| File name: | UpdateAXGATE_VPN_Client.exe |
| Full analysis: | https://app.any.run/tasks/0dcde870-ecb3-4c72-81d0-38781e1eabc8 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | October 05, 2024, 10:26:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | A144210866B3DF7D8EF5A4A10DEFBBE5 |
| SHA1: | F9765345EA38CB7C953DD745B0F157AEB4D79A55 |
| SHA256: | 7AD32718D840C46BF294CF0A6EA03B80A6DA40C0FDD6FE5ADF6EA36DDFB67558 |
| SSDEEP: | 49152:uMECrOQhvlvgAjq6YxHD3gHzlEXDknVrY79Hlmjh6ZNCqdP7kxcNP81DzUMazGcT:uMRrFoAjpcjw0DuVW326PZ4V1DzUMaAM |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- UpdateAXGATE_VPN_Client.exe (PID: 3824)
Reads the date of Windows installation
- UpdateAXGATE_VPN_Client.exe (PID: 3824)
Uses REG/REGEDIT.EXE to modify registry
- UpdateAXGATE_VPN_Client.exe (PID: 3824)
Executable content was dropped or overwritten
- UpdateAXGATE_VPN_Client.exe (PID: 3824)
- UpdateAgent_http_210.178.134.254_7778.exe (PID: 5988)
- AXGATE_VPN_Client_Installer.exe (PID: 6852)
- AXGATE_VPN_Client_Installer.exe (PID: 2632)
- vcredist_x86_VC2013.exe (PID: 4404)
- HashDialog.exe (PID: 300)
- vcredist_x86_VC2013.exe (PID: 3448)
- AxgateVpnClient.exe (PID: 2640)
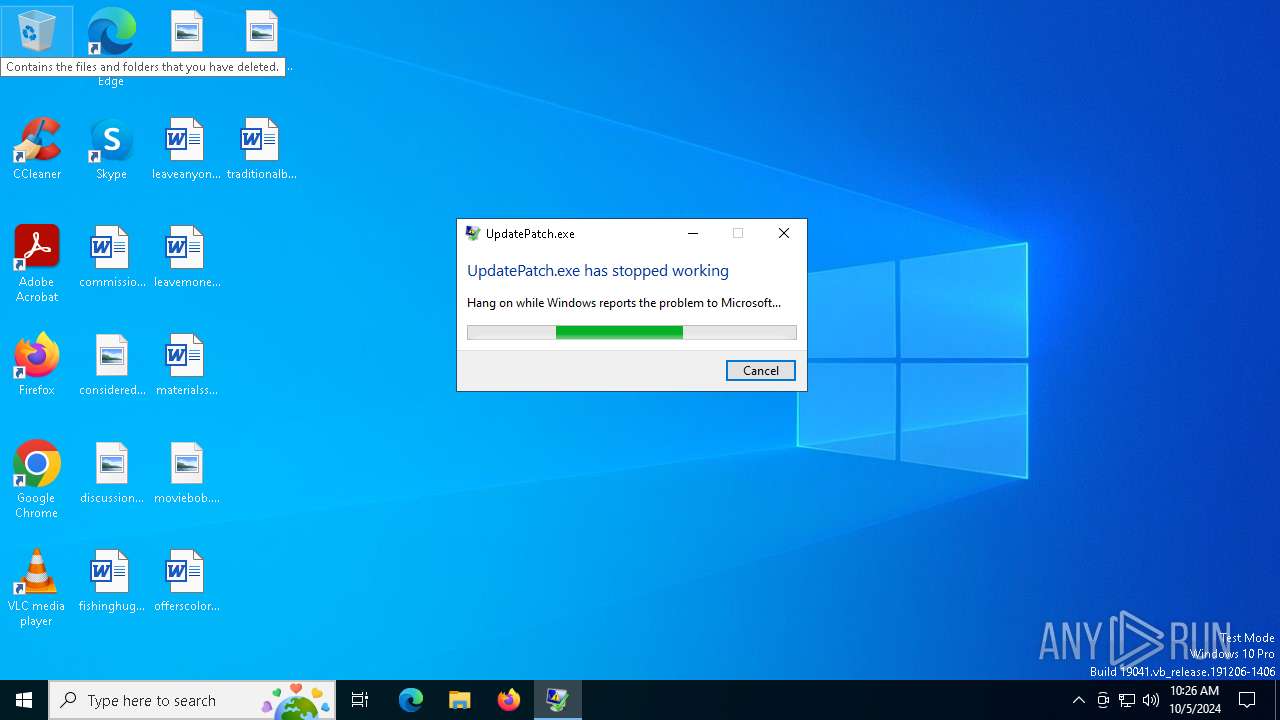
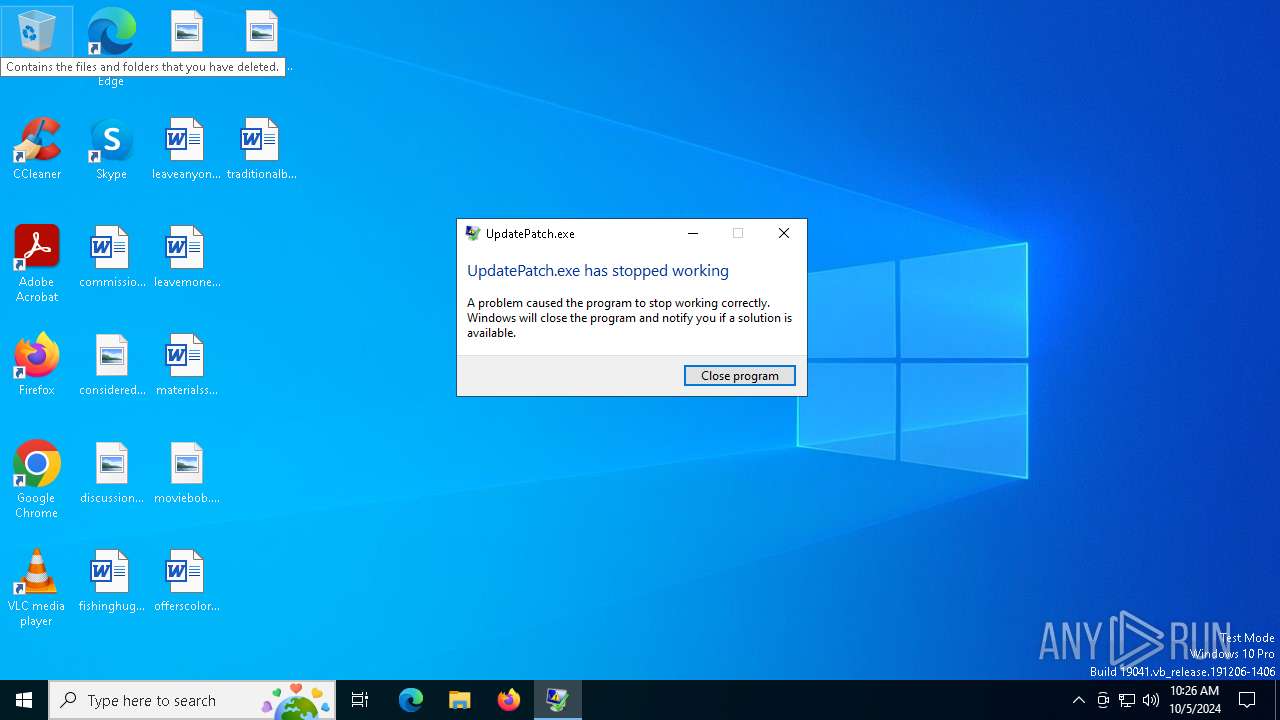
Executes application which crashes
- UpdatePatch.exe (PID: 5400)
Connects to unusual port
- UpdateAgent_http_210.178.134.254_7778.exe (PID: 5988)
Potential Corporate Privacy Violation
- UpdateAgent_http_210.178.134.254_7778.exe (PID: 5988)
Starts itself from another location
- AXGATE_VPN_Client_Installer.exe (PID: 6852)
Starts a Microsoft application from unusual location
- vcredist_x86_VC2013.exe (PID: 4404)
- vcredist_x86_VC2013.exe (PID: 3448)
Process drops legitimate windows executable
- msiexec.exe (PID: 1280)
- vcredist_x86_VC2013.exe (PID: 3448)
- vcredist_x86_VC2013.exe (PID: 4404)
- msiexec.exe (PID: 1232)
Application launched itself
- vcredist_x86_VC2013.exe (PID: 4404)
Executes as Windows Service
- VSSVC.exe (PID: 6716)
The process drops C-runtime libraries
- msiexec.exe (PID: 1232)
Starts CMD.EXE for commands execution
- AXGATE_VPN_Client_Installer.exe (PID: 2632)
- UpdateAgent_http_210.178.134.254_7778.exe (PID: 5988)
Drops a system driver (possible attempt to evade defenses)
- HashDialog.exe (PID: 300)
The process deletes folder without confirmation
- AXGATE_VPN_Client_Installer.exe (PID: 2632)
Executing commands from a ".bat" file
- UpdateAgent_http_210.178.134.254_7778.exe (PID: 5988)
INFO
Creates files in the program directory
- UpdateAXGATE_VPN_Client.exe (PID: 3824)
Reads the computer name
- UpdateAXGATE_VPN_Client.exe (PID: 3824)
Checks supported languages
- UpdateAXGATE_VPN_Client.exe (PID: 3824)
Process checks computer location settings
- UpdateAXGATE_VPN_Client.exe (PID: 3824)
The process uses the downloaded file
- UpdateAXGATE_VPN_Client.exe (PID: 3824)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1280)
- msiexec.exe (PID: 1232)
Manages system restore points
- SrTasks.exe (PID: 1144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:05:12 10:17:15+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.33 |
| CodeSize: | 236032 |
| InitializedDataSize: | 270848 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x266b0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
169
Monitored processes
38
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\Users\admin\AppData\Local\Temp\{D29019F5-2F41-41B6-9696-B6925C6445F1}\HashDialog.exe C:\ProgramData\AXGATE\AXGATE VPN Client\ | C:\Users\admin\AppData\Local\Temp\{D29019F5-2F41-41B6-9696-B6925C6445F1}\HashDialog.exe | AXGATE_VPN_Client_Installer.exe | ||||||||||||
User: admin Company: AXGATE Co., Ltd Integrity Level: HIGH Description: HashDialog Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
| 1144 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1232 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | C:\Windows\syswow64\MsiExec.exe -Embedding CBAF11CCC05B74A093E496C84729824E C | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | C:\Windows\syswow64\MsiExec.exe -Embedding C8713EA6FEF601FDB83E8AEDC8610FB0 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1972 | C:\Users\admin\AppData\Local\Temp\{D29019F5-2F41-41B6-9696-B6925C6445F1}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{C255C6DA-A839-403C-932C-A819603EDFC3} | C:\Users\admin\AppData\Local\Temp\{D29019F5-2F41-41B6-9696-B6925C6445F1}\ISBEW64.exe | — | AXGATE_VPN_Client_Installer.exe | |||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 28.0.759 Modules
| |||||||||||||||
| 2512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2632 | C:\Users\admin\AppData\Local\Temp\{03EC156F-C389-45C5-B020-AA4D95C9AA08}\AXGATE_VPN_Client_Installer.exe /q"C:\Users\admin\AppData\Roaming\AXGATE\AXGATE_VPN_Client_Installer.exe" /tempdisk1folder"C:\Users\admin\AppData\Local\Temp\{03EC156F-C389-45C5-B020-AA4D95C9AA08}" -S /IS_temp | C:\Users\admin\AppData\Local\Temp\{03EC156F-C389-45C5-B020-AA4D95C9AA08}\AXGATE_VPN_Client_Installer.exe | AXGATE_VPN_Client_Installer.exe | ||||||||||||
User: admin Company: AXGATE Integrity Level: HIGH Description: Setup Launcher Unicode Exit code: 0 Version: 1.4.0.43 Modules
| |||||||||||||||
| 2640 | "C:\ProgramData\AXGATE\AXGATE VPN Client\Bin\AxgateVpnClient.exe" | C:\ProgramData\AXGATE\AXGATE VPN Client\Bin\AxgateVpnClient.exe | UpdateAgent_http_210.178.134.254_7778.exe | ||||||||||||
User: admin Company: AXGATE Co., Ltd Integrity Level: HIGH Description: AXGATE VPN Client Version: 1, 4, 0, 43 Modules
| |||||||||||||||
Total events
21 087
Read events
20 135
Write events
859
Delete events
93
Modification events
| (PID) Process: | (5988) UpdateAgent_http_210.178.134.254_7778.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\AXGATE\AxgateVpnClient\Settings |
| Operation: | write | Name: | UseCustomTrayIcon |
Value: 0 | |||
| (PID) Process: | (5988) UpdateAgent_http_210.178.134.254_7778.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5988) UpdateAgent_http_210.178.134.254_7778.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5988) UpdateAgent_http_210.178.134.254_7778.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5988) UpdateAgent_http_210.178.134.254_7778.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\AXGATE\AxgateVpnClient\Settings |
| Operation: | delete value | Name: | SystemVersion |
Value: | |||
| (PID) Process: | (5988) UpdateAgent_http_210.178.134.254_7778.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\AXGATE\AxgateVpnClient\Settings |
| Operation: | delete value | Name: | SystemVersion2 |
Value: | |||
| (PID) Process: | (5988) UpdateAgent_http_210.178.134.254_7778.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\AXGATE\AxgateVpnClient\Settings |
| Operation: | delete value | Name: | FindProcessName |
Value: | |||
| (PID) Process: | (5988) UpdateAgent_http_210.178.134.254_7778.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\AXGATE\AxgateVpnClient\Settings |
| Operation: | delete value | Name: | FindProcessNameMac |
Value: | |||
| (PID) Process: | (5988) UpdateAgent_http_210.178.134.254_7778.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\AXGATE\AxgateVpnClient\Settings |
| Operation: | delete value | Name: | FindProcessHash |
Value: | |||
| (PID) Process: | (5988) UpdateAgent_http_210.178.134.254_7778.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\AXGATE\AxgateVpnClient\Settings |
| Operation: | delete value | Name: | FindProcessHashMac |
Value: | |||
Executable files
90
Suspicious files
92
Text files
39
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4484 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_UpdatePatch.exe_3579125eabccbd6b7f9798ceaae33564a828d3f_06d669a9_583f8073-f75e-446a-bb92-9e845601d19a\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4484 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER782B.tmp.dmp | binary | |
MD5:4A8DBC94D5A1F34EBA6C3376ACE6CE47 | SHA256:EA790676429C1A141A71593F6EBB03AAAAA88320E90DCCED66697034B05DC7C4 | |||
| 3824 | UpdateAXGATE_VPN_Client.exe | C:\ProgramData\AXGATE\AXGATE VPN Client\Bin\UpdatePatch.exe | executable | |
MD5:39F877B469DDE11E06979A111FFDD590 | SHA256:847FF4FDFB746066F56FA607C3F06E259C94277472770791D161C84CE927AB50 | |||
| 5988 | UpdateAgent_http_210.178.134.254_7778.exe | C:\Users\admin\AppData\Roaming\updateUI.ini | binary | |
MD5:E8B7E85FB43CE48A20417B7570319EB6 | SHA256:1FB517486A8F0085C5CEA0A4C73ADF1FD60ECC4CD1E7CAB69DA37590FA421CE0 | |||
| 6852 | AXGATE_VPN_Client_Installer.exe | C:\Users\admin\AppData\Local\Temp\~BC99.tmp | text | |
MD5:42C0E457A433CEA1A266C03D04271202 | SHA256:7B312C45DBFAD07175049690EB35E71CEE24651F482FFFE34D8CB6FF12673EC2 | |||
| 2632 | AXGATE_VPN_Client_Installer.exe | C:\Users\admin\AppData\Local\Temp\{03EC156F-C389-45C5-B020-AA4D95C9AA08}\AXGATE VPN Client.msi | — | |
MD5:— | SHA256:— | |||
| 2632 | AXGATE_VPN_Client_Installer.exe | C:\Users\admin\AppData\Local\Downloaded Installations\{09CD551F-FAF7-4C84-8816-C2E414C48FA8}\AXGATE VPN Client.msi | — | |
MD5:— | SHA256:— | |||
| 5988 | UpdateAgent_http_210.178.134.254_7778.exe | C:\Users\admin\AppData\Roaming\version.ini | text | |
MD5:557E511D6D06CA08E2C55C4EB913D36F | SHA256:8F531E36AF200072B22D3D1BC4B0032B9407D5372C3AC1F9D71F7A0069B96DA6 | |||
| 4484 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER79D3.tmp.xml | xml | |
MD5:BC16E39DEB707D18879384F7BB160E34 | SHA256:B2D71E4127380EB3DEED3E2760D16E7D9A9E6E032A82214458533BFA07A3041D | |||
| 4484 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:1B7FD5177461034E4086724C5845E927 | SHA256:065AF18C229898A1C2A8D989911ADCD9B1E2AB14B1953EBF8EAF34AE37EA1627 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
52
DNS requests
17
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5988 | UpdateAgent_http_210.178.134.254_7778.exe | POST | 200 | 210.178.134.254:7778 | http://210.178.134.254:7778/install_files.cgi | unknown | — | — | malicious |
5988 | UpdateAgent_http_210.178.134.254_7778.exe | POST | 200 | 210.178.134.254:7778 | http://210.178.134.254:7778/install_files.cgi | unknown | — | — | malicious |
5988 | UpdateAgent_http_210.178.134.254_7778.exe | POST | 200 | 210.178.134.254:7778 | http://210.178.134.254:7778/install_files.cgi | unknown | — | — | malicious |
5988 | UpdateAgent_http_210.178.134.254_7778.exe | POST | 200 | 210.178.134.254:7778 | http://210.178.134.254:7778/install_files.cgi | unknown | — | — | malicious |
4484 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1636 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1636 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3848 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4288 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5400 | UpdatePatch.exe | 193.122.105.160:8080 | — | ORACLE-BMC-31898 | KR | unknown |
5988 | UpdateAgent_http_210.178.134.254_7778.exe | 210.178.134.254:7778 | — | National Health Insurance Service | KR | unknown |
4324 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4484 | WerFault.exe | 104.208.16.94:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5988 | UpdateAgent_http_210.178.134.254_7778.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
5988 | UpdateAgent_http_210.178.134.254_7778.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
5988 | UpdateAgent_http_210.178.134.254_7778.exe | Misc activity | ET INFO EXE - Served Attached HTTP |