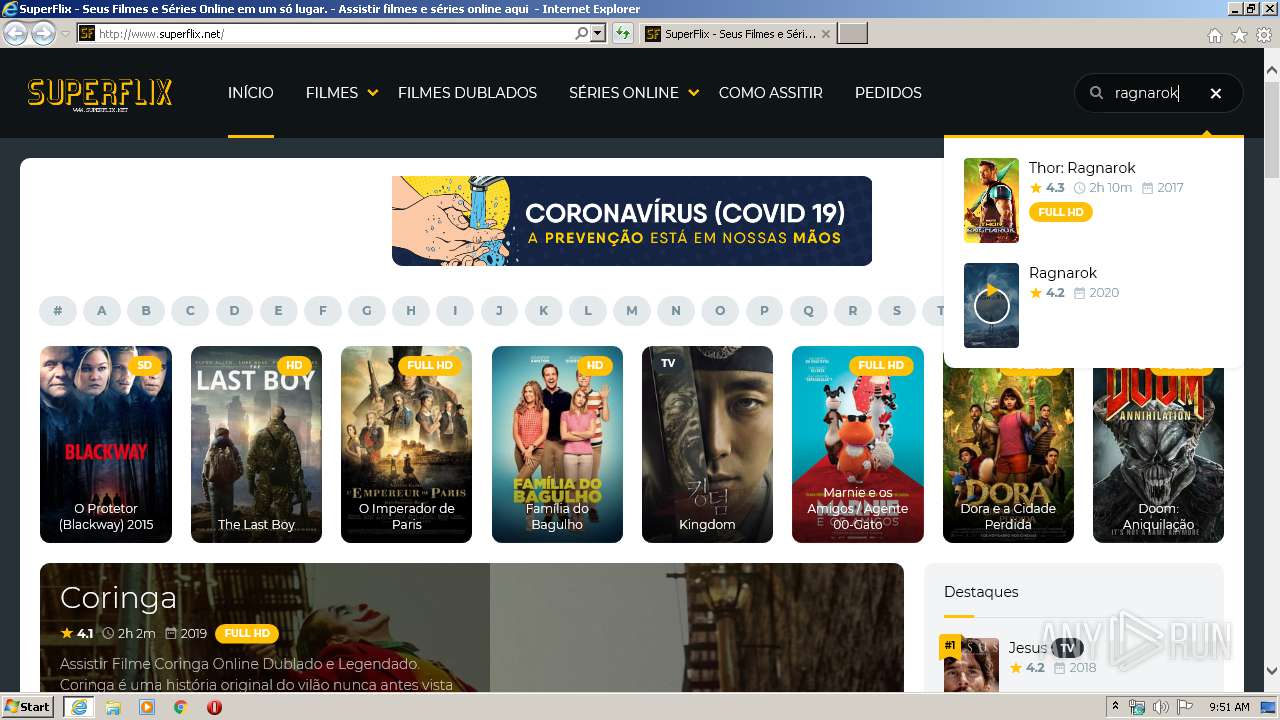
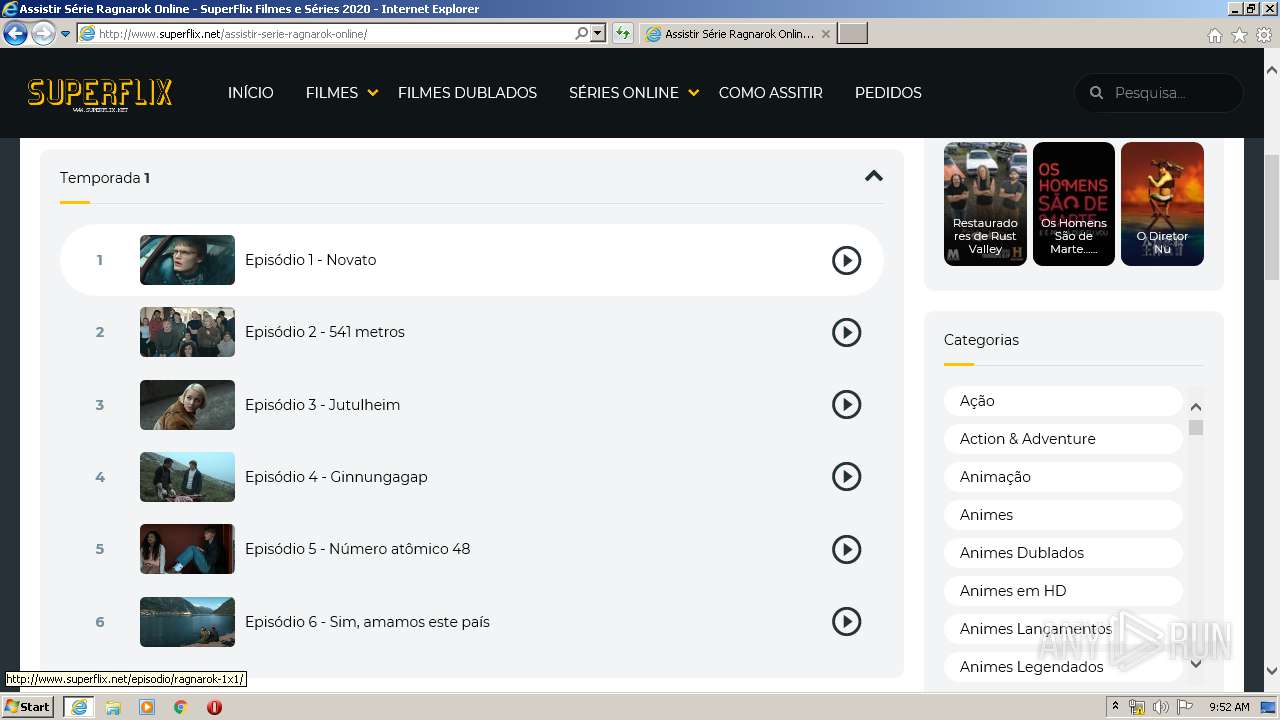
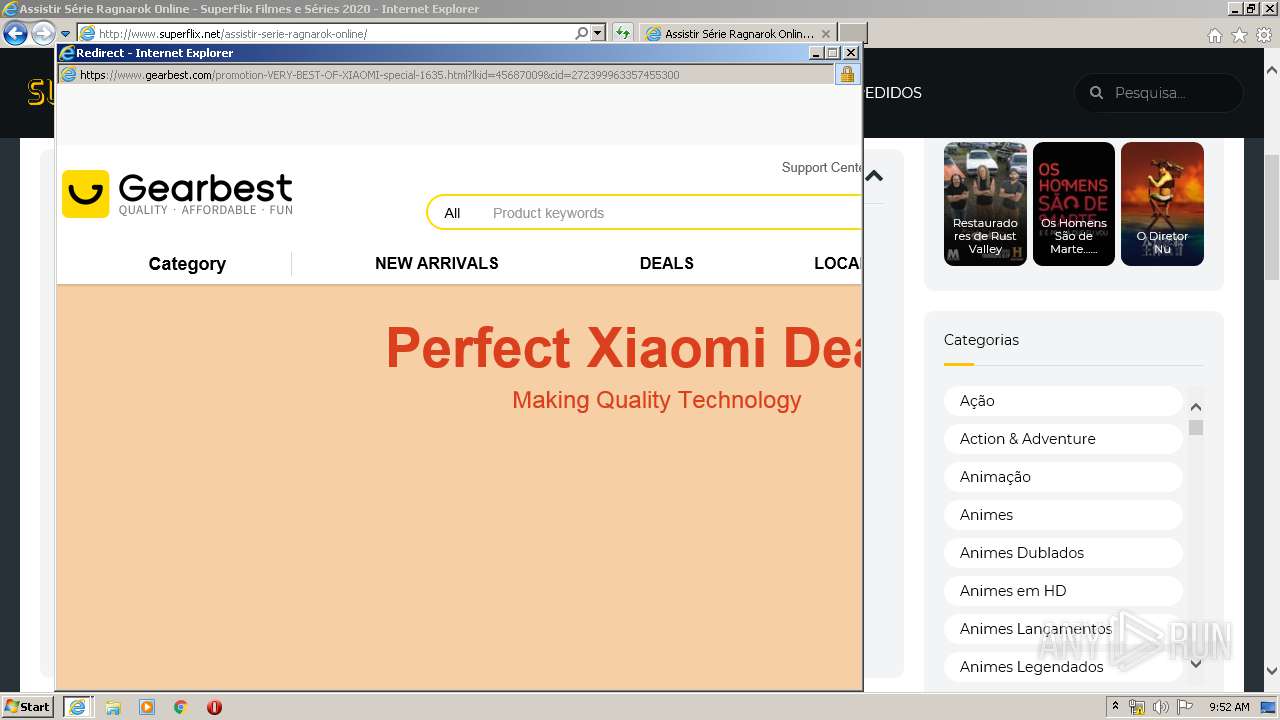
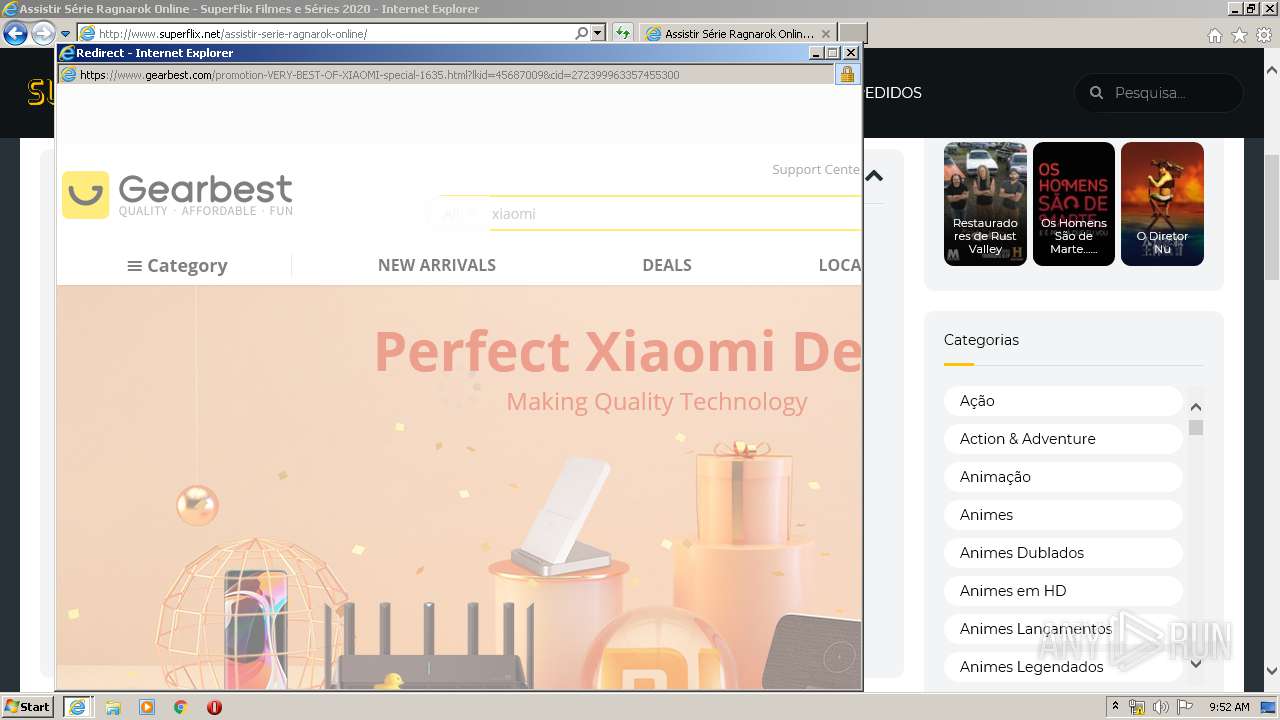
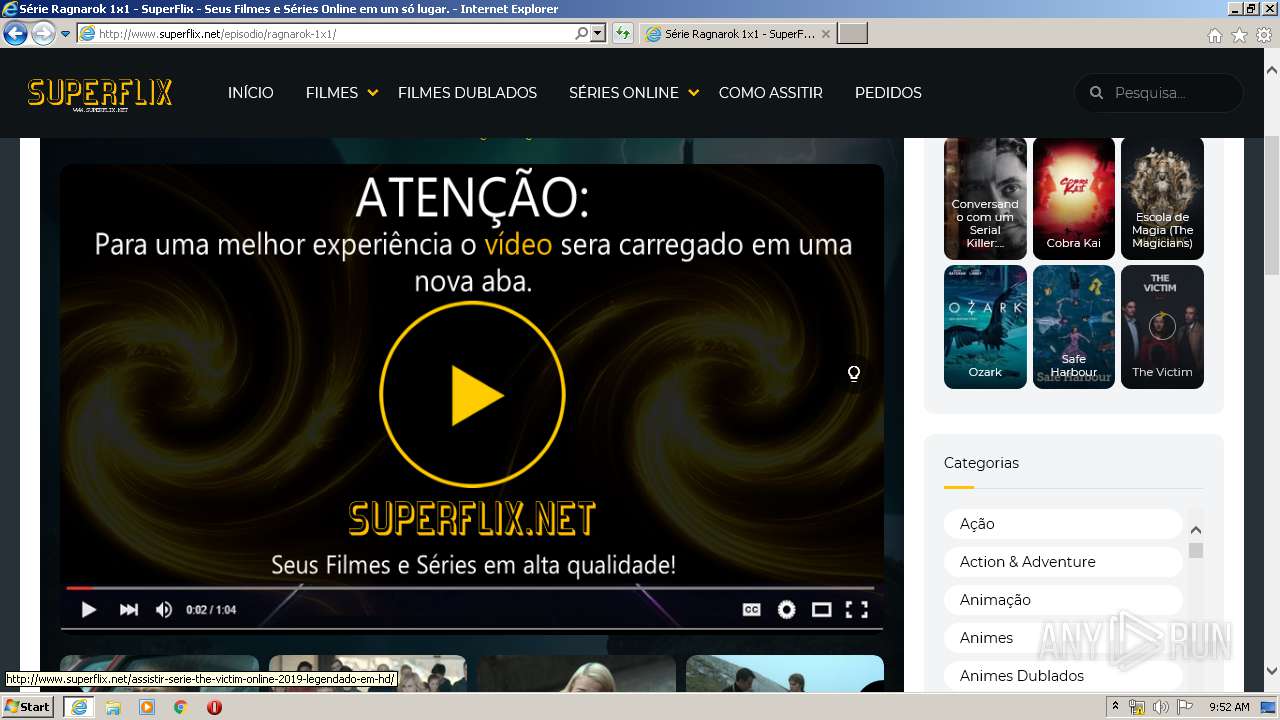
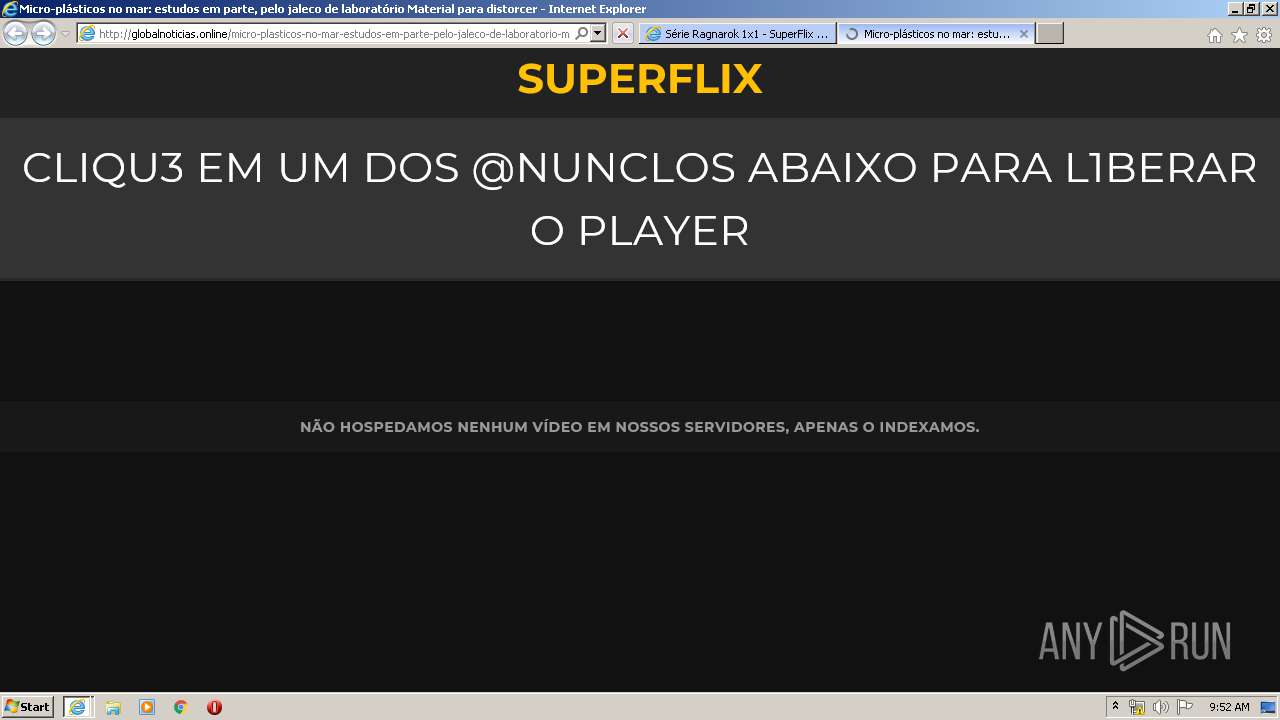
| URL: | http://superflix.net |
| Full analysis: | https://app.any.run/tasks/78d2e52a-01fc-4187-813b-d5cd4c5c22fa |
| Verdict: | Malicious activity |
| Analysis date: | April 10, 2020, 08:50:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 39464503C309D43B4721E392BF33A551 |
| SHA1: | B91C0EA95653CCF70FD1615A0A5B0407ACFCF169 |
| SHA256: | 79359DA32F8DB0002FE0A3A83F61D4AB69AF31E50D316D014FEEA5CAAEB5B615 |
| SSDEEP: | 3:N1KNQVX0:CCV0 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1852)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2052)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3420)
Reads Internet Cache Settings
- iexplore.exe (PID: 3408)
- iexplore.exe (PID: 3420)
- iexplore.exe (PID: 3900)
- iexplore.exe (PID: 3524)
Drops Coronavirus (possible) decoy
- iexplore.exe (PID: 3408)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3408)
- iexplore.exe (PID: 3900)
- iexplore.exe (PID: 3420)
- iexplore.exe (PID: 3524)
Reads internet explorer settings
- iexplore.exe (PID: 3408)
- iexplore.exe (PID: 3900)
- iexplore.exe (PID: 3524)
Creates files in the user directory
- iexplore.exe (PID: 3408)
- iexplore.exe (PID: 3420)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2052)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1852)
- iexplore.exe (PID: 3524)
- iexplore.exe (PID: 3900)
Application launched itself
- iexplore.exe (PID: 3420)
Dropped object may contain TOR URL's
- iexplore.exe (PID: 3900)
Reads settings of System Certificates
- iexplore.exe (PID: 3900)
- iexplore.exe (PID: 3408)
- iexplore.exe (PID: 3524)
- iexplore.exe (PID: 3420)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3420)
Changes settings of System certificates
- iexplore.exe (PID: 3420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
43
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1852 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 2052 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 3408 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3420 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3420 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://superflix.net" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3524 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3420 CREDAT:660824 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3900 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3420 CREDAT:202018 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
15 651
Read events
3 204
Write events
8 619
Delete events
3 828
Modification events
| (PID) Process: | (3420) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 876731824 | |||
| (PID) Process: | (3420) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30805781 | |||
| (PID) Process: | (3420) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3420) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3420) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3420) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3420) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3420) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3420) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3420) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
516
Text files
949
Unknown types
325
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3408 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\3PLWVN89.txt | — | |
MD5:— | SHA256:— | |||
| 3408 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\logosuper2[1].png | image | |
MD5:— | SHA256:— | |||
| 3408 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\R04YRGR8.txt | text | |
MD5:— | SHA256:— | |||
| 3408 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\corona[1].png | image | |
MD5:— | SHA256:— | |||
| 3408 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\jesus-novela-record-92x138[1].jpg | image | |
MD5:— | SHA256:— | |||
| 3408 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\tAlGYFGssx7BoWtAPsz76uYCPWG[1].jpg | image | |
MD5:— | SHA256:— | |||
| 3408 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\C5MD1VIC.htm | html | |
MD5:— | SHA256:— | |||
| 3408 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\game-of-thrones-23-backdrop[1].jpg | image | |
MD5:— | SHA256:— | |||
| 3408 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\z4jYhWtI8npPRoW59lo5xfvDNuW[1].jpg | image | |
MD5:— | SHA256:— | |||
| 3408 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\ygUsgb6WSTZ4iyZJXpjswgngqBY[1].jpg | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
454
TCP/UDP connections
807
DNS requests
255
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3408 | iexplore.exe | GET | 301 | 104.27.162.204:80 | http://superflix.net/ | US | — | — | whitelisted |
3408 | iexplore.exe | GET | 200 | 104.27.162.204:80 | http://www.superflix.net/ | US | html | 56.1 Kb | suspicious |
3408 | iexplore.exe | GET | 200 | 104.16.60.155:80 | http://image.tmdb.org/t/p/w185/tAlGYFGssx7BoWtAPsz76uYCPWG.jpg | US | image | 13.0 Kb | whitelisted |
3408 | iexplore.exe | GET | 200 | 104.27.162.204:80 | http://www.superflix.net/wp-content/uploads/2020/03/corona.png | US | image | 82.0 Kb | suspicious |
3408 | iexplore.exe | GET | 200 | 104.16.60.155:80 | http://image.tmdb.org/t/p/w185/ygUsgb6WSTZ4iyZJXpjswgngqBY.jpg | US | image | 12.3 Kb | whitelisted |
3408 | iexplore.exe | GET | 200 | 104.16.60.155:80 | http://image.tmdb.org/t/p/w185/73KrcLh1DpnBP3HwGpqoUUwKWF4.jpg | US | image | 16.7 Kb | whitelisted |
3408 | iexplore.exe | GET | 200 | 104.16.60.155:80 | http://image.tmdb.org/t/p/w185/lG6yg4GLIq89ngkUpu0ZevHNrbu.jpg | US | image | 17.3 Kb | whitelisted |
3408 | iexplore.exe | GET | 200 | 104.16.60.155:80 | http://image.tmdb.org/t/p/w185/2NSuxpv0e5Oti2qPQbGts8OtjMY.jpg | US | image | 12.6 Kb | whitelisted |
3408 | iexplore.exe | GET | 200 | 104.27.162.204:80 | http://www.superflix.net/wp-content/uploads/2017/08/logosuper2.png | US | image | 6.07 Kb | suspicious |
3408 | iexplore.exe | GET | 200 | 104.27.162.204:80 | http://www.superflix.net/wp-content/uploads/2017/08/game-of-thrones-23-backdrop.jpg | US | image | 30.2 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3408 | iexplore.exe | 104.27.163.204:80 | www.superflix.net | Cloudflare Inc | US | unknown |
3420 | iexplore.exe | 104.27.162.204:80 | www.superflix.net | Cloudflare Inc | US | shared |
3408 | iexplore.exe | 89.19.36.44:80 | rotumal.com | — | — | unknown |
3900 | iexplore.exe | 206.54.165.211:80 | rotumal.com | Webzilla B.V. | NL | unknown |
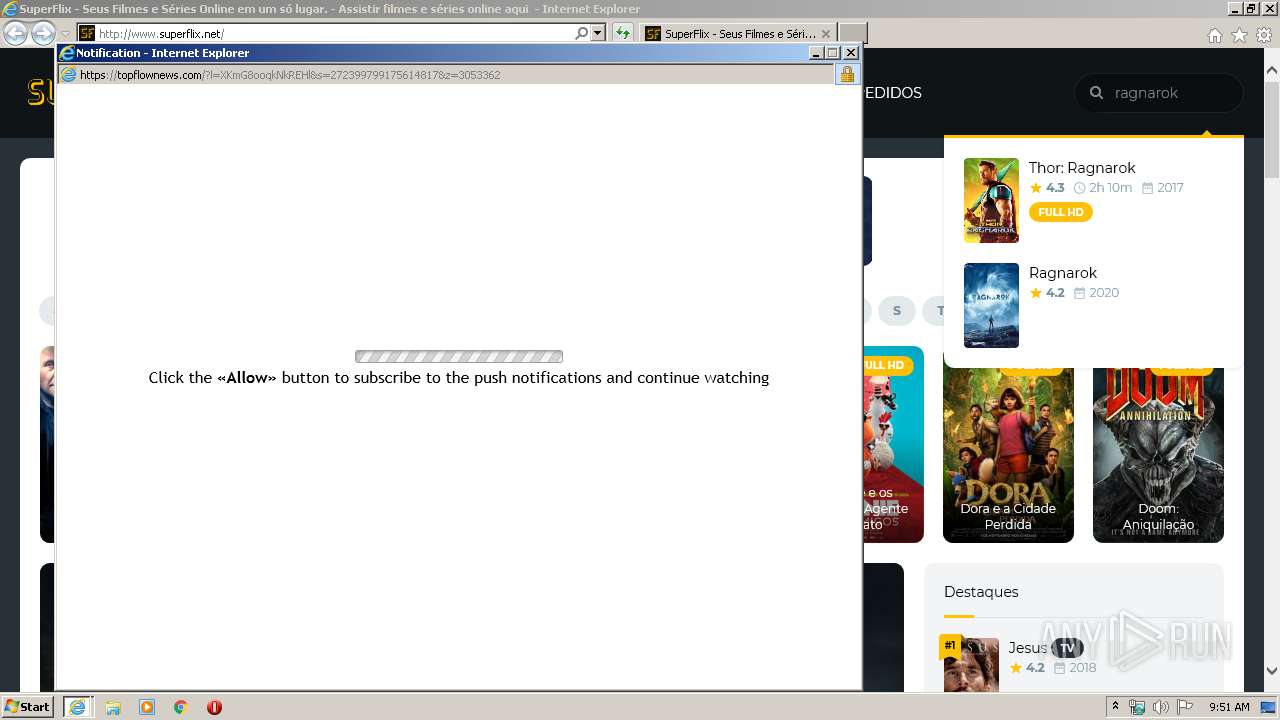
3408 | iexplore.exe | 104.18.226.52:443 | cdn.onesignal.com | Cloudflare Inc | US | malicious |
3408 | iexplore.exe | 104.27.162.204:80 | www.superflix.net | Cloudflare Inc | US | shared |
3408 | iexplore.exe | 206.54.165.211:80 | rotumal.com | Webzilla B.V. | NL | unknown |
3408 | iexplore.exe | 104.16.60.155:80 | image.tmdb.org | Cloudflare Inc | US | shared |
3408 | iexplore.exe | 104.16.60.155:443 | image.tmdb.org | Cloudflare Inc | US | shared |
3408 | iexplore.exe | 172.217.22.35:80 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
superflix.net |
| whitelisted |
www.superflix.net |
| suspicious |
cdn.onesignal.com |
| whitelisted |
rotumal.com |
| malicious |
www.googletagmanager.com |
| whitelisted |
image.tmdb.org |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3408 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious GET Request with Possible COVID-19 URI M2 |
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
3900 | iexplore.exe | Misc activity | SUSPICIOUS [PTsecurity] JS obfuscation (obfuscator.io) |
3900 | iexplore.exe | Misc activity | SUSPICIOUS [PTsecurity] Redirection JScript Obfuscated (seen Banload) |
3900 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |
3900 | iexplore.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |