| File name: | 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch |
| Full analysis: | https://app.any.run/tasks/09a34de2-b867-411c-b8dc-ba98daaa2b57 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 20:27:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64 (stripped to external PDB), for MS Windows, 14 sections |
| MD5: | F9DFD80E29F67A04DF8A3260BFE0EAA8 |
| SHA1: | F4ACCFCC71C88DF50087ECF56A610E78736346B0 |
| SHA256: | 7A74B7F7FDA52C8897A0B788A26425D44E7A664F99B806CD9402C58EE3C1A56A |
| SSDEEP: | 98304:F9pZYkzdaaOhPn+jpQAGNV22Y6naY5sMKfRC5BETE3QYrCKJXowPJon86S78P4yi:FKfJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
Process drops legitimate windows executable
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
The process drops C-runtime libraries
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
Process drops python dynamic module
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
Connects to unusual port
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
INFO
Reads the computer name
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
Checks supported languages
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
Reads the machine GUID from the registry
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
Reads the software policy settings
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
- rundll32.exe (PID: 1472)
- slui.exe (PID: 6232)
Detects GO elliptic curve encryption (YARA)
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
Application based on Golang
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
Creates files or folders in the user directory
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
- rundll32.exe (PID: 1472)
The sample compiled with english language support
- 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe (PID: 1852)
Python executable
- python.exe (PID: 7008)
- pythonw.exe (PID: 4824)
Manual execution by a user
- python.exe (PID: 7008)
- pythonw.exe (PID: 4824)
- notepad.exe (PID: 2612)
- WinRAR.exe (PID: 2876)
- rundll32.exe (PID: 1472)
- notepad.exe (PID: 6128)
- cmd.exe (PID: 6684)
Reads security settings of Internet Explorer
- notepad.exe (PID: 2612)
- rundll32.exe (PID: 1472)
- notepad.exe (PID: 6128)
Checks proxy server information
- rundll32.exe (PID: 1472)
- slui.exe (PID: 6232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 3 |
| CodeSize: | 2400768 |
| InitializedDataSize: | 256512 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5c350 |
| OSVersion: | 6.1 |
| ImageVersion: | 1 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows command line |
Total processes
143
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1472 | "C:\WINDOWS\system32\rundll32.exe" cryptext.dll,CryptExtOpenCAT C:\Users\admin\Desktop\python.cat | C:\Windows\System32\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1852 | "C:\Users\admin\Desktop\2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe" | C:\Users\admin\Desktop\2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2612 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\LICENSE.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2876 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\python311.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4648 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
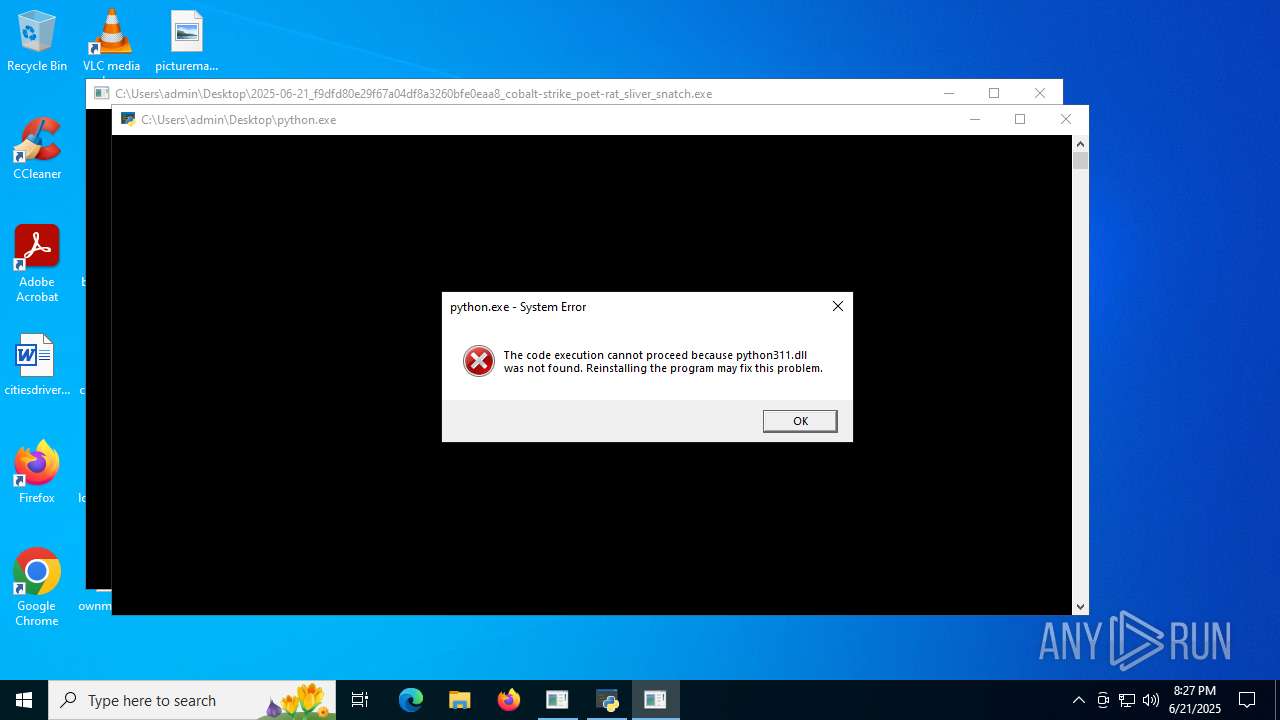
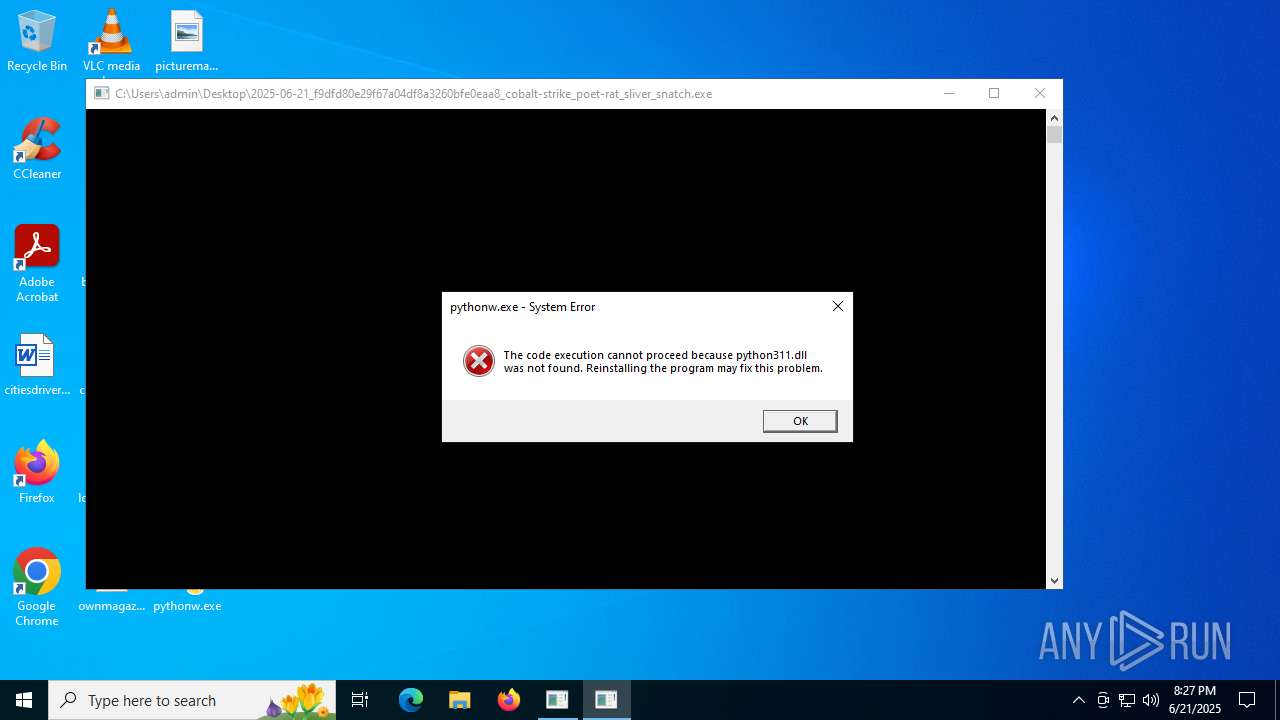
| 4824 | "C:\Users\admin\Desktop\pythonw.exe" | C:\Users\admin\Desktop\pythonw.exe | — | explorer.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 3221225781 Version: 3.11.4 Modules
| |||||||||||||||
| 5240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | python.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6128 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6232 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 845
Read events
11 837
Write events
8
Delete events
0
Modification events
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\python311.zip | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2876) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
30
Suspicious files
7
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1852 | 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\python.zip | compressed | |
MD5:D0E85BF50D2ADEA597C40EE28E774081 | SHA256:126802FF9FE787B961AE4D877262E6D6CE807D636295EF429C02E4DFD3E48041 | |||
| 1852 | 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\LICENSE.txt | text | |
MD5:EBCF45A479F291A0D965EA60B5F1C30B | SHA256:616FA565945ECA2F0E0A5440B3973FED7D5291622B90849212077FE68E27DCB0 | |||
| 1852 | 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\python.exe | executable | |
MD5:B6EF5717317F6300D663ED9559EE9967 | SHA256:4FB049EEDDD221E5470CD33177299DD13F85EBA25BEEF7ACED7A0890AD85181F | |||
| 1852 | 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\pyexpat.pyd | executable | |
MD5:9C21A5540FC572F75901820CF97245EC | SHA256:2FF8CD82E7CC255E219E7734498D2DEA0C65A5AB29DC8581240D40EB81246045 | |||
| 1852 | 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\winsound.pyd | executable | |
MD5:1C856FABFF6967DD21ADE8338E15D637 | SHA256:63ED931F692B63A8D6D7948BD8EF3B6C678B57C0C0574BF649F783C602B4E7E4 | |||
| 1852 | 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\unicodedata.pyd | executable | |
MD5:AA13EE6770452AF73828B55AF5CD1A32 | SHA256:8FBED20E9225FF82132E97B4FEFBB5DDBC10C062D9E3F920A6616AB27BB5B0FB | |||
| 1852 | 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\_bz2.pyd | executable | |
MD5:3859239CED9A45399B967EBCE5A6BA23 | SHA256:A4DD883257A7ACE84F96BCC6CD59E22D843D0DB080606DEFAE32923FC712C75A | |||
| 1852 | 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\python311.dll | executable | |
MD5:5A5DD7CAD8028097842B0AFEF45BFBCF | SHA256:A811C7516F531F1515D10743AE78004DD627EBA0DC2D3BC0D2E033B2722043CE | |||
| 1852 | 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\pythonw.exe | executable | |
MD5:9D0F19A3FDF077FC90CB1055018669FD | SHA256:695EC4080F596F485E4E36DE383A32F18042BC13620CF93BA5708EC354B6CA0D | |||
| 1852 | 2025-06-21_f9dfd80e29f67a04df8a3260bfe0eaa8_cobalt-strike_poet-rat_sliver_snatch.exe | C:\Users\admin\AppData\Roaming\Suh\python_portable\vcruntime140.dll | executable | |
MD5:4585A96CC4EEF6AAFD5E27EA09147DC6 | SHA256:A8F950B4357EC12CFCCDDC9094CCA56A3D5244B95E09EA6E9A746489F2D58736 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
26
DNS requests
11
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 184.24.77.39:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.39:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6012 | RUXIMICS.exe | GET | 200 | 184.24.77.39:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6012 | RUXIMICS.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 151.101.0.223:443 | https://www.python.org/ftp/python/3.11.4/python-3.11.4-embed-amd64.zip | unknown | compressed | 10.1 Mb | whitelisted |
1472 | rundll32.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
1472 | rundll32.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAcfFBuLMA0l8xTrIwzQ0d0%3D | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6012 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 184.24.77.39:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.24.77.39:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6012 | RUXIMICS.exe | 184.24.77.39:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.python.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
— | — | Misc activity | ET INFO Go-http-client User-Agent Observed Outbound |