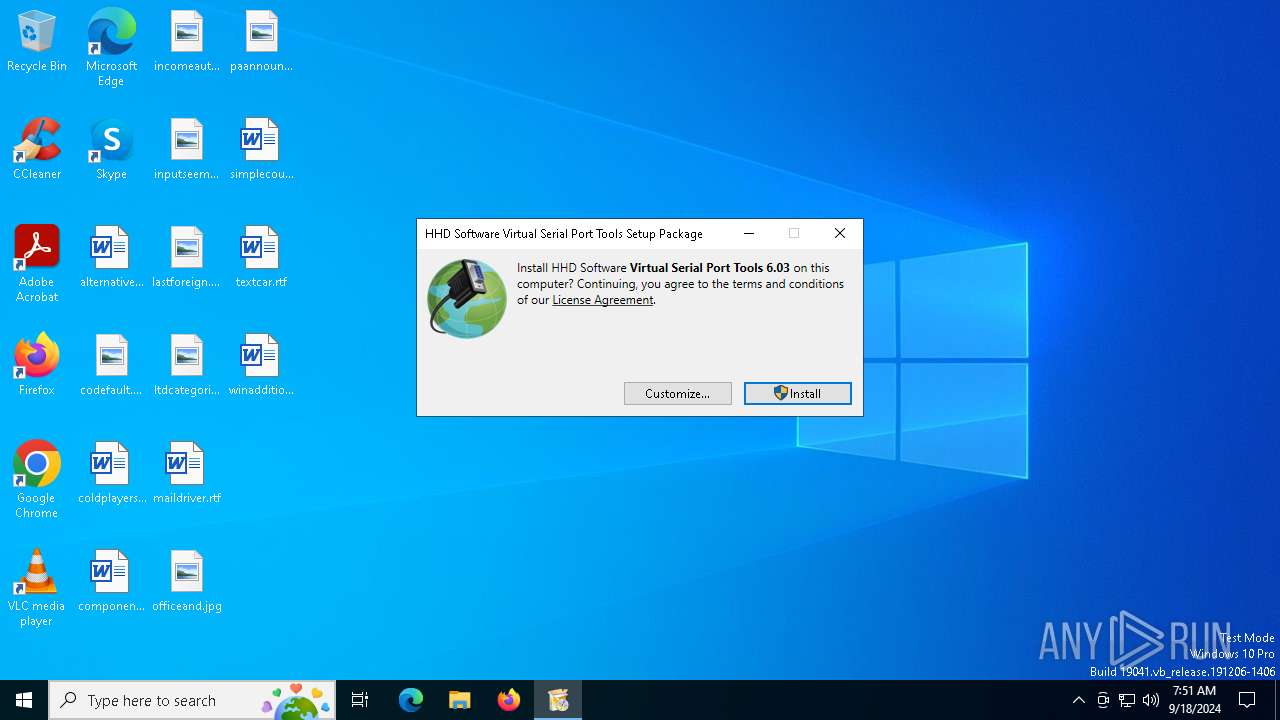
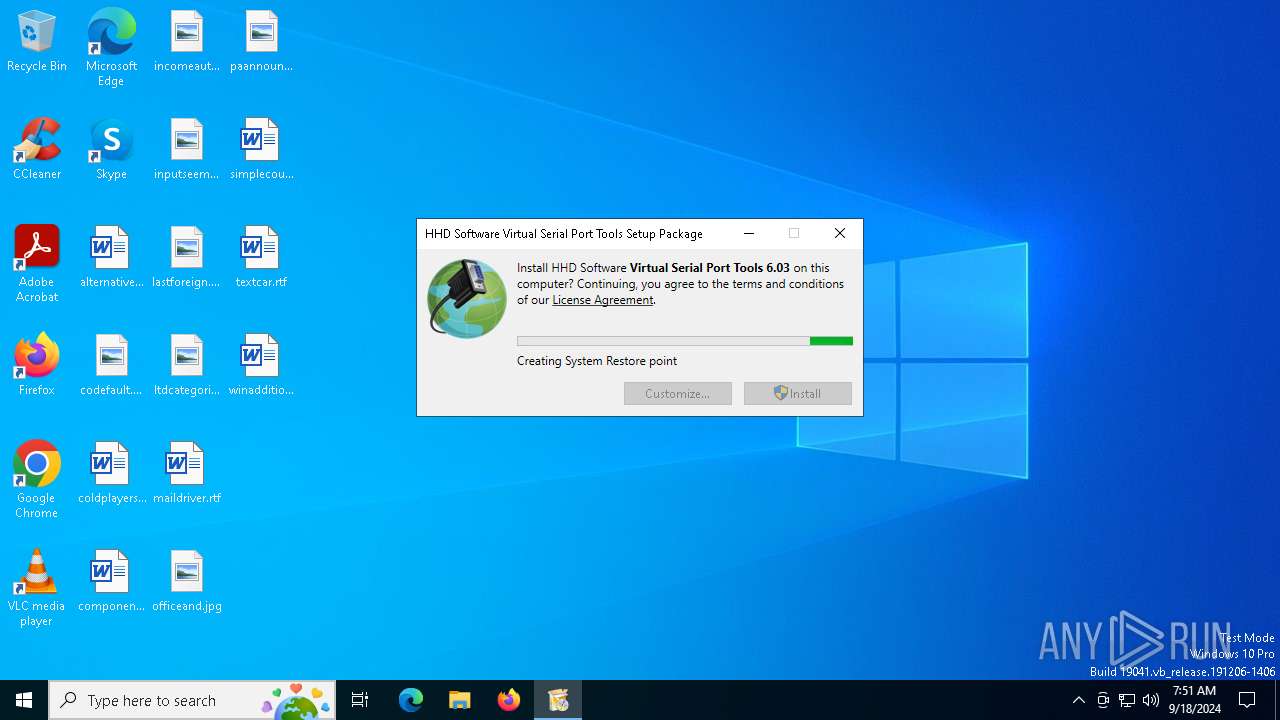
| File name: | free-virtual-serial-port-tools(1).exe |
| Full analysis: | https://app.any.run/tasks/0274c31b-53c4-4161-b6fe-7261b5c0bb90 |
| Verdict: | Malicious activity |
| Analysis date: | September 18, 2024, 07:51:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 65ECF5996DB6D672826D98D4658EDEF5 |
| SHA1: | C3633162C6C7B7A64DD5F04D165D324C25AE36A9 |
| SHA256: | 79F235B457ECB489FE9499485BE50D09A51FD25ABB51C1AFADF8D59B2FC80B46 |
| SSDEEP: | 98304:3uhicp9GarsEfBX3P6KgRywIvjOCON/dyBLjSVaBg+uPRqgODIyhWwoZy2vFRXad:OB4wKxVtvv4gjpK/WVWx |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- drvinst.exe (PID: 5552)
- setup.exe (PID: 4976)
- free-virtual-serial-port-tools(1).exe (PID: 6356)
Application launched itself
- setup.exe (PID: 6856)
INFO
Application launched itself
- msedge.exe (PID: 5104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:03 11:36:59+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 70144 |
| InitializedDataSize: | 68096 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x7de0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.3.0.1321 |
| ProductVersionNumber: | 6.3.0.1321 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | HHD Software Ltd. |
| FileDescription: | Virtual Serial Port Tools Installation Package |
| FileVersion: | 6.03.00.1321 |
| LegalCopyright: | © 2018 - 2024 by HHD Software Ltd. All rights reserved. |
| InternalName: | setup.exe |
| OriginalFileName: | setup.exe |
| ProductName: | Virtual Serial Port Tools |
| ProductVersion: | 6.03.00.1321 |
Total processes
172
Monitored processes
40
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1048 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3636 --field-trial-handle=2388,i,18275769241577326399,2890648372876365517,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1076 | "C:\Program Files\HHD Software\Virtual Serial Port Tools\vspcfg.exe" | C:\Program Files\HHD Software\Virtual Serial Port Tools\vspcfg.exe | setup.exe | ||||||||||||
User: admin Company: HHD Software Ltd. Integrity Level: HIGH Description: Virtual Serial Port Tools Configuration Utility Version: 6.03.00.1321 Modules
| |||||||||||||||
| 1776 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x2ec,0x2f0,0x2f4,0x2e8,0x2fc,0x7fffd3df5fd8,0x7fffd3df5fe4,0x7fffd3df5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2264 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2376 | "C:\Program Files\HHD Software\Virtual Serial Port Tools\psip_server.exe" | C:\Program Files\HHD Software\Virtual Serial Port Tools\psip_server.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: HHD Software Ltd. Integrity Level: SYSTEM Description: TCP/IP Serial Ports Server Application Version: 6.03.00.1321 Modules
| |||||||||||||||
| 2976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3316 | "C:\Program Files\HHD Software\Virtual Serial Port Tools\vspcfg.exe" | C:\Program Files\HHD Software\Virtual Serial Port Tools\vspcfg.exe | — | setup.exe | |||||||||||
User: admin Company: HHD Software Ltd. Integrity Level: MEDIUM Description: Virtual Serial Port Tools Configuration Utility Exit code: 3221226540 Version: 6.03.00.1321 Modules
| |||||||||||||||
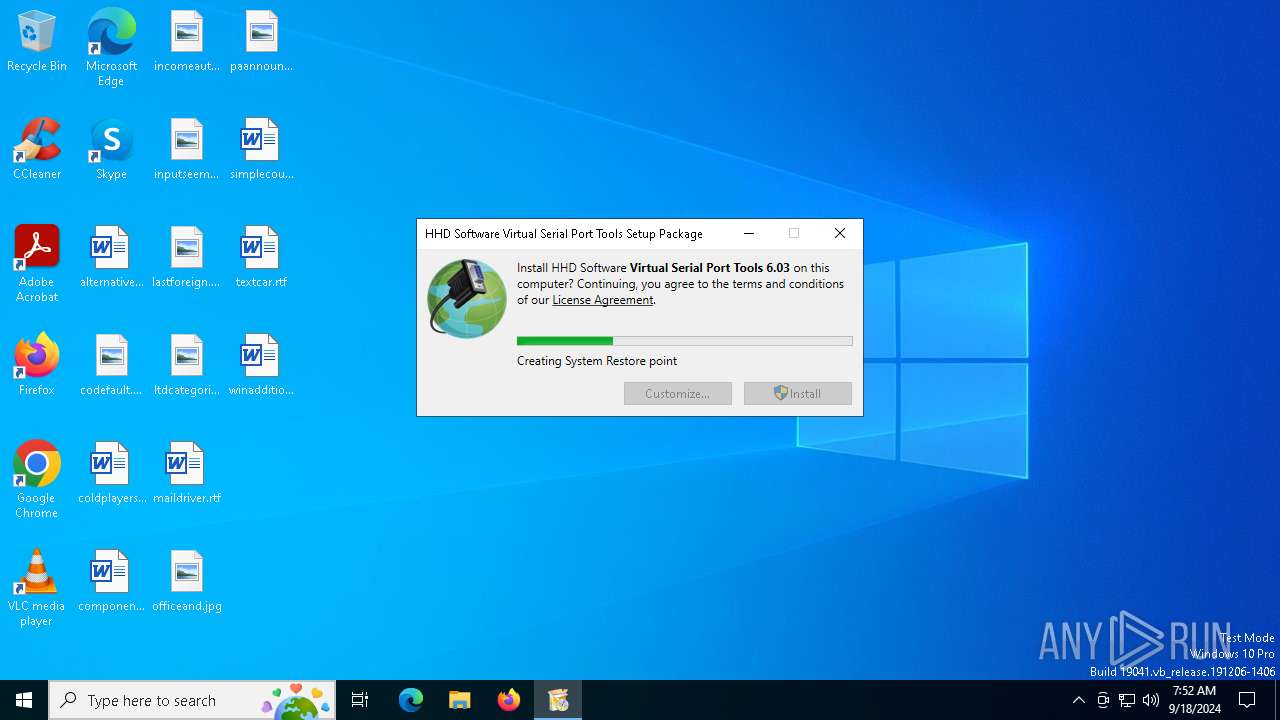
| 4976 | "C:\Users\admin\AppData\Local\Temp\7zFC43C8D4\setup.exe" -machine -silent --allow-error --type 1 --server {C128E9BE-00D7-4693-9A85-F0462AF7533E} --source "C:\Users\admin\AppData\Local\Temp\7zFC43C8D4" | C:\Users\admin\AppData\Local\Temp\7zFC43C8D4\setup.exe | setup.exe | ||||||||||||
User: admin Company: HHD Software Ltd. Integrity Level: HIGH Description: Virtual Serial Port Tools Installation Package Exit code: 0 Version: 6.03.00.1321 Modules
| |||||||||||||||
| 5000 | "C:\Program Files\HHD Software\Virtual Serial Port Tools\ps_server.exe" | C:\Program Files\HHD Software\Virtual Serial Port Tools\ps_server.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: HHD Software Ltd. Integrity Level: SYSTEM Description: Remote Serial Ports Server Application Version: 6.03.00.1321 Modules
| |||||||||||||||
| 5104 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://www.hhdsoftware.com/dispatch/vspt/release-notes?version=6.03.00.01321 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
11 112
Read events
10 659
Write events
426
Delete events
27
Modification events
| (PID) Process: | (4976) setup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000AF322AA09F09DB0170130000C00F0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4976) setup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000AF322AA09F09DB0170130000C00F0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4976) setup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000079E9CA09F09DB0170130000C00F0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4976) setup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000079E9CA09F09DB0170130000C00F0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4976) setup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000008F2CA6A09F09DB0170130000C00F0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4976) setup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000BA90A8A09F09DB0170130000C00F0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4976) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (4976) setup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000EFC13EA19F09DB0170130000C00F0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4976) setup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000D68943A19F09DB017013000088150000E80300000100000000000000000000008BA0ED69F1AA464994A0767EC65616F100000000000000000000000000000000 | |||
| (PID) Process: | (2264) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000001D6A4FA19F09DB01D80800008C1B0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
84
Suspicious files
235
Text files
64
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6356 | free-virtual-serial-port-tools(1).exe | C:\Users\admin\AppData\Local\Temp\7zFC43C8D4\{150A905B-EF26-4780-9315-63DE2CA08DD6}.7z | — | |
MD5:— | SHA256:— | |||
| 6356 | free-virtual-serial-port-tools(1).exe | C:\Users\admin\AppData\Local\Temp\7zFC43C8D4\config.ini | text | |
MD5:BAE8294CA49708DED3FF6AF16EE09213 | SHA256:3E404775E0BAF04672D4BA14AD4278D81EC8F9757DA33E06E7D898E0EB079303 | |||
| 4976 | setup.exe | C:\Users\admin\AppData\Local\Temp\{6555B11C-1702-4BDD-895D-46D723BBDBFB}\Components\drvreg_win10\psharedrv_x64.cat | binary | |
MD5:151B3FBE12C761C2300072634B85B20C | SHA256:3F6C49D50D51B41946C678E4869FE7422F996043ACC205B55B8D946A3B9E790B | |||
| 4976 | setup.exe | C:\Users\admin\AppData\Local\Temp\{6555B11C-1702-4BDD-895D-46D723BBDBFB}\Components\cppheader\clientctl.tlh | text | |
MD5:C61030211D570EA47DB71EE0B43DEB74 | SHA256:89949A91862DE7754A6F4B2669FA3B0B235E57BFD677F3BF23B26B5011FE258E | |||
| 6356 | free-virtual-serial-port-tools(1).exe | C:\Users\admin\AppData\Local\Temp\7zFC43C8D4\xp.url | text | |
MD5:57A82C02A8C57AA84EAE2B69A3749A18 | SHA256:1B11912F7649E45BC495673707AE5B1070CCB6959918DC9018082033542E39B0 | |||
| 4976 | setup.exe | C:\Users\admin\AppData\Local\Temp\{6555B11C-1702-4BDD-895D-46D723BBDBFB}\Components\cppheader\clientctl.tli | text | |
MD5:39F097722645B7C553210249729CBB58 | SHA256:1A0DA0FCA15F8FAF36551F72BB92A870BA254619C6D1BD62915AD547D45B9BB9 | |||
| 4976 | setup.exe | C:\Users\admin\AppData\Local\Temp\{6555B11C-1702-4BDD-895D-46D723BBDBFB}\Components\hhdvspkit32.dll\hhdvspkit.dll.rgs | text | |
MD5:AE5DBB26B2BBB3F563999490709E34BC | SHA256:011A4542BFDA8A1DF1309B55CDEABB1108CC1F6F972BAEF392D7F54E5E8BB741 | |||
| 6356 | free-virtual-serial-port-tools(1).exe | C:\Users\admin\AppData\Local\Temp\7zFC43C8D4\setup.exe | executable | |
MD5:0DB80F36674854118A68ADE96FE88FE6 | SHA256:CA2FD7B751BE066CA1C47559CF69403092B29C1CEB6F37C6837C46DA98B0C0D6 | |||
| 4976 | setup.exe | C:\Users\admin\AppData\Local\Temp\{6555B11C-1702-4BDD-895D-46D723BBDBFB}\Components\drvreg_win8\psharedrv.inf | binary | |
MD5:7D51E4868D171E97FEE74FEF35D34B7D | SHA256:8C17ABDC3392218E57E8B39046761D317EF1FCF10FE0DE0A52E9C455665D9572 | |||
| 4976 | setup.exe | C:\Users\admin\AppData\Local\Temp\{6555B11C-1702-4BDD-895D-46D723BBDBFB}\Components\drvreg_win10\psharedrv_x86.cat | binary | |
MD5:17643B24390D0771D9D564FCDFE660BA | SHA256:E157D765A07B6DAA4FD406692E482A27F9CCD8E6938FD1AC7542004C294072CE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
57
DNS requests
51
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1076 | vspcfg.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
1076 | vspcfg.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEBN9U5yqfDGppDNwGWiEeo0%3D | unknown | — | — | whitelisted |
6264 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6840 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6840 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
368 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4200 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.189.173.16:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 2.23.209.191:443 | — | Akamai International B.V. | GB | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4324 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
www.hhdsoftware.com |
| unknown |