| File name: | RobloxPlayerInstaller.exe |
| Full analysis: | https://app.any.run/tasks/c6faf52e-b305-4ef8-ac5b-f666b2838c63 |
| Verdict: | Malicious activity |
| Analysis date: | April 13, 2024, 11:49:31 |
| OS: | Ubuntu 22.04.2 |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9FB66FFA1E1F4DEDFD16EB3A8170BAFD |
| SHA1: | 69B5D57DDDA6B97ADDE820B9CEADDAE9C33D53BD |
| SHA256: | 7953B28B736795AAA54E6CD5CB591E794E2F770C1045CA2E33AF5FF19F480EAA |
| SSDEEP: | 98304:wps0+wLp7069ZBLHB/Evdm/85D3vtjDnx9LdkZo2+pTJWkoLNQXXOz9x9PNvxaas:uLC0C5L |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks DMI information (probably VM detection)
- systemd-hostnamed (PID: 9288)
Executes commands using command-line interpreter
- gnome-terminal-server (PID: 9302)
- su (PID: 9333)
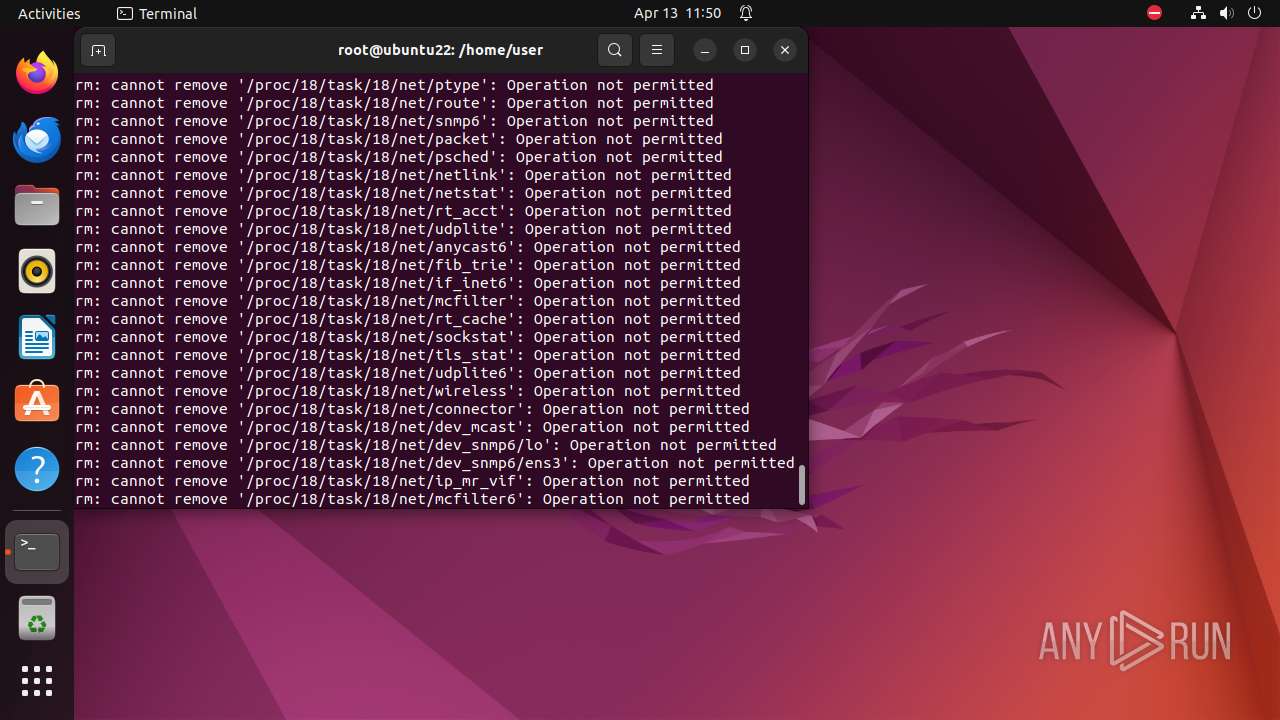
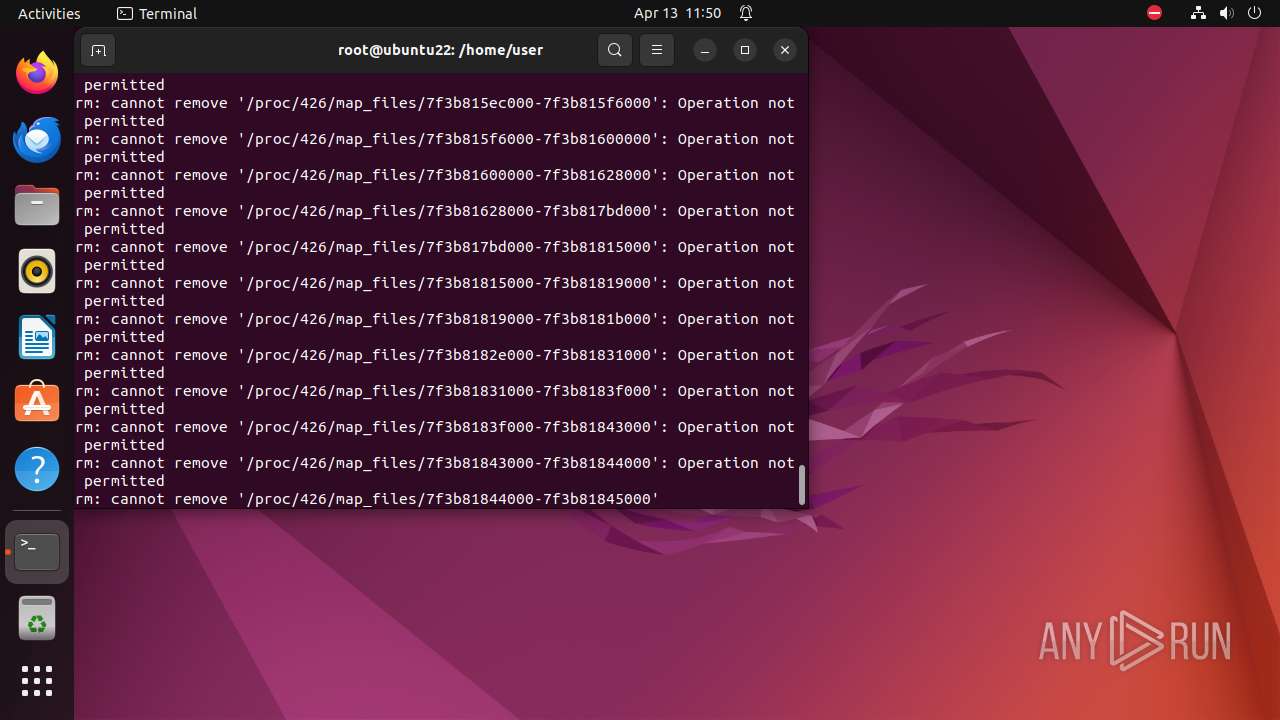
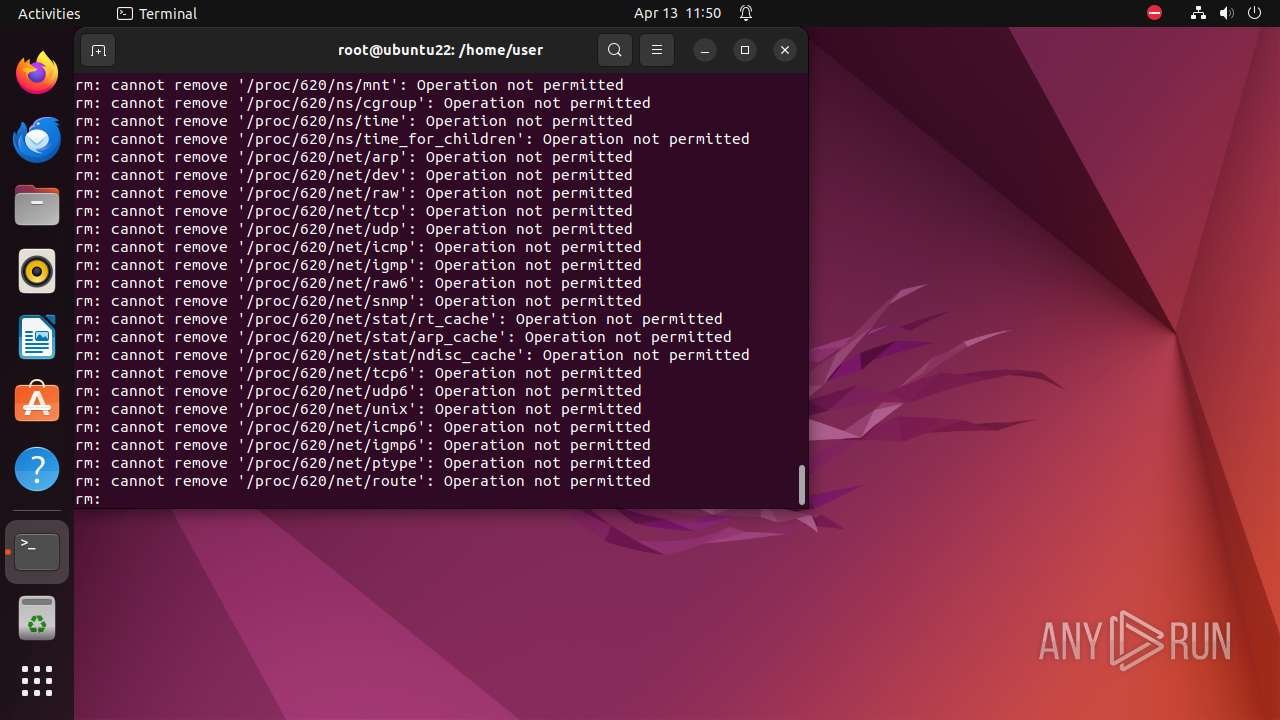
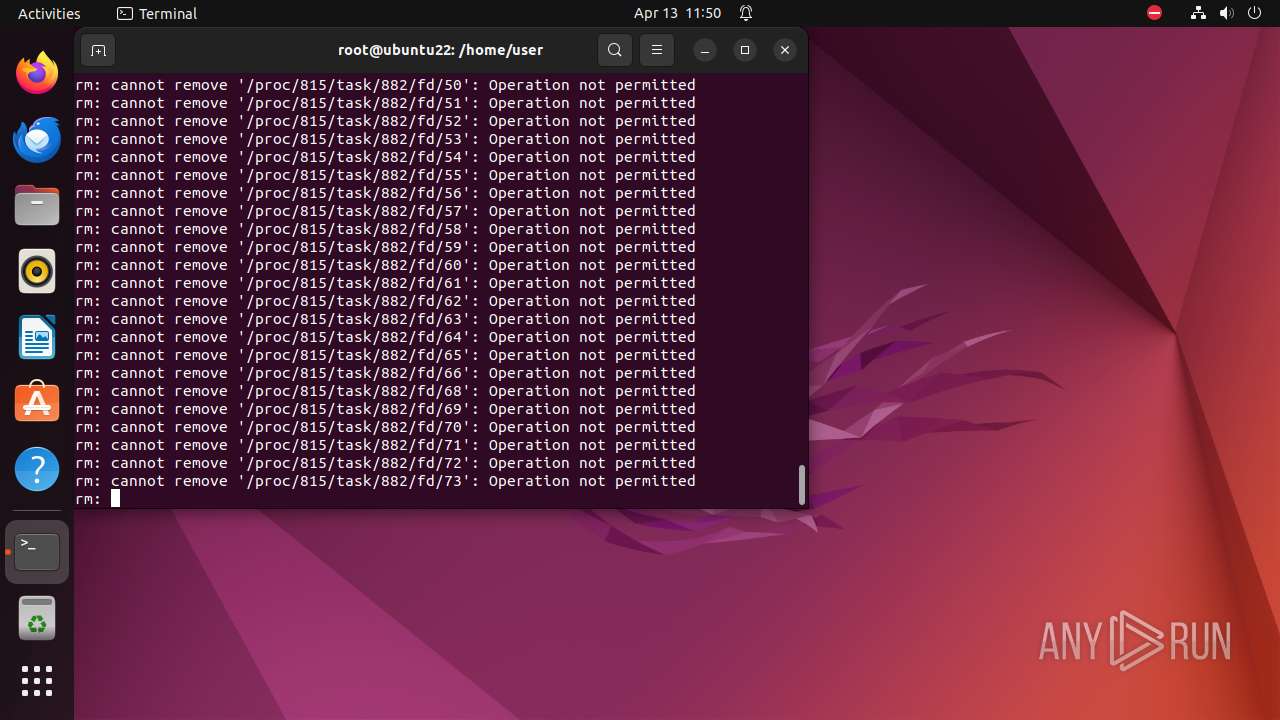
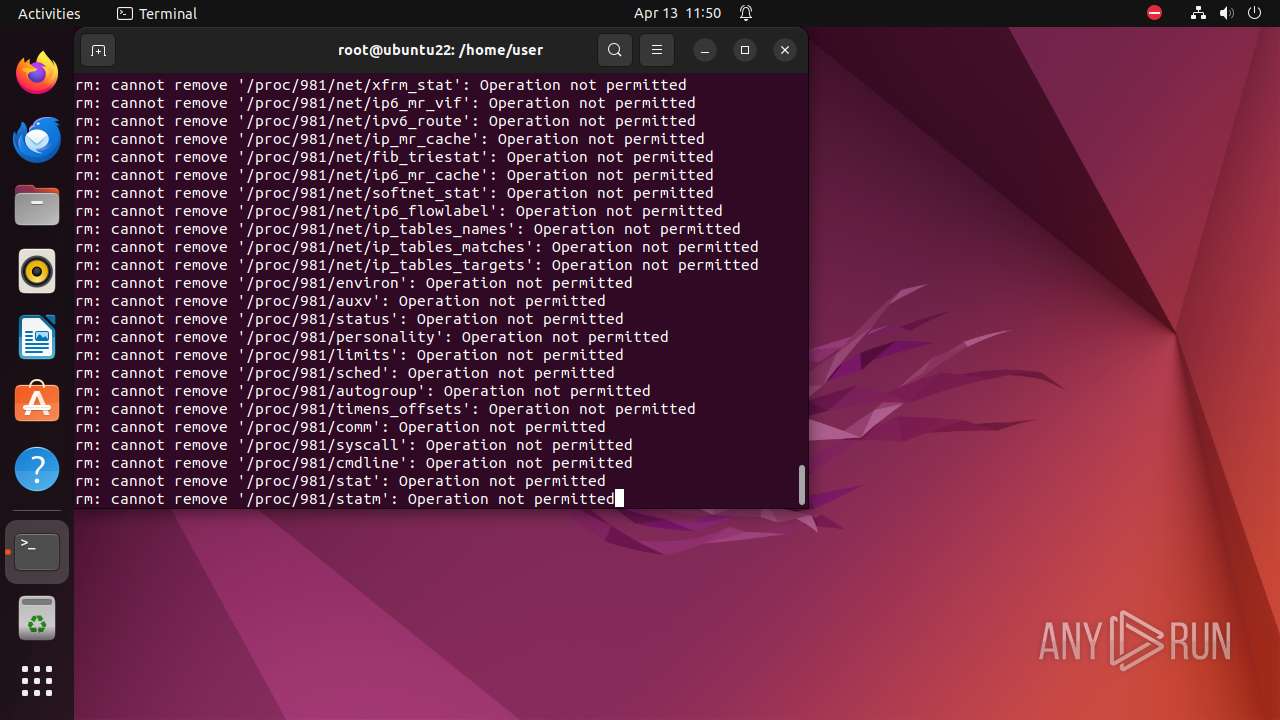
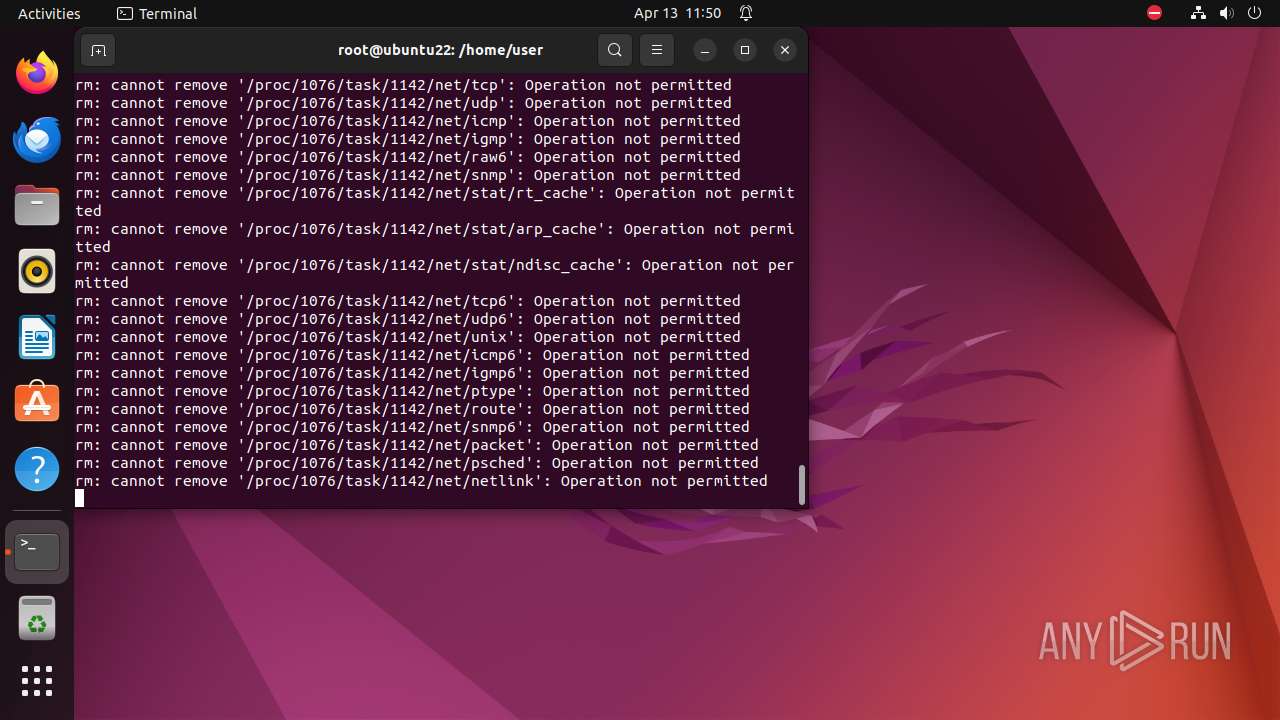
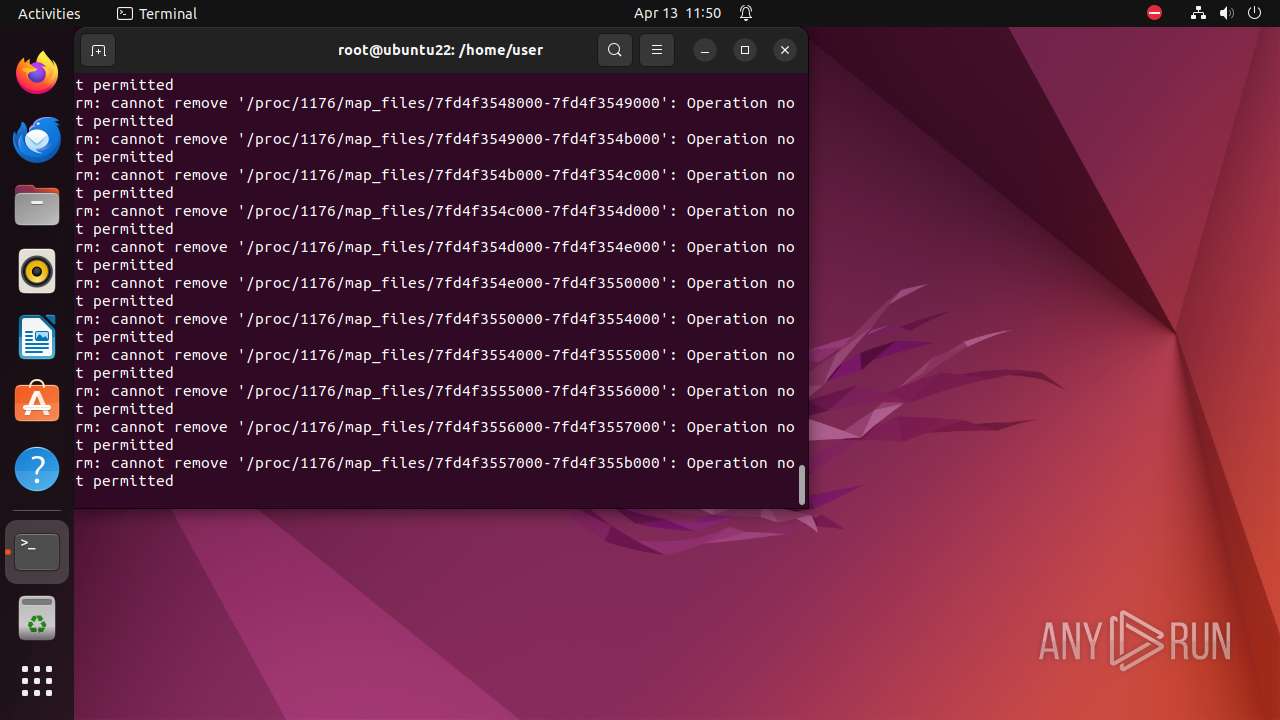
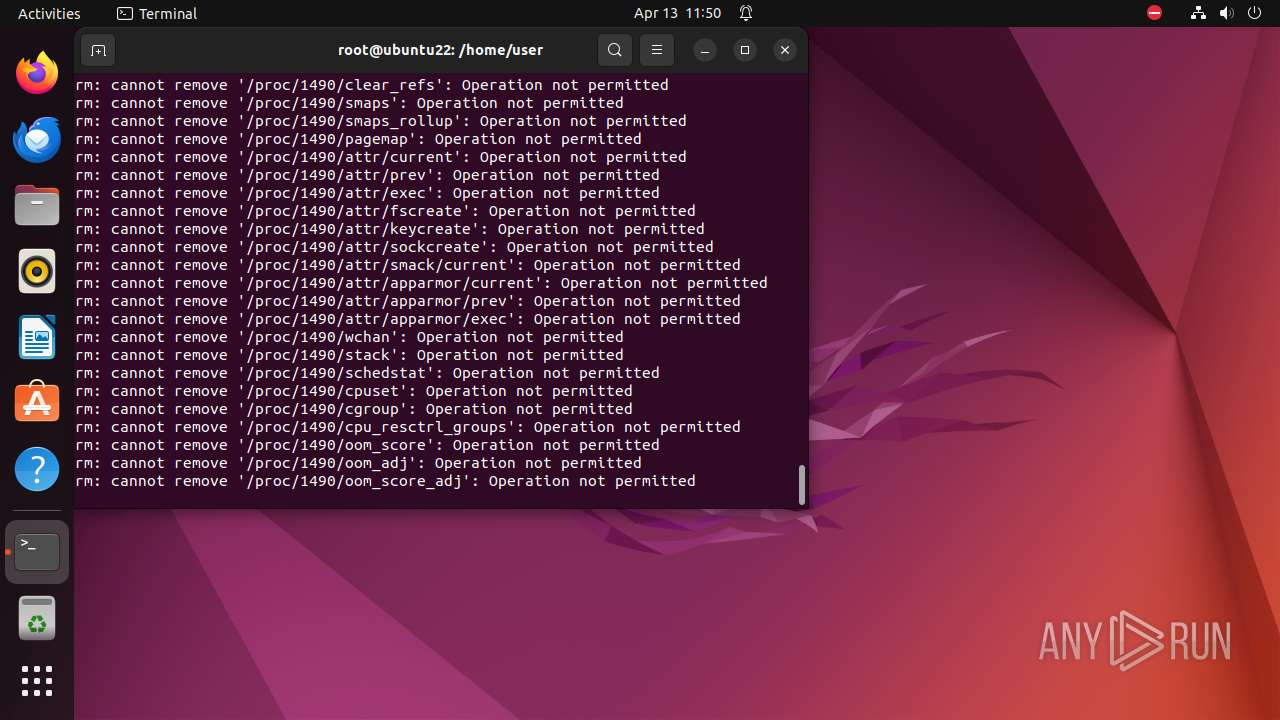
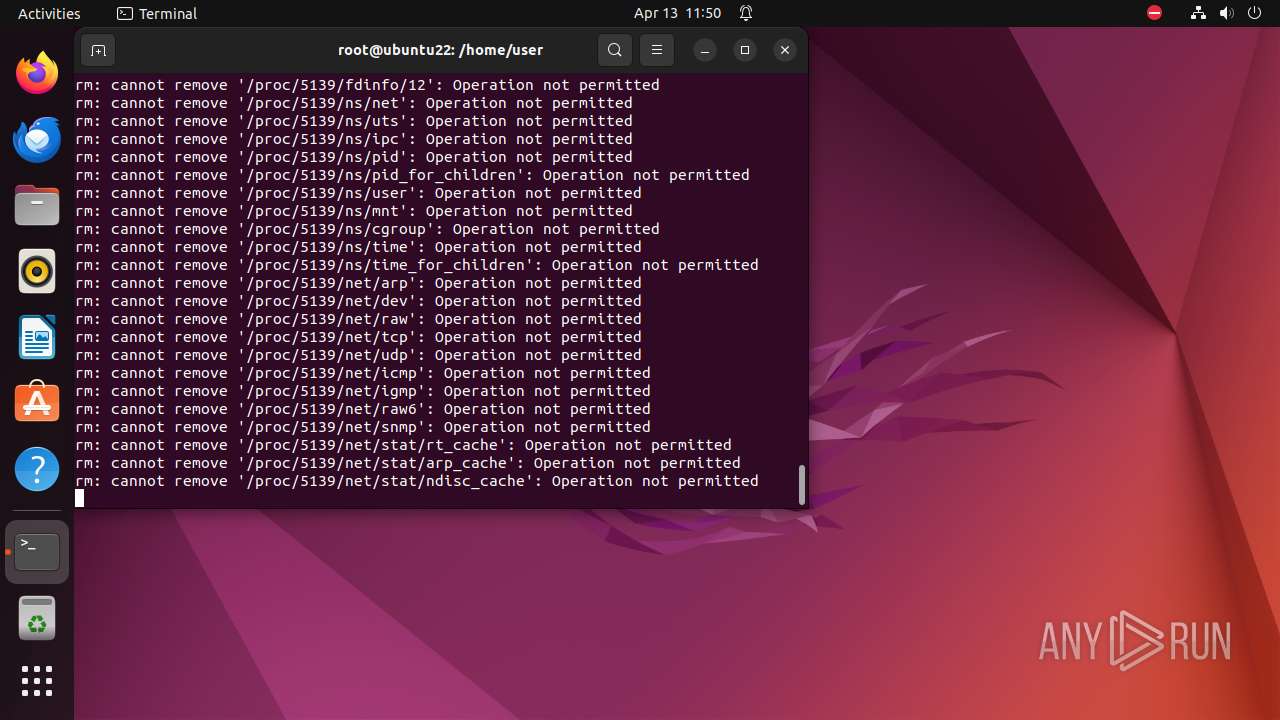
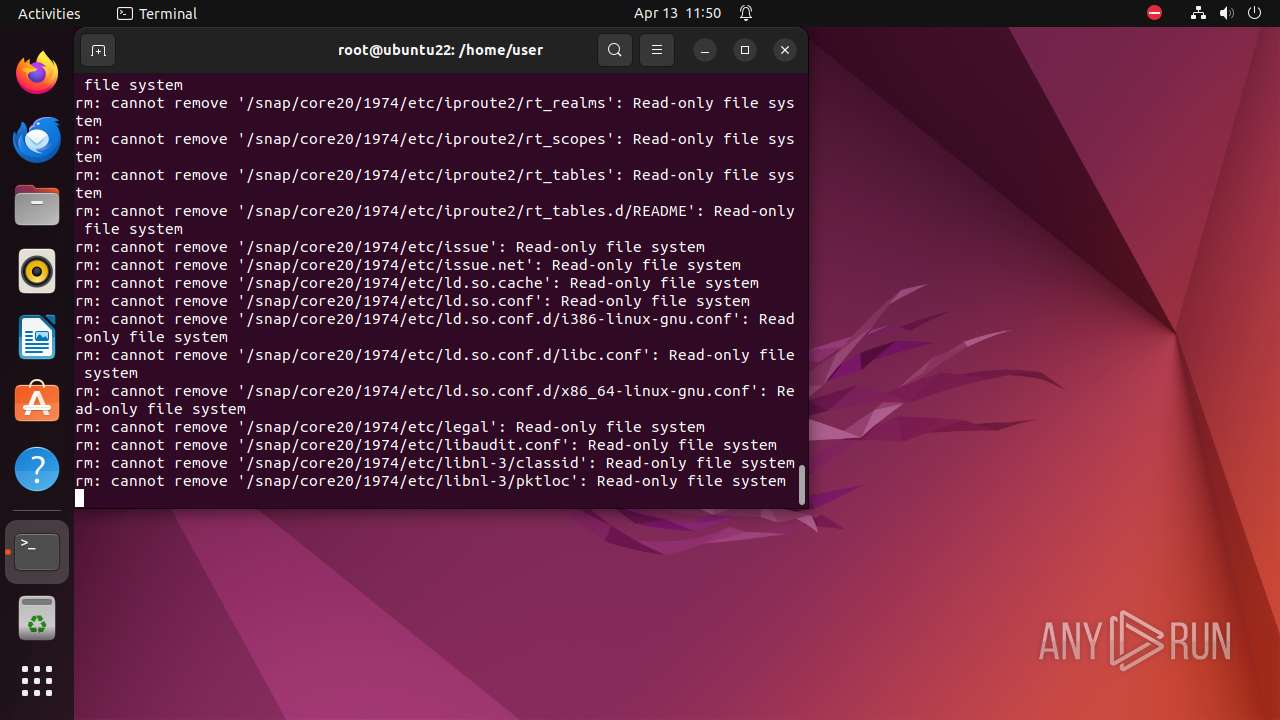
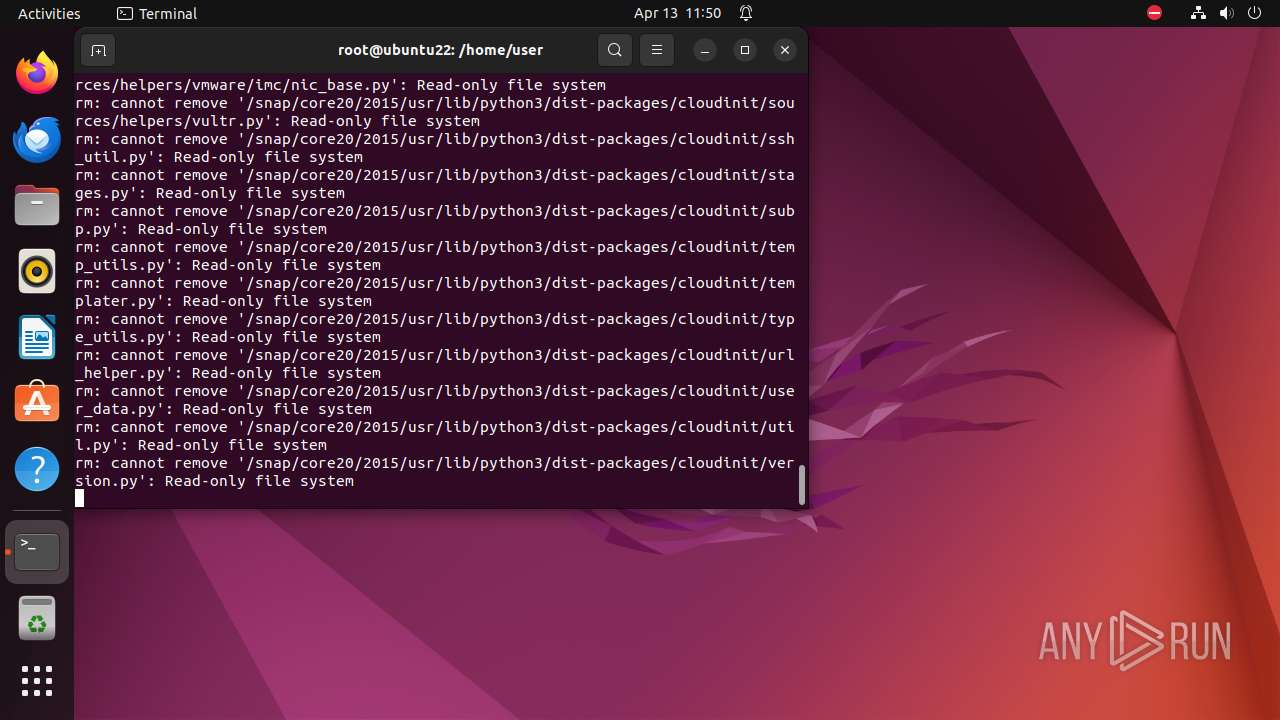
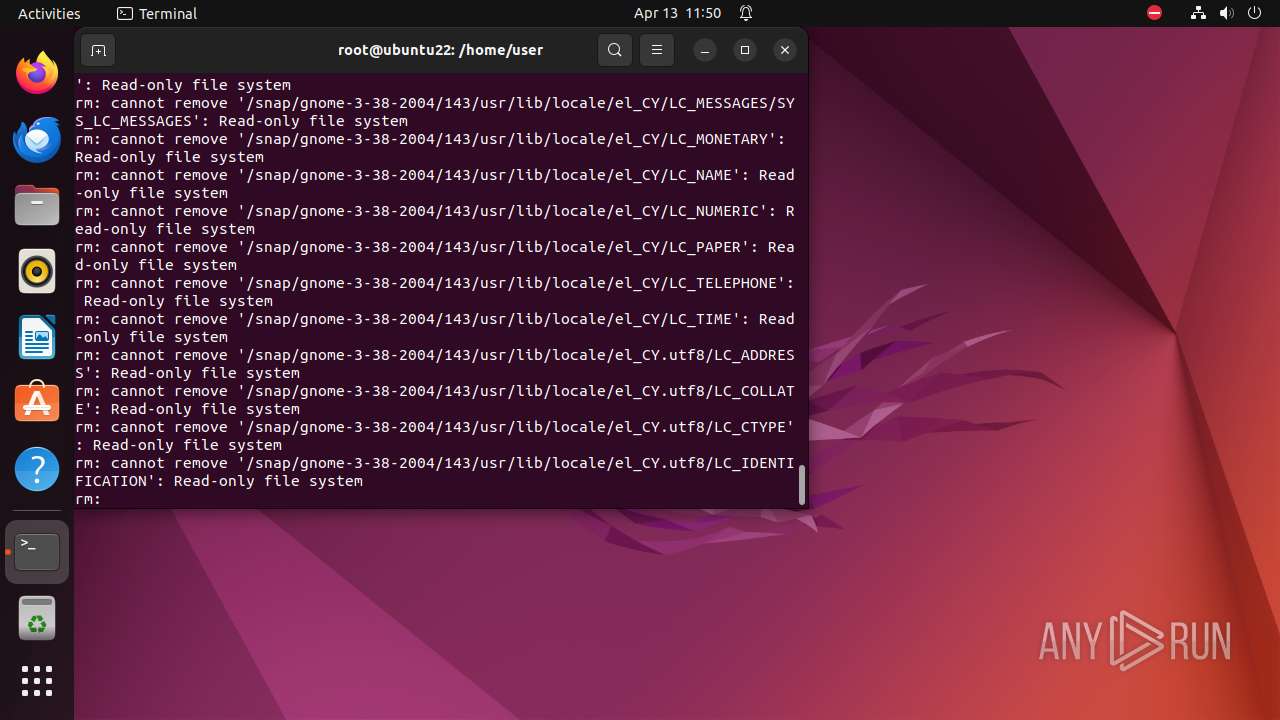
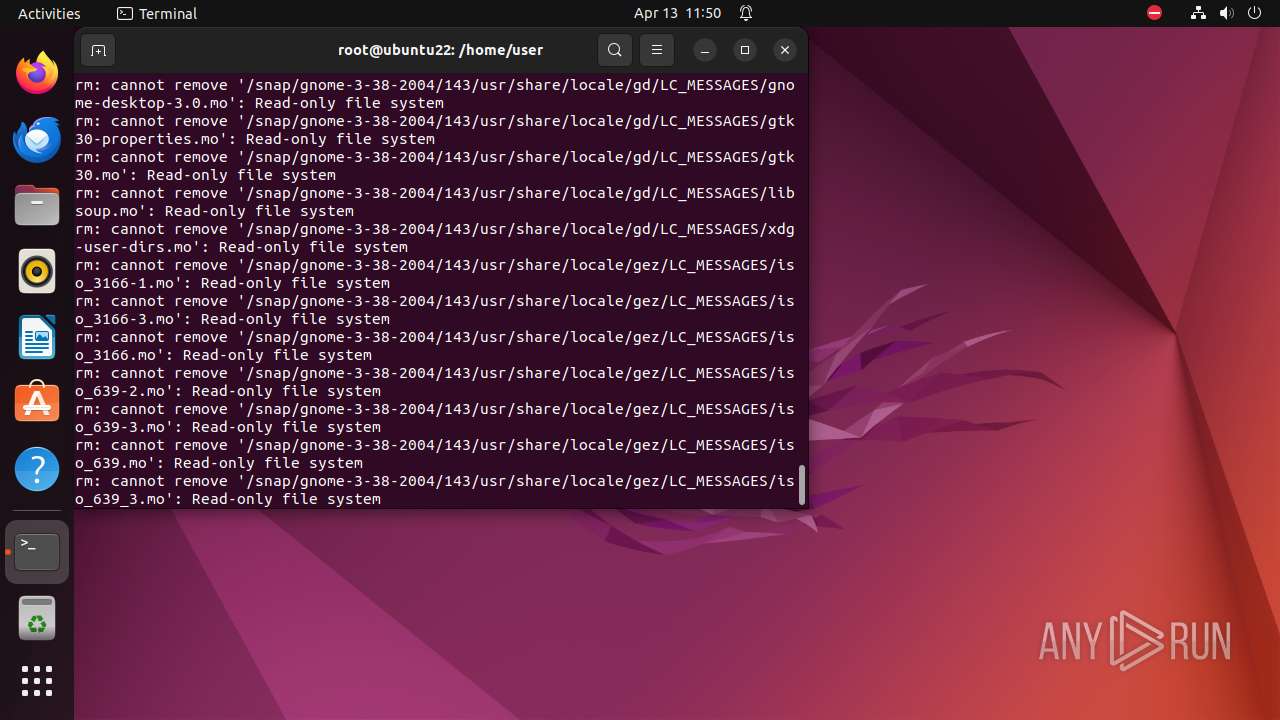
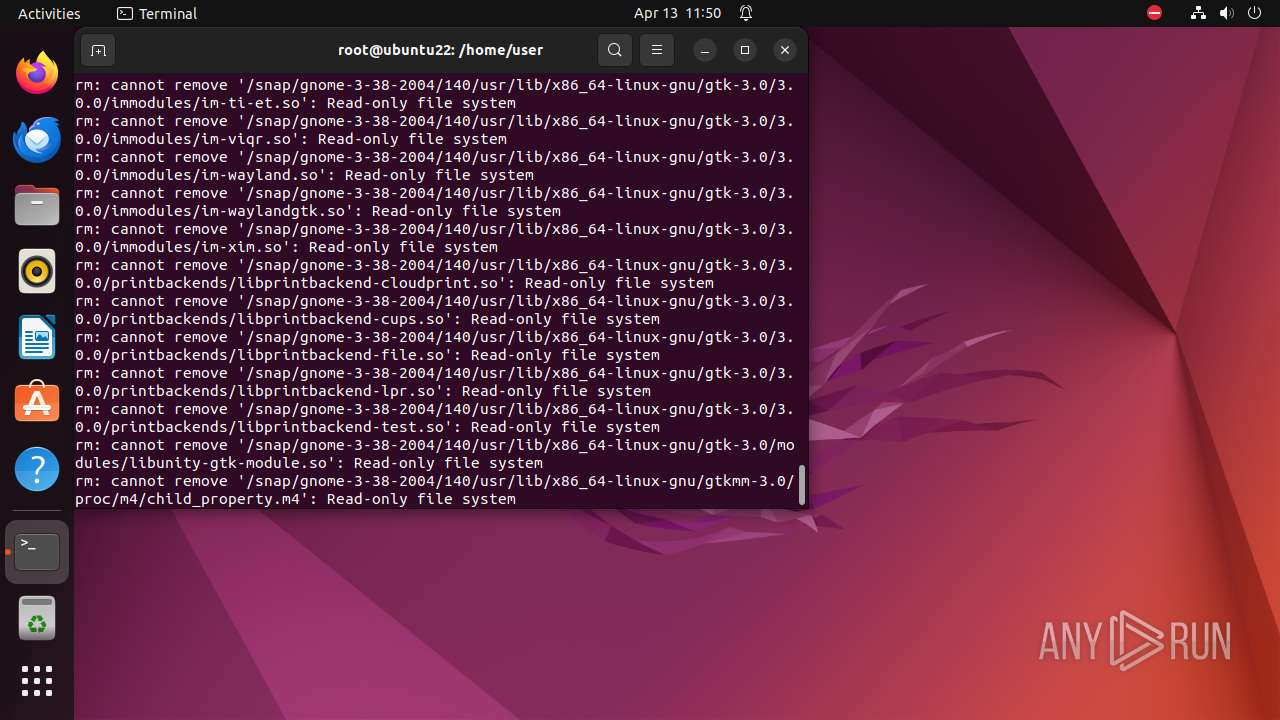
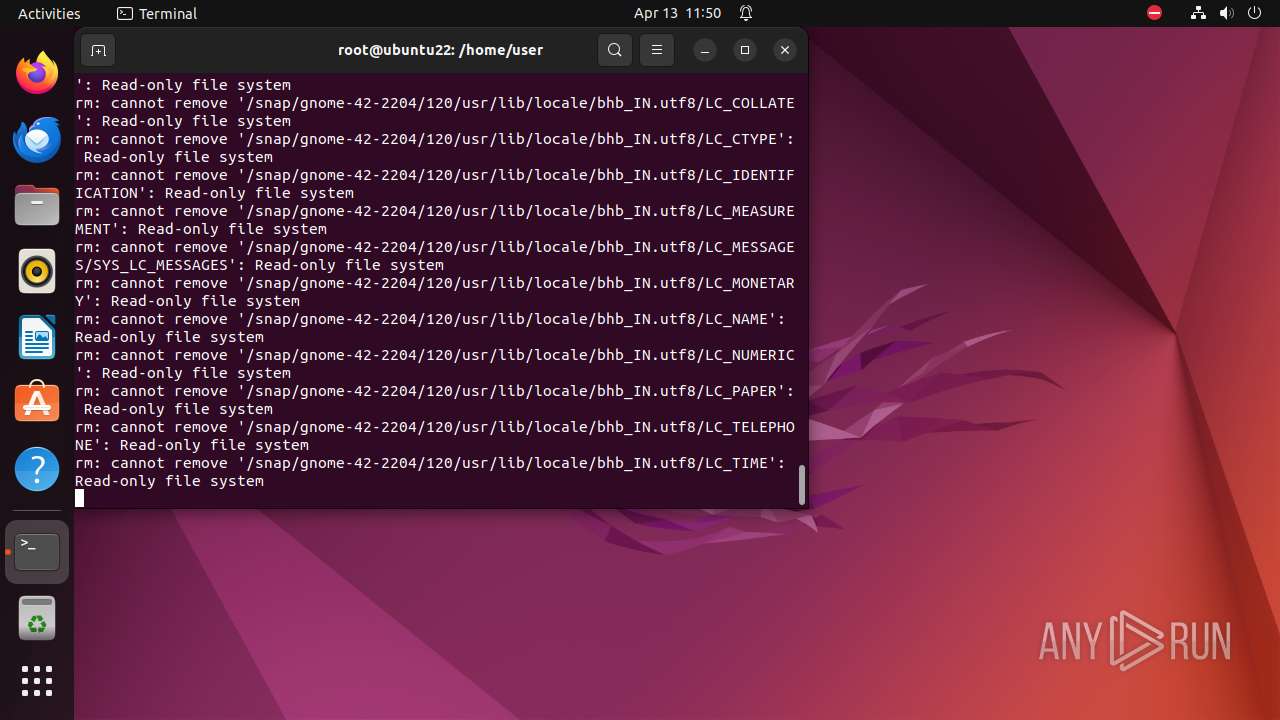
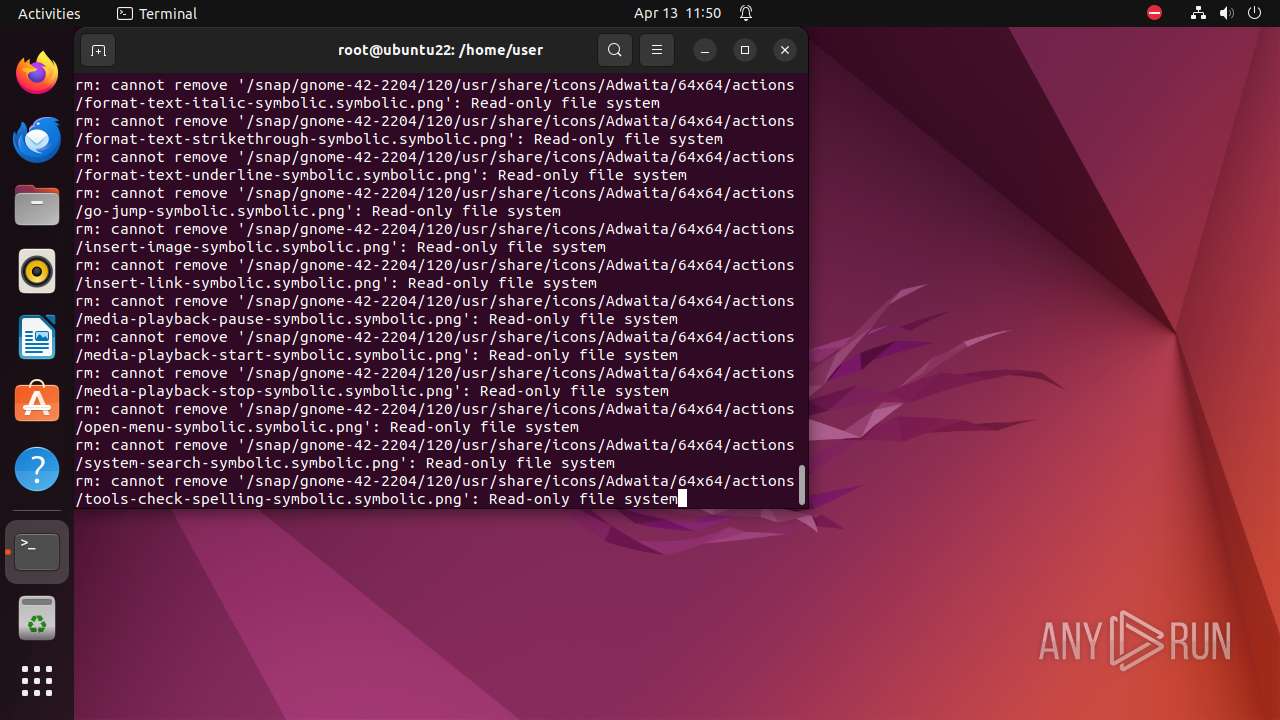
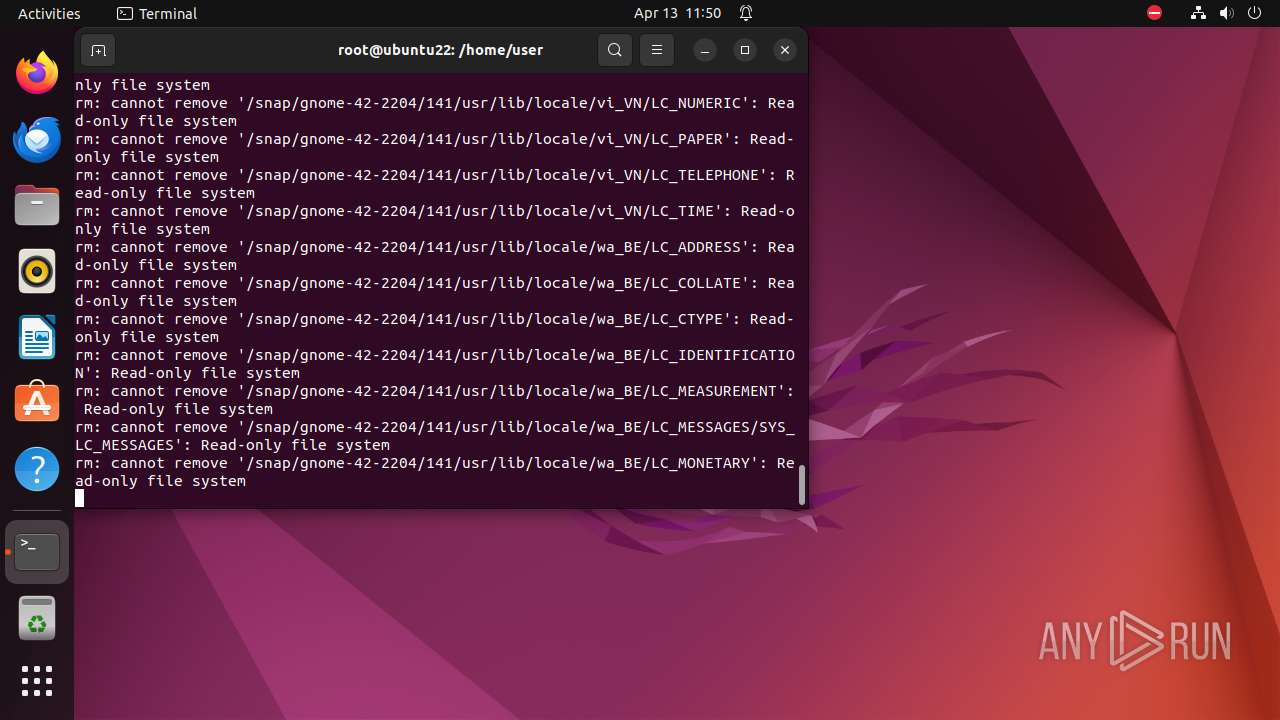
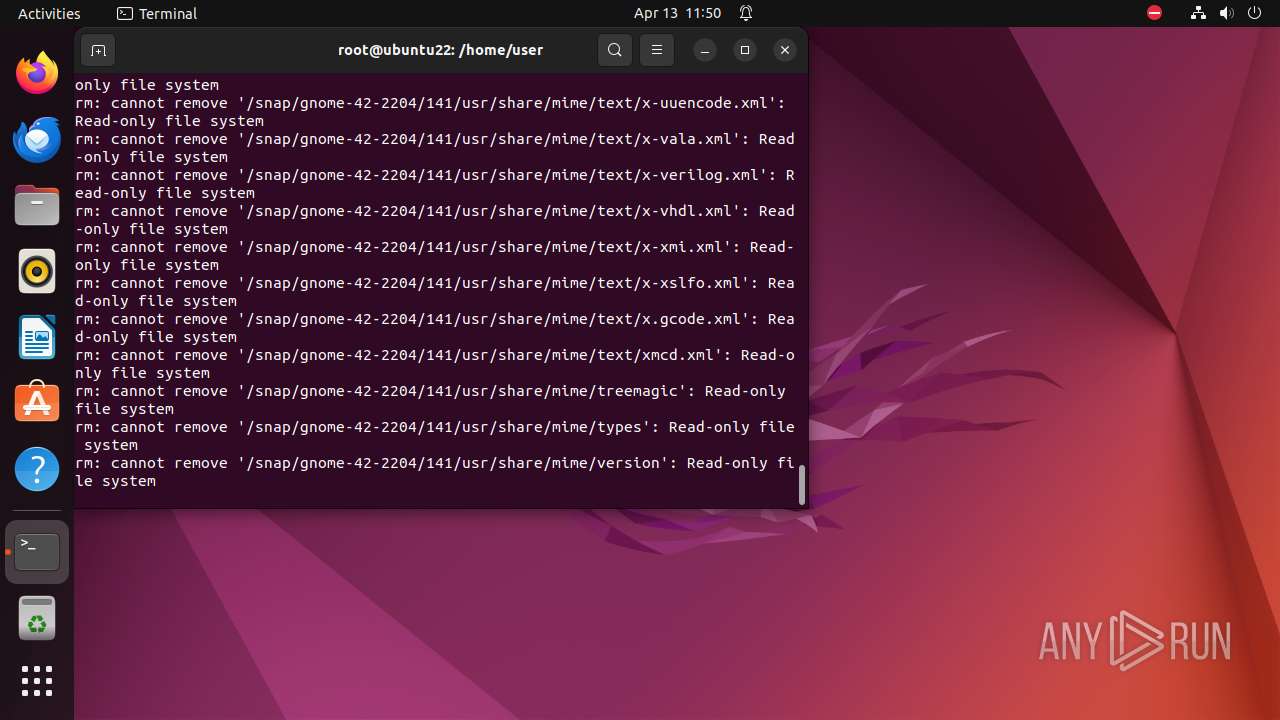
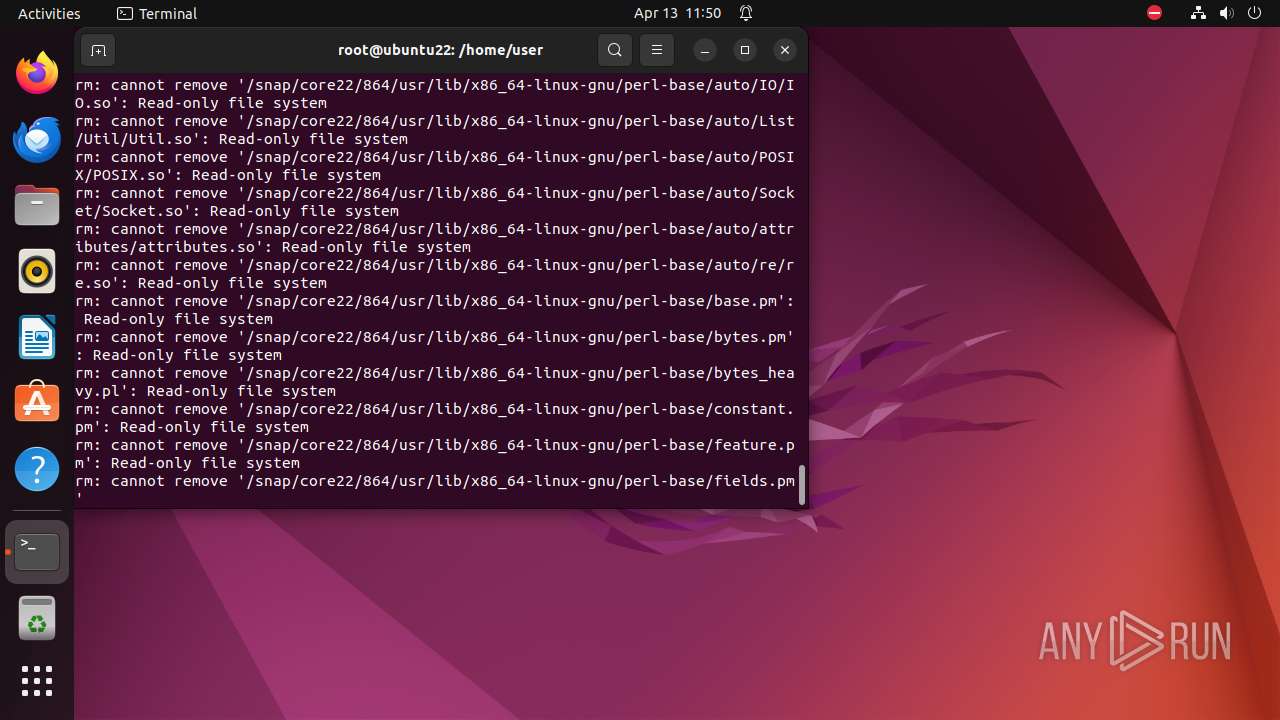
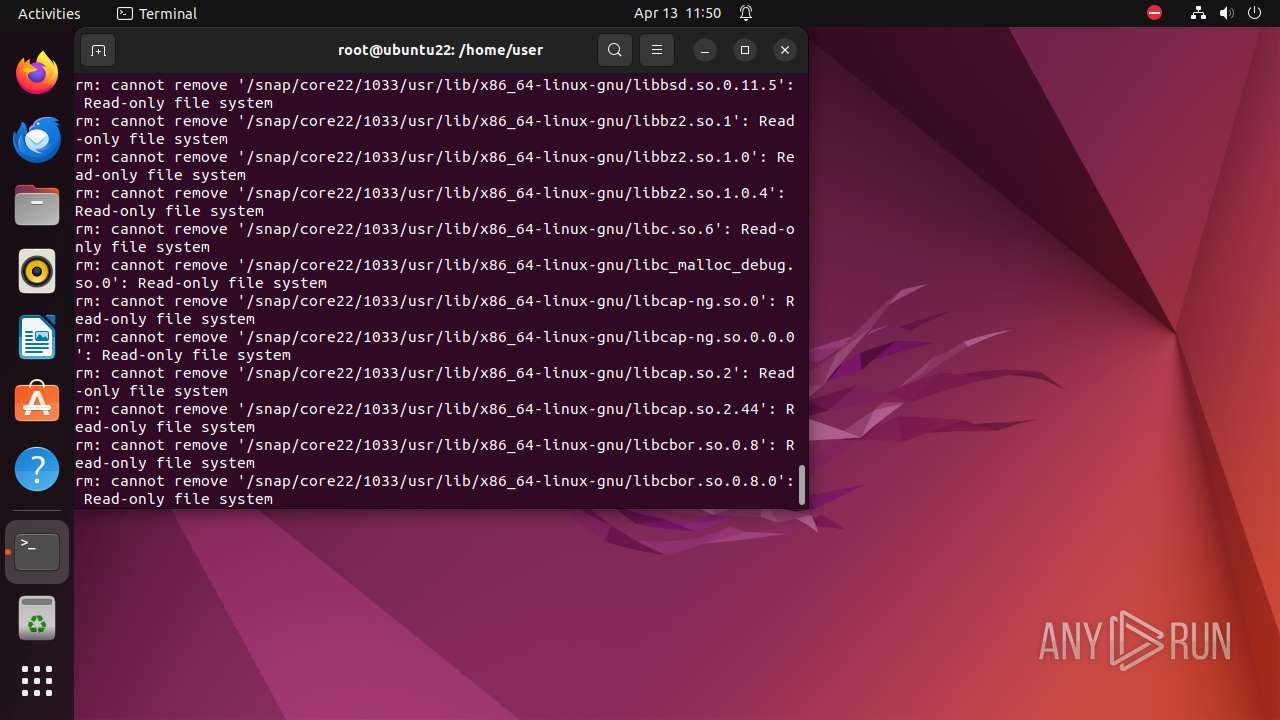
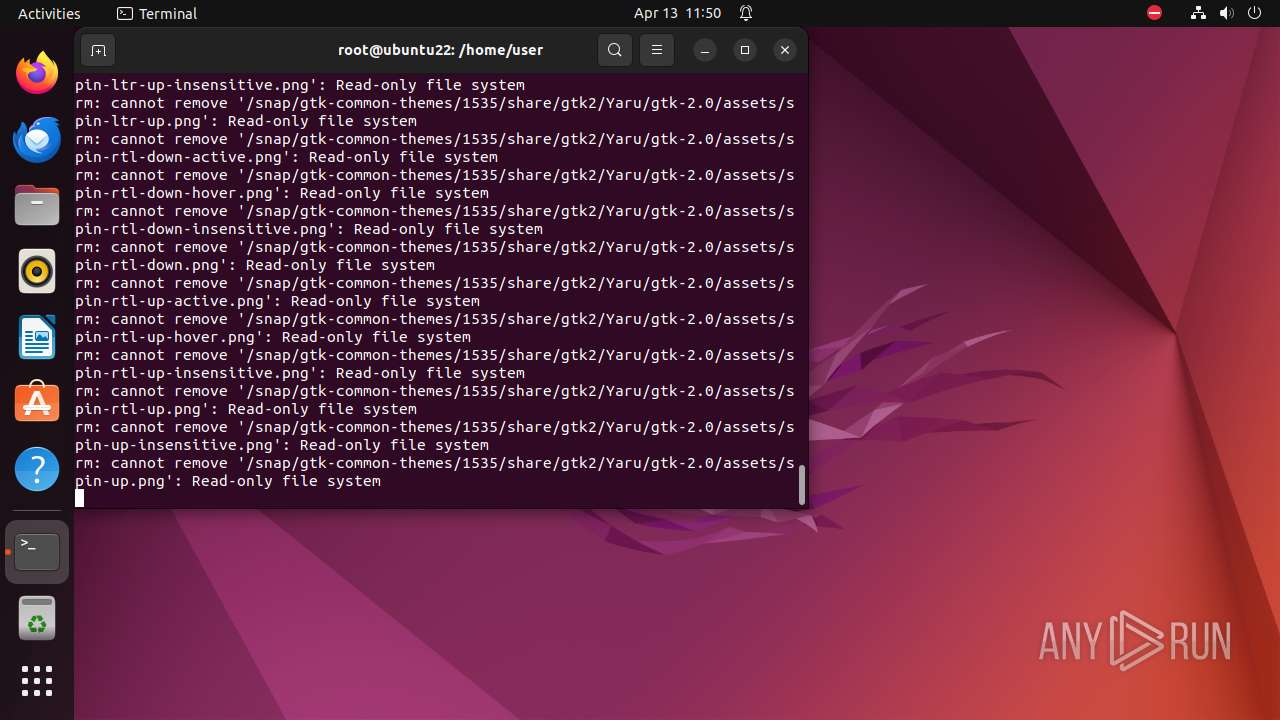
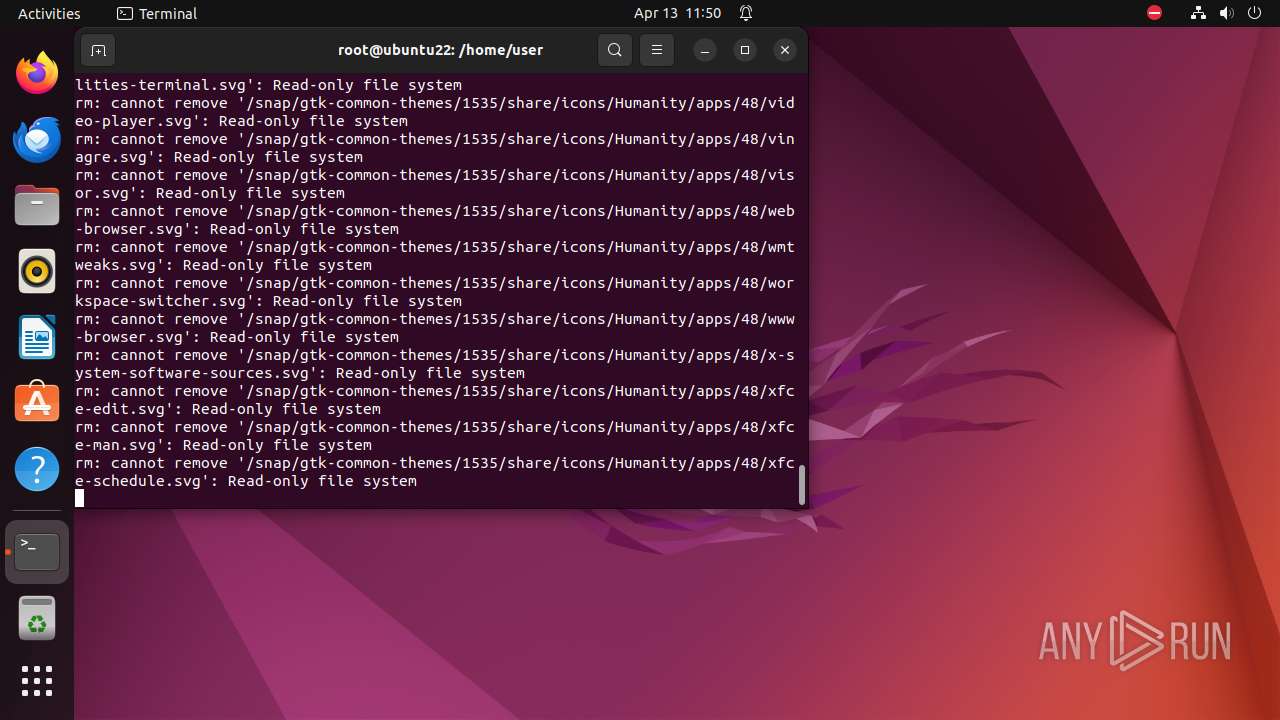
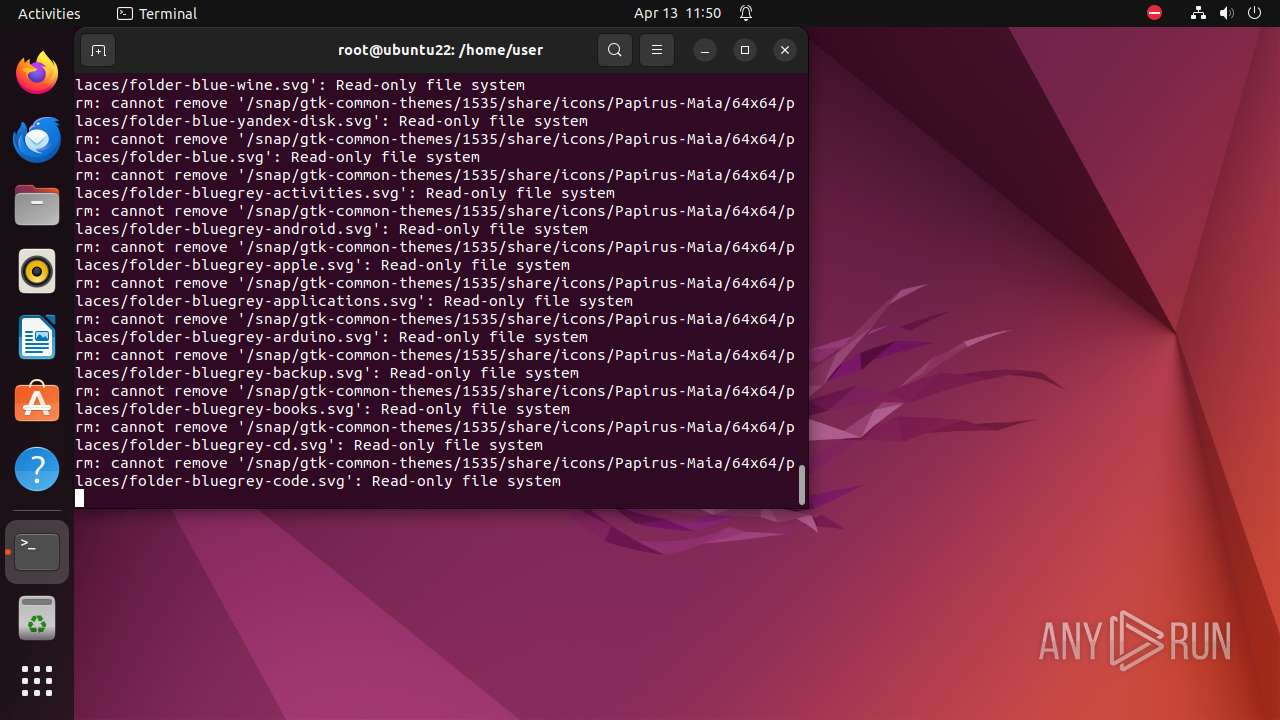
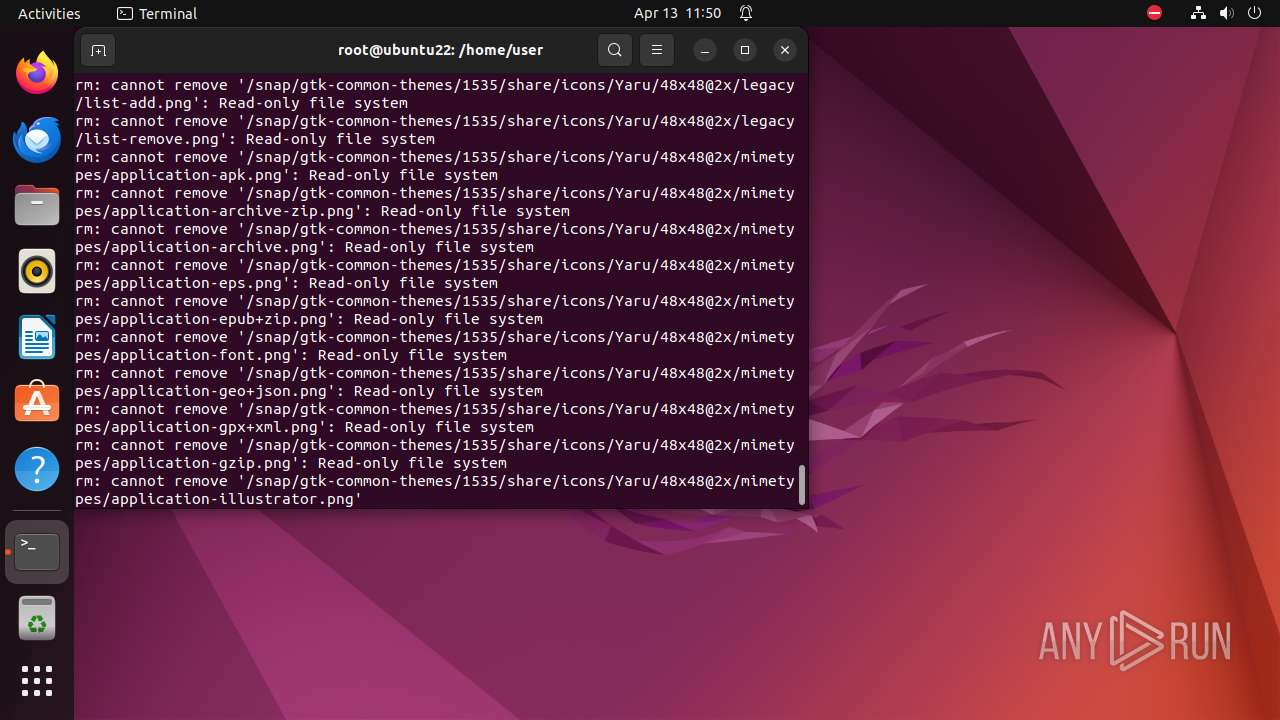
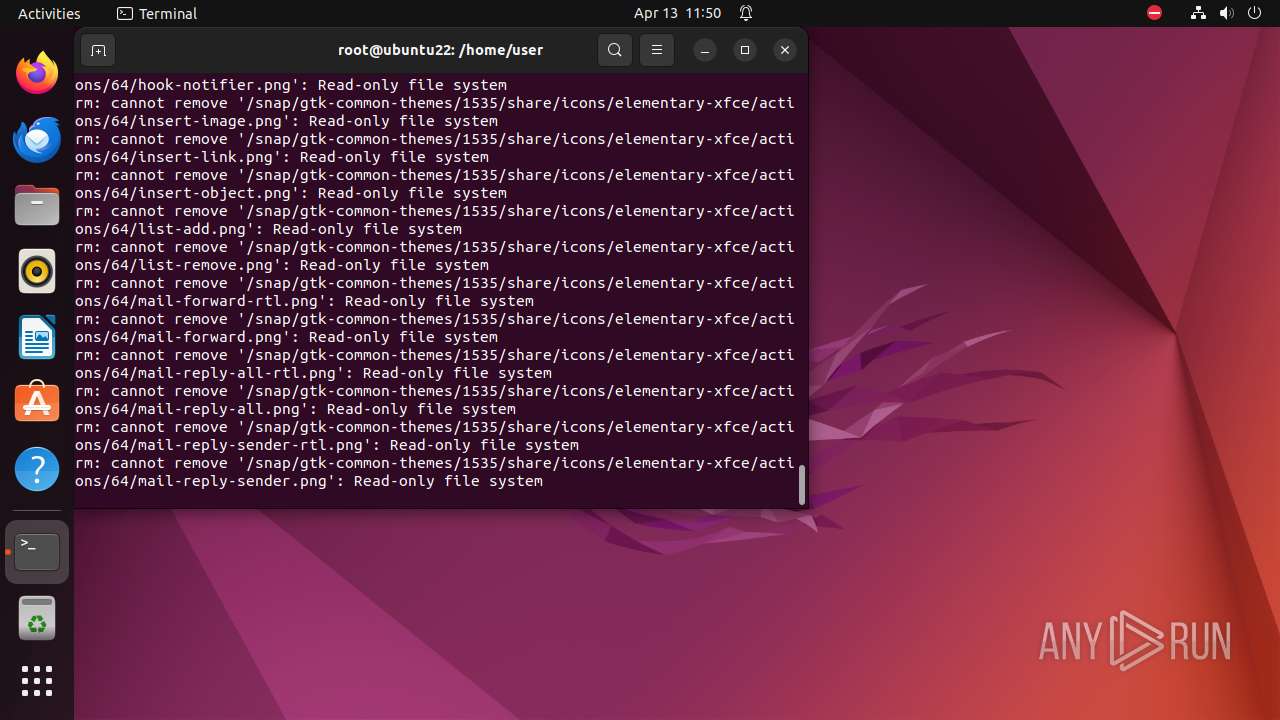
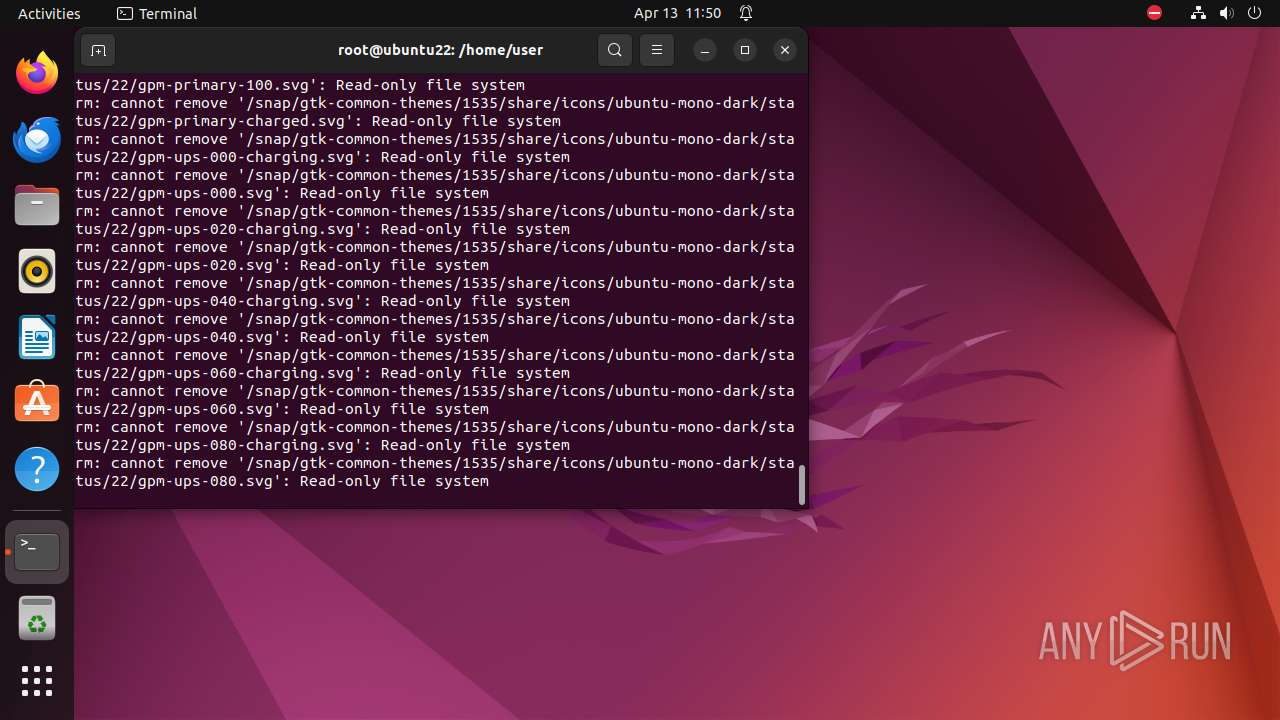
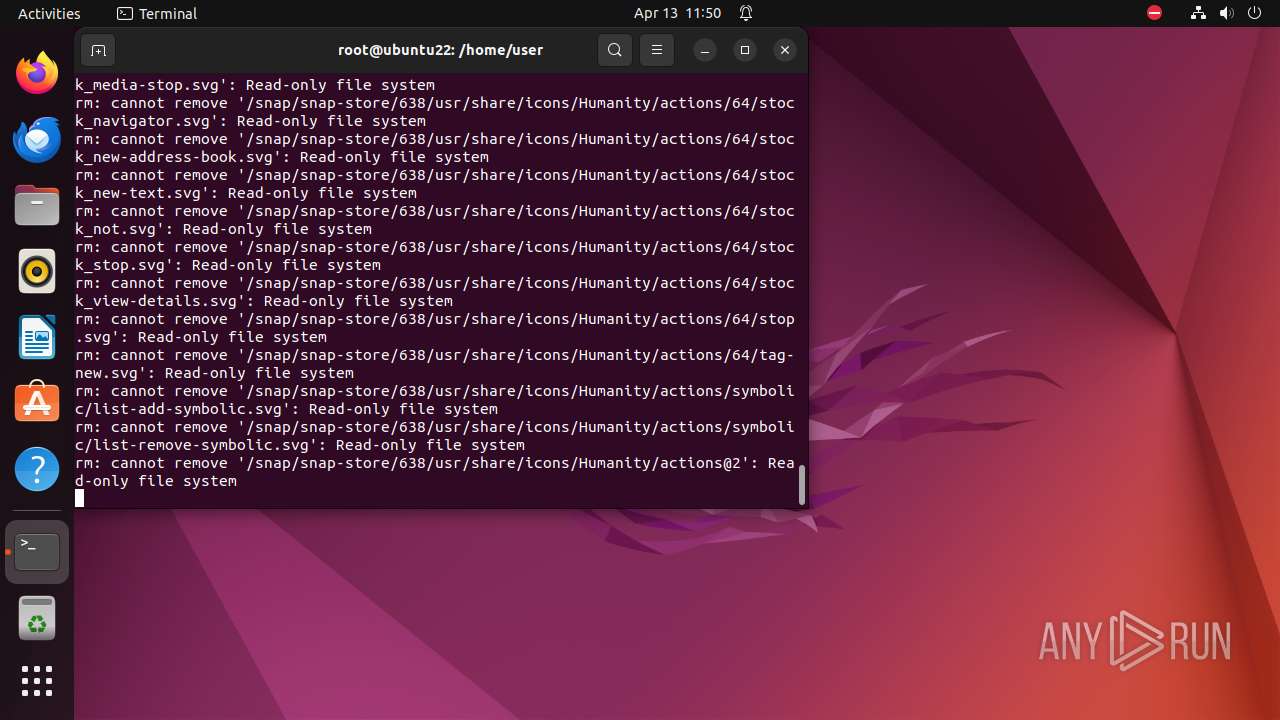
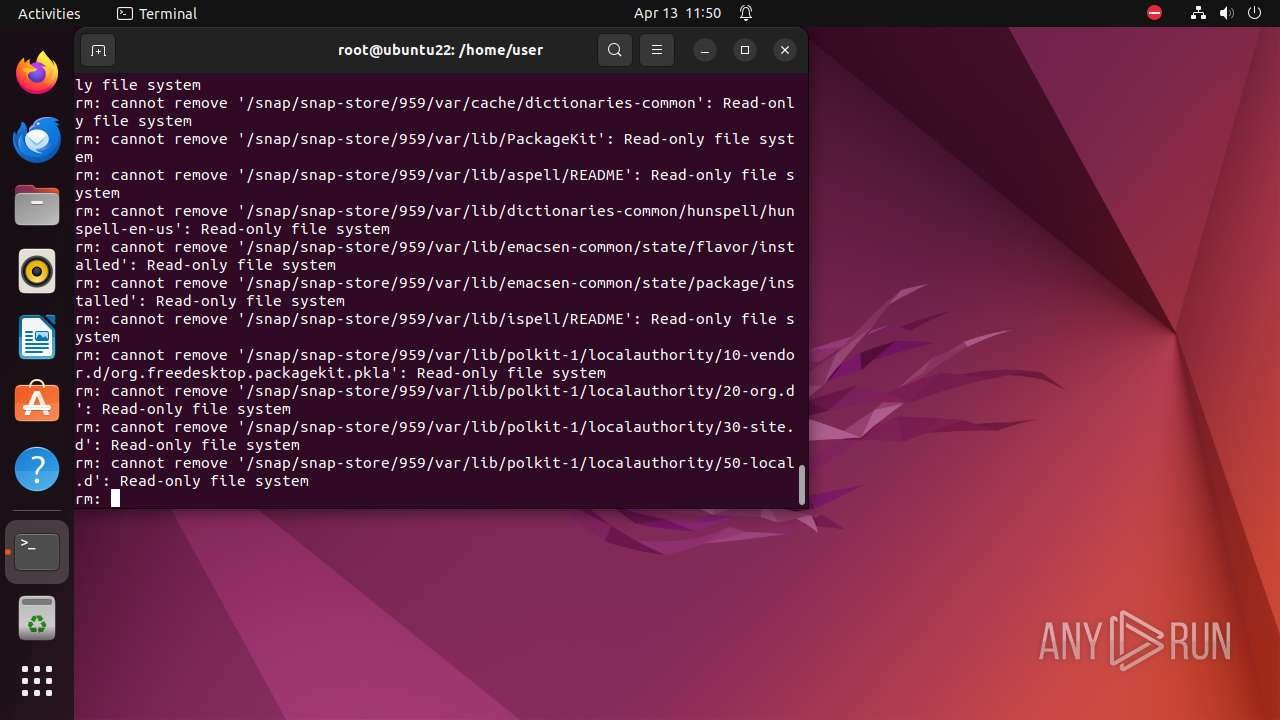
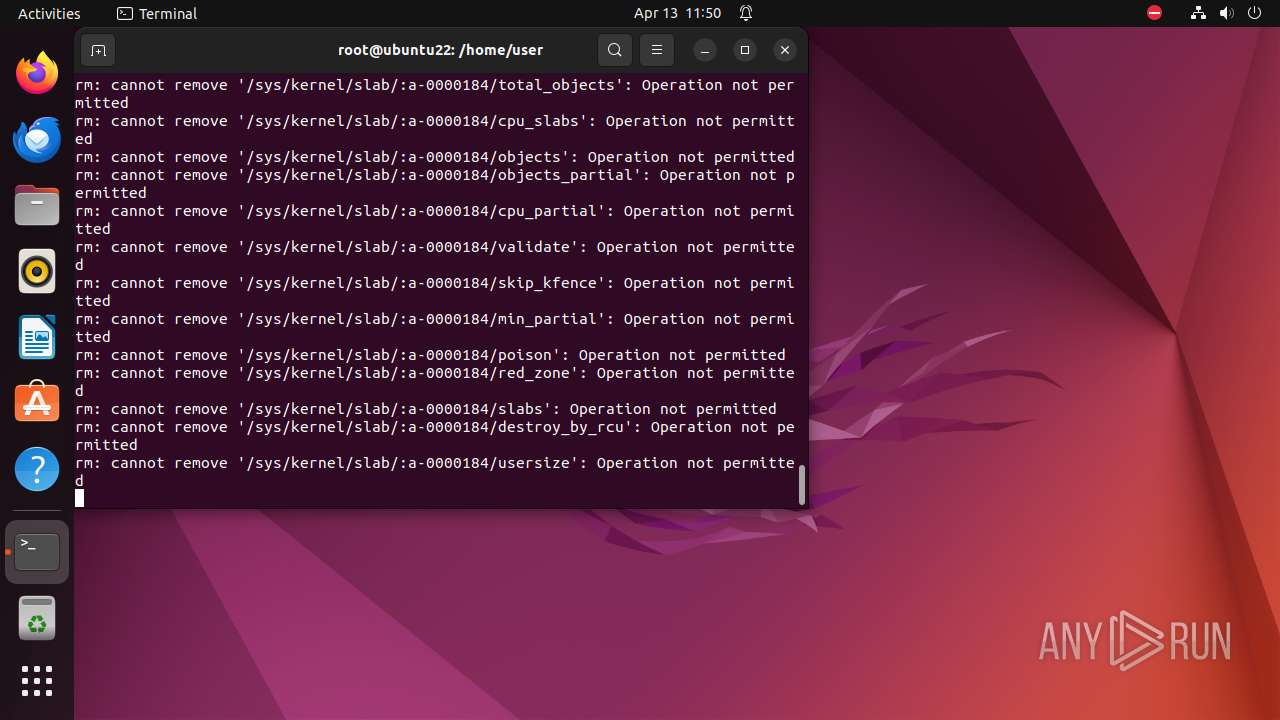
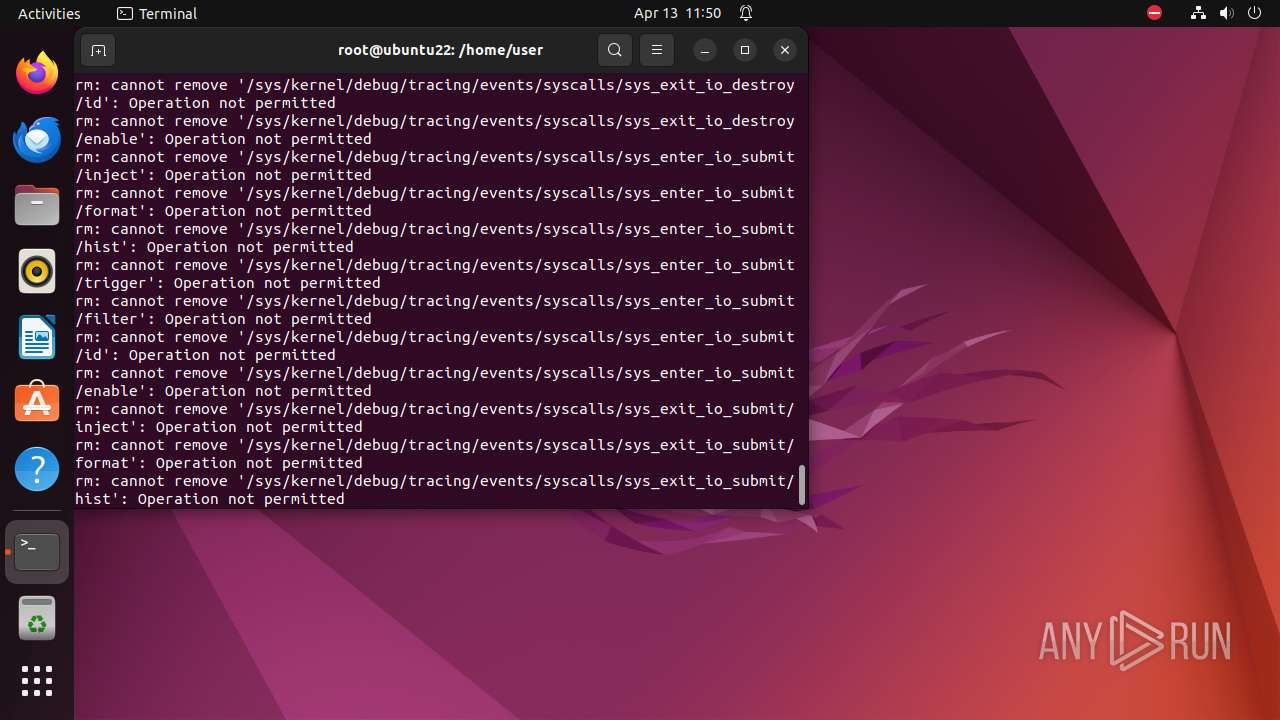
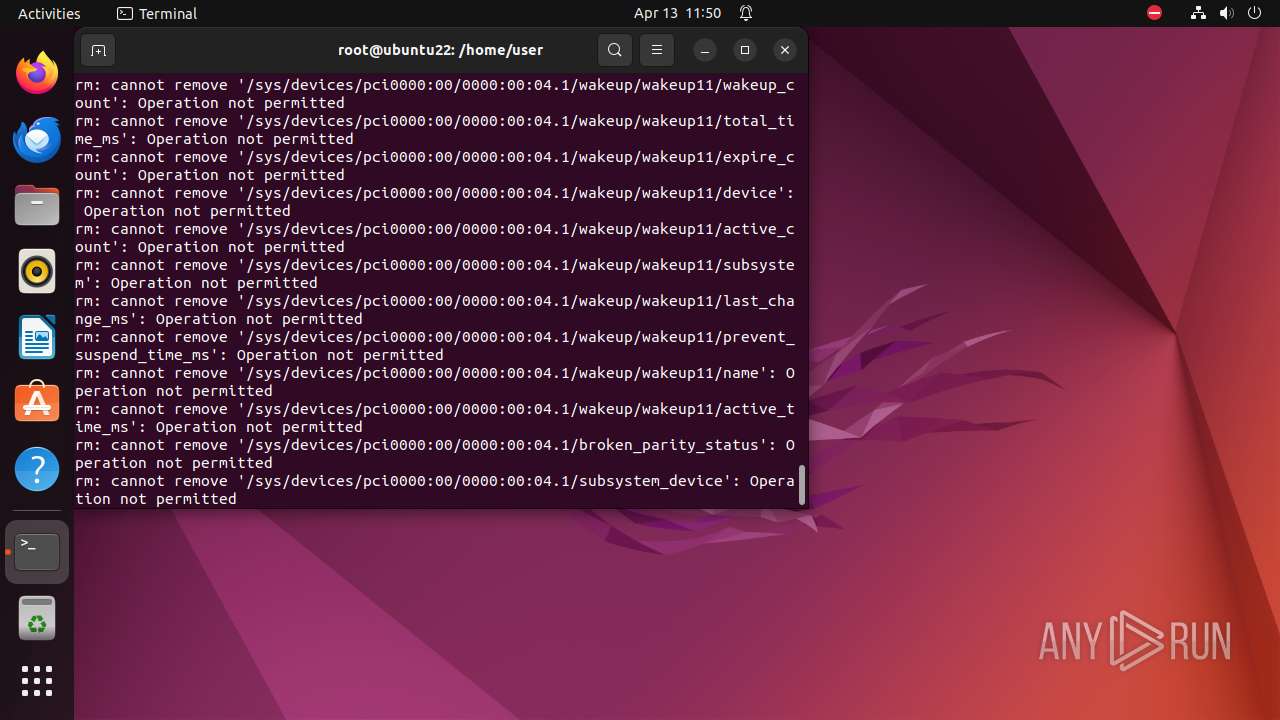
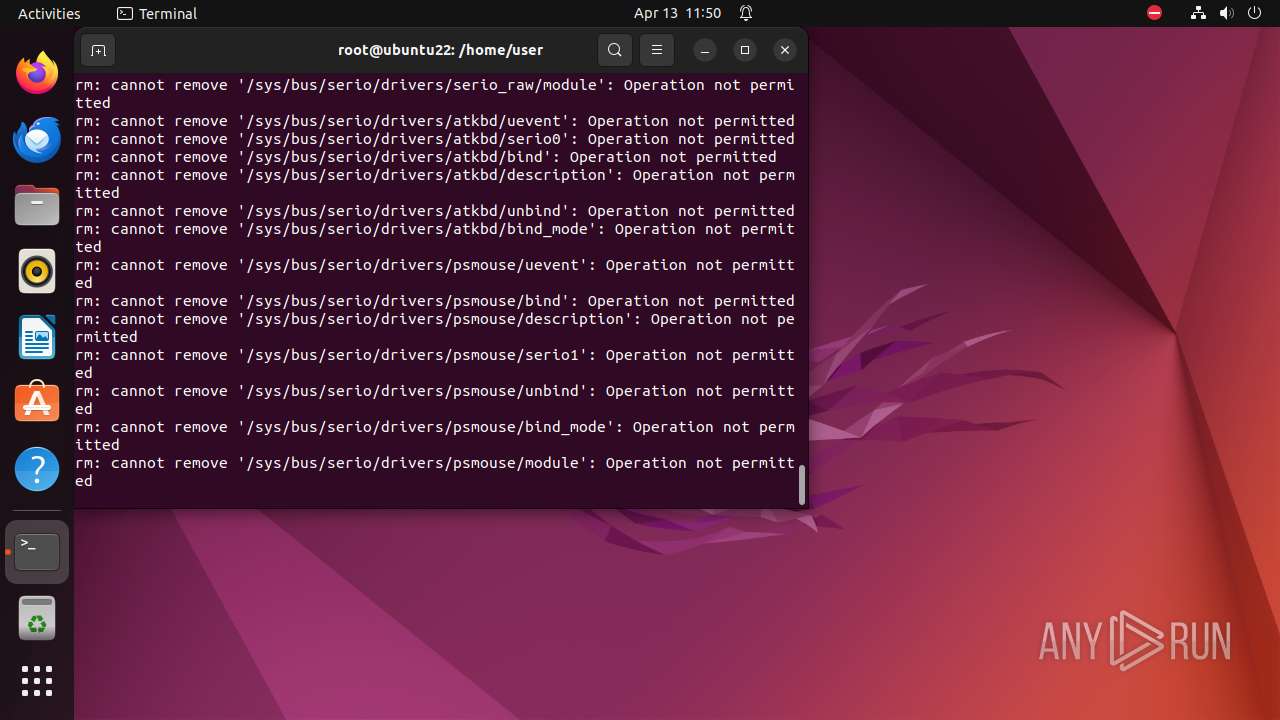
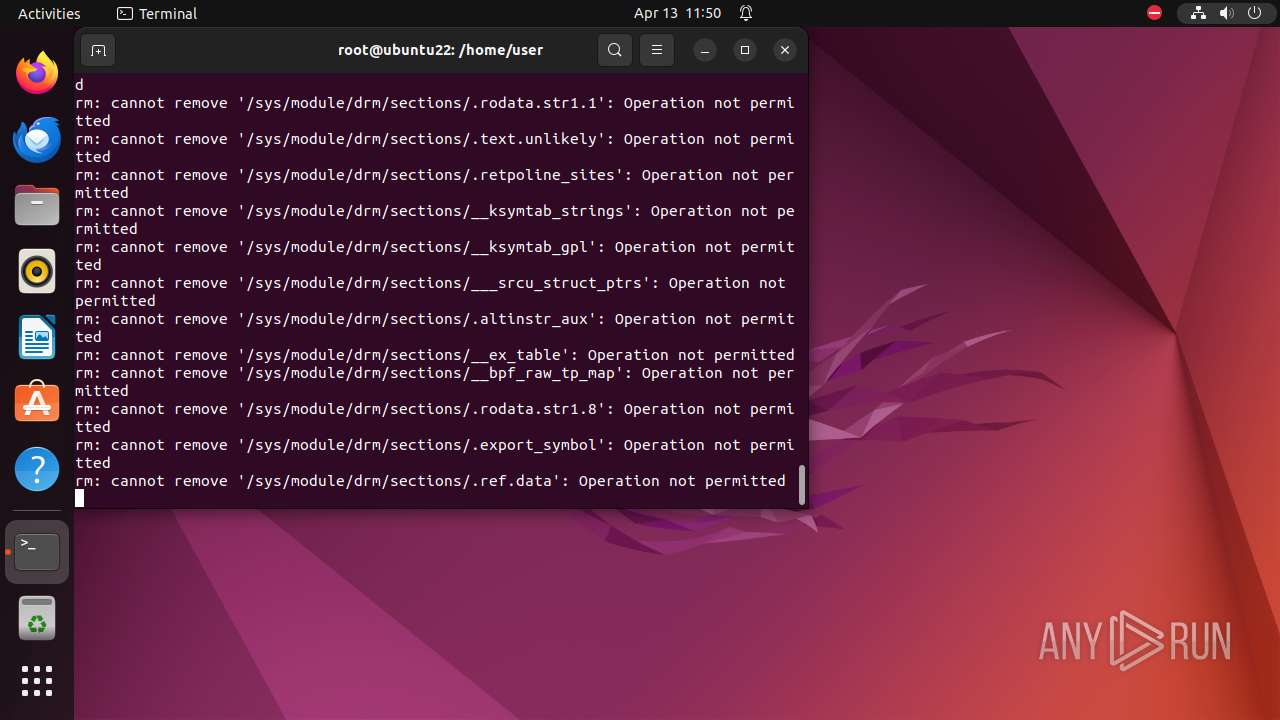
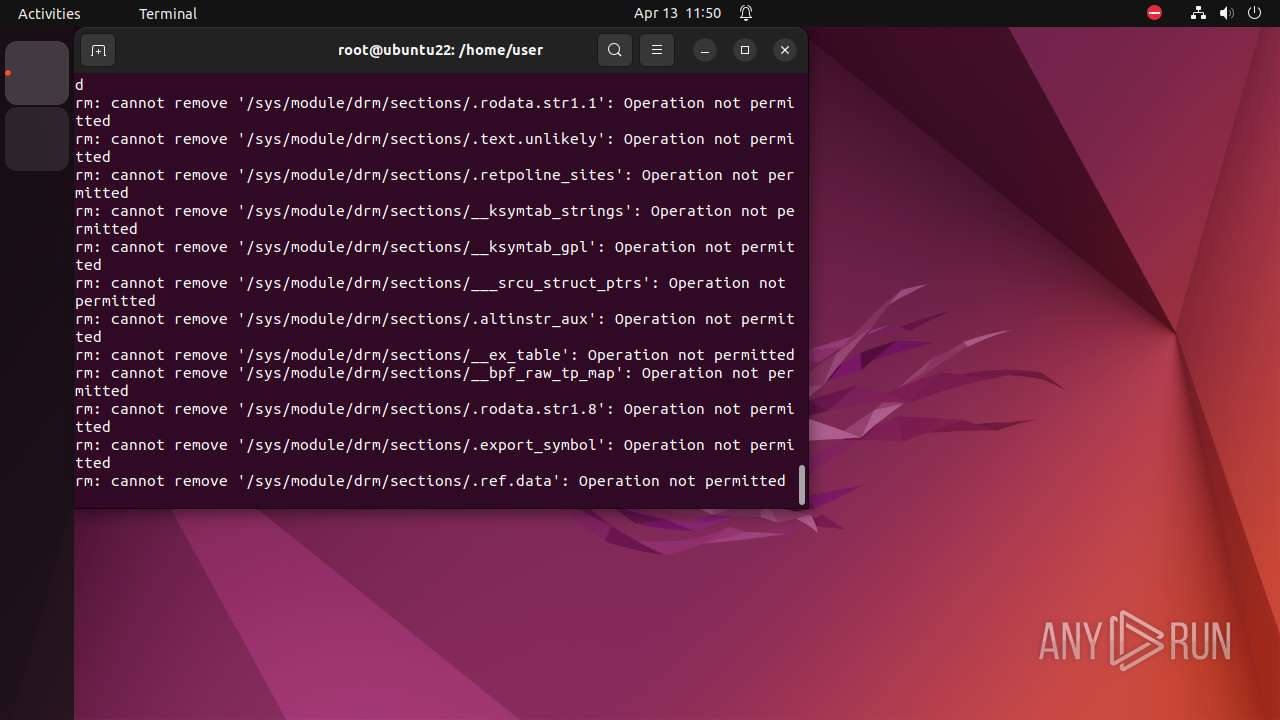
Executes the "rm" command to delete files or directories
- bash (PID: 9334)
Reads information about logins, logouts, and login attempts
- sudo (PID: 9332)
- bash (PID: 9320)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2043:01:15 20:10:58+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 3329536 |
| InitializedDataSize: | 9658368 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2da800 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.6.0.40079 |
| ProductVersionNumber: | 1.6.0.40079 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Roblox Corporation |
| FileDescription: | Roblox |
| FileVersion: | 1, 6, 0, 6200463 |
| LegalCopyright: | Copyright © 2020 Roblox Corporation. All rights reserved. |
| OriginalFileName: | Roblox.exe |
| ProductName: | Roblox Bootstrapper |
| ProductVersion: | 1, 6, 0, 6200463 |
Total processes
262
Monitored processes
40
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 9266 | /bin/sh -c "DISPLAY=:0 sudo -iu user nautilus \"/tmp/RobloxPlayerInstaller\.exe\" " | /bin/sh | — | any-guest-agent |
User: user Integrity Level: UNKNOWN Exit code: 9340 | ||||
| 9267 | sudo -iu user nautilus /tmp/RobloxPlayerInstaller.exe | /usr/bin/sudo | — | sh |
User: user Integrity Level: UNKNOWN Exit code: 676 | ||||
| 9268 | nautilus /tmp/RobloxPlayerInstaller.exe | /usr/bin/nautilus | — | sudo |
User: user Integrity Level: UNKNOWN Exit code: 9340 | ||||
| 9269 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | nautilus |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 9288 | /lib/systemd/systemd-hostnamed | /lib/systemd/systemd-hostnamed | — | systemd |
User: root Integrity Level: UNKNOWN Exit code: 9340 | ||||
| 9295 | /usr/bin/python3 /usr/bin/gnome-terminal | /usr/bin/gnome-terminal | — | gnome-shell |
User: user Integrity Level: UNKNOWN Exit code: 496 | ||||
| 9297 | /usr/bin/gnome-terminal.real | /usr/bin/gnome-terminal.real | — | gnome-terminal |
User: user Integrity Level: UNKNOWN Exit code: 496 | ||||
| 9302 | /usr/libexec/gnome-terminal-server | /usr/libexec/gnome-terminal-server | — | systemd |
User: user Integrity Level: UNKNOWN | ||||
| 9320 | bash | /bin/bash | — | gnome-terminal-server |
User: user Integrity Level: UNKNOWN | ||||
| 9321 | /bin/sh /usr/bin/lesspipe | /usr/bin/lesspipe | — | bash |
User: user Integrity Level: UNKNOWN Exit code: 496 | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 9268 | nautilus | /home/user/.local/share/nautilus/tags/meta.db-wal | — | |
MD5:— | SHA256:— | |||
| 9268 | nautilus | /home/user/.local/share/nautilus/tags/meta.db-shm | — | |
MD5:— | SHA256:— | |||
| 9268 | nautilus | /home/user/.local/share/nautilus/tags/.meta.isrunning | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
4
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 185.125.190.98:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.125.190.98:80 | — | Canonical Group Limited | GB | unknown |
— | — | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.snapcraft.io |
| unknown |
38.100.168.192.in-addr.arpa |
| unknown |
connectivity-check.ubuntu.com |
| unknown |