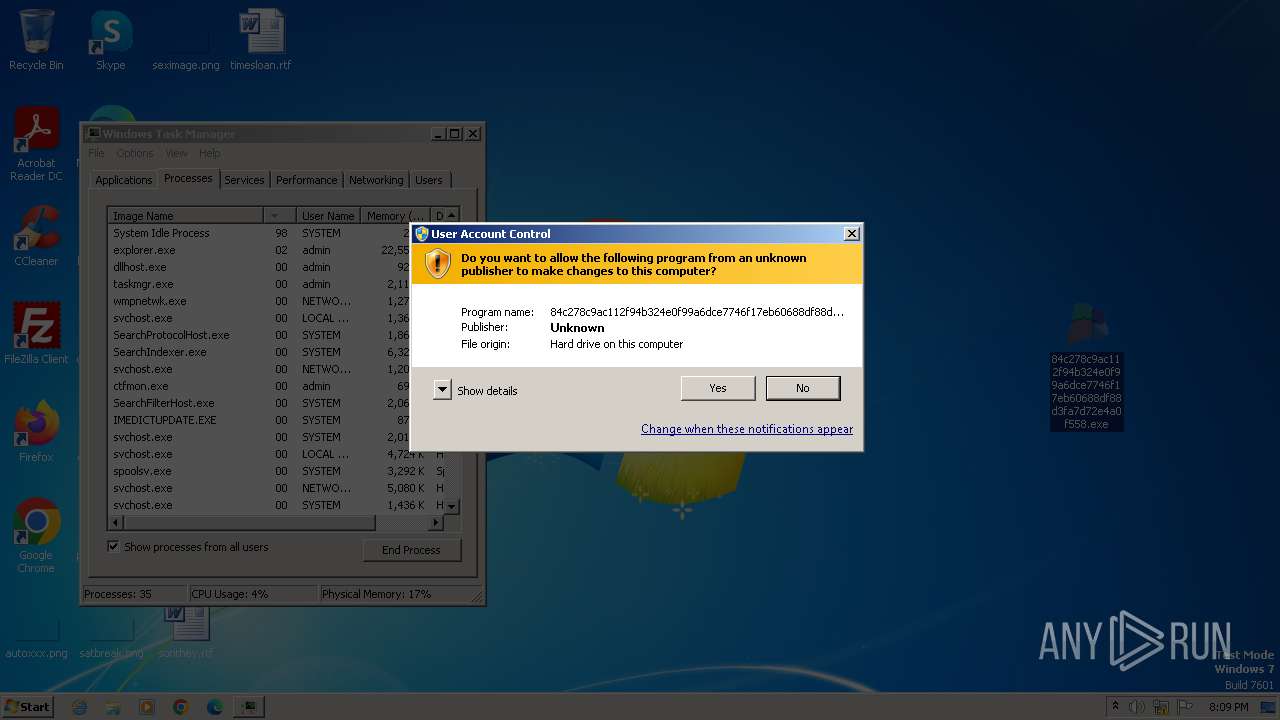
| File name: | Trojan.GenericKD.6178125.7z |
| Full analysis: | https://app.any.run/tasks/40e9ab45-ca90-4cdd-9256-044a58b0b5f6 |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2023, 20:09:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 080BD050650F5F61F7F598D81F3127C4 |
| SHA1: | 29A739F7D65F6FAB7398E91842468E22FDEC3894 |
| SHA256: | 79DA8CA0A3C490DD4CB2410E3B1A6FE8E70B317CAA5D537CF58B5B622F035BDC |
| SSDEEP: | 6144:ZjsCufKJ2JR0AsSrRdjGQsiXJLuCq0xxsPu/BTqYBJGUyR4iBNo0I/0:ZjsRiwXvrPjGQsaICq0xguwsk4iBNopM |
MALICIOUS
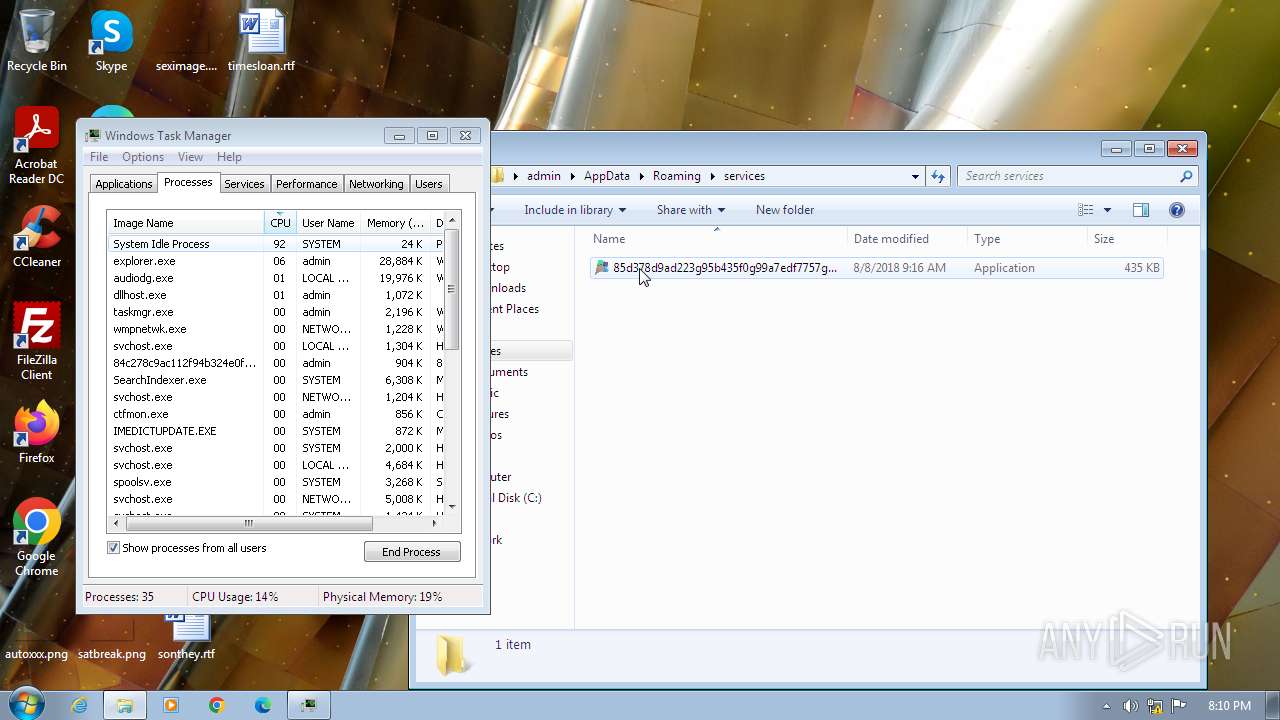
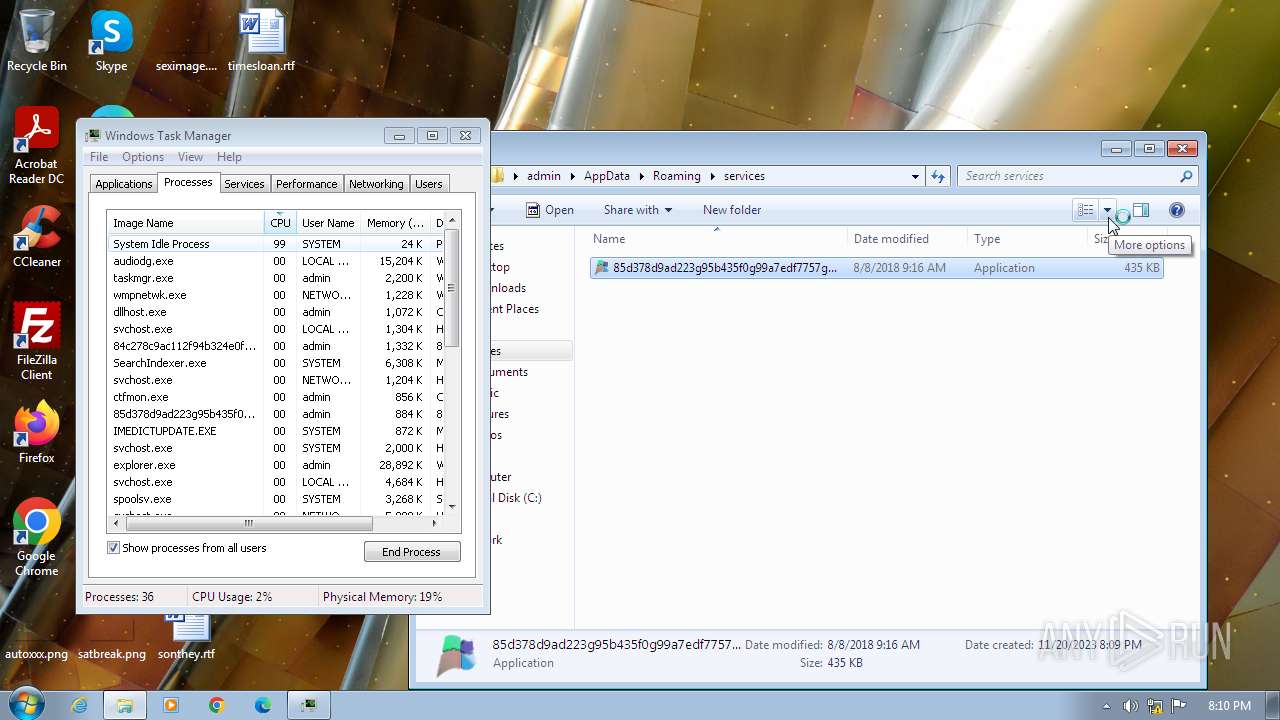
Drops the executable file immediately after the start
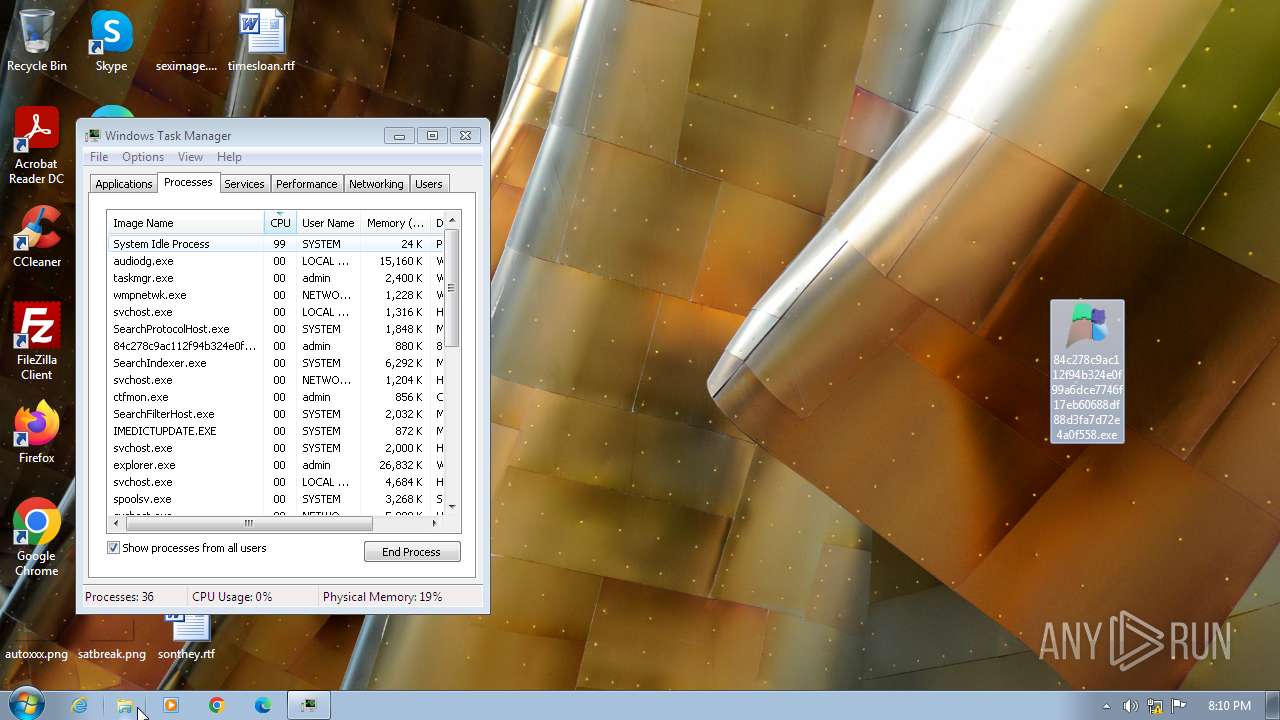
- 84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe (PID: 2116)
SUSPICIOUS
Application launched itself
- taskmgr.exe (PID: 3508)
Checks for external IP
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 1584)
Reads the Internet Settings
- taskmgr.exe (PID: 3508)
Starts itself from another location
- 84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe (PID: 2116)
- 84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe (PID: 2312)
The process executes via Task Scheduler
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 2876)
INFO
Checks supported languages
- 84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe (PID: 2116)
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 1612)
- 84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe (PID: 2312)
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 1584)
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 1700)
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 2876)
- wmpnscfg.exe (PID: 3868)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3440)
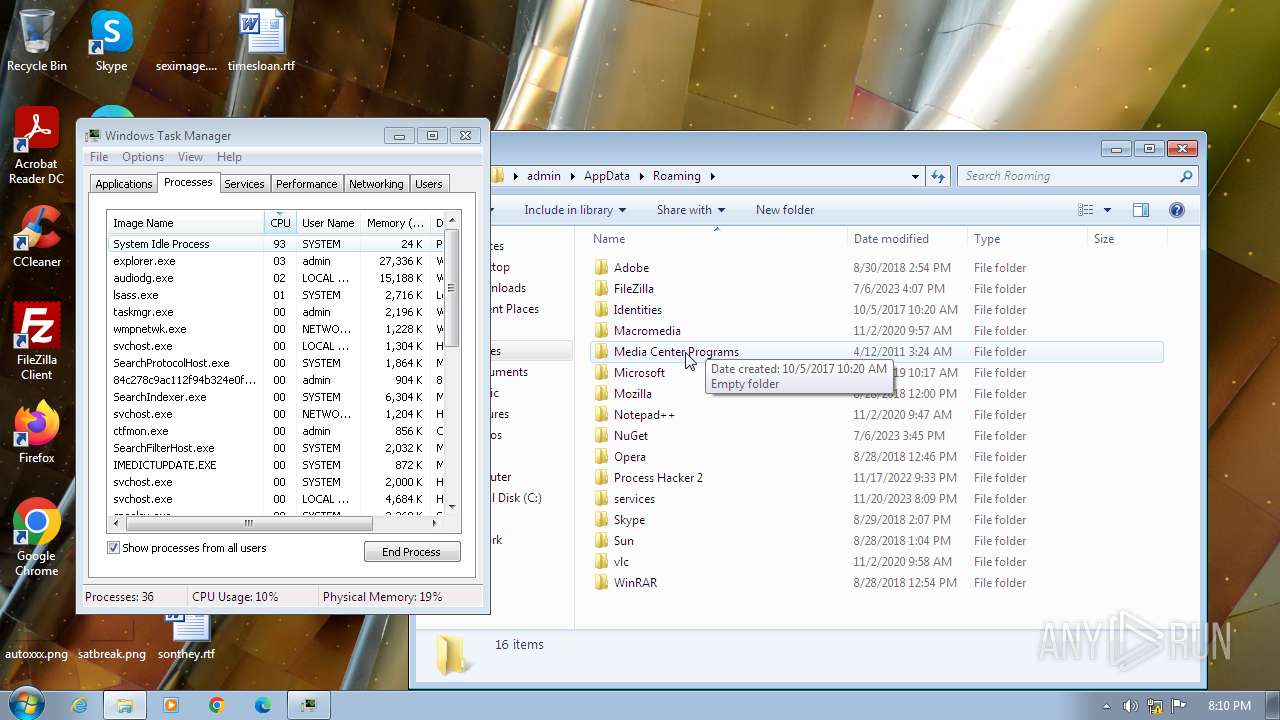
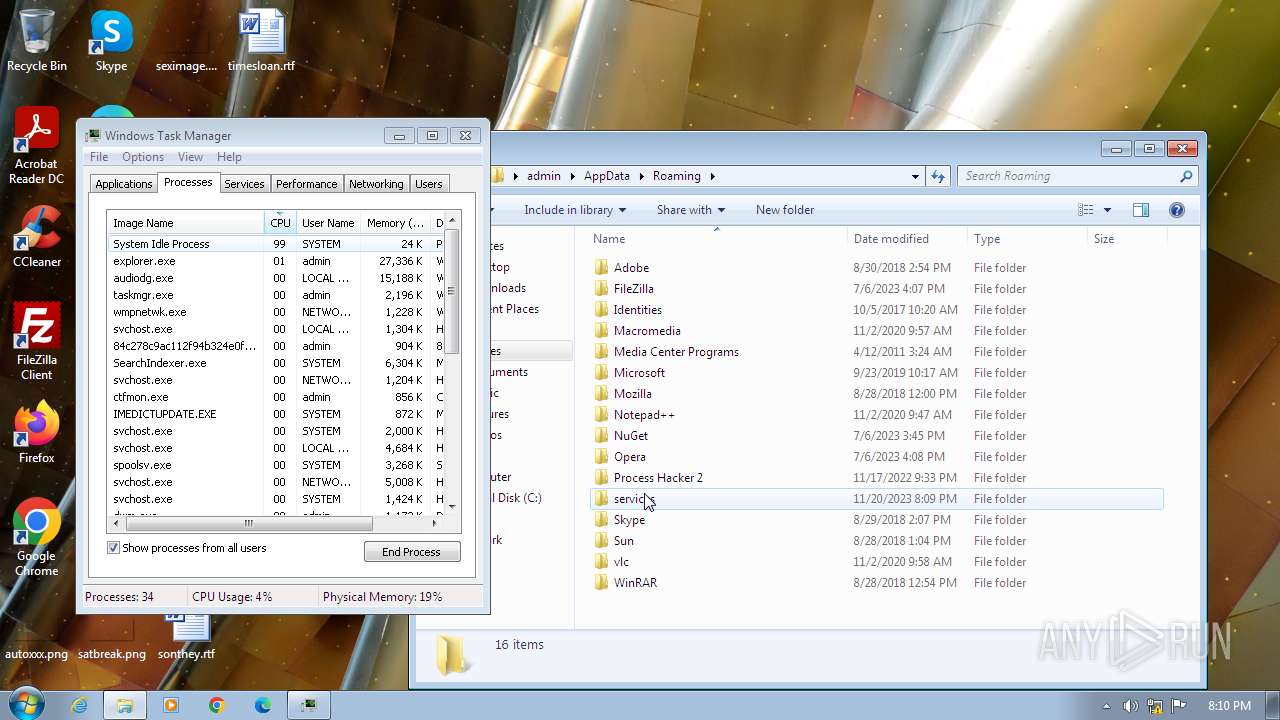
Creates files or folders in the user directory
- 84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe (PID: 2116)
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 1584)
Manual execution by a user
- taskmgr.exe (PID: 3508)
- 84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe (PID: 2116)
- 84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe (PID: 2312)
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 1584)
- explorer.exe (PID: 2268)
- wmpnscfg.exe (PID: 3868)
Reads the computer name
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 1612)
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 1584)
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 1700)
- wmpnscfg.exe (PID: 3868)
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 2876)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3868)
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 1584)
- 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe (PID: 2876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
57
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1584 | "C:\Users\admin\AppData\Roaming\services\85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe" | C:\Users\admin\AppData\Roaming\services\85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1612 | C:\Users\admin\AppData\Roaming\services\85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | C:\Users\admin\AppData\Roaming\services\85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | — | 84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Modules
| |||||||||||||||
| 1700 | C:\Users\admin\AppData\Roaming\services\85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | C:\Users\admin\AppData\Roaming\services\85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | — | 84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 2116 | "C:\Users\admin\Desktop\84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe" | C:\Users\admin\Desktop\84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2268 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2312 | "C:\Users\admin\Desktop\84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe" | C:\Users\admin\Desktop\84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2876 | C:\Users\admin\AppData\Roaming\services\85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | C:\Users\admin\AppData\Roaming\services\85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | taskeng.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 3440 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Trojan.GenericKD.6178125.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3508 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3680 | "C:\Windows\system32\taskmgr.exe" /1 | C:\Windows\System32\taskmgr.exe | taskmgr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 630
Read events
8 597
Write events
30
Delete events
3
Modification events
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3440) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
2
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2116 | 84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe | C:\Users\admin\AppData\Roaming\services\85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | executable | |
MD5:06E67970894DA9AE379BECFA19C0EF64 | SHA256:84C278C9AC112F94B324E0F99A6DCE7746F17EB60688DF88D3FA7D72E4A0F558 | |||
| 3440 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3440.43456\Trojan.GenericKD.6178125\84c278c9ac112f94b324e0f99a6dce7746f17eb60688df88d3fa7d72e4a0f558.exe.bak | executable | |
MD5:06E67970894DA9AE379BECFA19C0EF64 | SHA256:84C278C9AC112F94B324E0F99A6DCE7746F17EB60688DF88D3FA7D72E4A0F558 | |||
| 1584 | 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | C:\Users\admin\AppData\Roaming\services\group_tag | binary | |
MD5:BE865D32BB18263269B80AF97721AC2A | SHA256:225B5F28EDE041B9E5FD9779E9826DF1209C7C362B8FF129D69E35B370F29AE1 | |||
| 1584 | 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | C:\Users\admin\AppData\Roaming\services\client_id | binary | |
MD5:A4BF4E14C3BE029F77B9F189B93C7ACE | SHA256:E56AB453F945753032FEC8FB9ED37EEA1D552A2C560E4FFDD55CA704516BC741 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
28
DNS requests
2
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1584 | 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | GET | 200 | 15.204.2.228:80 | http://wtfismyip.com/text | unknown | text | 13 b | unknown |
2876 | 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | GET | 200 | 63.32.132.40:80 | http://checkip.amazonaws.com/ | unknown | text | 13 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1584 | 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | 15.204.2.228:80 | wtfismyip.com | OVH SAS | US | unknown |
1584 | 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | 185.158.114.72:443 | — | Ip Server LLC | RU | unknown |
2876 | 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | 63.32.132.40:80 | checkip.amazonaws.com | AMAZON-02 | IE | unknown |
2876 | 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | 62.109.31.123:443 | — | JSC IOT | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wtfismyip.com |
| shared |
checkip.amazonaws.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1584 | 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | Potential Corporate Privacy Violation | ET POLICY IP Check wtfismyip.com |
1584 | 85d378d9ad223g95b435f0g99a7edf7757g27fb70788eg88e4ga7e73f5a0g668.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] Received IP address from server as result of HTTP request |
2 ETPRO signatures available at the full report