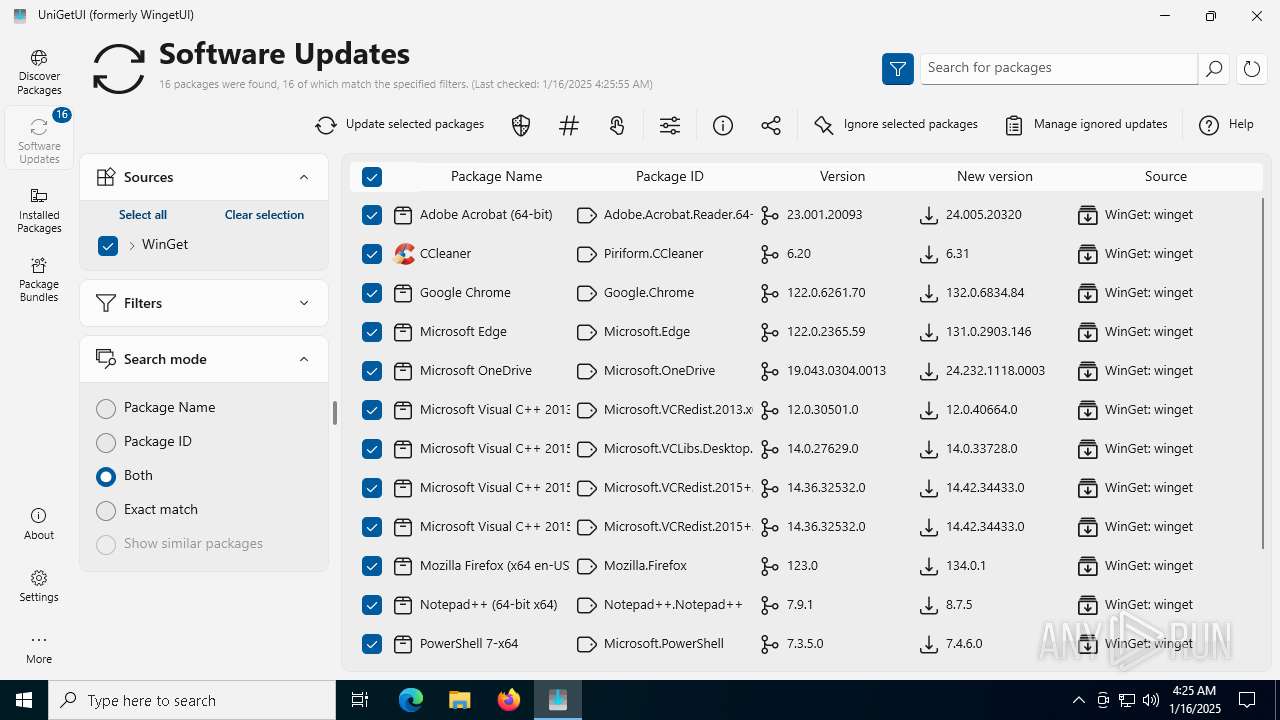
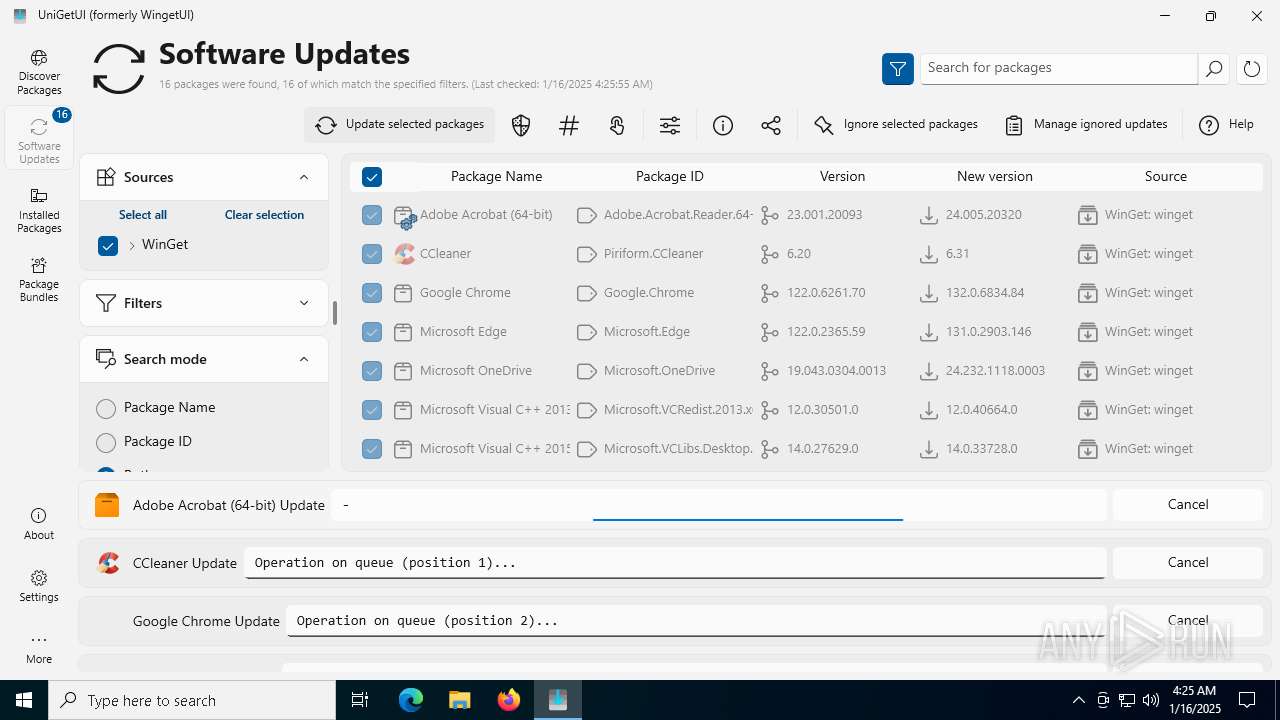
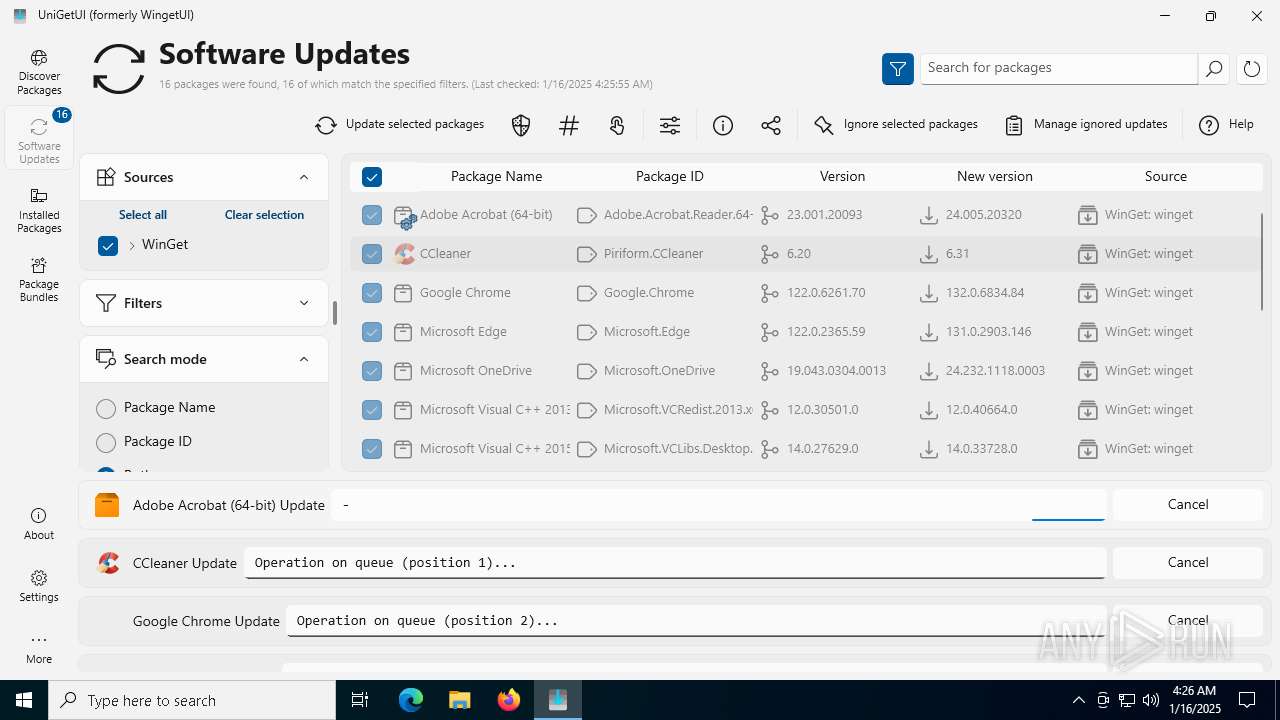
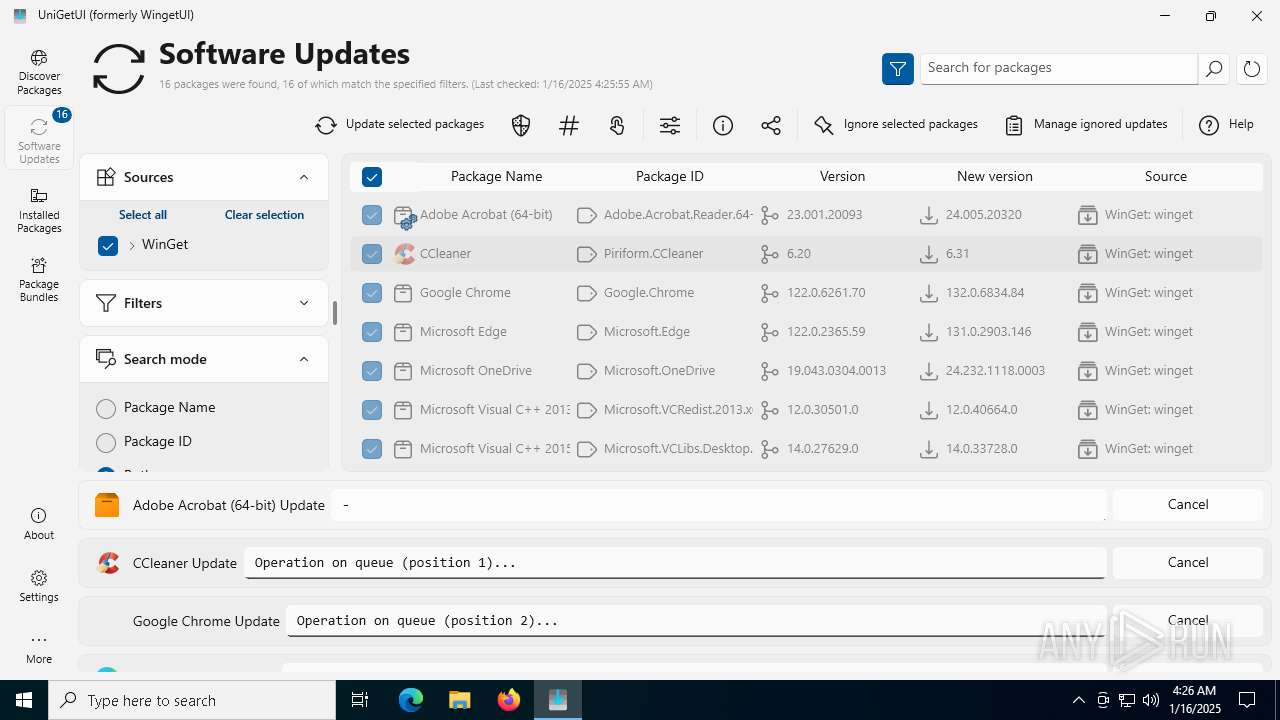
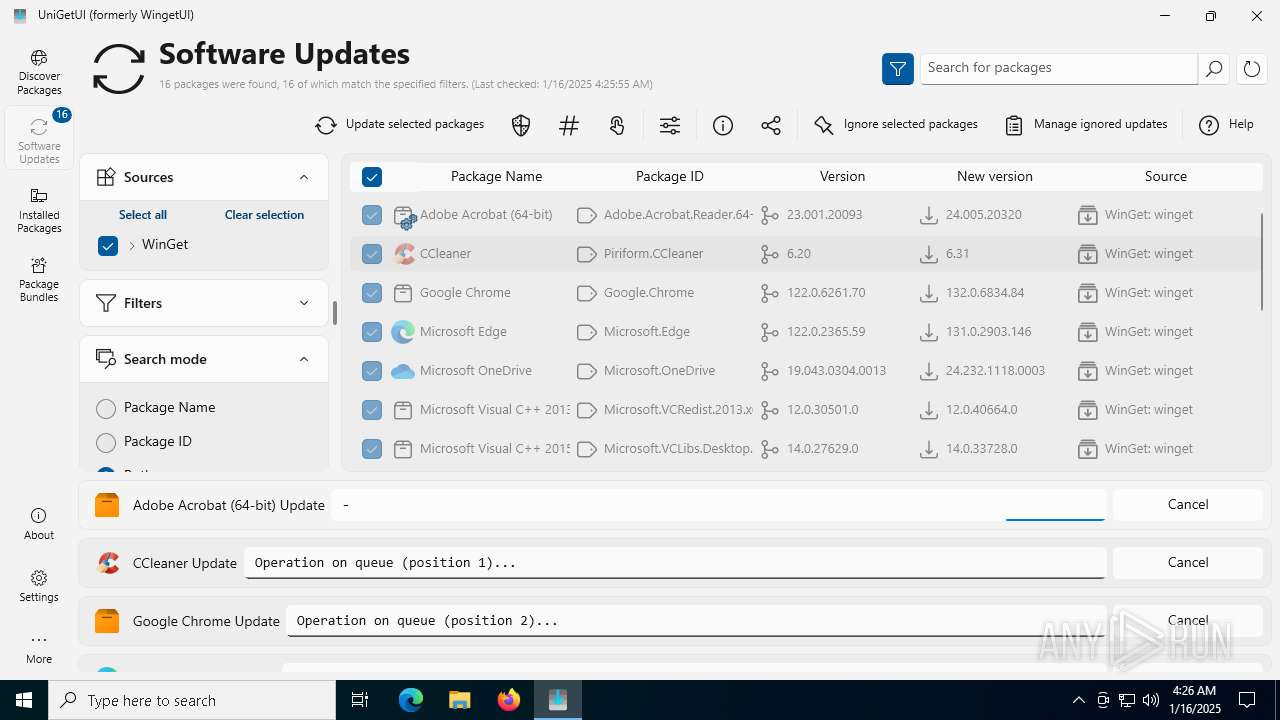
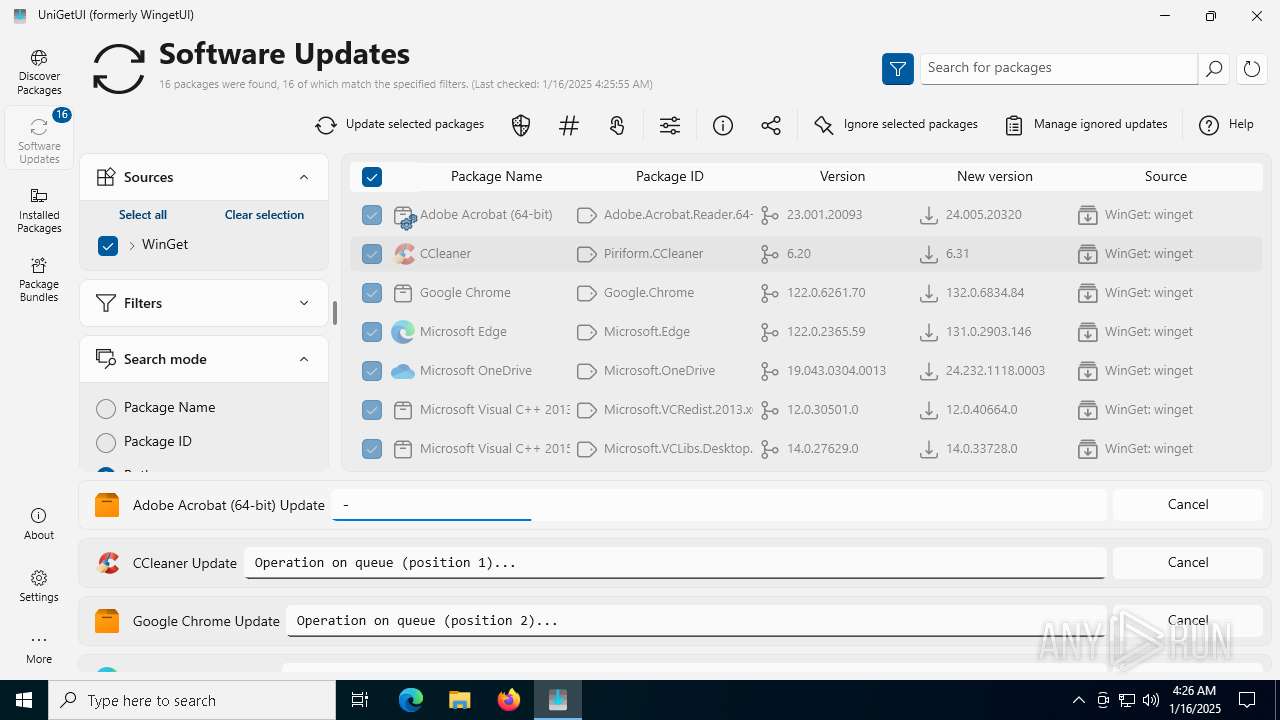
| URL: | https://github.com/marticliment/UniGetUI/releases/download/3.1.5/UniGetUI.Installer.exe |
| Full analysis: | https://app.any.run/tasks/3a7e8253-528a-42a0-bd81-689f642efe90 |
| Verdict: | Malicious activity |
| Analysis date: | January 16, 2025, 04:21:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E54A989543C989A52C5C6D4946CDDC82 |
| SHA1: | DAE4F870B48F58168092CB3C9A987D180BBD15B6 |
| SHA256: | 7949E86ADB91757F7C13A2FA1C927A15D03795F366E6CCF3D4A3803B7143805D |
| SSDEEP: | 3:N8tEd4uiIuRr8wDdkCWgsLMiARwbWigXLNn:2uuwuRr8ud4gq8RCgXLN |
MALICIOUS
Changes the autorun value in the registry
- UniGetUI.Installer.tmp (PID: 5588)
Bypass execution policy to execute commands
- powershell.exe (PID: 6692)
- powershell.exe (PID: 3688)
Changes powershell execution policy (Bypass)
- UniGetUI.Installer.tmp (PID: 5588)
- UniGetUI.exe (PID: 6560)
SUSPICIOUS
Executable content was dropped or overwritten
- UniGetUI.Installer.exe (PID: 5028)
- UniGetUI.Installer.tmp (PID: 5588)
- MicrosoftEdgeWebview2Setup.exe (PID: 4764)
- MicrosoftEdgeUpdate.exe (PID: 5460)
- MicrosoftEdgeWebview_X64_131.0.2903.146.exe (PID: 7940)
- setup.exe (PID: 6376)
- csc.exe (PID: 7844)
- csc.exe (PID: 5980)
- csc.exe (PID: 2392)
Reads the Windows owner or organization settings
- UniGetUI.Installer.tmp (PID: 5588)
Reads security settings of Internet Explorer
- UniGetUI.Installer.tmp (PID: 5588)
- MicrosoftEdgeUpdate.exe (PID: 5460)
- MicrosoftEdgeUpdate.exe (PID: 7728)
- UniGetUI.exe (PID: 6560)
- winget.exe (PID: 6980)
- winget.exe (PID: 6468)
- winget.exe (PID: 1684)
- winget.exe (PID: 6420)
Process drops legitimate windows executable
- MicrosoftEdgeWebview2Setup.exe (PID: 4764)
- MicrosoftEdgeUpdate.exe (PID: 5460)
- setup.exe (PID: 6376)
- MicrosoftEdgeWebview_X64_131.0.2903.146.exe (PID: 7940)
- UniGetUI.Installer.tmp (PID: 5588)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 4764)
- MicrosoftEdgeUpdate.exe (PID: 5460)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 5460)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdate.exe (PID: 5032)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7232)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7568)
Checks Windows Trust Settings
- MicrosoftEdgeUpdate.exe (PID: 7728)
- winget.exe (PID: 6468)
- winget.exe (PID: 1684)
- winget.exe (PID: 6420)
Application launched itself
- setup.exe (PID: 6376)
- MicrosoftEdgeUpdate.exe (PID: 7728)
Uses TASKKILL.EXE to kill process
- UniGetUI.Installer.tmp (PID: 5588)
Drops 7-zip archiver for unpacking
- UniGetUI.Installer.tmp (PID: 5588)
Creates file in the systems drive root
- explorer.exe (PID: 4488)
Starts POWERSHELL.EXE for commands execution
- UniGetUI.Installer.tmp (PID: 5588)
- UniGetUI.exe (PID: 6560)
The process executes Powershell scripts
- UniGetUI.Installer.tmp (PID: 5588)
The process hide an interactive prompt from the user
- UniGetUI.Installer.tmp (PID: 5588)
Starts application with an unusual extension
- UniGetUI.exe (PID: 6560)
The process bypasses the loading of PowerShell profile settings
- UniGetUI.exe (PID: 6560)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 3416)
- powershell.exe (PID: 7000)
- powershell.exe (PID: 6764)
CSC.EXE is used to compile C# code
- csc.exe (PID: 7844)
- csc.exe (PID: 5980)
- csc.exe (PID: 2392)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 3416)
- powershell.exe (PID: 7000)
- powershell.exe (PID: 6764)
Searches for installed software
- winget.exe (PID: 6468)
- winget.exe (PID: 1684)
- winget.exe (PID: 6420)
INFO
Application launched itself
- firefox.exe (PID: 5916)
- firefox.exe (PID: 3612)
Executable content was dropped or overwritten
- firefox.exe (PID: 3612)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4488)
Creates files or folders in the user directory
- explorer.exe (PID: 4488)
- MicrosoftEdgeUpdate.exe (PID: 5460)
- MicrosoftEdgeWebview_X64_131.0.2903.146.exe (PID: 7940)
- setup.exe (PID: 6376)
- setup.exe (PID: 6356)
- UniGetUI.Installer.tmp (PID: 5588)
- UniGetUI.exe (PID: 6560)
- choco.exe (PID: 6276)
- winget.exe (PID: 6468)
- winget.exe (PID: 6420)
The process uses the downloaded file
- firefox.exe (PID: 3612)
- explorer.exe (PID: 4488)
- UniGetUI.Installer.tmp (PID: 5588)
- powershell.exe (PID: 3416)
- pwsh.exe (PID: 4580)
- pwsh.exe (PID: 6780)
- pwsh.exe (PID: 6720)
- powershell.exe (PID: 7000)
Checks proxy server information
- explorer.exe (PID: 4488)
- UniGetUI.Installer.tmp (PID: 5588)
- MicrosoftEdgeUpdate.exe (PID: 7064)
- powershell.exe (PID: 3416)
- winget.exe (PID: 6980)
- winget.exe (PID: 6468)
- powershell.exe (PID: 7000)
- powershell.exe (PID: 6764)
- winget.exe (PID: 1684)
- winget.exe (PID: 6420)
Checks supported languages
- UniGetUI.Installer.tmp (PID: 5588)
- UniGetUI.Installer.exe (PID: 5028)
- MicrosoftEdgeWebview2Setup.exe (PID: 4764)
- MicrosoftEdgeUpdate.exe (PID: 5460)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6544)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7232)
- MicrosoftEdgeUpdate.exe (PID: 7064)
- MicrosoftEdgeUpdate.exe (PID: 7880)
- MicrosoftEdgeUpdate.exe (PID: 5032)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7568)
- setup.exe (PID: 6376)
- setup.exe (PID: 6356)
- MicrosoftEdgeUpdate.exe (PID: 7728)
- MicrosoftEdgeUpdate.exe (PID: 8036)
- UniGetUI.exe (PID: 6560)
- chcp.com (PID: 6600)
- UniGetUI.exe (PID: 5628)
- winget.exe (PID: 1544)
- pwsh.exe (PID: 1616)
- winget.exe (PID: 4592)
- pwsh.exe (PID: 4580)
- choco.exe (PID: 6276)
- csc.exe (PID: 7844)
- cvtres.exe (PID: 7756)
- choco.exe (PID: 6824)
- winget.exe (PID: 6468)
- pwsh.exe (PID: 6720)
- pwsh.exe (PID: 6780)
- choco.exe (PID: 7524)
- csc.exe (PID: 5980)
- cvtres.exe (PID: 1412)
- csc.exe (PID: 2392)
- winget.exe (PID: 1684)
- winget.exe (PID: 6420)
Reads the software policy settings
- explorer.exe (PID: 4488)
- UniGetUI.Installer.tmp (PID: 5588)
- MicrosoftEdgeUpdate.exe (PID: 7064)
- MicrosoftEdgeUpdate.exe (PID: 7728)
- winget.exe (PID: 6468)
- winget.exe (PID: 6980)
- winget.exe (PID: 1684)
- winget.exe (PID: 6420)
Create files in a temporary directory
- UniGetUI.Installer.exe (PID: 5028)
- UniGetUI.Installer.tmp (PID: 5588)
- MicrosoftEdgeWebview2Setup.exe (PID: 4764)
- MicrosoftEdgeUpdate.exe (PID: 5460)
- winget.exe (PID: 1544)
- winget.exe (PID: 4592)
- csc.exe (PID: 7844)
- winget.exe (PID: 6468)
- winget.exe (PID: 6980)
- winget.exe (PID: 1684)
- csc.exe (PID: 5980)
- winget.exe (PID: 6420)
Reads the computer name
- UniGetUI.Installer.tmp (PID: 5588)
- MicrosoftEdgeUpdate.exe (PID: 5460)
- MicrosoftEdgeUpdate.exe (PID: 7064)
- MicrosoftEdgeUpdate.exe (PID: 5032)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7568)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 7232)
- setup.exe (PID: 6376)
- MicrosoftEdgeUpdate.exe (PID: 8036)
- UniGetUI.exe (PID: 5628)
- UniGetUI.exe (PID: 6560)
- choco.exe (PID: 6276)
- pwsh.exe (PID: 1616)
- winget.exe (PID: 4592)
- choco.exe (PID: 4056)
- choco.exe (PID: 6824)
- choco.exe (PID: 7524)
- winget.exe (PID: 6420)
The sample compiled with english language support
- MicrosoftEdgeWebview2Setup.exe (PID: 4764)
- MicrosoftEdgeUpdate.exe (PID: 5460)
- setup.exe (PID: 6376)
- MicrosoftEdgeWebview_X64_131.0.2903.146.exe (PID: 7940)
- UniGetUI.Installer.tmp (PID: 5588)
Process checks computer location settings
- UniGetUI.Installer.tmp (PID: 5588)
- MicrosoftEdgeUpdate.exe (PID: 5460)
- setup.exe (PID: 6376)
- UniGetUI.exe (PID: 6560)
- pwsh.exe (PID: 4580)
- pwsh.exe (PID: 6780)
- winget.exe (PID: 1684)
- winget.exe (PID: 6468)
- winget.exe (PID: 6420)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 7064)
- choco.exe (PID: 4056)
- choco.exe (PID: 7524)
Reads the machine GUID from the registry
- MicrosoftEdgeUpdate.exe (PID: 7728)
- choco.exe (PID: 6276)
- csc.exe (PID: 7844)
- choco.exe (PID: 4056)
- choco.exe (PID: 7524)
- winget.exe (PID: 6468)
- choco.exe (PID: 6824)
- csc.exe (PID: 5980)
- csc.exe (PID: 2392)
- winget.exe (PID: 1684)
- winget.exe (PID: 6420)
The sample compiled with Indonesian language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with arabic language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with bulgarian language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with czech language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with german language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with spanish language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with french language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with japanese language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with Italian language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with turkish language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with portuguese language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with russian language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with slovak language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with swedish language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with chinese language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with korean language support
- UniGetUI.Installer.tmp (PID: 5588)
The sample compiled with polish language support
- UniGetUI.Installer.tmp (PID: 5588)
Creates files in the program directory
- UniGetUI.exe (PID: 5628)
Changes the display of characters in the console
- UniGetUI.exe (PID: 6560)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3688)
Disables trace logs
- powershell.exe (PID: 3416)
- choco.exe (PID: 6824)
- powershell.exe (PID: 6764)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6764)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
237
Monitored processes
106
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winget.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 880 | "C:\WINDOWS\system32\where.exe" python.exe | C:\Windows\System32\where.exe | — | UniGetUI.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Where - Lists location of files Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1304 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | where.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | winget.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1412 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES5091.tmp" "c:\Users\admin\AppData\Local\Temp\CSC6EC00132270E4386AB835013673CD8AF.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 | ||||
| 1544 | "C:\Users\admin\AppData\Local\Programs\UniGetUI\winget-cli_x64\winget.exe" --version | C:\Users\admin\AppData\Local\Programs\UniGetUI\winget-cli_x64\winget.exe | — | UniGetUI.exe |
User: admin Integrity Level: MEDIUM Exit code: 0 | ||||
| 1616 | "C:\Program Files\PowerShell\7\pwsh.exe" -Version | C:\Program Files\PowerShell\7\pwsh.exe | — | UniGetUI.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: pwsh Exit code: 0 Version: 7.3.5.500 | ||||
| 1684 | "C:\Users\admin\AppData\Local\Programs\UniGetUI\winget-cli_x64\winget.exe" update --include-unknown --accept-source-agreements | C:\Users\admin\AppData\Local\Programs\UniGetUI\winget-cli_x64\winget.exe | UniGetUI.exe | |
User: admin Integrity Level: MEDIUM Exit code: 0 | ||||
| 1828 | "C:\WINDOWS\system32\where.exe" vcpkg | C:\Windows\System32\where.exe | — | UniGetUI.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Where - Lists location of files Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1868 | "C:\WINDOWS\system32\where.exe" dotnet.exe | C:\Windows\System32\where.exe | — | UniGetUI.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Where - Lists location of files Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
Total events
107 723
Read events
106 210
Write events
1 434
Delete events
79
Modification events
| (PID) Process: | (3612) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000801FE |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456A48A294F7A40804AB924005FF030B61F | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppBadgeUpdated |
| Operation: | write | Name: | 308046B0AF4A39CB |
Value: 21 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppLaunch |
| Operation: | write | Name: | Microsoft.Windows.Explorer |
Value: 51 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 5B89886700000000 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | MinimizedStateTabletModeOff |
Value: 0 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Ribbon |
| Operation: | write | Name: | QatItems |
Value: 3C7369713A637573746F6D554920786D6C6E733A7369713D22687474703A2F2F736368656D61732E6D6963726F736F66742E636F6D2F77696E646F77732F323030392F726962626F6E2F716174223E3C7369713A726962626F6E206D696E696D697A65643D2266616C7365223E3C7369713A71617420706F736974696F6E3D2230223E3C7369713A736861726564436F6E74726F6C733E3C7369713A636F6E74726F6C206964513D227369713A3136313238222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3136313239222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333532222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333834222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333336222076697369626C653D22747275652220617267756D656E743D223022202F3E3C7369713A636F6E74726F6C206964513D227369713A3132333537222076697369626C653D2266616C73652220617267756D656E743D223022202F3E3C2F7369713A736861726564436F6E74726F6C733E3C2F7369713A7161743E3C2F7369713A726962626F6E3E3C2F7369713A637573746F6D55493E | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar\ShellBrowser |
| Operation: | write | Name: | ITBar7Layout |
Value: 13000000000000000000000020000000100000000000000001000000010700005E01000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (4488) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 03000000040000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
Executable files
1 245
Suspicious files
449
Text files
471
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3612 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | binary | |
MD5:C78F36BF78A74A5C37232FA18305FA6E | SHA256:319C730AC6614FDCE611894E281CBE1B5E1A304DCD812D6B642D3BE978E82EEC | |||
| 3612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db-journal | binary | |
MD5:E2C22D46B09C26C62642E1C2EF232793 | SHA256:49433E1F3A4B3EA5CE5AED0ECE828D27820214E7247EE570C69D1948AB47A55C | |||
| 3612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db | binary | |
MD5:E819CC6C5FE7B1C819E92D417EC6EC5B | SHA256:73C46F6410CC390F6FA9CAA88E2239DFB80E171FA1626BDE6BC598EFF736E060 | |||
| 3612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\protections.sqlite-journal | binary | |
MD5:D4D62CAD8525070F65FD41ABB593B2E3 | SHA256:79E6459008988665166DAC352F295B5495038C4F10891A0BC1EE85E98B5F1793 | |||
| 3612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 3612 | firefox.exe | C:\Users\admin\Downloads\UniGetUI.7syBiMLG.Installer.exe.part | — | |
MD5:— | SHA256:— | |||
| 3612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
113
DNS requests
126
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6068 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6068 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3612 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
3612 | firefox.exe | POST | — | 142.250.185.195:80 | http://o.pki.goog/s/wr3/3cs | unknown | — | — | whitelisted |
3612 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
3612 | firefox.exe | POST | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
3612 | firefox.exe | POST | 200 | 142.250.185.195:80 | http://o.pki.goog/s/wr3/jLM | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6068 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6068 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
github.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image Sharing Service (imgur.com) |
6560 | UniGetUI.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |