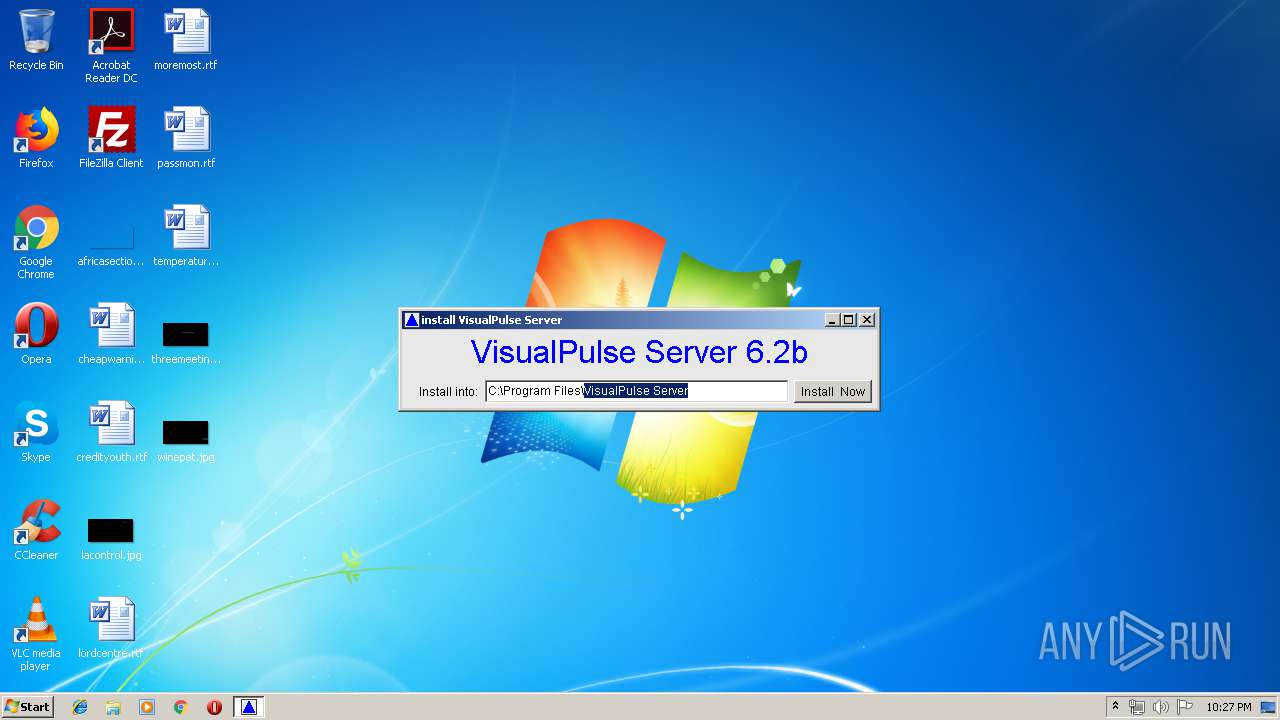
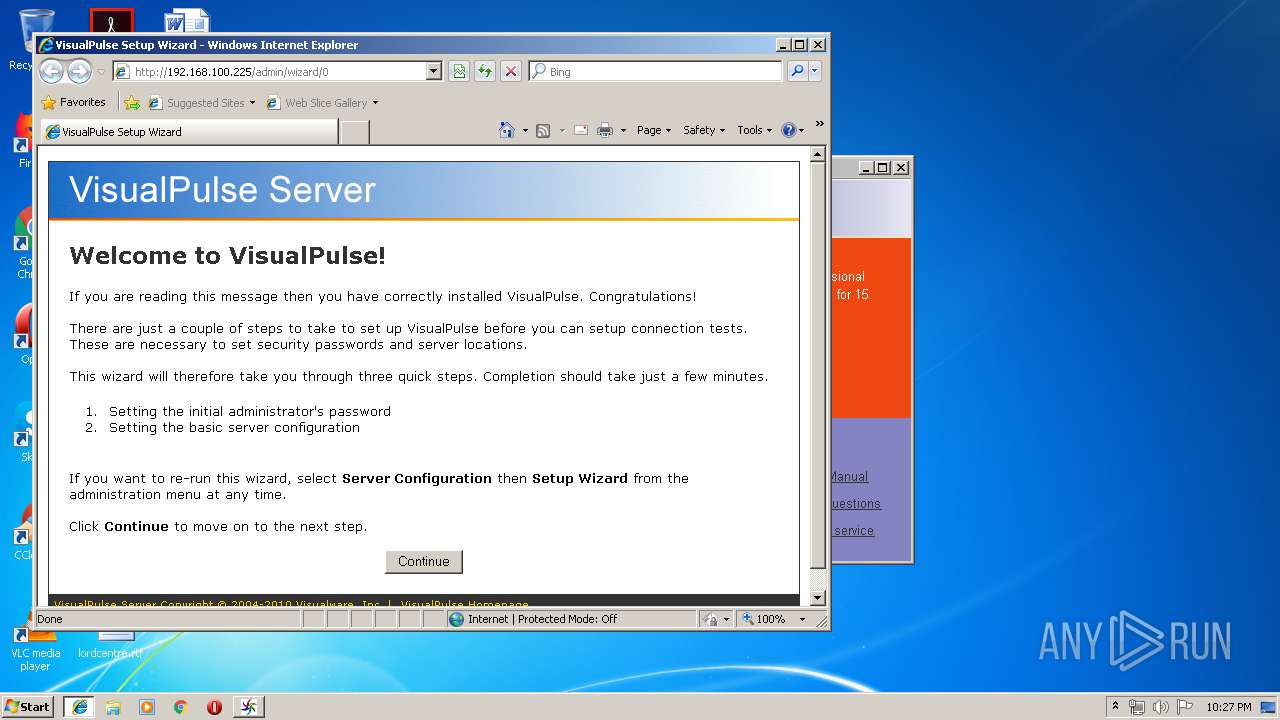
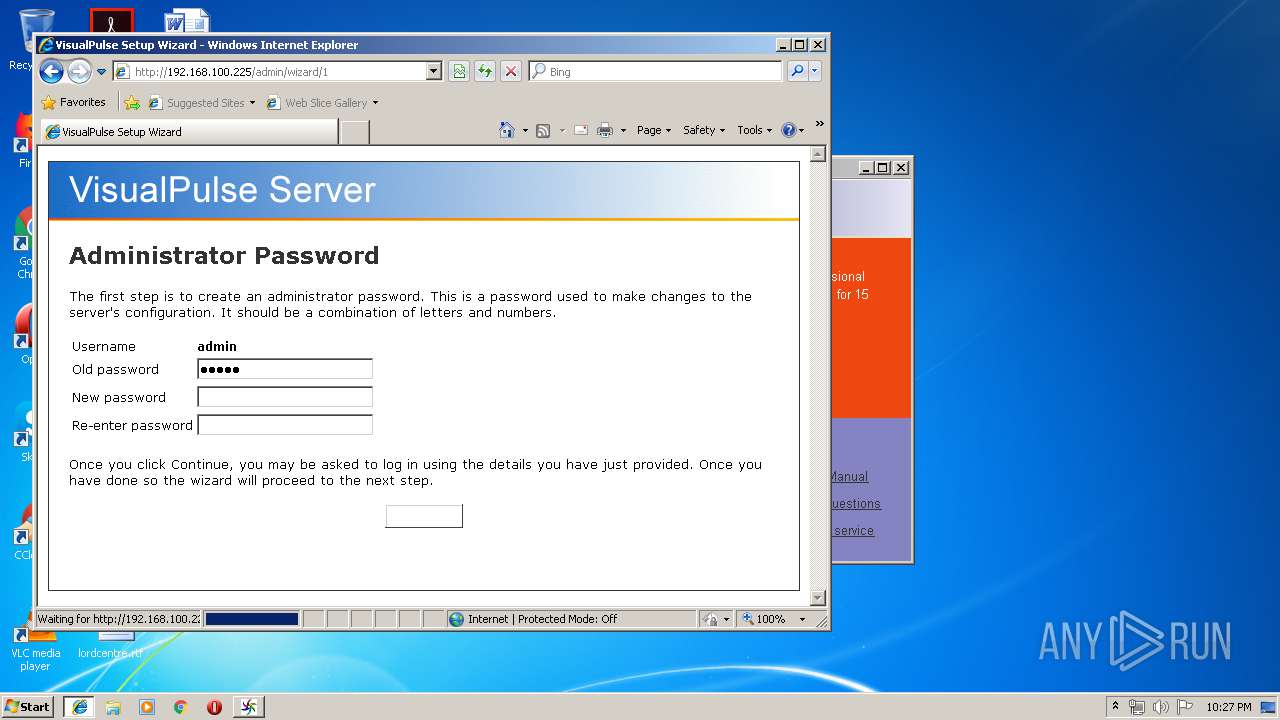
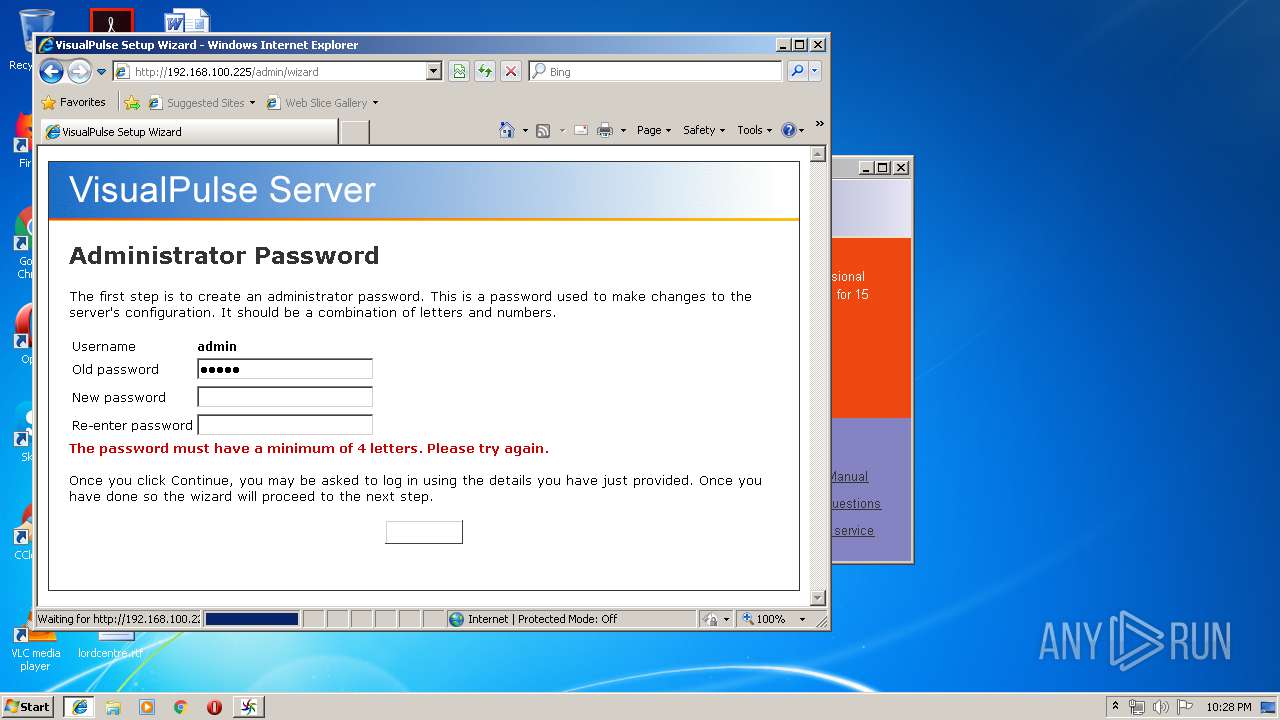
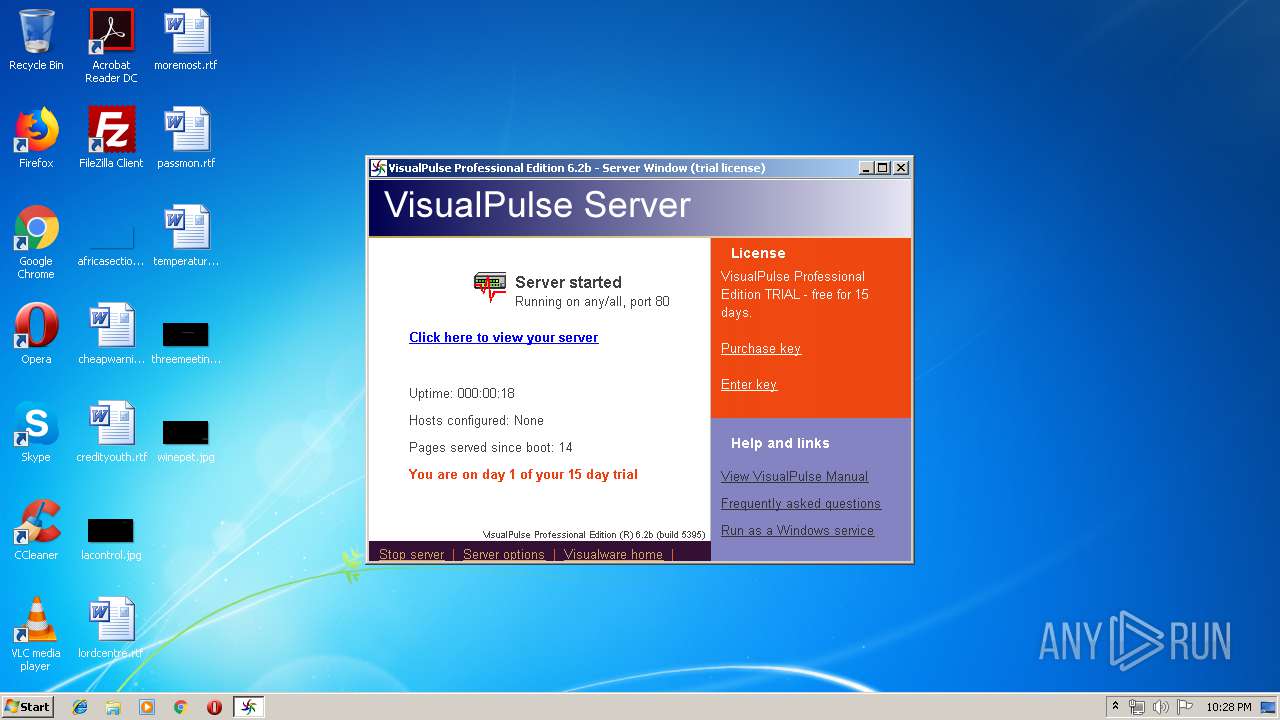
| download: | vip.exe |
| Full analysis: | https://app.any.run/tasks/cd9dcb46-b181-489b-90ad-f93bb49e8018 |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2019, 21:27:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A9679422E143615945EB0B6B3ECA6A43 |
| SHA1: | 91BAE25BDFD6281989975BDEA0A667DDE31CB53D |
| SHA256: | 7B5671DE10313F6151AC474CB3BDA7B0E2BA7620233F2431D36A31F5394CEEB6 |
| SSDEEP: | 24576:JnzABXFT5Nkp28OTkjPz+ynIAtuf+zsQ5jhKbitpW31c8lWt7Str1kfEPunnfmd:BzukUZwb+ynttuf+zsACitpW3r0t782k |
MALICIOUS
Loads dropped or rewritten executable
- java.exe (PID: 2448)
- java.exe (PID: 1100)
Application was dropped or rewritten from another process
- MakeLink.exe (PID: 3504)
- VisualPulse.exe (PID: 2540)
- vropen0.exe (PID: 2960)
SUSPICIOUS
Executable content was dropped or overwritten
- java.exe (PID: 2448)
Creates files in the program directory
- MakeLink.exe (PID: 3504)
- java.exe (PID: 2448)
- java.exe (PID: 1100)
Creates a software uninstall entry
- java.exe (PID: 2448)
Starts Internet Explorer
- vropen0.exe (PID: 2960)
Uses IPCONFIG.EXE to discover IP address
- java.exe (PID: 1100)
INFO
Application launched itself
- iexplore.exe (PID: 2748)
Changes internet zones settings
- iexplore.exe (PID: 2748)
Reads internet explorer settings
- iexplore.exe (PID: 1084)
Creates files in the user directory
- iexplore.exe (PID: 1084)
Reads Internet Cache Settings
- iexplore.exe (PID: 2748)
- iexplore.exe (PID: 1084)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2005:12:19 19:55:35+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 6656 |
| InitializedDataSize: | 5632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x26c8 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Dec-2005 18:55:35 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 19-Dec-2005 18:55:35 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000185C | 0x00001A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.99769 |
.rdata | 0x00003000 | 0x0000062A | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.11709 |
.data | 0x00004000 | 0x000005A4 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.3583 |
.rsrc | 0x00005000 | 0x00000604 | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.97743 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.82354 | 542 | Latin 1 / Western European | English - United States | RT_MANIFEST |
234 | 2.16096 | 20 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
KERNEL32.dll |
MSVCRT.dll |
SHELL32.dll |
USER32.dll |
Total processes
46
Monitored processes
10
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 592 | "C:\Users\admin\AppData\Local\Temp\vip.exe" | C:\Users\admin\AppData\Local\Temp\vip.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1084 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2748 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1100 | java -mx256m jexepackboot ER "C:\Program Files\VisualPulse Server\VisualPulse.exe" "C:\Users\admin\AppData\Local\Temp\5CB3A5D5106F85" /install | C:\ProgramData\Oracle\Java\javapath\java.exe | VisualPulse.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2448 | java -mx256m jexepackboot ER "C:\Users\admin\AppData\Local\Temp\vip.exe" "C:\Users\admin\AppData\Local\Temp\X42F250" | C:\ProgramData\Oracle\Java\javapath\java.exe | vip.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2540 | "C:\Program Files\VisualPulse Server\VisualPulse.exe" -Q* /install | C:\Program Files\VisualPulse Server\VisualPulse.exe | — | java.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2632 | "C:\Users\admin\AppData\Local\Temp\vip.exe" | C:\Users\admin\AppData\Local\Temp\vip.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2748 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | vropen0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2752 | ipconfig.exe /all | C:\Windows\system32\ipconfig.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2960 | "C:\Program Files\VisualPulse Server\exe\vropen0" http://192.168.100.225:80/homepage | C:\Program Files\VisualPulse Server\exe\vropen0.exe | — | java.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3504 | "C:\Users\admin\AppData\Local\Temp\X42F250\MakeLink" C:\Users\admin\AppData\Local\Temp\X42F250\makelinks.txt | C:\Users\admin\AppData\Local\Temp\X42F250\MakeLink.exe | — | java.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
530
Read events
460
Write events
69
Delete events
1
Modification events
| (PID) Process: | (2448) java.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: java.exe | |||
| (PID) Process: | (2448) java.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\VisualPulse.exe |
| Operation: | write | Name: | |
Value: C:\Program Files\VisualPulse Server\VisualPulse.exe | |||
| (PID) Process: | (2448) java.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\VisualPulse.exe |
| Operation: | write | Name: | Path |
Value: C:\Program Files\VisualPulse Server | |||
| (PID) Process: | (1100) java.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: java.exe | |||
| (PID) Process: | (2448) java.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualPulse Server |
| Operation: | write | Name: | DisplayName |
Value: VisualPulse Server | |||
| (PID) Process: | (2448) java.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualPulse Server |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\VisualPulse Server\Uninstall.exe" "C:\Program Files\VisualPulse Server" | |||
| (PID) Process: | (2748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2748) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
Executable files
14
Suspicious files
8
Text files
170
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 592 | vip.exe | C:\Users\admin\AppData\Local\Temp\X42F250\jexepackboot.class | — | |
MD5:— | SHA256:— | |||
| 2448 | java.exe | C:\Users\admin\AppData\Local\Temp\X42F250\packlist.txt | text | |
MD5:— | SHA256:— | |||
| 2448 | java.exe | C:\Users\admin\AppData\Local\Temp\X42F250\install.ini | text | |
MD5:— | SHA256:— | |||
| 2448 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2448 | java.exe | C:\Users\admin\AppData\Local\Temp\X42F250\MakeLink.exe | executable | |
MD5:61C2C167AC821487C6EE506B7BDD9F10 | SHA256:740658EC880397CD4B96DD8FD9B12E94C6C4F643A85965EA89FCA573E406DD02 | |||
| 2448 | java.exe | C:\Users\admin\AppData\Local\Temp\X42F250\src\data\vip.gif | image | |
MD5:— | SHA256:— | |||
| 2448 | java.exe | C:\Users\admin\AppData\Local\Temp\X42F250\Win32.class | class | |
MD5:9B299F75002E0026CBA02F210287A8DE | SHA256:6E8A613BE31EADE2EC96CFB34BF766CF79CF15D25191EFD3DCF77445BF144D23 | |||
| 2448 | java.exe | C:\Users\admin\AppData\Local\Temp\X42F250\src\jntsvcv1.dll | executable | |
MD5:— | SHA256:— | |||
| 2448 | java.exe | C:\Users\admin\AppData\Local\Temp\X42F250\LicenseAgreement.class | class | |
MD5:4B5933A6927997F56F7B4623CAC4BE5F | SHA256:26C6D5EA64F4FC3AE29530F27E7C0337545E5E974001E60288A5E214056E1CD2 | |||
| 2448 | java.exe | C:\Users\admin\AppData\Local\Temp\X42F250\jwin32v8.dll | executable | |
MD5:6C213F6DFA2D3A4E5187EC97D3F89878 | SHA256:A3D01D7D138A918BE744C0E2EF624EAAB315951F2890345D851DE2CB6F3BDC83 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1100 | java.exe | GET | 400 | 38.100.141.75:80 | http://secure.visualware.com./crm/LiveUpdate?q=PjiQVzV3Nq2XyJgzsW41W0BFvY2wEK0dWivSl9ONRzp1S9MpZEXVPUdUsu613LyHwqUQtNw33eUvbgB18cZdFdBmgOPMuYYDtk1YsD2VhSG5MK5QZYK3RJ716Oqtgict4H | US | — | — | suspicious |
2748 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1100 | java.exe | 38.100.141.76:80 | www.visualware.com | Cogent Communications | US | suspicious |
1100 | java.exe | 38.100.141.75:80 | secure.visualware.com | Cogent Communications | US | unknown |
2748 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.visualware.com |
| malicious |
secure.visualware.com |
| suspicious |
www.bing.com |
| whitelisted |
PjiQVzV3Nq2XyJgzsW41W0BFvY2wEK0dWivSl9ONRzp.1S9MpZEXVPUdUsu613LyHwqUQtNw33eUvbgB18cZdFd.BmgOPMuYYDtk1YsD2VhSG5MK5QZYK3RJ716Oqtgict4H.LiveUpdate.crm.visualware.com |
| unknown |