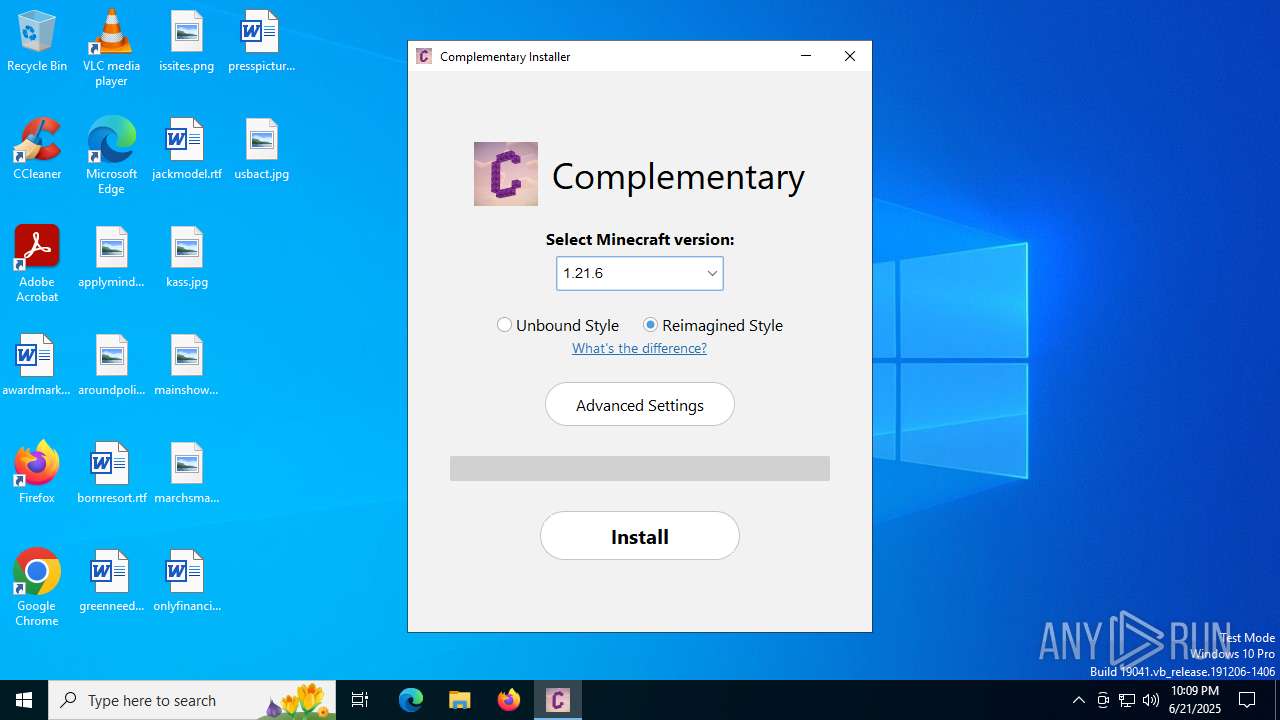
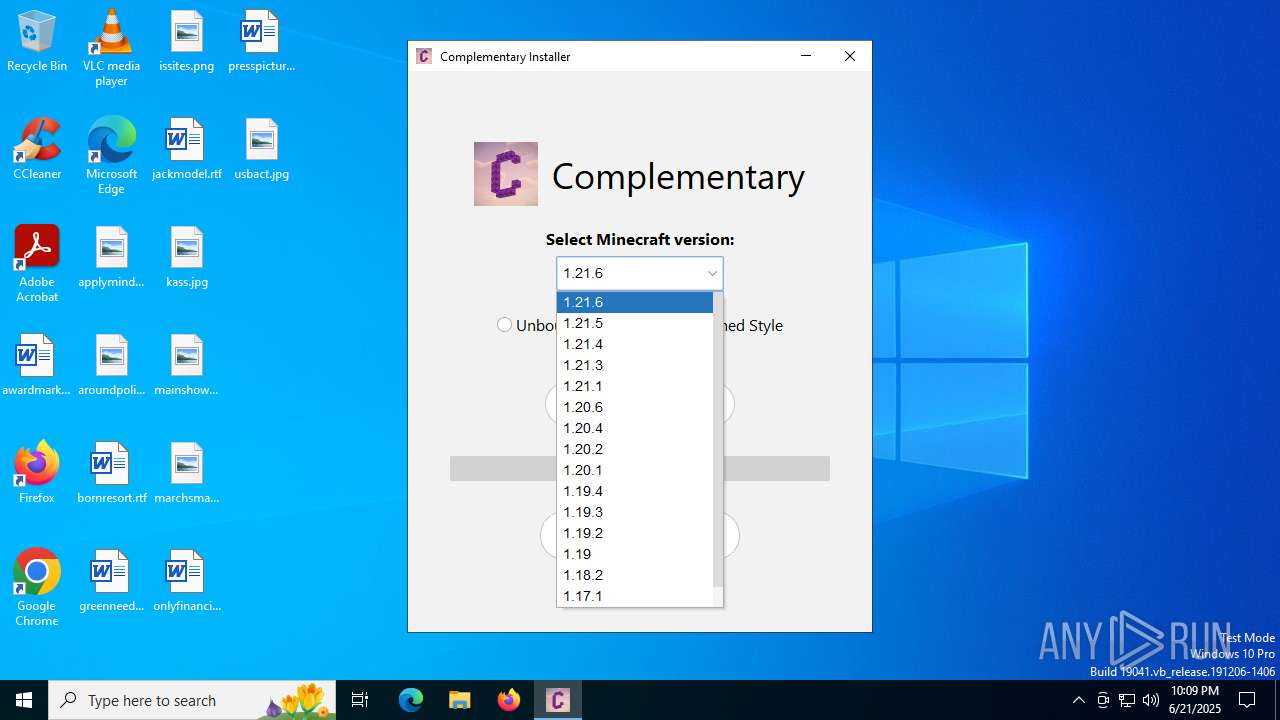
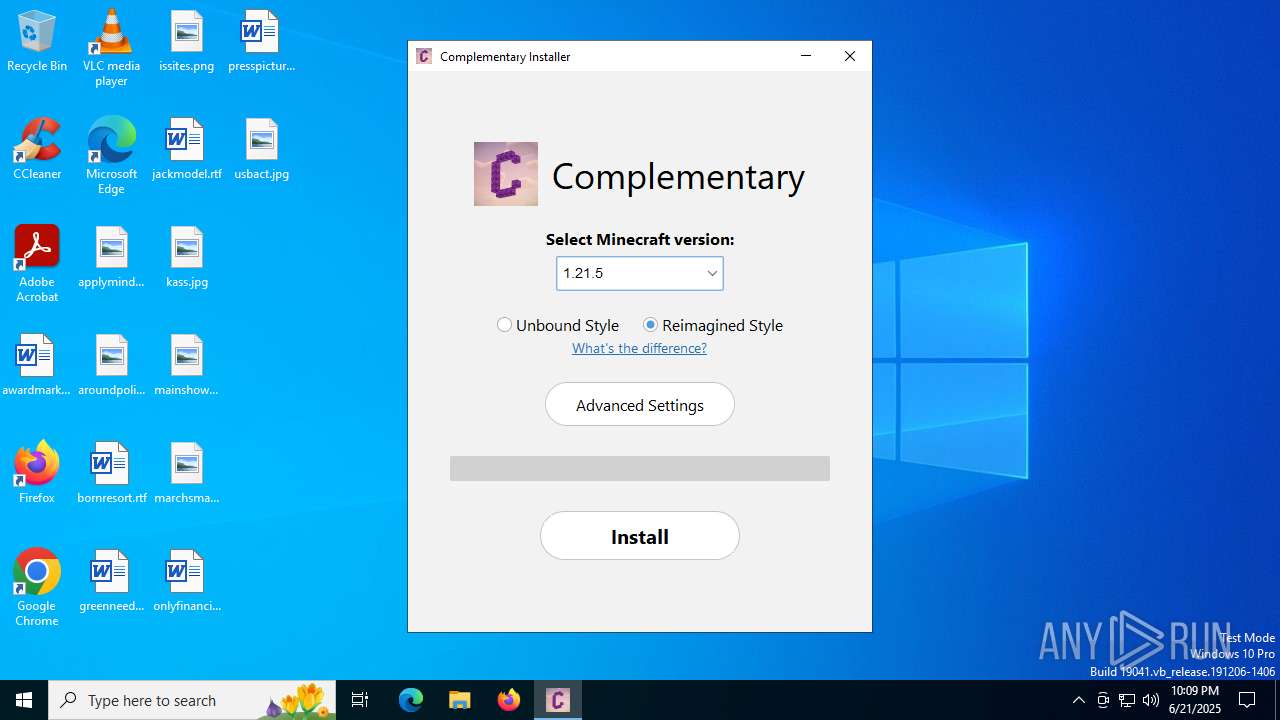
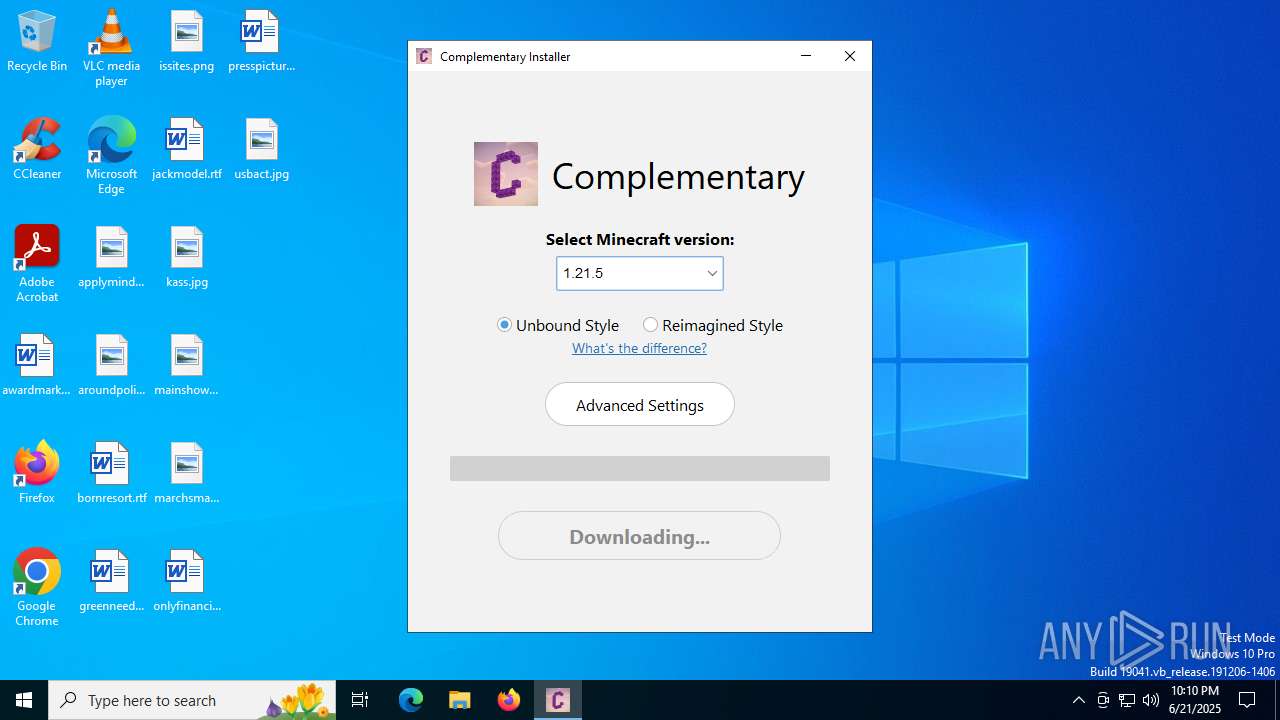
| File name: | Complementary-Installer-1.3.0.exe |
| Full analysis: | https://app.any.run/tasks/0d4eb65f-295e-4490-8f68-188e5353aa7b |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 22:09:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive, with extra data prepended |
| MD5: | 388A6476CD39BACB17C1894975E57B5A |
| SHA1: | 7C1E1CE0576D7A063E927C890E7338EDF73C868B |
| SHA256: | 7B0080B7A64B7220E0EB25DC5709C70CE38D7001F443BE103F951D9EF2E9EEC4 |
| SSDEEP: | 49152:OYnkpm5YlGQMSWWS19kfygviEDRNGA1WB9+MlrSC9o9SICJNAMofGRVWrmrbl/iv:Bkpm5YlH8kaMrNGaU+8rS8aSICJuFfG+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks for Java to be installed
- javaw.exe (PID: 5884)
- javaw.exe (PID: 6336)
Executable content was dropped or overwritten
- javaw.exe (PID: 6336)
There is functionality for taking screenshot (YARA)
- javaw.exe (PID: 6336)
INFO
The sample compiled with english language support
- Complementary-Installer-1.3.0.exe (PID: 1604)
Checks supported languages
- Complementary-Installer-1.3.0.exe (PID: 1604)
- javaw.exe (PID: 5884)
- javaw.exe (PID: 6336)
Create files in a temporary directory
- Complementary-Installer-1.3.0.exe (PID: 1604)
- javaw.exe (PID: 5884)
- javaw.exe (PID: 6336)
Creates files in the program directory
- javaw.exe (PID: 5884)
Reads the computer name
- javaw.exe (PID: 6336)
Reads the machine GUID from the registry
- javaw.exe (PID: 6336)
Creates files or folders in the user directory
- javaw.exe (PID: 6336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:12:30 15:00:19+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.37 |
| CodeSize: | 172544 |
| InitializedDataSize: | 91648 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xe260 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| CompanyName: | Fabric Team |
| FileDescription: | Fabric Installer |
| FileVersion: | 1.0.0.1 |
| InternalName: | fabric-i.exe |
| LegalCopyright: | Copyright (C) 2022 |
| OriginalFileName: | fabric-installer-native-bootstrap.exe |
| ProductName: | Fabric Installer |
| ProductVersion: | 1.0.0.1 |
Total processes
142
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1136 | reg query "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Themes\Personalize" /v AppsUseLightTheme | C:\Windows\System32\reg.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1604 | "C:\Users\admin\AppData\Local\Temp\Complementary-Installer-1.3.0.exe" | C:\Users\admin\AppData\Local\Temp\Complementary-Installer-1.3.0.exe | — | explorer.exe | |||||||||||
User: admin Company: Fabric Team Integrity Level: MEDIUM Description: Fabric Installer Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 3092 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3924 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5884 | "javaw.exe" "-version" | C:\Program Files (x86)\Common Files\Oracle\Java\javapath_target_2989500\javaw.exe | — | Complementary-Installer-1.3.0.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 6336 | "javaw.exe" "-jar" "C:\Users\admin\AppData\Local\Temp\Complementary-Installer-1.3.0.exe" "-fabricInstallerBootstrap" "true" | C:\Program Files (x86)\Common Files\Oracle\Java\javapath_target_2989500\javaw.exe | Complementary-Installer-1.3.0.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 6360 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7000 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 107
Read events
1 107
Write events
0
Delete events
0
Modification events
Executable files
3
Suspicious files
4
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6336 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\shaderpacks\aaaConfirmUnboundDownload.txt | text | |
MD5:9891BB18576B6508453D2D0704F0D51C | SHA256:7B1E36E4A8F64933E3F69594B76ECEBAFAD6F05DC3A882A8F0FC8CC6F5D587A5 | |||
| 5884 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:00D1878DEC934C5FDA9B37C7BA64C26D | SHA256:2F1D994E6FB9DFBED407749CCDFD4C65A10A852DFAFE388A6216DB5291500E76 | |||
| 6336 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\versions\iris-fabric-loader-0.16.14-1.21.5\iris-fabric-loader-0.16.14-1.21.5.json | binary | |
MD5:DE935C0EE172FD3497FD9EB79E393759 | SHA256:DE462A6FF0EC44E8EBFCE077B89450B8F5445CE07462A89C9DE8E3815136A9F9 | |||
| 6336 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\iris-reserved\1.21.5\iris-fabric-1.8.11+mc1.21.5.jar | java | |
MD5:C08A1725CF3AE49482431E9F67054769 | SHA256:E961C1FC63493B56EDAEA7A4934B8F8B13A913CD95437927EA18EC1E870EF93F | |||
| 6336 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\iris-reserved\1.21.5\sodium-fabric-0.6.12+mc1.21.5.jar | java | |
MD5:8FB8E80FB7330FB85480AF9A6252E8CB | SHA256:A4A93781D90506A96B677A21B6523571314417B641AC13890C7475378D570780 | |||
| 6336 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\config\iris.properties | text | |
MD5:3AAE7140A42569881E29A51B439587A1 | SHA256:A4A953F7AD04B00C65A128AAD3316BAD7F2EB730E86E8A6835AEEF0EFB16475E | |||
| 6336 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\config\installedByCompInstaller.txt | text | |
MD5:EC66A5E65385562CEC9E10355880897B | SHA256:AFB0F434E296604490AFDF74BC83C5C603D7E791A6D66EFFBABEFF306316940E | |||
| 1604 | Complementary-Installer-1.3.0.exe | C:\Users\admin\AppData\Local\Temp\fabric-installer-1750543788.log | text | |
MD5:78FBC175AB34B954E7CE5632095940BB | SHA256:3D1B8A5204BB5BC8B5809DA7A6A4CE5906BB63BB85AC266673799B1C4E21BDFA | |||
| 6336 | javaw.exe | C:\Users\admin\AppData\Local\Temp\flatlaf.temp\flatlaf-windows-x86_64-15321966699670.dll | executable | |
MD5:B0366E31F3704DA1E9552633A07F77DB | SHA256:18F1F5AFEC89F152AFE1C57CFFE9A77C158D840F6E00EC7A343B685CAA3D8853 | |||
| 6336 | javaw.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1693682860-607145093-2874071422-1001\83aa4cc77f591dfc2374580bbd95f6ba_bb926e54-e3ca-40fd-ae90-2764341e7792 | binary | |
MD5:C8366AE350E7019AEFC9D1E6E6A498C6 | SHA256:11E6ACA8E682C046C83B721EEB5C72C5EF03CB5936C60DF6F4993511DDC61238 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
31
DNS requests
21
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.30:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5924 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4232 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4232 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6876 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6336 | javaw.exe | 188.114.97.3:443 | meta.fabricmc.net | CLOUDFLARENET | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6336 | javaw.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 184.24.77.30:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
meta.fabricmc.net |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
github.com |
| whitelisted |
objects.githubusercontent.com |
| whitelisted |
api.modrinth.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |