| File name: | 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe |
| Full analysis: | https://app.any.run/tasks/a5f8fc42-0923-4d41-9426-924afdce7b63 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 09:32:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 2A3D5E4C47FD8A78B3FCEBE4800D1E15 |
| SHA1: | 7BBB6F2129A834EC61B1BAAB56B0C7FA7191E692 |
| SHA256: | 79446EE8304FF1EEF2CEEF72969C415D51C446B852AEFD0DA1EA70534590C811 |
| SSDEEP: | 98304:A3nKq3/TyZCBBWdEeUYNNJisHvyG9W3nKq3/TyZCBBWdEeUYNNJisHvyU9AD2kEv:Gq |
MALICIOUS
No malicious indicators.SUSPICIOUS
ADVANCEDINSTALLER mutex has been found
- 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe (PID: 6392)
Process drops legitimate windows executable
- 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe (PID: 6392)
Reads the Windows owner or organization settings
- 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe (PID: 6392)
Executable content was dropped or overwritten
- 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe (PID: 6392)
Detects AdvancedInstaller (YARA)
- 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe (PID: 6392)
There is functionality for taking screenshot (YARA)
- 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe (PID: 6392)
INFO
Reads the computer name
- 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe (PID: 6392)
- msiexec.exe (PID: 4896)
- msiexec.exe (PID: 5528)
Checks supported languages
- 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe (PID: 6392)
- msiexec.exe (PID: 4896)
- msiexec.exe (PID: 5528)
The sample compiled with english language support
- 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe (PID: 6392)
Reads Environment values
- 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe (PID: 6392)
- msiexec.exe (PID: 5528)
Create files in a temporary directory
- 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe (PID: 6392)
Creates files or folders in the user directory
- 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe (PID: 6392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (3.6) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (1.6) |
| .exe | | | DOS Executable Generic (1.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:03:23 09:36:36+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 1132032 |
| InitializedDataSize: | 648192 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xd2ba3 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.0.0.0 |
| ProductVersionNumber: | 5.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | SecurityXploded |
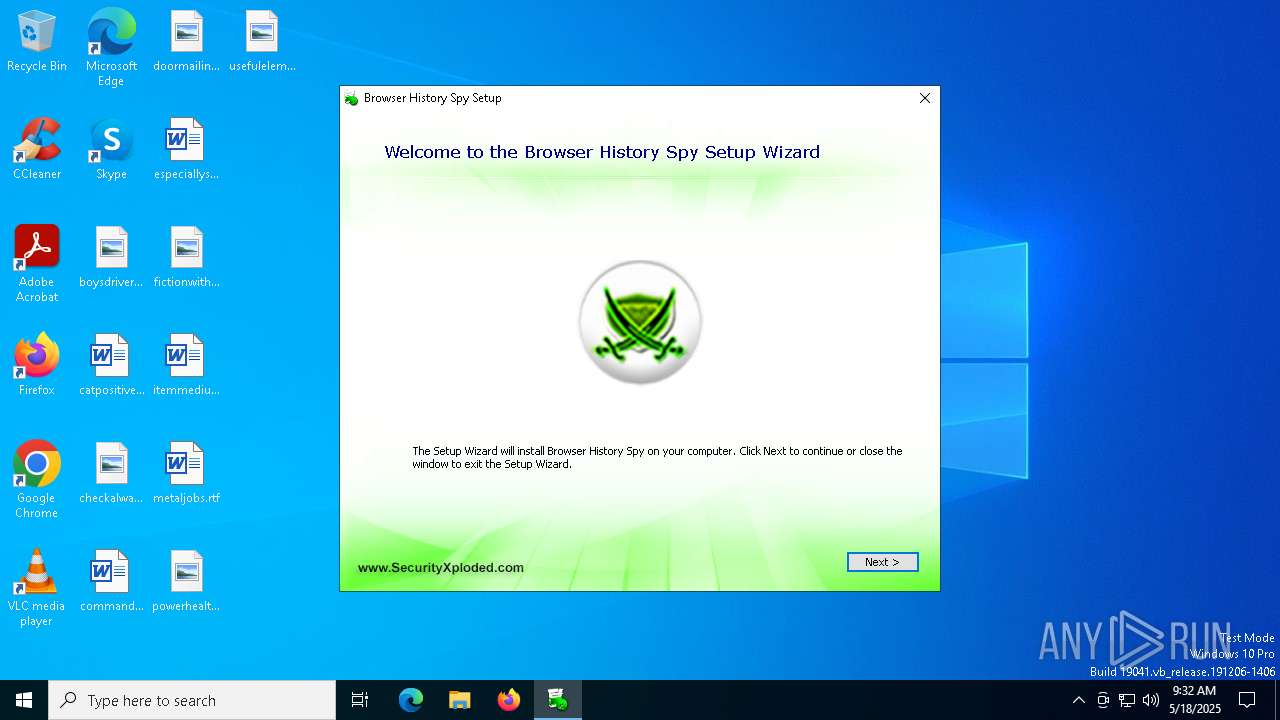
| FileDescription: | This installer database contains the logic and data required to install Browser History Spy. |
| FileVersion: | 5 |
| InternalName: | Setup_BrowserHistorySpy |
| LegalCopyright: | Copyright (C) 2017 SecurityXploded |
| OriginalFileName: | Setup_BrowserHistorySpy.exe |
| ProductName: | Browser History Spy |
| ProductVersion: | 5 |
Total processes
131
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4896 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5528 | C:\Windows\syswow64\MsiExec.exe -Embedding 1DF95150680253C01AF5787D75B80693 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6148 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6392 | "C:\Users\admin\AppData\Local\Temp\79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe" | C:\Users\admin\AppData\Local\Temp\79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe | explorer.exe | ||||||||||||
User: admin Company: SecurityXploded Integrity Level: MEDIUM Description: This installer database contains the logic and data required to install Browser History Spy. Version: 5.0 Modules
| |||||||||||||||
Total events
318
Read events
318
Write events
0
Delete events
0
Modification events
Executable files
12
Suspicious files
2
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6392 | 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe | C:\Users\admin\AppData\Roaming\SecurityXploded\Browser History Spy 5.0\install\BrowserHistorySpy.aiui | executable | |
MD5:9DEEAAD4B9C12FE5EFD1C7EC92AF853B | SHA256:6A01E17EFE49A869E4E76963E941AB1844C2C469F2B1018FA8F54754215F3A52 | |||
| 6392 | 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe | C:\Users\admin\AppData\Local\Temp\MSICAE5.tmp | executable | |
MD5:CA367C9FD5FB936729B4B6DCD78B003A | SHA256:287610819C64C5C5D0DA75C8691046CFFAA4538DD5F4CCDD14997B804D34F705 | |||
| 6392 | 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe | C:\Users\admin\AppData\Roaming\SecurityXploded\Browser History Spy 5.0\install\holder0.aiph | binary | |
MD5:F462C07581393BF29DA7D1B10A7F31E4 | SHA256:5636933327B0B777F50E20A2DC29786B6F58003D7981728C487DF4CBFA59DEDC | |||
| 6392 | 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe | C:\Users\admin\AppData\Roaming\SecurityXploded\Browser History Spy 5.0\install\BrowserHistorySpy.msi | executable | |
MD5:27CECA33CA9FC96ECFC5F2BFED7509C7 | SHA256:D88BF0CC4CD378B039276B7D65F612120488994F35010C244791DC7446843657 | |||
| 6392 | 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_6392\installer_minbackground.jpg | image | |
MD5:4803AF8D5739D1983939214F3F1DE420 | SHA256:A943EDF18CB701EDD53E42CBE13D6E70111897874F11DD7FE505262482BB1CBE | |||
| 6392 | 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe | C:\Users\admin\AppData\Local\Temp\shiBD08.tmp | executable | |
MD5:CE85F5D941EBCA72DA2A55835B303EB9 | SHA256:6CF60B8101CBB475F3803E18617172CC180AFA4BC0CA8CA261C2AB6ED1C93EA1 | |||
| 6392 | 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe | C:\Users\admin\AppData\Local\Temp\MSICAF6.tmp | executable | |
MD5:CA367C9FD5FB936729B4B6DCD78B003A | SHA256:287610819C64C5C5D0DA75C8691046CFFAA4538DD5F4CCDD14997B804D34F705 | |||
| 6392 | 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_6392\New | image | |
MD5:C23CBF002D82192481B61ED7EC0890F4 | SHA256:4F92E804A11453382EBFF7FB0958879BAE88FE3366306911DEC9D811CD306EED | |||
| 6392 | 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_6392\waitlogoicon | image | |
MD5:5C95ADF9CBC1231E805DE8529778E1C4 | SHA256:81873D1DB5399D8B42A371FD0BFCEB4FF9F4E21446E9B180245055CCBDCC1235 | |||
| 6392 | 79446ee8304ff1eef2ceef72969c415d51c446b852aefd0da1ea70534590c811.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_6392\info | image | |
MD5:FD535E63F539EACB3F11D03B52B39A80 | SHA256:0086BC01150989F553A0A4AE0E14926C6E247CEDDA312E1F946AE35D575742AB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
20
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4756 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4756 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |