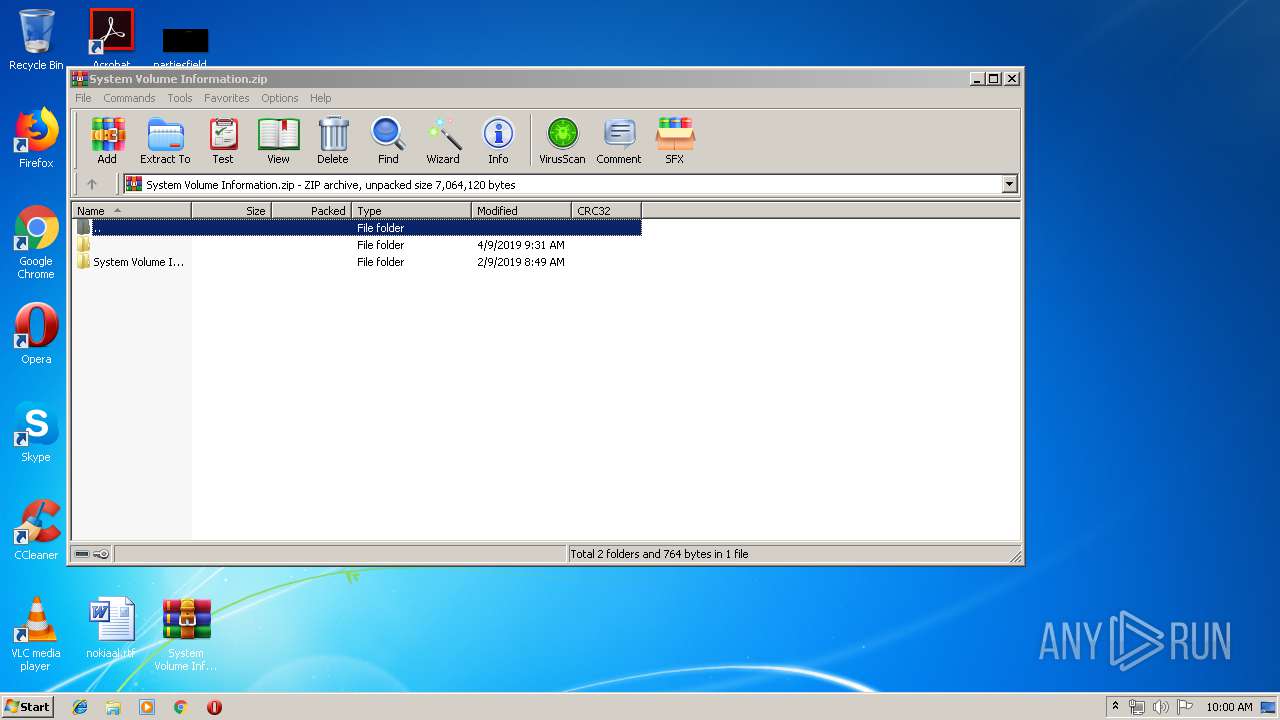
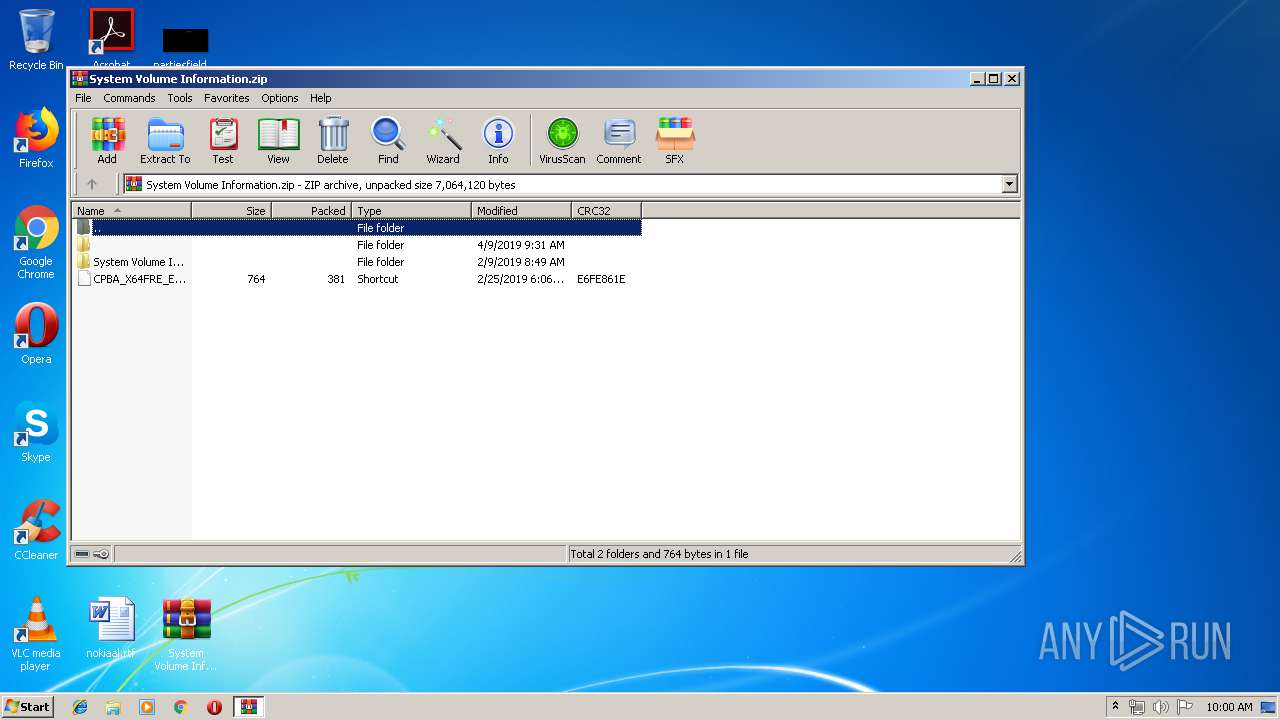
| File name: | System Volume Information.zip |
| Full analysis: | https://app.any.run/tasks/2f367426-d02d-4297-8ebc-b3df4362a792 |
| Verdict: | Malicious activity |
| Analysis date: | April 09, 2019, 09:00:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 586EF57542A3CB761009DB36CB1796B1 |
| SHA1: | CBF3FF34B71CF62115AA5B53E1AEDEF4DD7E5167 |
| SHA256: | 793837D84196D916323588A2F7088B384C34E83CBF1E4CFA37BBDEB537F7A37F |
| SSDEEP: | 98304:QagnCTK1EjQOnYpnBTAFtcdl6Gzu8N/QRvsKiftVF2hMv0W0mRFuiMjDSnb66v:QjnCTk2QTq7GzdQ9sHX2hVmRFwSb6O |
MALICIOUS
Loads dropped or rewritten executable
- rundll32.exe (PID: 3544)
Changes the autorun value in the registry
- msiexec.exe (PID: 2888)
SUSPICIOUS
Writes to a desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 3968)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3968)
Creates files in the user directory
- rundll32.exe (PID: 3544)
Starts application with an unusual extension
- rundll32.exe (PID: 3544)
Creates files in the program directory
- msiexec.exe (PID: 2888)
Starts Microsoft Office Application
- explorer.exe (PID: 2056)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 868)
- WINWORD.EXE (PID: 664)
Creates files in the user directory
- WINWORD.EXE (PID: 664)
- WINWORD.EXE (PID: 868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:02:09 13:19:09 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | System Volume Information/ |
Total processes
44
Monitored processes
9
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
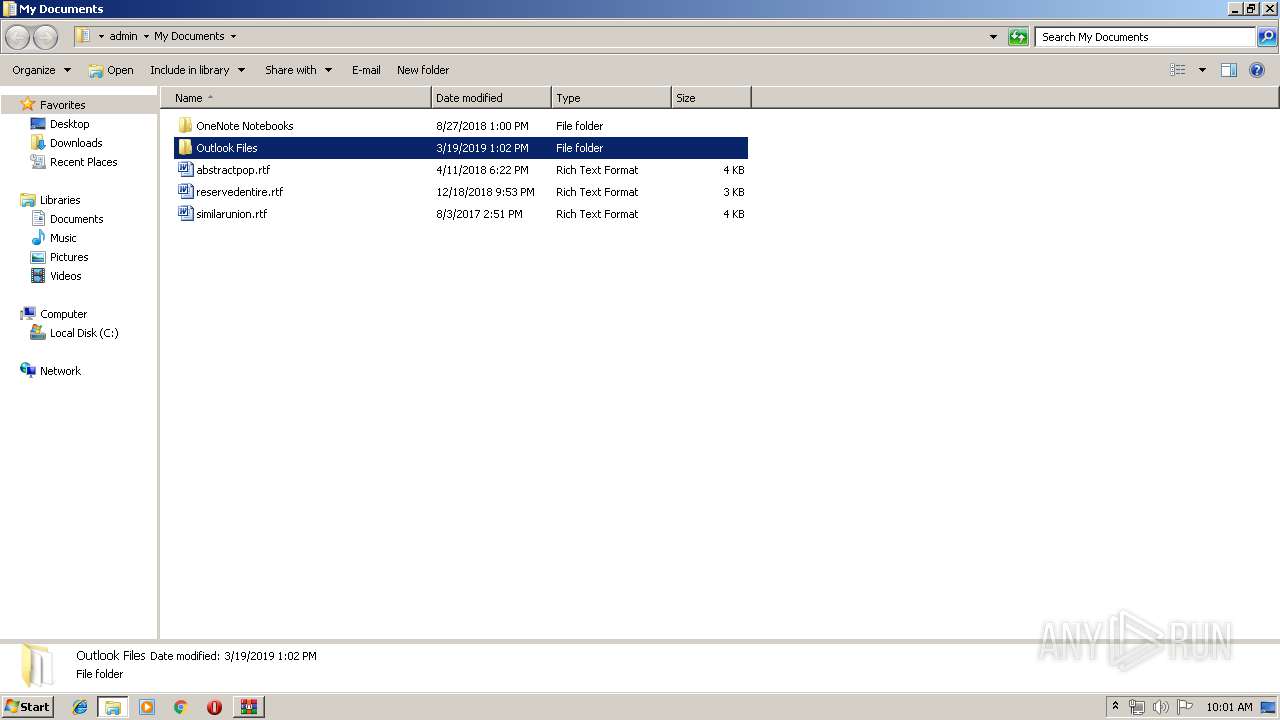
| 664 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Documents\similarunion.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
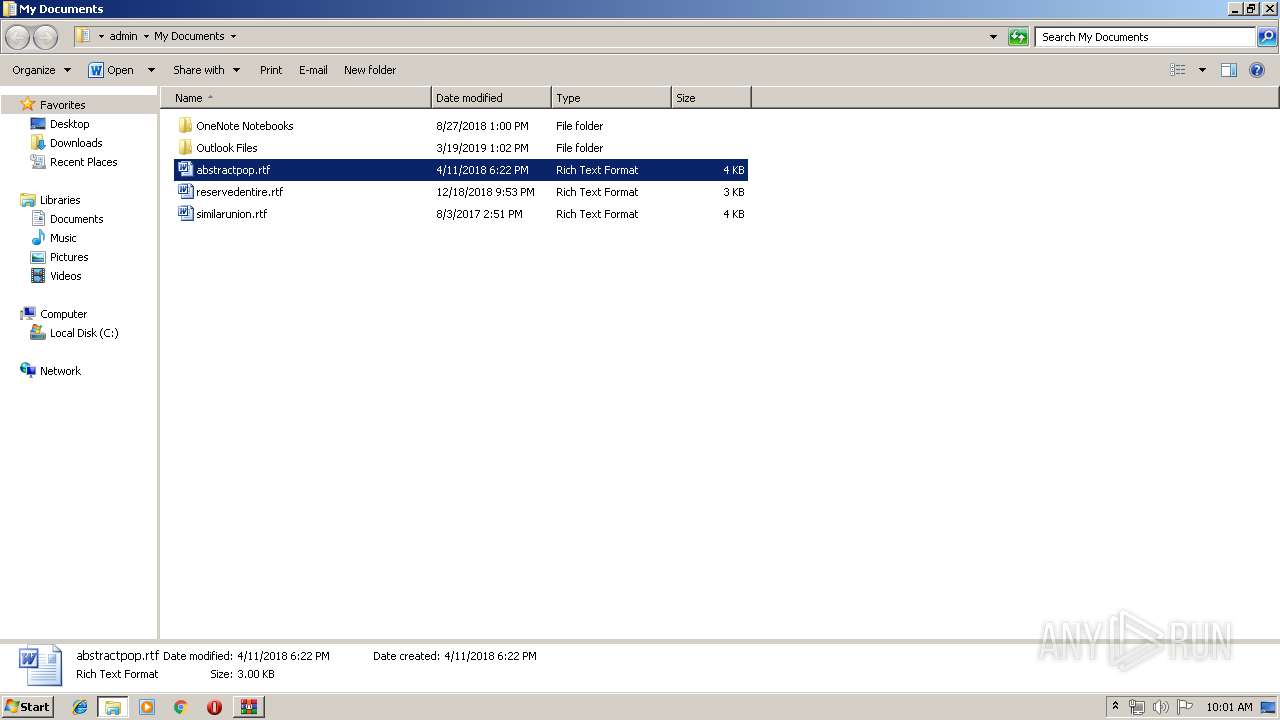
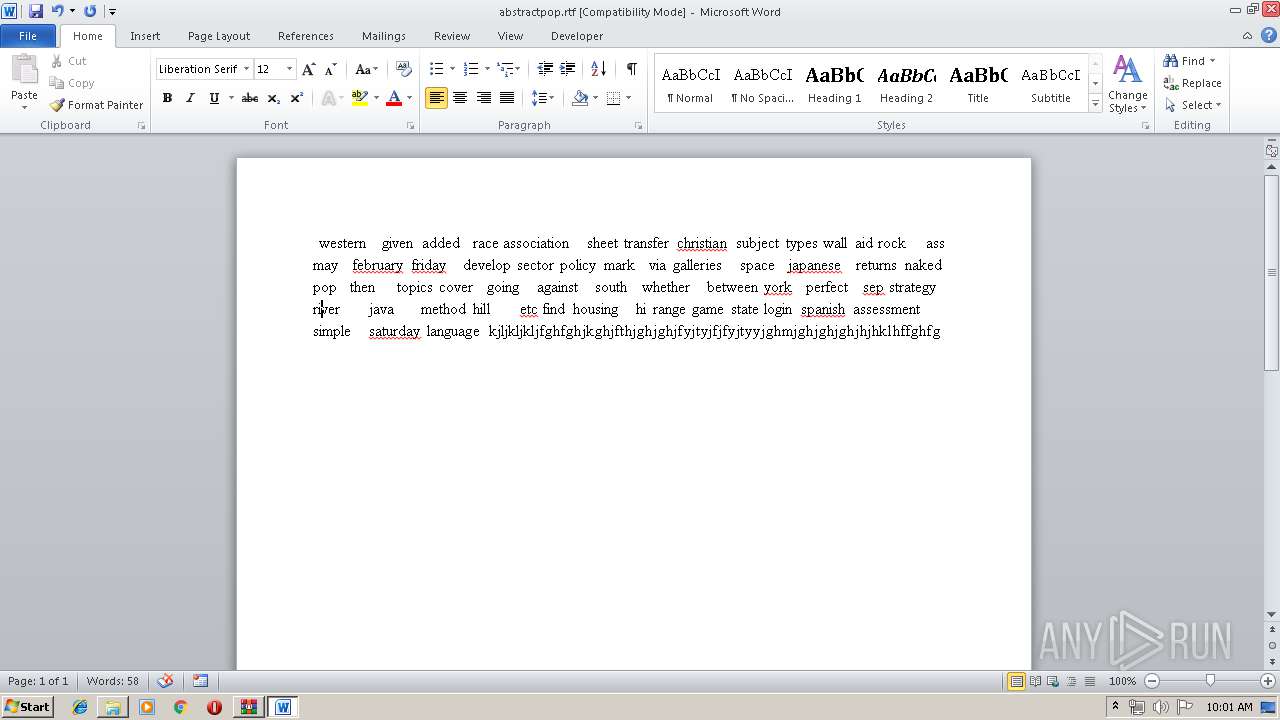
| 868 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Documents\abstractpop.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 940 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\System Volume Information.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1524 | /n,"C:\ " | C:\Windows\explorer.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2056 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2736 | "C:\Users\admin\AppData\Local\Temp\New703B.tmp" | C:\Users\admin\AppData\Local\Temp\New703B.tmp | — | rundll32.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2888 | "C:\Windows\system32\msiexec.exe" | C:\Windows\system32\msiexec.exe | New703B.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3544 | "C:\Windows\system32\rundll32.exe" \&&&^&&^^&^^^^&^^&&^&&^&^^^&&^^&&.2,MA2yqeWOG4wsI6qK | C:\Windows\system32\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3968 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\System Volume Information.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
3 247
Read events
2 945
Write events
274
Delete events
28
Modification events
| (PID) Process: | (940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (940) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\System Volume Information.zip | |||
| (PID) Process: | (940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
1
Suspicious files
0
Text files
8
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3544 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\New703B.tmp | — | |
MD5:— | SHA256:— | |||
| 868 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8634.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 868 | WINWORD.EXE | C:\Users\admin\Documents\~WRD0000.tmp | — | |
MD5:— | SHA256:— | |||
| 868 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{9F17932A-DCF8-4E4F-A597-BAA38020A284}.tmp | — | |
MD5:— | SHA256:— | |||
| 868 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{531597B6-DF32-46E0-BDEF-CF351B4476D8}.tmp | — | |
MD5:— | SHA256:— | |||
| 868 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{17281111-4801-4425-8D6F-97895AB7DF21}.tmp | — | |
MD5:— | SHA256:— | |||
| 664 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE481.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2888 | msiexec.exe | C:\ProgramData\msuxjn.exe | — | |
MD5:— | SHA256:— | |||
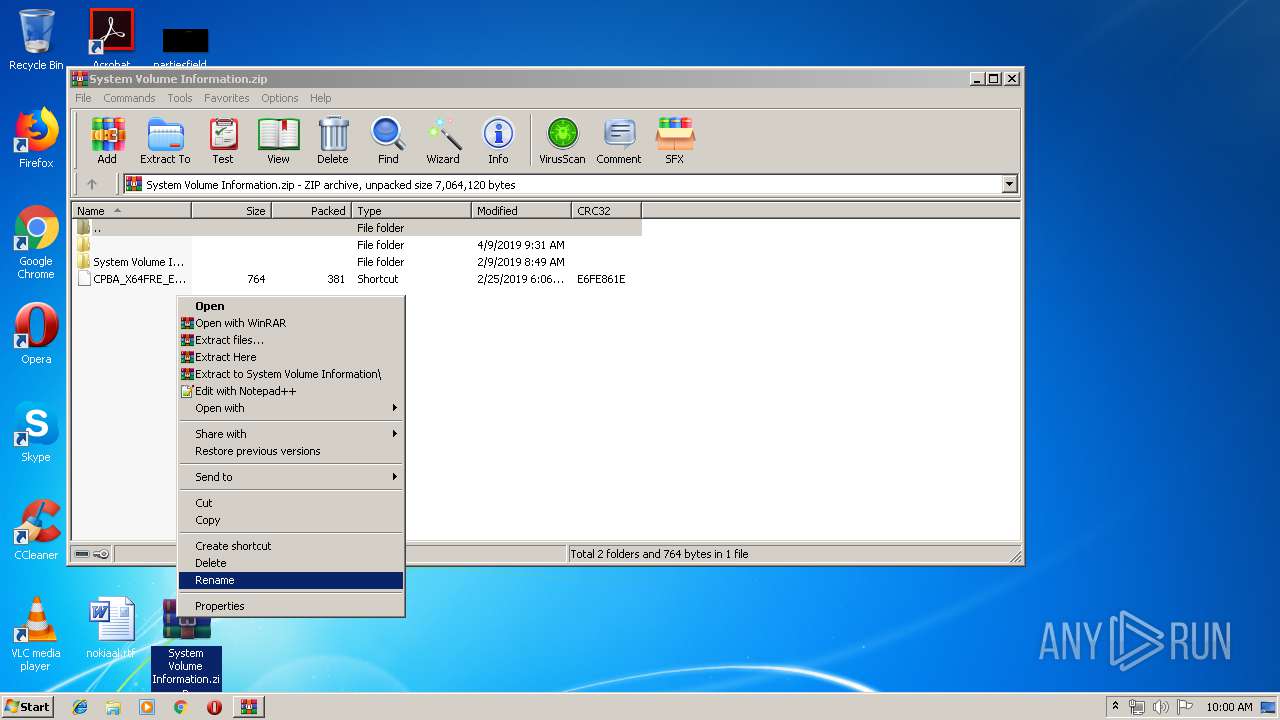
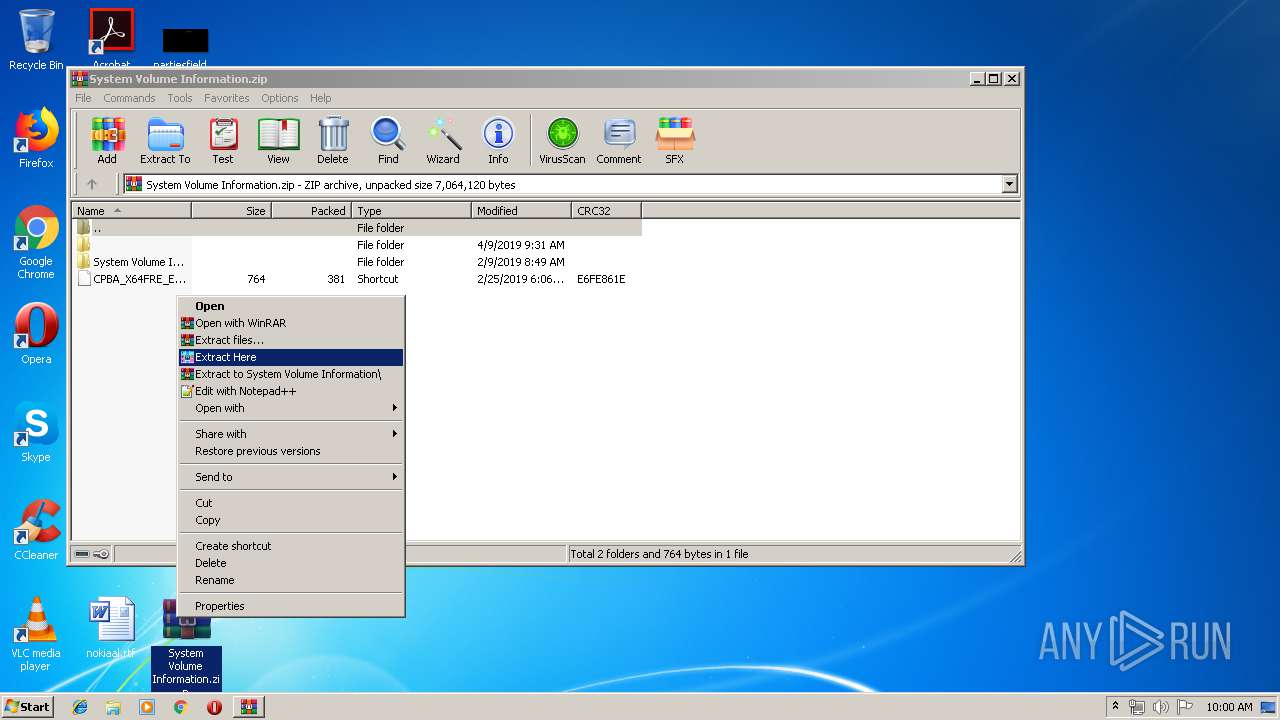
| 3968 | WinRAR.exe | C:\Users\admin\Desktop\CPBA_X64FRE_EN-US_DV9 (16GB).lnk | lnk | |
MD5:— | SHA256:— | |||
| 868 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\abstractpop.rtf.LNK | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
9
DNS requests
10
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3544 | rundll32.exe | 2.23.109.62:443 | www.microsoft.com | Akamai Technologies, Inc. | — | whitelisted |
2888 | msiexec.exe | 178.136.117.33:123 | pool.ntp.org | Private Joint-stock Company farlep-invest | UA | unknown |
— | — | 8.8.4.4:53 | — | Google Inc. | US | whitelisted |
2888 | msiexec.exe | 192.36.143.130:123 | europe.pool.ntp.org | Svensk Teleutveckling & Produktinnovation, STUPI AB | SE | unknown |
2888 | msiexec.exe | 192.111.144.114:123 | north-america.pool.ntp.org | Centrilogic, Inc. | US | unknown |
2888 | msiexec.exe | 200.160.7.186:123 | south-america.pool.ntp.org | Núcleo de Inf. e Coord. do Ponto BR - NIC. | BR | unknown |
2888 | msiexec.exe | 202.28.116.236:123 | asia.pool.ntp.org | Ministry of University Affairs | TH | unknown |
2888 | msiexec.exe | 27.124.125.251:123 | oceania.pool.ntp.org | Dreamscape Networks Limited | AU | unknown |
2888 | msiexec.exe | 197.84.150.123:123 | africa.pool.ntp.org | OPTINET | ZA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
ww1.s5nubdeqb.ru |
| unknown |
europe.pool.ntp.org |
| suspicious |
north-america.pool.ntp.org |
| malicious |
south-america.pool.ntp.org |
| suspicious |
asia.pool.ntp.org |
| suspicious |
oceania.pool.ntp.org |
| suspicious |
africa.pool.ntp.org |
| unknown |
pool.ntp.org |
| malicious |
update.microsoft.com |
| whitelisted |