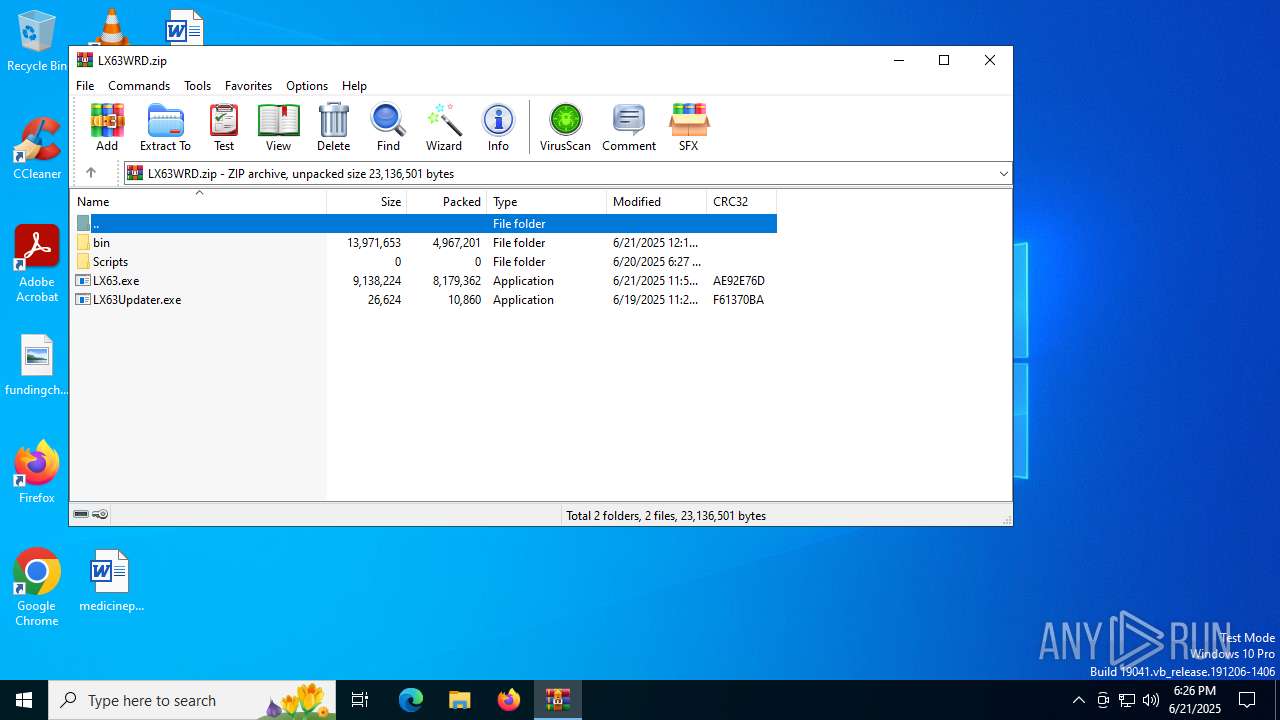
| File name: | LX63WRD.zip |
| Full analysis: | https://app.any.run/tasks/aada6160-c814-44e0-b7d4-552c30f7996f |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 18:25:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 3B75B173A75BE3AD4DE973D92F048245 |
| SHA1: | 6ABBFFE6849A83A56F13F3B4AF3503582875E670 |
| SHA256: | 7989B7BF5190EA5076E2B12309C2B04D2545135C6E403F22273362BF30D3DD61 |
| SSDEEP: | 98304:fZffVeGNabqpVnf2MB4RDPSPw8i0WTW3fGk3kD8uBPd+92X9jpLZ8upBRBDgD58z:zfuxD7tlgwro7NEYUM0PDvCR4Z |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6532)
SUSPICIOUS
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 4476)
- net.exe (PID: 1164)
- cmd.exe (PID: 3844)
- net.exe (PID: 1880)
Starts process via Powershell
- powershell.exe (PID: 2276)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4476)
- cmd.exe (PID: 1336)
Executing commands from a ".bat" file
- powershell.exe (PID: 2276)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2276)
- cmd.exe (PID: 3844)
Application launched itself
- cmd.exe (PID: 3844)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1336)
Executable content was dropped or overwritten
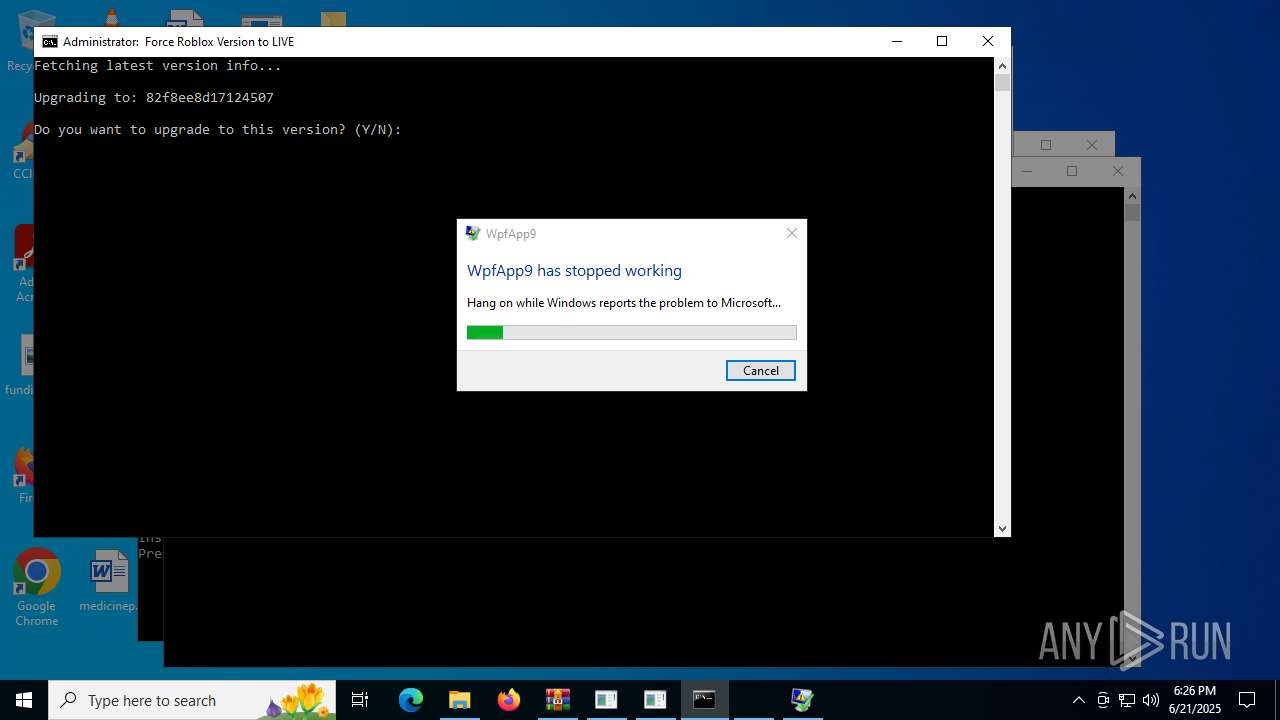
- LX63.exe (PID: 984)
Reads security settings of Internet Explorer
- LX63.exe (PID: 984)
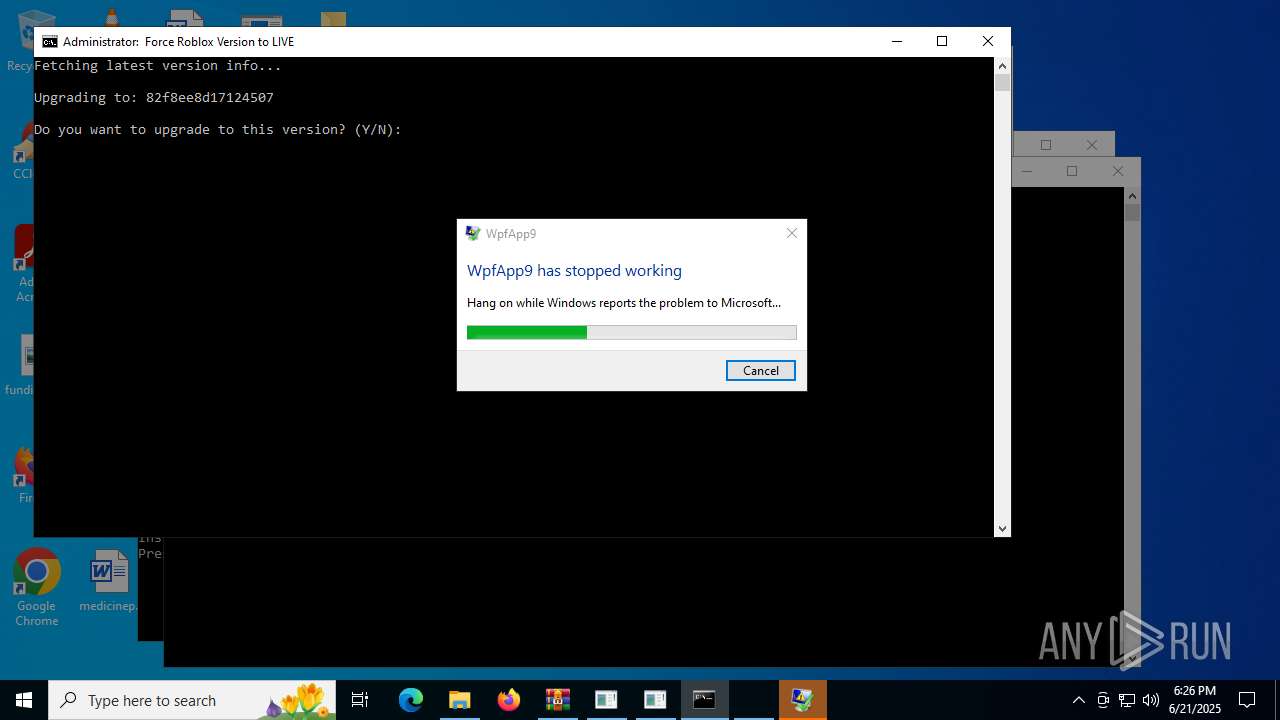
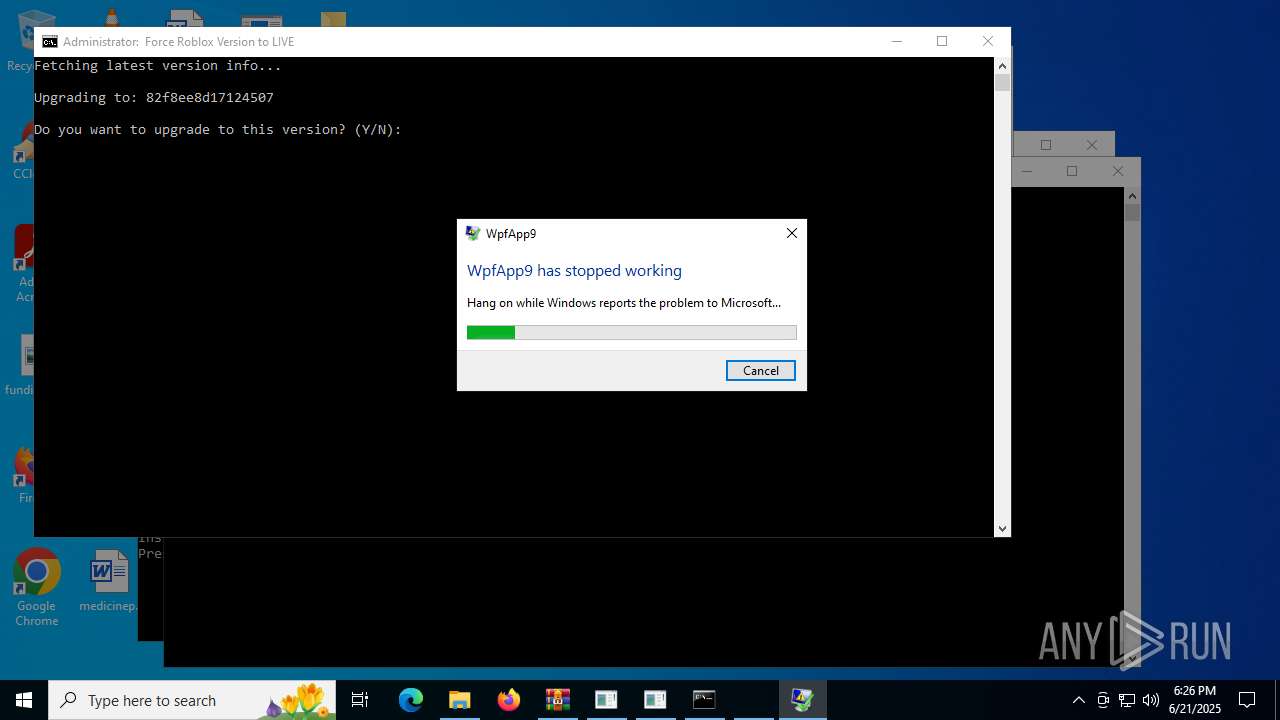
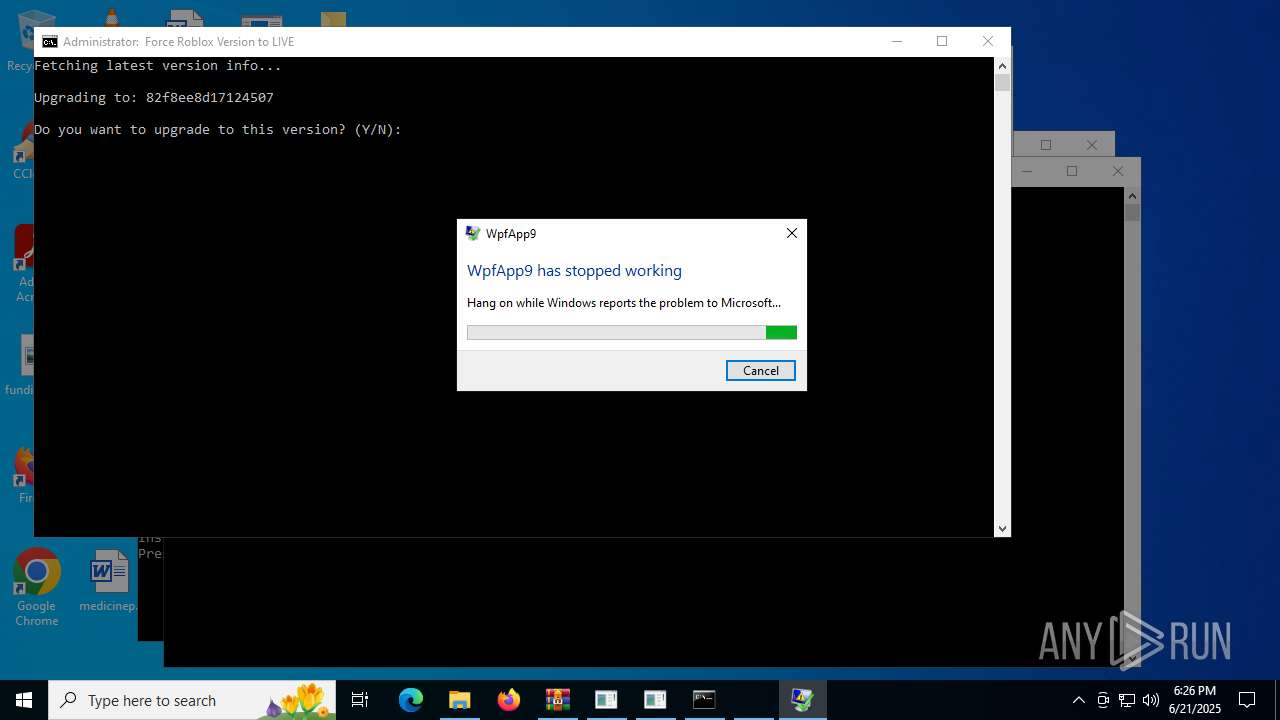
Executes application which crashes
- LX63.exe (PID: 984)
INFO
Manual execution by a user
- cmd.exe (PID: 4476)
- LX63Updater.exe (PID: 5532)
- Injector.exe (PID: 2804)
- LX63.exe (PID: 984)
Checks supported languages
- LX63Updater.exe (PID: 5532)
- Injector.exe (PID: 2804)
- LX63.exe (PID: 984)
Reads the computer name
- LX63Updater.exe (PID: 5532)
- LX63.exe (PID: 984)
Reads the machine GUID from the registry
- LX63Updater.exe (PID: 5532)
- LX63.exe (PID: 984)
Disables trace logs
- LX63Updater.exe (PID: 5532)
- powershell.exe (PID: 4172)
- LX63.exe (PID: 984)
Checks proxy server information
- LX63Updater.exe (PID: 5532)
- powershell.exe (PID: 4172)
- WerFault.exe (PID: 6368)
- LX63.exe (PID: 984)
- slui.exe (PID: 3476)
- WerFault.exe (PID: 5724)
Reads the software policy settings
- LX63Updater.exe (PID: 5532)
- LX63.exe (PID: 984)
- WerFault.exe (PID: 5724)
- slui.exe (PID: 3476)
- WerFault.exe (PID: 6368)
Create files in a temporary directory
- LX63Updater.exe (PID: 5532)
- LX63.exe (PID: 984)
Reads Environment values
- LX63.exe (PID: 984)
Creates files or folders in the user directory
- WerFault.exe (PID: 6368)
- WerFault.exe (PID: 5724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:06:21 15:15:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | bin/ |
Total processes
155
Monitored processes
20
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 984 | "C:\Users\admin\Desktop\LX63.exe" | C:\Users\admin\Desktop\LX63.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WpfApp9 Exit code: 3221226525 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1164 | net session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
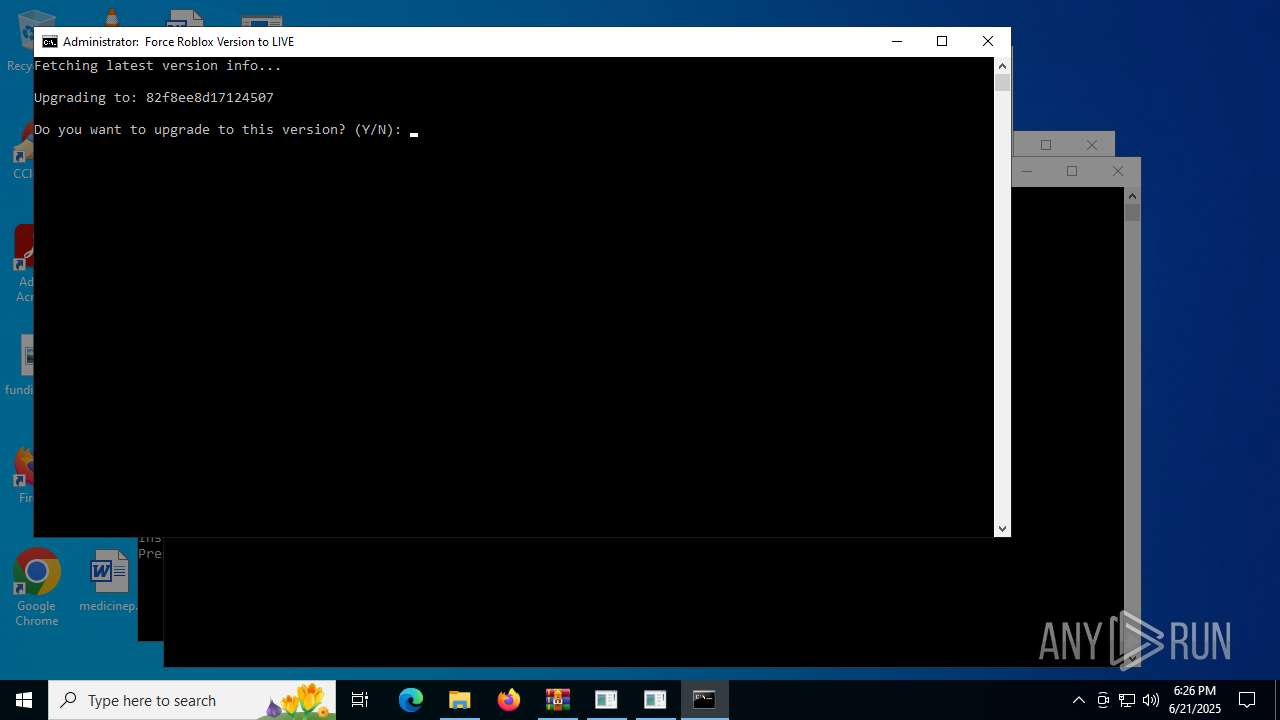
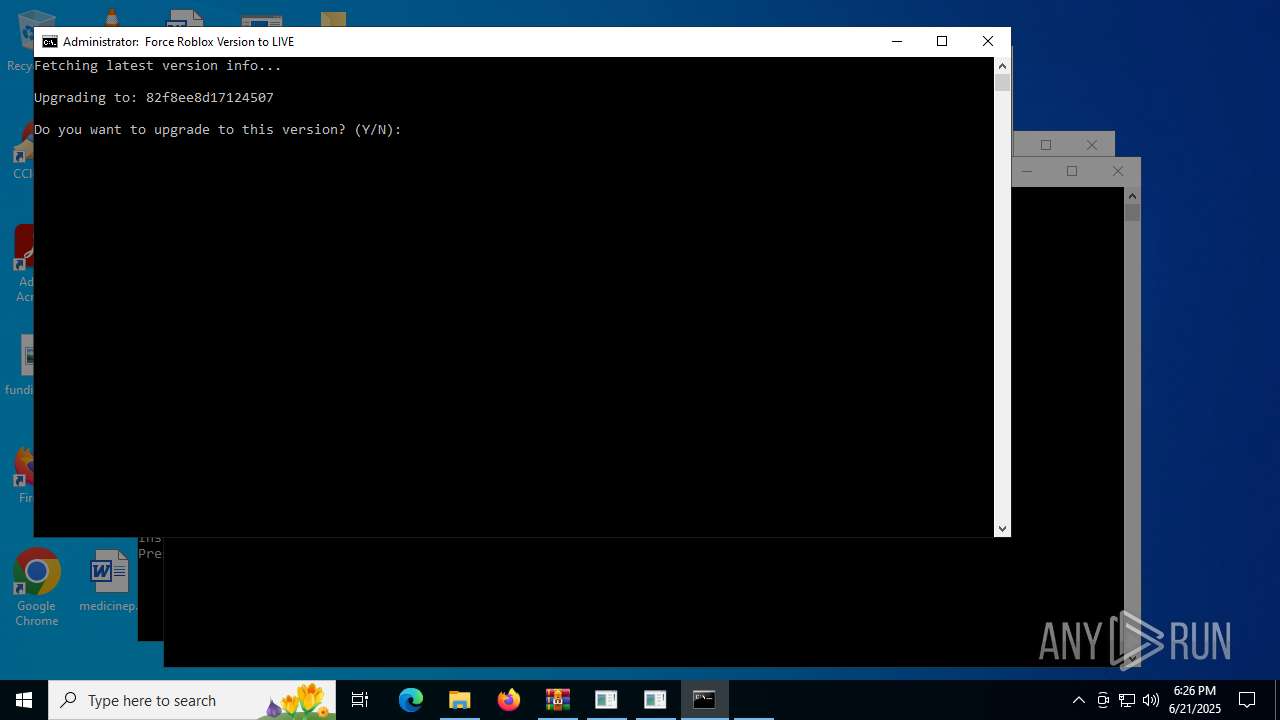
| 1336 | C:\WINDOWS\system32\cmd.exe /c powershell -NoProfile -Command "$json = (Invoke-WebRequest -Uri 'https://clientsettings.roblox.com/v2/client-version/WindowsPlayer/channel/LIVE').Content | ConvertFrom-Json; $json.clientVersionUpload" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1880 | net session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2276 | powershell -Command "Start-Process 'C:\Users\admin\Desktop\roblox LIVE forcer.bat' -Verb RunAs" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | LX63Updater.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2804 | "C:\Users\admin\Desktop\Injector.exe" | C:\Users\admin\Desktop\Injector.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3000 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Injector.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3476 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
38 040
Read events
37 999
Write events
41
Delete events
0
Modification events
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\LX63WRD.zip | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
4
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6368 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_LX63.exe_99d8708455698bf4dad92ab7087119f7d733_1f8cf156_023d8e19-ab05-4fce-9c11-078856e154f5\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6368 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\LX63.exe.984.dmp | — | |
MD5:— | SHA256:— | |||
| 5724 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_LX63.exe_c0e3bfd1dd526562e759e5c31d74fcb6ec7ec1fa_1f8cf156_fbcd0422-f3c8-48df-ad8a-7c90a85d1363\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5724 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\LX63.exe(1).984.dmp | — | |
MD5:— | SHA256:— | |||
| 4172 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_flutmsvy.tal.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2276 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4fraqw53.hih.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5724 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER14DB.tmp.dmp | binary | |
MD5:440AEA2148DDD555B54DC07EC23B32C1 | SHA256:F3B6857CF2198AC00F3984D073B4819FF15A58181C6B44735879F861918CC4C5 | |||
| 6368 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERFADA.tmp.dmp | binary | |
MD5:7B903CB5D16821544FEEC7BF863ADC64 | SHA256:E728CB20F1F3A43F57F5F26B7D741FF8D1298C10DEE285CFA5BBE819BC6B9D65 | |||
| 6368 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERFD7B.tmp.WERInternalMetadata.xml | xml | |
MD5:7CF6169AB7056642EC86BBBF304CD747 | SHA256:6169BAA007DF08643D9E4AD33B0981ACFAD8E695E612661FCFB482C33D754FA1 | |||
| 5724 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER16D1.tmp.xml | xml | |
MD5:FD2810939A2B777074AC58A924CC2997 | SHA256:2BF0885DA42F898A3F16D3E9155A63383AE696B09CD5C3F70A06E7F1C9938333 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
29
DNS requests
14
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4868 | RUXIMICS.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4868 | RUXIMICS.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 140.82.121.3:443 | https://raw.githubusercontent.com/Gogogamer61/LX63-Updater/refs/heads/master/test | unknown | text | 76 b | whitelisted |
— | — | GET | 302 | 140.82.121.3:443 | https://github.com/x64lx/QQQQQQQQQQQQQQ/raw/refs/heads/main/LX63AUTOUP2.zip | unknown | — | — | unknown |
— | — | GET | 200 | 140.82.121.3:443 | https://raw.githubusercontent.com/x64lx/QQQQQQQQQQQQQQ/refs/heads/main/LX63AUTOUP2.zip | unknown | compressed | 12.5 Mb | whitelisted |
— | — | GET | 200 | 140.82.121.3:443 | https://raw.githubusercontent.com/Gogogamer61/LX63-Updater/refs/heads/master/awandaro?cb=638861272014802520 | unknown | text | 6 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4868 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
4868 | RUXIMICS.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1268 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
clientsettings.roblox.com |
| whitelisted |
github.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |