| File name: | nexxzy installer.exe |
| Full analysis: | https://app.any.run/tasks/44daaf13-14a0-422e-8242-9eaaa9f93a1c |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | June 24, 2023, 19:03:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | D3BF20288FA21EE2557DF3F46E1F8395 |
| SHA1: | E90F3CDEF678C630068C60D99AF6754CA6E2FF6B |
| SHA256: | 792F9553F588AC0CAF6D148585FFE48B4CD343146852EE92C78B65BEA562F457 |
| SSDEEP: | 12288:OzPpADAQZ7xgTLXc3SMZcbxN79keUKvi8UhB8d3:OWD/dg6ZSbvi8KBy3 |
MALICIOUS
Application was dropped or rewritten from another process
- svhost.exe (PID: 240)
VIDAR was detected
- svhost.exe (PID: 240)
Vidar is detected
- svhost.exe (PID: 240)
SUSPICIOUS
Starts CMD.EXE for commands execution
- nexxzy installer.exe (PID: 2976)
Executable content was dropped or overwritten
- cmd.exe (PID: 3572)
- nexxzy installer.exe (PID: 2976)
Reads the Internet Settings
- nexxzy installer.exe (PID: 2976)
- svhost.exe (PID: 240)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3768)
The process creates files with name similar to system file names
- nexxzy installer.exe (PID: 2976)
Connects to the server without a host name
- svhost.exe (PID: 240)
INFO
Checks supported languages
- nexxzy installer.exe (PID: 2976)
- svhost.exe (PID: 240)
Reads the computer name
- nexxzy installer.exe (PID: 2976)
- svhost.exe (PID: 240)
The process checks LSA protection
- nexxzy installer.exe (PID: 2976)
- svhost.exe (PID: 240)
- taskmgr.exe (PID: 2464)
Reads the machine GUID from the registry
- nexxzy installer.exe (PID: 2976)
- svhost.exe (PID: 240)
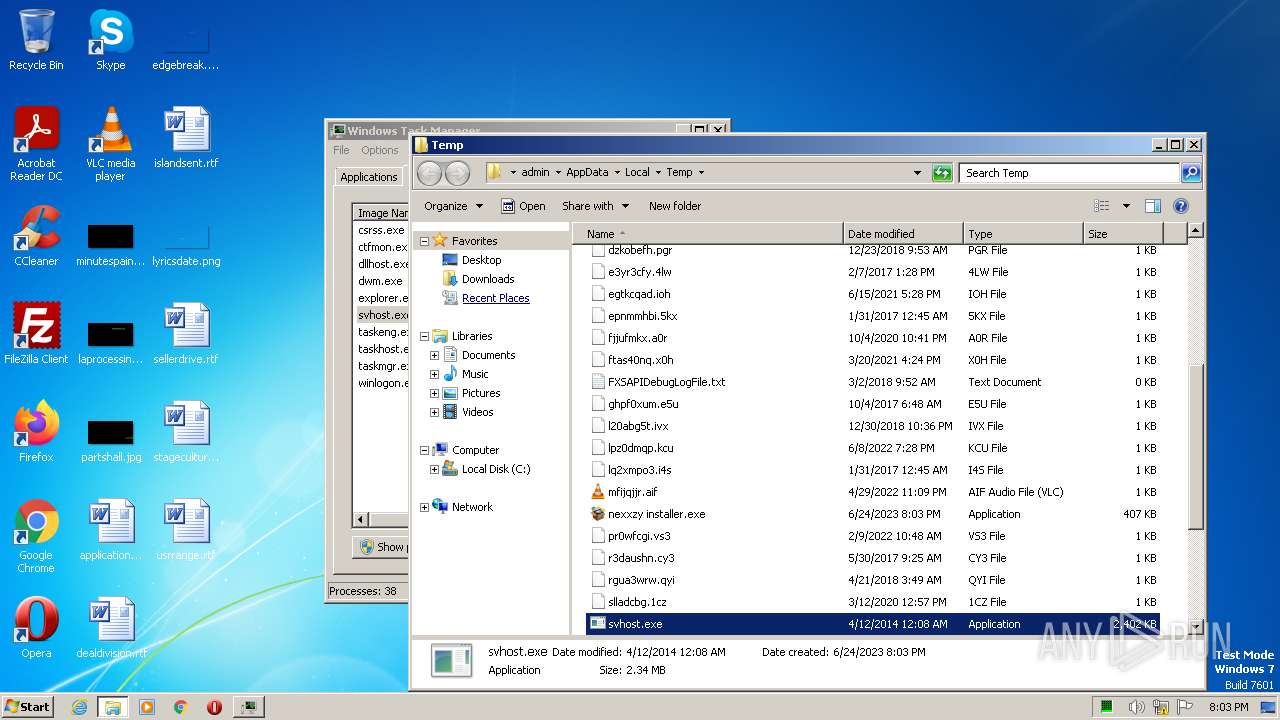
Create files in a temporary directory
- nexxzy installer.exe (PID: 2976)
The process uses the downloaded file
- cmd.exe (PID: 952)
Checks proxy server information
- svhost.exe (PID: 240)
Manual execution by a user
- taskmgr.exe (PID: 2464)
- chrome.exe (PID: 3288)
Application launched itself
- chrome.exe (PID: 3288)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| ProductVersion: | 1.3.16.0 |
|---|---|
| ProductName: | DMG Extractor |
| LegalCopyright: | Copyright (c) Reincubate Ltd |
| FileVersion: | 1.3.16.0 |
| FileDescription: | DMG Extractor installer |
| CompanyName: | Reincubate Ltd |
| CharacterSet: | Windows, Latin1 |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x0000 |
| ProductVersionNumber: | 1.3.16.0 |
| FileVersionNumber: | 1.3.16.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x4a342 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 109568 |
| CodeSize: | 295936 |
| LinkerVersion: | 8 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, 32-bit |
| TimeStamp: | 2020:01:05 23:56:47+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 05-Jan-2020 23:56:47 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 05-Jan-2020 23:56:47 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00048348 | 0x00048400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.5693 |
.rsrc | 0x0004C000 | 0x0001A87F | 0x0001AA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.43165 |
.reloc | 0x00068000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 5.1407 | 16936 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 5.24484 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 5.43083 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 5.66985 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
103 | 2.65209 | 76 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
mscoree.dll |
Total processes
65
Monitored processes
22
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Users\admin\AppData\Local\Temp\svhost.exe" | C:\Users\admin\AppData\Local\Temp\svhost.exe | nexxzy installer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 12.0.51209.34209 Modules
| |||||||||||||||
| 616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1016,4134096669251102224,9105972924881958202,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3452 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 952 | "C:\Windows\System32\cmd.exe" /c echo [zoneTransfer]ZoneID = 2 > %temp%\FolderN\name.exe:Zone.Identifier | C:\Windows\System32\cmd.exe | — | nexxzy installer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1368 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1016,4134096669251102224,9105972924881958202,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1284 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1016,4134096669251102224,9105972924881958202,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2844 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1016,4134096669251102224,9105972924881958202,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1048 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1932 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,4134096669251102224,9105972924881958202,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3468 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1016,4134096669251102224,9105972924881958202,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3256 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2464 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2512 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1016,4134096669251102224,9105972924881958202,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3340 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
12 984
Read events
12 900
Write events
82
Delete events
2
Modification events
| (PID) Process: | (2976) nexxzy installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2976) nexxzy installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2976) nexxzy installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2976) nexxzy installer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (240) svhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (240) svhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (240) svhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (240) svhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (240) svhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (240) svhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
4
Suspicious files
153
Text files
114
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3288 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-64973E40-CD8.pma | — | |
MD5:— | SHA256:— | |||
| 2976 | nexxzy installer.exe | C:\Users\admin\AppData\Local\Temp\FolderN\name.exe.lnk | binary | |
MD5:97C4716B48BE3FD16543A68D6BE09413 | SHA256:38A61DDE6231073D9653D769C6EDF3703963D3B1F68623E991628ECA59B3E11D | |||
| 3572 | cmd.exe | C:\Users\admin\AppData\Local\Temp\FolderN\name.exe | executable | |
MD5:D3BF20288FA21EE2557DF3F46E1F8395 | SHA256:792F9553F588AC0CAF6D148585FFE48B4CD343146852EE92C78B65BEA562F457 | |||
| 3288 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8FF312A95D60ED89857FEB720D80D4E1 | SHA256:946A57FAFDD28C3164D5AB8AB4971B21BD5EC5BFFF7554DBF832CB58CC37700B | |||
| 2976 | nexxzy installer.exe | C:\Users\admin\AppData\Local\Temp\svhost.exe | executable | |
MD5:1500086E0B7F3004CA84B8B858C69F6A | SHA256:A6EA2EE57EF3CA4A2A8253D1587183A4739F03DBCEFD6B2C8AD7171D2F790CD0 | |||
| 3288 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3288 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF12cc8f.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
| 3288 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
| 3592 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 3288 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF12cc80.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
13
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
240 | svhost.exe | POST | — | 111.90.150.191:80 | http://111.90.150.191/msvcp140.dll | unknown | — | — | malicious |
240 | svhost.exe | POST | — | 111.90.150.191:80 | http://111.90.150.191/softokn3.dll | unknown | — | — | malicious |
240 | svhost.exe | POST | — | 111.90.150.191:80 | http://111.90.150.191/sqlite3.dll | unknown | — | — | malicious |
1368 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | binary | 242 Kb | whitelisted |
240 | svhost.exe | POST | — | 111.90.150.191:80 | http://111.90.150.191/mozglue.dll | unknown | — | — | malicious |
240 | svhost.exe | POST | — | 111.90.150.191:80 | http://111.90.150.191/freebl3.dll | unknown | — | — | malicious |
240 | svhost.exe | POST | — | 111.90.150.191:80 | http://111.90.150.191/nss3.dll | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
240 | svhost.exe | 111.90.150.191:80 | — | Shinjiru Technology Sdn Bhd | MY | malicious |
3288 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1368 | chrome.exe | 142.250.185.99:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
1368 | chrome.exe | 142.250.185.173:443 | accounts.google.com | GOOGLE | US | suspicious |
1368 | chrome.exe | 142.250.186.46:443 | clients2.google.com | GOOGLE | US | whitelisted |
1368 | chrome.exe | 142.250.186.164:443 | www.google.com | GOOGLE | US | whitelisted |
1368 | chrome.exe | 142.250.186.33:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
1368 | chrome.exe | 142.250.186.74:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |
accounts.google.com |
| shared |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
240 | svhost.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
240 | svhost.exe | A Network Trojan was detected | ET MALWARE Vidar/Arkei/Megumin/Oski Stealer HTTP POST Pattern |
240 | svhost.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
240 | svhost.exe | A Network Trojan was detected | ET MALWARE Vidar/Arkei/Megumin/Oski Stealer HTTP POST Pattern |
240 | svhost.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
240 | svhost.exe | A Network Trojan was detected | ET MALWARE Vidar/Arkei/Megumin/Oski Stealer HTTP POST Pattern |
240 | svhost.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
240 | svhost.exe | A Network Trojan was detected | ET MALWARE Vidar/Arkei/Megumin/Oski Stealer HTTP POST Pattern |
240 | svhost.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
240 | svhost.exe | A Network Trojan was detected | ET MALWARE Vidar/Arkei/Megumin/Oski Stealer HTTP POST Pattern |