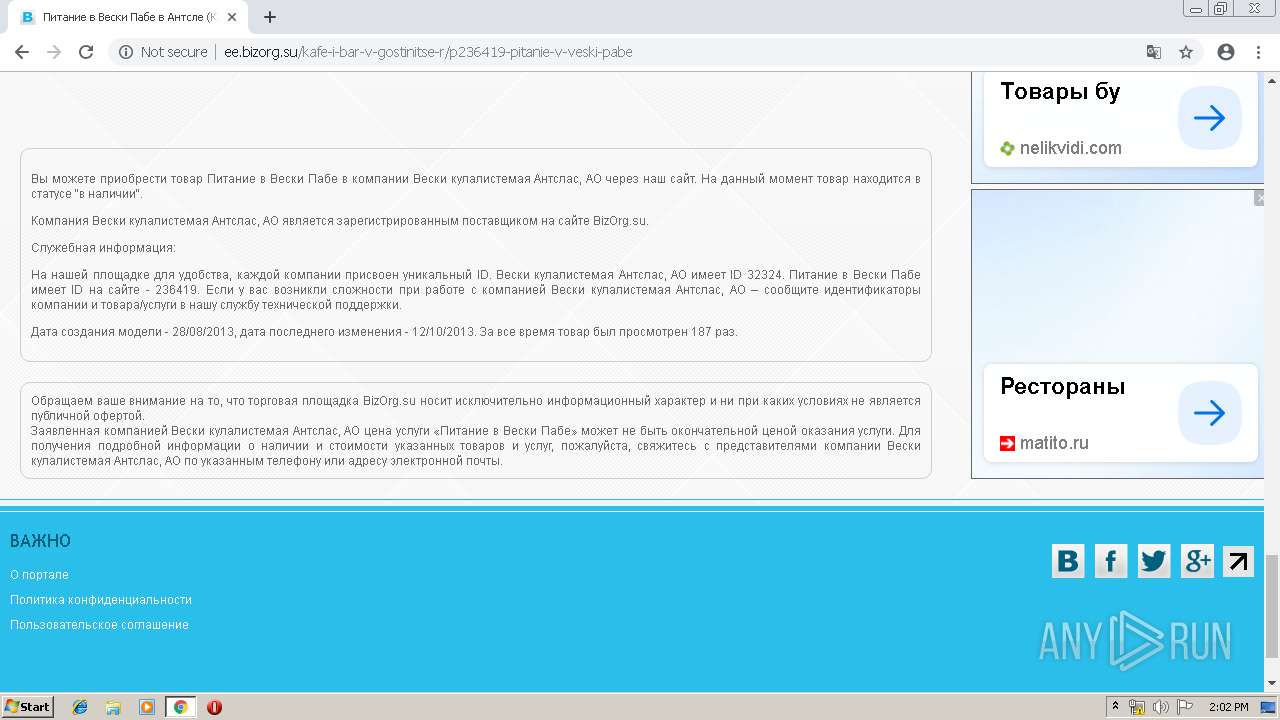
| URL: | http://ee.bizorg.su |
| Full analysis: | https://app.any.run/tasks/cf4bf3ec-e181-429a-9096-c3795871628c |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2019, 12:59:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B04B6FC8CE16EC90EC59F06B21689F3D |
| SHA1: | 5719927753C8472E5C59E72CA1D8AFA22CAE5F5A |
| SHA256: | 795EC6D3603379BF7C3B97D351ACDD9780FEE0079B686F9BED847FFEB3572F00 |
| SSDEEP: | 3:N1KbZXWQ:CdWQ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2948)
INFO
Application launched itself
- chrome.exe (PID: 2948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
18
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 804 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,14153359556614846771,5797823042694672624,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1007803929571019809 --mojo-platform-channel-handle=3820 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1628 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,14153359556614846771,5797823042694672624,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12858383648011254599 --mojo-platform-channel-handle=4344 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2220 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,14153359556614846771,5797823042694672624,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6303045223941707294 --mojo-platform-channel-handle=2216 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,14153359556614846771,5797823042694672624,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=16334111289924218514 --mojo-platform-channel-handle=3536 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,14153359556614846771,5797823042694672624,131072 --enable-features=PasswordImport --service-pipe-token=17650728372182753376 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17650728372182753376 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1940 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,14153359556614846771,5797823042694672624,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=18011796439574686963 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=18011796439574686963 --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1820 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2680 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2952 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2732 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,14153359556614846771,5797823042694672624,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5980257012125211517 --mojo-platform-channel-handle=3376 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2800 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=960,14153359556614846771,5797823042694672624,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=5283681220832023288 --mojo-platform-channel-handle=4376 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,14153359556614846771,5797823042694672624,131072 --enable-features=PasswordImport --service-pipe-token=6170257844413139568 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6170257844413139568 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1976 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
559
Read events
467
Write events
87
Delete events
5
Modification events
| (PID) Process: | (2948) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2948) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2948) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2948) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2948) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2948) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2680) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2948-13200498011593125 |
Value: 259 | |||
| (PID) Process: | (2948) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2948) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
| (PID) Process: | (2948) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
0
Suspicious files
76
Text files
158
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2948 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2948 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2948 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 2948 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 2948 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 2948 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\2ecec5eb-d372-4c6f-a821-a5077eb4c180.tmp | — | |
MD5:— | SHA256:— | |||
| 2948 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2948 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2948 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2948 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
279
TCP/UDP connections
67
DNS requests
45
Threats
272
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2948 | chrome.exe | GET | 200 | 136.243.18.232:80 | http://ee.bizorg.su/content/img/region.png | DE | image | 934 b | suspicious |
2948 | chrome.exe | GET | 200 | 136.243.18.232:80 | http://ee.bizorg.su/content/img/logo.png | DE | image | 2.63 Kb | suspicious |
2948 | chrome.exe | GET | 200 | 136.243.18.232:80 | http://ee.bizorg.su/Content/img/rubric_icons/sborka_pk_i_ustanovka_programmnogo_obespecheniya.png | DE | image | 1.18 Kb | suspicious |
2948 | chrome.exe | GET | 200 | 136.243.18.232:80 | http://ee.bizorg.su/ | DE | html | 17.0 Kb | suspicious |
2948 | chrome.exe | GET | 200 | 136.243.18.232:80 | http://ee.bizorg.su/content/img/man.png | DE | image | 64.0 Kb | suspicious |
2948 | chrome.exe | GET | 200 | 136.243.18.232:80 | http://ee.bizorg.su/Content/img/rubric_icons/promyshlennoe_oborudovanie_stanki_mekhanizmy_.png | DE | image | 698 b | suspicious |
2948 | chrome.exe | GET | 200 | 136.243.18.232:80 | http://ee.bizorg.su/Content/img/rubric_icons/sport_i_otdykh.png | DE | image | 1.54 Kb | suspicious |
2948 | chrome.exe | GET | 200 | 136.243.18.232:80 | http://ee.bizorg.su/Content/img/rubric_icons/Okhrana_zaschita_obespechenie_bezopasnosti.png | DE | image | 1.65 Kb | suspicious |
2948 | chrome.exe | GET | 200 | 136.243.18.232:80 | http://ee.bizorg.su/Content/img/rubric_icons/stroitelnaya_tekhnika_i_oborudovanie_uslugi2.png | DE | image | 1.13 Kb | suspicious |
2948 | chrome.exe | GET | 200 | 136.243.18.232:80 | http://ee.bizorg.su/Content/img/rubric_icons/stroitelnaya_tekhnika_i_oborudovanie_uslugi.png | DE | image | 1.96 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2948 | chrome.exe | 172.217.23.141:443 | accounts.google.com | Google Inc. | US | whitelisted |
2948 | chrome.exe | 136.243.18.232:80 | ee.bizorg.su | Hetzner Online GmbH | DE | suspicious |
— | — | 216.58.207.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2948 | chrome.exe | 216.58.210.4:443 | www.google.com | Google Inc. | US | whitelisted |
— | — | 172.217.22.106:80 | ajax.googleapis.com | Google Inc. | US | whitelisted |
2948 | chrome.exe | 172.217.22.106:80 | ajax.googleapis.com | Google Inc. | US | whitelisted |
2948 | chrome.exe | 5.9.147.156:80 | img.bizorg.su | Hetzner Online GmbH | DE | suspicious |
2948 | chrome.exe | 213.180.204.90:80 | an.yandex.ru | YANDEX LLC | RU | whitelisted |
— | — | 88.212.196.103:80 | counter.yadro.ru | United Network LLC | RU | unknown |
— | — | 172.217.16.206:443 | cse.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
ee.bizorg.su |
| suspicious |
accounts.google.com |
| shared |
www.google.com |
| malicious |
img.bizorg.su |
| suspicious |
ajax.googleapis.com |
| whitelisted |
by.bizorg.su |
| suspicious |
bizorg.su |
| whitelisted |
kg.bizorg.su |
| suspicious |
lt.bizorg.su |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
2948 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
2948 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
2948 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
2948 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
2948 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
2948 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
2948 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
2948 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
2948 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |