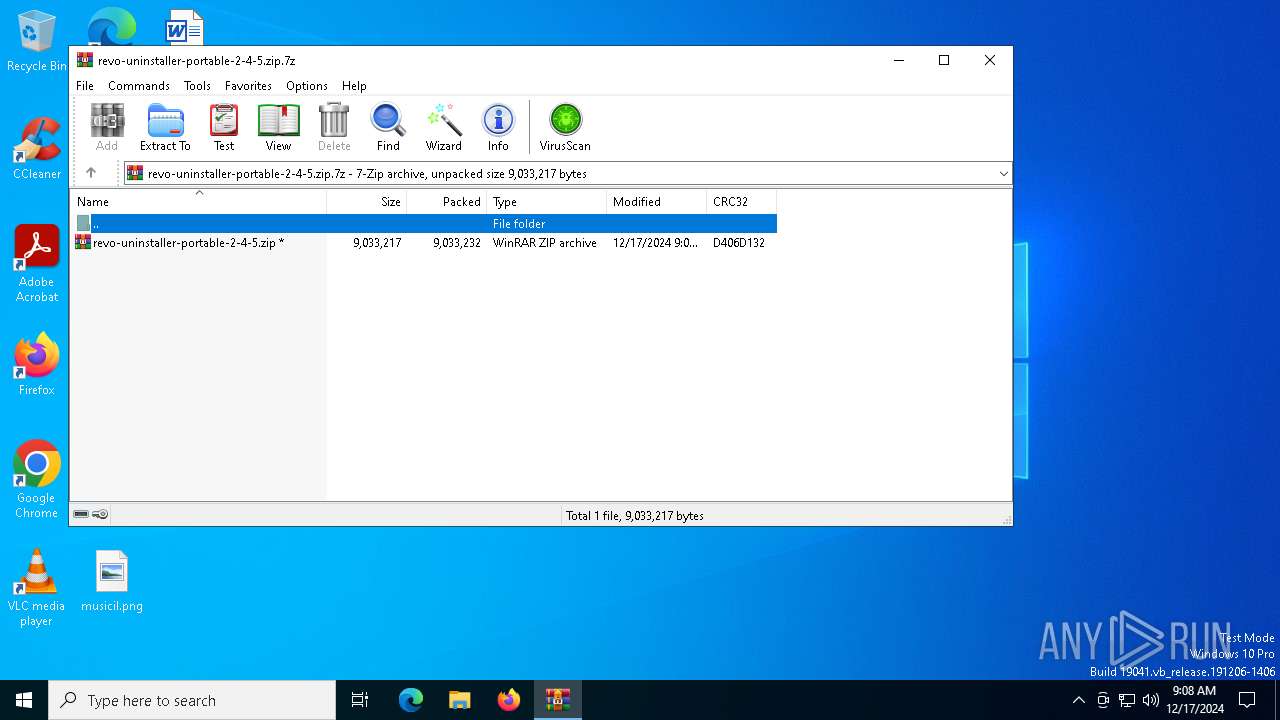
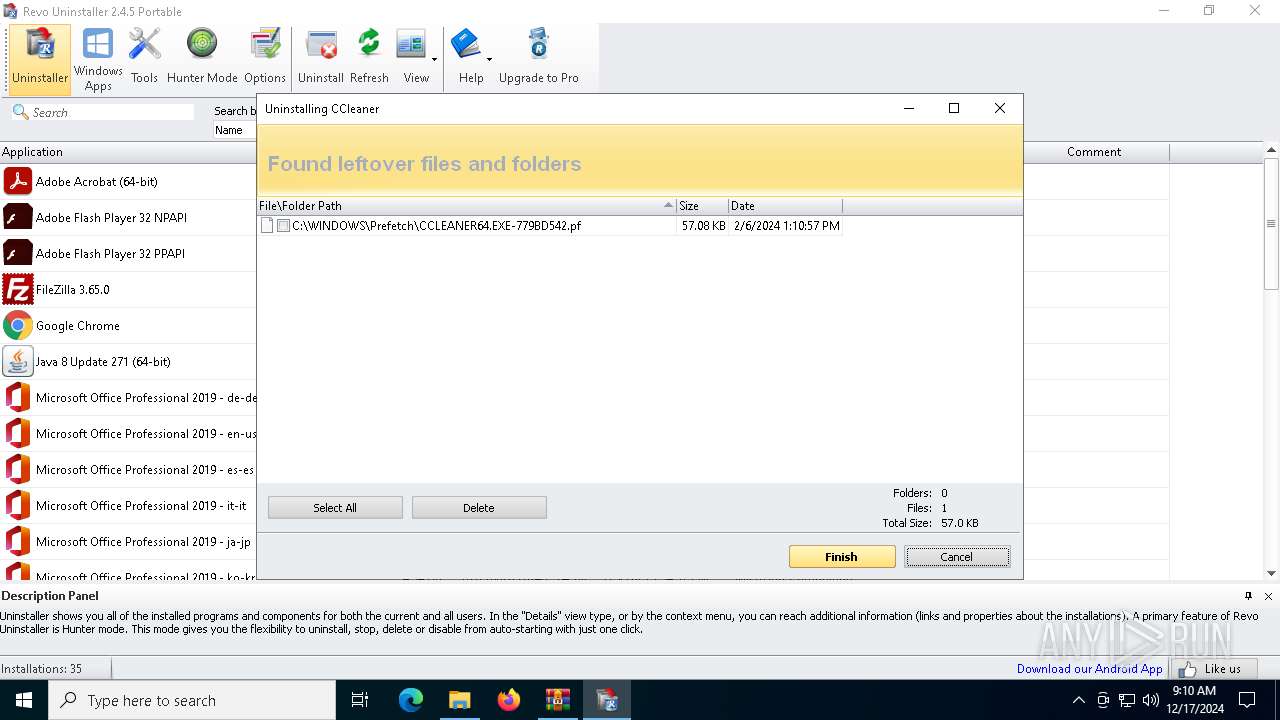
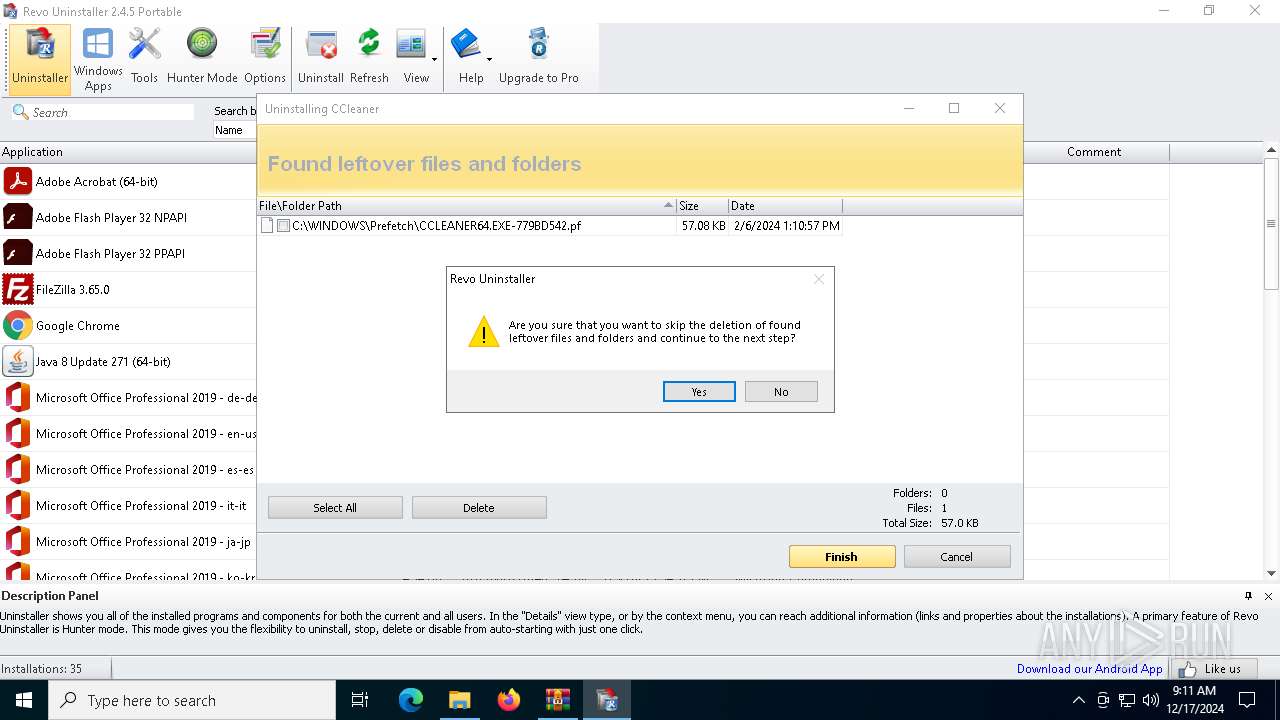
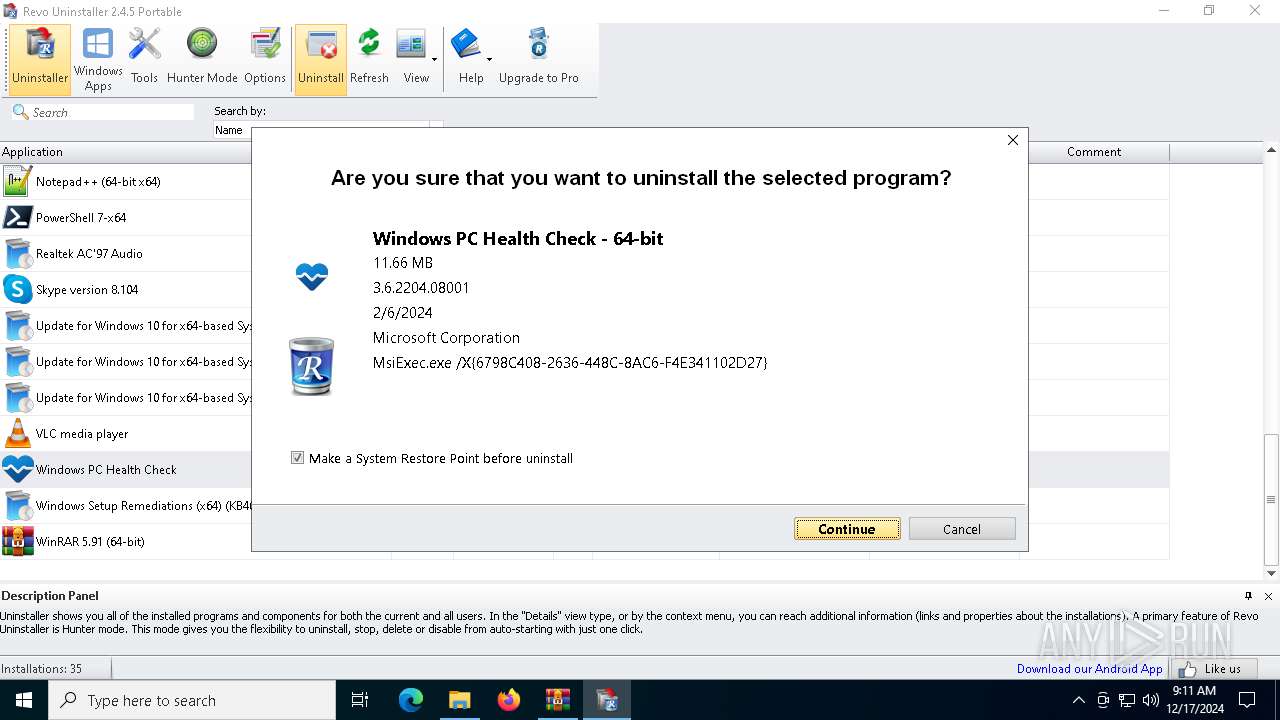
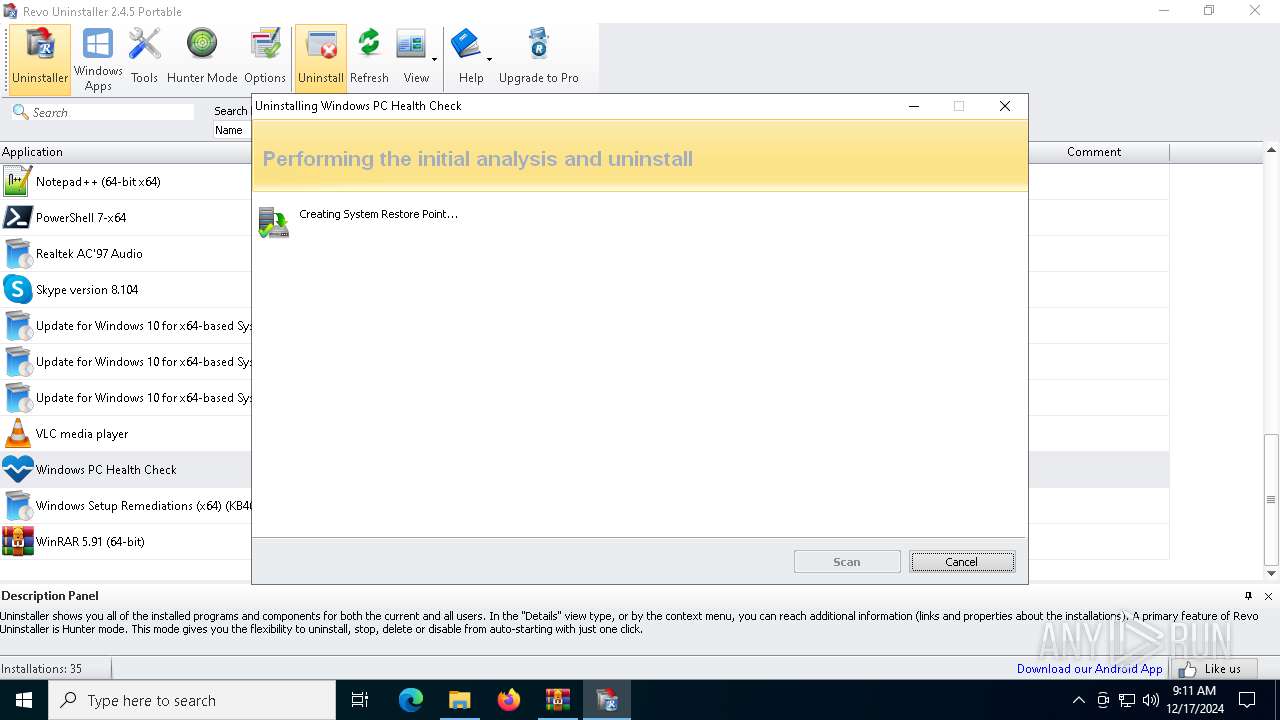
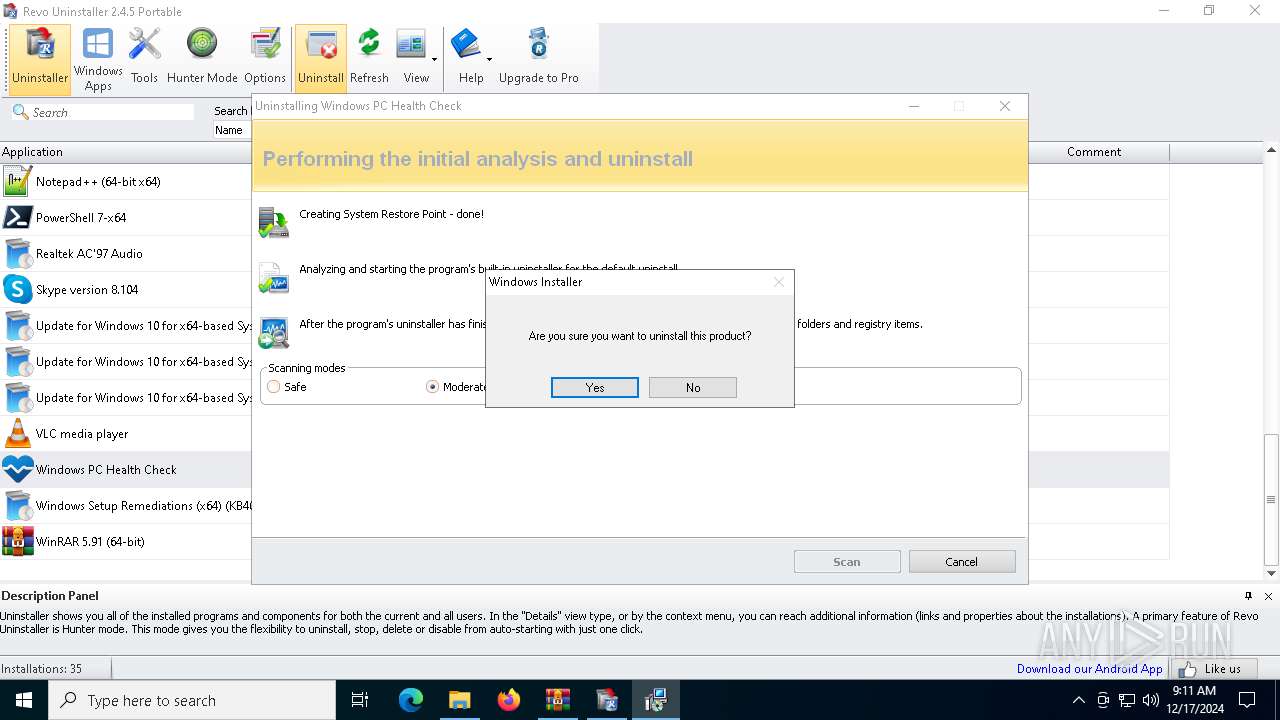
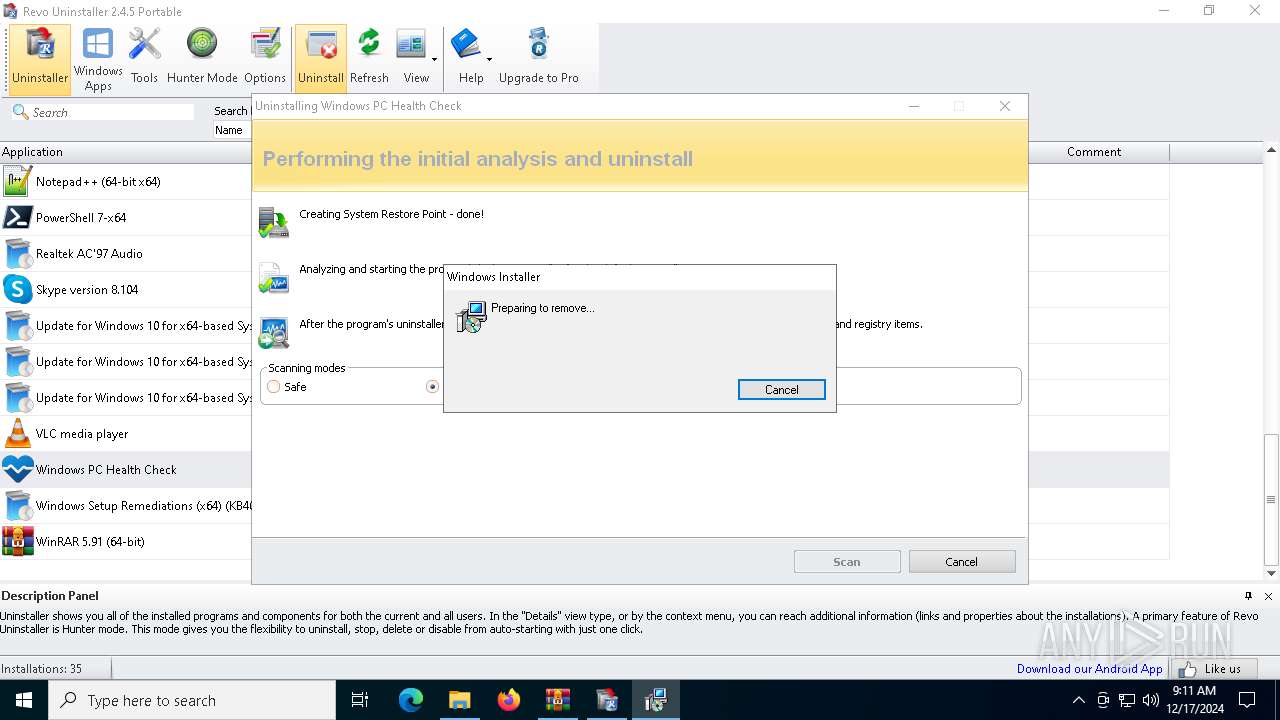
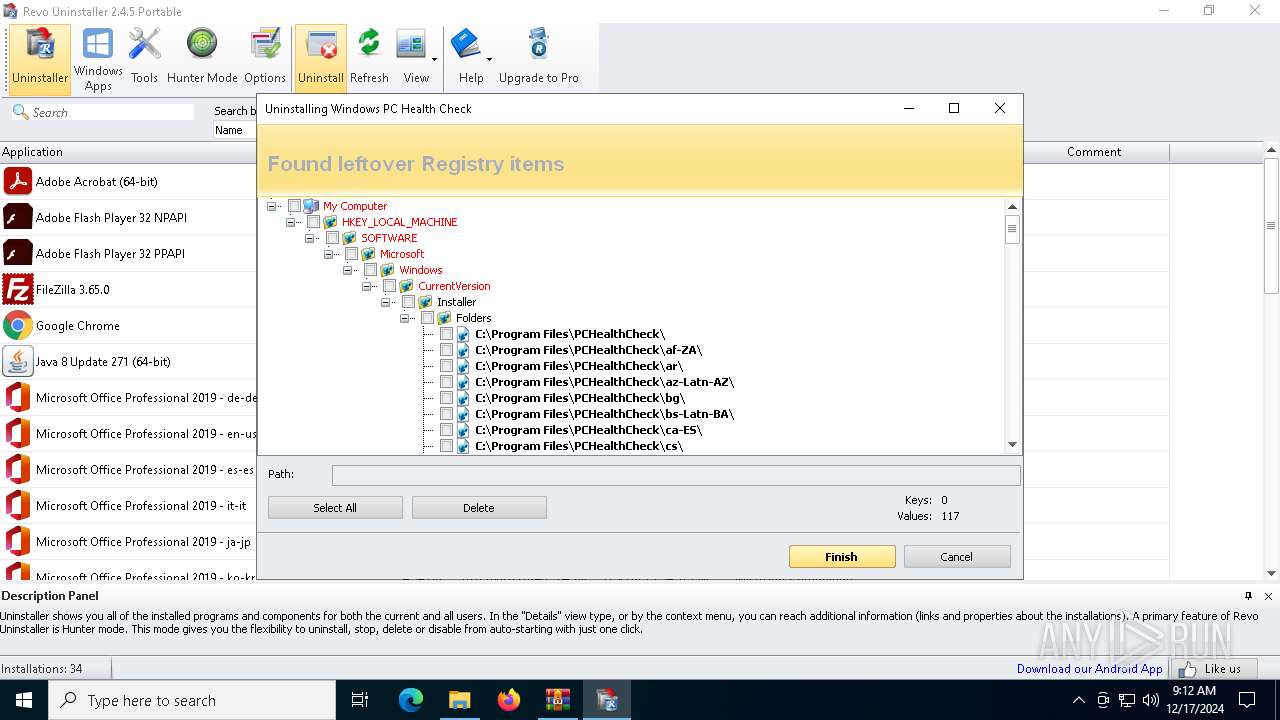
| File name: | revo-uninstaller-portable-2-4-5.zip.7z |
| Full analysis: | https://app.any.run/tasks/573fd1a0-7431-4dba-a3d5-c00462328d17 |
| Verdict: | Malicious activity |
| Analysis date: | December 17, 2024, 09:07:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | C55DA5DB0955205756F8ABCC03EBE37A |
| SHA1: | D1C71D4EA00EFC9F433B2DD3B8ACAFF950B4D9C9 |
| SHA256: | 7B0A43859BBB5433EBE80C28B99E736508425E9913C8CD43F0943BC53E6ABC2D |
| SSDEEP: | 98304:yZFM7/+pfB48aWhVWC1VA0zhDfHBmBB/mF4gPFEyv9QKHWwlvF97aHGeFYxI4e5U:wIGEdRmofi+Xi |
MALICIOUS
Executing a file with an untrusted certificate
- RevoUn.exe (PID: 4556)
- RevoUn.exe (PID: 3832)
- RevoUn.exe (PID: 5544)
SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6236)
Reads security settings of Internet Explorer
- RevoUn.exe (PID: 4556)
- RevoUn.exe (PID: 3832)
- Un_A.exe (PID: 7000)
Searches for installed software
- RevoUn.exe (PID: 3832)
- dllhost.exe (PID: 6532)
- Un_A.exe (PID: 7000)
- dllhost.exe (PID: 2728)
- RevoUn.exe (PID: 4556)
Executes as Windows Service
- VSSVC.exe (PID: 6516)
Executable content was dropped or overwritten
- uninst.exe (PID: 7124)
- Un_A.exe (PID: 7000)
Starts itself from another location
- uninst.exe (PID: 7124)
Malware-specific behavior (creating "System.dll" in Temp)
- Un_A.exe (PID: 7000)
Checks Windows Trust Settings
- Un_A.exe (PID: 7000)
Starts CMD.EXE for commands execution
- Un_A.exe (PID: 7000)
- cmd.exe (PID: 4128)
Application launched itself
- cmd.exe (PID: 4128)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6656)
Lists all scheduled tasks in specific format
- schtasks.exe (PID: 6796)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 396)
- schtasks.exe (PID: 4164)
- schtasks.exe (PID: 4816)
Process drops legitimate windows executable
- msiexec.exe (PID: 3828)
Reads the date of Windows installation
- msiexec.exe (PID: 3828)
INFO
Manual execution by a user
- WinRAR.exe (PID: 6968)
- WinRAR.exe (PID: 7160)
- RevoUPort.exe (PID: 5872)
- RevoUPort.exe (PID: 3076)
- RevoUn.exe (PID: 5544)
- RevoUn.exe (PID: 3832)
The process uses the downloaded file
- WinRAR.exe (PID: 6236)
- WinRAR.exe (PID: 7160)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7160)
- msiexec.exe (PID: 3828)
Checks supported languages
- RevoUPort.exe (PID: 3076)
- RevoUn.exe (PID: 4556)
- uninst.exe (PID: 7124)
- Un_A.exe (PID: 7000)
- CCUpdate.exe (PID: 1752)
- msiexec.exe (PID: 3828)
- msiexec.exe (PID: 6604)
- RevoUn.exe (PID: 3832)
Reads the computer name
- RevoUn.exe (PID: 4556)
- Un_A.exe (PID: 7000)
- CCUpdate.exe (PID: 1752)
- msiexec.exe (PID: 3828)
- msiexec.exe (PID: 6604)
Process checks computer location settings
- RevoUn.exe (PID: 4556)
Manages system restore points
- SrTasks.exe (PID: 5076)
- SrTasks.exe (PID: 2456)
- SrTasks.exe (PID: 6508)
Create files in a temporary directory
- uninst.exe (PID: 7124)
- Un_A.exe (PID: 7000)
The sample compiled with english language support
- uninst.exe (PID: 7124)
- Un_A.exe (PID: 7000)
- msiexec.exe (PID: 3828)
Reads Environment values
- Un_A.exe (PID: 7000)
- msiexec.exe (PID: 3828)
Checks proxy server information
- Un_A.exe (PID: 7000)
Reads the software policy settings
- Un_A.exe (PID: 7000)
Reads the machine GUID from the registry
- Un_A.exe (PID: 7000)
Application launched itself
- msiexec.exe (PID: 3828)
Write to the desktop.ini file (may be used to cloak folders)
- msiexec.exe (PID: 3828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2024:12:17 09:06:29+00:00 |
| ArchivedFileName: | revo-uninstaller-portable-2-4-5.zip |
Total processes
163
Monitored processes
34
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | C:\WINDOWS\system32\schtasks /delete /tn "CCleanerSkipUAC - admin" /f | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 880 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1752 | "C:\Program Files\CCleaner\ccupdate.exe" /unreg | C:\Program Files\CCleaner\CCUpdate.exe | — | Un_A.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner CCleaner emergency updater Exit code: 0 Version: 23.3.12.0 Modules
| |||||||||||||||
| 2148 | findstr /i CCleanerSkipUAC | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:14 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 2147942487 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2728 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3076 | "C:\Users\admin\Desktop\RevoUninstaller_Portable\RevoUPort.exe" | C:\Users\admin\Desktop\RevoUninstaller_Portable\RevoUPort.exe | explorer.exe | ||||||||||||
User: admin Company: VS Revo Group Integrity Level: HIGH Exit code: 0 Version: 2, 0, 0, 0 Modules
| |||||||||||||||
| 3828 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3832 | "C:\Users\admin\Desktop\RevoUninstaller_Portable\x64\RevoUn.exe" | C:\Users\admin\Desktop\RevoUninstaller_Portable\x64\RevoUn.exe | explorer.exe | ||||||||||||
User: admin Company: VS Revo Group Integrity Level: HIGH Description: Revo Uninstaller Version: 2.4.5.0 Modules
| |||||||||||||||
Total events
35 631
Read events
34 266
Write events
633
Delete events
732
Modification events
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\revo-uninstaller-portable-2-4-5.zip.7z | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (6236) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
Executable files
15
Suspicious files
28
Text files
52
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7160 | WinRAR.exe | C:\Users\admin\Desktop\RevoUninstaller_Portable\lang\french.ini | text | |
MD5:267BCE0C687901EF0C9B94853164FF22 | SHA256:F7B544068FCFE69F5A718A9EE0B790620F85477AFBF0C5DB5215A318C67E3B7F | |||
| 7160 | WinRAR.exe | C:\Users\admin\Desktop\RevoUninstaller_Portable\lang\hellenic.ini | text | |
MD5:2750A46C066CE37250BE338D2D4B2C28 | SHA256:1FBFEE3E9FB3D7E4BAC9AB89C49B25B1D93D65389A1DB3D9276C0B8C1A9C363B | |||
| 7160 | WinRAR.exe | C:\Users\admin\Desktop\RevoUninstaller_Portable\lang\dutch.ini | text | |
MD5:484AAB4E4A291B4C2F2D1718B3754D2B | SHA256:7A47C9E44EF1E4CE0D5FC678DDF505D8213995E55599D7F4779E10462C002880 | |||
| 7160 | WinRAR.exe | C:\Users\admin\Desktop\RevoUninstaller_Portable\lang\german.ini | text | |
MD5:00155578B98E07FC6288870E2AECCA68 | SHA256:8CEF19D9D89BE0528643C45647085A85B136DF74987F7D25483732D431C70D12 | |||
| 7160 | WinRAR.exe | C:\Users\admin\Desktop\RevoUninstaller_Portable\lang\bulgarian.ini | text | |
MD5:29C6FA77CAFF22CEBEF89FE7CBB7E564 | SHA256:8AD919E2DF77256C9DE97E5AB3BCB62669517360051E1F8C3444D2BDCDC9E824 | |||
| 7160 | WinRAR.exe | C:\Users\admin\Desktop\RevoUninstaller_Portable\lang\Estonian.ini | text | |
MD5:FB4844267D83DE0565C5AB8D8475605F | SHA256:1899006AAB38B129BAC93E3935BEF214ACCC31D7FBE08FEE733E7A89EEEF9E08 | |||
| 7160 | WinRAR.exe | C:\Users\admin\Desktop\RevoUninstaller_Portable\lang\azerbaijani.ini | text | |
MD5:2952EBFB627A4E0ECA6AE36179FB77E8 | SHA256:104F10070994CA92176913A71726590DF2487BA756512CE6B3ABAA50CED8679B | |||
| 7160 | WinRAR.exe | C:\Users\admin\Desktop\RevoUninstaller_Portable\lang\finnish.ini | text | |
MD5:A3D974340201C1D00AF3A87F4D3DA6DC | SHA256:FEDCC719AC22D45A77F117372E0E124AA0EDE73DFC0768E7CDF7420539140731 | |||
| 7160 | WinRAR.exe | C:\Users\admin\Desktop\RevoUninstaller_Portable\lang\danish.ini | text | |
MD5:B460A1121BDB6806E308212EB9F63F8F | SHA256:7A2F9651F01898D76E4B0AD81272D12602162AAB0AF87EB7E0294ED345C1A6B2 | |||
| 7160 | WinRAR.exe | C:\Users\admin\Desktop\RevoUninstaller_Portable\lang\bengali.ini | text | |
MD5:966C8ECA86F43A502D9836709ED34D6E | SHA256:25205DBA08243AEEB6516221847738D47F3C72C295F7D973E09433E2635C943D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
43
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2356 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7012 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7012 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7000 | Un_A.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1380 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.163:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |