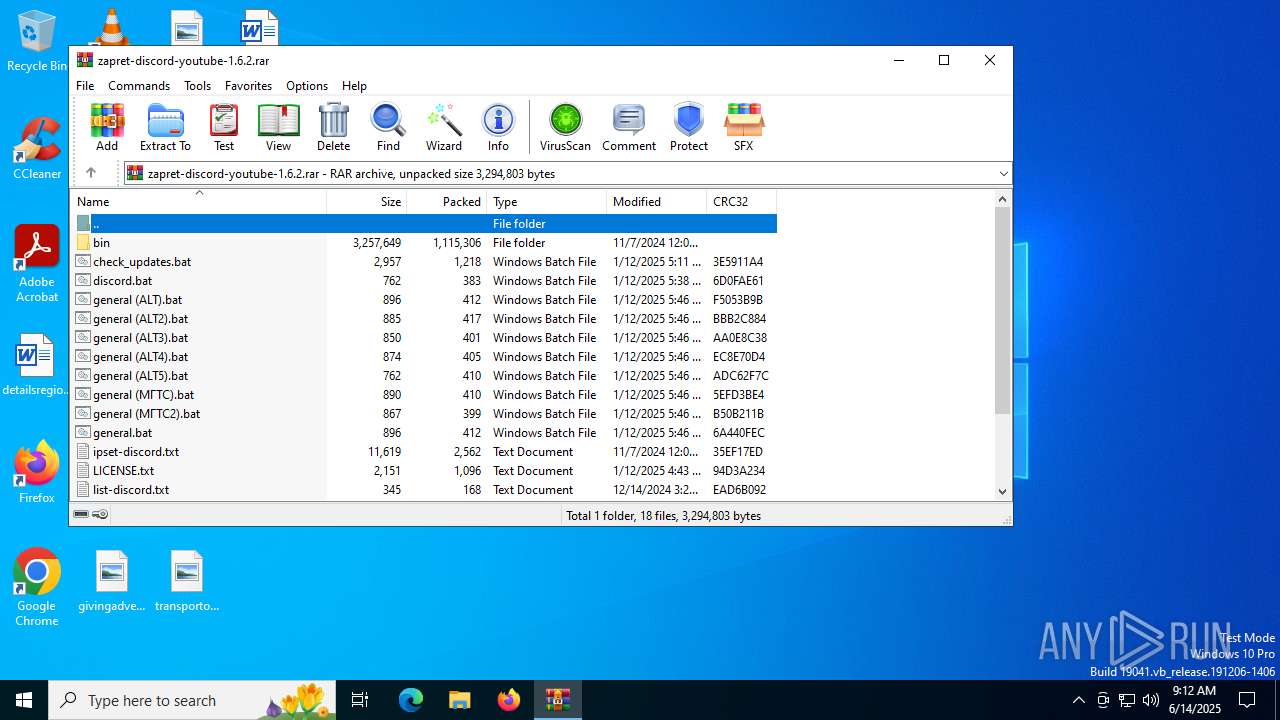
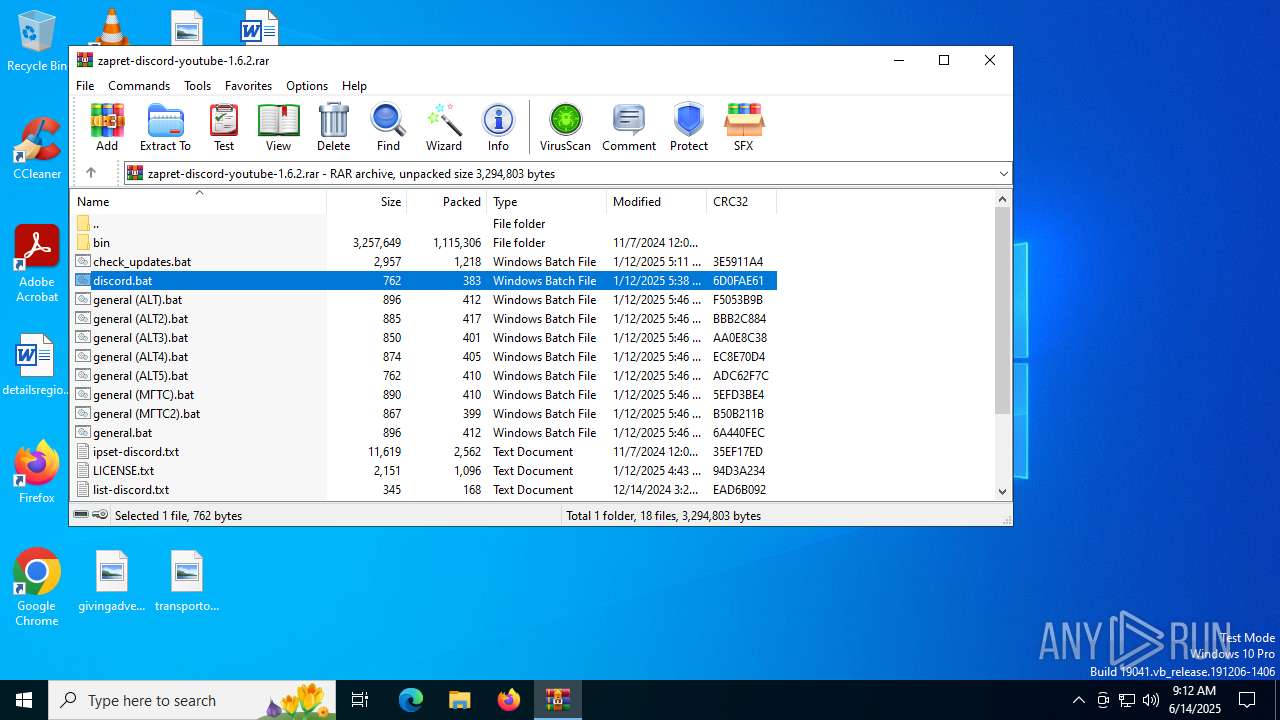
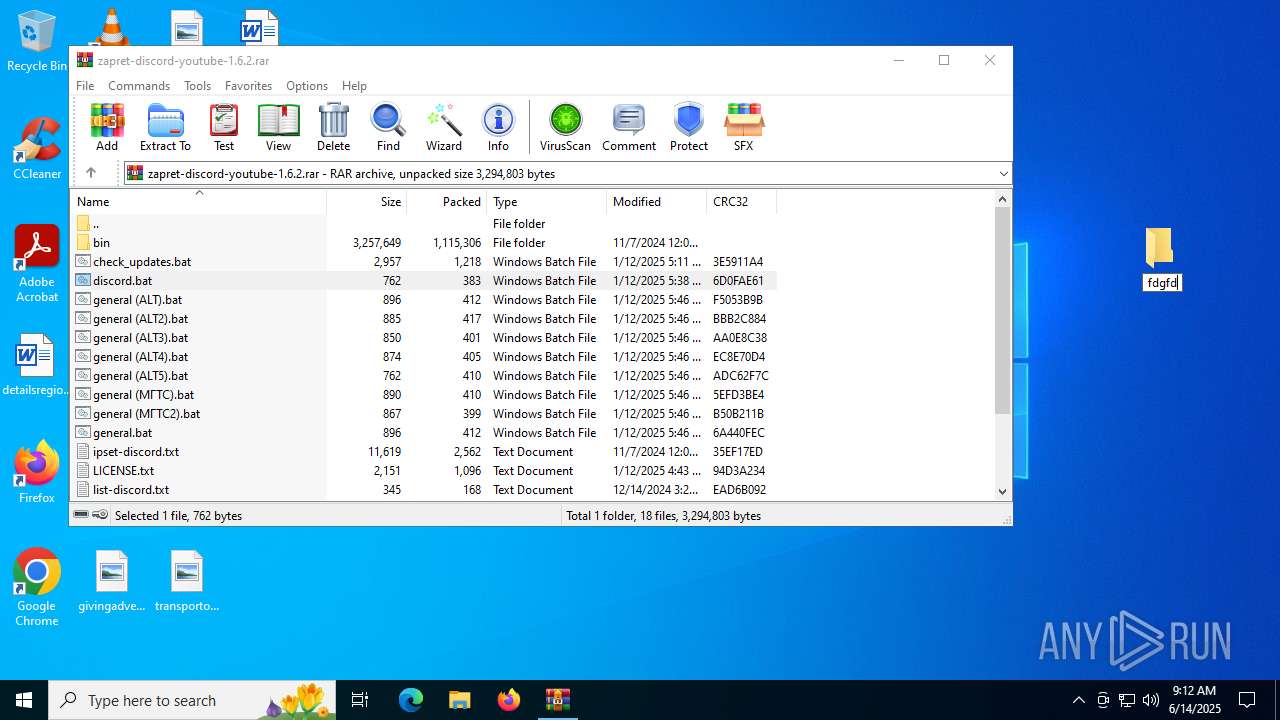
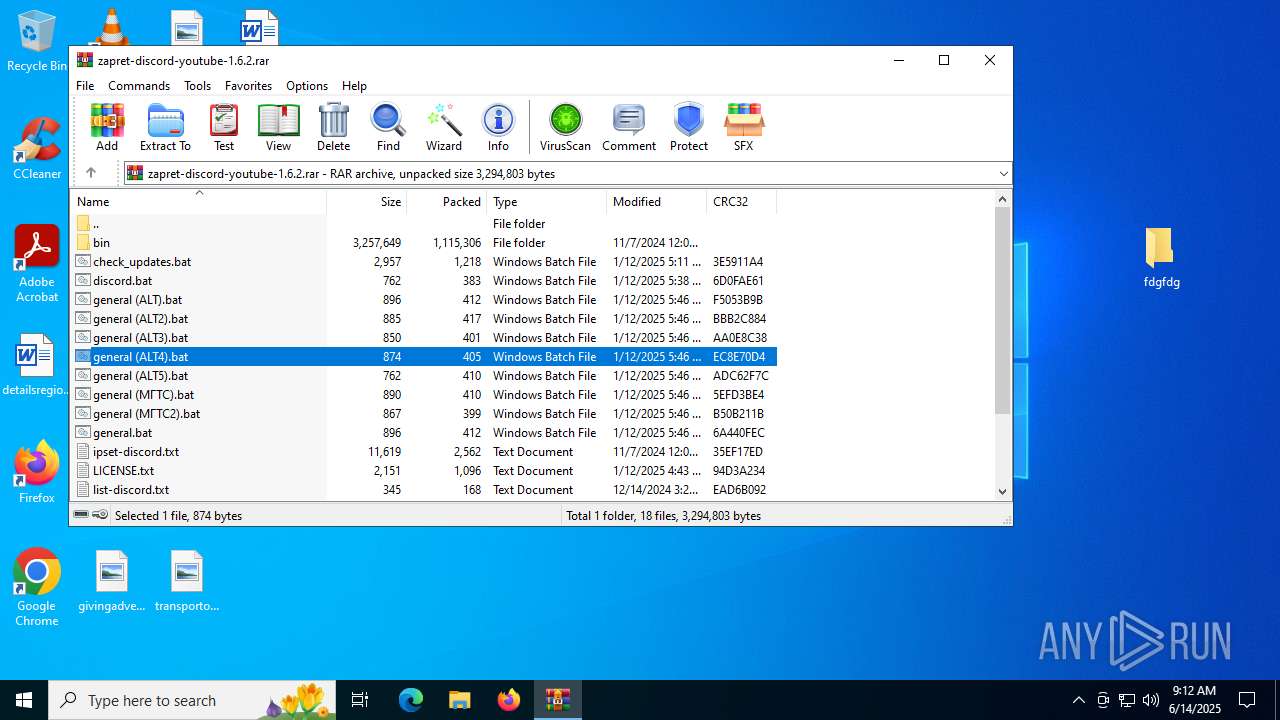
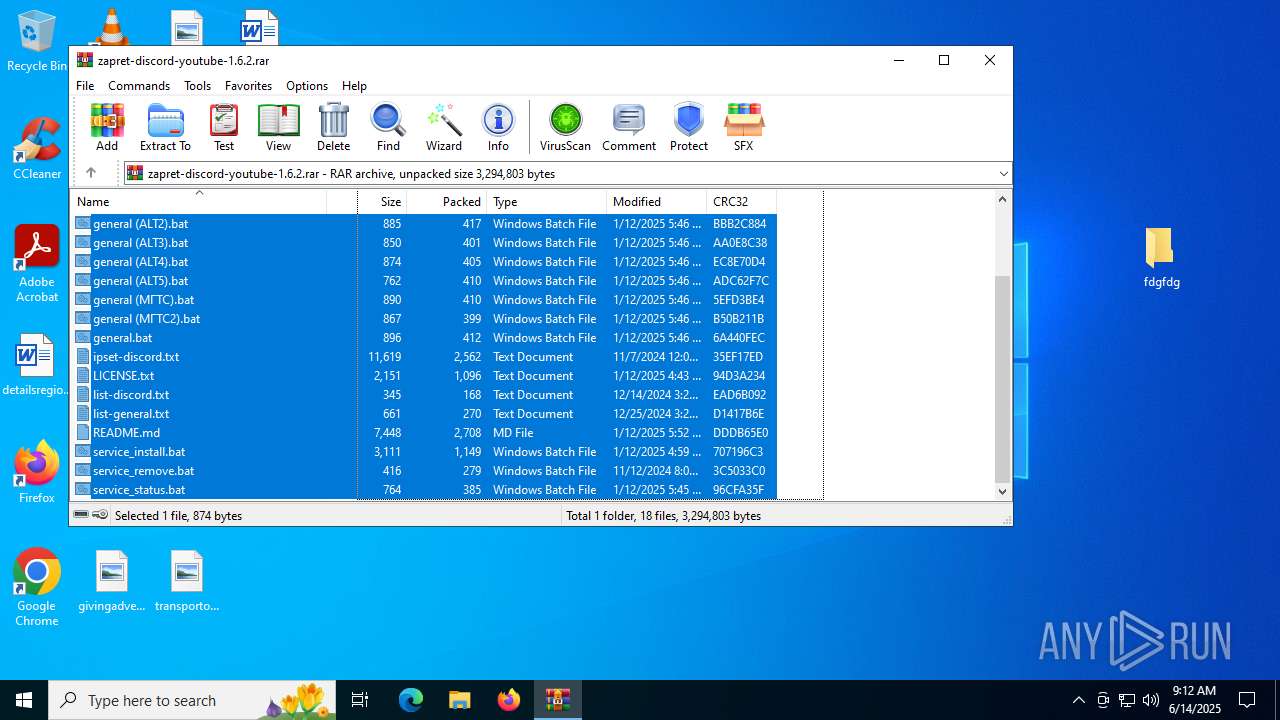
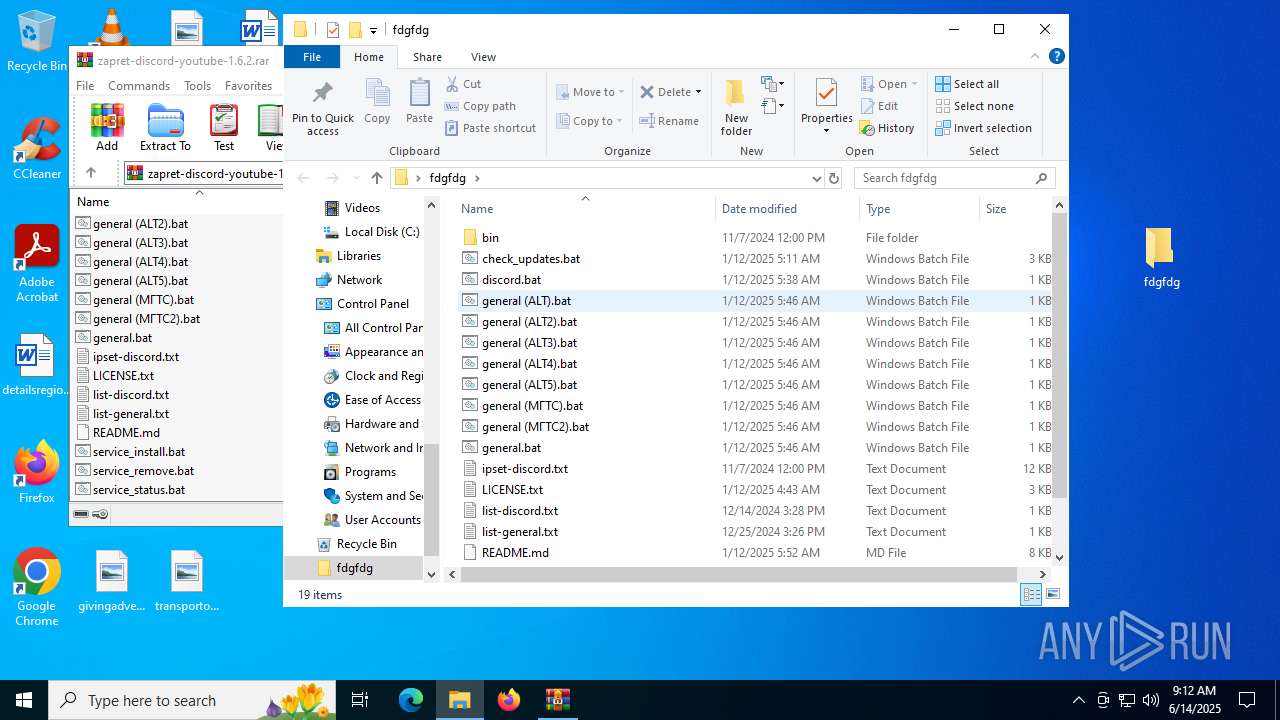
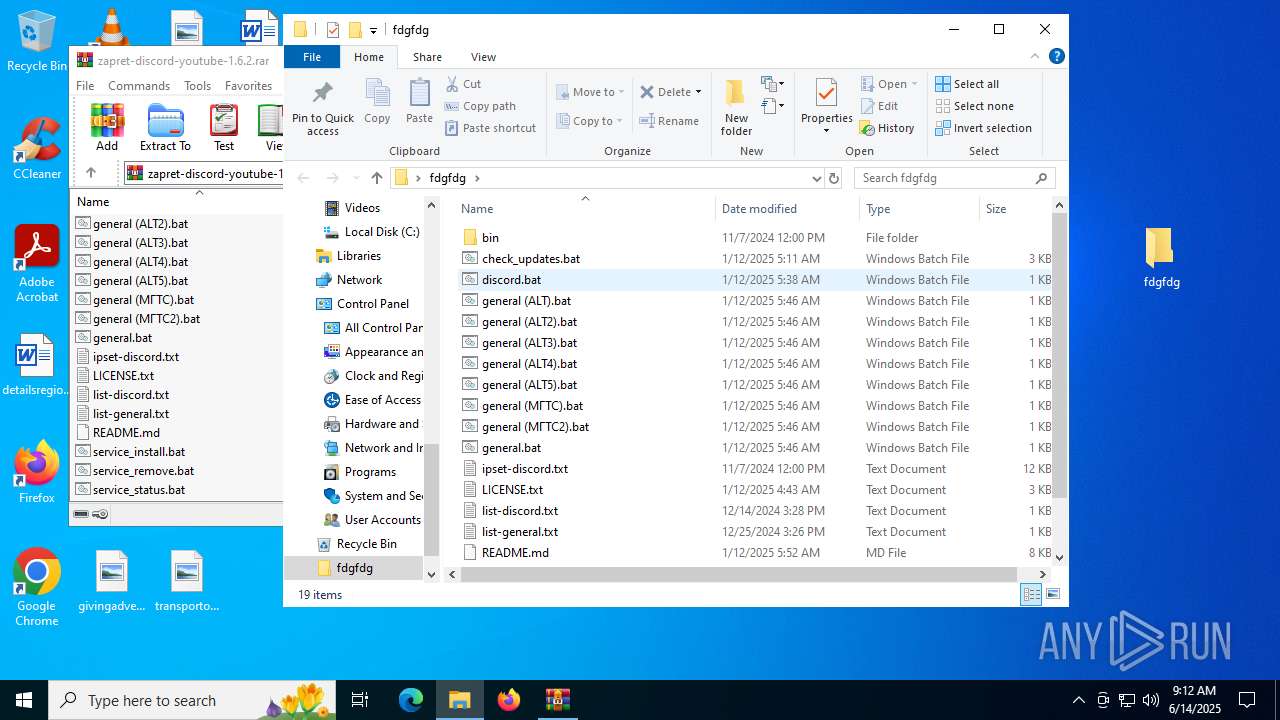
| File name: | zapret-discord-youtube-1.6.2.rar |
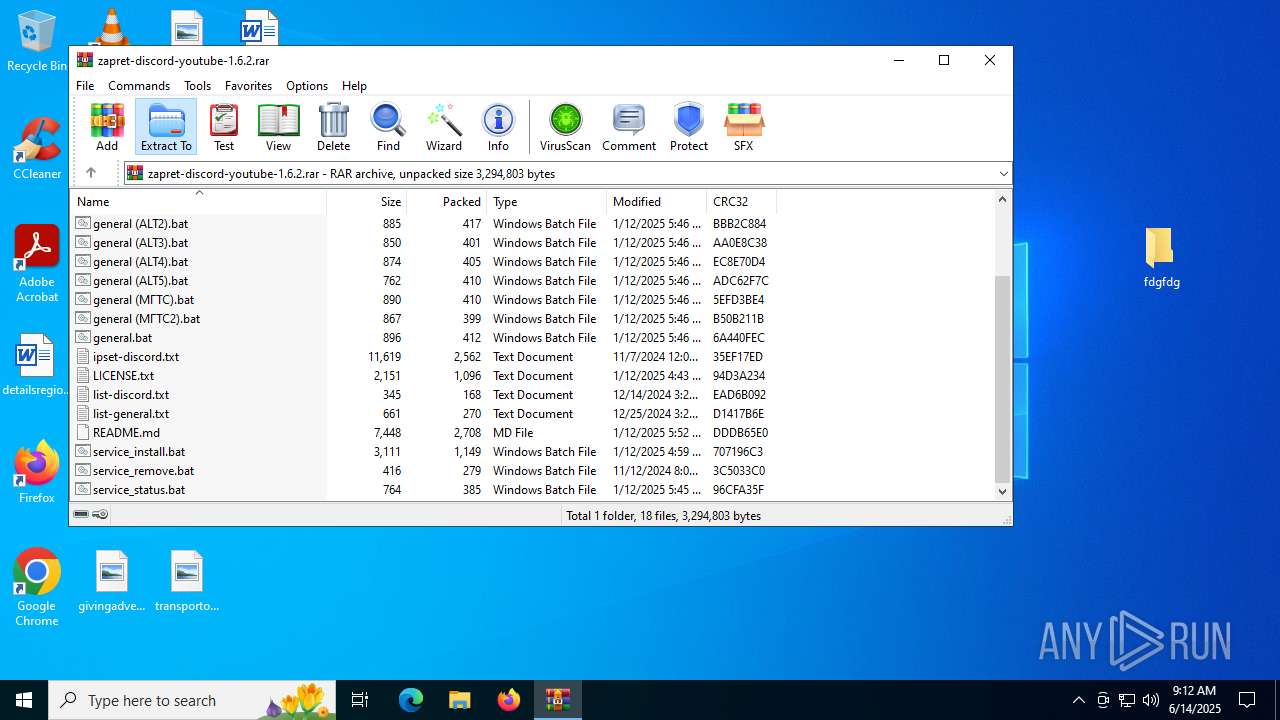
| Full analysis: | https://app.any.run/tasks/caf94b32-3041-4051-bbcd-7af79cb89b1e |
| Verdict: | Malicious activity |
| Analysis date: | June 14, 2025, 09:11:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | E176C1C6DEF5D68F96A6F63F5B7041A9 |
| SHA1: | A84C6A5C3D693892B16B9AF0CEAFB99995F6E9AD |
| SHA256: | 794AD16D8BC98FCB4B4F06CAA811FFEC8C81324C6336132F726BF09E21B66FC6 |
| SSDEEP: | 49152:ZRckt37ZRWJIIw3nM7ZfsDvHlkoanajWkEhhSdq5XKlvaB0mkr5Bw0IHZj09u70p:Z6kVZ4IIw34ZfsbSoWajHUGqtKli1krr |
MALICIOUS
Detects Cygwin installation
- WinRAR.exe (PID: 5616)
Malicious driver has been detected
- WinRAR.exe (PID: 5616)
SUSPICIOUS
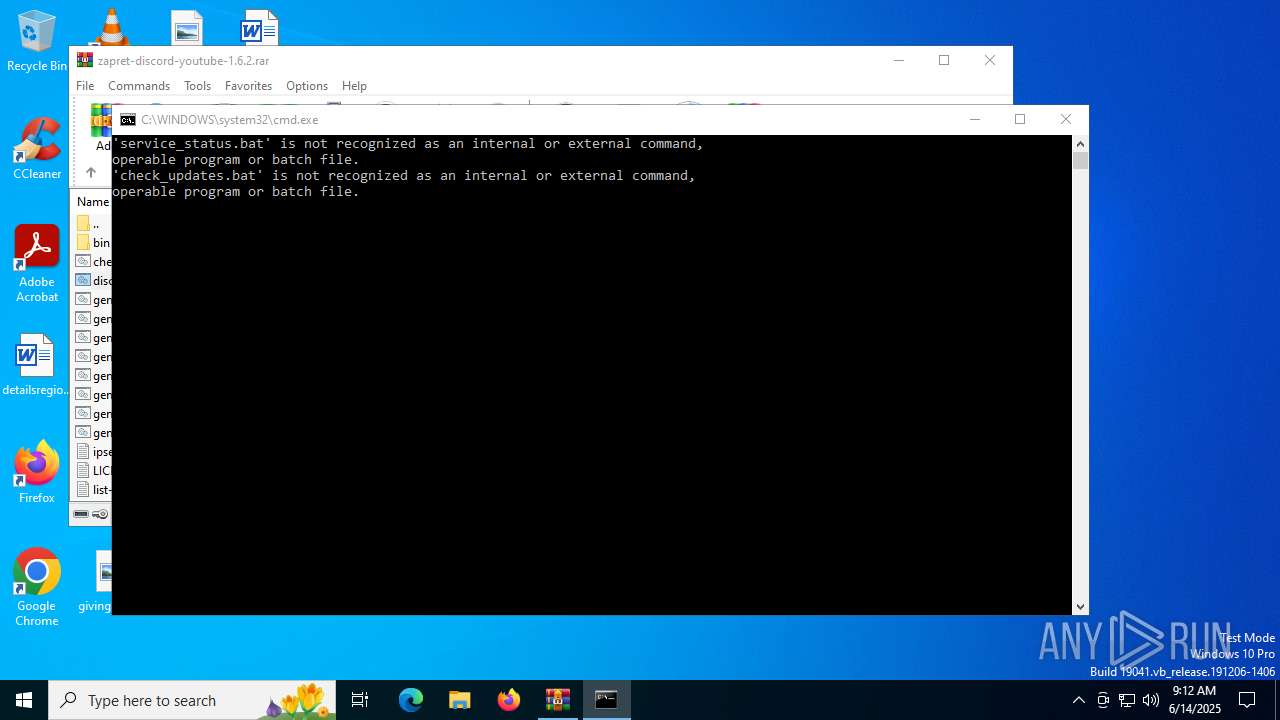
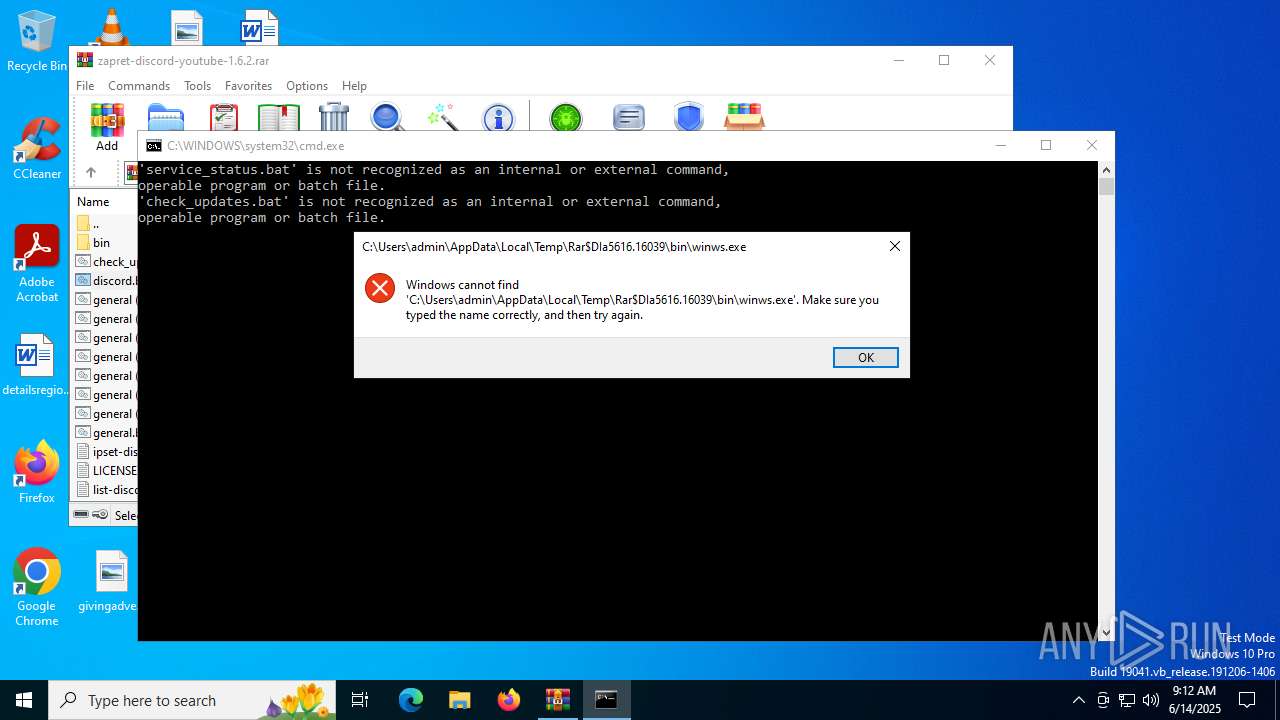
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 5616)
- cmd.exe (PID: 4916)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 5616)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5616)
Starts application with an unusual extension
- cmd.exe (PID: 3964)
- cmd.exe (PID: 4196)
- cmd.exe (PID: 4916)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 5616)
Application launched itself
- cmd.exe (PID: 4916)
Starts SC.EXE for service management
- cmd.exe (PID: 7124)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6892)
- cmd.exe (PID: 2028)
Windows service management via SC.EXE
- sc.exe (PID: 4800)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7124)
Hides command output
- cmd.exe (PID: 2028)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 5616)
Checks supported languages
- chcp.com (PID: 2044)
- chcp.com (PID: 7056)
- chcp.com (PID: 3876)
- chcp.com (PID: 4664)
- chcp.com (PID: 1148)
- winws.exe (PID: 5904)
Changes the display of characters in the console
- cmd.exe (PID: 3964)
- cmd.exe (PID: 4196)
- cmd.exe (PID: 4916)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5616)
Manual execution by a user
- cmd.exe (PID: 4916)
Checks proxy server information
- powershell.exe (PID: 6148)
Disables trace logs
- powershell.exe (PID: 6148)
Reads the computer name
- winws.exe (PID: 5904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 412 |
| UncompressedSize: | 896 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | general (ALT).bat |
Total processes
163
Monitored processes
26
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1148 | chcp 437 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2028 | C:\WINDOWS\system32\cmd.exe /c powershell -command "(Invoke-WebRequest -Uri https://raw.githubusercontent.com/Flowseal/zapret-discord-youtube/refs/heads/main/.service/version.txt -Headers @{\"Cache-Control\"=\"no-cache\"} -TimeoutSec 5).Content" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2044 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2804 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2980 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3196 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
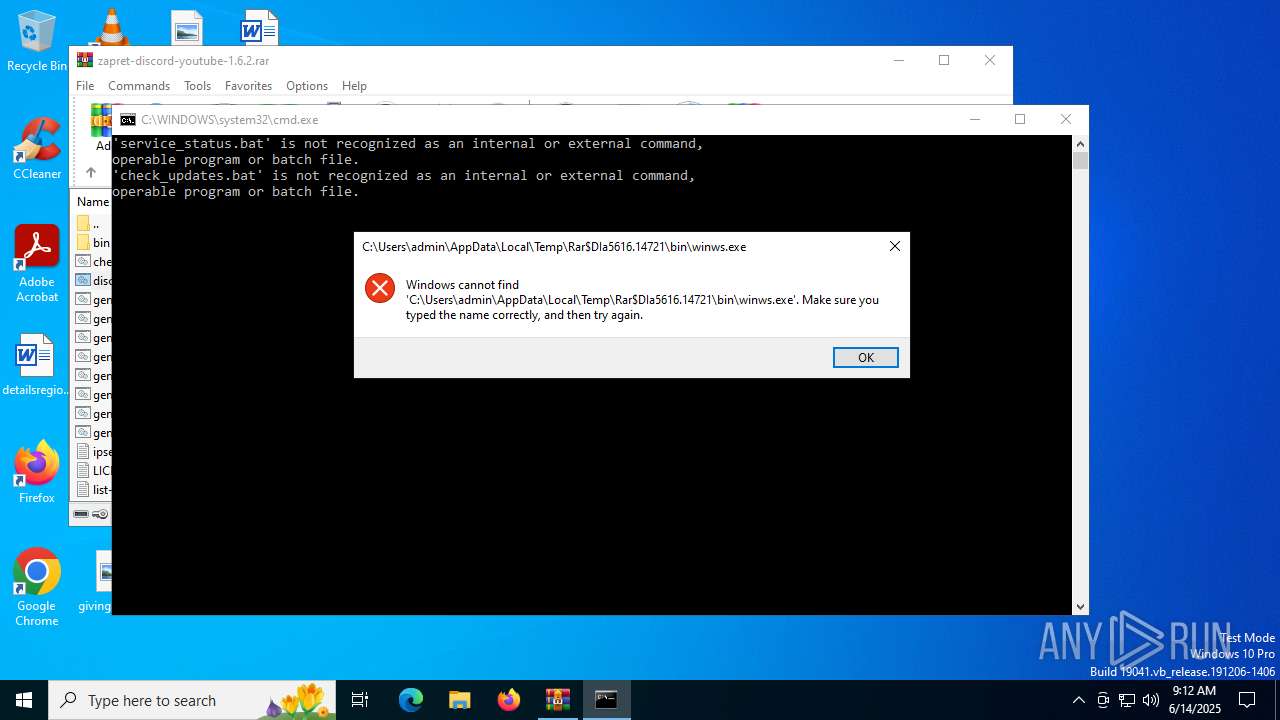
| 3480 | "C:\Users\admin\Desktop\fdgfdg\bin\winws.exe" --wf-tcp=443 --wf-udp=443,50000-50100 --filter-udp=443 --hostlist="list-discord.txt" --dpi-desync=fake --dpi-desync-repeats=6 --dpi-desync-fake-quic="C:\Users\admin\Desktop\fdgfdg\bin\quic_initial_www_google_com.bin" --new --filter-udp=50000-50100 --ipset="ipset-discord.txt" --dpi-desync=fake --dpi-desync-any-protocol --dpi-desync-cutoff=d3 --dpi-desync-repeats=6 --new --filter-tcp=443 --hostlist="list-discord.txt" --dpi-desync=fake,split --dpi-desync-autottl=2 --dpi-desync-repeats=6 --dpi-desync-fooling=badseq --dpi-desync-fake-tls="C:\Users\admin\Desktop\fdgfdg\bin\tls_clienthello_www_google_com.bin" | C:\Users\admin\Desktop\fdgfdg\bin\winws.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3620 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winws.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3756 | powershell -command "[datetime]::Now.ToString('yyyy-MM-dd HH:mm:ss')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
16 004
Read events
15 967
Write events
24
Delete events
13
Modification events
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\zapret-discord-youtube-1.6.2.rar | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
3
Text files
25
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa5616.14721\discord.bat | text | |
MD5:EBF82AEABAB4E1D541DD6103186B7FA2 | SHA256:356D30EEBA3E1276FA40A49F3253B661519B18405FFF3068E124558AAB10FFD3 | |||
| 5616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa5616.16039\discord.bat | text | |
MD5:EBF82AEABAB4E1D541DD6103186B7FA2 | SHA256:356D30EEBA3E1276FA40A49F3253B661519B18405FFF3068E124558AAB10FFD3 | |||
| 5616 | WinRAR.exe | C:\Users\admin\Desktop\fdgfdg\LICENSE.txt | text | |
MD5:F05293DFD349AF032AF60C2967254D8F | SHA256:20F43BDBA649F9F0276BB6F63CB3FC8D85D9FA1B18DEDA8462CE65B32E6C90B0 | |||
| 5616 | WinRAR.exe | C:\Users\admin\Desktop\fdgfdg\general (ALT4).bat | text | |
MD5:23A14A9B766D996F8358320714FCD178 | SHA256:EF95EFB9729E30796012633CA00EE80ABD85E4FF0ABBF3500B65FC1425FA688D | |||
| 5616 | WinRAR.exe | C:\Users\admin\Desktop\fdgfdg\general.bat | text | |
MD5:9F677A817AFEC358B8A77CF4024ACF54 | SHA256:3603C27734B3DBD02B695FD10CA9D2F9CB2505983D4A17EEE60E0CE1A3D71818 | |||
| 5616 | WinRAR.exe | C:\Users\admin\Desktop\fdgfdg\general (МГТС).bat | text | |
MD5:2A5363D20832A82D6BD5EE7DB2ADBDF6 | SHA256:7F25EEA3B79A0A712E52D927158A671A4A5511EC2C93AE75A89AF98E048DE1B8 | |||
| 5616 | WinRAR.exe | C:\Users\admin\Desktop\fdgfdg\general (МГТС2).bat | text | |
MD5:F559732BBBBD1124BFDDCD9FB0F0E009 | SHA256:E338F10142F4A1653D751E2F66CC0D82354D1ACC1302E33EC5E27D23E18A4E82 | |||
| 5616 | WinRAR.exe | C:\Users\admin\Desktop\fdgfdg\general (ALT).bat | text | |
MD5:B4103E2394E1FA4EF5AFE39F58560AEB | SHA256:2C6DCFEACB31B908A4A7EB67AB1F787F7FEB77E920AEC58C4830FB00E34B0D03 | |||
| 5616 | WinRAR.exe | C:\Users\admin\Desktop\fdgfdg\general (ALT2).bat | text | |
MD5:FE32BC53254B5603A1DA4EB4E93B6D55 | SHA256:98ED9781ABE72ABF3BFEFA66B7B633EE6FBCDEA173F290B9FA7A3B73E8A5D777 | |||
| 5616 | WinRAR.exe | C:\Users\admin\Desktop\fdgfdg\general (ALT3).bat | text | |
MD5:63075028AEF8BEB04FD54286700A75CF | SHA256:CDD4936D6CE4D5C59777C4758D427393EBD68835BE6EDB4C1762C87905CF30F3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
25
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2552 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6776 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6776 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3800 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2552 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2552 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |