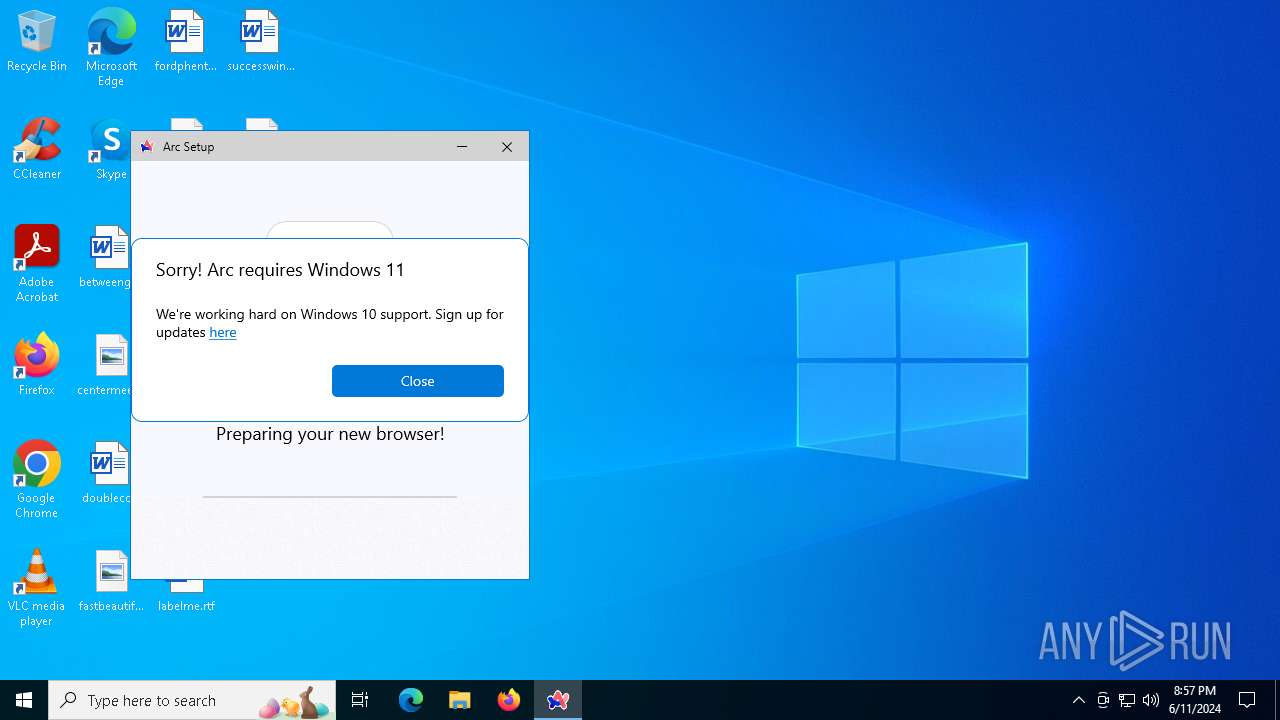
| File name: | ArcInstaller.exe |
| Full analysis: | https://app.any.run/tasks/6b66f11f-65b8-4eaa-84c7-025f06e55fc7 |
| Verdict: | Malicious activity |
| Analysis date: | June 11, 2024, 20:56:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | F4681C38E0505E3CF383726C470AB363 |
| SHA1: | FD52AD8363DF705DB584539BE945CE7CC01BB77B |
| SHA256: | 7B3B581BEA2602573F1F54D01FE1C09191354B23B416FFAB5C95F0B0FB02ACC9 |
| SSDEEP: | 98304:noGkx59Dm1DoGkQ59b1Lfhhn8EGJYGRxJ0MTTIGmcctOw6bmkH01bL6fNqzMlixf:cEf |
MALICIOUS
Drops the executable file immediately after the start
- ArcInstaller.exe (PID: 3692)
SUSPICIOUS
Reads security settings of Internet Explorer
- ArcInstaller.exe (PID: 3692)
Checks Windows Trust Settings
- ArcInstaller.exe (PID: 3692)
INFO
Reads the computer name
- ArcInstaller.exe (PID: 3692)
Checks supported languages
- ArcInstaller.exe (PID: 3692)
Disables trace logs
- ArcInstaller.exe (PID: 3692)
Creates files in the program directory
- ArcInstaller.exe (PID: 3692)
Create files in a temporary directory
- ArcInstaller.exe (PID: 3692)
Reads the machine GUID from the registry
- ArcInstaller.exe (PID: 3692)
Reads Environment values
- ArcInstaller.exe (PID: 3692)
Creates files or folders in the user directory
- ArcInstaller.exe (PID: 3692)
Checks proxy server information
- ArcInstaller.exe (PID: 3692)
Reads the software policy settings
- ArcInstaller.exe (PID: 3692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (49.4) |
|---|---|---|
| .scr | | | Windows screen saver (23.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (11.7) |
| .exe | | | Win32 Executable (generic) (8) |
| .exe | | | Generic Win/DOS Executable (3.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2071:10:14 23:00:44+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 1907200 |
| InitializedDataSize: | 45056 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d38ee |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.0.0 |
| ProductVersionNumber: | 1.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | ArcInstaller |
| FileDescription: | ArcInstaller |
| FileVersion: | 1.1.0.0 |
| InternalName: | ArcInstaller.exe |
| LegalCopyright: | |
| OriginalFileName: | ArcInstaller.exe |
| ProductName: | ArcInstaller |
| ProductVersion: | 1.1.0+1d4f050a1f1f60533e0d8fd2f0348a7d1d62f194 |
| AssemblyVersion: | 1.1.0.0 |
Total processes
115
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3692 | "C:\Users\admin\Desktop\ArcInstaller.exe" | C:\Users\admin\Desktop\ArcInstaller.exe | explorer.exe | ||||||||||||
User: admin Company: ArcInstaller Integrity Level: MEDIUM Description: ArcInstaller Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
Total events
6 964
Read events
6 948
Write events
16
Delete events
0
Modification events
| (PID) Process: | (3692) ArcInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ArcInstaller_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3692) ArcInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ArcInstaller_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3692) ArcInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ArcInstaller_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3692) ArcInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ArcInstaller_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3692) ArcInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ArcInstaller_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3692) ArcInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ArcInstaller_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3692) ArcInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ArcInstaller_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3692) ArcInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ArcInstaller_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3692) ArcInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ArcInstaller_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3692) ArcInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\ArcInstaller_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
0
Suspicious files
9
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3692 | ArcInstaller.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\357F04AD41BCF5FE18FCB69F60C6680F_FBCEF2048DFCB4EE55D00BA204530C64 | binary | |
MD5:A15376BFED1A9693FF188C4DF47C5324 | SHA256:5A7977B39E2FE9934CF8D618013A3BA7F389EB68987A3C1E17250FAF2A325A16 | |||
| 3692 | ArcInstaller.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:812DB4AC73A0836BC3CDF59ADDC0764B | SHA256:0361BECADD341E93A7DAFB09D5101D37E67C19853273801E63F286CA5FAE838F | |||
| 3692 | ArcInstaller.exe | C:\Users\admin\AppData\Local\IsolatedStorage\t555h3ls.kli\f1vleokl.zau\Publisher.qkouhz2ds2gk0w5435bumkcrozad3zua\Publisher.qkouhz2ds2gk0w5435bumkcrozad3zua\Files\LaunchDarkly\anonUser | text | |
MD5:AF21E4AD80CA832B266ED91216C6C2EC | SHA256:EF60FC417199075D0392522E8D91E6BA935B68C5D581361DC0F4B48C86E8CF9F | |||
| 3692 | ArcInstaller.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BD92F95DED26541D3AF7F44DC7914843 | binary | |
MD5:DEF09A82B5577ABCC05E0B6F1F1E70C7 | SHA256:A6198CEBF50266F7A498A1231B7A44B2D7FE97C5A20B04F6EA608ABD423A451F | |||
| 3692 | ArcInstaller.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:4CC3211B48D5A3C1579EE8039D222202 | SHA256:4F510AB99B92A1454F3DFD1A8963DD74C8A5F29380DBBB295F5F9876F8D5EBF2 | |||
| 3692 | ArcInstaller.exe | C:\Users\admin\AppData\Local\IsolatedStorage\t555h3ls.kli\f1vleokl.zau\Publisher.qkouhz2ds2gk0w5435bumkcrozad3zua\identity.dat | binary | |
MD5:A9687A21CDFE5A1EB84D2CFA4DDB7874 | SHA256:A149FC62021D8DB2ACD3A1AB3F9486898D59EF2C21C950C8E52D98164E172E74 | |||
| 3692 | ArcInstaller.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BD92F95DED26541D3AF7F44DC7914843 | binary | |
MD5:A91FE5C2AAB79E27C1C440831593ED25 | SHA256:7D77ABD0EAB3D1FE54103F2DB08CA114AE346E06799E49CD922906DB0B34B85E | |||
| 3692 | ArcInstaller.exe | C:\Users\admin\AppData\Local\IsolatedStorage\t555h3ls.kli\f1vleokl.zau\Publisher.qkouhz2ds2gk0w5435bumkcrozad3zua\Publisher.qkouhz2ds2gk0w5435bumkcrozad3zua\identity.dat | binary | |
MD5:A9687A21CDFE5A1EB84D2CFA4DDB7874 | SHA256:A149FC62021D8DB2ACD3A1AB3F9486898D59EF2C21C950C8E52D98164E172E74 | |||
| 3692 | ArcInstaller.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\357F04AD41BCF5FE18FCB69F60C6680F_FBCEF2048DFCB4EE55D00BA204530C64 | binary | |
MD5:B7533FB62DA20F9857A114EC5FD9B04A | SHA256:24F882A787C0E069E978980698957D5CD75886DA74D5B42CA736EA3A2D8C49A7 | |||
| 3692 | ArcInstaller.exe | C:\Users\admin\AppData\Local\Sentry\7F91F275957D28EEE48F184E0B2D9ABD48A5EFF3\.installation | text | |
MD5:2A90D0522E47D2D6486E0B098679DF20 | SHA256:5AE8576C99F14C7E366012F712D17C57ADE6CD42B7CD0860B8DD2DD7138D7FF4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
27
DNS requests
9
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5076 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
5076 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
3692 | ArcInstaller.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | unknown |
— | — | POST | — | 52.201.12.96:443 | https://mobile.launchdarkly.com/mobile/events/diagnostic | unknown | — | — | unknown |
— | — | POST | 202 | 52.201.12.96:443 | https://mobile.launchdarkly.com/mobile/events/bulk | unknown | — | — | unknown |
— | — | POST | 200 | 34.120.195.249:443 | https://o298668.ingest.us.sentry.io/api/4507114371284992/envelope/ | unknown | — | 41 b | unknown |
— | — | POST | — | 54.175.64.186:443 | https://mobile.launchdarkly.com/mobile/events/diagnostic | unknown | — | — | unknown |
— | — | POST | 200 | 34.120.195.249:443 | https://o298668.ingest.us.sentry.io/api/4507114371284992/envelope/ | unknown | binary | 2 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5076 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5140 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5076 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5140 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
5140 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5076 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3692 | ArcInstaller.exe | 34.120.195.249:443 | o298668.ingest.us.sentry.io | GOOGLE-CLOUD-PLATFORM | US | unknown |
3692 | ArcInstaller.exe | 104.18.20.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
o298668.ingest.us.sentry.io |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
crl.globalsign.com |
| unknown |
mobile.launchdarkly.com |
| unknown |
clientstream.launchdarkly.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET HUNTING Suspicious POST With Reference to WINDOWS Folder Possible Malware Infection |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |