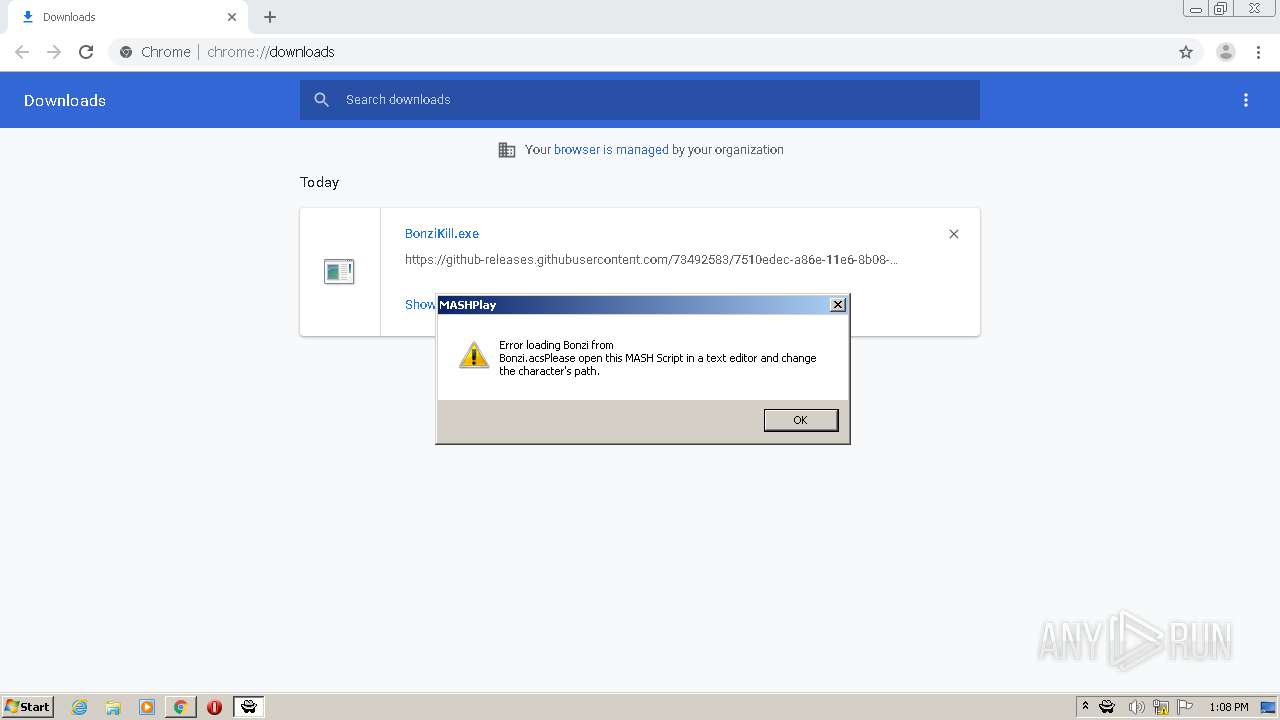
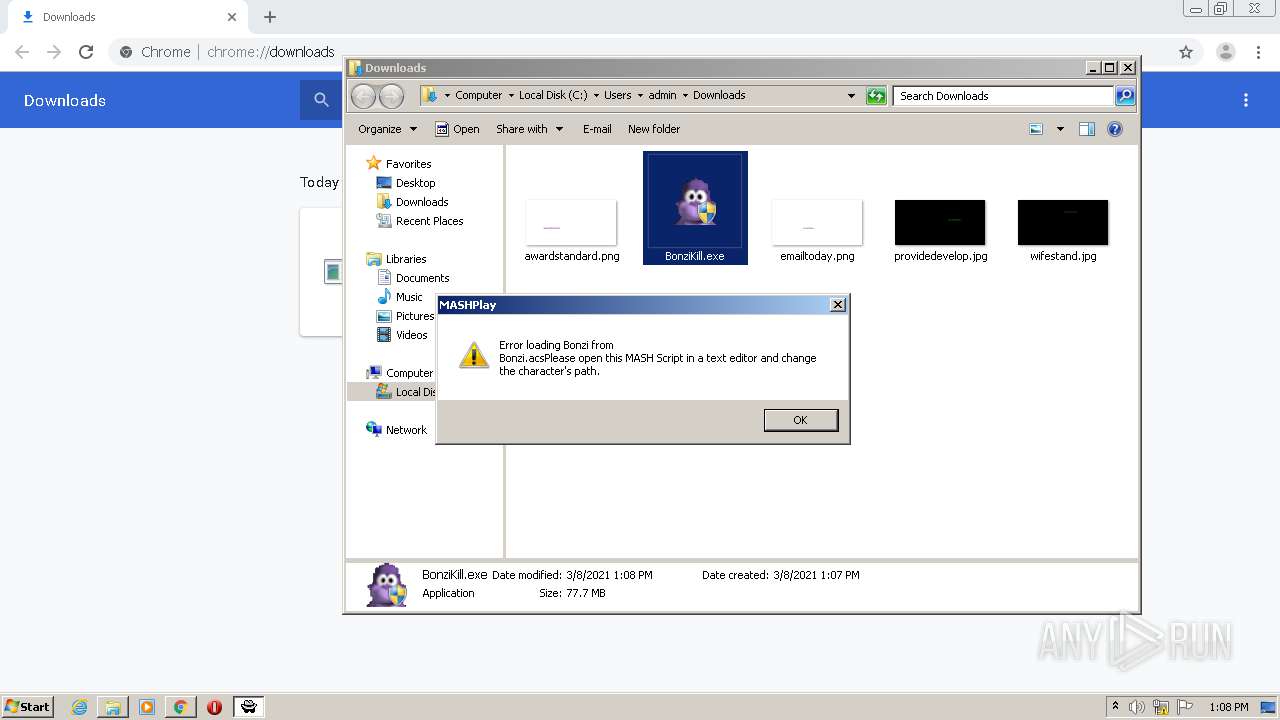
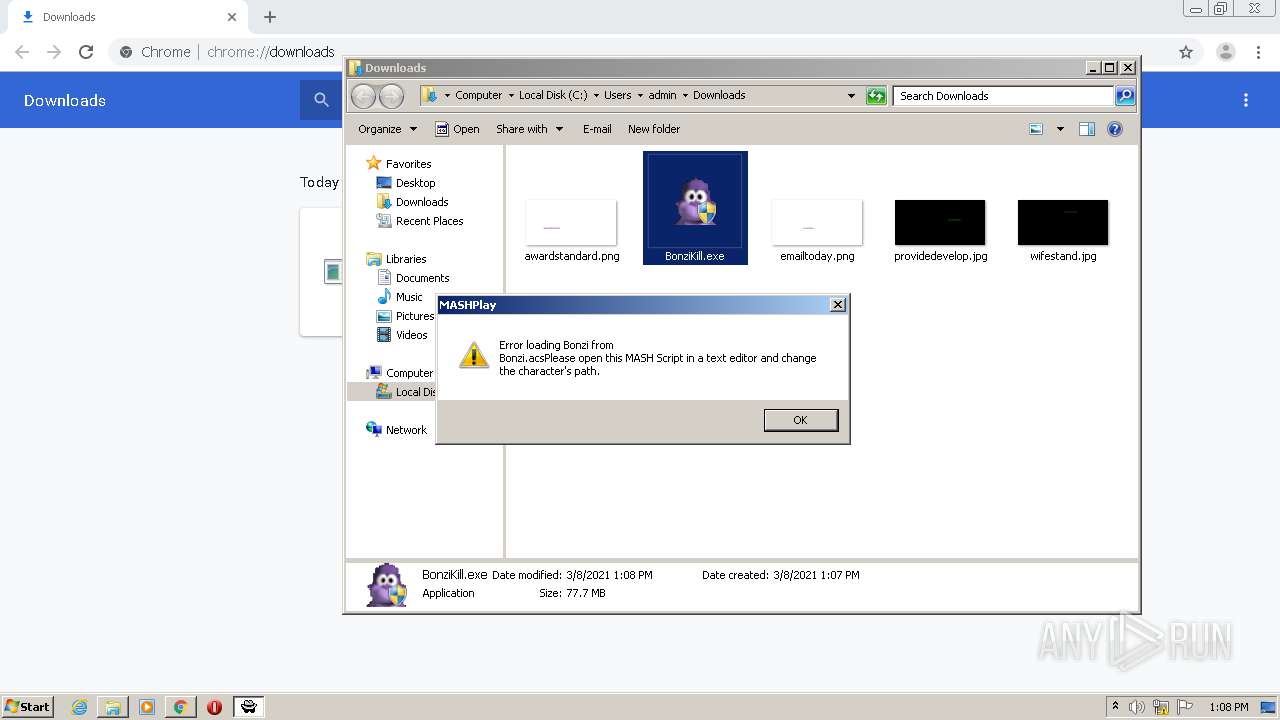
| URL: | https://github.com/x8BitRain/BonziRogue/releases/download/1/BonziKill.exe |
| Full analysis: | https://app.any.run/tasks/36cf006e-88f1-4f4a-ba11-67122e185cb5 |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2021, 13:06:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E60DBA73E9D0F50C90BC8B4DAEB98DA6 |
| SHA1: | 04661DEAD2D96C8D1E771F1C3C23FB440CBD1028 |
| SHA256: | 796F3E6602F62ECCCE12EF671A5C512D1150B4501048DF2FF8011EEA6783ED86 |
| SSDEEP: | 3:N8tEdtdnMR0RK2KCgtkCUHv0J:2ujZgt6HcJ |
MALICIOUS
Application was dropped or rewritten from another process
- BonziKill.exe (PID: 1768)
- BonziKill.exe (PID: 3092)
- BonziBuddy_original.exe (PID: 3668)
- BonziKill.exe (PID: 3604)
- BonziKill.exe (PID: 3944)
- BonziBuddy_original.exe (PID: 2400)
- BonziKill.exe (PID: 2436)
- BonziKill.exe (PID: 2192)
- BonziBuddy_original.exe (PID: 1460)
Drops executable file immediately after starts
- BonziKill.exe (PID: 3092)
- BonziKill.exe (PID: 3944)
- BonziKill.exe (PID: 2192)
Loads the Task Scheduler COM API
- CCleaner.exe (PID: 3488)
Steals credentials from Web Browsers
- CCleaner.exe (PID: 1488)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 1488)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2720)
- BonziKill.exe (PID: 3092)
- BonziKill.exe (PID: 3944)
- BonziKill.exe (PID: 2192)
Drops a file that was compiled in debug mode
- chrome.exe (PID: 2720)
- BonziKill.exe (PID: 3092)
- BonziKill.exe (PID: 3944)
- BonziKill.exe (PID: 2192)
Drops a file with too old compile date
- BonziKill.exe (PID: 3092)
- BonziKill.exe (PID: 3944)
- BonziKill.exe (PID: 2192)
Creates files in the Windows directory
- BonziKill.exe (PID: 3092)
- BonziKill.exe (PID: 3944)
- BonziKill.exe (PID: 2192)
Removes files from Windows directory
- BonziKill.exe (PID: 3944)
- BonziKill.exe (PID: 2192)
Creates files in the user directory
- filezilla.exe (PID: 4072)
- CCleaner.exe (PID: 1488)
Executed via Task Scheduler
- CCleaner.exe (PID: 1488)
Reads internet explorer settings
- CCleaner.exe (PID: 1488)
Low-level read access rights to disk partition
- CCleaner.exe (PID: 1488)
INFO
Application launched itself
- chrome.exe (PID: 2720)
Reads the hosts file
- chrome.exe (PID: 2720)
- chrome.exe (PID: 992)
Reads settings of System Certificates
- chrome.exe (PID: 992)
- CCleaner.exe (PID: 1488)
Manual execution by user
- BonziKill.exe (PID: 3604)
- BonziKill.exe (PID: 3944)
- BonziKill.exe (PID: 2436)
- BonziKill.exe (PID: 2192)
- CCleaner.exe (PID: 3488)
- filezilla.exe (PID: 4072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
75
Monitored processes
24
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,15106852856973557697,10830305289614288988,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=15041611347185805946 --mojo-platform-channel-handle=1068 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,15106852856973557697,10830305289614288988,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=14281860970927284615 --mojo-platform-channel-handle=1536 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1460 | "C:\bonzi\BonziBuddy_original.exe" | C:\bonzi\BonziBuddy_original.exe | — | BonziKill.exe | |||||||||||
User: admin Company: BellCraft Technologies Integrity Level: HIGH Exit code: 3221225547 Version: 7.05 Modules
| |||||||||||||||
| 1488 | "C:\Program Files\CCleaner\CCleaner.exe" /uac | C:\Program Files\CCleaner\CCleaner.exe | taskeng.exe | ||||||||||||
User: admin Company: Piriform Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 5, 35, 0, 6210 Modules
| |||||||||||||||
| 1768 | "C:\Users\admin\Downloads\BonziKill.exe" | C:\Users\admin\Downloads\BonziKill.exe | — | chrome.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,15106852856973557697,10830305289614288988,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=9086468322943507671 --mojo-platform-channel-handle=1052 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2192 | "C:\Users\admin\Downloads\BonziKill.exe" | C:\Users\admin\Downloads\BonziKill.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1000 Modules
| |||||||||||||||
| 2400 | "C:\bonzi\BonziBuddy_original.exe" | C:\bonzi\BonziBuddy_original.exe | — | BonziKill.exe | |||||||||||
User: admin Company: BellCraft Technologies Integrity Level: HIGH Exit code: 3221225547 Version: 7.05 Modules
| |||||||||||||||
| 2436 | "C:\Users\admin\Downloads\BonziKill.exe" | C:\Users\admin\Downloads\BonziKill.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,15106852856973557697,10830305289614288988,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5527894116507598712 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2172 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 215
Read events
1 937
Write events
275
Delete events
3
Modification events
| (PID) Process: | (2720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3068) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2720-13259682429077750 |
Value: 259 | |||
| (PID) Process: | (2720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2720) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2720) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
188
Suspicious files
67
Text files
568
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-6046217D-AA0.pma | — | |
MD5:— | SHA256:— | |||
| 2720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\e2e61903-8e3b-495a-8bf2-5ccab3710160.tmp | — | |
MD5:— | SHA256:— | |||
| 2720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF1d4f7a.TMP | text | |
MD5:— | SHA256:— | |||
| 2720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 4064 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:9543068B6751E1F3E11F91D72EE78D95 | SHA256:D060AD21AE6E04CB58668CAA52ADFCA573E018102CC07554D2ED3EAE11AB7785 | |||
| 2720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1d4f8a.TMP | text | |
MD5:— | SHA256:— | |||
| 2720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF1d4fb9.TMP | text | |
MD5:— | SHA256:— | |||
| 2720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2720 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF1d519d.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
17
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1488 | CCleaner.exe | GET | 301 | 151.101.0.64:80 | http://www.piriform.com/auto?a=0&p=cc&v=5.35.6210&l=1033&lk=&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-VAKU&o=6.1W3&au=1&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gu=00000000-0000-4000-8000-d6f7f2be5127 | US | — | — | whitelisted |
1488 | CCleaner.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/rootr1/MEwwSjBIMEYwRDAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCCwQAAAAAAURO8EJH | US | der | 1.48 Kb | whitelisted |
1488 | CCleaner.exe | GET | 200 | 151.101.2.109:80 | http://license.piriform.com/verify/?p=ccpro&c=cc&cv=5.35.6210&l=1033&lk=CJ9T-J7CU-SPNV-GWMB-WBEC&mk=IJR6-W5SV-5KYR-QBZD-6BY4-RN5Z-WAV9-RVK2-VAKU&mx=97B7721C4994E2556FF6A439510F665DB45337A341A47E15F4997584423BF714&gu=00000000-0000-4000-8000-d6f7f2be5127 | US | text | 14 b | whitelisted |
1488 | CCleaner.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/ME8wTTBLMEkwRzAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDkbwjNvPLFRm7zMB3V80 | US | der | 1.49 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
992 | chrome.exe | 172.217.18.109:443 | accounts.google.com | Google Inc. | US | suspicious |
992 | chrome.exe | 185.199.108.154:443 | github-releases.githubusercontent.com | GitHub, Inc. | NL | suspicious |
992 | chrome.exe | 142.250.185.99:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
992 | chrome.exe | 172.217.16.142:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
1488 | CCleaner.exe | 151.101.2.202:443 | www.ccleaner.com | Fastly | US | suspicious |
1488 | CCleaner.exe | 104.18.20.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
1488 | CCleaner.exe | 151.101.2.109:80 | license.piriform.com | Fastly | US | suspicious |
1488 | CCleaner.exe | 151.101.2.109:443 | license.piriform.com | Fastly | US | suspicious |
1488 | CCleaner.exe | 151.101.0.64:80 | www.piriform.com | Fastly | US | whitelisted |
1488 | CCleaner.exe | 104.18.21.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| malicious |
accounts.google.com |
| shared |
github-releases.githubusercontent.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
clients4.google.com |
| whitelisted |
clients1.google.com |
| whitelisted |
www.piriform.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |