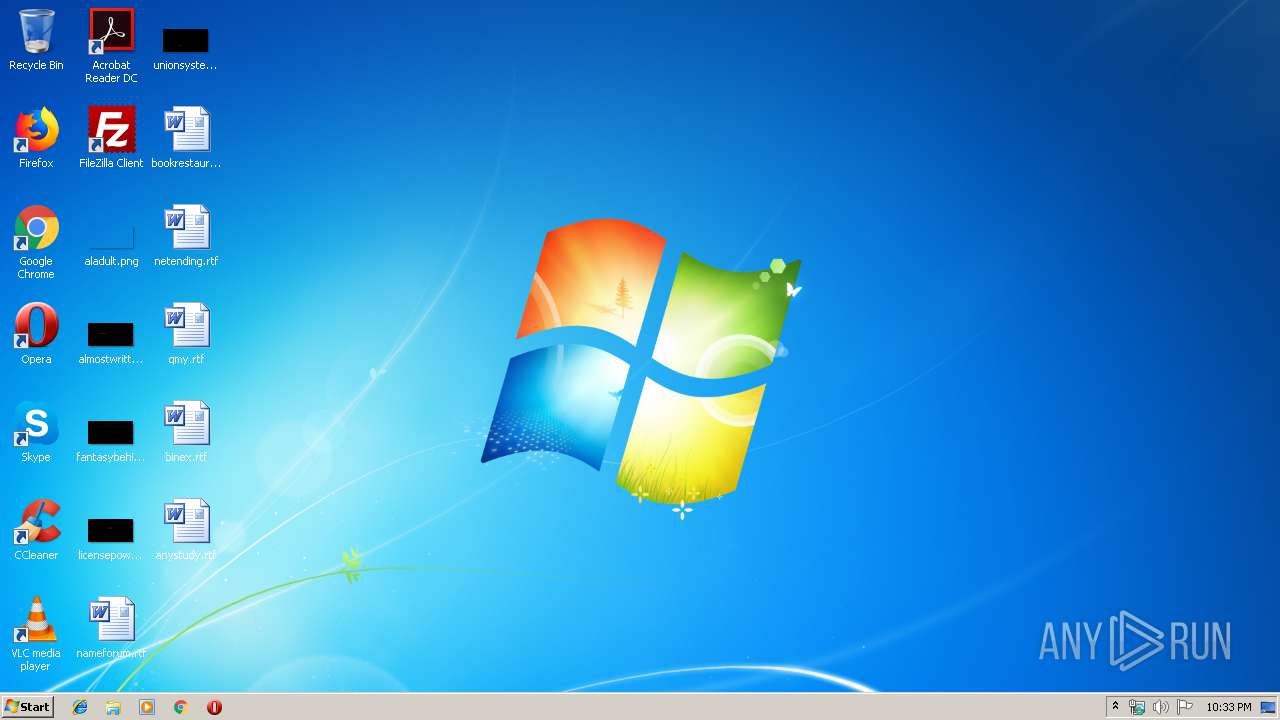
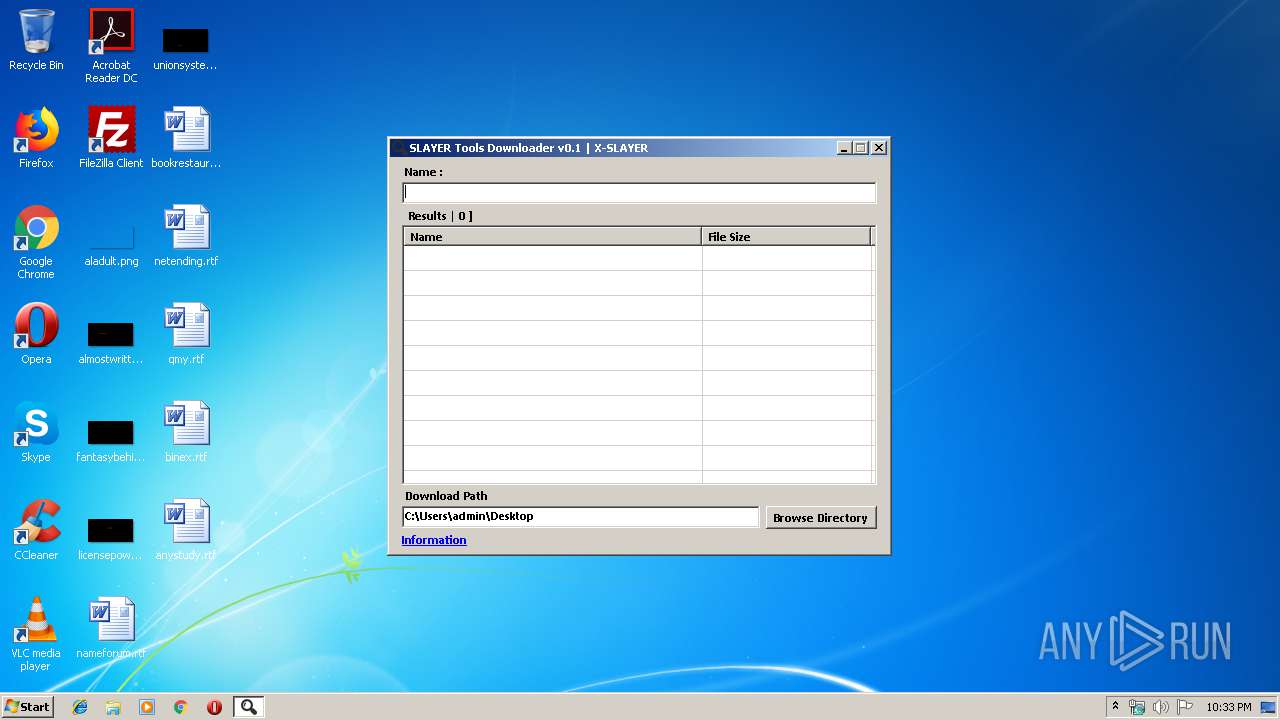
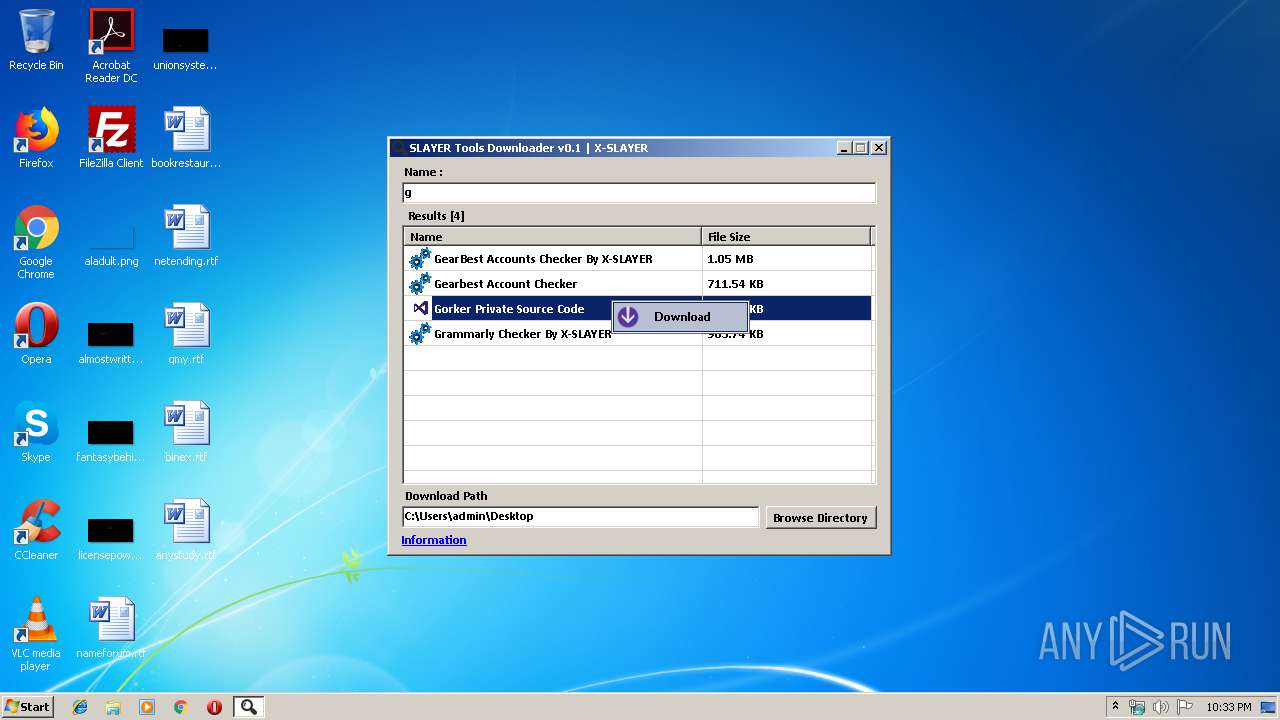
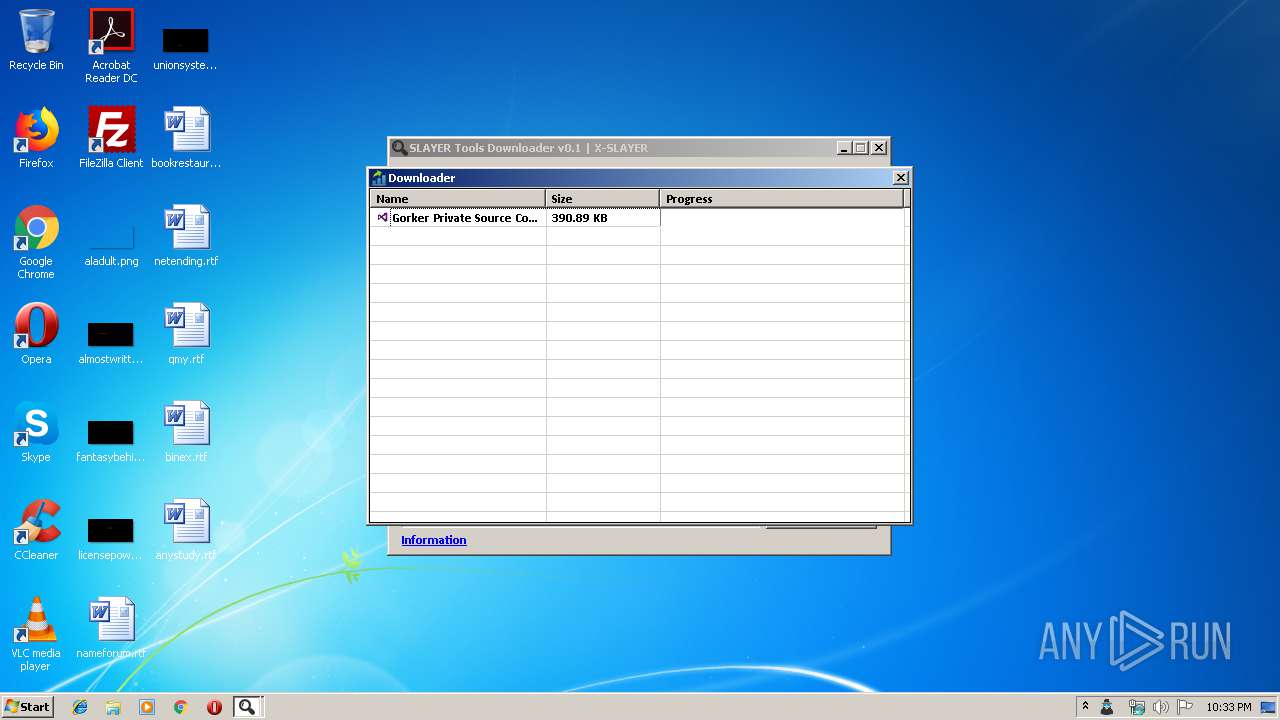
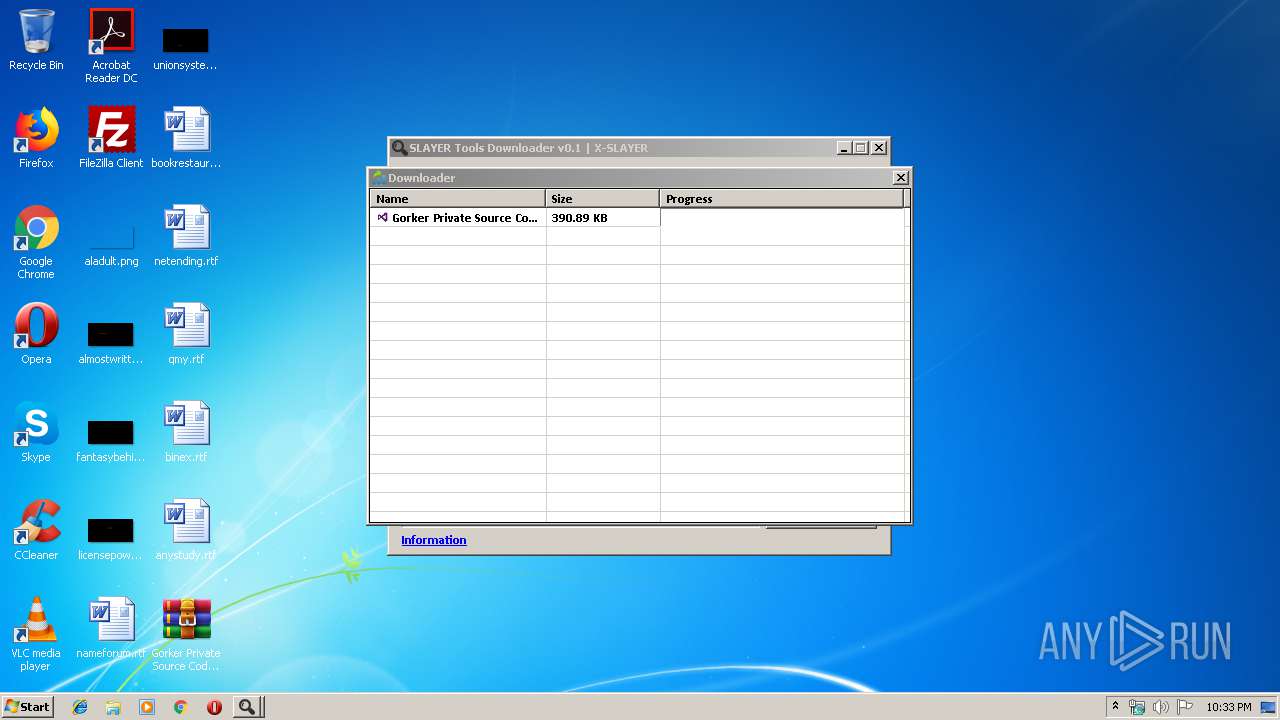
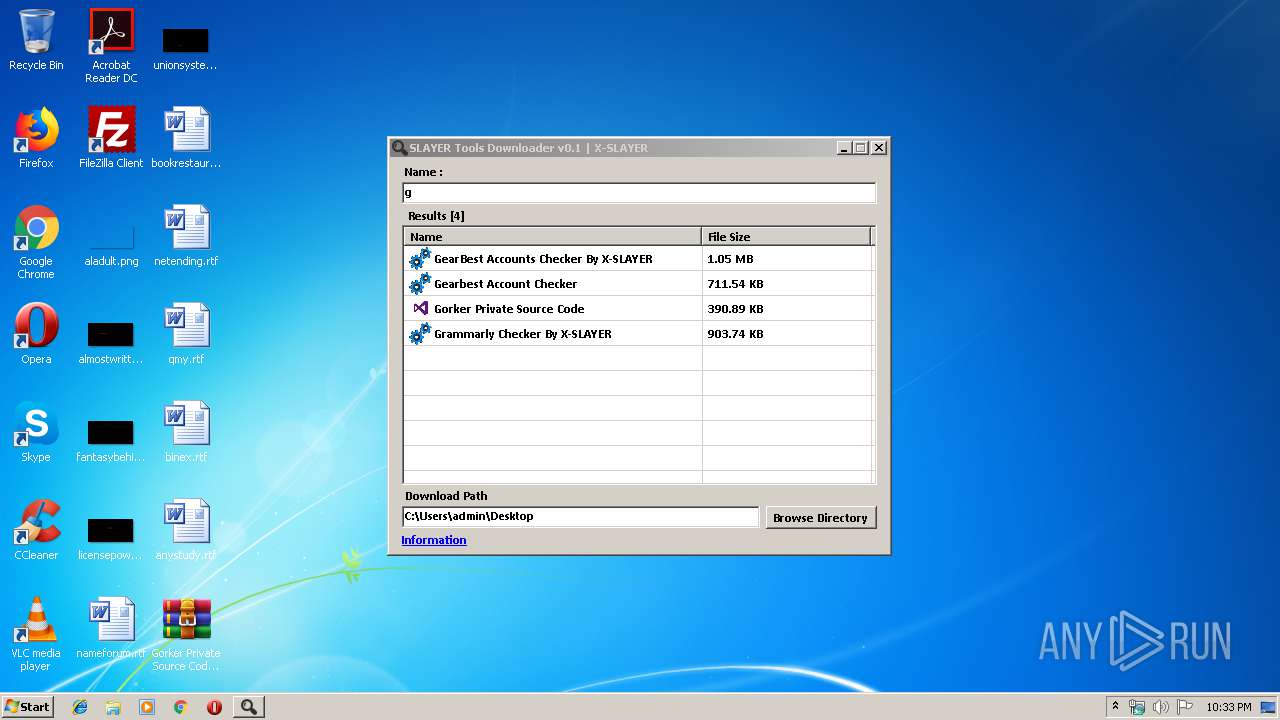
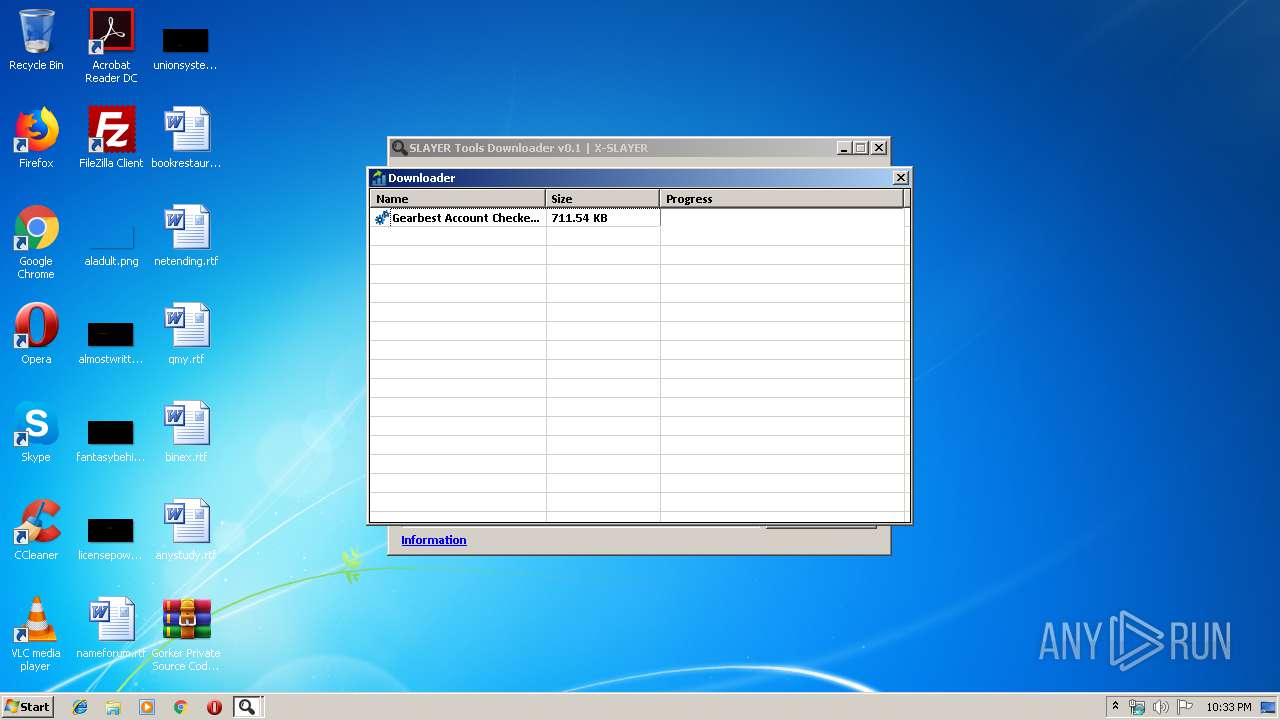
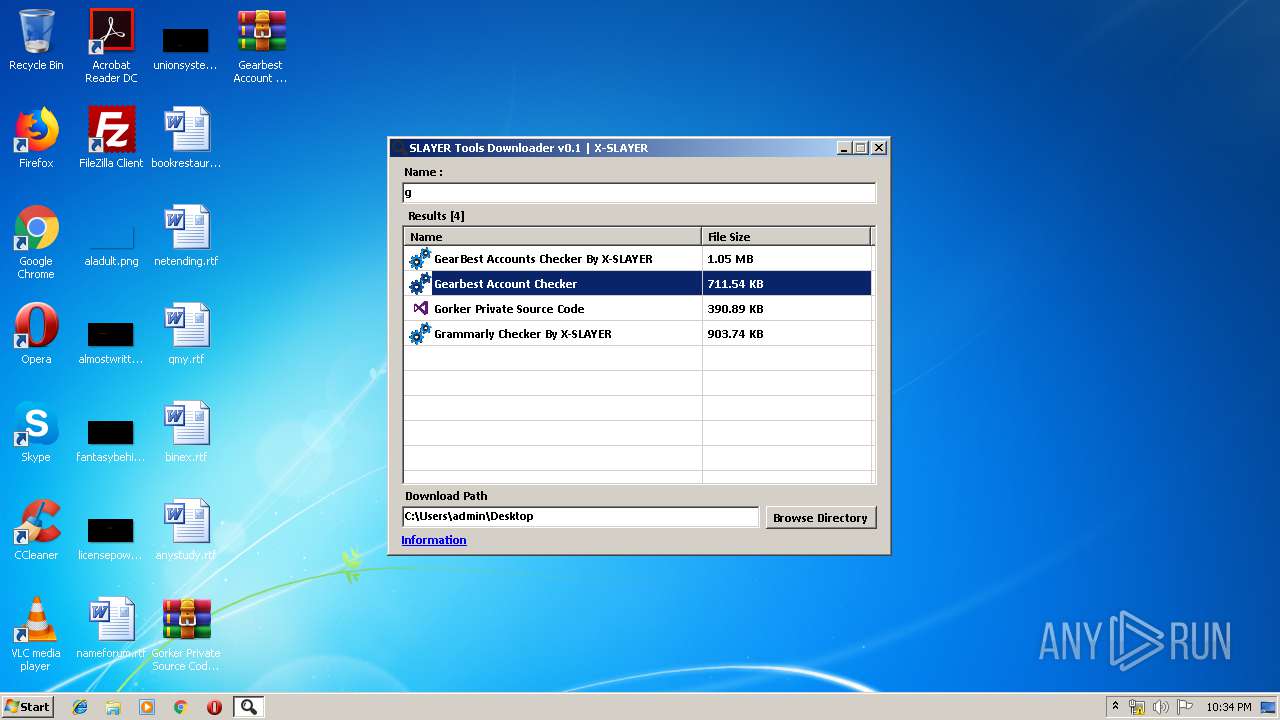
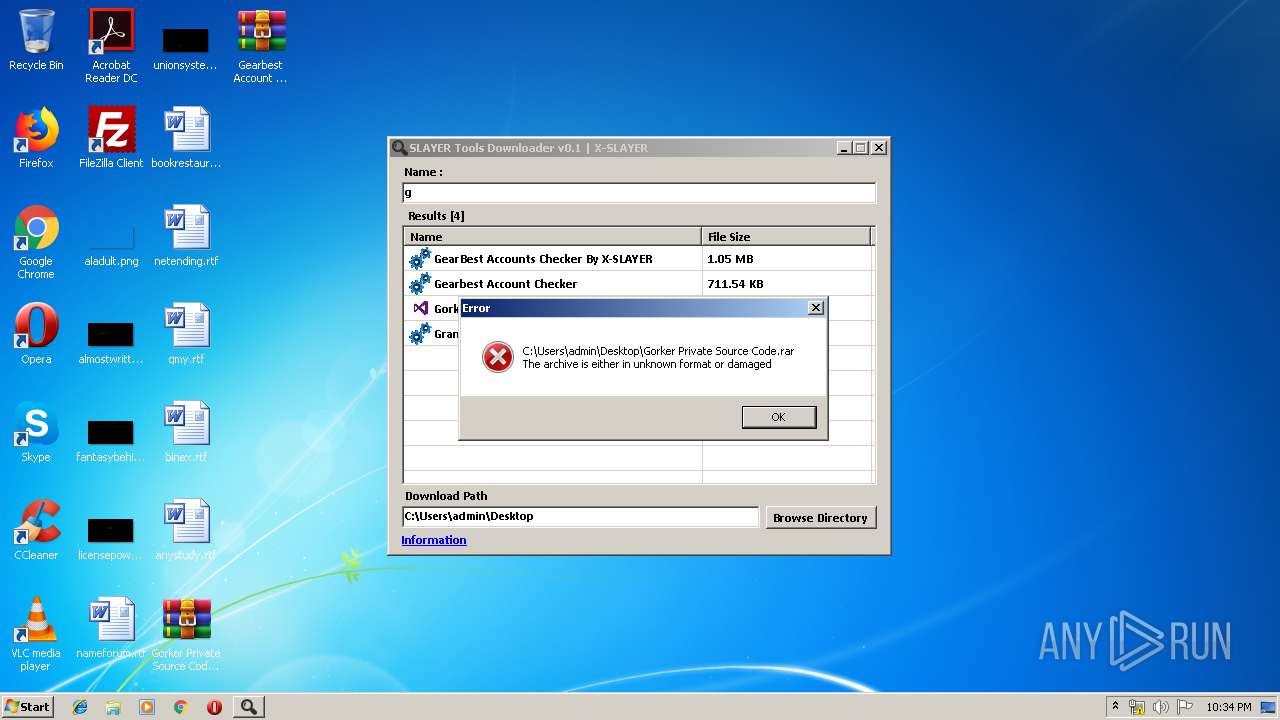
| File name: | SLAYER Tools Downloader v0.1.exe |
| Full analysis: | https://app.any.run/tasks/bd5410d2-5342-492c-8843-77d023f58fe8 |
| Verdict: | No threats detected |
| Analysis date: | March 22, 2019, 22:32:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 6DF2FF3ECF36975AE870244A206B857B |
| SHA1: | AFD60F31C9BE1634E9718A5679AC2CFEB28239FF |
| SHA256: | 79AB286E1B3250CE14108453A82ECF6E9D0272385F33C676AC9000020876A5CB |
| SSDEEP: | 24576:/KzVK4sFwpcpH2iBj6ZqqqqSqqqqqqLqq/qqAZlHLcb24EgU1oY:oC4cpvjn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads internet explorer settings
- SLAYER Tools Downloader v0.1.exe (PID: 292)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (55.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21) |
| .scr | | | Windows screen saver (9.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:02:15 17:36:40+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 1679360 |
| InitializedDataSize: | 172032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x19be6e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | Download X-SLAYER Tools v0.1 |
| FileVersion: | 1.0.0.0 |
| InternalName: | Download X-SLAYER Tools v0.1.exe |
| LegalCopyright: | Copyright © 2019 |
| OriginalFileName: | Download X-SLAYER Tools v0.1.exe |
| ProductName: | Download X-SLAYER Tools v0.1 |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 15-Feb-2019 16:36:40 |
| Debug artifacts: |
|
| FileDescription: | Download X-SLAYER Tools v0.1 |
| FileVersion: | 1.0.0.0 |
| InternalName: | Download X-SLAYER Tools v0.1.exe |
| LegalCopyright: | Copyright © 2019 |
| OriginalFilename: | Download X-SLAYER Tools v0.1.exe |
| ProductName: | Download X-SLAYER Tools v0.1 |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 15-Feb-2019 16:36:40 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00199E74 | 0x0019A000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.96936 |
.sdata | 0x0019C000 | 0x00000138 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.93419 |
.rsrc | 0x0019E000 | 0x00029B10 | 0x00029C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.48897 |
.reloc | 0x001C8000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 7.88838 | 6867 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 1.54503 | 67624 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 2.02553 | 38056 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 2.00829 | 21640 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 1.72304 | 16936 | UNKNOWN | UNKNOWN | RT_ICON |
7 | 2.36337 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
8 | 2.46472 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
9 | 3.13245 | 2440 | UNKNOWN | UNKNOWN | RT_ICON |
10 | 3.51142 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
Imports
mscoree.dll |
Total processes
33
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Users\admin\AppData\Local\Temp\SLAYER Tools Downloader v0.1.exe" | C:\Users\admin\AppData\Local\Temp\SLAYER Tools Downloader v0.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Download X-SLAYER Tools v0.1 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2260 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Gorker Private Source Code.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.60.0 Modules
| |||||||||||||||
Total events
382
Read events
349
Write events
33
Delete events
0
Modification events
| (PID) Process: | (292) SLAYER Tools Downloader v0.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SLAYER Tools Downloader v0_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (292) SLAYER Tools Downloader v0.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SLAYER Tools Downloader v0_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (292) SLAYER Tools Downloader v0.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SLAYER Tools Downloader v0_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (292) SLAYER Tools Downloader v0.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SLAYER Tools Downloader v0_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (292) SLAYER Tools Downloader v0.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SLAYER Tools Downloader v0_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (292) SLAYER Tools Downloader v0.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SLAYER Tools Downloader v0_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (292) SLAYER Tools Downloader v0.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SLAYER Tools Downloader v0_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (292) SLAYER Tools Downloader v0.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SLAYER Tools Downloader v0_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (292) SLAYER Tools Downloader v0.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SLAYER Tools Downloader v0_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (292) SLAYER Tools Downloader v0.1.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SLAYER Tools Downloader v0_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
3
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
292 | SLAYER Tools Downloader v0.1.exe | 104.20.209.21:443 | pastebin.com | Cloudflare Inc | US | shared |
292 | SLAYER Tools Downloader v0.1.exe | 162.125.66.6:443 | dl.dropbox.com | Dropbox, Inc. | DE | shared |
292 | SLAYER Tools Downloader v0.1.exe | 162.125.72.6:443 | dl.dropboxusercontent.com | Dropbox, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
dl.dropbox.com |
| shared |
dl.dropboxusercontent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
292 | SLAYER Tools Downloader v0.1.exe | Potential Corporate Privacy Violation | SUSPICIOUS [PTsecurity] Dropbox SSL Payload Request |
292 | SLAYER Tools Downloader v0.1.exe | Potential Corporate Privacy Violation | SUSPICIOUS [PTsecurity] Dropbox SSL Payload Request |