| URL: | trendingintesting.com |
| Full analysis: | https://app.any.run/tasks/22ffec7d-21f4-4e41-9263-93fda291a7ac |
| Verdict: | Malicious activity |
| Analysis date: | June 20, 2024, 16:57:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B5C520951244053D382468B9B29C9043 |
| SHA1: | 2FBDD3127AACFF18AE84C7580ACAFA6B8A1026C6 |
| SHA256: | 79CD405997BE86C0AF5C007FF5382256514A50E1F0CE39EC217AB20CE4B8E299 |
| SSDEEP: | 3:5fVK:tVK |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- wmpnscfg.exe (PID: 2536)
Reads the computer name
- wmpnscfg.exe (PID: 2536)
Application launched itself
- iexplore.exe (PID: 3380)
Manual execution by a user
- wmpnscfg.exe (PID: 2536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2536 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3380 | "C:\Program Files\Internet Explorer\iexplore.exe" "trendingintesting.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3432 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3380 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
24 413
Read events
24 278
Write events
107
Delete events
28
Modification events
| (PID) Process: | (3380) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3380) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3380) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31114034 | |||
| (PID) Process: | (3380) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3380) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31114034 | |||
| (PID) Process: | (3380) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3380) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3380) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3380) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3380) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
55
Text files
91
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ADB1G1RJ.txt | text | |
MD5:B7AD764D8AC40E0B92DC6C100D9B0F7A | SHA256:1EC19C4E943FE2863A8050758792112DD8DE5D10740B76B073CEC62258CE3697 | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:469549317E6EF80A219060D244A4DF04 | SHA256:3F44E50FF94554BE75D2ED080B8C8A036915AB855FAF0B61898D6203E252143B | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\mediaelementplayer-legacy.min[1].css | text | |
MD5:2B0DD7EECEA03B4BDEDB94BA622FDB03 | SHA256:B7908A015A567EC2363011DF2475368DBFF34360E9DA3FDFF50604D6395FB646 | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:BB48A70F3CF648AE52B2C6D5D3F113E2 | SHA256:64E9364775EDC4E9E1BFAE2420CBFDDE4498AC6F4E94DF1A1DDA93FF9F1CEA92 | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:2138655DC2513DD99C3F2DB7EBFB528A | SHA256:B07044750FAA6C4F168D156C786F8039E11E20B5683DEB422B48A2F26DD33F6F | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_89854CA6A0F0936A4D2ECA78845CEA25 | binary | |
MD5:02970C00EE3BDD300D666D3D474A8FC7 | SHA256:7B4C3AE4892D7FF578077A8DE759D6F021A6512967E381EC422D6FF70FF4DD79 | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:276100D8194F2612B75634C2A2B1B02D | SHA256:9FACC722BEF588EFF911197DDBD94495170CF6C3ECE1D301822266D6EFC11500 | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:6D8A1BFA63C515AE6AF1E2218874E1EF | SHA256:BF68FA917200FDF984F0E94FDFD5F83C6DFA6B1E2464017AD33CD868CC873881 | |||
| 3432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D0E1C4B6144E7ECAB3F020E4A19EFC29_B5F77004C894173A10E3A199871D2D90 | binary | |
MD5:058F9935C8F89C005BE2F49701B15A71 | SHA256:9A7127503795747E0D02FC770D44A367C6F10301FE4A6F89822CD36CD3270F7E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
79
DNS requests
48
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
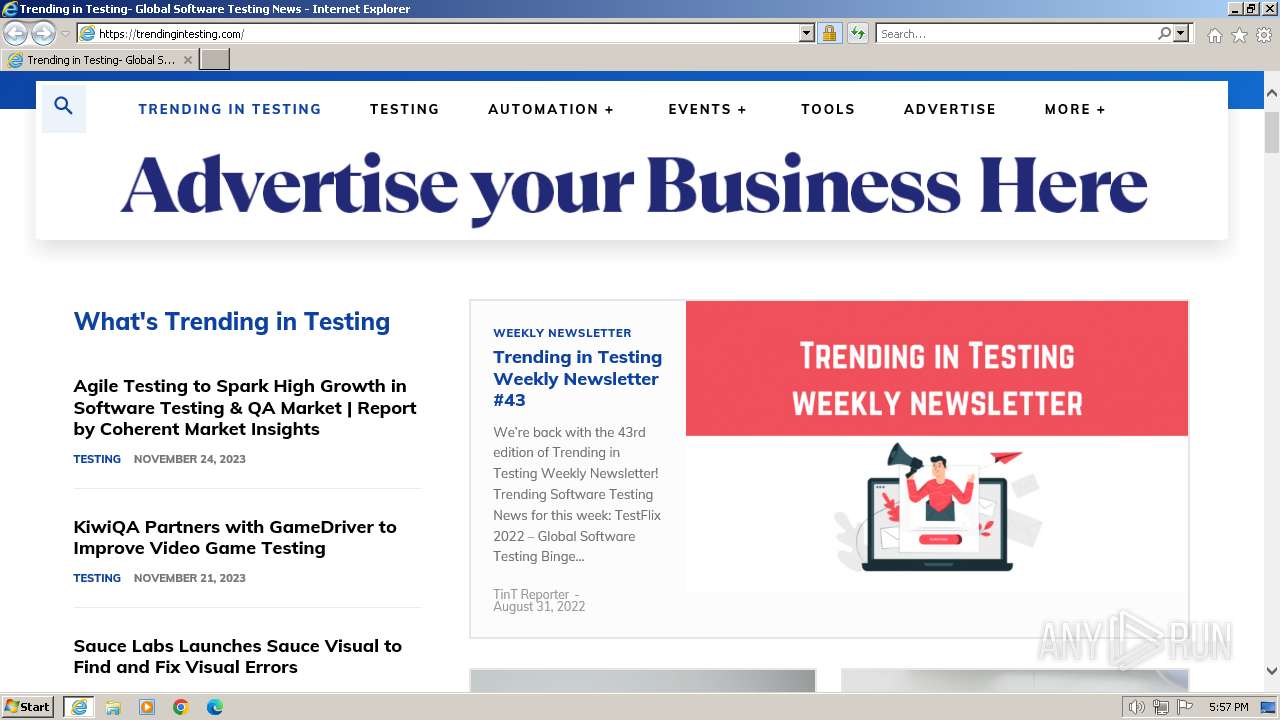
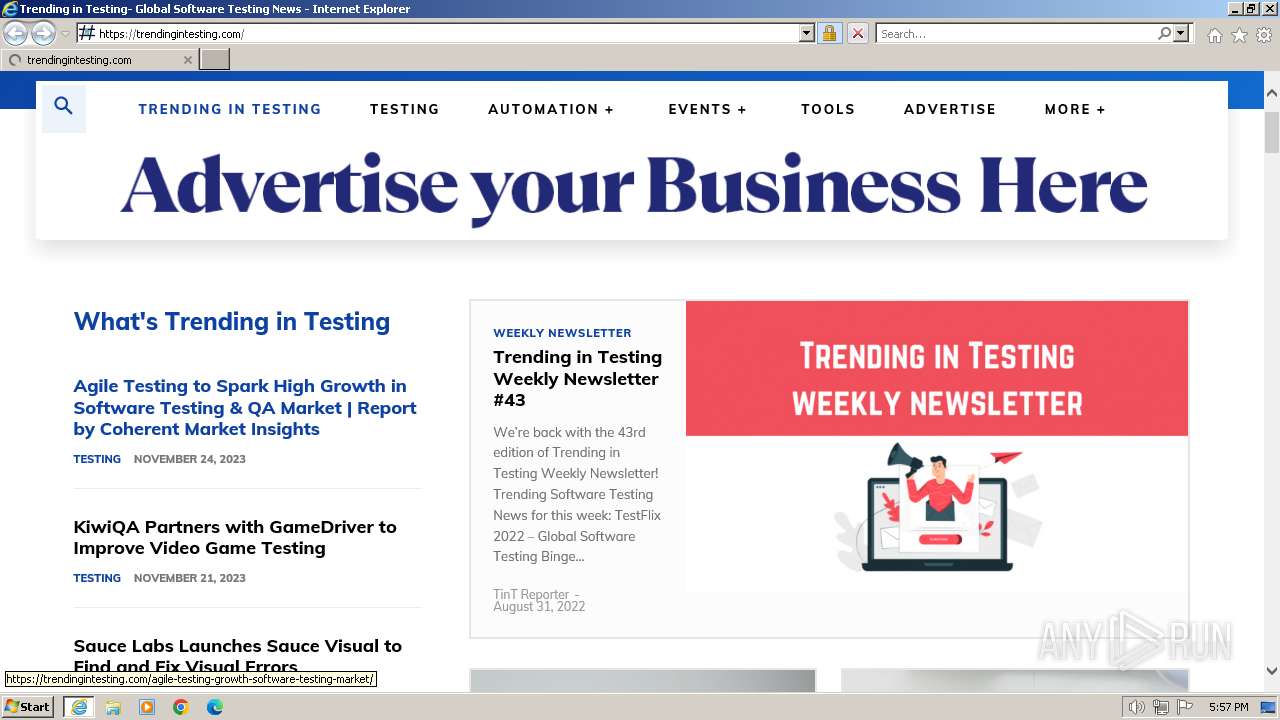
3432 | iexplore.exe | GET | 301 | 35.213.178.19:80 | http://trendingintesting.com/ | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?44f00a3e0bc750c9 | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | unknown |
3432 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEAIE94ivqY0gCWDtim5%2Ffhw%3D | unknown | — | — | unknown |
3380 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?82802e0cbf4dd56c | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3432 | iexplore.exe | 35.213.178.19:80 | trendingintesting.com | GOOGLE | SG | unknown |
3432 | iexplore.exe | 35.213.178.19:443 | trendingintesting.com | GOOGLE | SG | unknown |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3432 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3432 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
3432 | iexplore.exe | 142.250.184.202:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
trendingintesting.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
cdnjs.buymeacoffee.com |
| whitelisted |
secure.gdcstatic.com |
| malicious |
stats.wp.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |