| File name: | Trojan;Win32.Malgent!MTB.zip |
| Full analysis: | https://app.any.run/tasks/5cbd8ff3-c400-40ac-ae16-18012e85ff06 |
| Verdict: | Malicious activity |
| Analysis date: | June 20, 2024, 22:02:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 5C1B7D49200CE0272838D7B5E934AC8D |
| SHA1: | 6C45A549331C39A560A831F7EF279408D696DE0A |
| SHA256: | 7A7CF91F73E69D9B831CC8A48EE5B58659F4F69D6265EB0E6E75DC047BF0EA48 |
| SSDEEP: | 98304:usVk1VujdIAuDqVIGycyenCw1G/+/ayzqHjgWdSl1wnNQFNeYvQmHfDycE8ArGbn:gGOwwOM4jS/ZMhrrblkMrzF |
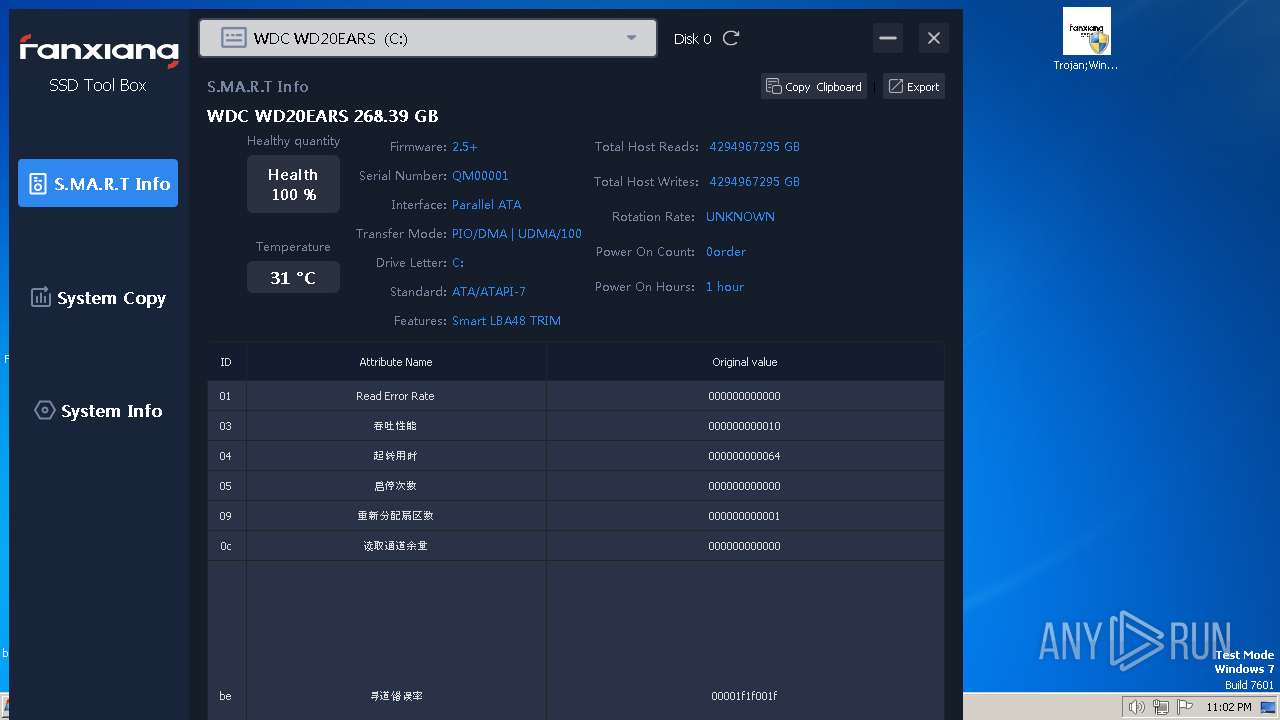
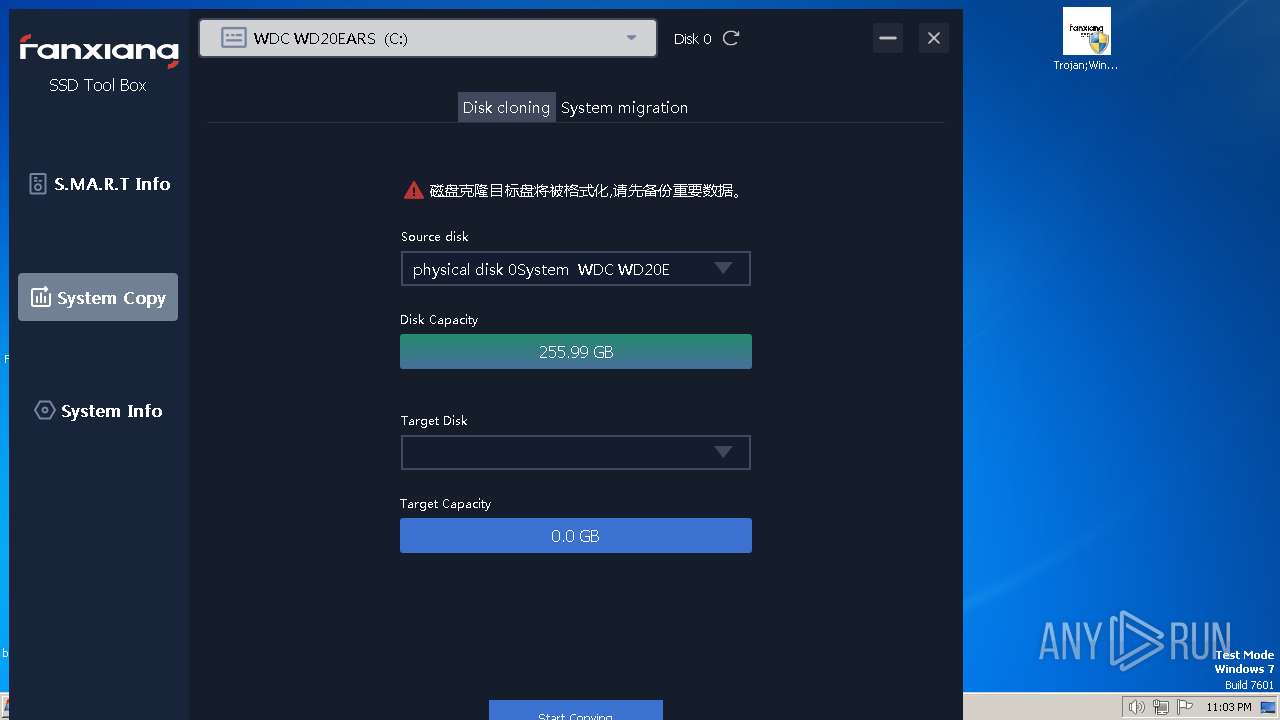
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3428)
- Trojan;Win32.Malgent!MTB.exe (PID: 3856)
- sg.tmp (PID: 964)
SUSPICIOUS
The process drops C-runtime libraries
- sg.tmp (PID: 964)
Starts application with an unusual extension
- Trojan;Win32.Malgent!MTB.exe (PID: 3856)
Process drops legitimate windows executable
- sg.tmp (PID: 964)
Starts CMD.EXE for commands execution
- Trojan;Win32.Malgent!MTB.exe (PID: 3856)
Executable content was dropped or overwritten
- Trojan;Win32.Malgent!MTB.exe (PID: 3856)
- sg.tmp (PID: 964)
Creates file in the systems drive root
- SSDmanagement.exe (PID: 268)
Uses WMIC.EXE to obtain CPU information
- SSDmanagement.exe (PID: 268)
Uses WMIC.EXE to obtain operating system information
- SSDmanagement.exe (PID: 268)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 3844)
Reads the Internet Settings
- WMIC.exe (PID: 4016)
- WMIC.exe (PID: 1608)
- WMIC.exe (PID: 3324)
- WMIC.exe (PID: 3844)
- WMIC.exe (PID: 2000)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- SSDmanagement.exe (PID: 268)
Uses WMIC.EXE to obtain BIOS management information
- SSDmanagement.exe (PID: 268)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3428)
Reads the computer name
- sg.tmp (PID: 964)
- Trojan;Win32.Malgent!MTB.exe (PID: 3856)
- SSDmanagement.exe (PID: 268)
Checks supported languages
- SSDmanagement.exe (PID: 268)
- Trojan;Win32.Malgent!MTB.exe (PID: 3856)
- sg.tmp (PID: 964)
Manual execution by a user
- Trojan;Win32.Malgent!MTB.exe (PID: 3856)
Create files in a temporary directory
- sg.tmp (PID: 964)
- Trojan;Win32.Malgent!MTB.exe (PID: 3856)
Reads the machine GUID from the registry
- Trojan;Win32.Malgent!MTB.exe (PID: 3856)
- SSDmanagement.exe (PID: 268)
UPX packer has been detected
- Trojan;Win32.Malgent!MTB.exe (PID: 3856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:20 16:58:58 |
| ZipCRC: | 0x7e8af884 |
| ZipCompressedSize: | 12669513 |
| ZipUncompressedSize: | 12939911 |
| ZipFileName: | Trojan;Win32.Malgent!MTB.exe |
Total processes
58
Monitored processes
10
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Users\admin\AppData\Local\Temp\~1347193478775578046\SSDmanagement.exe" | C:\Users\admin\AppData\Local\Temp\~1347193478775578046\SSDmanagement.exe | — | Trojan;Win32.Malgent!MTB.exe | |||||||||||
User: admin Integrity Level: HIGH Version: 0.0.0.0 Modules
| |||||||||||||||
| 964 | 7zG_exe x "C:\Users\admin\Desktop\Trojan;Win32.Malgent!MTB.exe" -y -aoa -o"C:\Users\admin\AppData\Local\Temp\~1347193478775578046" | C:\Users\admin\AppData\Local\Temp\~1512130915225489763~\sg.tmp | Trojan;Win32.Malgent!MTB.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1608 | wmic baseboard get manufacturer | C:\Windows\System32\wbem\WMIC.exe | — | SSDmanagement.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2000 | wmic bios get smbiosbiosversion | C:\Windows\System32\wbem\WMIC.exe | — | SSDmanagement.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3324 | wmic baseboard get product | C:\Windows\System32\wbem\WMIC.exe | — | SSDmanagement.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3336 | cmd.exe /c set | C:\Windows\System32\cmd.exe | — | Trojan;Win32.Malgent!MTB.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3428 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Trojan;Win32.Malgent!MTB.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3844 | wmic os get caption | C:\Windows\System32\wbem\WMIC.exe | — | SSDmanagement.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3856 | "C:\Users\admin\Desktop\Trojan;Win32.Malgent!MTB.exe" | C:\Users\admin\Desktop\Trojan;Win32.Malgent!MTB.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 0.0.0.0 Modules
| |||||||||||||||
| 4016 | wmic cpu get name | C:\Windows\System32\wbem\WMIC.exe | — | SSDmanagement.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 273
Read events
4 251
Write events
22
Delete events
0
Modification events
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan;Win32.Malgent!MTB.zip | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
28
Suspicious files
22
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 964 | sg.tmp | C:\Users\admin\AppData\Local\Temp\~1347193478775578046\translate\tr_zh.qm | qm | |
MD5:7C11E17325929CDC570CB1D2EDC6D389 | SHA256:13121E9DBCC396D2E971248939B0DDC94E32B0CECC132C61EB7B39CEB550F461 | |||
| 964 | sg.tmp | C:\Users\admin\AppData\Local\Temp\~1347193478775578046\translations\qt_ca.qm | qm | |
MD5:26534ADF1704EA33CCB83381F36A2CD0 | SHA256:EF196C601EF5A0AF8C77FA62601EE1630ED919CEF048B903BA48FFDEAB246D3C | |||
| 964 | sg.tmp | C:\Users\admin\AppData\Local\Temp\~1347193478775578046\translations\qt_cs.qm | qm | |
MD5:987E045E06AEBA29A8E05A074E6BDB91 | SHA256:86E174EFF79F096D81146860DD5CA9E946C643A3464C7DA8919C972747B8DF09 | |||
| 3856 | Trojan;Win32.Malgent!MTB.exe | C:\Users\admin\AppData\Local\Temp\~1512130915225489763~\sg.tmp | executable | |
MD5:7C4718943BD3F66EBDB47CCCA72C7B1E | SHA256:4CC32D00338FC7B206A7C052297ACF9AC304AE7DE9D61A2475A116959C1524FC | |||
| 964 | sg.tmp | C:\Users\admin\AppData\Local\Temp\~1347193478775578046\translate\tr_en.qm | qm | |
MD5:0559D0F7BAFA379F711E7D075360710A | SHA256:E29C40C8458C4186C4D4594D86A529563143C2C3CE8B4A0B208F021051A80730 | |||
| 964 | sg.tmp | C:\Users\admin\AppData\Local\Temp\~1347193478775578046\translations\qt_en.qm | qm | |
MD5:4AEF4415F2E976B2CC6F24B877804A57 | SHA256:307CEF95DD5B36FF215055D427E1885B7FC3650C9224CF76D63056545996FF60 | |||
| 964 | sg.tmp | C:\Users\admin\AppData\Local\Temp\~1347193478775578046\translations\qt_ar.qm | qm | |
MD5:E7EC8B6E07D62634777DBCB47BD611D3 | SHA256:820EB8876A61022B371D557EEBD83A99A3872C6E93ACBF3E98026DFCB3CE8EFB | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3428.25344\Trojan;Win32.Malgent!MTB.exe | executable | |
MD5:DB2B4EFA11A04CE3A785D706CB231D2A | SHA256:7A752283EB17BE491A2411AE9D95D11D436D3310CF0FCA01BE49ED484A7C0280 | |||
| 964 | sg.tmp | C:\Users\admin\AppData\Local\Temp\~1347193478775578046\translations\qt_es.qm | qm | |
MD5:7479D957C5309AEDD4F58E4556590F69 | SHA256:F6A0734903BBFCD9FD447FBCFD7AD6B9BBEA50D038DC9388038C9ECFC13752A4 | |||
| 964 | sg.tmp | C:\Users\admin\AppData\Local\Temp\~1347193478775578046\translations\qt_da.qm | qm | |
MD5:08A231EF3ABB7A813A41BC9F3B198EB5 | SHA256:885BCCBA9B953370CA8A9D1366485158482B5AB341112BEC3CAC94D2EB16DDDF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
11
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.15.179.146:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fbe613066ac7852b | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 72.247.166.29:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1372 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.15.179.146:80 | crl.microsoft.com | Akamai International B.V. | FR | whitelisted |
1372 | svchost.exe | 72.247.166.29:80 | www.microsoft.com | AKAMAI-AS | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |