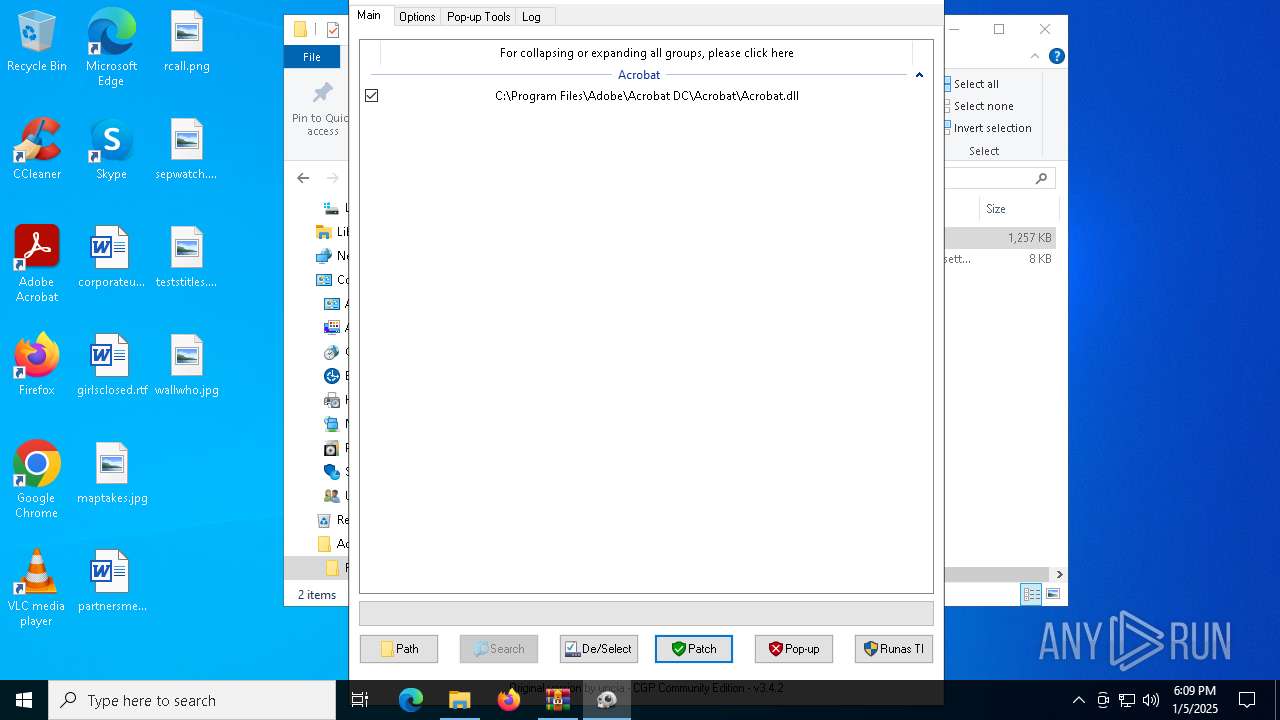
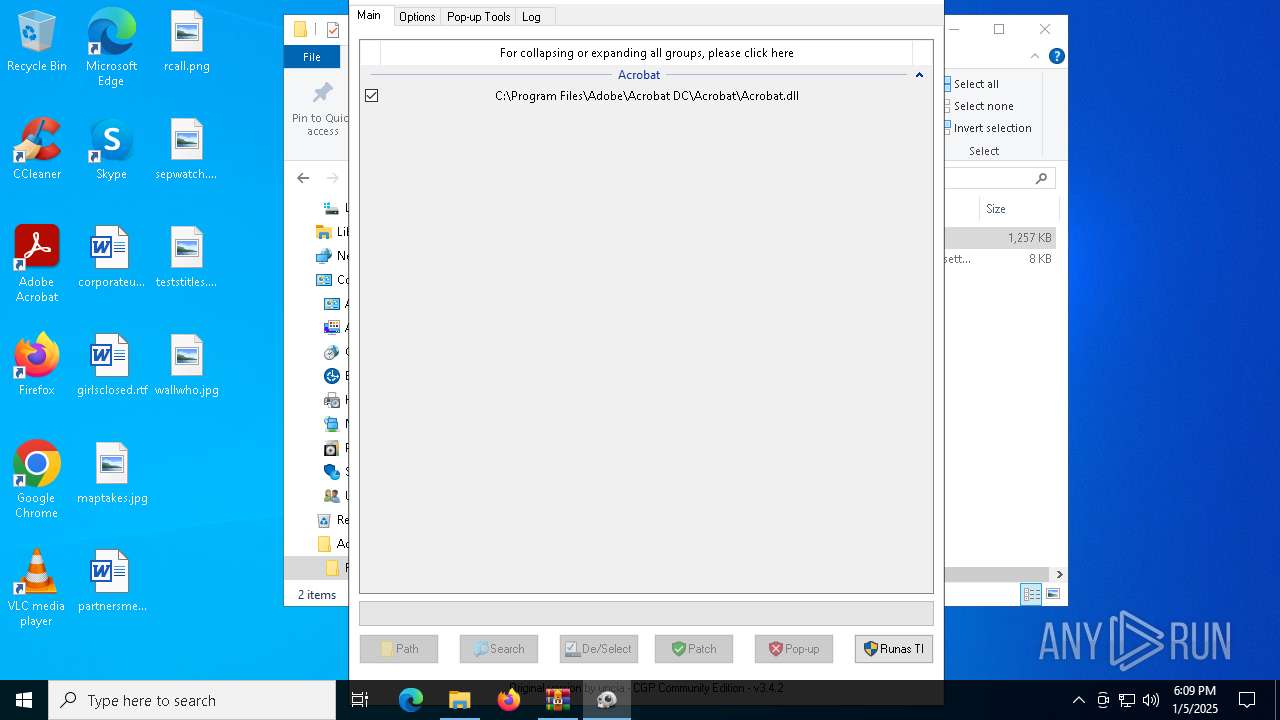
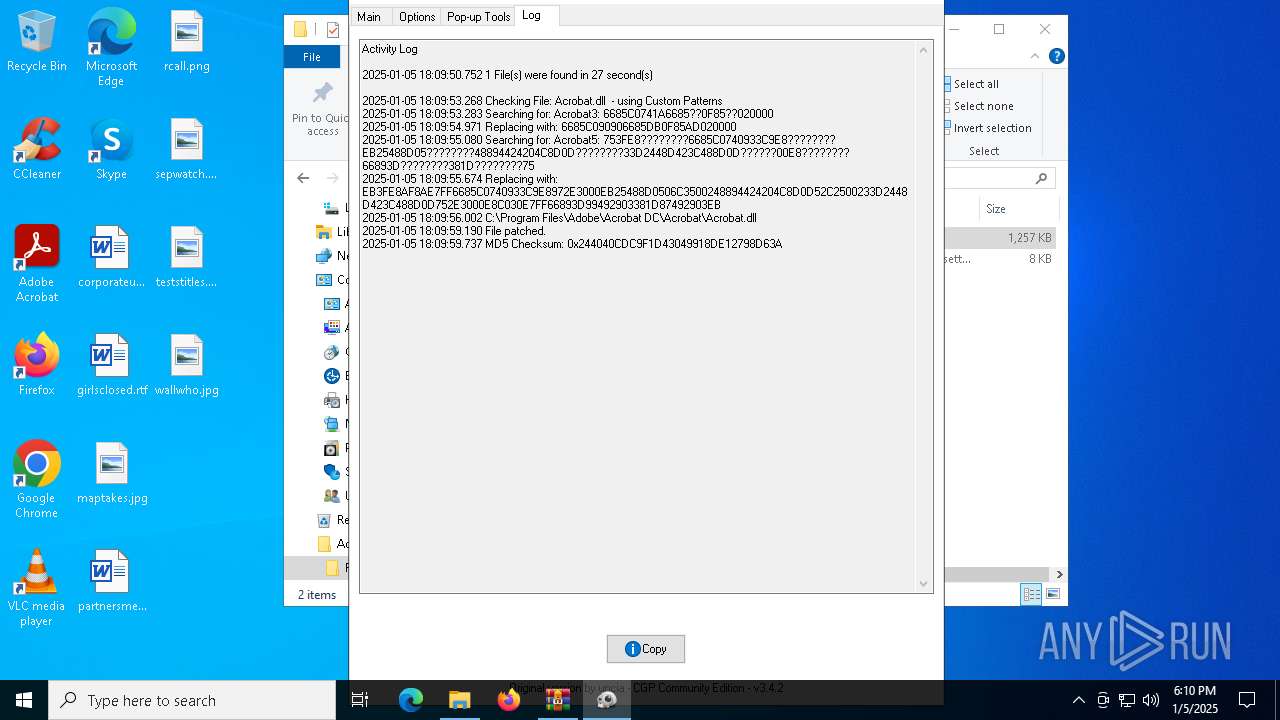
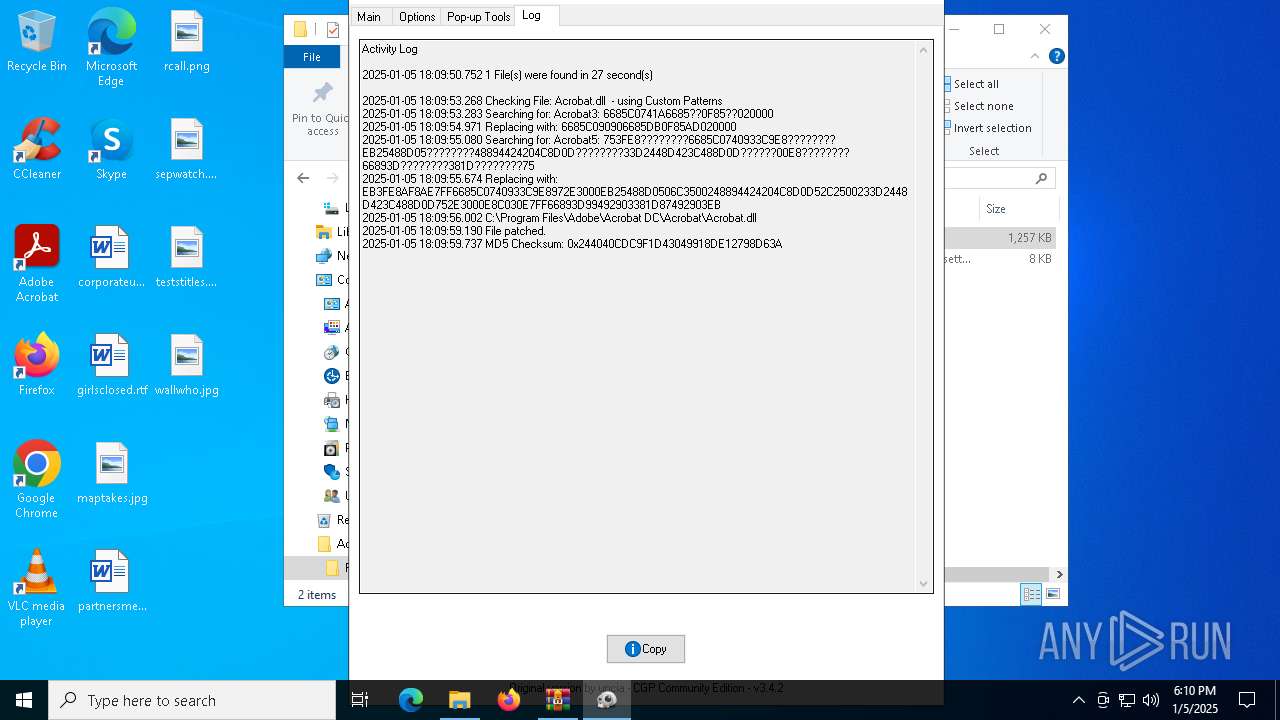
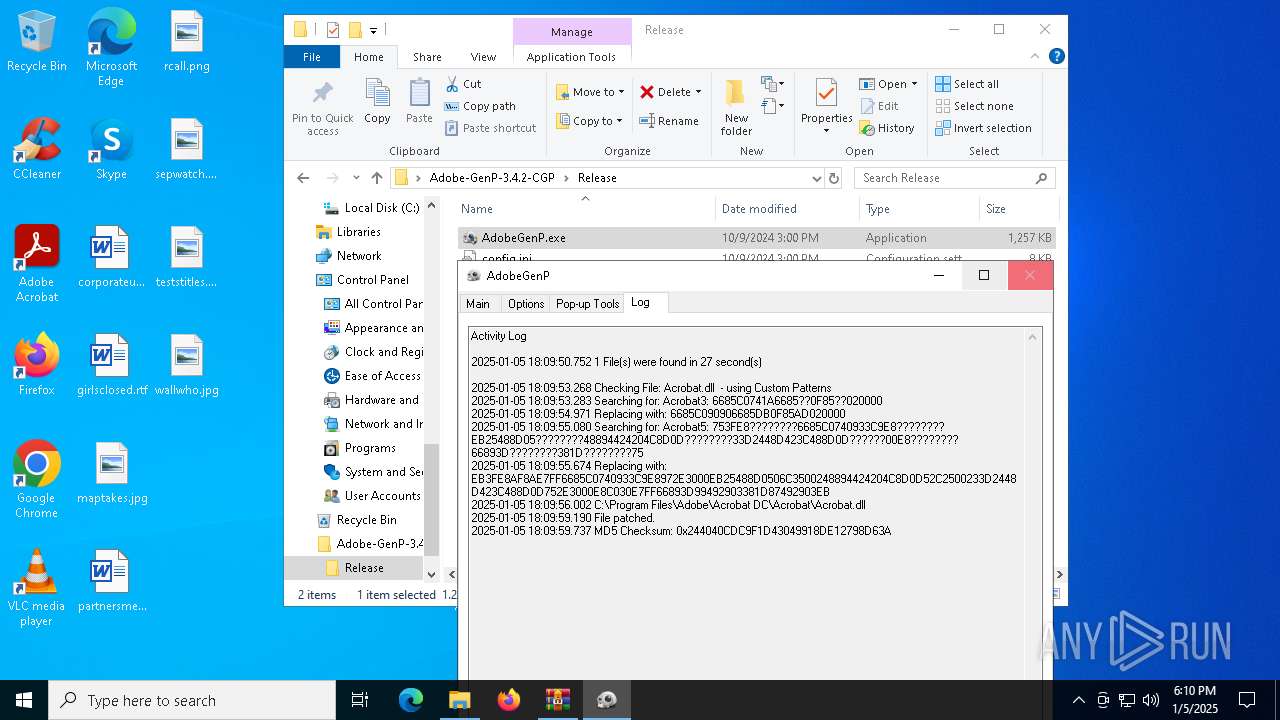
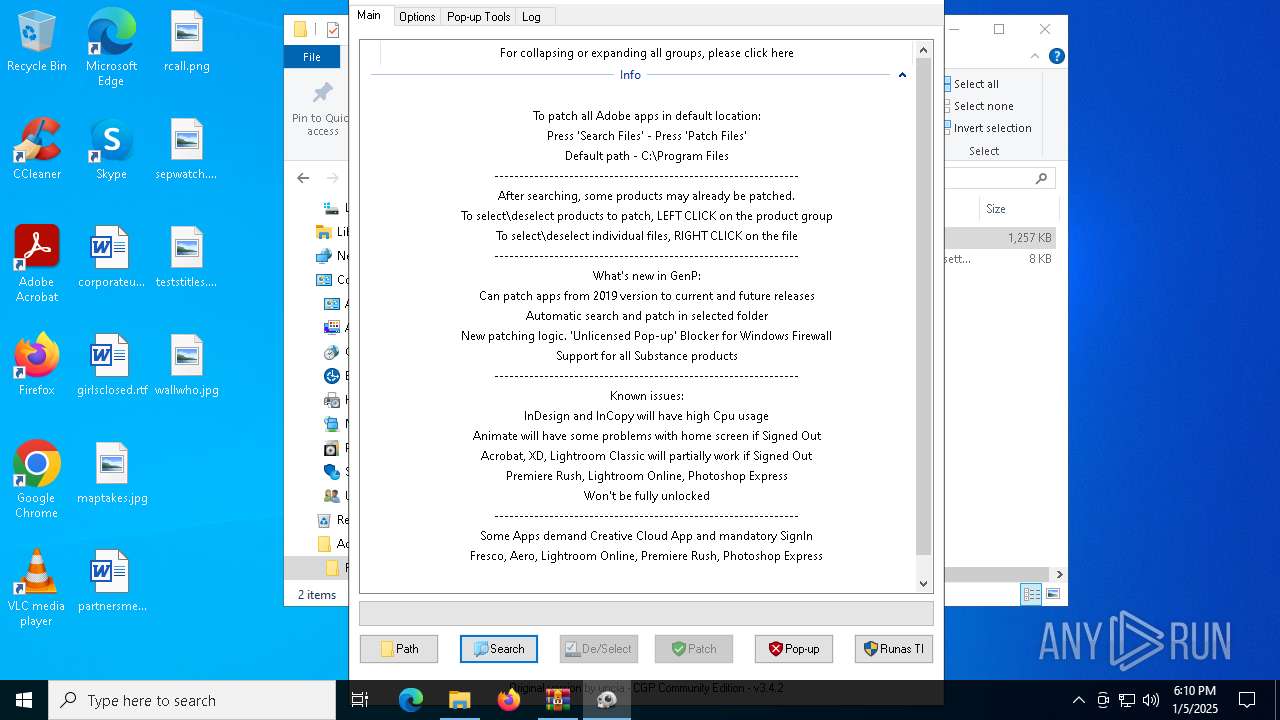
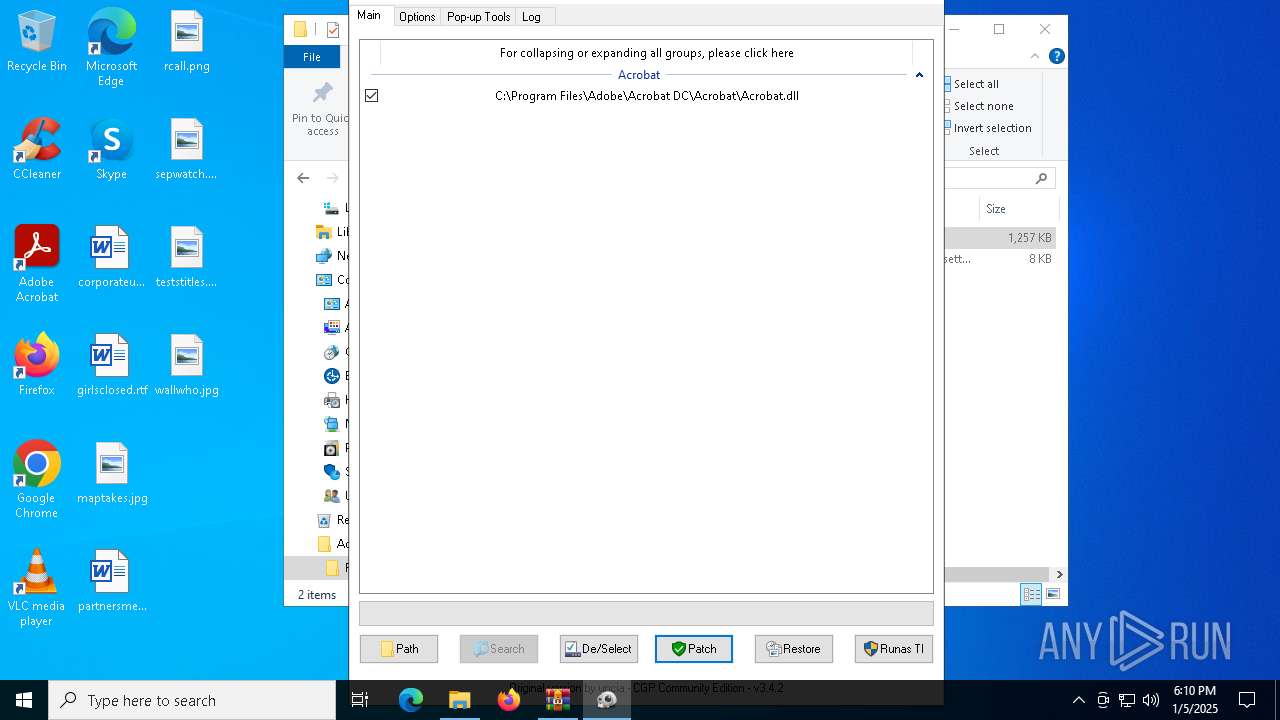
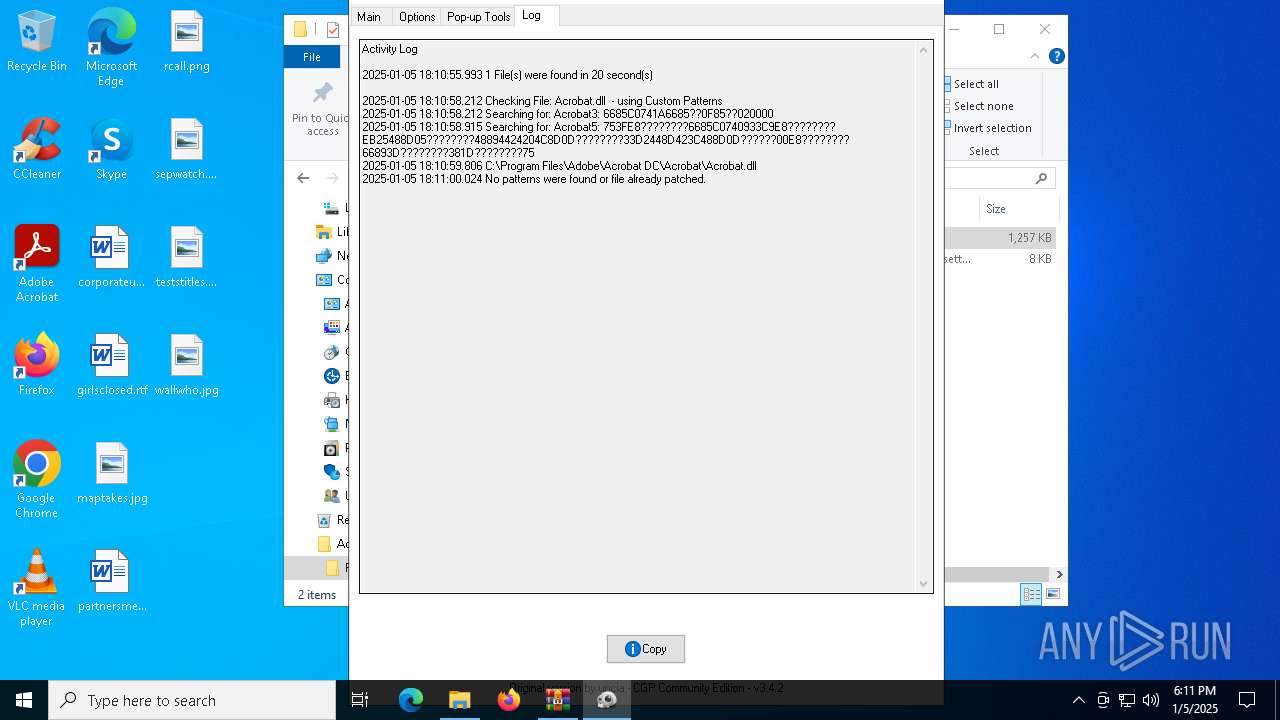
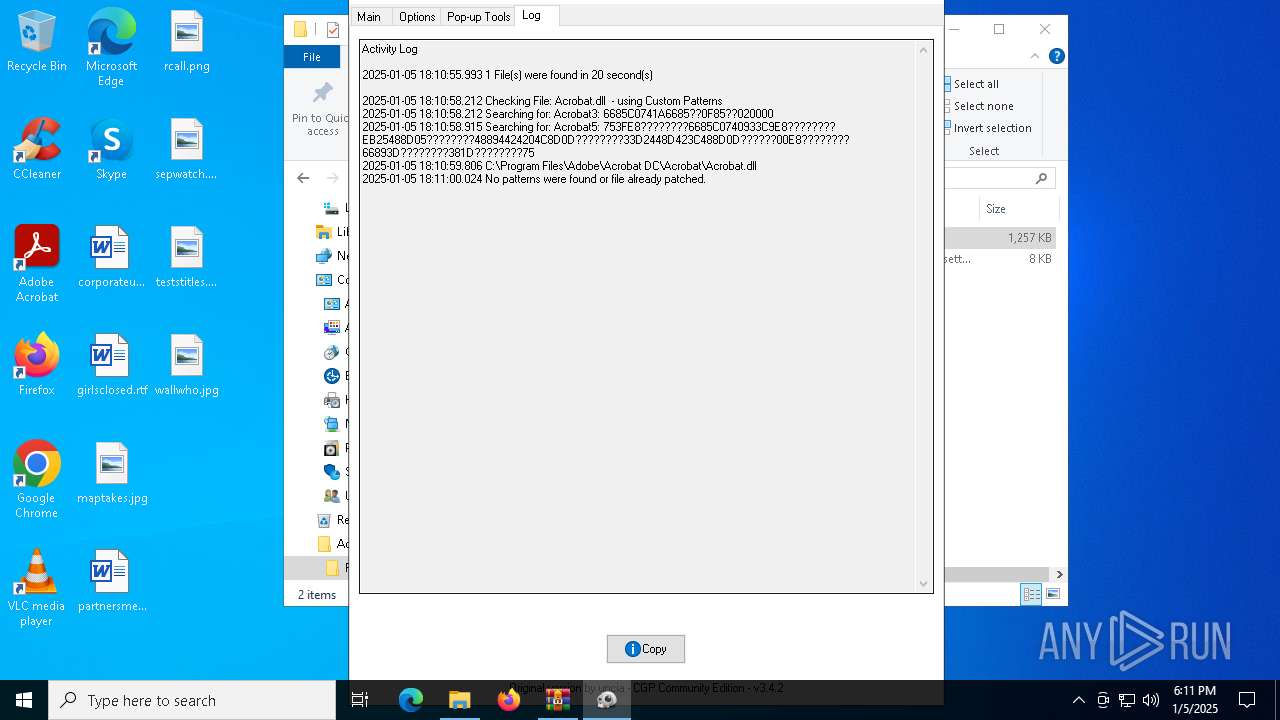
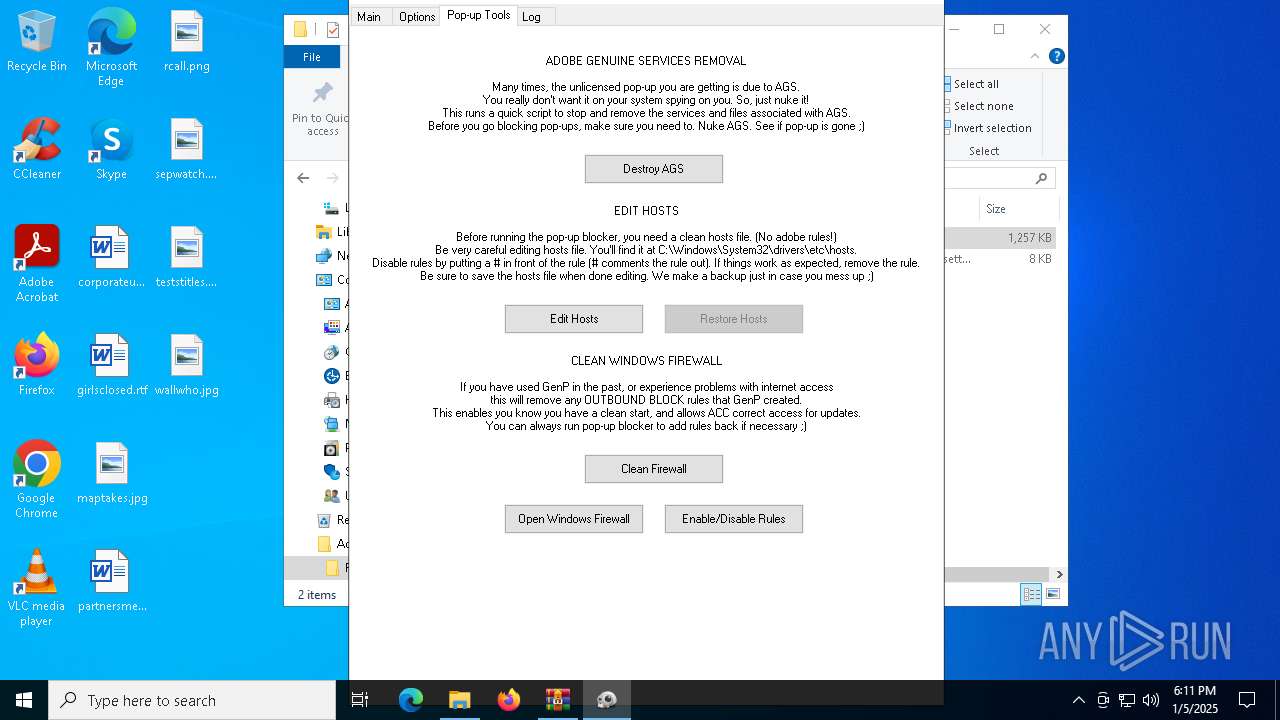
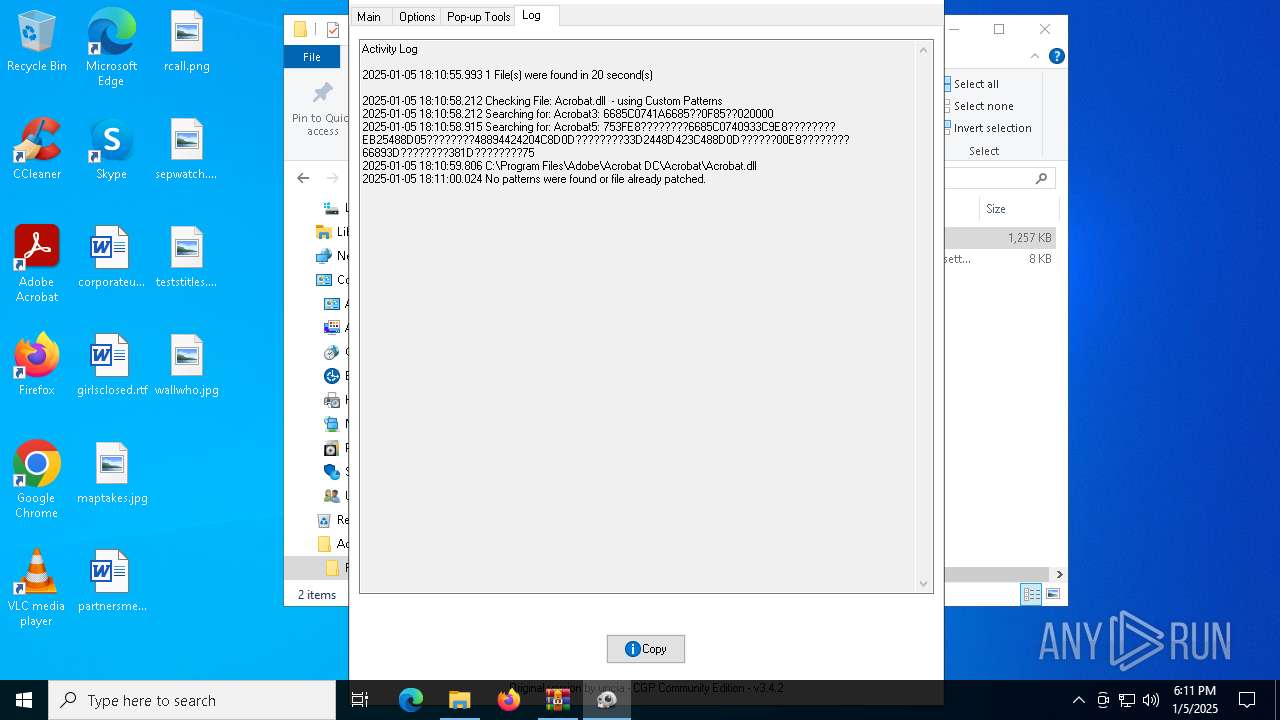
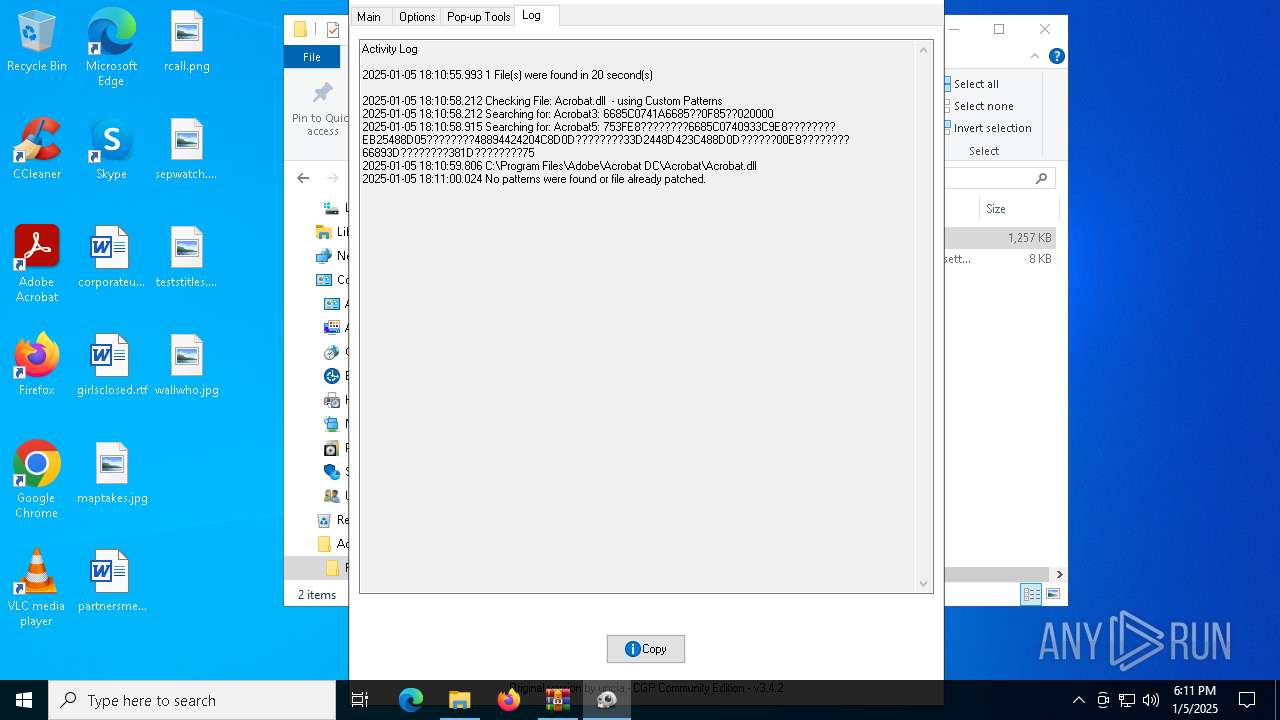
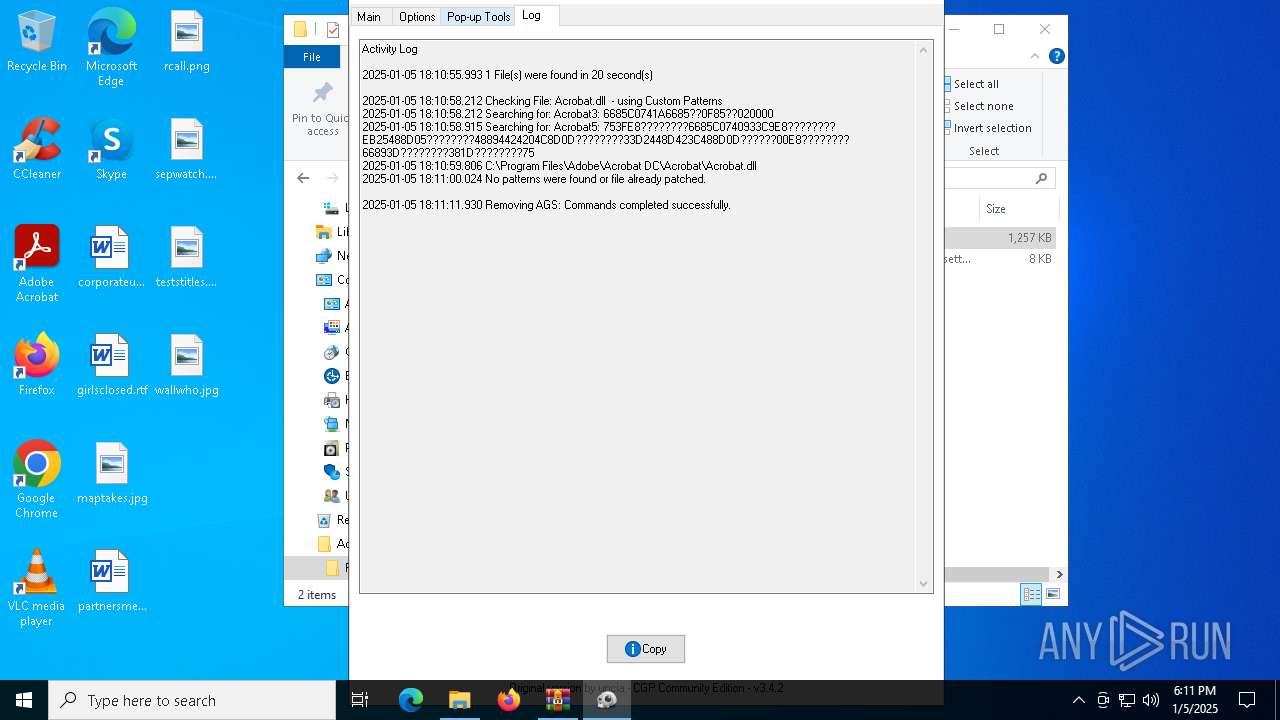
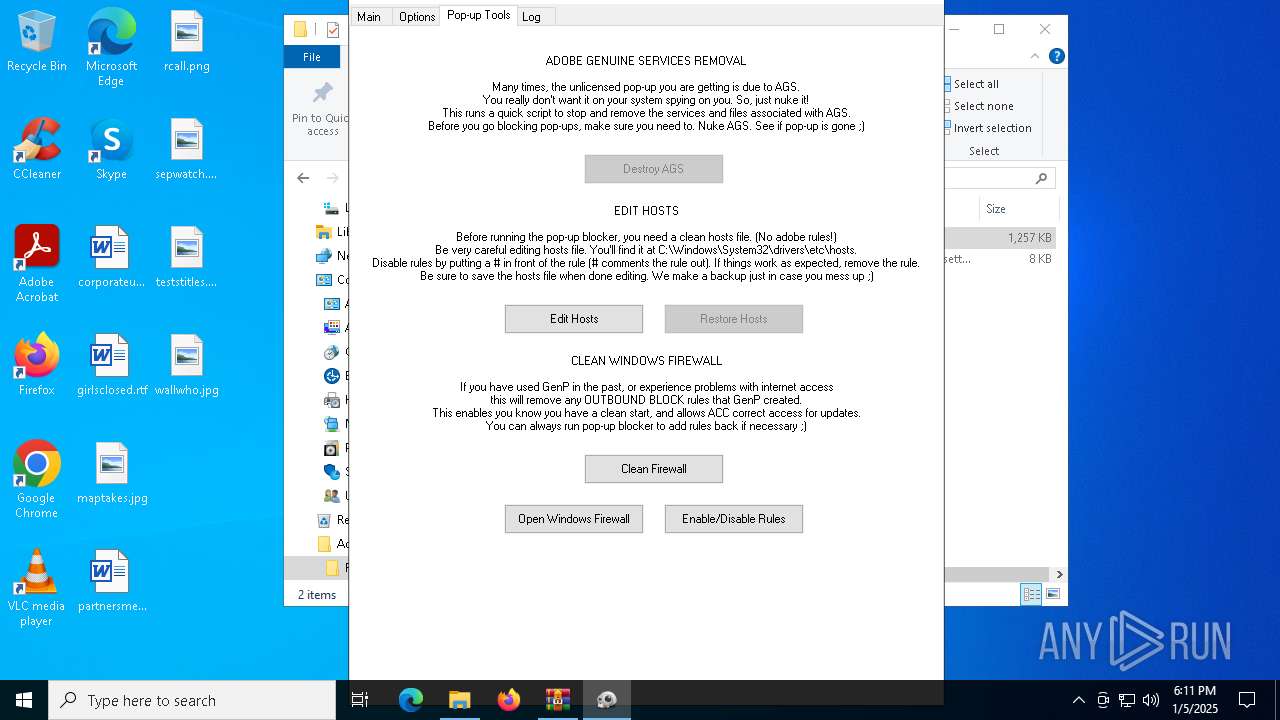
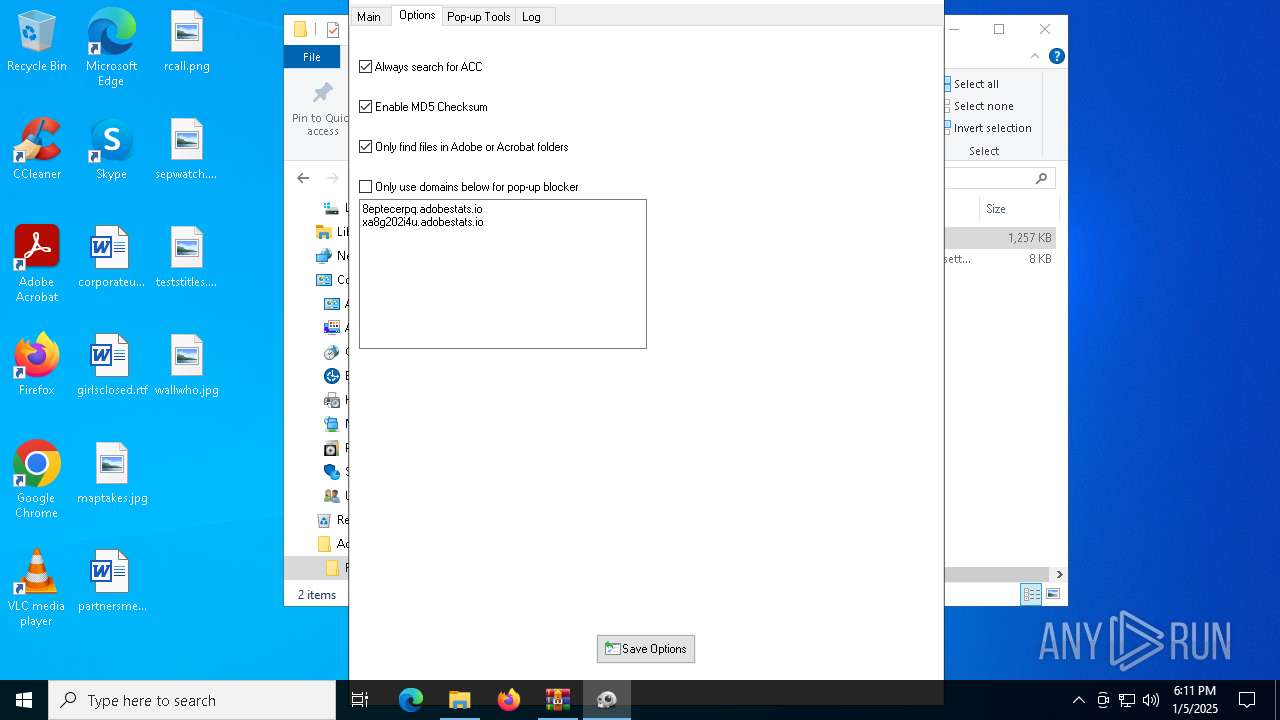
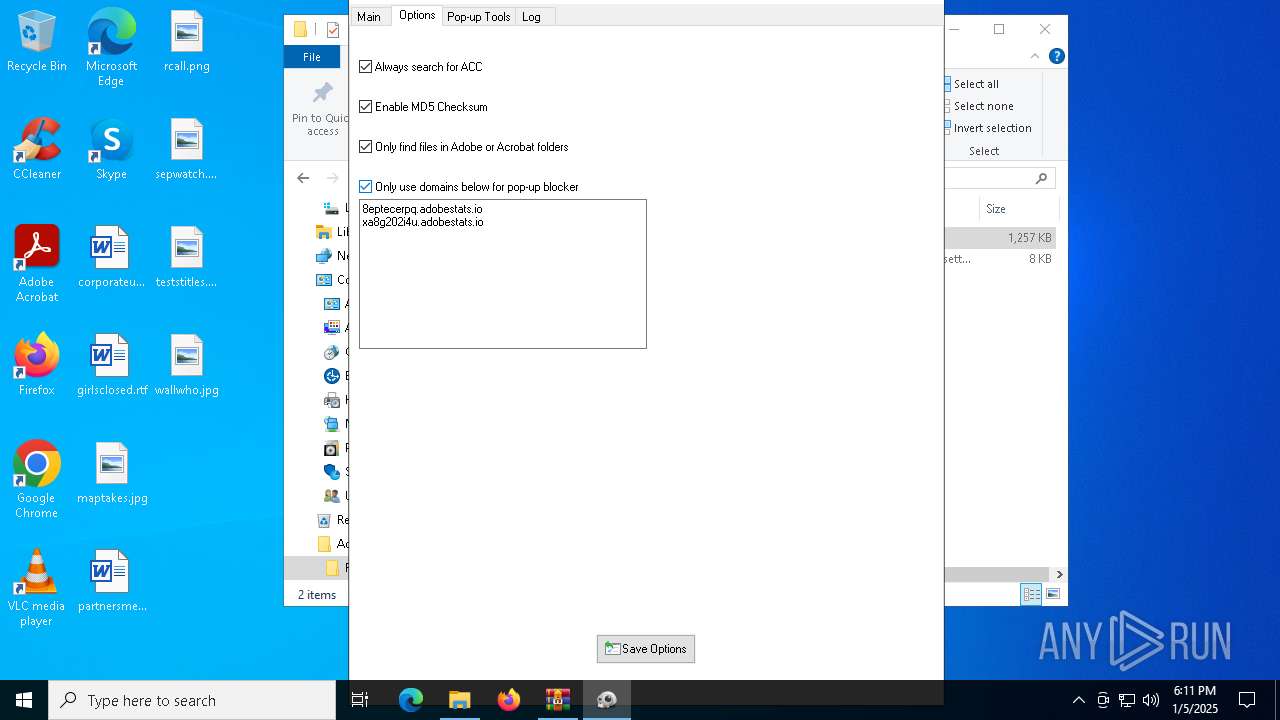
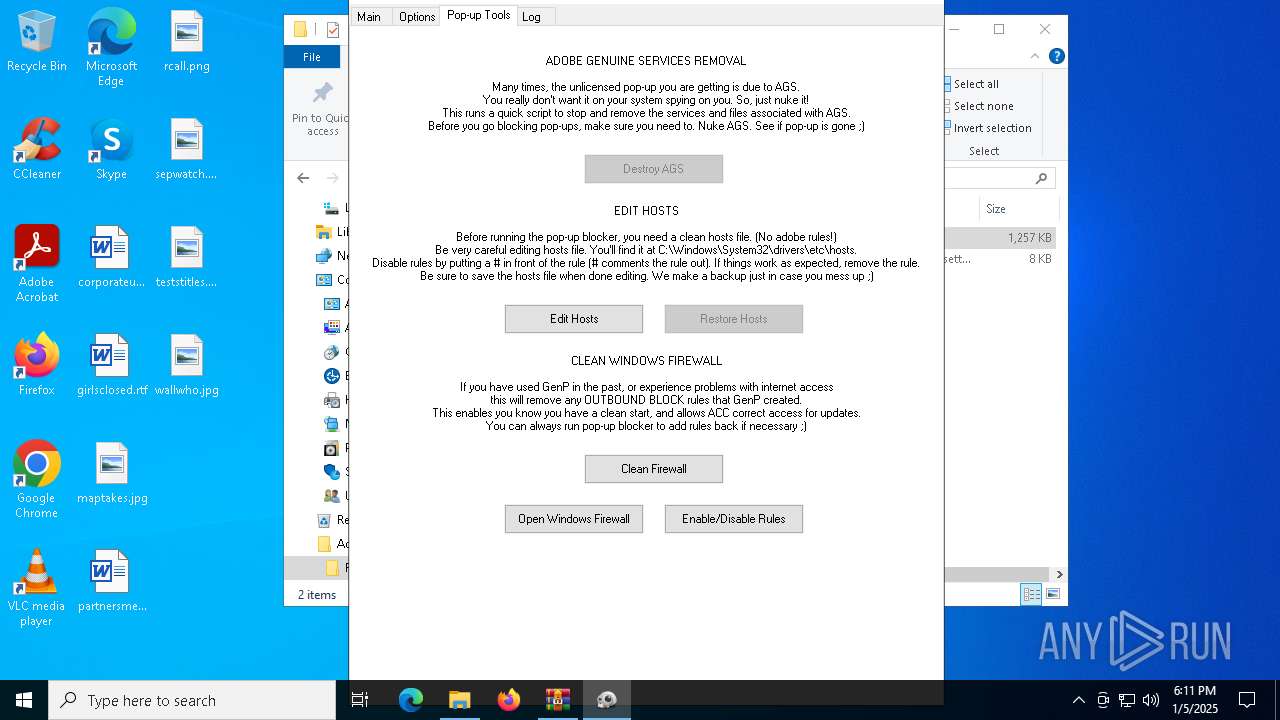
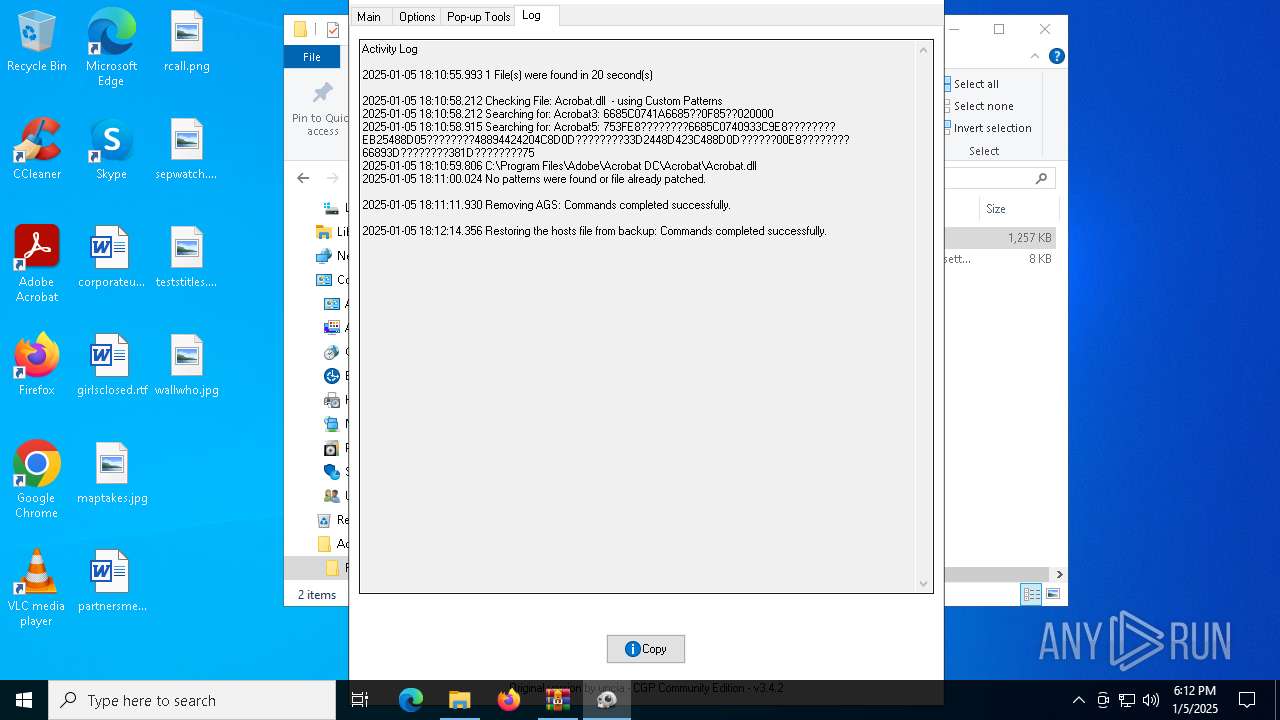
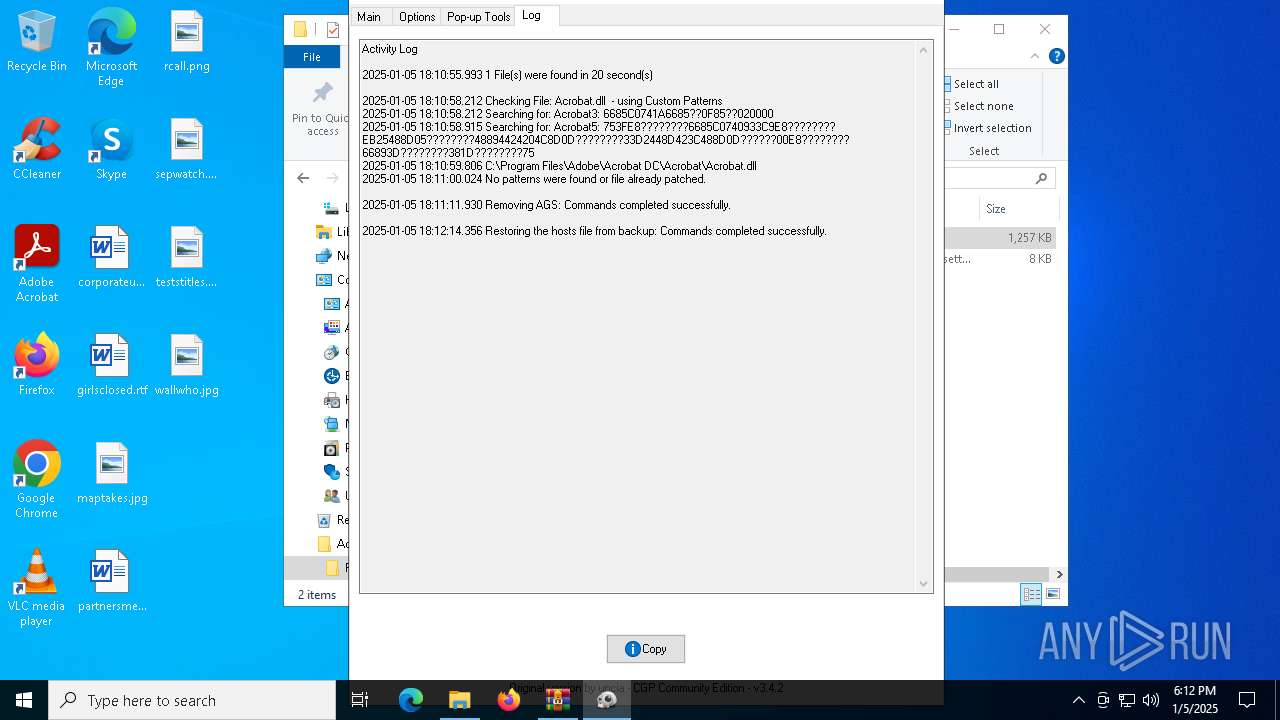
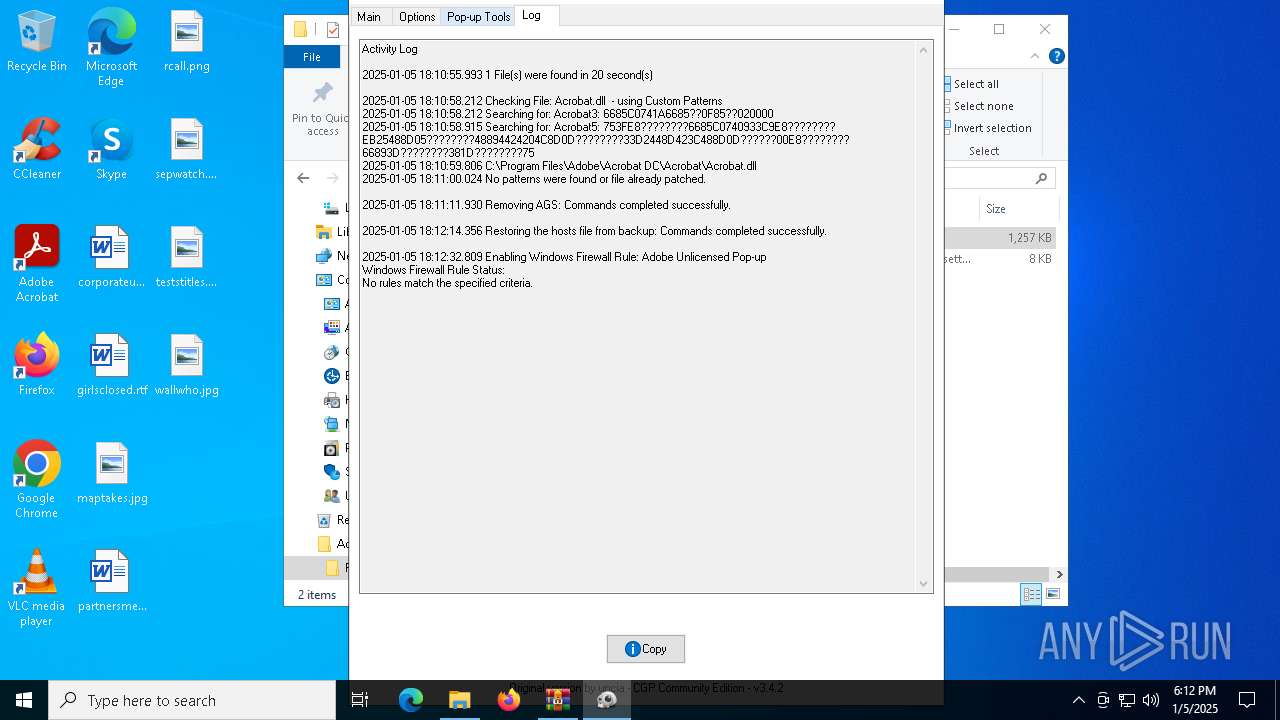
| File name: | Adobe-GenP-3.4.2-CGP.zip |
| Full analysis: | https://app.any.run/tasks/5bd3ed88-207b-48de-a801-7da9e644dddc |
| Verdict: | Malicious activity |
| Analysis date: | January 05, 2025, 18:08:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 08D5C8105B2C3C592DC9470615CC0174 |
| SHA1: | 66B3EB4DA007023B36B2E47DC5A8B6D81147B438 |
| SHA256: | 799E746EFEFE5B536F532D1D7F93CA03DDC2BD571494E5C6BB34A54FE274F79C |
| SSDEEP: | 24576:a43p9k9kSGSnXMssNJSC9mzO7Vnlnrdfjebwk3bqtkbbd86VocO71Fos2eAmiOQo:a43p9k9kSGSnXMssNJSCgzOBnlnrdfq2 |
MALICIOUS
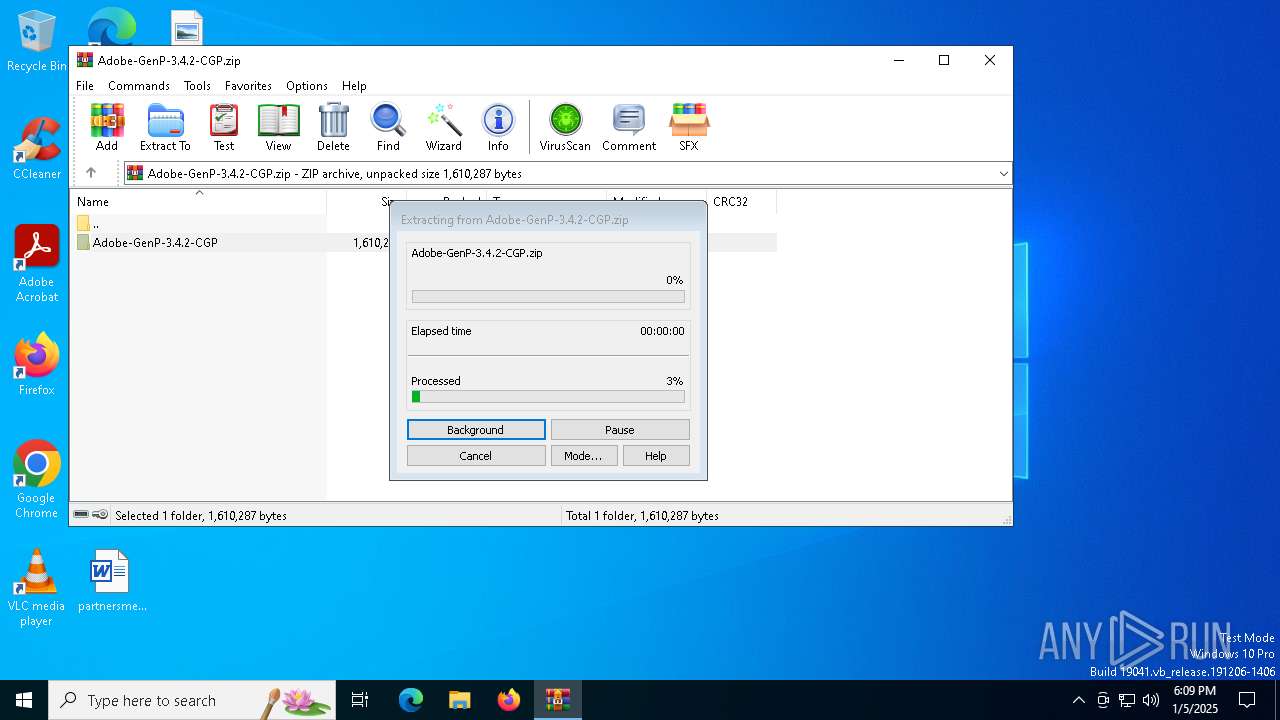
Generic archive extractor
- WinRAR.exe (PID: 2324)
Bypass execution policy to execute commands
- powershell.exe (PID: 3488)
- powershell.exe (PID: 2144)
Changes powershell execution policy (Bypass)
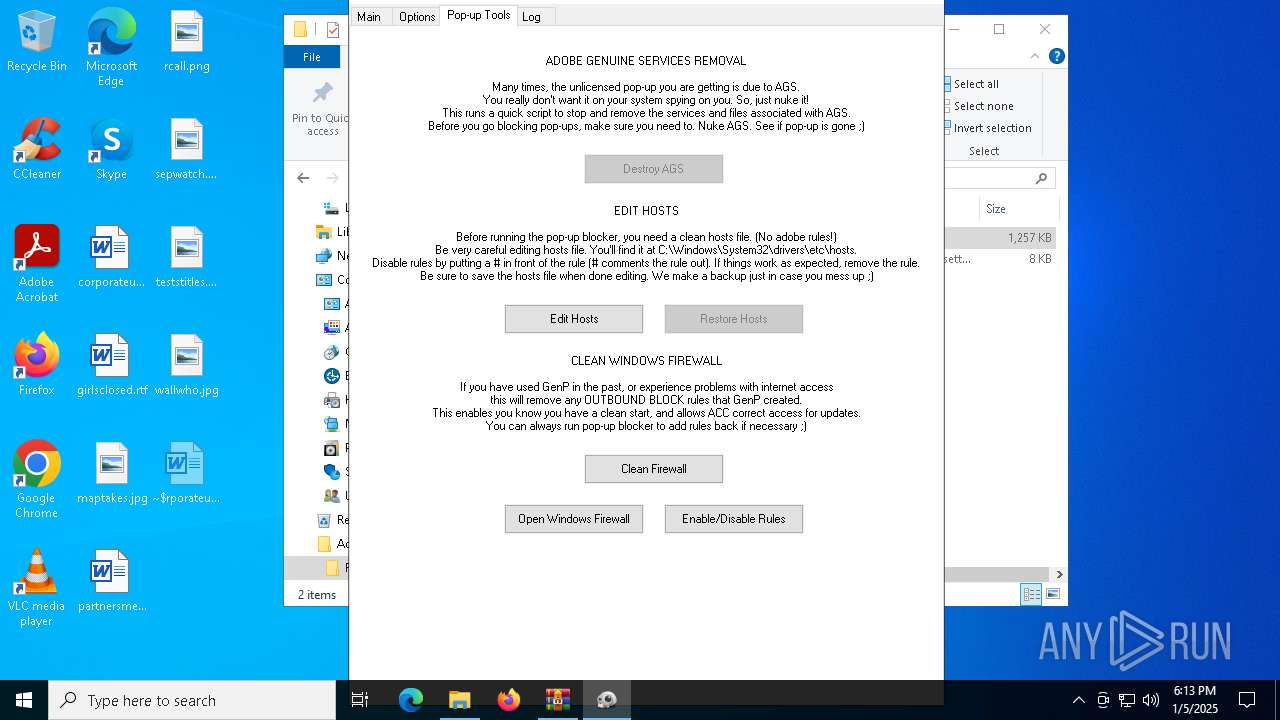
- AdobeGenP.exe (PID: 6904)
SUSPICIOUS
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 3488)
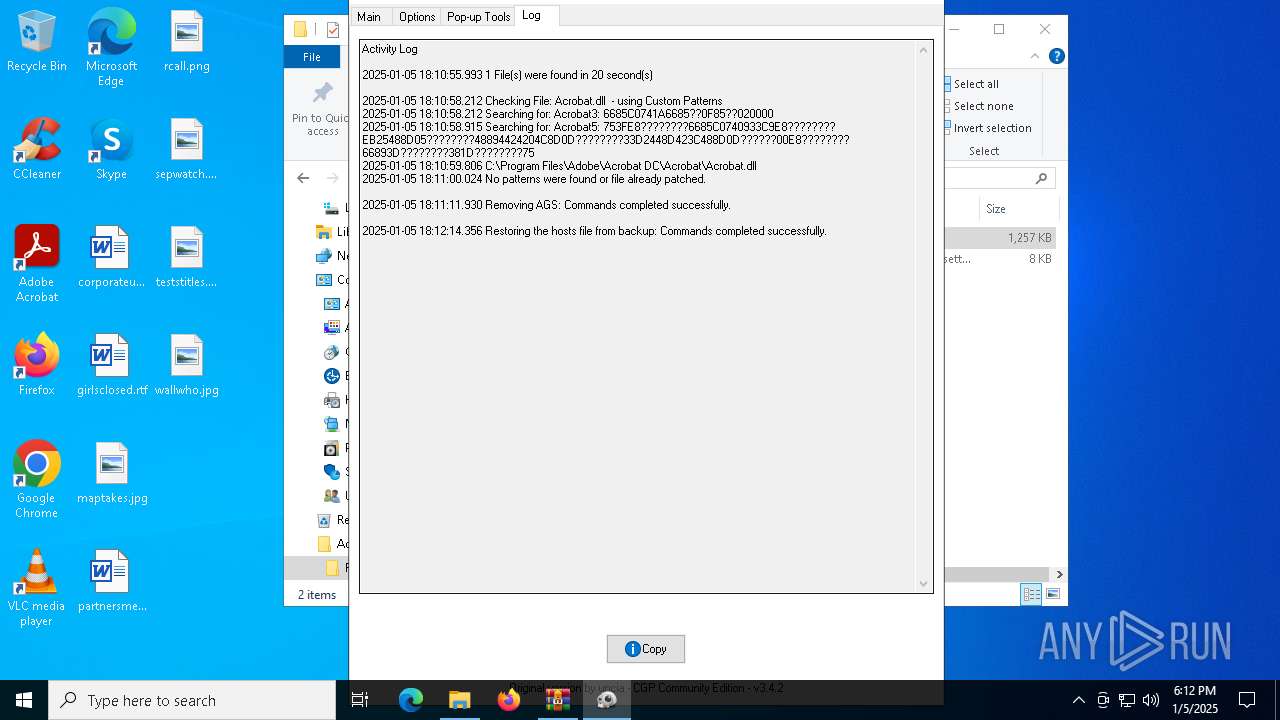
Removes files via Powershell
- powershell.exe (PID: 3488)
Likely accesses (executes) a file from the Public directory
- powershell.exe (PID: 3488)
Starts SC.EXE for service management
- powershell.exe (PID: 3488)
Kill processes via PowerShell
- powershell.exe (PID: 3488)
Base64-obfuscated command line is found
- AdobeGenP.exe (PID: 6904)
Starts POWERSHELL.EXE for commands execution
- AdobeGenP.exe (PID: 6904)
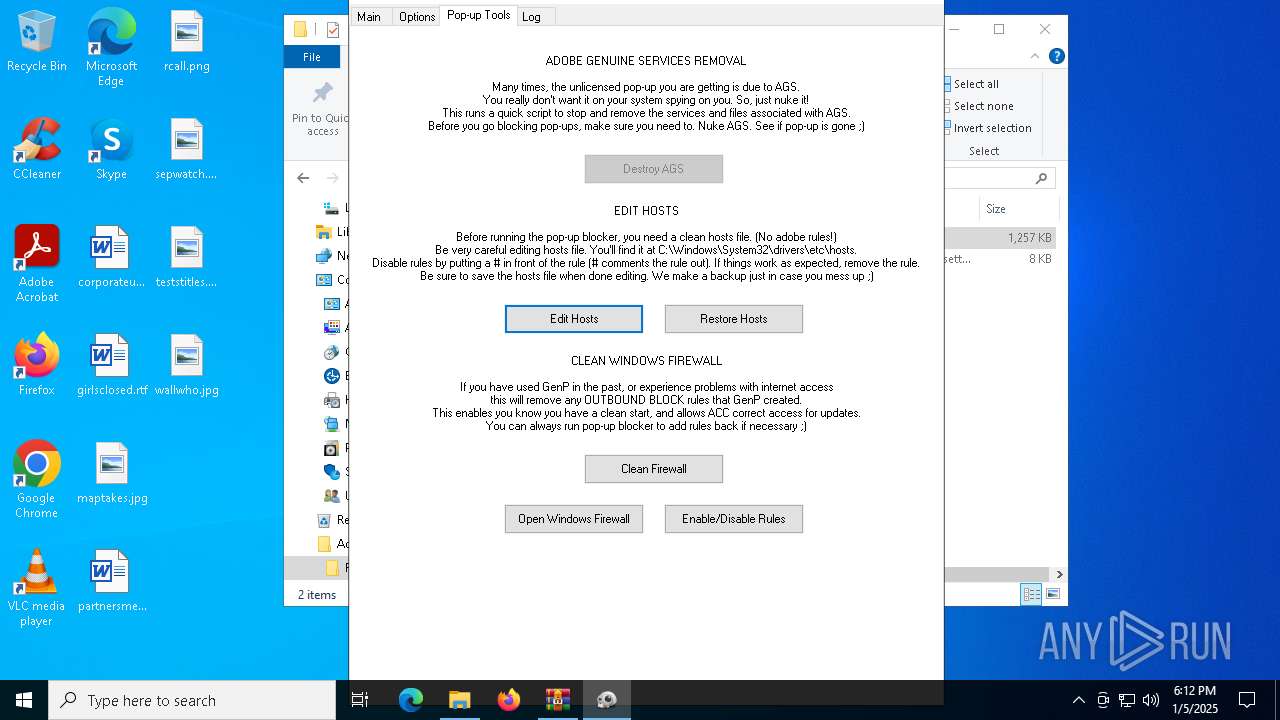
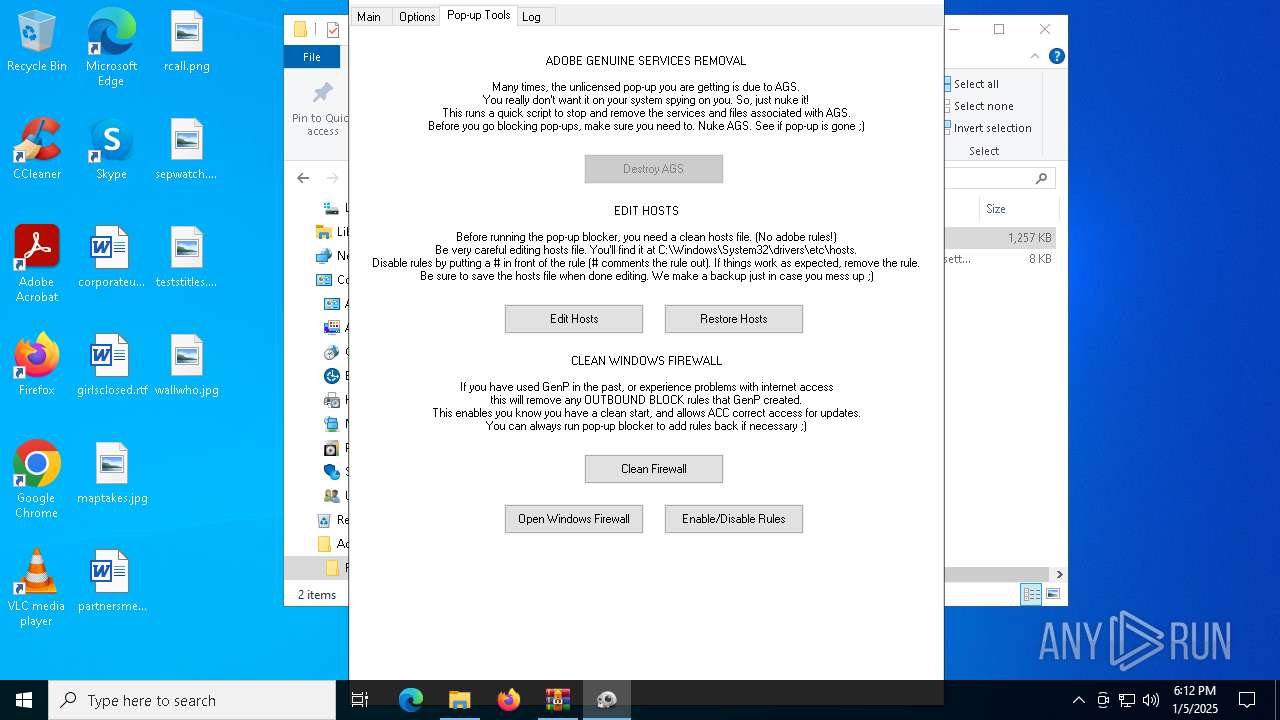
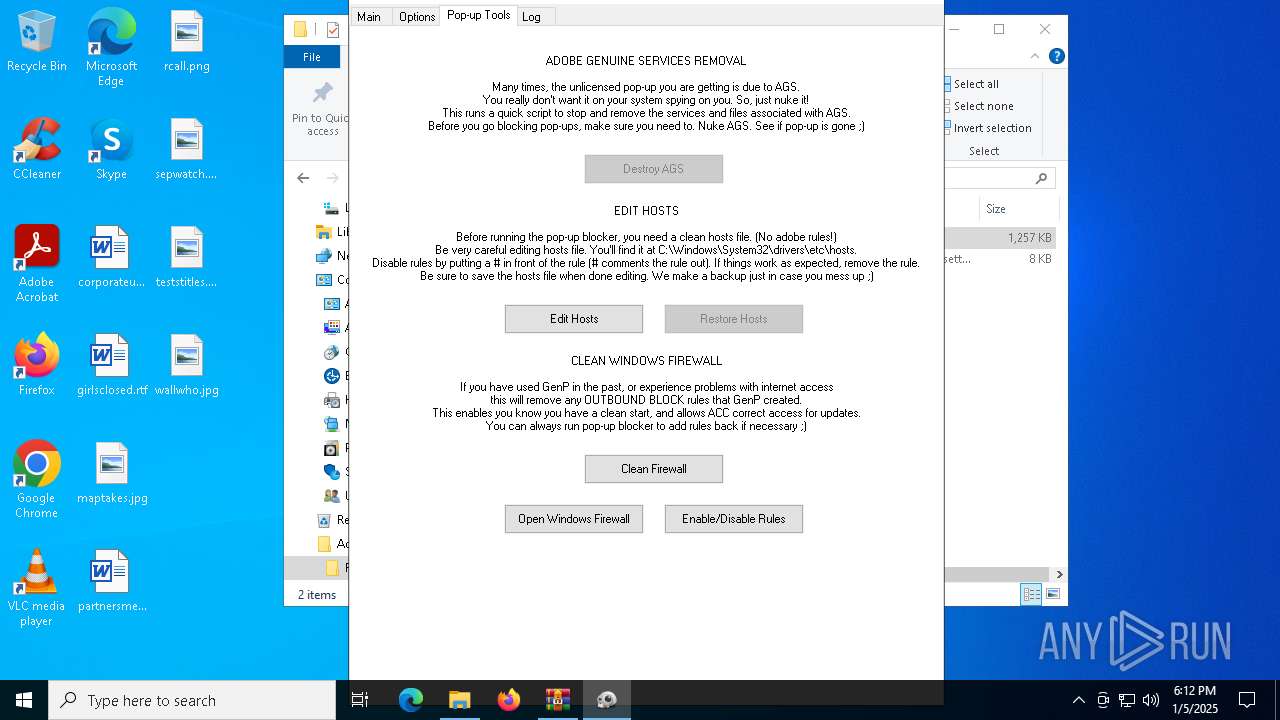
Start notepad (likely ransomware note)
- AdobeGenP.exe (PID: 6904)
Windows service management via SC.EXE
- sc.exe (PID: 6408)
- sc.exe (PID: 2976)
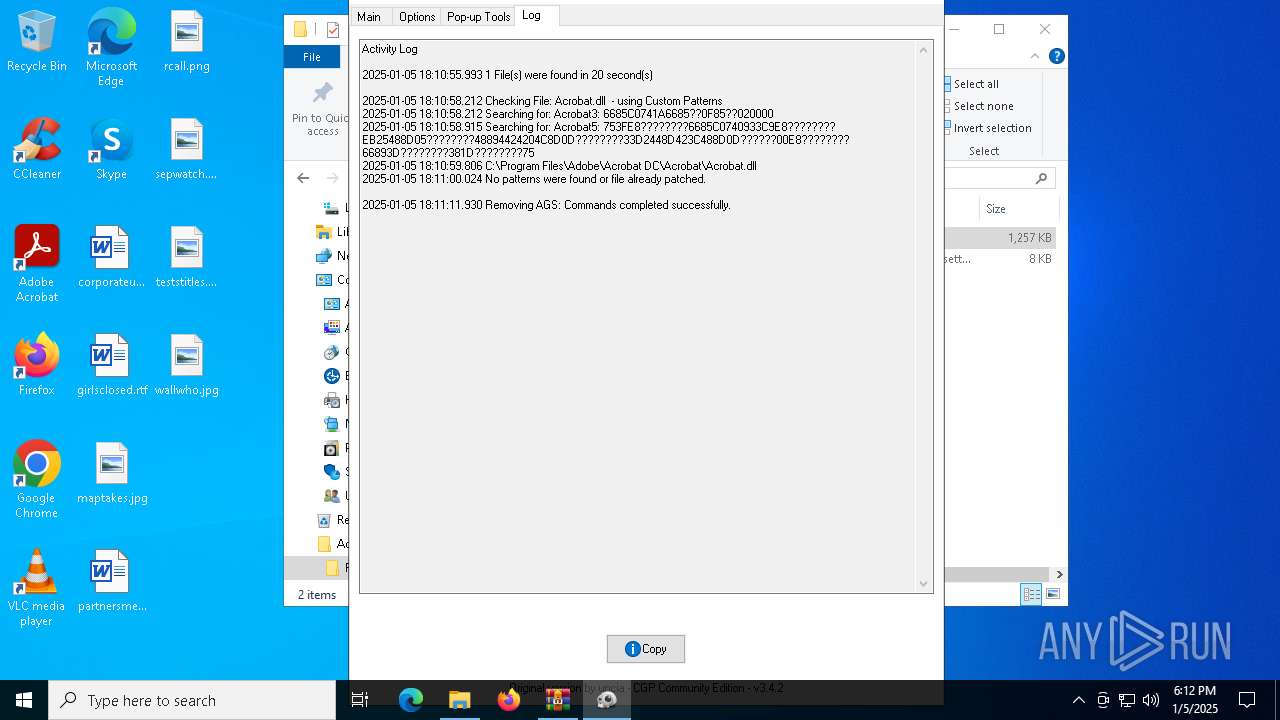
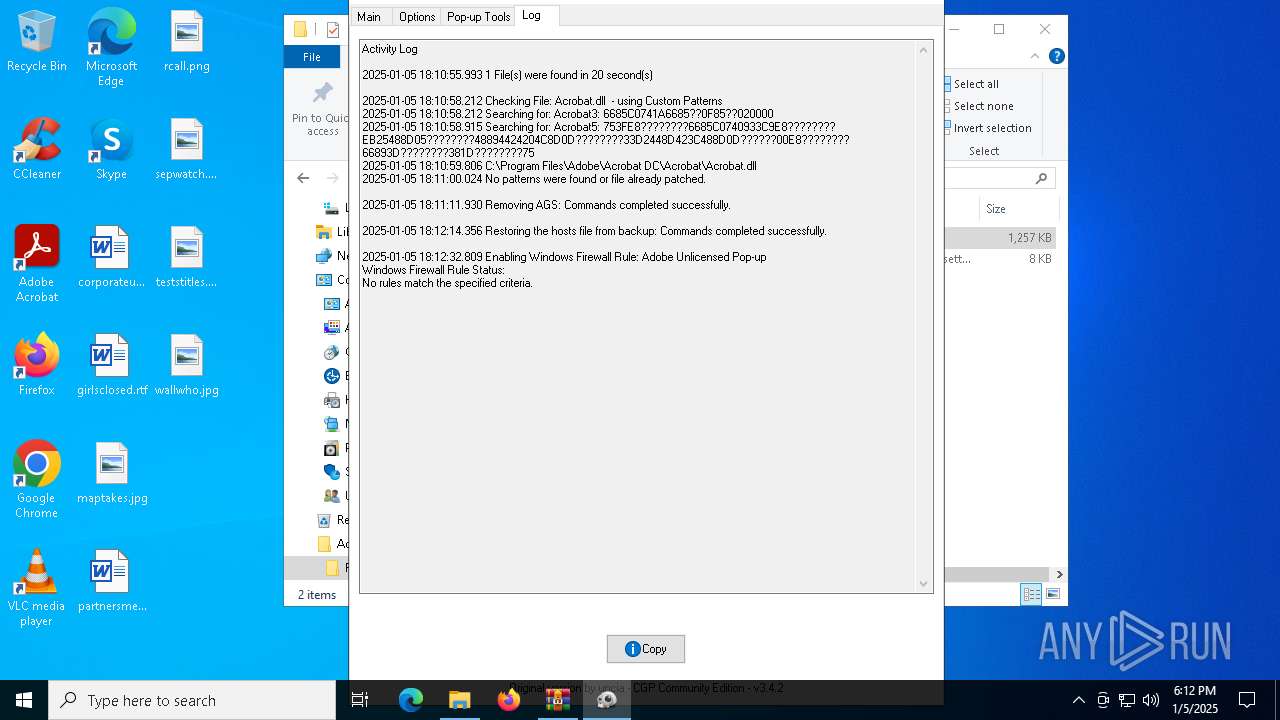
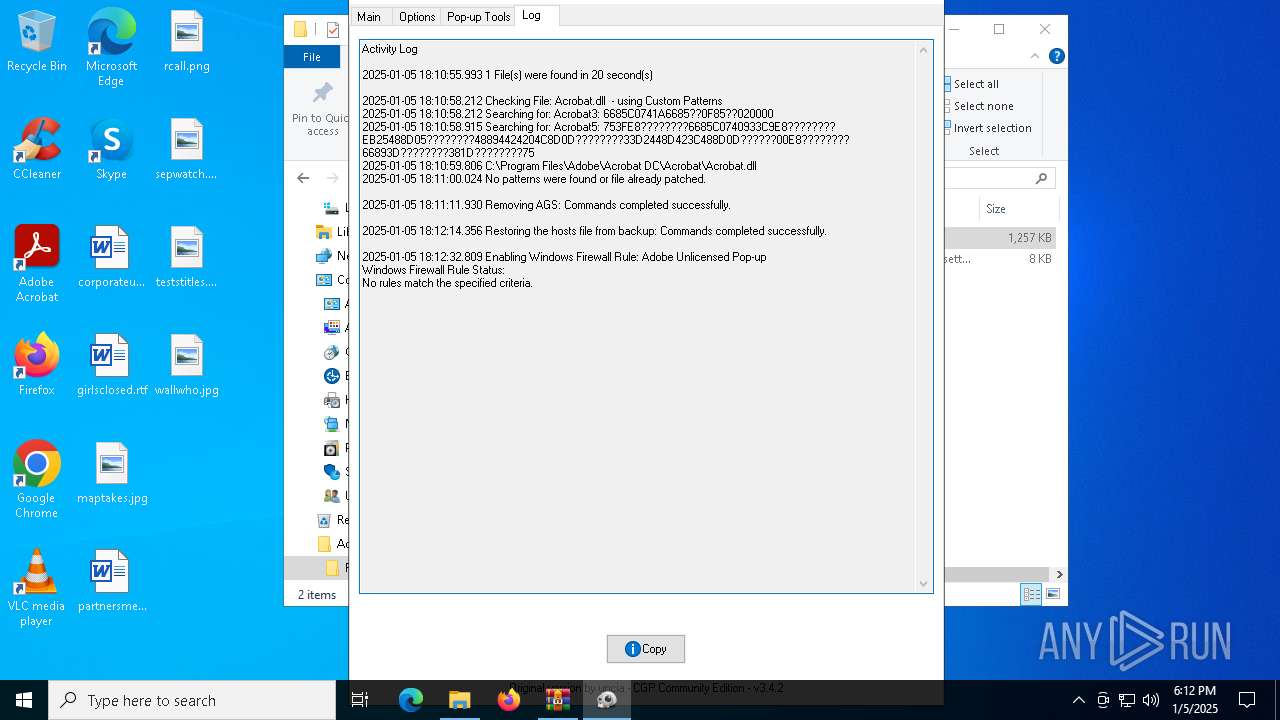
Creates files in the driver directory
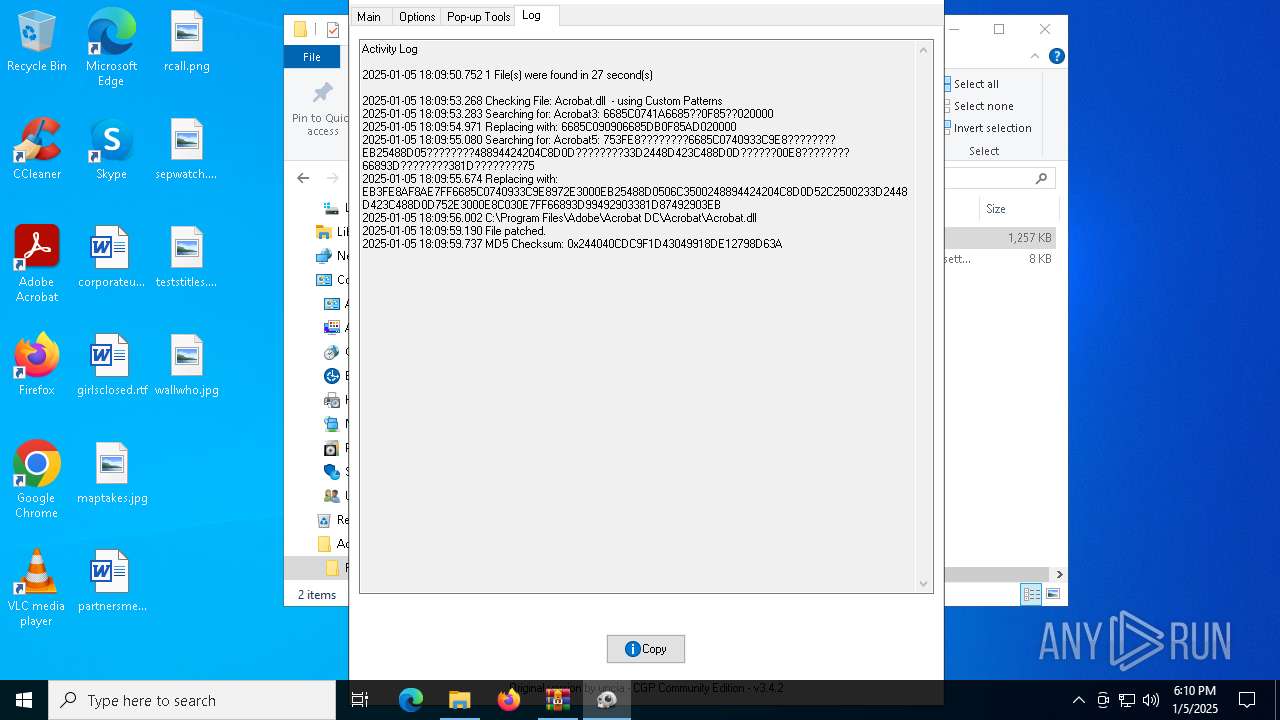
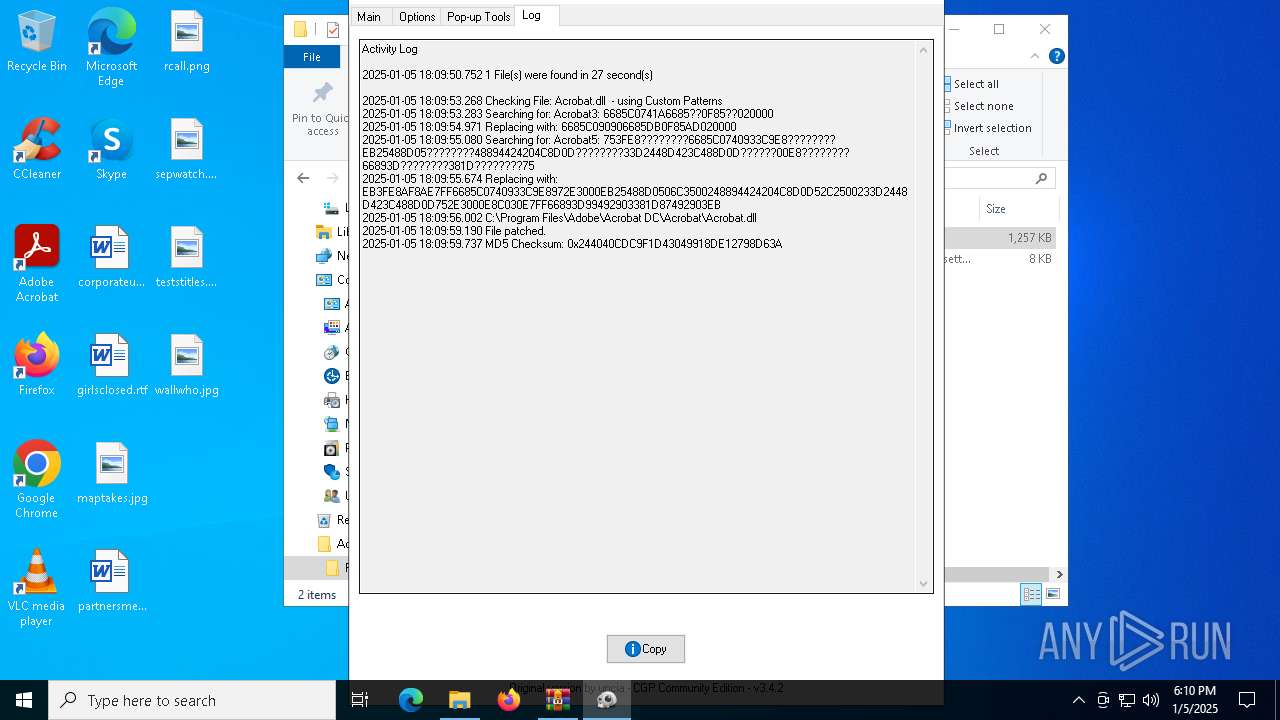
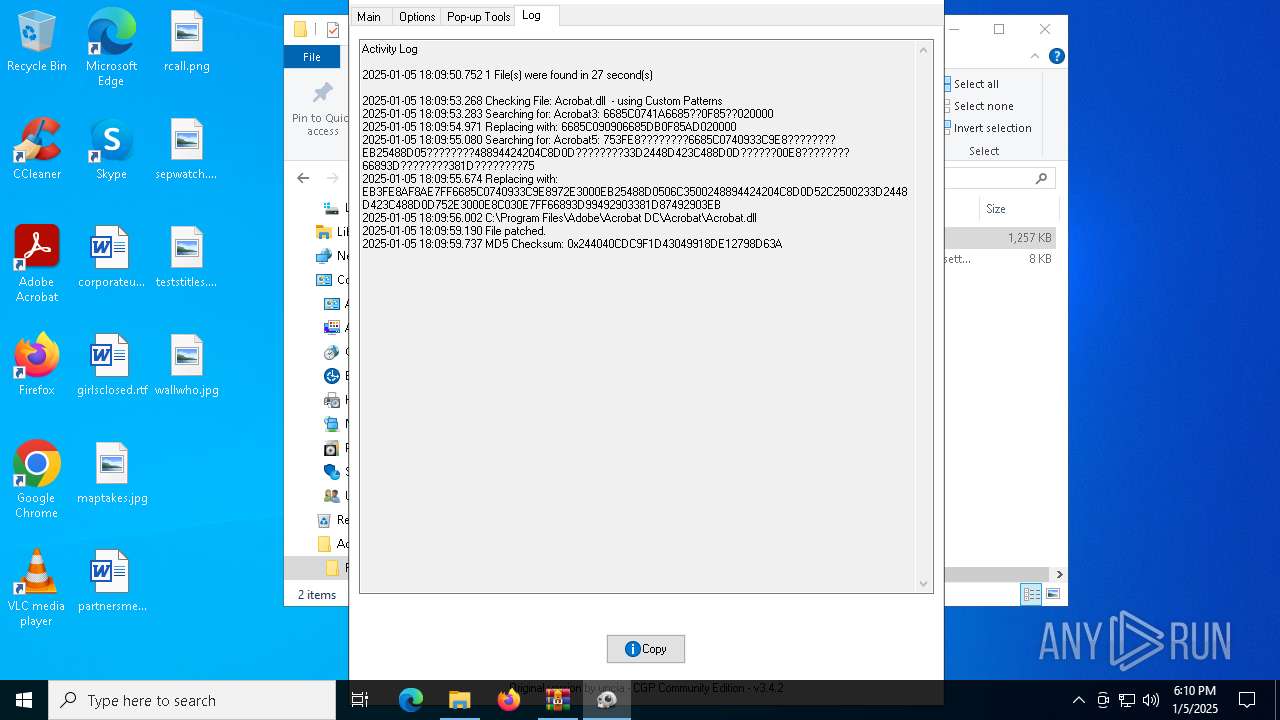
- AdobeGenP.exe (PID: 6904)
Uses NETSH.EXE to change the status of the firewall
- AdobeGenP.exe (PID: 6904)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2324)
- powershell.exe (PID: 2144)
Manual execution by a user
- AdobeGenP.exe (PID: 6532)
- AdobeGenP.exe (PID: 6716)
- Acrobat.exe (PID: 2972)
- AdobeGenP.exe (PID: 4976)
- AdobeGenP.exe (PID: 6904)
- mspaint.exe (PID: 2392)
- Acrobat.exe (PID: 5628)
- WINWORD.EXE (PID: 6432)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2324)
The sample compiled with english language support
- WinRAR.exe (PID: 2324)
Checks supported languages
- AdobeGenP.exe (PID: 6716)
- AdobeGenP.exe (PID: 6904)
Reads mouse settings
- AdobeGenP.exe (PID: 6716)
- AdobeGenP.exe (PID: 6904)
Reads the computer name
- AdobeGenP.exe (PID: 6716)
- AdobeGenP.exe (PID: 6904)
Creates files in the program directory
- AdobeGenP.exe (PID: 6716)
Reads the machine GUID from the registry
- AdobeGenP.exe (PID: 6716)
The process uses AutoIt
- AdobeGenP.exe (PID: 6716)
- AdobeGenP.exe (PID: 6904)
Application launched itself
- Acrobat.exe (PID: 2972)
- AcroCEF.exe (PID: 5888)
- Acrobat.exe (PID: 5628)
- AcroCEF.exe (PID: 1752)
Sends debugging messages
- Acrobat.exe (PID: 3544)
- Acrobat.exe (PID: 6696)
- WINWORD.EXE (PID: 6432)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3488)
- powershell.exe (PID: 2144)
Reads security settings of Internet Explorer
- notepad.exe (PID: 624)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:10:10 02:00:08 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Adobe-GenP-3.4.2-CGP/ |
Total processes
181
Monitored processes
41
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | netsh advfirewall firewall set rule name="Adobe Unlicensed Pop-up" new enable=yes | C:\Windows\System32\netsh.exe | — | AdobeGenP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 188 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3024 --field-trial-handle=1648,i,18277335778188213935,4608896613796948806,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 444 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --first-renderer-process --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2344 --field-trial-handle=1648,i,4532256610509293480,6216210625794507326,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
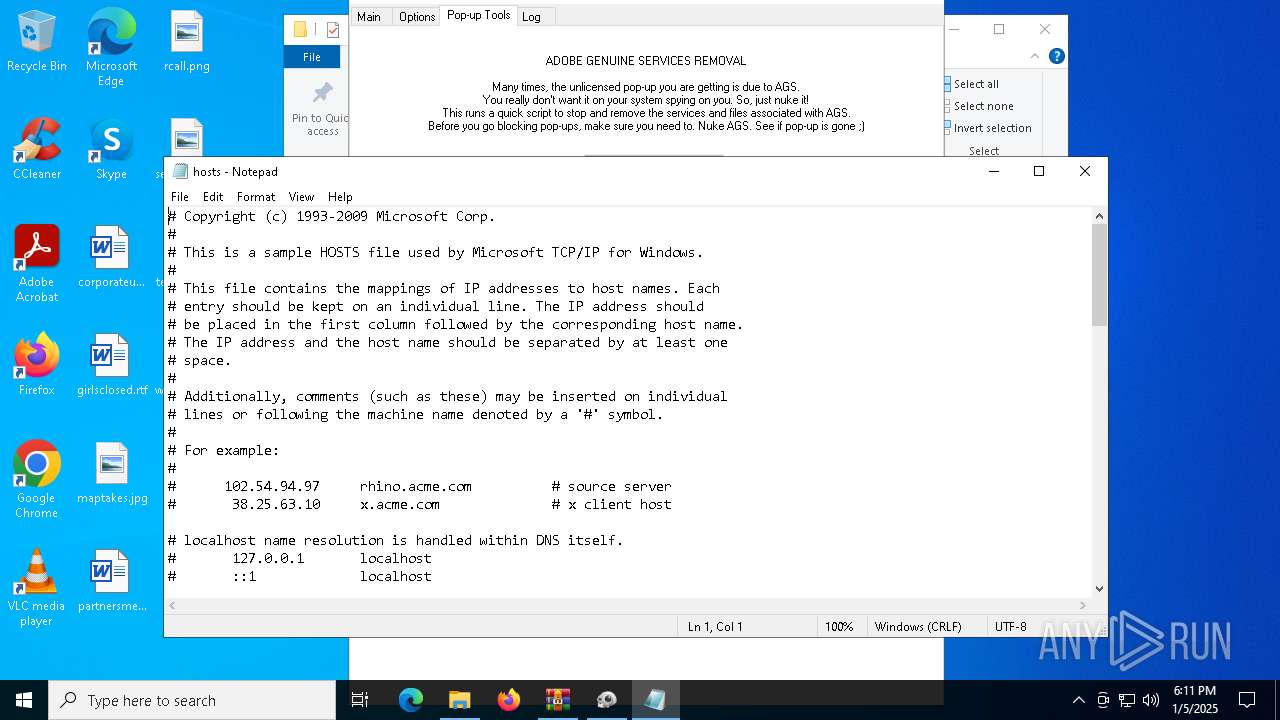
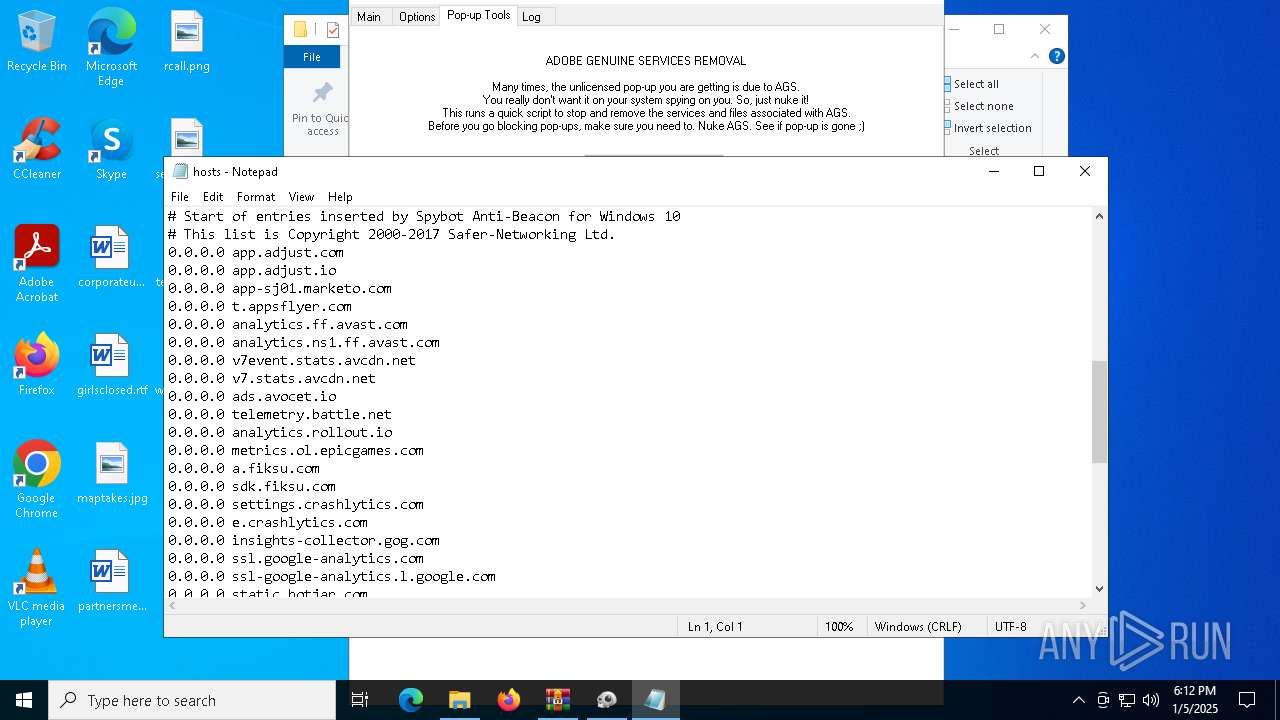
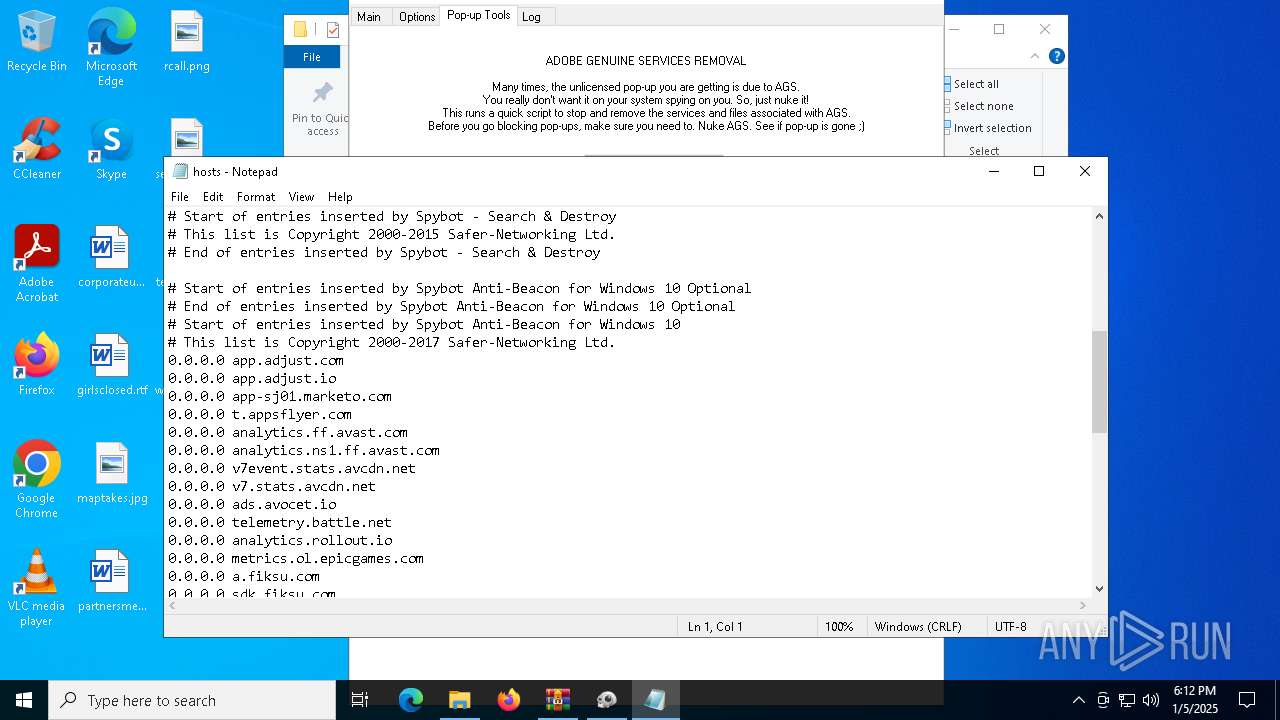
| 624 | notepad.exe C:\Windows\System32\drivers\etc\hosts | C:\Windows\System32\notepad.exe | — | AdobeGenP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=72 --field-trial-handle=1648,i,4532256610509293480,6216210625794507326,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | AcroCEF.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1752 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1916 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2144 | PowerShell Set-ExecutionPolicy Bypass -scope Process -Force;try{$name = (Get-NetFirewallRule -DisplayName 'Adobe Unlicensed Pop-up').Name} catch{$name='no'};If($name -ne 'no'){(Get-NetFirewallRule -Name $name).Enabled}; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | AdobeGenP.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Adobe-GenP-3.4.2-CGP.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2392 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\maptakes.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
47 366
Read events
46 794
Write events
536
Delete events
36
Modification events
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Adobe-GenP-3.4.2-CGP.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2972) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (3544) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
Executable files
3
Suspicious files
326
Text files
35
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6716 | AdobeGenP.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.dll.bak | — | |
MD5:— | SHA256:— | |||
| 6716 | AdobeGenP.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.dll | — | |
MD5:— | SHA256:— | |||
| 3544 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.35597\Adobe-GenP-3.4.2-CGP\Source\RunAsTI.exe | executable | |
MD5:80454E70784F1DDB0C91D41469E2498D | SHA256:A3E0BA70BA908DE8A75825C3A1FF36147E02C686280993C2CAA8A9A6968764B0 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.35597\Adobe-GenP-3.4.2-CGP\Release\config.ini | ini | |
MD5:F2EF246F608DF6970968FBDE300CA7AA | SHA256:3709022A13F41251621C34AA2AD72301AAD4D5B1CEB8A5095A3FCDAEDBD73804 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.35597\Adobe-GenP-3.4.2-CGP\Source\AdobeGenP-3.4.2.au3 | text | |
MD5:85F3842816D6FC08E92DFEBB2903A7F8 | SHA256:E9B47E9B429359D2374D398B97C486546E93BC0B0B7A65637DE123F339134ECE | |||
| 3544 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.35597\Adobe-GenP-3.4.2-CGP\Release\AdobeGenP.exe | executable | |
MD5:6F1A436F28CB5386B19C15FB6DE09D42 | SHA256:B09EC2AC41CC220B2B2B68B23BF120DCB518850341D8E3E088B50185EF624ED7 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2324.35597\Adobe-GenP-3.4.2-CGP\Source\Skull.ico | image | |
MD5:C37B537E533890560FE52664A7F1C1A0 | SHA256:1532311559D17CF7ECC0BE72FB47EC7D0EA086C414E2280566E0803133FD1D50 | |||
| 5888 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Local Storage\leveldb\LOG.old~RF148173.TMP | text | |
MD5:ED7D8AAE48211E2BFAF557130572C62A | SHA256:A5CF8D8ADC86DCA357396AF7E3A24A116072D5C1E5552EEB76601AE2673DED6E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
51
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1684 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1684 | svchost.exe | GET | 200 | 184.30.230.103:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7116 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7116 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6620 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6432 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5628 | Acrobat.exe | PROPFIND | 501 | 2.20.245.140:80 | http://www.adobe.com/go/homeacrordrunified18_2018 | unknown | — | — | whitelisted |
5628 | Acrobat.exe | GET | 301 | 2.20.245.140:80 | http://www.adobe.com/go/homeacrordrunified18_2018 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1684 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1684 | svchost.exe | 184.30.230.103:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1684 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| unknown |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|