| File name: | Test_Zip.zip |
| Full analysis: | https://app.any.run/tasks/74be4922-ec41-4ad3-883d-0bf1bf62f279 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 19:10:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 2F30417644D208DF5A6EFF22FF893FA2 |
| SHA1: | C30159096C8156D18409473F4F9D8C8E8186B1C3 |
| SHA256: | 7A07618B83B9B0B95933BFDA01C6370B5A2A12B264E919B28E1CC5A3DFFDA314 |
| SSDEEP: | 98304:6fxe+FUYtb9g3vu+ZG0SKgH3TTCmXrJTMQ9vkj5L4PhpbsYkinxBXbgR/QRlKZ88:rfmxuJrzinZatamqeB78Yusd |
MALICIOUS
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 4620)
Bypass execution policy to execute commands
- powershell.exe (PID: 6644)
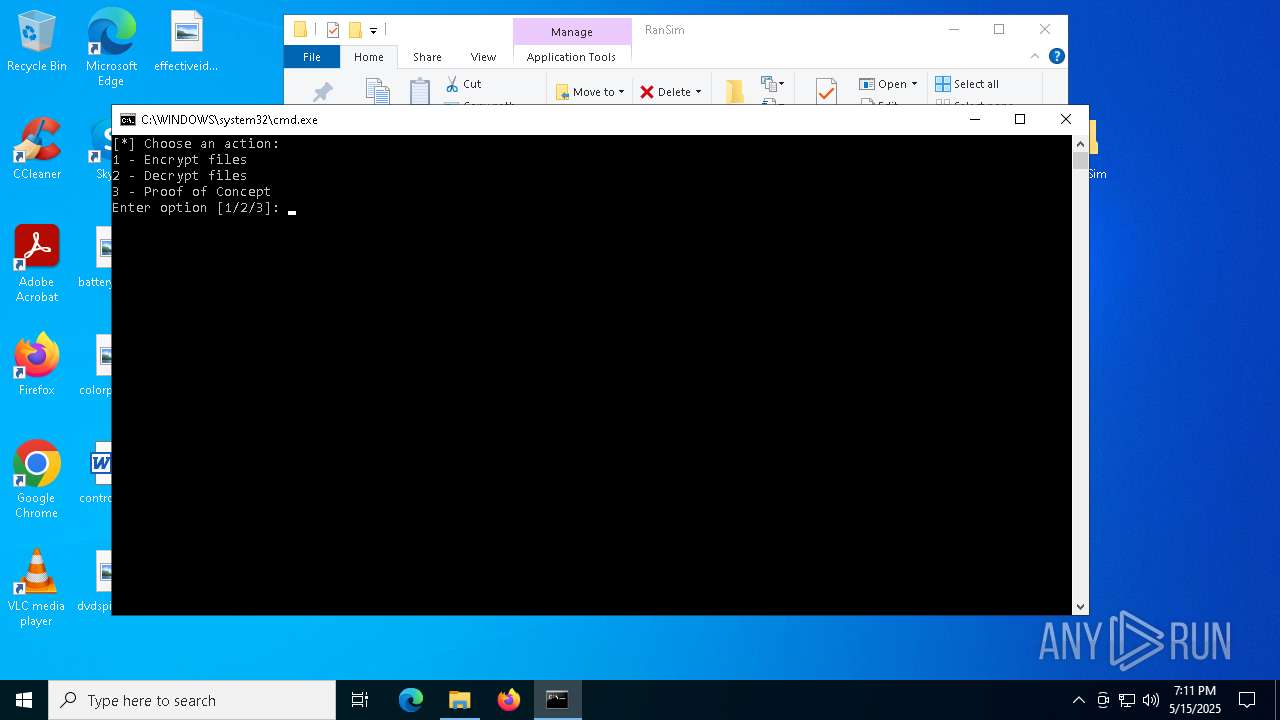
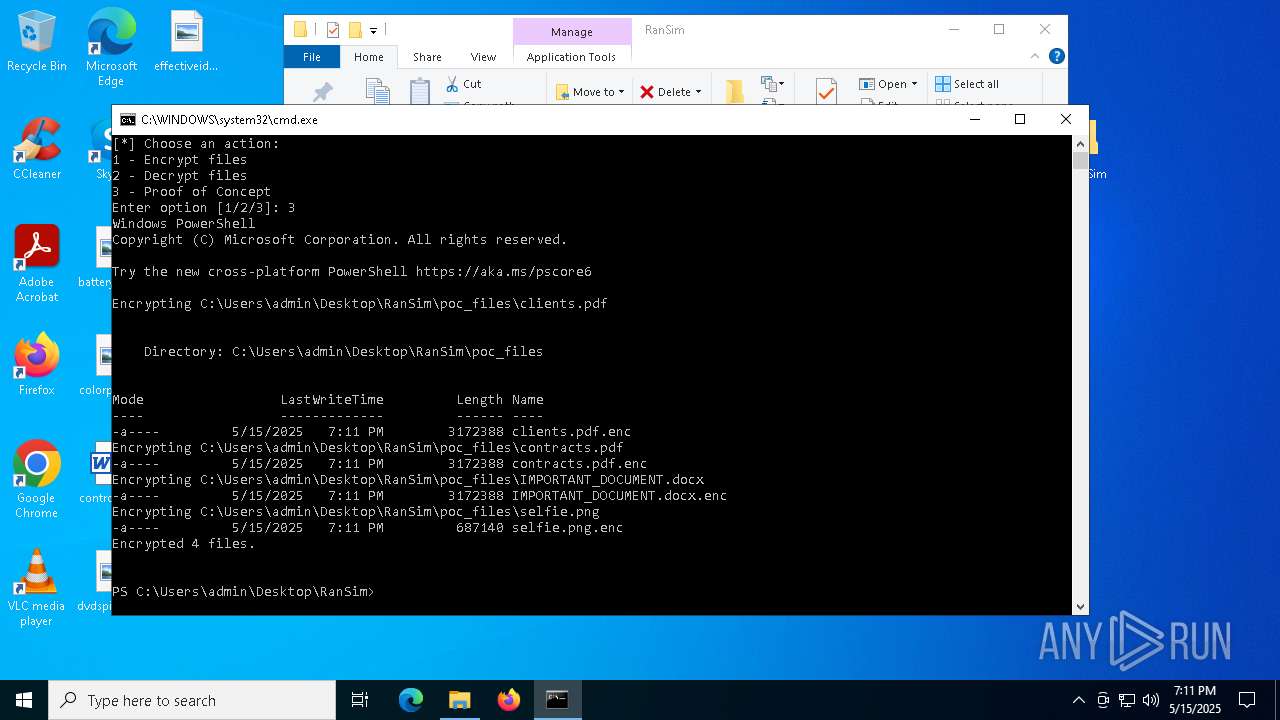
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 6644)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 6644)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 6644)
SUSPICIOUS
The process executes Powershell scripts
- cmd.exe (PID: 4620)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4620)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6644)
INFO
Manual execution by a user
- cmd.exe (PID: 4620)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6644)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6644)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 6644)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6644)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:14 18:32:54 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | RanSim/ |
Total processes
128
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1672 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2852 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3676 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Test_Zip.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4620 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\RanSim\start.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
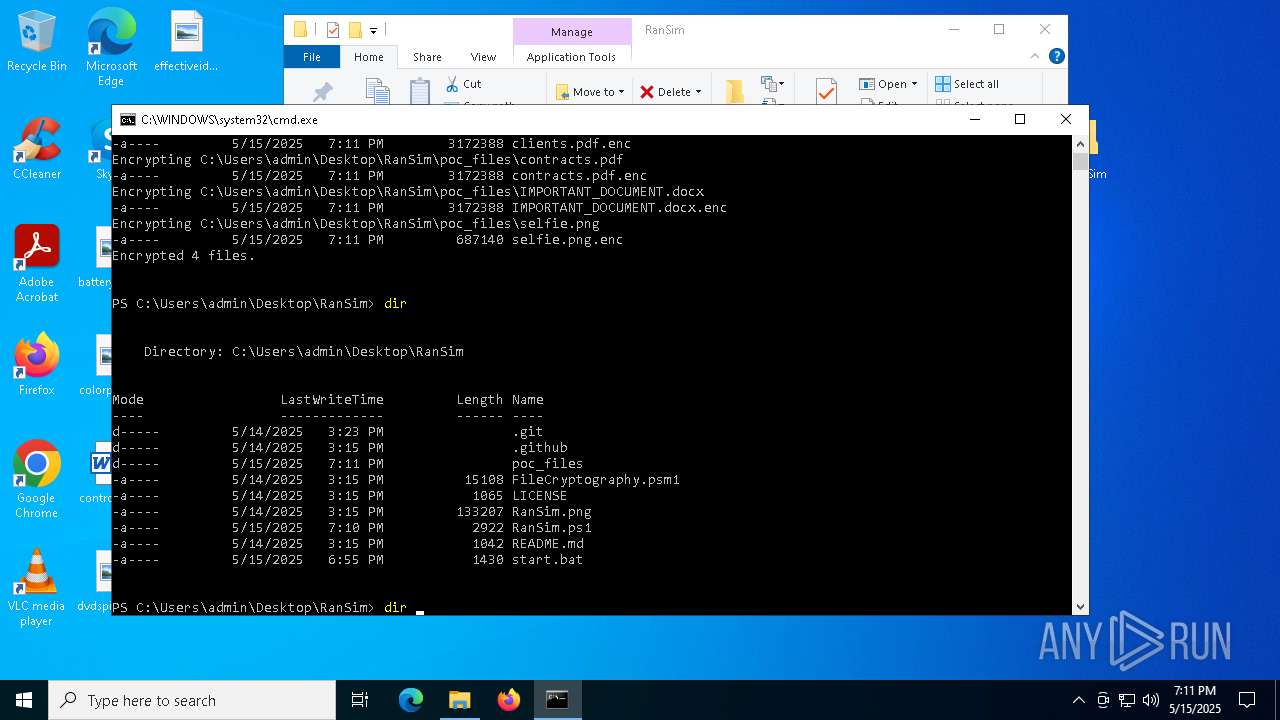
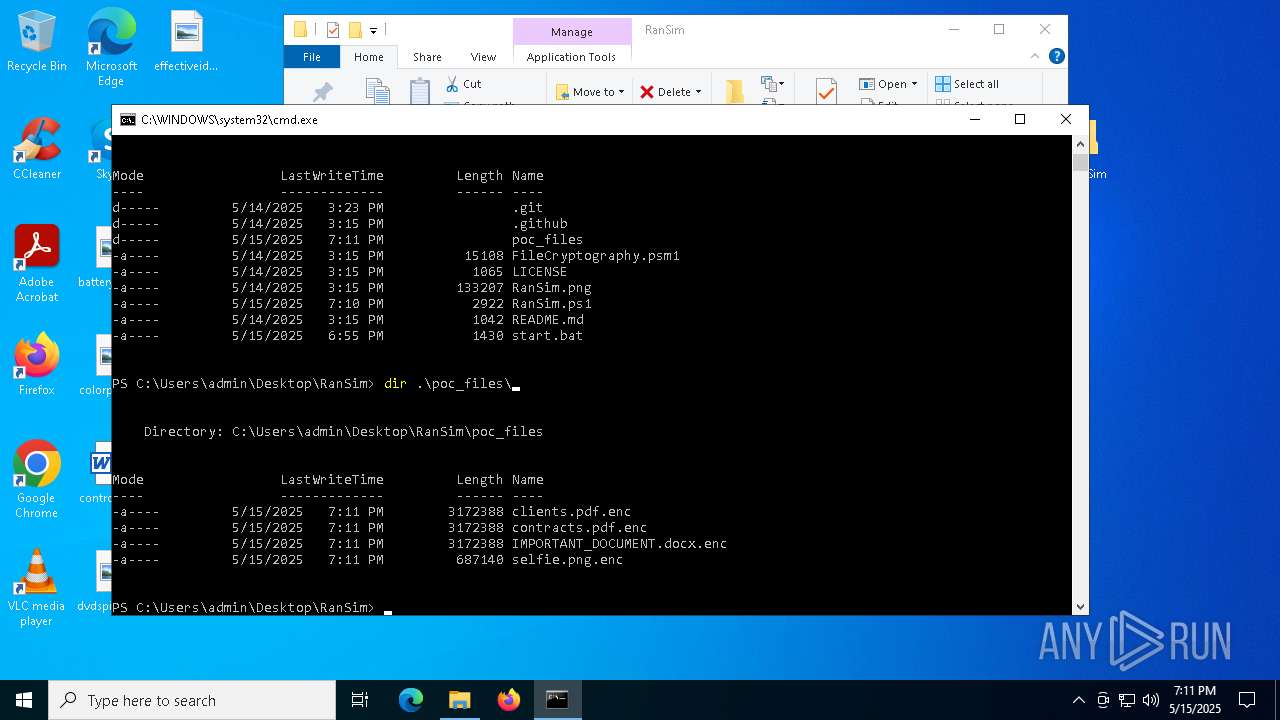
| 6644 | powershell -ExecutionPolicy Bypass -NoExit -File RanSim.ps1 -Mode encrypt -Extension ".enc" -Key "Q5KyUru6wn82hlY9k8xUjJOPIC9da41jgRkpt21jo2L=" -TargetPath ".\poc_files" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 907
Read events
6 889
Write events
18
Delete events
0
Modification events
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Test_Zip.zip | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
0
Suspicious files
13
Text files
34
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.8575\RanSim\.git\packed-refs | text | |
MD5:944E41CEAF16C74F7B2437C406C00EEC | SHA256:4F93537CE77DFC23BCEDDE1927B125DEF55545C87BF789E13FA9C13752A7EFBE | |||
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.8575\RanSim\.git\info\exclude | text | |
MD5:036208B4A1AB4A235D75C181E685E5A3 | SHA256:6671FE83B7A07C8932EE89164D1F2793B2318058EB8B98DC5C06EE0A5A3B0EC1 | |||
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.8575\RanSim\.github\FUNDING.yml | text | |
MD5:97828F037709E596E4074ECD7AA20936 | SHA256:D2EF80E462B7078260C1B3E8F15F211C2E464CD7C82D409671D9181A80112E67 | |||
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.8575\RanSim\LICENSE | text | |
MD5:7325E58BFC93561A31A5EC2775AB87AC | SHA256:C5232EF7D0F1DDC721E26817DC27A09F8DACA68CF45D7A82EE4F4C1E60FE040B | |||
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.8575\RanSim\.git\hooks\update.sample | text | |
MD5:647AE13C682F7827C22F5FC08A03674E | SHA256:8D5F2FA83E103CF08B57EAA67521DF9194F45CBDBCB37DA52AD586097A14D106 | |||
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.8575\RanSim\.git\hooks\pre-push.sample | text | |
MD5:2C642152299A94E05EA26EAE11993B13 | SHA256:ECCE9C7E04D3F5DD9D8ADA81753DD1D549A9634B26770042B58DDA00217D086A | |||
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.8575\RanSim\.git\hooks\pre-receive.sample | text | |
MD5:2AD18EC82C20AF7B5926ED9CEA6AEEDD | SHA256:A4C3D2B9C7BB3FD8D1441C31BD4EE71A595D66B44FCF49DDB310252320169989 | |||
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.8575\RanSim\.git\hooks\fsmonitor-watchman.sample | text | |
MD5:A0B2633A2C8E97501610BD3F73DA66FC | SHA256:E0549964E93897B519BD8E333C037E51FFF0F88BA13E086A331592BF801FA1D0 | |||
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.8575\RanSim\.git\hooks\pre-rebase.sample | text | |
MD5:56E45F2BCBC8226D2B4200F7C46371BF | SHA256:4FEBCE867790052338076F4E66CC47EFB14879D18097D1D61C8261859EAAA7B3 | |||
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.8575\RanSim\.git\refs\heads\main | text | |
MD5:9BE5355F7AB7E048F73CC415D4EF114E | SHA256:9D4F770D31EABD9D8D461ECD856404E6C9A7365ED003156E87F8B802CE097BF4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
38
DNS requests
11
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7152 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7152 | SIHClient.exe | 52.165.164.15:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
15.164.165.52.in-addr.arpa |
| unknown |
d.3.0.0.0.0.0.0.0.0.0.0.0.0.0.0.7.0.0.0.8.0.4.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |