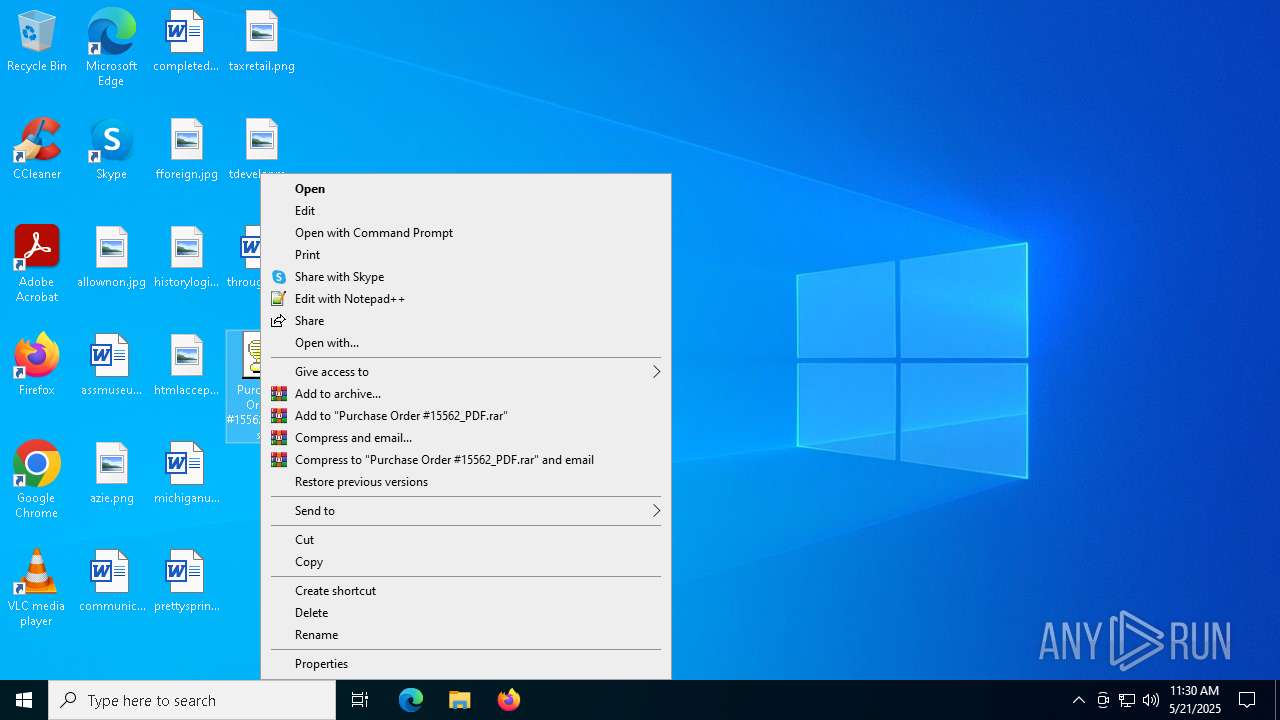
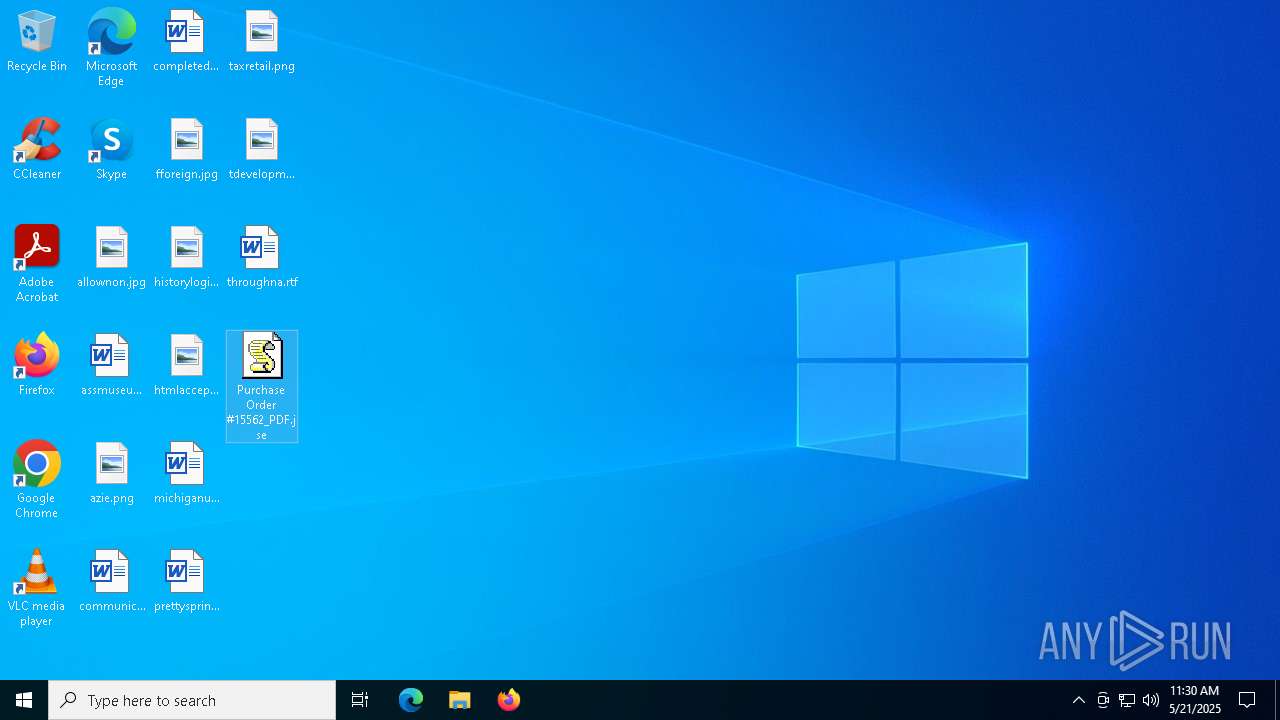
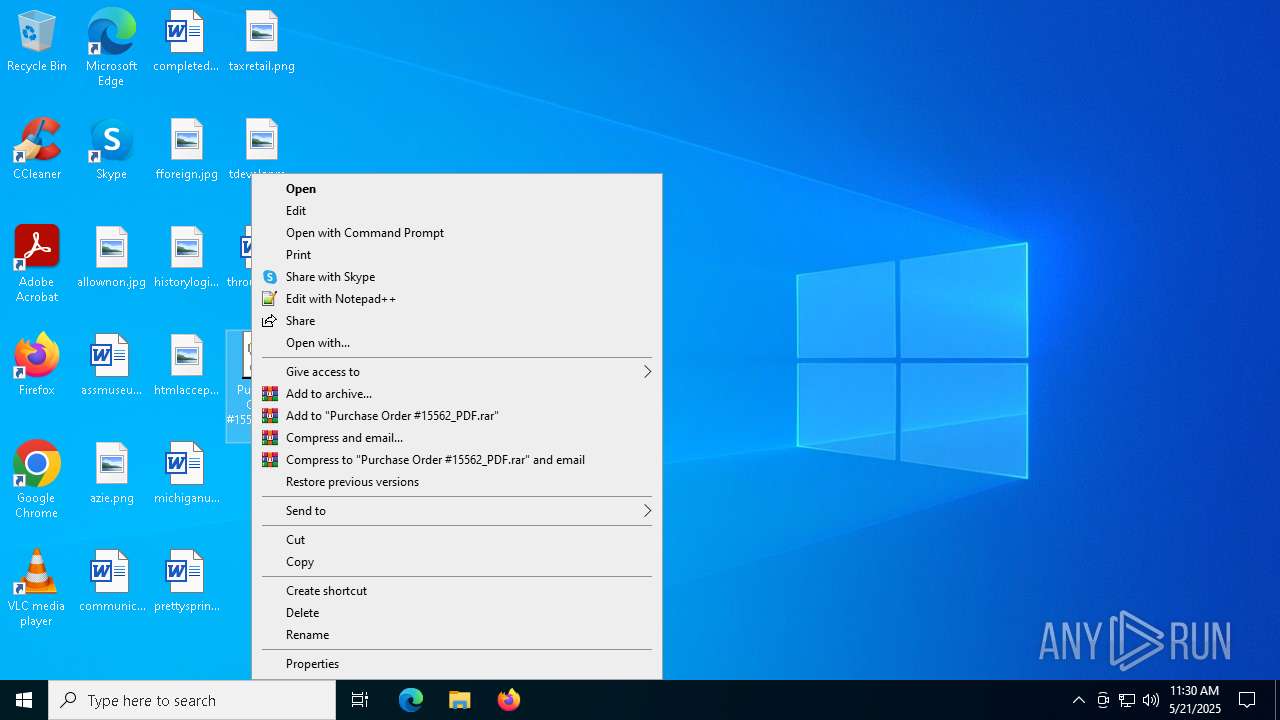
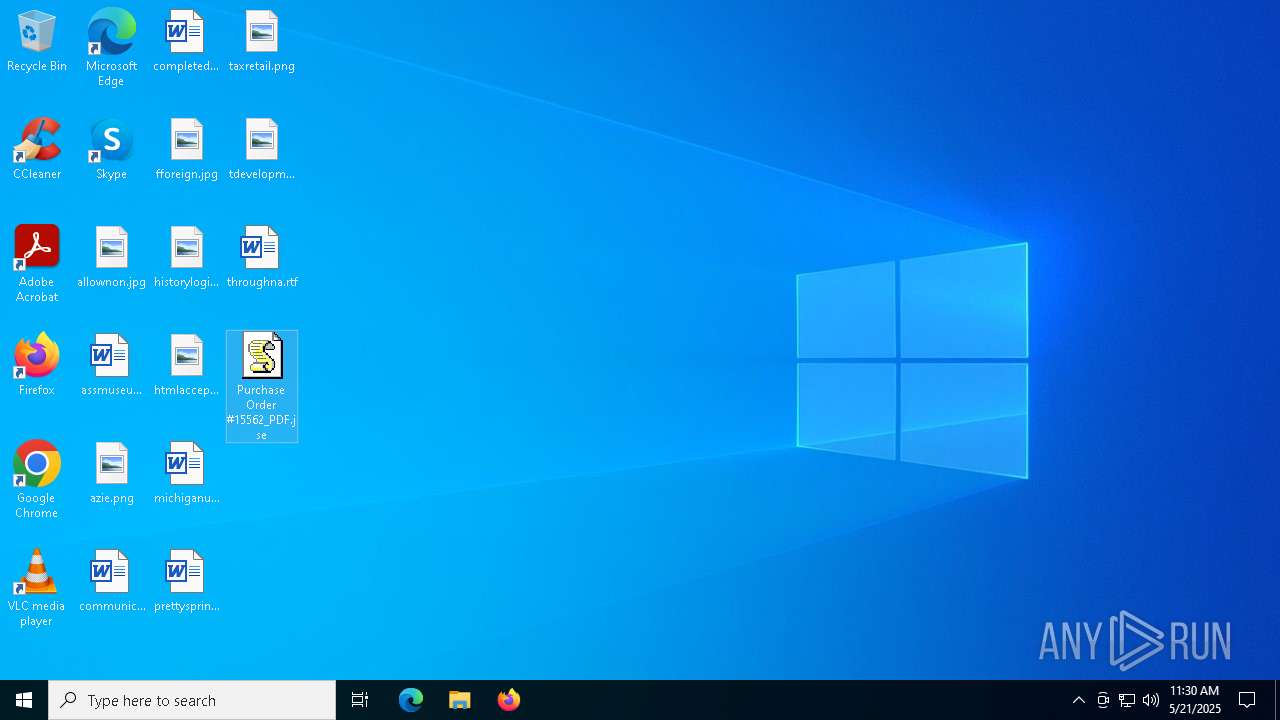
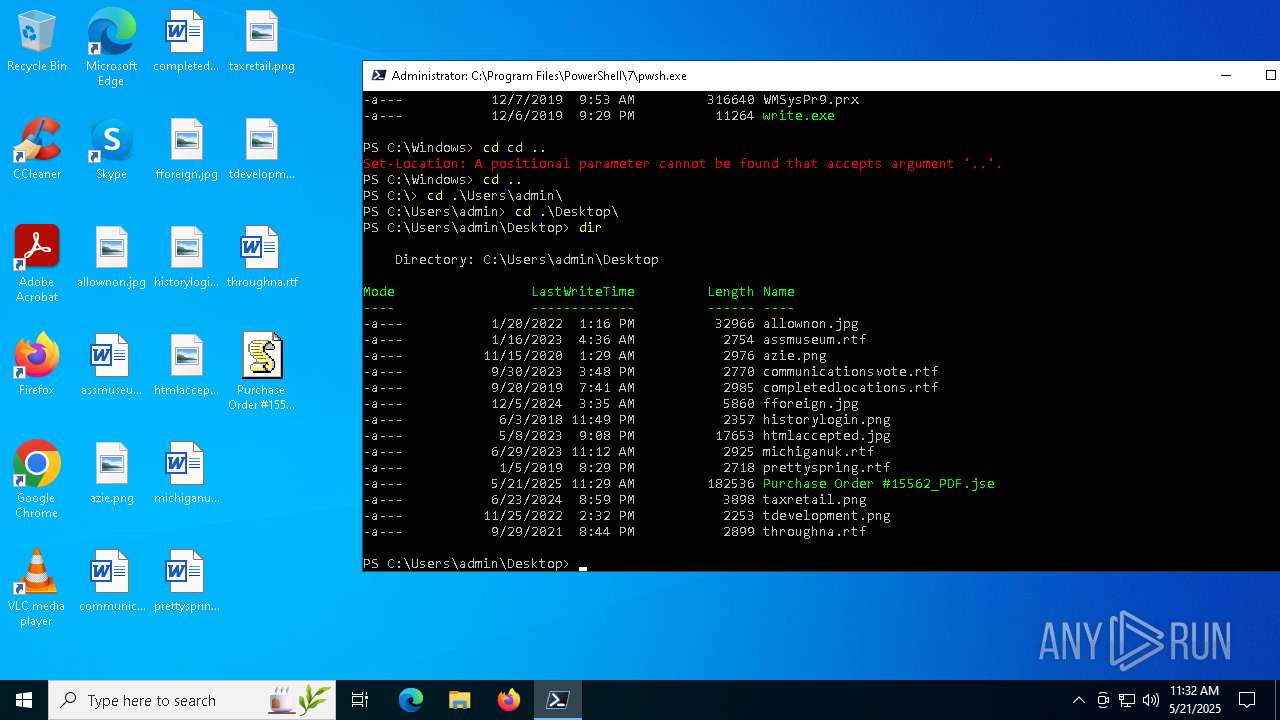
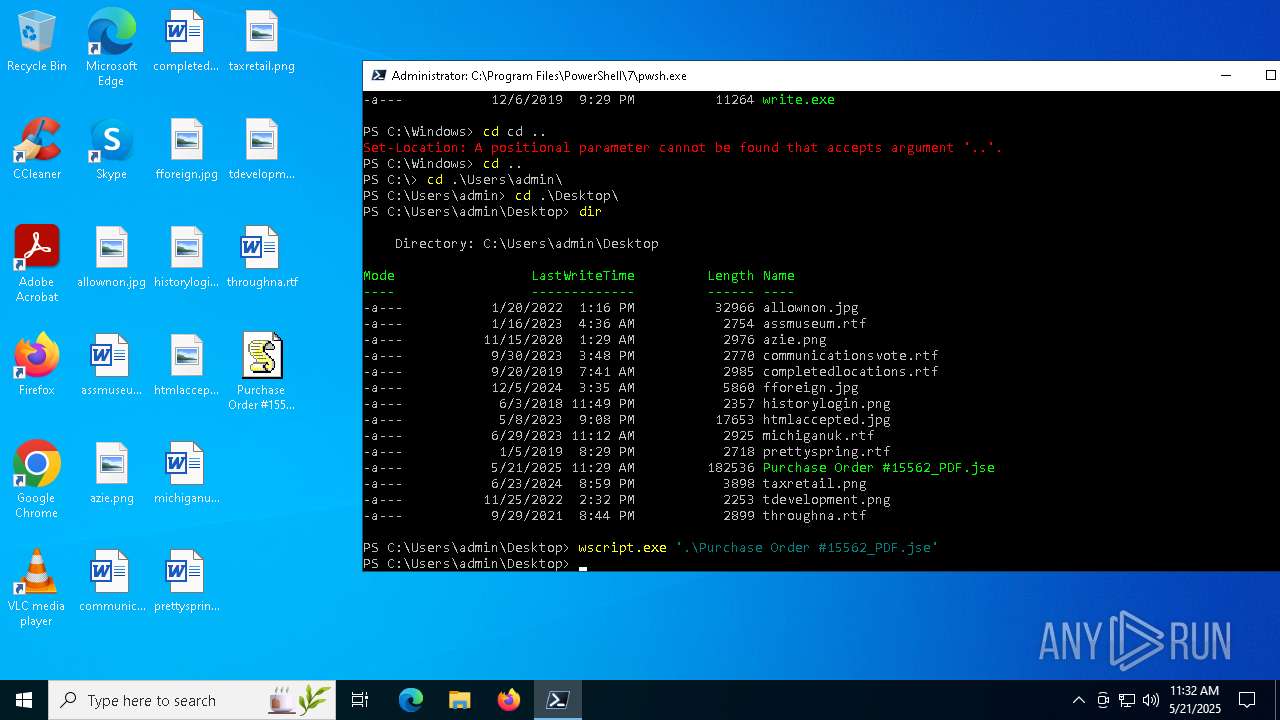
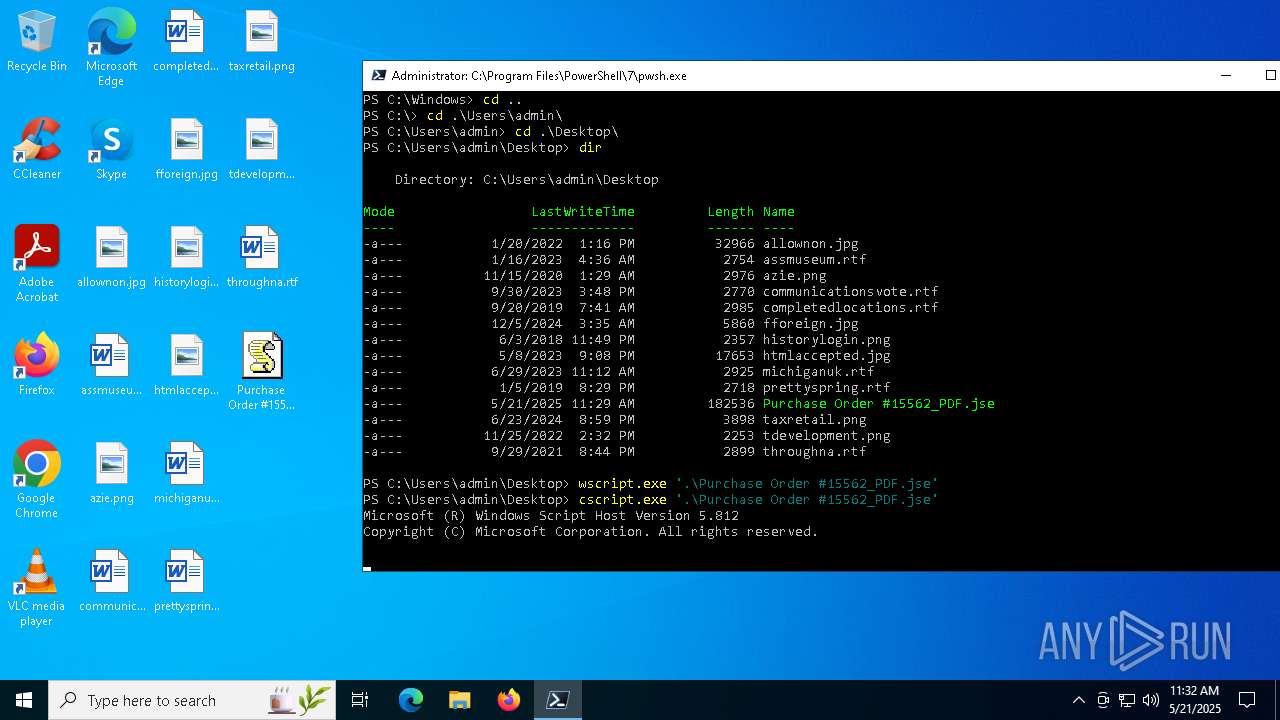
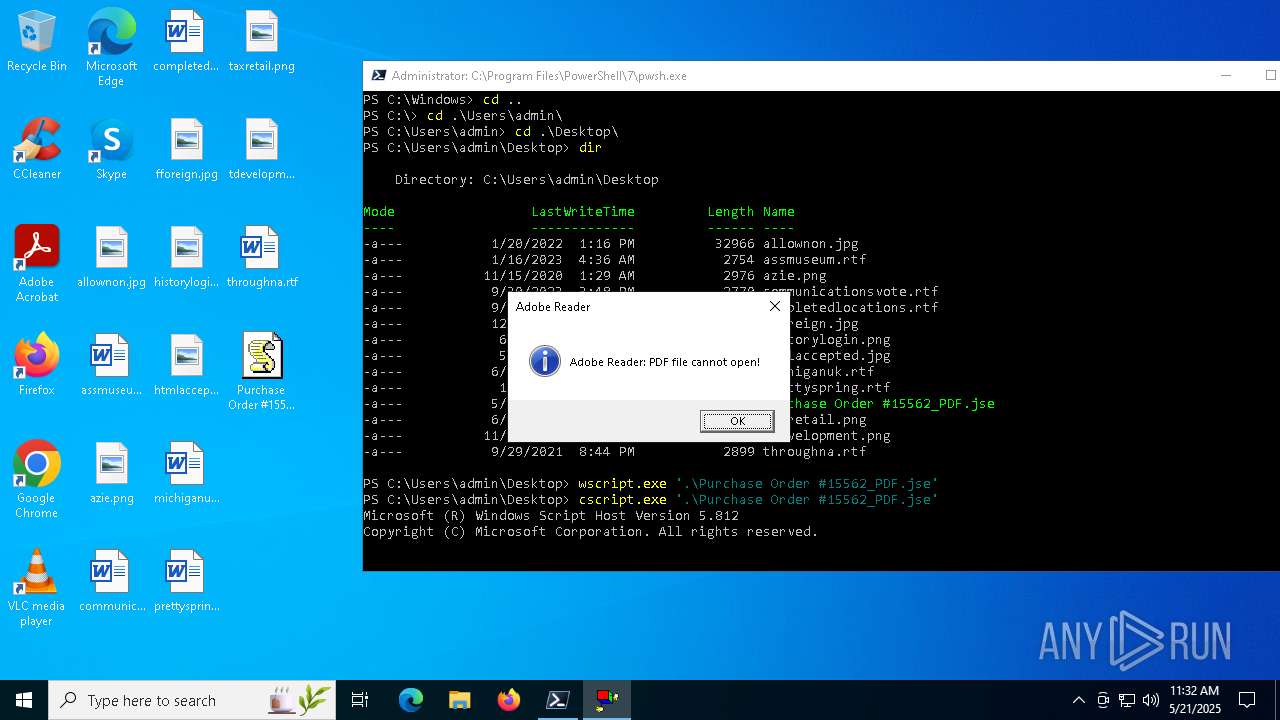
| File name: | Purchase Order #15562_PDF.jse |
| Full analysis: | https://app.any.run/tasks/3bb6b269-5395-4e58-af61-eea68a24cf6a |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2025, 11:29:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 80D51609822D384D88CC6F5622CB8507 |
| SHA1: | 4F9DD2C2BDF8927094F65FEC0F48AC5BA7DA9C6B |
| SHA256: | 79E25DA8DD8A8D797DE516BAB3372E550025FCAF20DC7CA3E706C92B4F3C550B |
| SSDEEP: | 3072:LhdbICPqyqotQxDmvaQi06JYtd39tKpV+uhlHK5m9ZvxbGWA7/sGUwuQY3q71wYG:Lhd27WaVJa9srljJvxCWA7sG2O13R0f/ |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6708)
- cscript.exe (PID: 4980)
- wscript.exe (PID: 4236)
- wscript.exe (PID: 5776)
SUSPICIOUS
Reads the date of Windows installation
- pwsh.exe (PID: 4988)
The process executes via Task Scheduler
- pwsh.exe (PID: 4988)
INFO
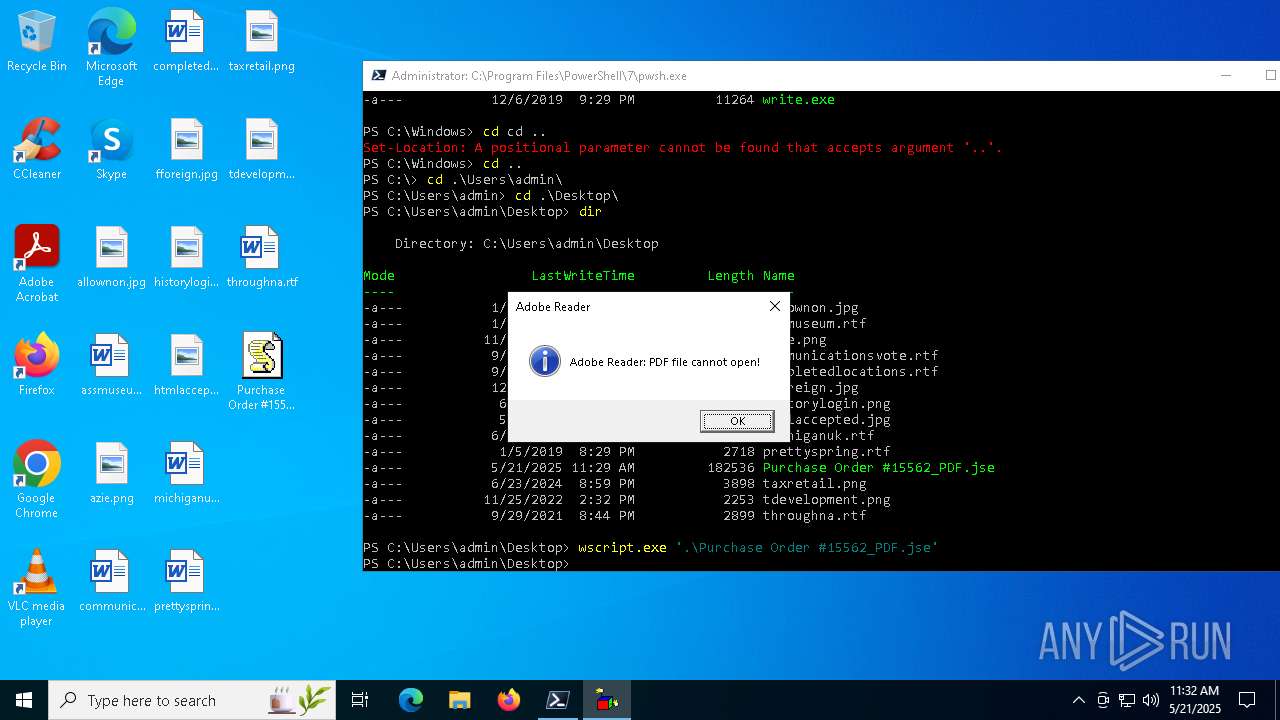
Drops encrypted JS script (Microsoft Script Encoder)
- wscript.exe (PID: 6708)
- wscript.exe (PID: 5776)
- wscript.exe (PID: 4236)
- pwsh.exe (PID: 4988)
- cscript.exe (PID: 4980)
Manual execution by a user
- wscript.exe (PID: 5776)
Checks supported languages
- pwsh.exe (PID: 4988)
Reads the computer name
- pwsh.exe (PID: 4988)
Reads the software policy settings
- slui.exe (PID: 6592)
Checks proxy server information
- slui.exe (PID: 6592)
Process checks computer location settings
- pwsh.exe (PID: 4988)
Reads security settings of Internet Explorer
- cscript.exe (PID: 4980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
142
Monitored processes
8
Malicious processes
1
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | pwsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3332 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 4236 | "C:\WINDOWS\system32\wscript.exe" ".\Purchase Order #15562_PDF.jse" | C:\Windows\System32\wscript.exe | — | pwsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4980 | "C:\WINDOWS\system32\cscript.exe" ".\Purchase Order #15562_PDF.jse" | C:\Windows\System32\cscript.exe | — | pwsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4988 | "C:\Program Files\PowerShell\7\pwsh.exe" | C:\Program Files\PowerShell\7\pwsh.exe | RuntimeBroker.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: pwsh Version: 7.3.5.500 Modules
| |||||||||||||||
| 5776 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\Purchase Order #15562_PDF.jse" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6592 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6708 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\Purchase Order #15562_PDF.jse" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
6 262
Read events
6 262
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
9
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4988 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\7.3.5\update1_v7.5.1_2025-05-13 | — | |
MD5:— | SHA256:— | |||
| 4988 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3c3871276e149215.customDestinations-ms~RF11c13a.TMP | binary | |
MD5:46E1C931FBFF22C77310388EB2BC9B98 | SHA256:704B8AE61BD9951DEA597ED475FD91BAD6ECDEC71726941BDAC64686A59263DB | |||
| 4988 | pwsh.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:0F7B8F6A846AA9CA52FA562DDDCDB5ED | SHA256:AFF90E65A81289B80D1FCC5E71B3D88E5D1AAFE22CE358EB6E28A56D1845263D | |||
| 4988 | pwsh.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:28C04C21F2600B8846294EAFFFCC3926 | SHA256:D7C892B7F6DC363191659D12230772AA6E983D0B67592D215E309019AF0CA6CB | |||
| 4988 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3c3871276e149215.customDestinations-ms | binary | |
MD5:2E2EA440229711F7B0CAFE5D00630BFB | SHA256:B2F0E9153AA9C2BEA3F44889A9EE58DDB58A6E11859A8D6D7CF9F2950816DAC9 | |||
| 4988 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\StartupProfileData-Interactive | binary | |
MD5:E5FE092FAFC6533BE439A6436215A744 | SHA256:47B78D296A67E56D78F8DAEB716237E6C83F5C82E44DC861C041D4A360DED4CB | |||
| 4988 | pwsh.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C0018BB1B5834735BFA60CD063B31956 | binary | |
MD5:7E22B7B38C2210B354040E5160336BF3 | SHA256:FF0BBB82D8C055F171D9E3BA0112357F6D5153EFC1635C19592F4DA74D1205BE | |||
| 4988 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt | text | |
MD5:5355EF14EF5ED217D91170A672AC9094 | SHA256:EDC479D233232A699F5B7A762F5386D7DDD90FCDC6004C23998D52BBFDAAE513 | |||
| 4988 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\ModuleAnalysisCache-0C86AEE9 | binary | |
MD5:7CE9A236A0AFC5701663782CCB154146 | SHA256:9D8C5DC94D6F0F7FEA38627ACC72166EE48B2703A6727BA5A741D0A09E1A14DA | |||
| 4988 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qyifmyd2.ggc.ps1 | text | |
MD5:1BED8C1CB19836DEAA2A60931BD3BB1A | SHA256:56AAC87B9CCE670E9AF361EFCF424527760B0AD1FD7C040B2AA826CE3818B0BA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
35
DNS requests
25
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5392 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5392 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4988 | pwsh.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4988 | pwsh.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5392 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4988 | pwsh.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |