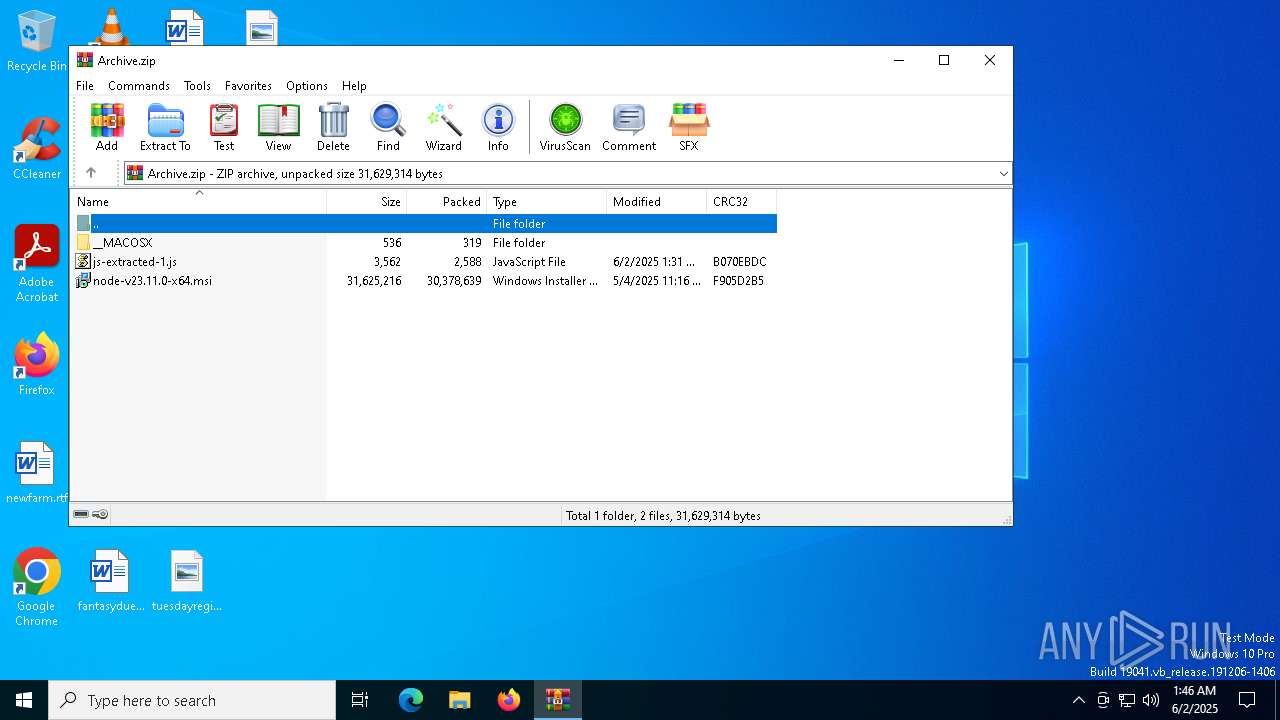
| File name: | Archive.zip |
| Full analysis: | https://app.any.run/tasks/17d4cbb2-691e-471e-8077-6cd7e8e98cd9 |
| Verdict: | Malicious activity |
| Analysis date: | June 02, 2025, 01:46:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 625F4068348CB8C04404BD5CD92FEFCD |
| SHA1: | 85E4773DB474D49F84BA210D5E9337BC5A190BE3 |
| SHA256: | 7A0324239D8E917246ECF563E901701077D35ED1D645EDA0FFC677B6C052EF65 |
| SSDEEP: | 393216:J+l58xUD6wvXnhNxPdMbxZHY6c5C6ytHx:04x06GXhNNdIZHYvBw |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7048)
SUSPICIOUS
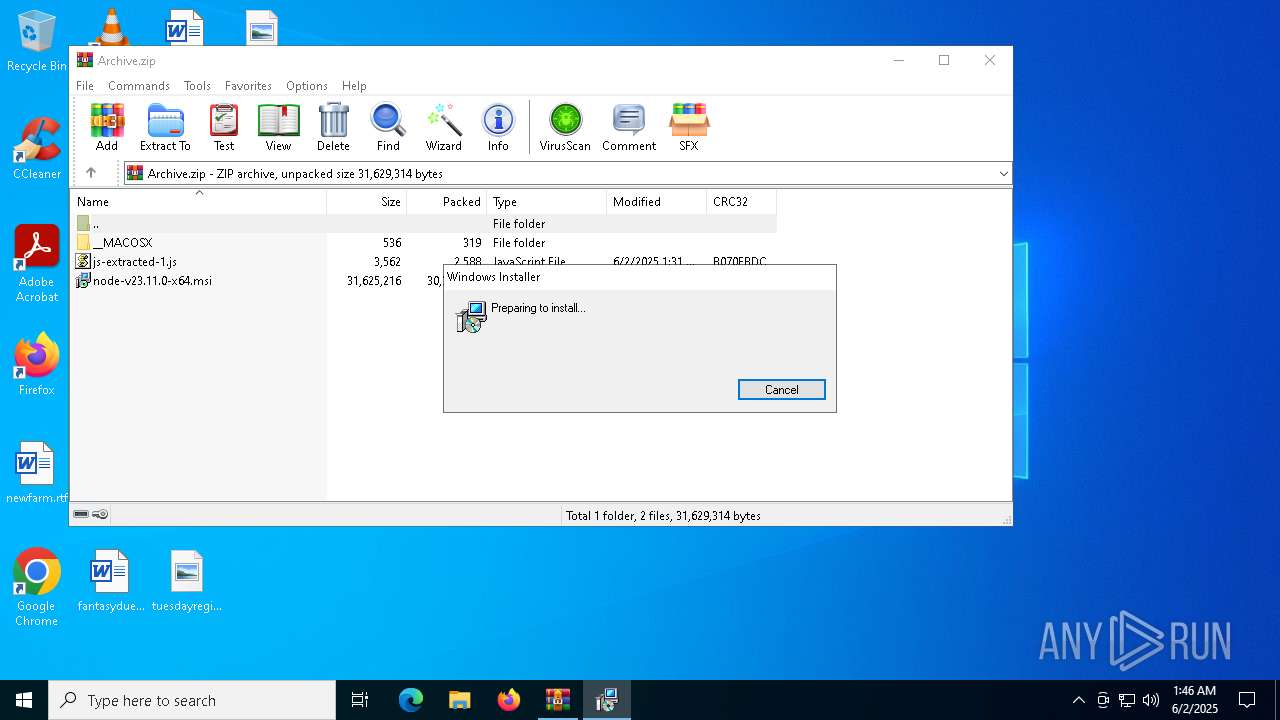
Application launched itself
- msiexec.exe (PID: 3096)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7048)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 7048)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 7048)
INFO
Manual execution by a user
- msiexec.exe (PID: 660)
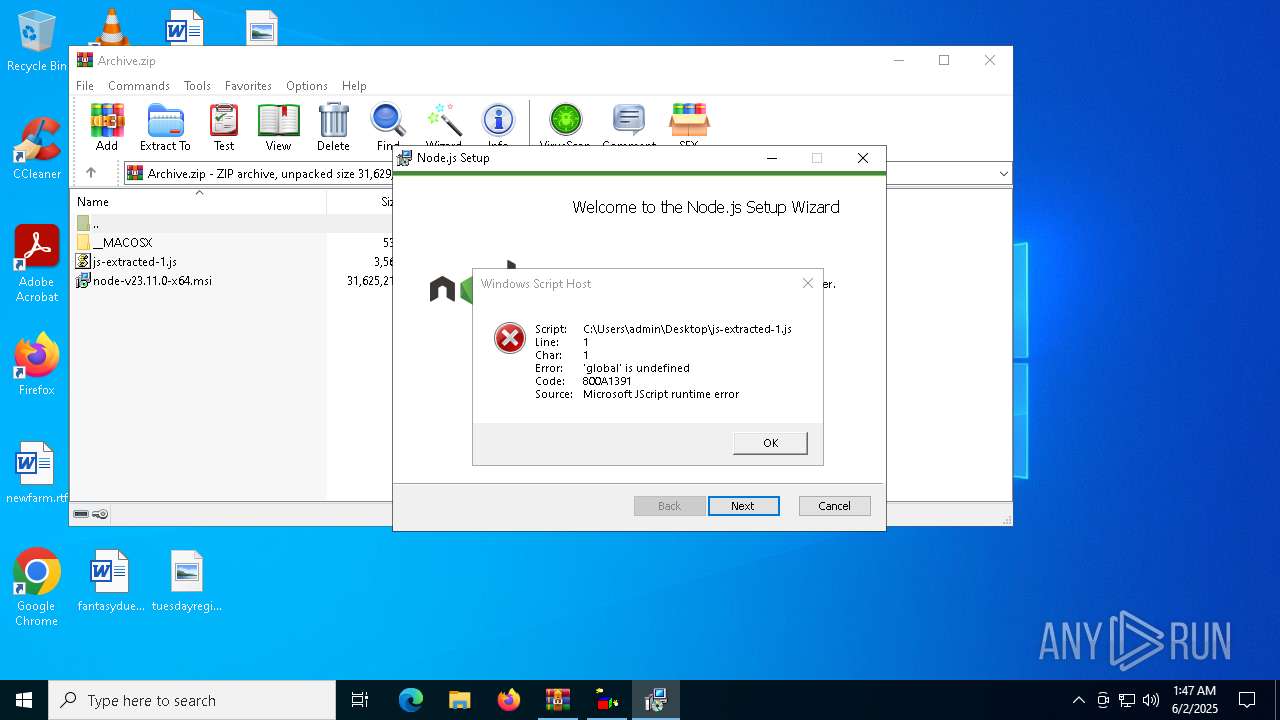
- wscript.exe (PID: 672)
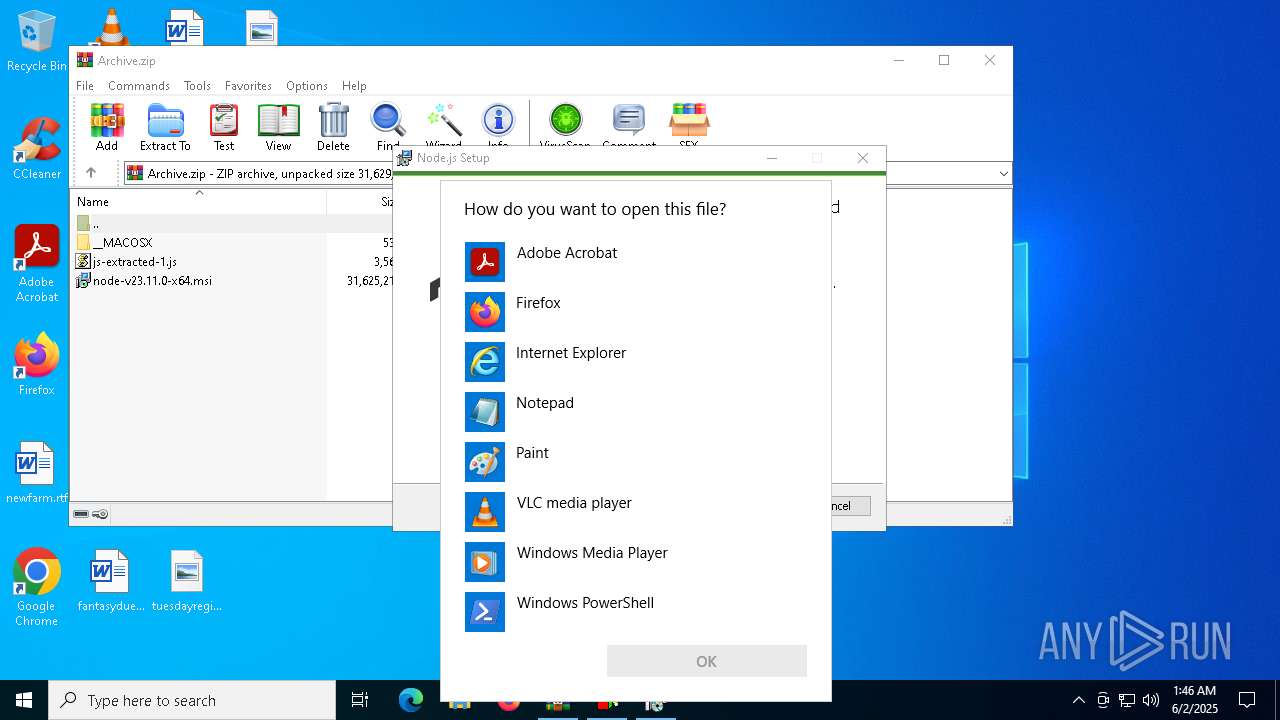
- OpenWith.exe (PID: 5360)
- OpenWith.exe (PID: 1240)
Creates files or folders in the user directory
- msiexec.exe (PID: 660)
Checks proxy server information
- msiexec.exe (PID: 660)
- slui.exe (PID: 6668)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 660)
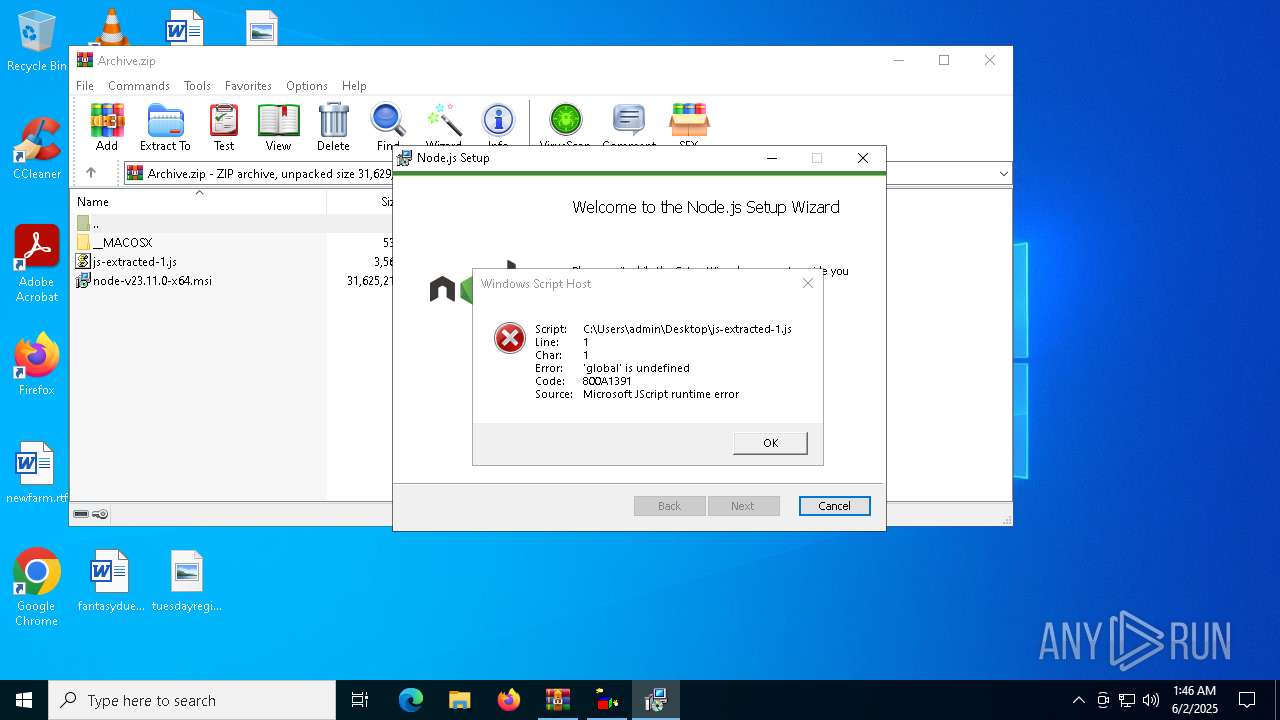
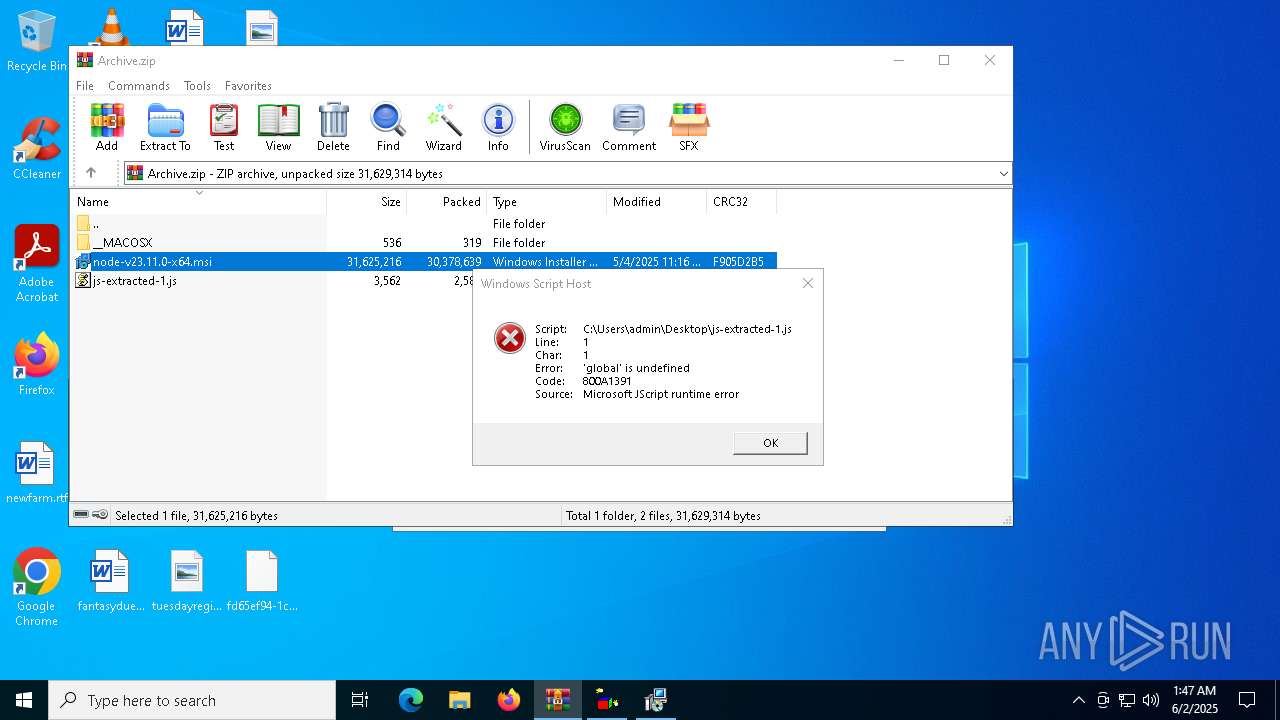
JScript runtime error (SCRIPT)
- wscript.exe (PID: 672)
Reads the software policy settings
- msiexec.exe (PID: 660)
- slui.exe (PID: 6668)
Checks supported languages
- msiexec.exe (PID: 3096)
- msiexec.exe (PID: 1472)
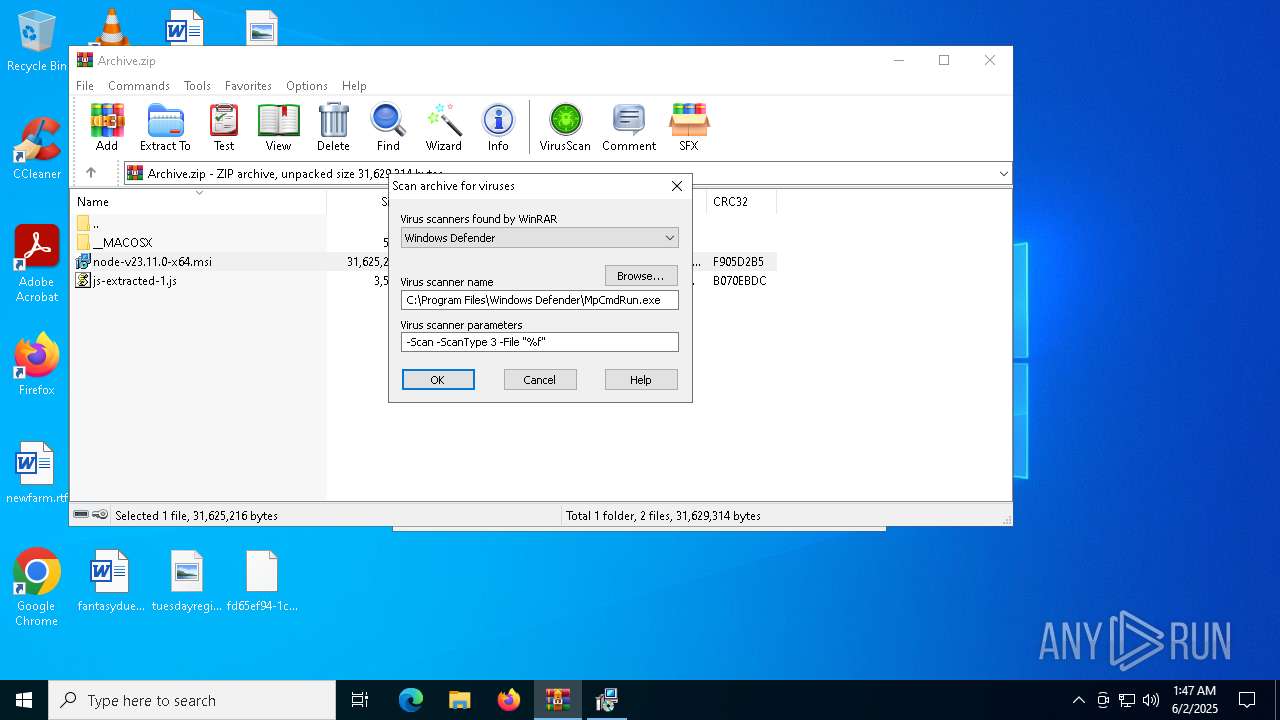
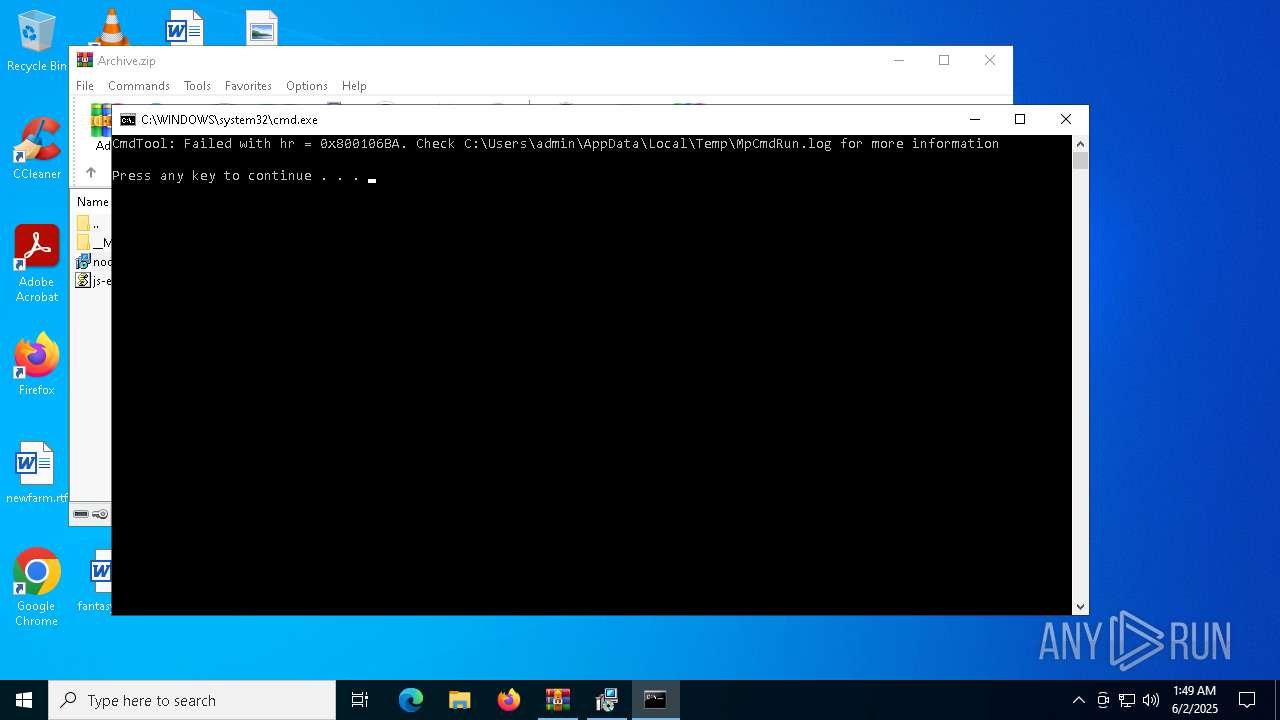
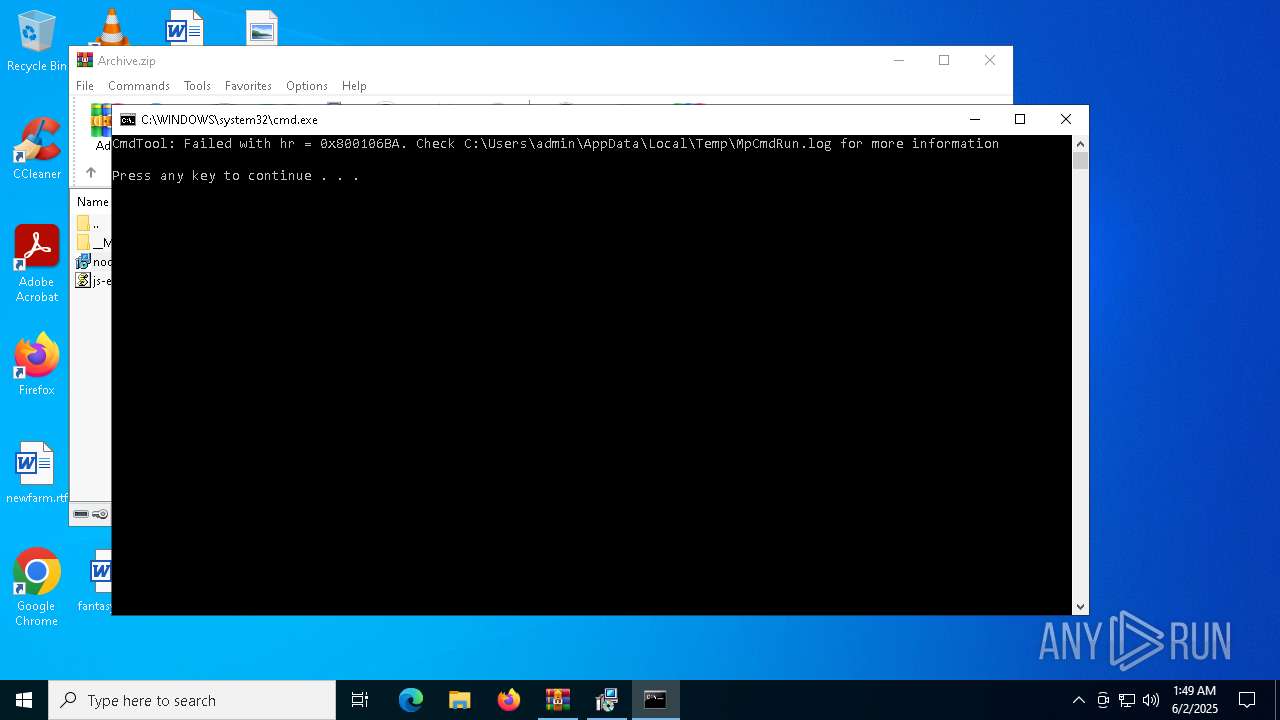
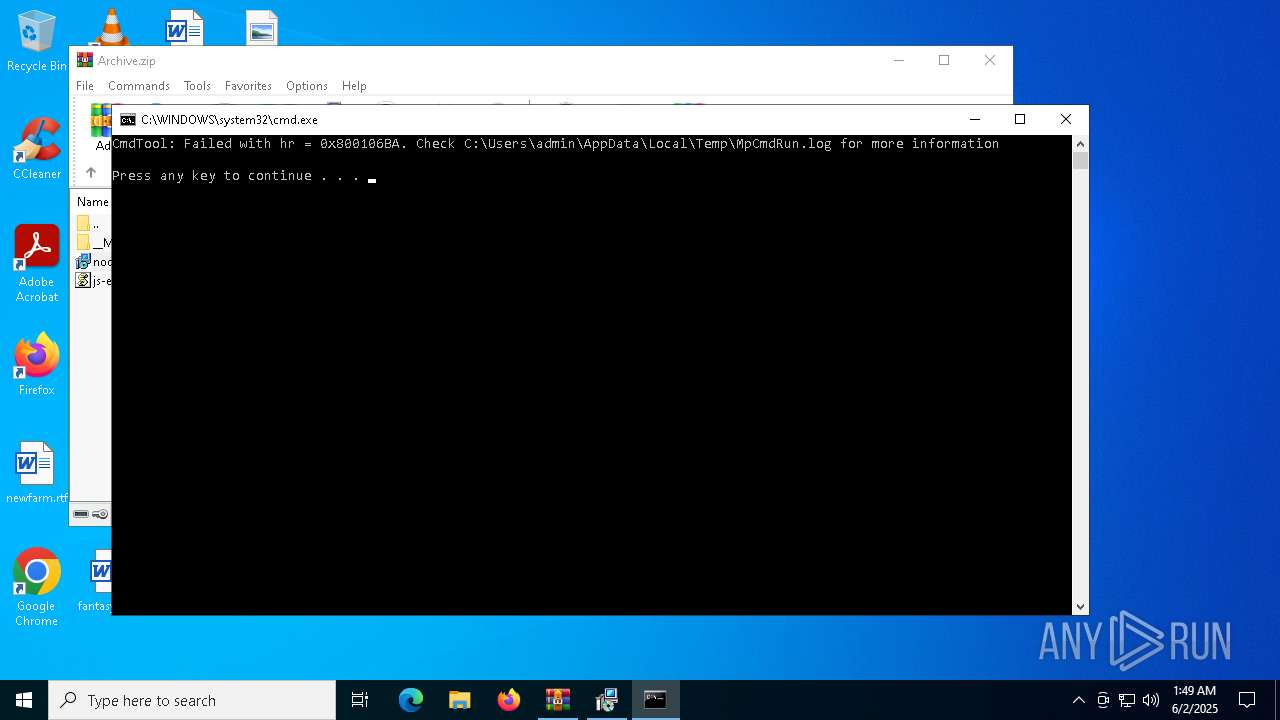
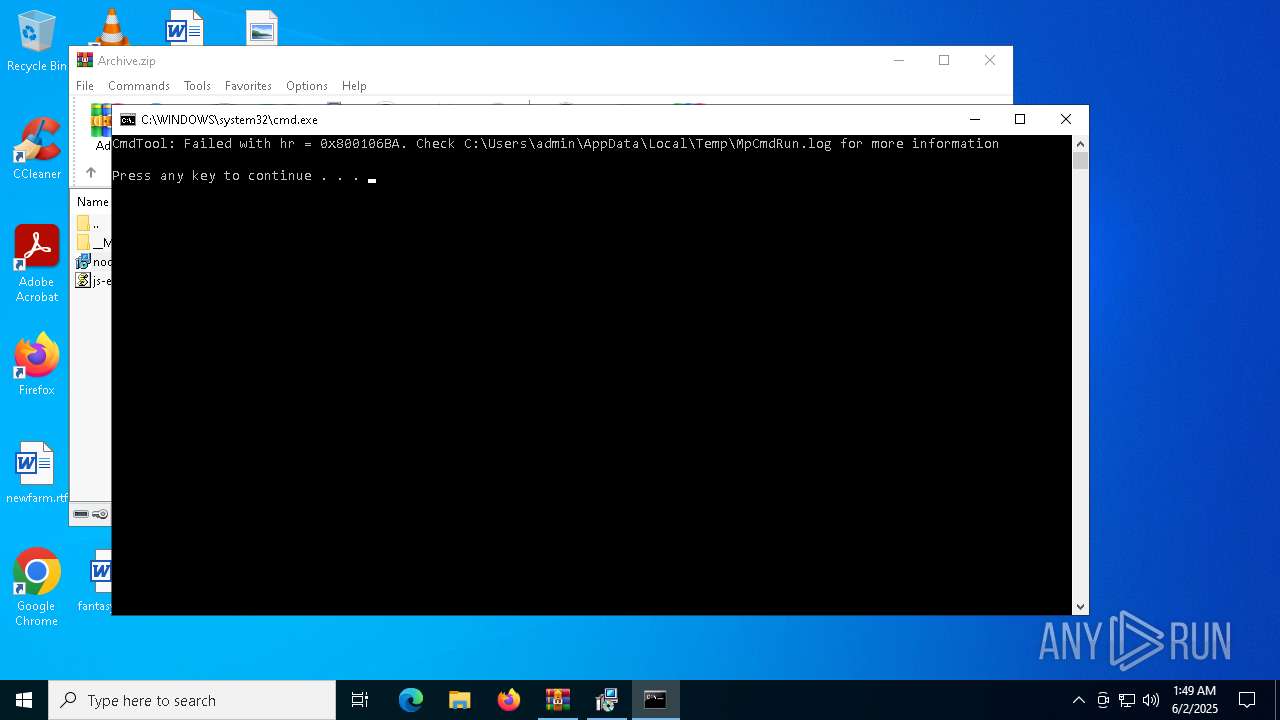
- MpCmdRun.exe (PID: 7268)
Reads the computer name
- msiexec.exe (PID: 3096)
- msiexec.exe (PID: 1472)
- MpCmdRun.exe (PID: 7268)
Executable content was dropped or overwritten
- msiexec.exe (PID: 660)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 5360)
- OpenWith.exe (PID: 1240)
The sample compiled with english language support
- msiexec.exe (PID: 660)
Create files in a temporary directory
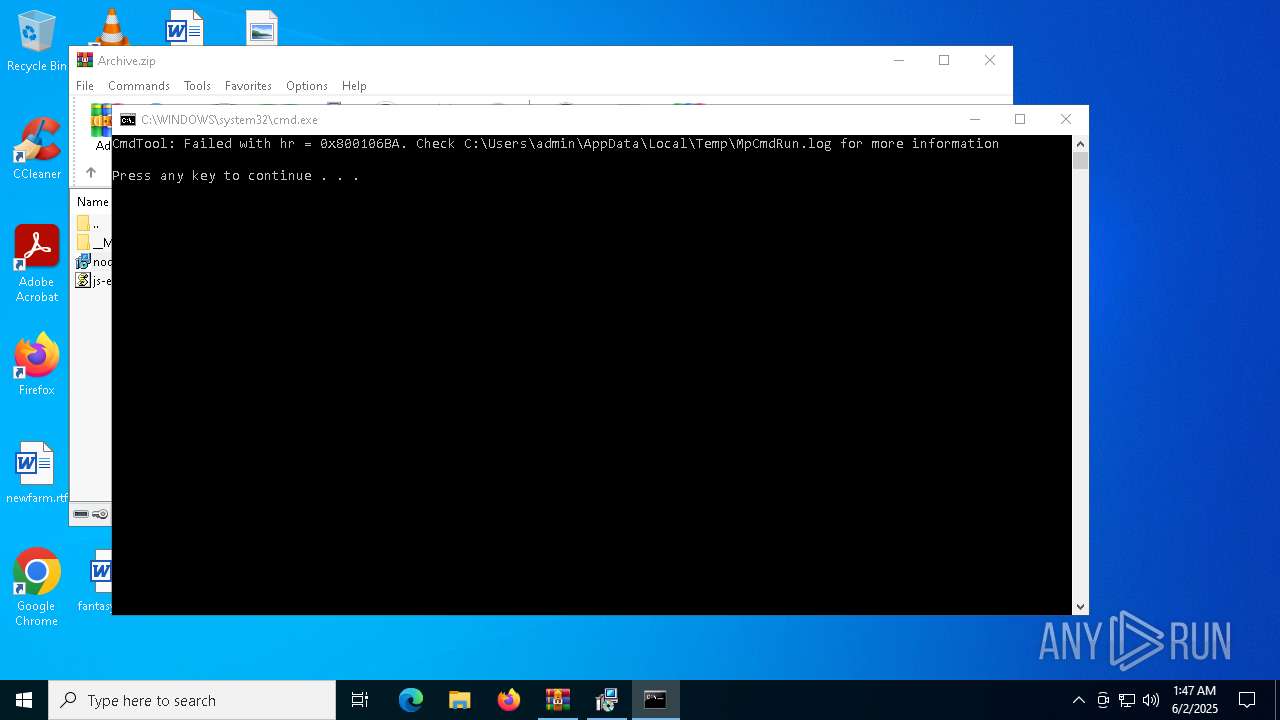
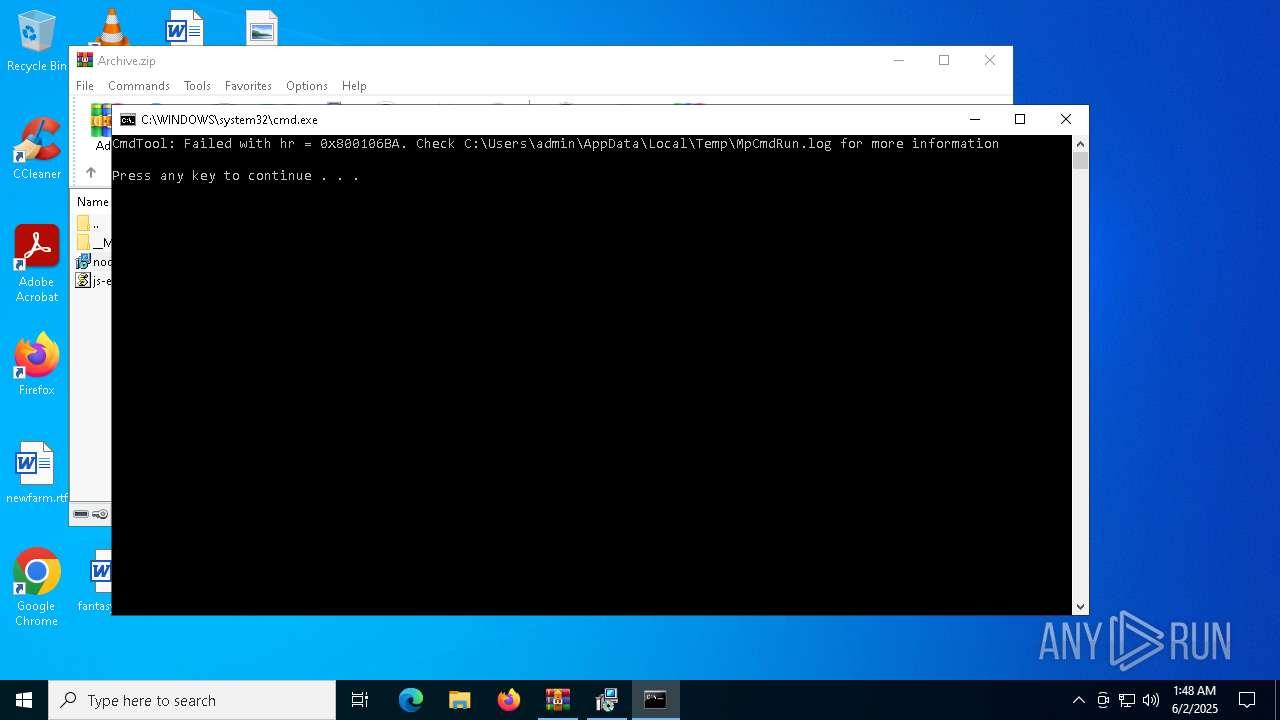
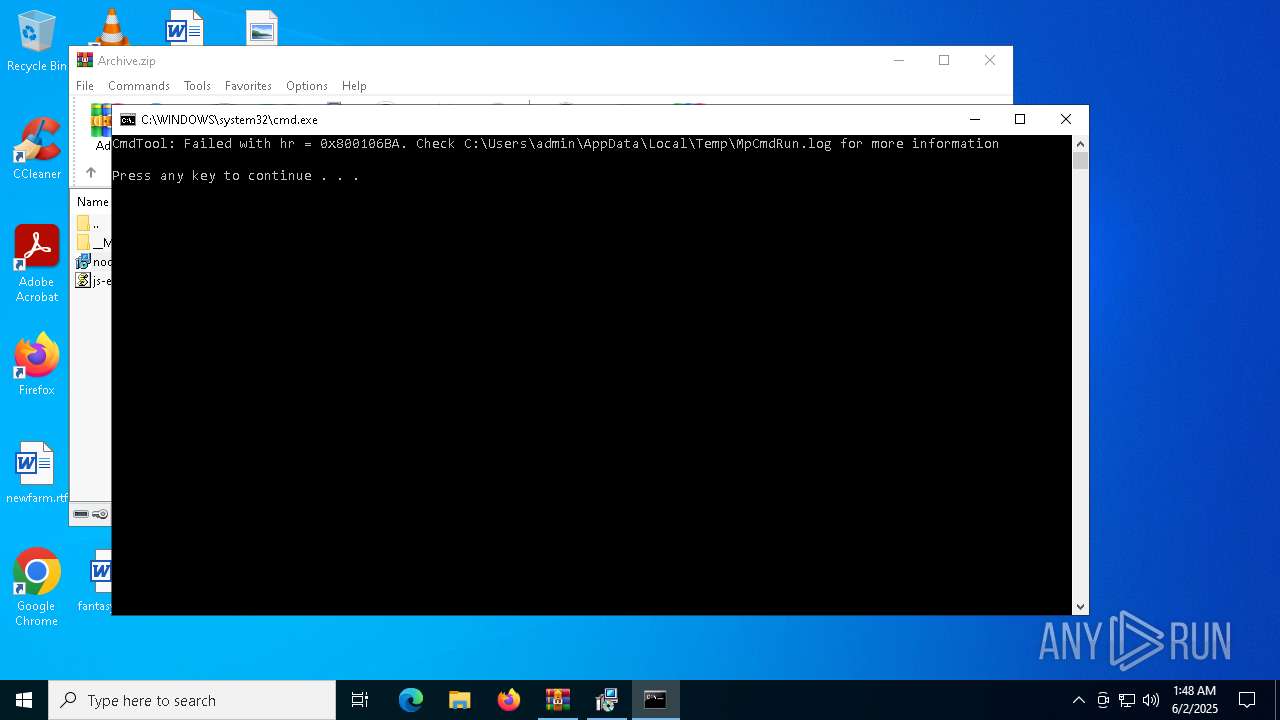
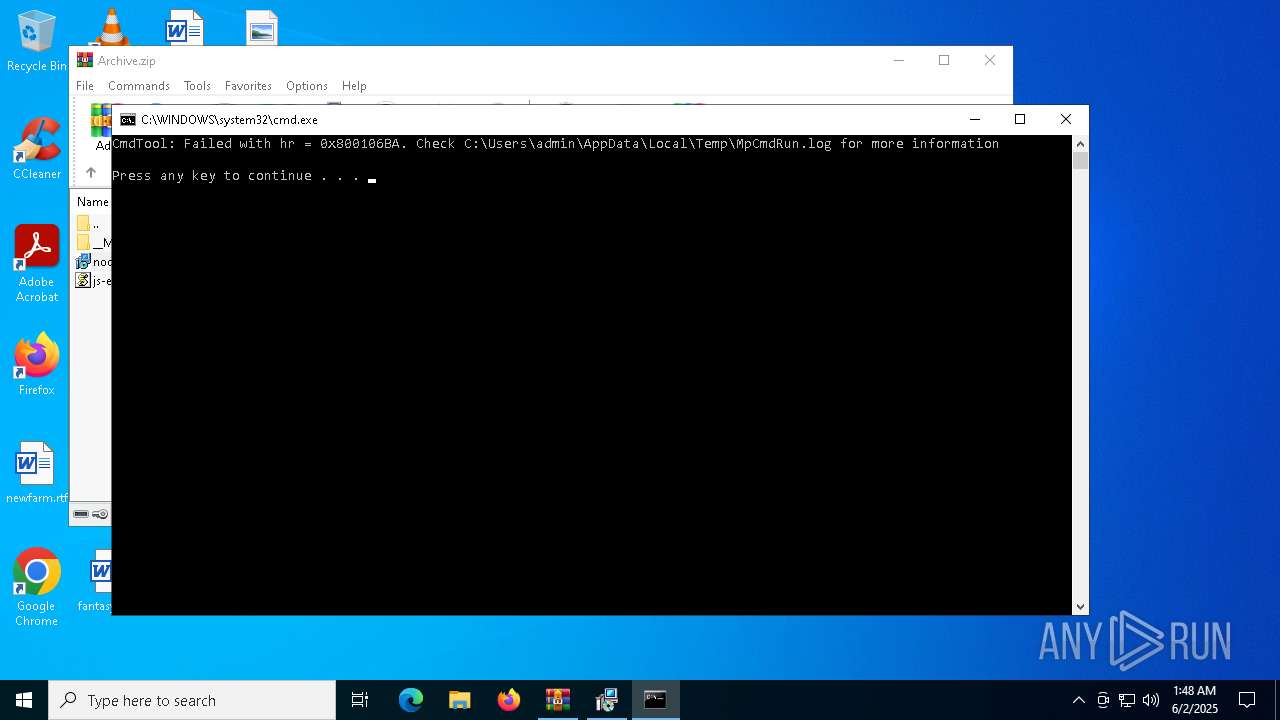
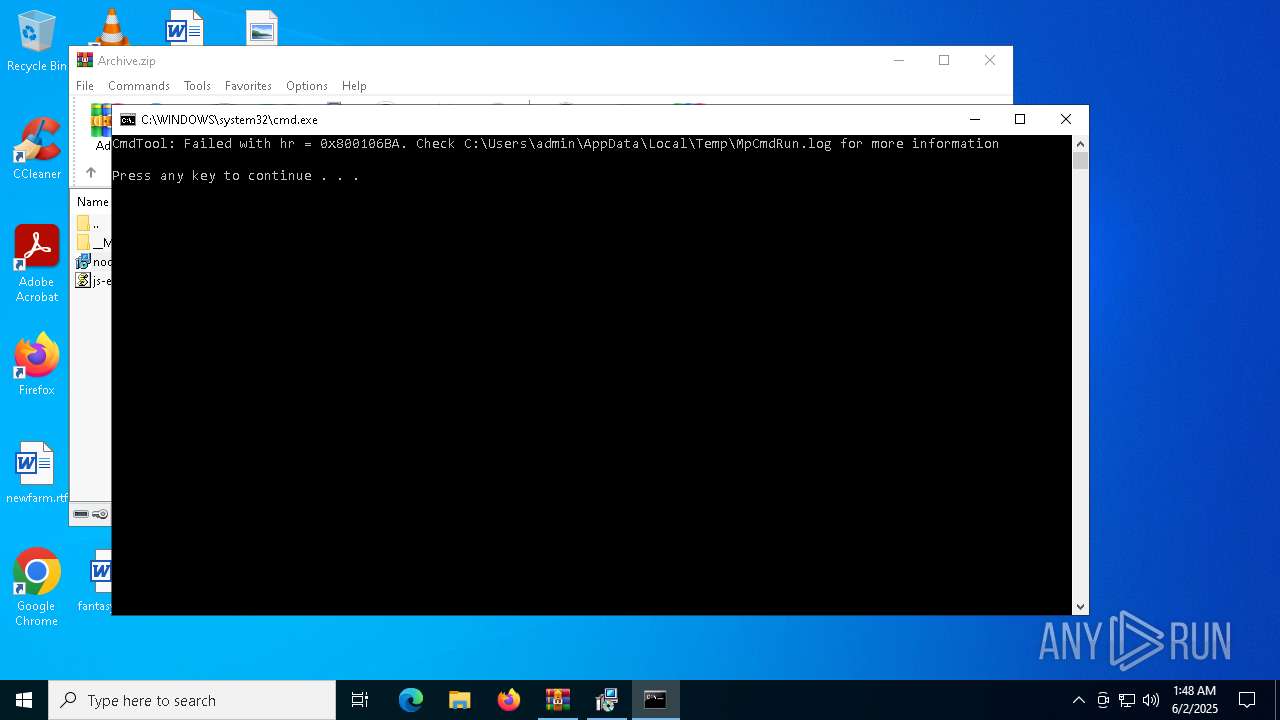
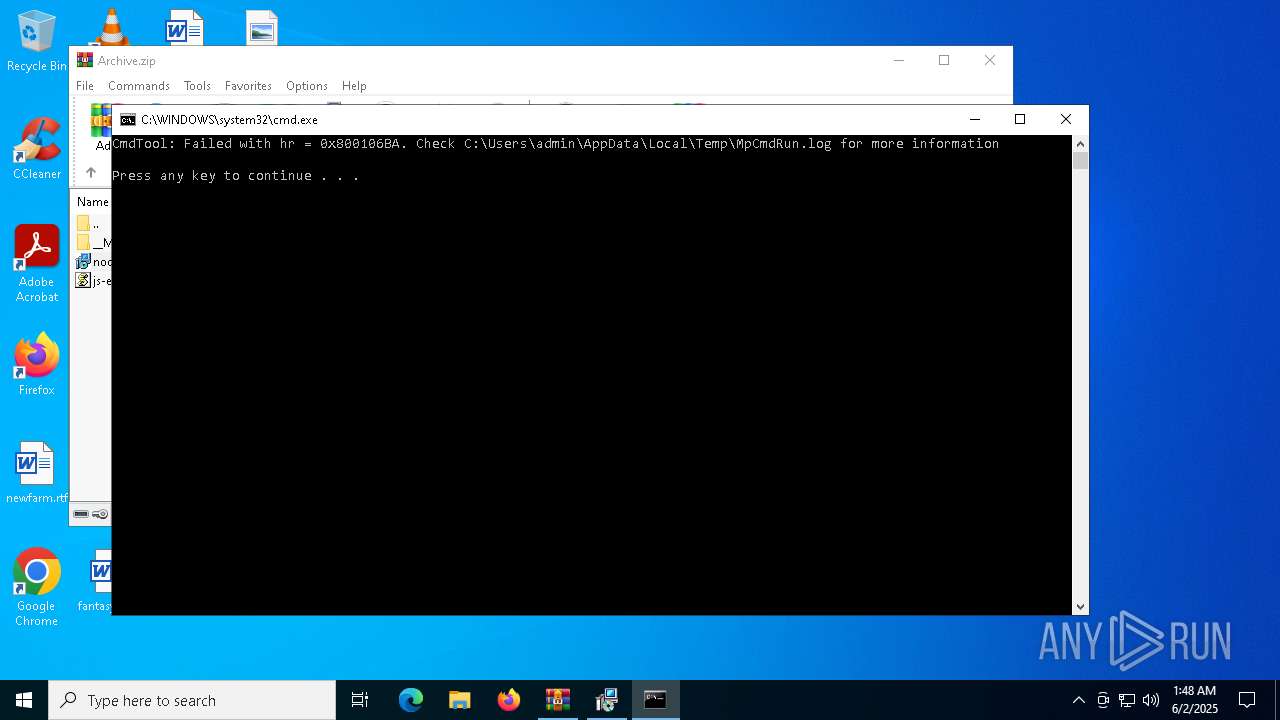
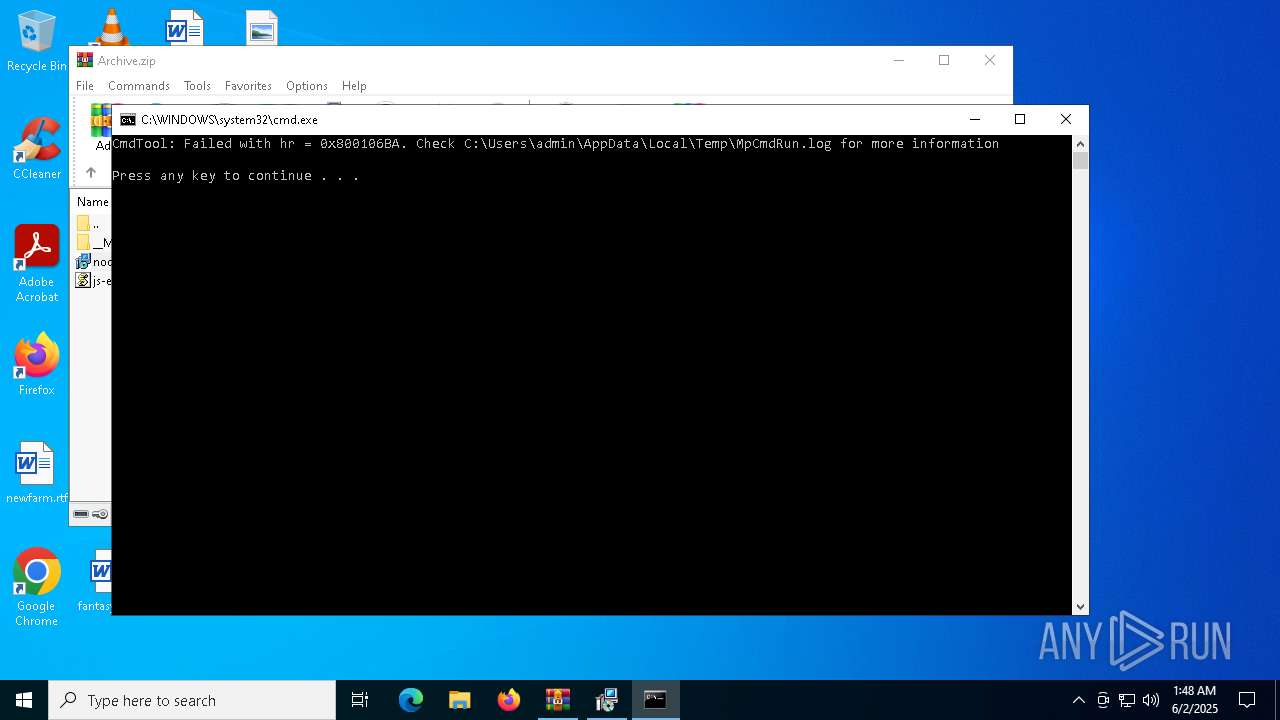
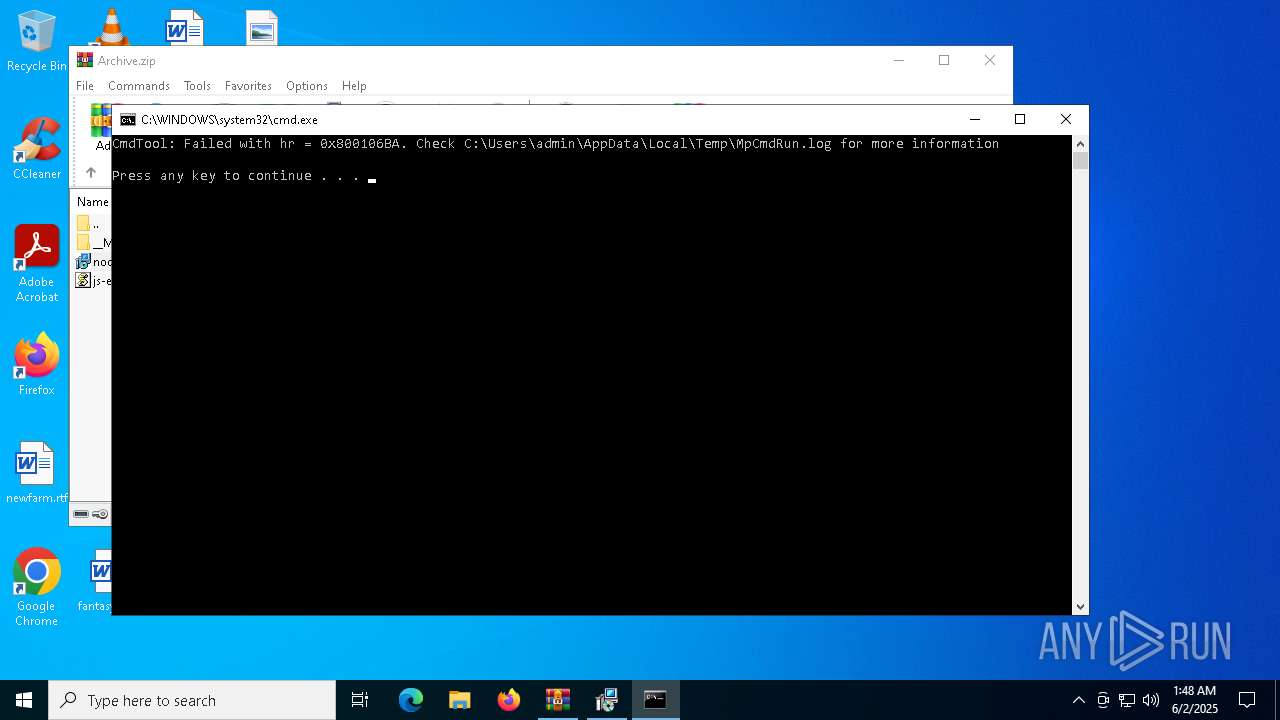
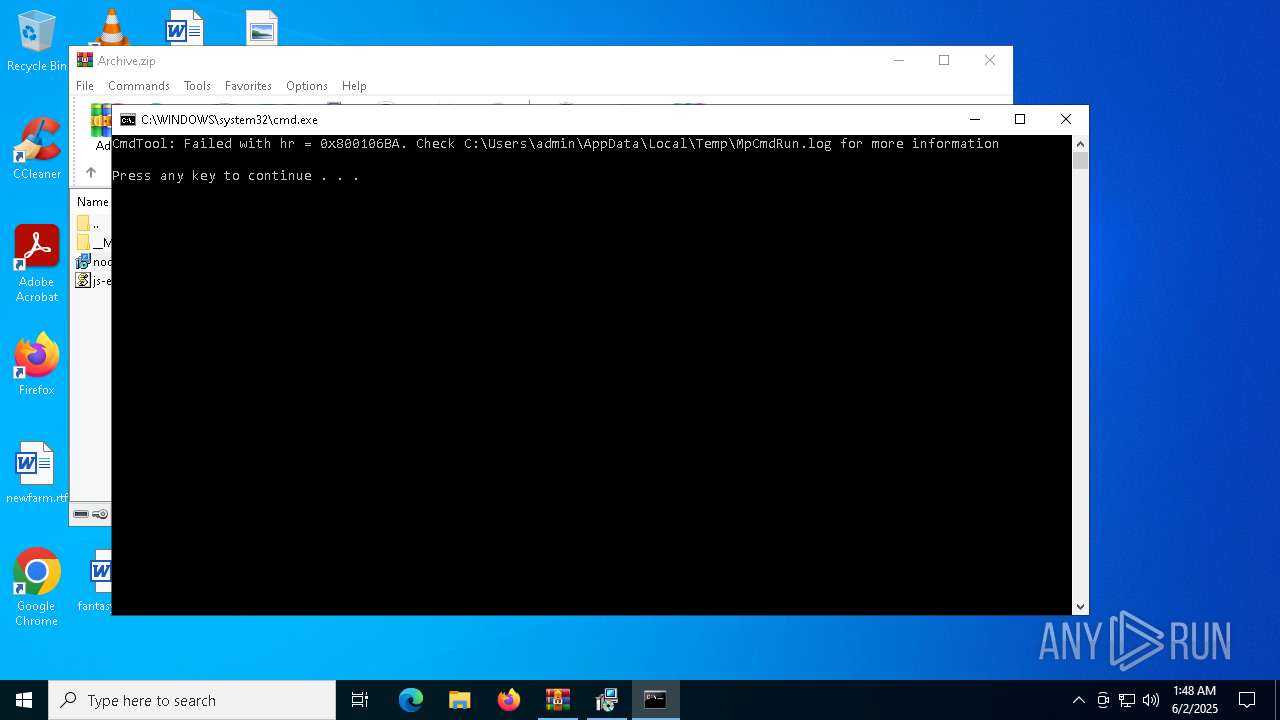
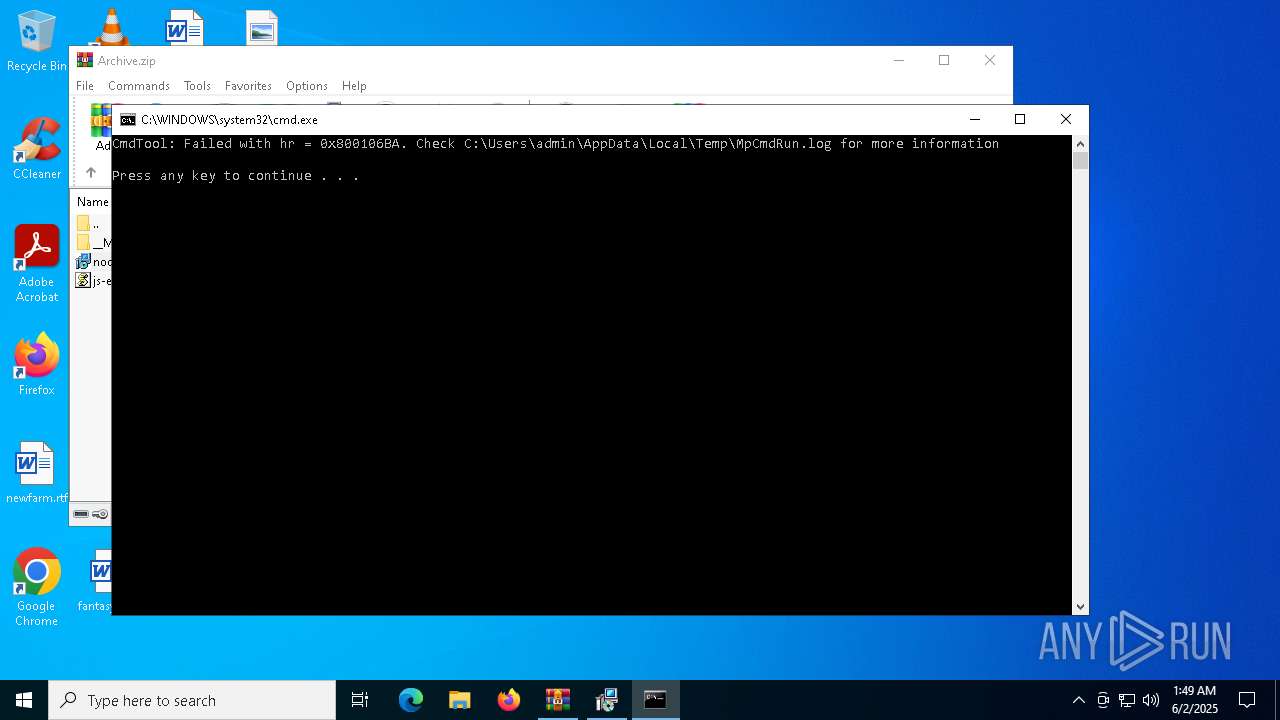
- MpCmdRun.exe (PID: 7268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:04 19:16:20 |
| ZipCRC: | 0xf905d2b5 |
| ZipCompressedSize: | 30378639 |
| ZipUncompressedSize: | 31625216 |
| ZipFileName: | node-v23.11.0-x64.msi |
Total processes
132
Monitored processes
11
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\Desktop\node-v23.11.0-x64.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\js-extracted-1.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1240 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\fd65ef94-1cbc-4d2d-be38-d269f64ead2f | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1472 | C:\Windows\System32\MsiExec.exe -Embedding 2B39C499994682F1833D4F34FCE412AF C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3096 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5360 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\58fe8660-675d-442c-95e7-2255fe82aacb | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5800 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6668 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7048 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Archive.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
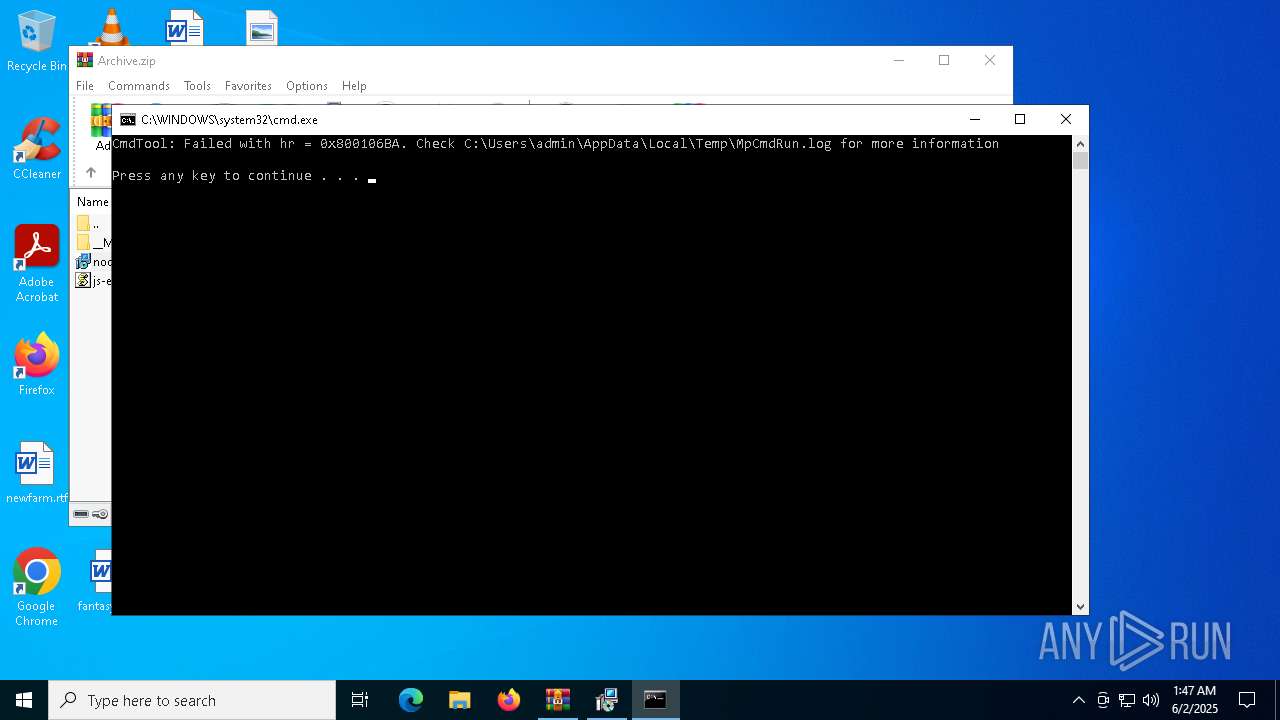
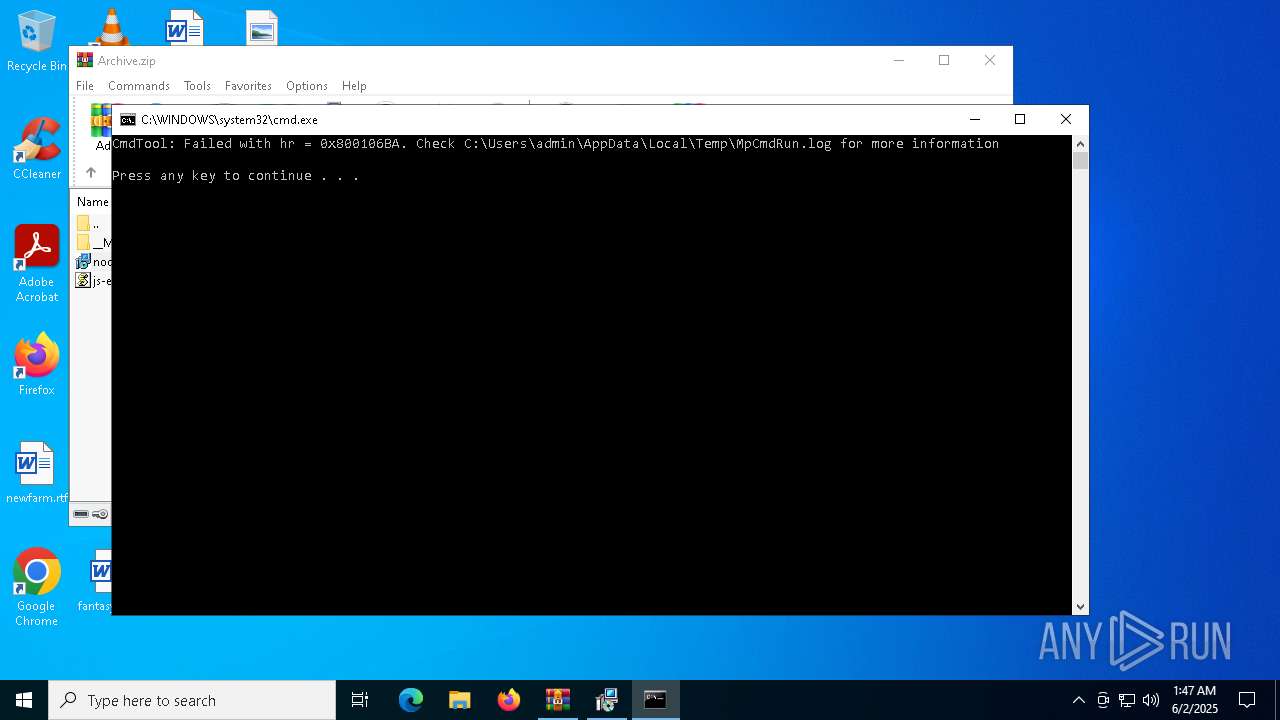
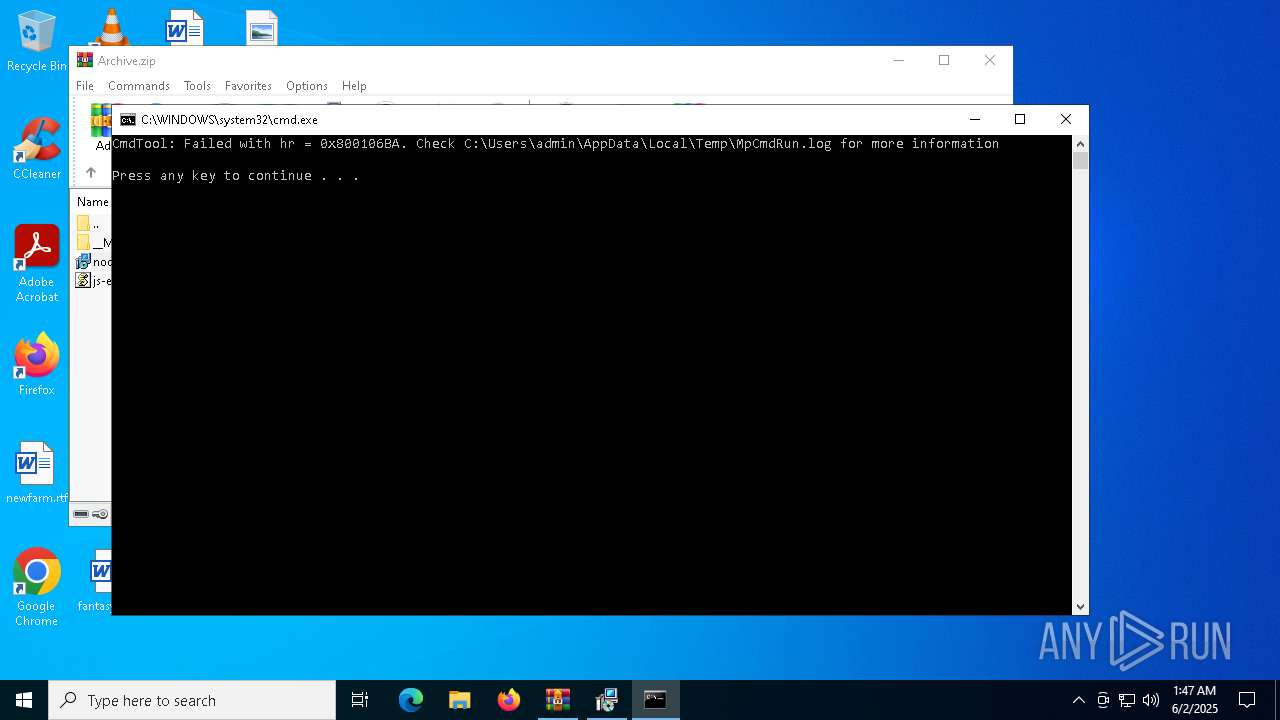
| 7268 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR7048.16468" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 169
Read events
12 155
Write events
14
Delete events
0
Modification events
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Archive.zip | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\System32\msimsg.dll,-34 |
Value: Windows Installer Package | |||
| (PID) Process: | (7048) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
2
Suspicious files
5
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 660 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | — | |
MD5:— | SHA256:— | |||
| 660 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | — | |
MD5:— | SHA256:— | |||
| 660 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_0D7BFF9D231ADDC3439B70E4C5E809D4 | — | |
MD5:— | SHA256:— | |||
| 660 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_0D7BFF9D231ADDC3439B70E4C5E809D4 | — | |
MD5:— | SHA256:— | |||
| 7048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7048.16468\Archive.zip\node-v23.11.0-x64.msi | — | |
MD5:— | SHA256:— | |||
| 7048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7048.16468\Rar$Scan42750.bat | — | |
MD5:— | SHA256:— | |||
| 7268 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | — | |
MD5:— | SHA256:— | |||
| 7048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7048.16468\Archive.zip\__MACOSX\._node-v23.11.0-x64.msi | binary | |
MD5:241F53966AB8C590ADDC7AE8A3F00237 | SHA256:080DDC2640319911C7132AE35AFB6CBA4CFEC9C6B8762B30C6FED2A86468C837 | |||
| 7048 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7048.16468\Archive.zip\js-extracted-1.js | binary | |
MD5:51AD9A30148601EE4E6E7B88EB7D482B | SHA256:CCF35A86928781238D46D0B0B33DB35AD7A03D6AEABFDB8D231CBC4B38F281BB | |||
| 660 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:1ADE33BA1718F8A8531CCB6D30F05916 | SHA256:4F77C65ED4068A54CA9B14D935FA700AAB5C3740C6FF9B81CE1A66D16DF6FBED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
21
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5056 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
660 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
660 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
5056 | RUXIMICS.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
660 | msiexec.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAJLAwSPdlGs15jn8KEgl8A%3D | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5056 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5056 | RUXIMICS.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5056 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
660 | msiexec.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7052 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6668 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |