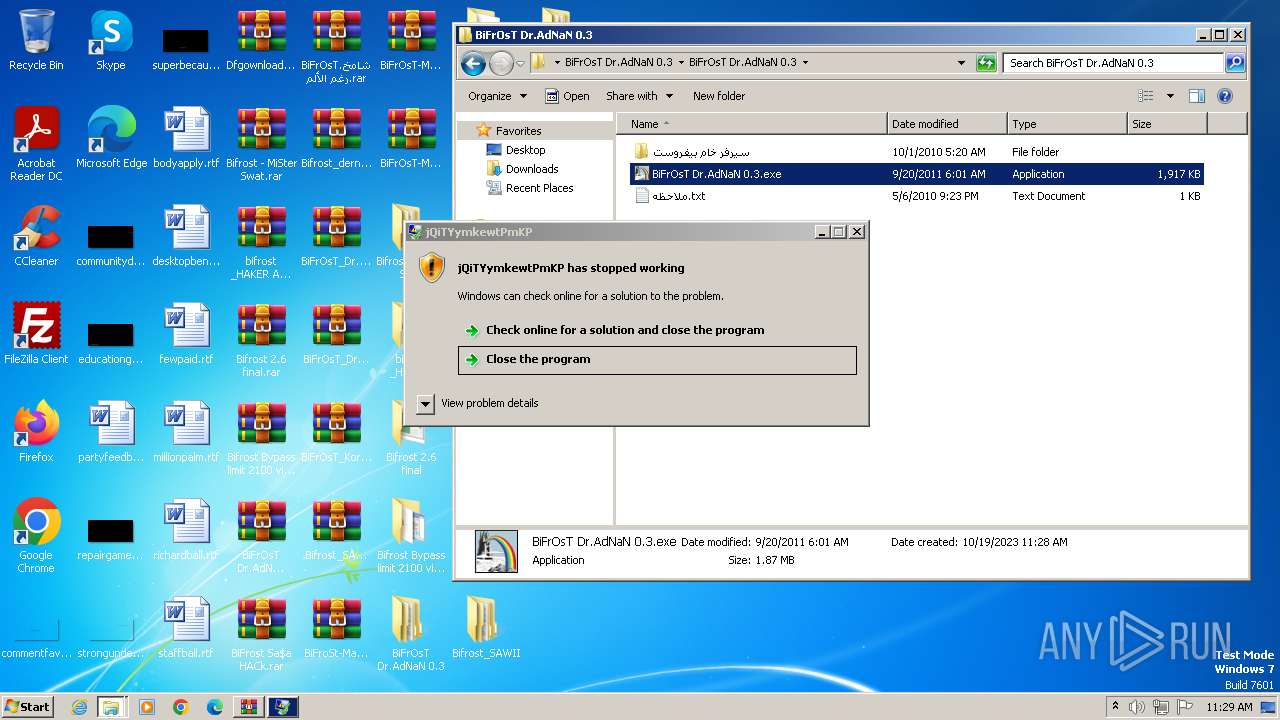
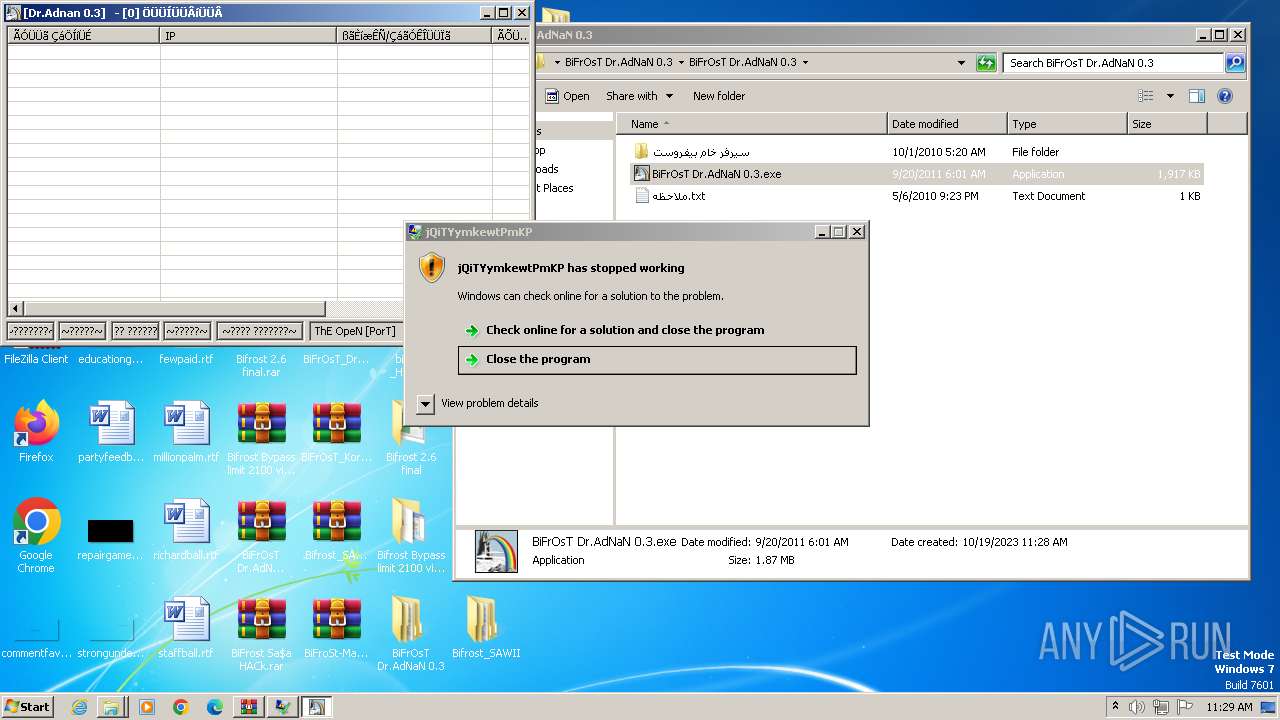
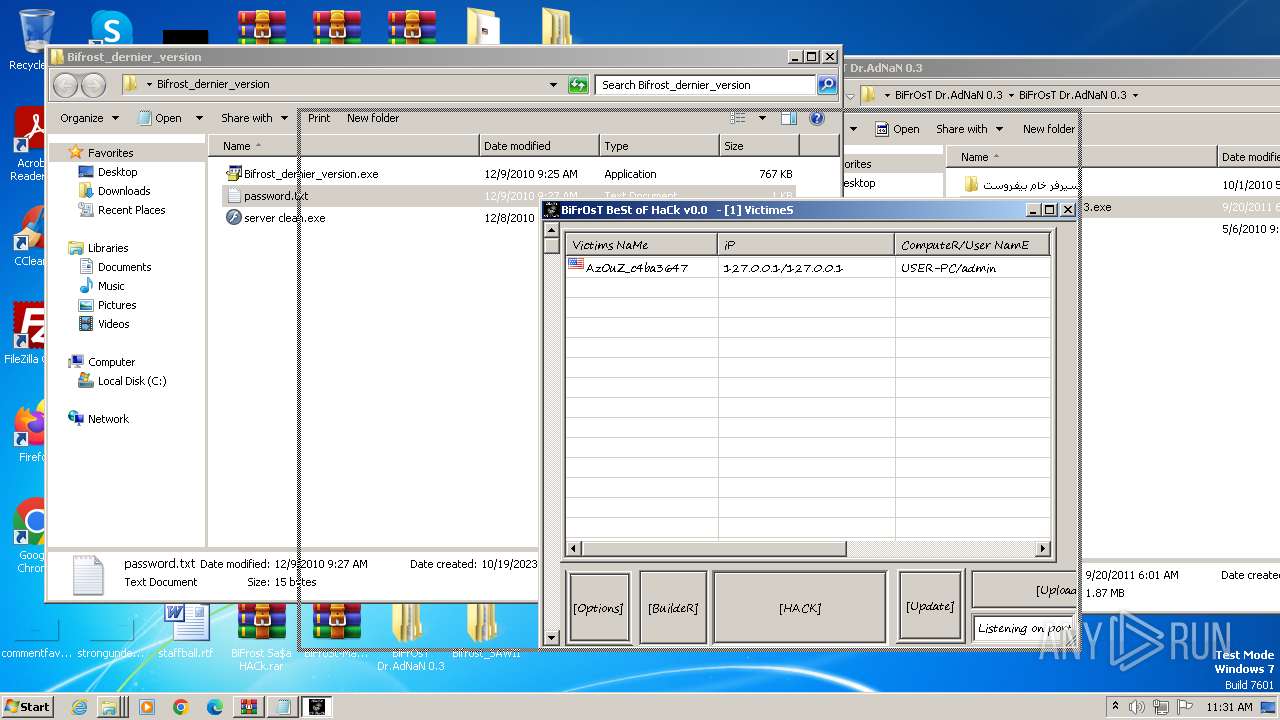
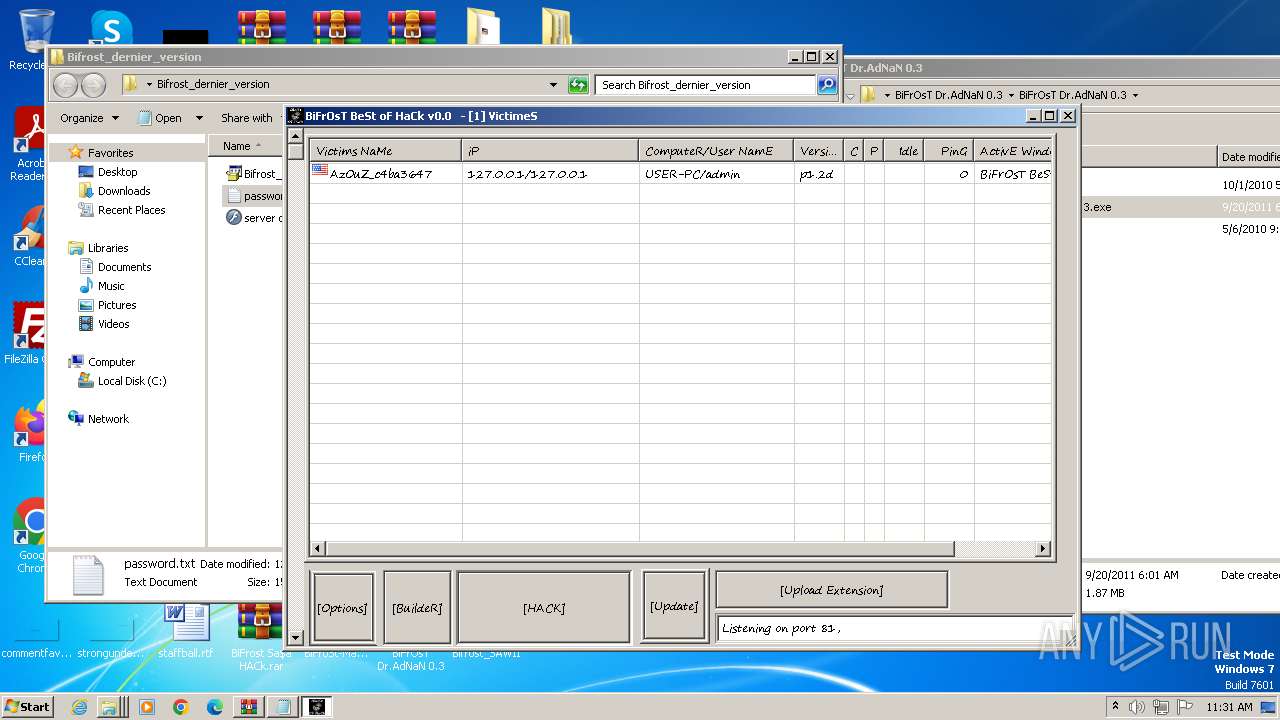
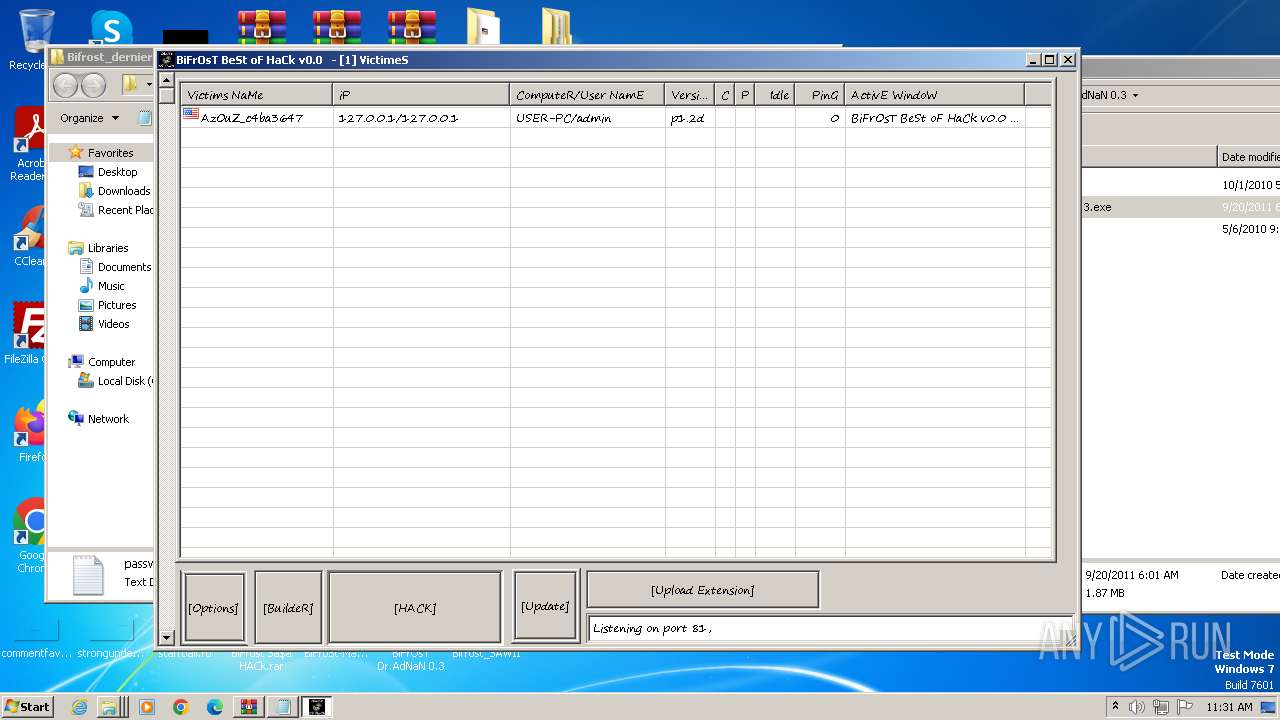
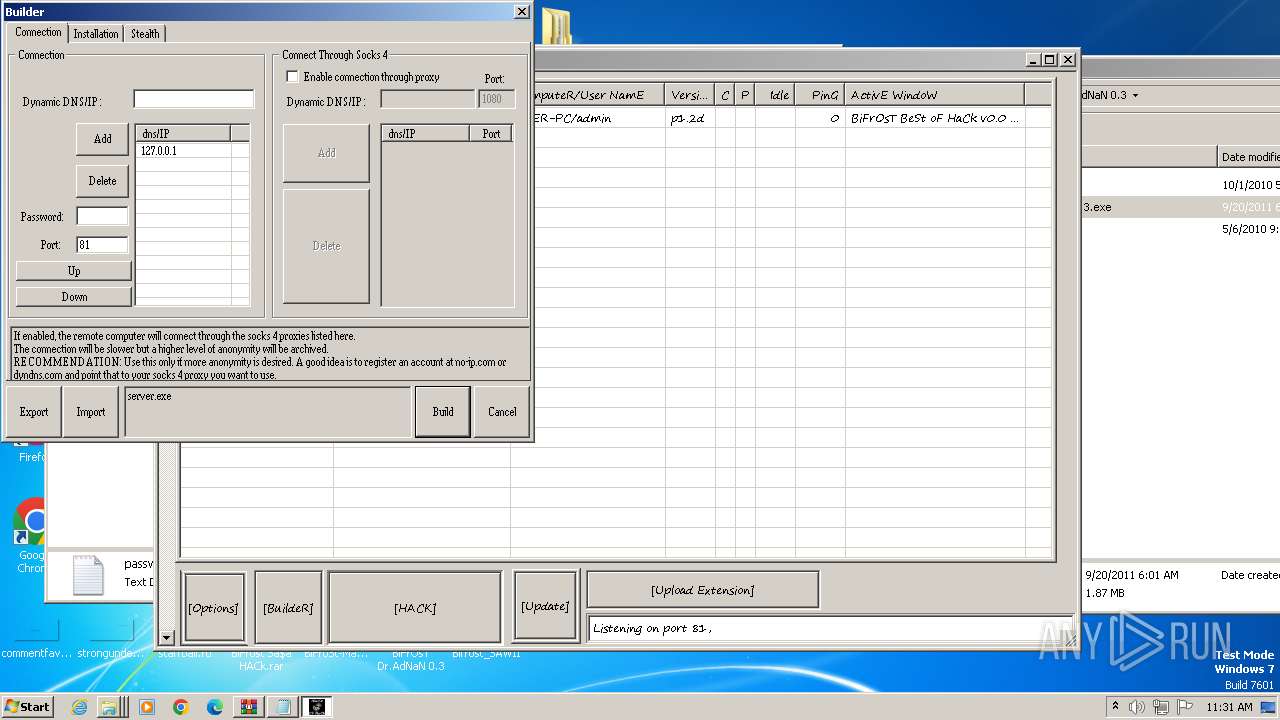
MALICIOUS
Application was dropped or rewritten from another process
- Bifrost.exe (PID: 1372)
- Bifrost.exe (PID: 3716)
- Bifrost 2.6 final.exe (PID: 3228)
- Bifrost 2.6 final.exe (PID: 1396)
- Bifrost Bypass limit 2100 victims bourkane.exe (PID: 3124)
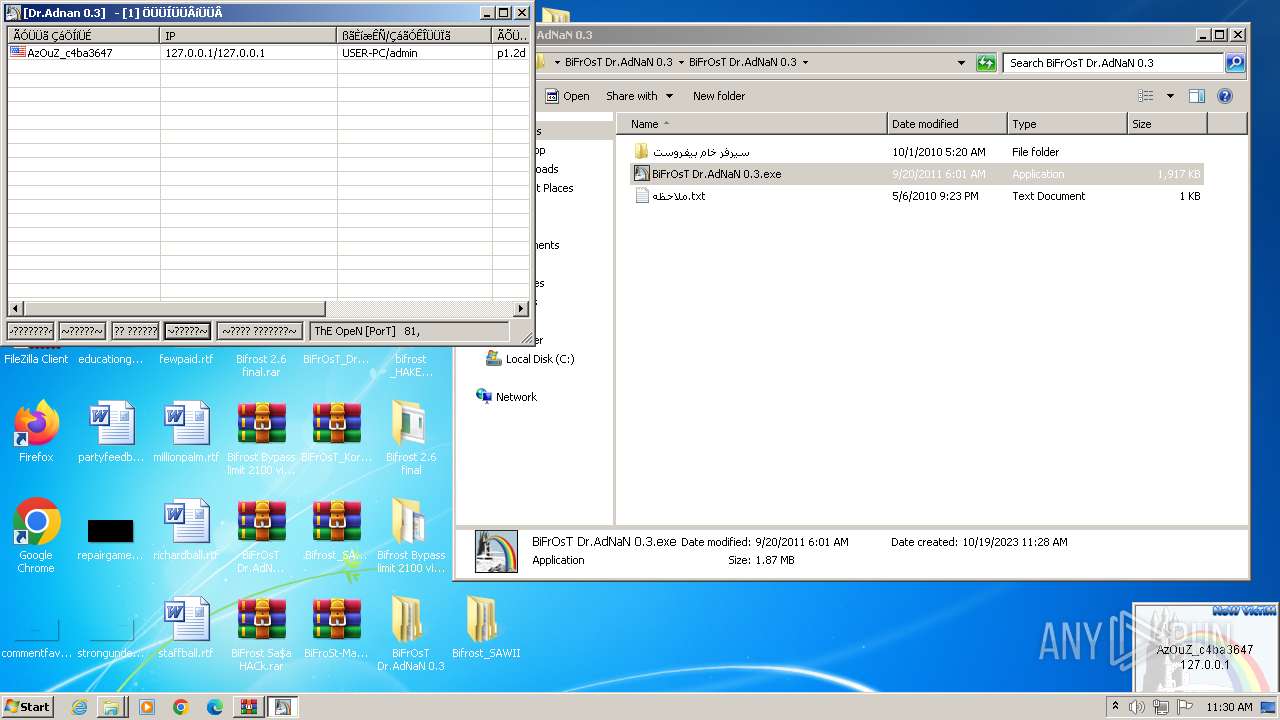
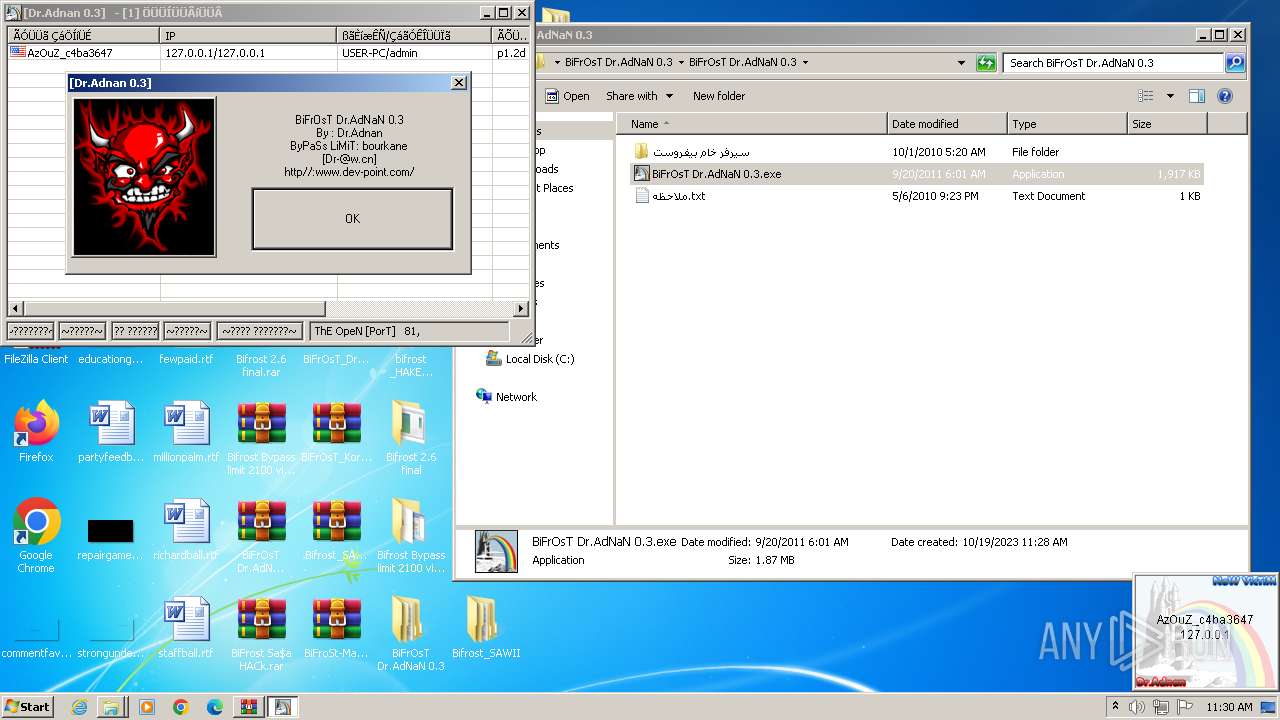
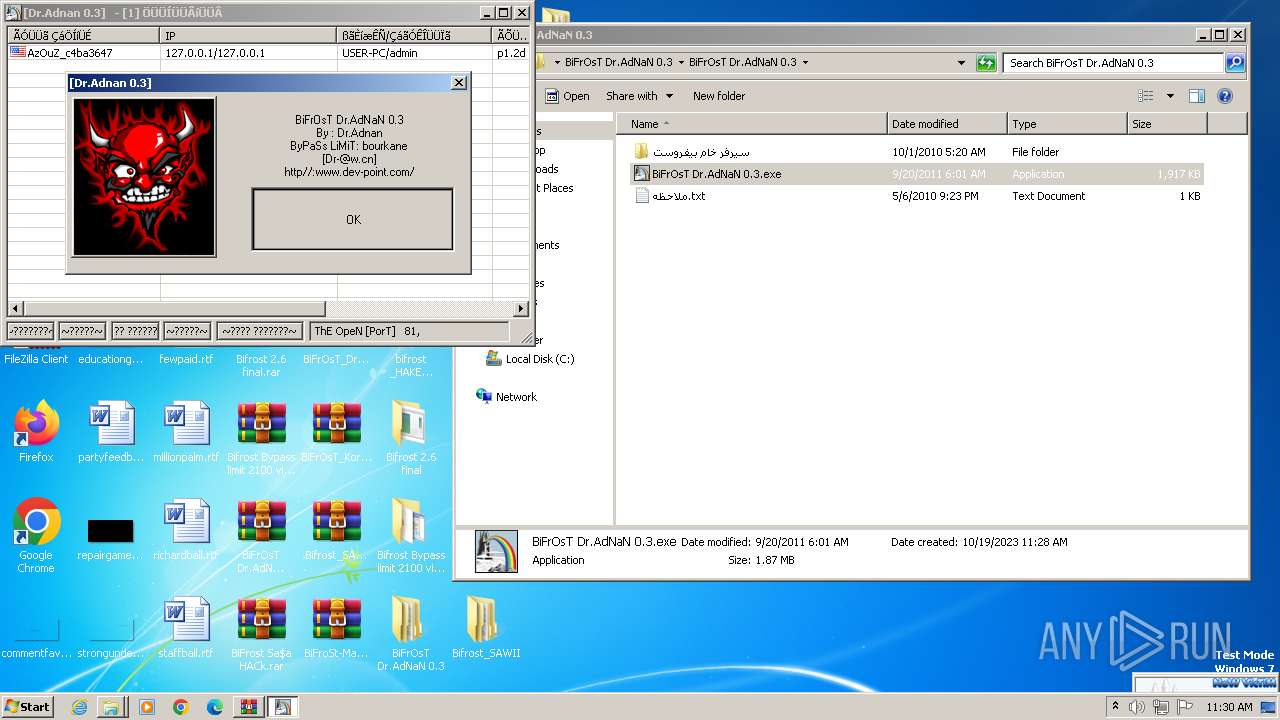
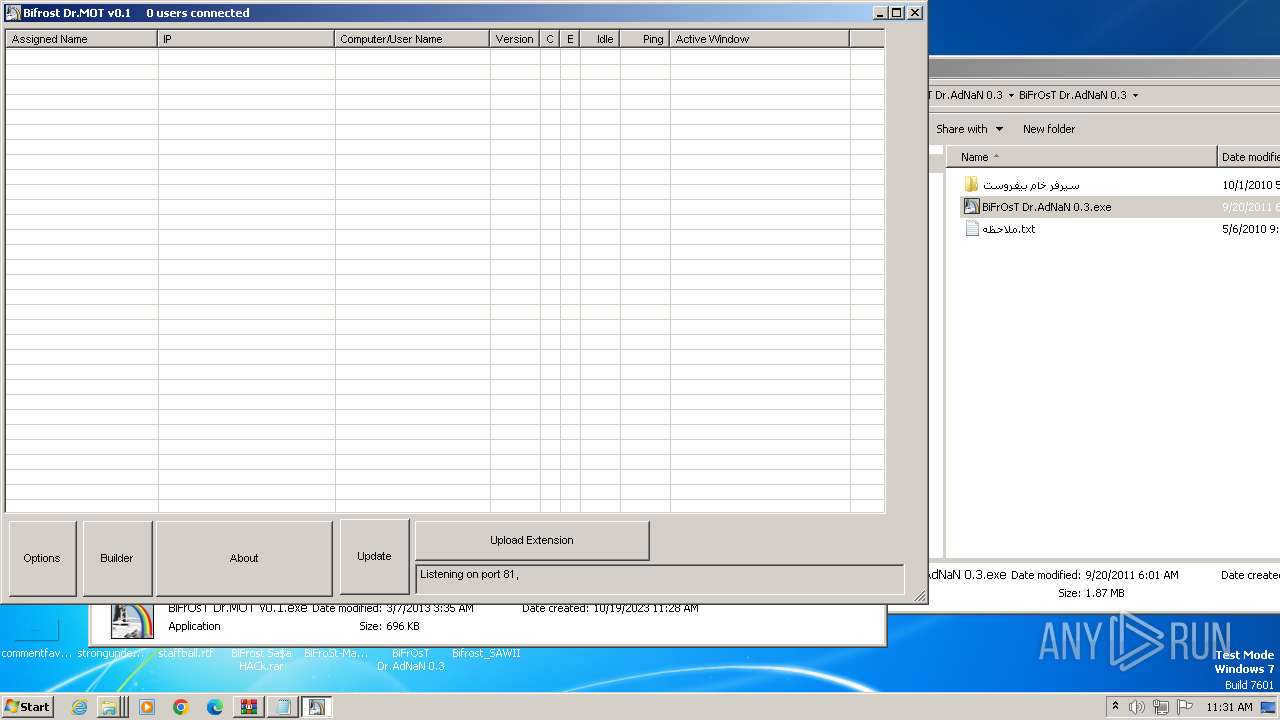
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 2388)
- Bifrost.exe (PID: 2956)
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 3304)
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 2224)
- BiFrost Sa$a HACk.exe (PID: 2996)
- BiFrOsT.شامخ رغم الألم.EXE (PID: 1556)
- TaFFaL.exe (PID: 3212)
- TaFFaL.exe (PID: 2440)
- BiFrOsT BeSt oF HaC.exe (PID: 2616)
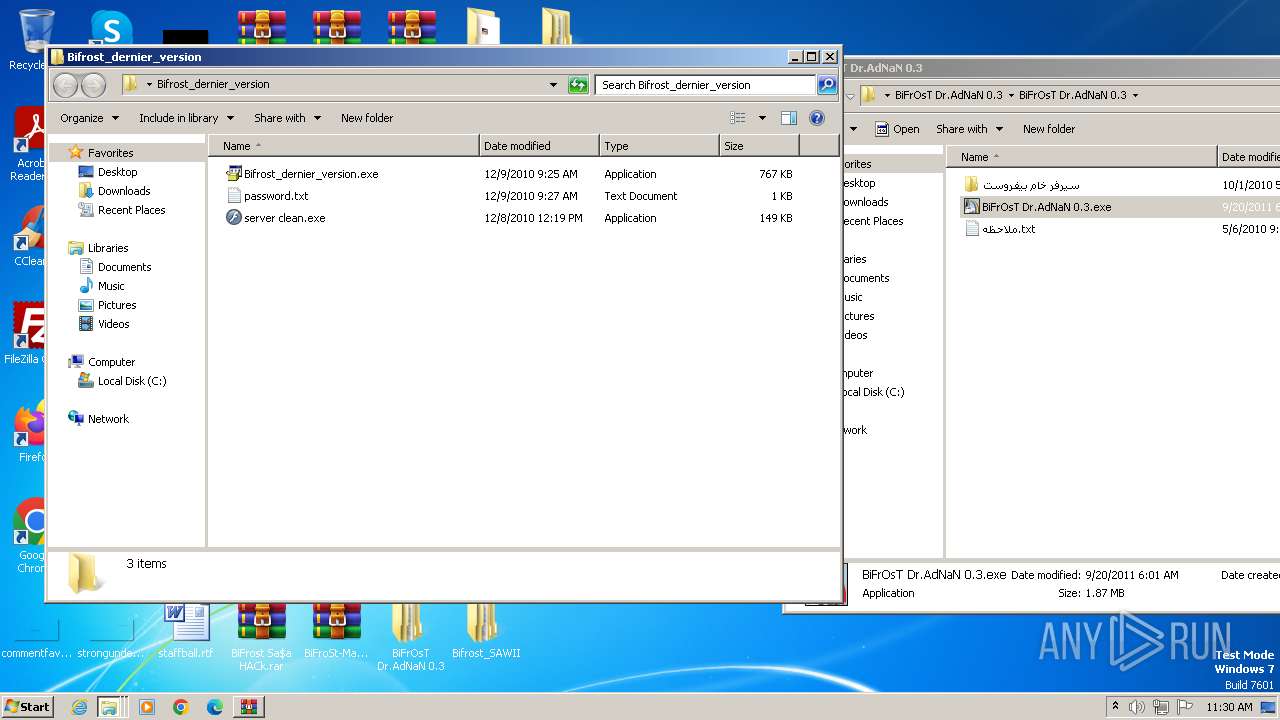
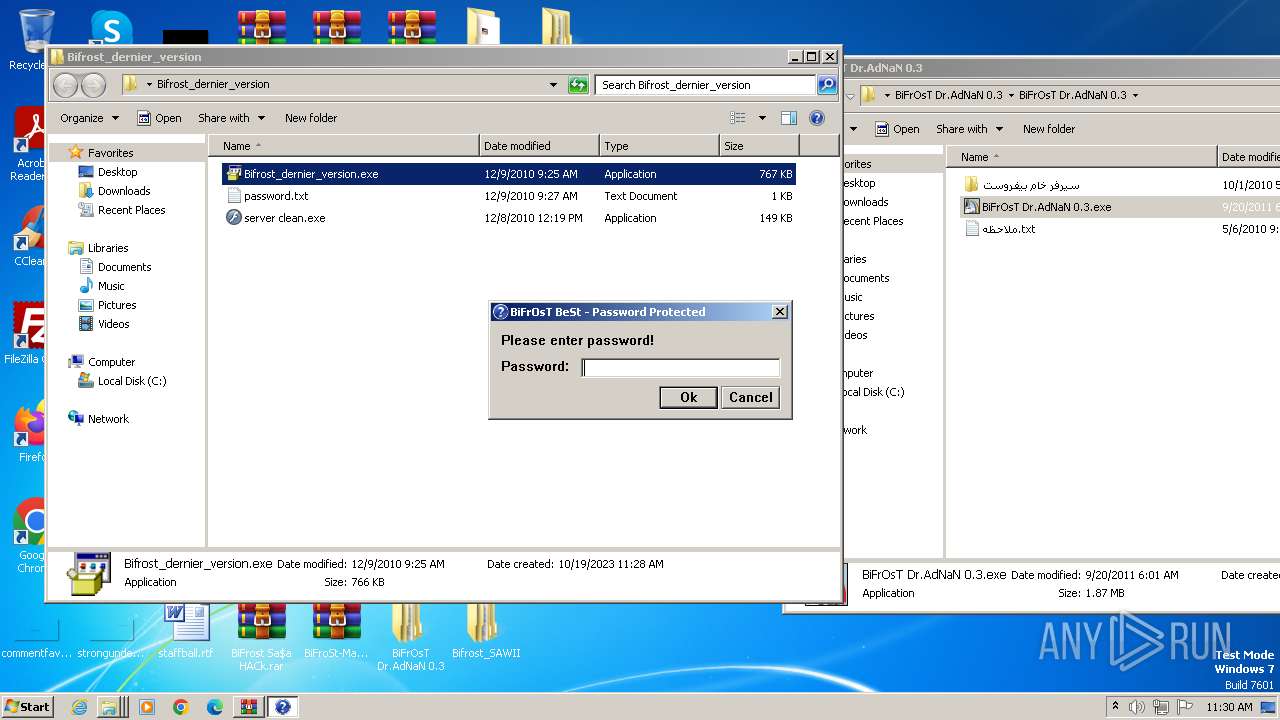
- Bifrost_dernier_version.exe (PID: 2124)
- BiFrOsT Dr.AdNaN 0.3 ByPaSs LiMiT.exe (PID: 3620)
- notepad.exe (PID: 3796)
- Bifrost Saw II.exe (PID: 3624)
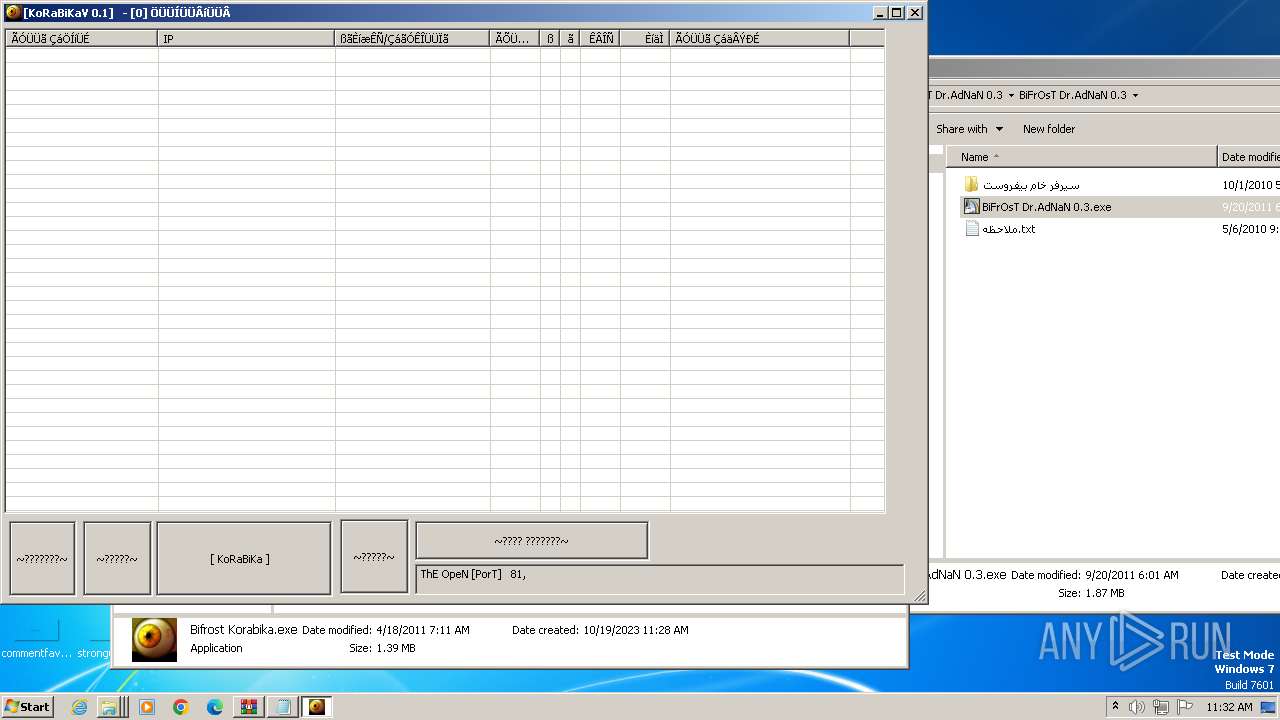
- Bifrost Korabika.exe (PID: 584)
- BiFrOsT Dr.AdNaN 0.3 ByPaSs LiMiT.exe (PID: 4056)
- مترجم الكيلوجر.exe (PID: 888)
- BiFroSt-MaTreX.exe (PID: 3912)
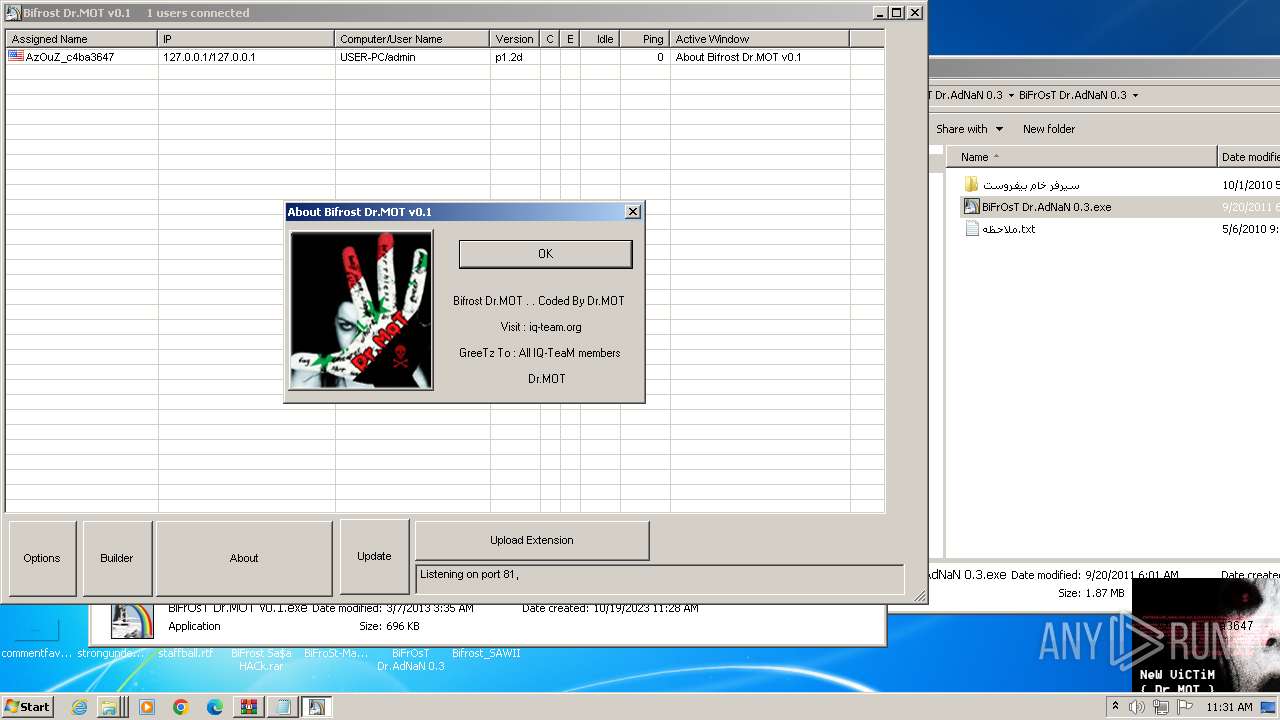
- BiFrOsT Dr.MOT v0.1.exe (PID: 3900)
- BiFrOsT-MoJaHeD.exe (PID: 2648)
- BiFrOsT-MoJaHeD.exe (PID: 1232)
- server.exe (PID: 964)
- notepad.exe (PID: 3584)
Application was injected by another process
- explorer.exe (PID: 1400)
- taskeng.exe (PID: 368)
- dwm.exe (PID: 928)
- ctfmon.exe (PID: 1708)
Runs injected code in another process
- Bifrost 2.6 final.exe (PID: 1396)
- 39E0.tmp (PID: 2608)
- TaFFaL.exe (PID: 2440)
Drops the executable file immediately after the start
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 2388)
- BiFrost Sa$a HACk.exe (PID: 2996)
- Bifrost_dernier_version.exe (PID: 2124)
- BiFroSt-MaTreX.exe (PID: 3912)
Changes appearance of the Explorer extensions
- BiFrost Sa$a HACk.exe (PID: 2996)
- 39E0.tmp (PID: 2608)
UAC/LUA settings modification
- BiFrost Sa$a HACk.exe (PID: 2996)
Changes Security Center notification settings
- BiFrost Sa$a HACk.exe (PID: 2996)
Changes the autorun value in the registry
- explorer.exe (PID: 1400)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 3192)
Application launched itself
- Bifrost 2.6 final.exe (PID: 3228)
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 2224)
- TaFFaL.exe (PID: 3212)
- BiFrOsT Dr.AdNaN 0.3 ByPaSs LiMiT.exe (PID: 3620)
Reads the Internet Settings
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 2388)
- Bifrost_dernier_version.exe (PID: 2124)
- BiFrOsT BeSt oF HaC.exe (PID: 2616)
Starts application with an unusual extension
- BiFrost Sa$a HACk.exe (PID: 2996)
Process drops legitimate windows executable
- explorer.exe (PID: 1400)
SMB connection has been detected (probably for file transfer)
- explorer.exe (PID: 1400)
INFO
Reads the Internet Settings
- explorer.exe (PID: 1400)
Reads the computer name
- Bifrost.exe (PID: 1372)
- Bifrost.exe (PID: 3716)
- wmpnscfg.exe (PID: 1028)
- Bifrost Bypass limit 2100 victims bourkane.exe (PID: 3124)
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 3304)
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 2388)
- 39E0.tmp (PID: 2608)
- BiFrost Sa$a HACk.exe (PID: 2996)
- Bifrost_dernier_version.exe (PID: 2124)
- BiFrOsT BeSt oF HaC.exe (PID: 2616)
- Bifrost Korabika.exe (PID: 584)
- BiFrOsT Dr.AdNaN 0.3 ByPaSs LiMiT.exe (PID: 4056)
- BiFrOsT Dr.MOT v0.1.exe (PID: 3900)
- BiFroSt-MaTreX.exe (PID: 3912)
- Bifrost Saw II.exe (PID: 3624)
- BiFrOsT-MoJaHeD.exe (PID: 1232)
- BiFrOsT-MoJaHeD.exe (PID: 2648)
Checks supported languages
- Bifrost.exe (PID: 1372)
- Bifrost.exe (PID: 3716)
- wmpnscfg.exe (PID: 1028)
- Bifrost 2.6 final.exe (PID: 3228)
- Bifrost 2.6 final.exe (PID: 1396)
- Bifrost Bypass limit 2100 victims bourkane.exe (PID: 3124)
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 2388)
- Bifrost.exe (PID: 2956)
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 2224)
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 3304)
- BiFrost Sa$a HACk.exe (PID: 2996)
- BiFrOsT.شامخ رغم الألم.EXE (PID: 1556)
- 39E0.tmp (PID: 2608)
- Bifrost_dernier_version.exe (PID: 2124)
- TaFFaL.exe (PID: 3212)
- TaFFaL.exe (PID: 2440)
- BiFrOsT BeSt oF HaC.exe (PID: 2616)
- BiFrOsT Dr.AdNaN 0.3 ByPaSs LiMiT.exe (PID: 3620)
- BiFrOsT Dr.AdNaN 0.3 ByPaSs LiMiT.exe (PID: 4056)
- BiFrOsT Dr.MOT v0.1.exe (PID: 3900)
- Bifrost Korabika.exe (PID: 584)
- مترجم الكيلوجر.exe (PID: 888)
- BiFroSt-MaTreX.exe (PID: 3912)
- Bifrost Saw II.exe (PID: 3624)
- BiFrOsT-MoJaHeD.exe (PID: 2648)
- BiFrOsT-MoJaHeD.exe (PID: 1232)
- server.exe (PID: 964)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3192)
- explorer.exe (PID: 1400)
Create files in a temporary directory
- explorer.exe (PID: 1400)
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 2388)
- BiFrost Sa$a HACk.exe (PID: 2996)
- Bifrost_dernier_version.exe (PID: 2124)
- مترجم الكيلوجر.exe (PID: 888)
Manual execution by a user
- Bifrost.exe (PID: 1372)
- WinRAR.exe (PID: 3192)
- Bifrost.exe (PID: 3716)
- wmpnscfg.exe (PID: 1028)
- Bifrost 2.6 final.exe (PID: 3228)
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 2388)
- BiFrost Sa$a HACk.exe (PID: 2996)
- Bifrost Bypass limit 2100 victims bourkane.exe (PID: 3124)
- Bifrost_dernier_version.exe (PID: 2124)
- BiFrOsT.شامخ رغم الألم.EXE (PID: 1556)
- notepad.exe (PID: 3796)
- iexplore.exe (PID: 2556)
- BiFrOsT Dr.AdNaN 0.3 ByPaSs LiMiT.exe (PID: 3620)
- BiFrOsT Dr.MOT v0.1.exe (PID: 3900)
- Bifrost Korabika.exe (PID: 584)
- Bifrost Saw II.exe (PID: 3624)
- مترجم الكيلوجر.exe (PID: 888)
- BiFrOsT-MoJaHeD.exe (PID: 1232)
- server.exe (PID: 964)
- notepad.exe (PID: 3584)
- BiFrOsT-MoJaHeD.exe (PID: 2648)
- BiFroSt-MaTreX.exe (PID: 3912)
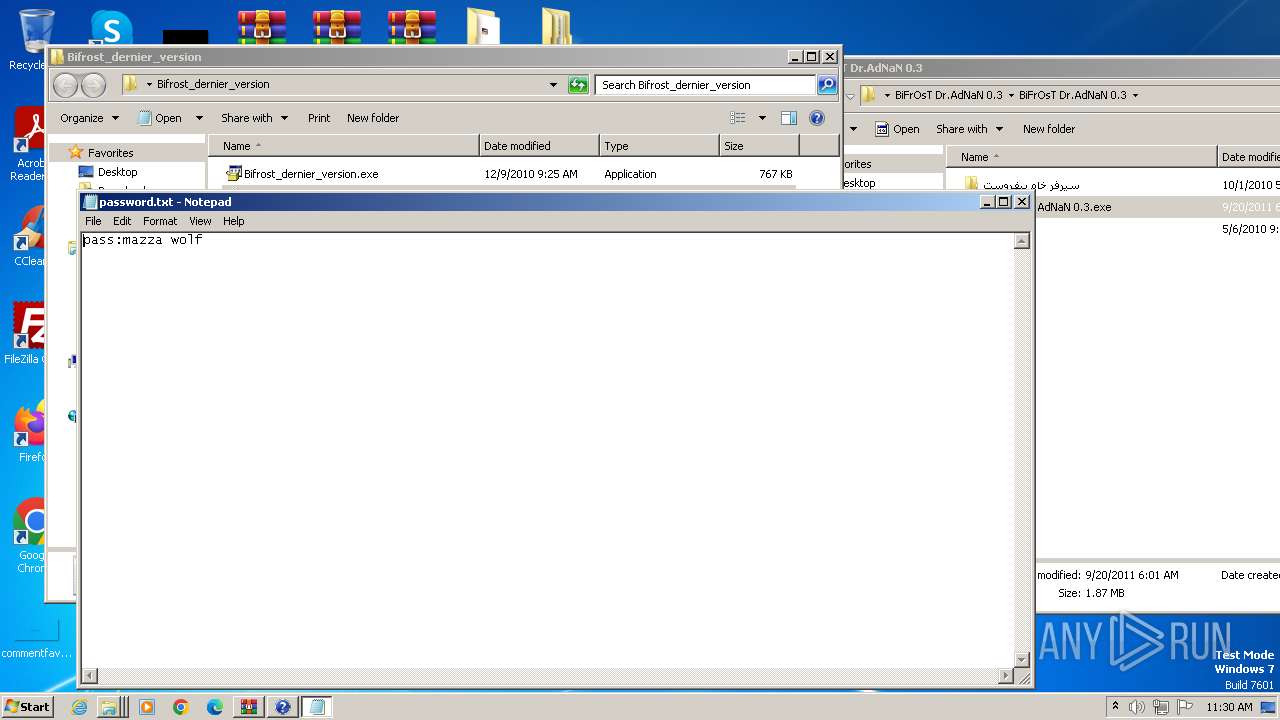
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 3192)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 1028)
- Bifrost Bypass limit 2100 victims bourkane.exe (PID: 3124)
- Bifrost.exe (PID: 3716)
- BiFrOsT Dr.AdNaN 0.3.exe (PID: 3304)
- BiFrost Sa$a HACk.exe (PID: 2996)
- BiFrOsT BeSt oF HaC.exe (PID: 2616)
- BiFrOsT Dr.MOT v0.1.exe (PID: 3900)
- BiFrOsT Dr.AdNaN 0.3 ByPaSs LiMiT.exe (PID: 4056)
- Bifrost Korabika.exe (PID: 584)
- Bifrost Saw II.exe (PID: 3624)
- مترجم الكيلوجر.exe (PID: 888)
- BiFrOsT-MoJaHeD.exe (PID: 2648)
Creates files or folders in the user directory
- explorer.exe (PID: 1400)
- BiFrost Sa$a HACk.exe (PID: 2996)
- TaFFaL.exe (PID: 2440)
Changes appearance of the Explorer extensions
- explorer.exe (PID: 1400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
85
Monitored processes
36
Malicious processes
24
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 368 | taskeng.exe {A138C7FA-105D-4695-A941-2BE80CB32127} | C:\Windows\System32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 584 | "C:\Users\admin\Desktop\BiFrOsT_Korabika_0.1\Dev-PoinT\Bifrost Korabika.exe" | C:\Users\admin\Desktop\BiFrOsT_Korabika_0.1\Dev-PoinT\Bifrost Korabika.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BiFrOsT KoRaBiKa 0.1 Exit code: 20 Version: 0, 1 Modules
| |||||||||||||||
| 888 | "C:\Users\admin\Desktop\Bifrost_SAWII\Bifrost_SAWII\مترجم الكيلوجر.exe" | C:\Users\admin\Desktop\Bifrost_SAWII\Bifrost_SAWII\مترجم الكيلوجر.exe | — | explorer.exe | |||||||||||
User: admin Company: alshamrani Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 928 | "C:\Windows\system32\Dwm.exe" | C:\Windows\System32\dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 964 | "C:\Users\admin\Desktop\BiFroSt-MaTreX\BiFroSt-MaTreX\server.exe" | C:\Users\admin\Desktop\BiFroSt-MaTreX\BiFroSt-MaTreX\server.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | "C:\Users\admin\Desktop\BiFrOsT-MoJaHeDN1\BiFrOsT-MoJaHeDN1\BiFrOsT-MoJaHeDN\BiFrOsT-MoJaHeD.exe" | C:\Users\admin\Desktop\BiFrOsT-MoJaHeDN1\BiFrOsT-MoJaHeDN1\BiFrOsT-MoJaHeDN\BiFrOsT-MoJaHeD.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: عآشق رسول الله Exit code: 4294967295 Version: 1, 2, 1, 0 Modules
| |||||||||||||||
| 1372 | "C:\Users\admin\Desktop\Bifrost - MiSter Swat\Bifrost - MiSter Swat\Bifrost.exe" | C:\Users\admin\Desktop\Bifrost - MiSter Swat\Bifrost - MiSter Swat\Bifrost.exe | — | explorer.exe | |||||||||||
User: admin Company: http://www.chasenet.org Integrity Level: MEDIUM Description: Bifrost 1.2.1 Exit code: 20 Version: 1, 2, 1, 0 Modules
| |||||||||||||||
| 1396 | "C:\Users\admin\Desktop\Bifrost 2.6 final\Bifrost 2.6 final.exe" | C:\Users\admin\Desktop\Bifrost 2.6 final\Bifrost 2.6 final.exe | — | Bifrost 2.6 final.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1400 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
38 423
Read events
37 045
Write events
1 372
Delete events
6
Modification events
| (PID) Process: | (1400) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage\NewShortcuts |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3708) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1400) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs |
| Operation: | write | Name: | MRUListEx |
Value: 020000001E0000001D0000001C0000001B0000001A000000000000001900000003000000180000001600000017000000150000001400000013000000120000000F00000011000000100000000E0000000D0000000C0000000B0000000A00000009000000080000000700000006000000050000000400000001000000FFFFFFFF | |||
Executable files
34
Suspicious files
43
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1400 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\Dfgownloads.rar.lnk | binary | |
MD5:90E1E451344DFC8DEC3BD6F36C80CA9C | SHA256:886F57A2FA882376312E73E8807631C252DBA61CBB7ECF34D5CFA7B230AE079C | |||
| 3708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3708.30443\BiFrost Sa$a HACk.rar | compressed | |
MD5:723F735E8EADD6D9F1FA60849FE675FC | SHA256:39D82928FAFA5FD976B3C7AD685726DD4C8CB30BC4A55E3427D1F9B7E7C4742D | |||
| 3708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3708.30443\BiFrOsT_Dr.MOT_2008.rar | compressed | |
MD5:8535446F8D8FA441D0BE923243A6D665 | SHA256:7BB1368FA1233EC61051186B27DDBBEF3FBEE744D7EA1A7630895D18ED11FD6B | |||
| 1400 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\290532160612e071.automaticDestinations-ms | binary | |
MD5:0F32F7BFD1D642F883AB4364F6FEDD3D | SHA256:28B64329C1AED82D898213D2EE32E0F14B3F4C3AEB0E2D3F6F6439C026F6C6B0 | |||
| 3708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3708.30443\BiFrOsT-MoJaHeD.rar | compressed | |
MD5:76A840E1022EC166EA025B9BC4E0E78F | SHA256:08EA26009DD5803894950BCB21B69876204CCA17C3BCA6E15DFA4D8EB8DFC80D | |||
| 3708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3708.30443\BiFrOsT_Korabika_0.1.rar | compressed | |
MD5:D4BFD71991E731DABECD8ED1D2CDF6BE | SHA256:1925BDF86B03FD170638B63756740560B5C19755452539CD84131538302C9C9F | |||
| 3708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3708.30443\BiFroSt-MaTreX.rar | compressed | |
MD5:C67283FF51E5752C9DCA2CBB546DE084 | SHA256:3AE275DE7412B92EC487596878CB78C258A8E84A2390C2B7C508D1C31BACFC9A | |||
| 3708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3708.30443\Bifrost - MiSter Swat.rar | compressed | |
MD5:61E3078B7A05607E28F4940F128BEB49 | SHA256:738C9C6AFE4F48466F1EB888EE121CDE5A20C847799D0AAB505B0595833D96F5 | |||
| 3708 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3708.30443\BiFrOsT_Dr.AdNaN_0.3_ByPaSs_LiMiT.rar | compressed | |
MD5:840B841CAFA3D80938E7416810A1F6DD | SHA256:64C0D187AF4FC6C065B0EB360A19359A827A6C8ED57EE0B15D57F3129A114E6E | |||
| 1400 | explorer.exe | C:\Users\admin\Desktop\Bifrost - MiSter Swat.rar | compressed | |
MD5:61E3078B7A05607E28F4940F128BEB49 | SHA256:738C9C6AFE4F48466F1EB888EE121CDE5A20C847799D0AAB505B0595833D96F5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
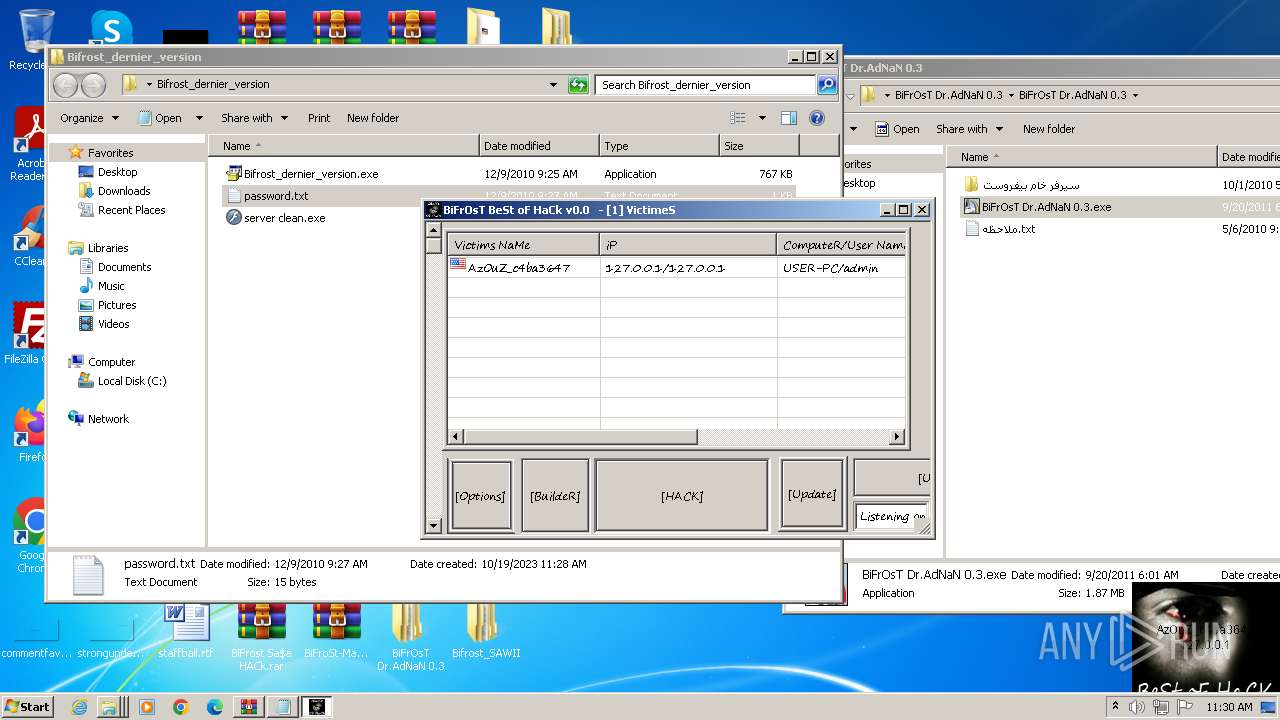
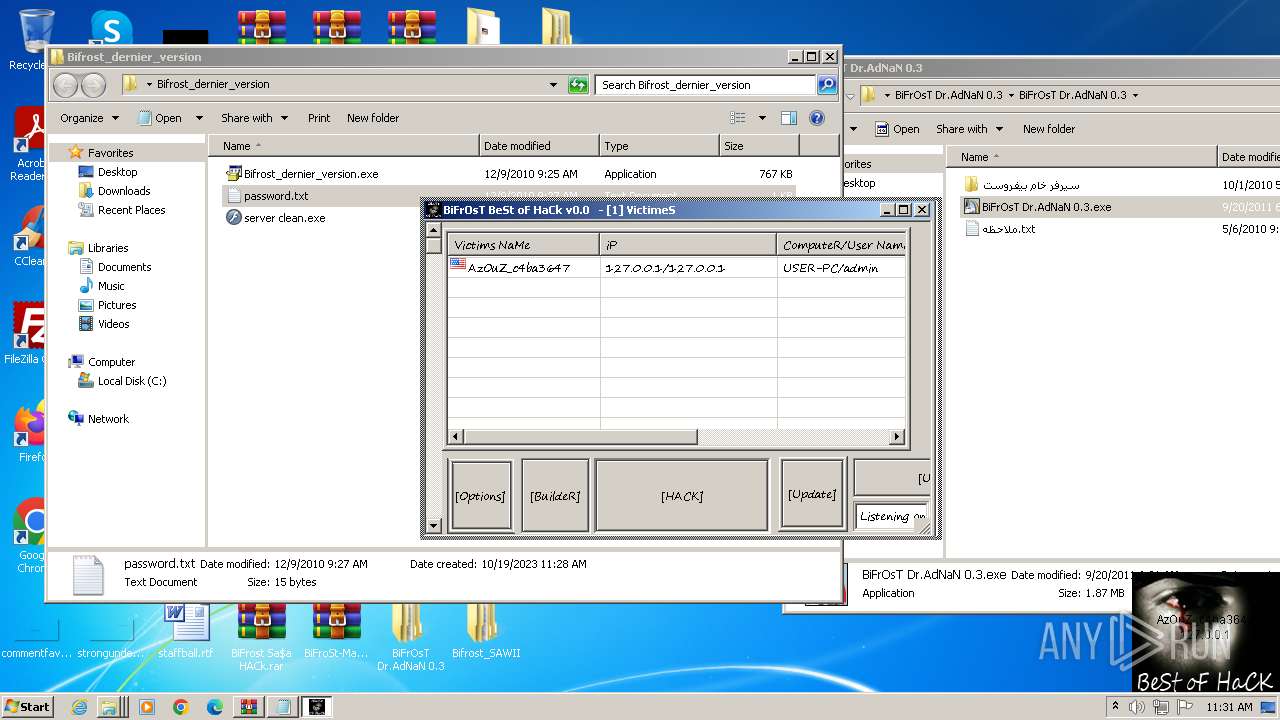
azouz0.no-ip.org |
| unknown |
saidsaid.no-ip.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to a Suspicious no-ip Domain |
1088 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to a Suspicious no-ip Domain |