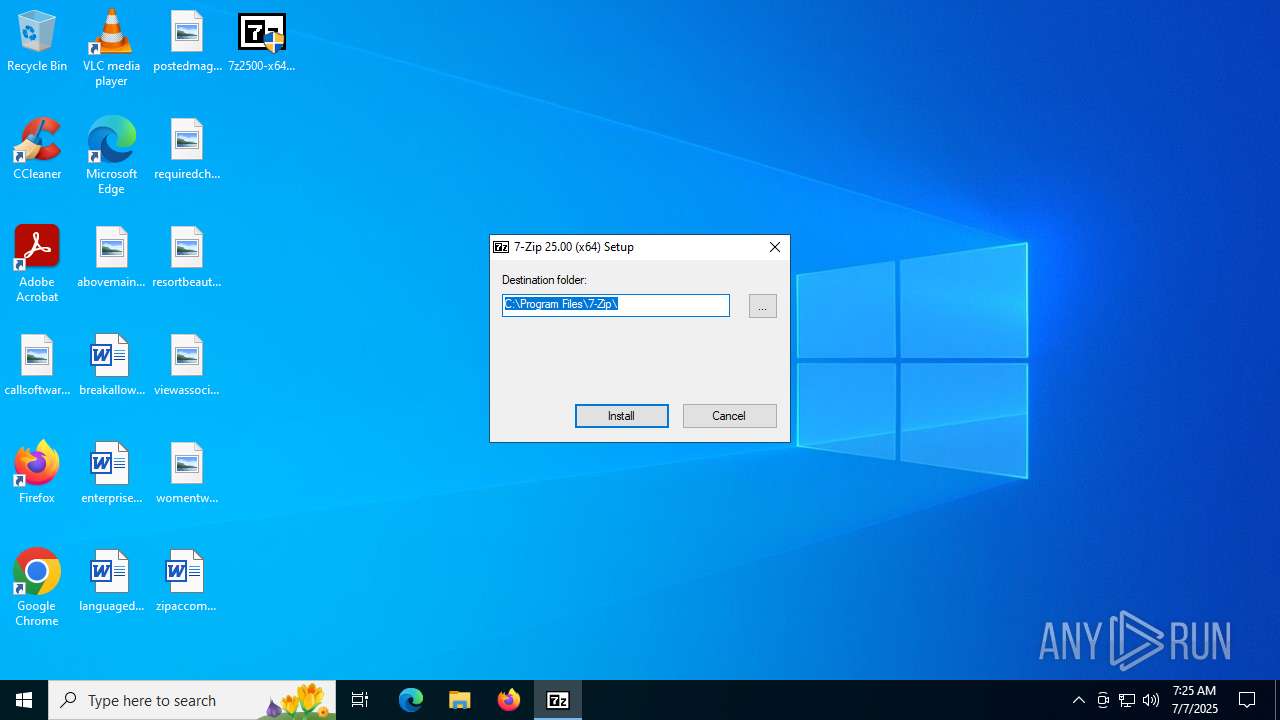
| File name: | 7z2500-x64.exe |
| Full analysis: | https://app.any.run/tasks/bc497ace-d749-44f6-90ae-1c06d3dc0103 |
| Verdict: | Malicious activity |
| Analysis date: | July 07, 2025, 07:25:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 9EECA41AA10EF3C99D7DB2EA97160E17 |
| SHA1: | 3BF66C442B446BB642AB75360077203A1DDDC16F |
| SHA256: | 7B67375B2B303E05D2989F23E986126EDA67435C71231FA4B0BDAEB7A619A0A6 |
| SSDEEP: | 49152:/PHtcOHyP4Rdkd2XMixIU8P8K1lGEfmvzqoVILcPyff7hkjIPdn0NdbZlpLYHqlQ:/ftcdWK2XMgqkKbt4ZtPg1kjI1n25zpI |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops 7-zip archiver for unpacking
- 7z2500-x64.exe (PID: 2136)
Creates/Modifies COM task schedule object
- 7z2500-x64.exe (PID: 2136)
Creates a software uninstall entry
- 7z2500-x64.exe (PID: 2136)
Executable content was dropped or overwritten
- 7z2500-x64.exe (PID: 2136)
The process executes via Task Scheduler
- updater.exe (PID: 1096)
Application launched itself
- updater.exe (PID: 1096)
INFO
The sample compiled with russian language support
- 7z2500-x64.exe (PID: 2136)
The sample compiled with english language support
- 7z2500-x64.exe (PID: 2136)
Reads the computer name
- 7z2500-x64.exe (PID: 2136)
- updater.exe (PID: 1096)
Checks supported languages
- 7z2500-x64.exe (PID: 2136)
- updater.exe (PID: 1096)
- updater.exe (PID: 6796)
Creates files in the program directory
- 7z2500-x64.exe (PID: 2136)
Process checks whether UAC notifications are on
- updater.exe (PID: 1096)
Checks proxy server information
- slui.exe (PID: 768)
Reads the software policy settings
- slui.exe (PID: 768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:07:05 12:00:00+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 24064 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7294 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 25.0.0.0 |
| ProductVersionNumber: | 25.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Igor Pavlov |
| FileDescription: | 7-Zip Installer |
| FileVersion: | 25 |
| InternalName: | 7zipInstall |
| LegalCopyright: | Copyright (c) 1999-2025 Igor Pavlov |
| OriginalFileName: | 7zipInstall.exe |
| ProductName: | 7-Zip |
| ProductVersion: | 25 |
Total processes
140
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 768 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --wake --system | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 2136 | "C:\Users\admin\Desktop\7z2500-x64.exe" | C:\Users\admin\Desktop\7z2500-x64.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Installer Exit code: 0 Version: 25.00 Modules
| |||||||||||||||
| 3652 | "C:\Users\admin\Desktop\7z2500-x64.exe" | C:\Users\admin\Desktop\7z2500-x64.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Installer Exit code: 3221226540 Version: 25.00 Modules
| |||||||||||||||
| 6796 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=134.0.6985.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x2a0,0x2a4,0x2a8,0x27c,0x2ac,0x111c460,0x111c46c,0x111c478 | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
Total events
3 623
Read events
3 602
Write events
21
Delete events
0
Modification events
| (PID) Process: | (2136) 7z2500-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path64 |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (2136) 7z2500-x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (2136) 7z2500-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path64 |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (2136) 7z2500-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\7-Zip |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (2136) 7z2500-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (2136) 7z2500-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{23170F69-40C1-278A-1000-000100020000}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (2136) 7z2500-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {23170F69-40C1-278A-1000-000100020000} |
Value: 7-Zip Shell Extension | |||
| (PID) Process: | (2136) 7z2500-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Approved |
| Operation: | write | Name: | {23170F69-40C1-278A-1000-000100020000} |
Value: 7-Zip Shell Extension | |||
| (PID) Process: | (2136) 7z2500-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\7zFM.exe |
| Operation: | write | Name: | Path |
Value: C:\Program Files\7-Zip\ | |||
| (PID) Process: | (2136) 7z2500-x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\7-Zip |
| Operation: | write | Name: | DisplayName |
Value: 7-Zip 25.00 (x64) | |||
Executable files
9
Suspicious files
0
Text files
98
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2136 | 7z2500-x64.exe | C:\Program Files\7-Zip\Lang\af.txt | text | |
MD5:DF216FAE5B13D3C3AFE87E405FD34B97 | SHA256:9CF684EA88EA5A479F510750E4089AEE60BBB2452AA85285312BAFCC02C10A34 | |||
| 2136 | 7z2500-x64.exe | C:\Program Files\7-Zip\History.txt | text | |
MD5:D0B8877E2887EBB5ED1C743536DAB79A | SHA256:9C92C646E66AC7C8F200659AE3153785E7D6C07EFDE95C81EC131EA4BBCC394E | |||
| 2136 | 7z2500-x64.exe | C:\Program Files\7-Zip\Lang\an.txt | text | |
MD5:F16218139E027338A16C3199091D0600 | SHA256:3AB9F7AACD38C4CDE814F86BC37EEC2B9DF8D0DDDB95FC1D09A5F5BCB11F0EEB | |||
| 2136 | 7z2500-x64.exe | C:\Program Files\7-Zip\Lang\az.txt | text | |
MD5:9CD3A23CA6F66F570607F63BE6AA0001 | SHA256:1DA941116E20E69F61A4A68481797E302C11FCF462CA7203A565588B26011615 | |||
| 2136 | 7z2500-x64.exe | C:\Program Files\7-Zip\Lang\co.txt | text | |
MD5:DE64842F09051E3AF6792930A0456B16 | SHA256:DCFB95B47A4435EB7504B804DA47302D8A62BBE450DADF1A34BAEA51C7F60C77 | |||
| 2136 | 7z2500-x64.exe | C:\Program Files\7-Zip\Lang\ar.txt | text | |
MD5:5747381DC970306051432B18FB2236F2 | SHA256:85A26C7B59D6D9932F71518CCD03ECEEBA42043CB1707719B72BFC348C1C1D72 | |||
| 2136 | 7z2500-x64.exe | C:\Program Files\7-Zip\Lang\ast.txt | text | |
MD5:1CF6411FF9154A34AFB512901BA3EE02 | SHA256:F5F2174DAF36E65790C7F0E9A4496B12E14816DAD2EE5B1D48A52307076BE35F | |||
| 2136 | 7z2500-x64.exe | C:\Program Files\7-Zip\Lang\ba.txt | text | |
MD5:387FF78CF5F524FC44640F3025746145 | SHA256:8A85C3FCB5F81157490971EE4F5E6B9E4F80BE69A802EBED04E6724CE859713F | |||
| 2136 | 7z2500-x64.exe | C:\Program Files\7-Zip\Lang\bg.txt | text | |
MD5:2D0C8197D84A083EF904F8F5608AFE46 | SHA256:62C6F410D011A109ABECB79CAA24D8AEB98B0046D329D611A4D07E66460EEF3F | |||
| 2136 | 7z2500-x64.exe | C:\Program Files\7-Zip\Lang\ca.txt | text | |
MD5:A77210BE2527533D1ECEB8F0EA49607A | SHA256:DA4DF6490C7BC8AFD804509F696F9AFA6F709B7A327044E2781FA6C95770B239 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
39
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5528 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 4.175.87.197:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | compressed | 23.9 Kb | whitelisted |
3000 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
3000 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
3000 | SIHClient.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
3000 | SIHClient.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
3000 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5528 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5528 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5528 | RUXIMICS.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5528 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |