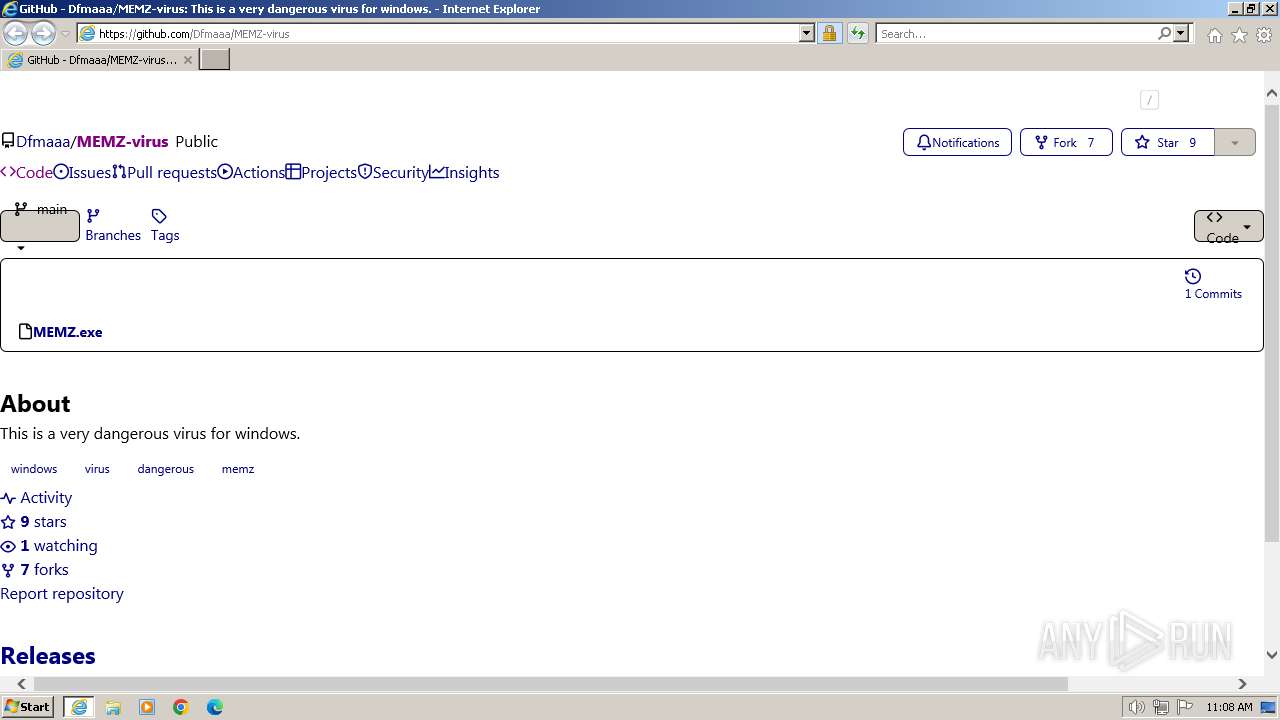
| URL: | https://github.com/Dfmaaa/MEMZ-virus |
| Full analysis: | https://app.any.run/tasks/704c41f3-0e5b-4de3-bb68-8a071aee7045 |
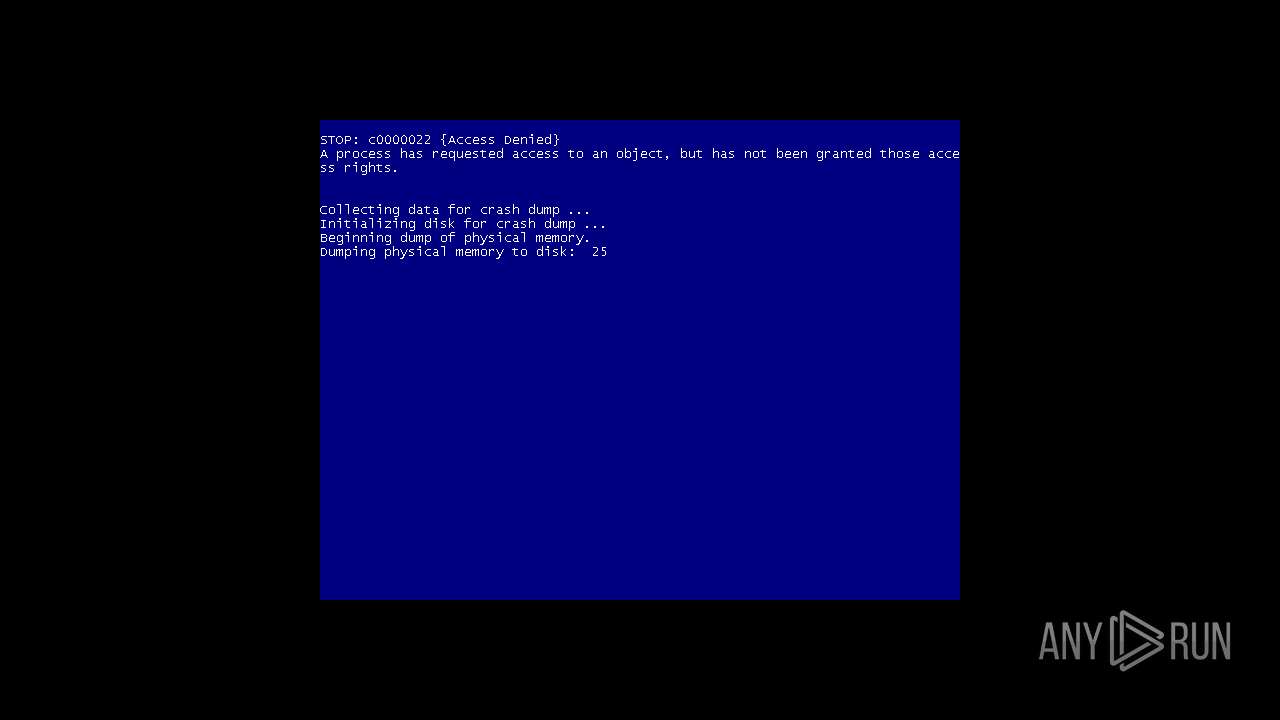
| Verdict: | Malicious activity |
| Analysis date: | March 01, 2024, 11:08:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 0ACD7C68F6C7EFD9B34A3096200DE247 |
| SHA1: | 8CE3EA00277717AB1AD1E5C4D9BBB915B6DD16DD |
| SHA256: | 792F1BF45BA3F9D590CBBB5F13310C8DEC4198B2E6CDEA5BDAEB4B2E8233C08D |
| SSDEEP: | 3:N8tEd1YMzn:2uwG |
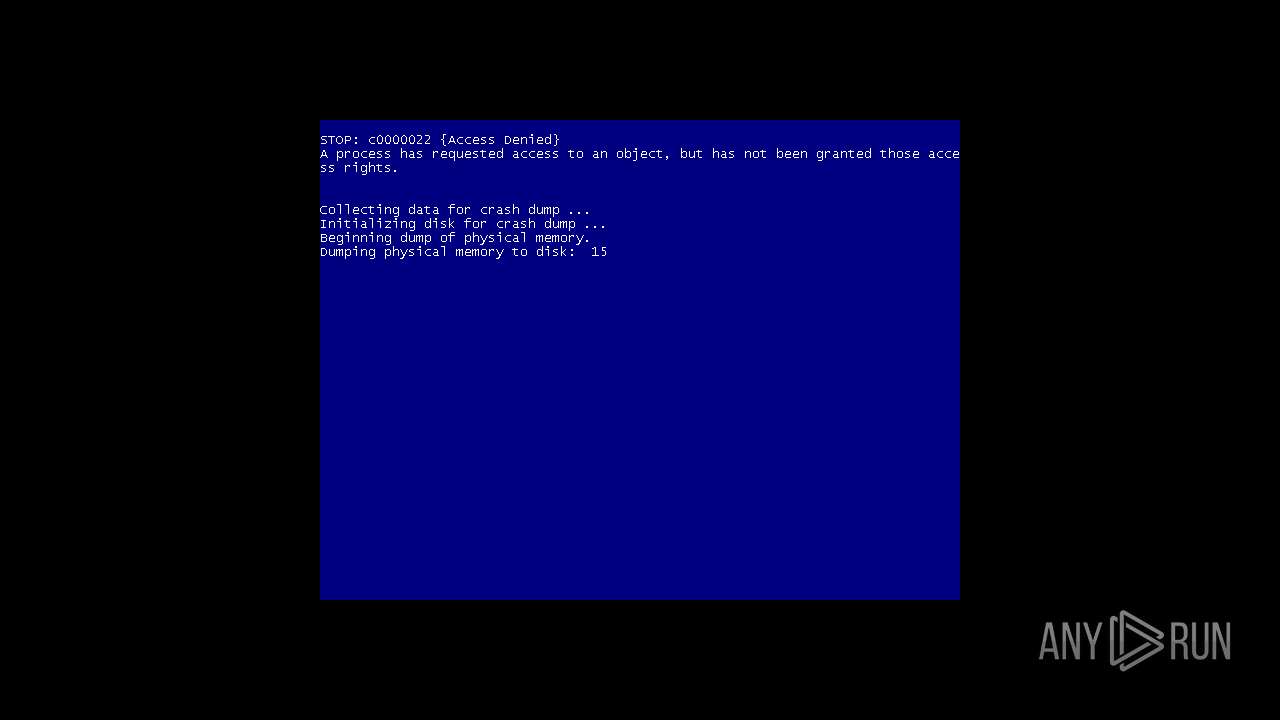
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- MEMZ.exe (PID: 3268)
- sipnotify.exe (PID: 1684)
- runonce.exe (PID: 604)
- WerFault.exe (PID: 2068)
- MEMZ.exe (PID: 2876)
- MEMZ.exe (PID: 3012)
Reads security settings of Internet Explorer
- MEMZ.exe (PID: 3268)
- MEMZ.exe (PID: 2876)
- MEMZ.exe (PID: 3012)
Application launched itself
- MEMZ.exe (PID: 3268)
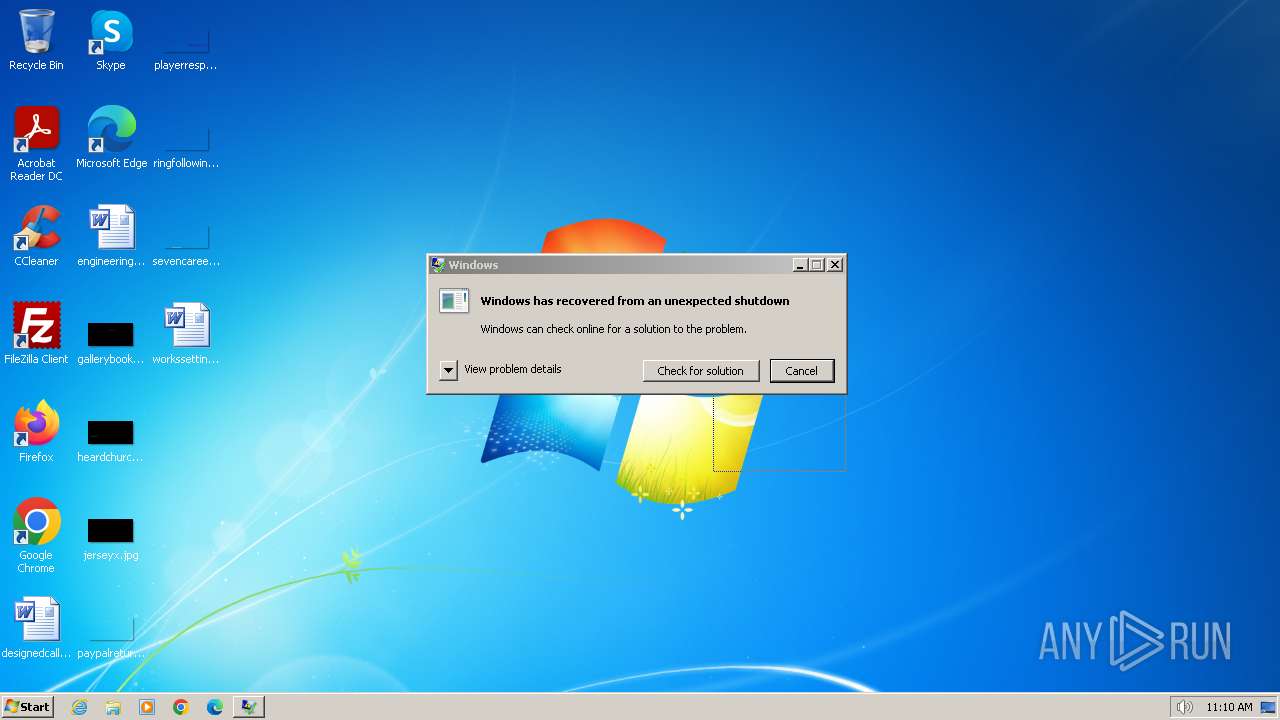
- WerFault.exe (PID: 2060)
- MEMZ.exe (PID: 2876)
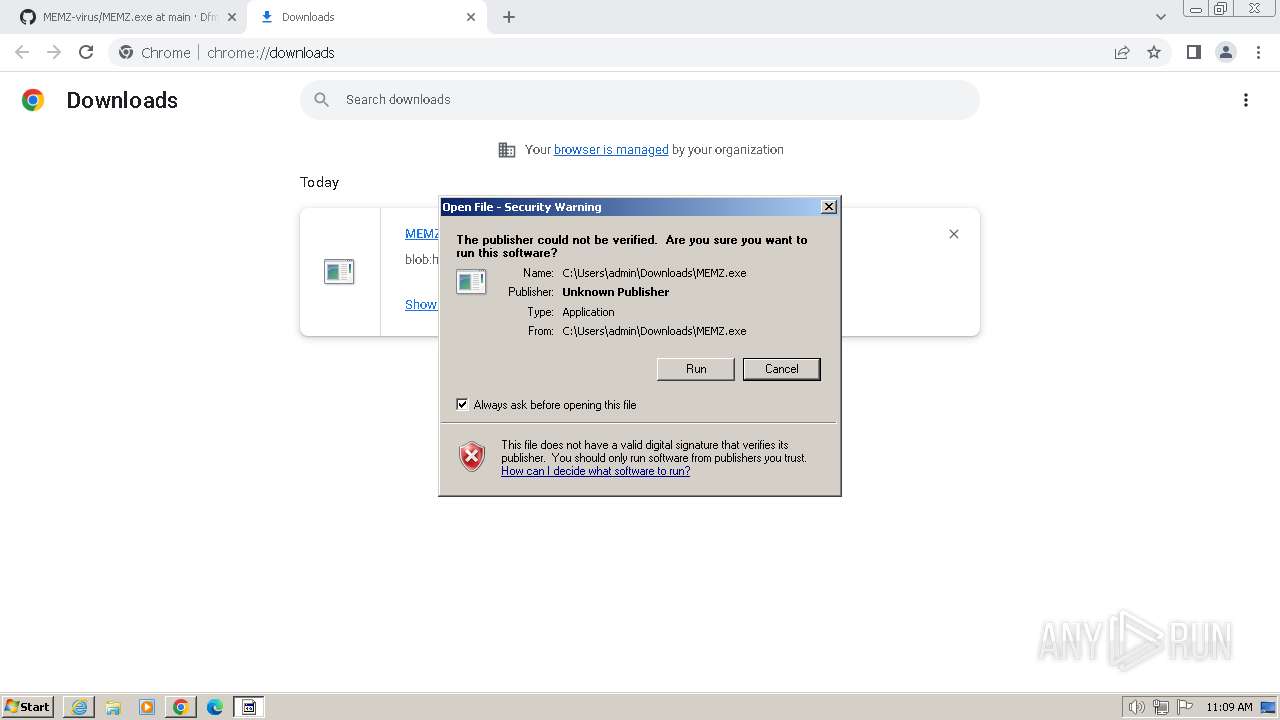
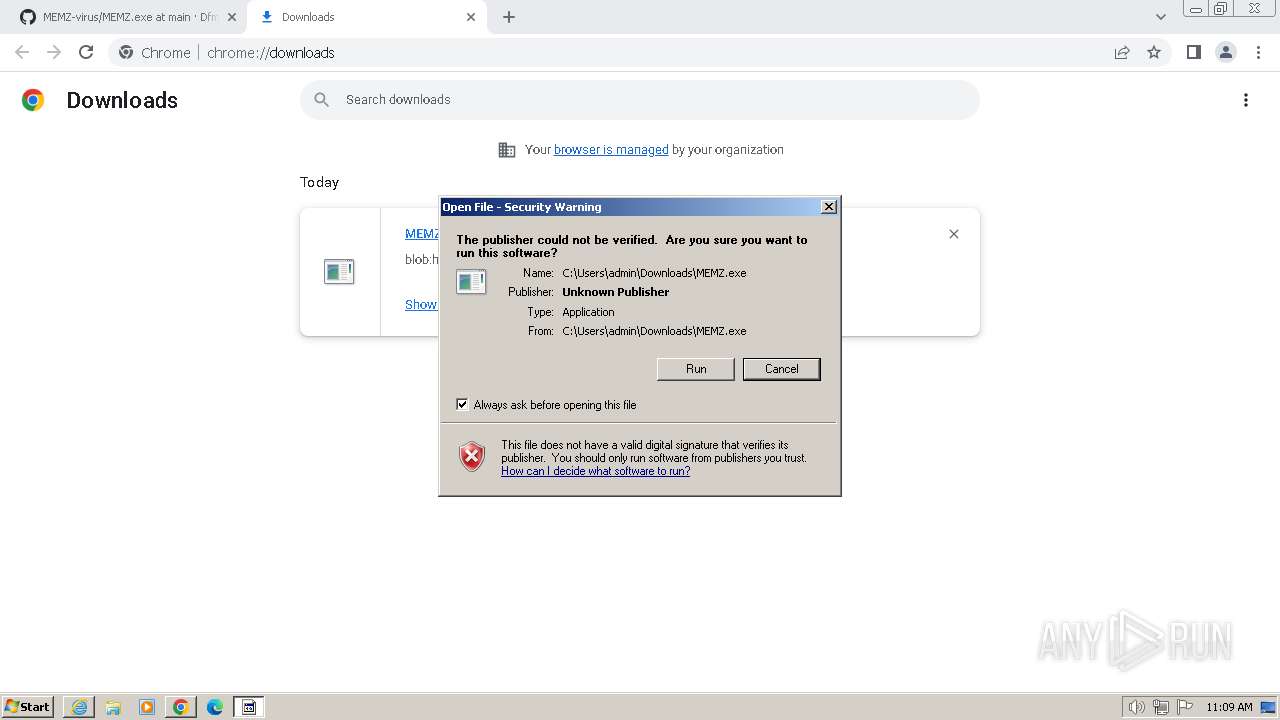
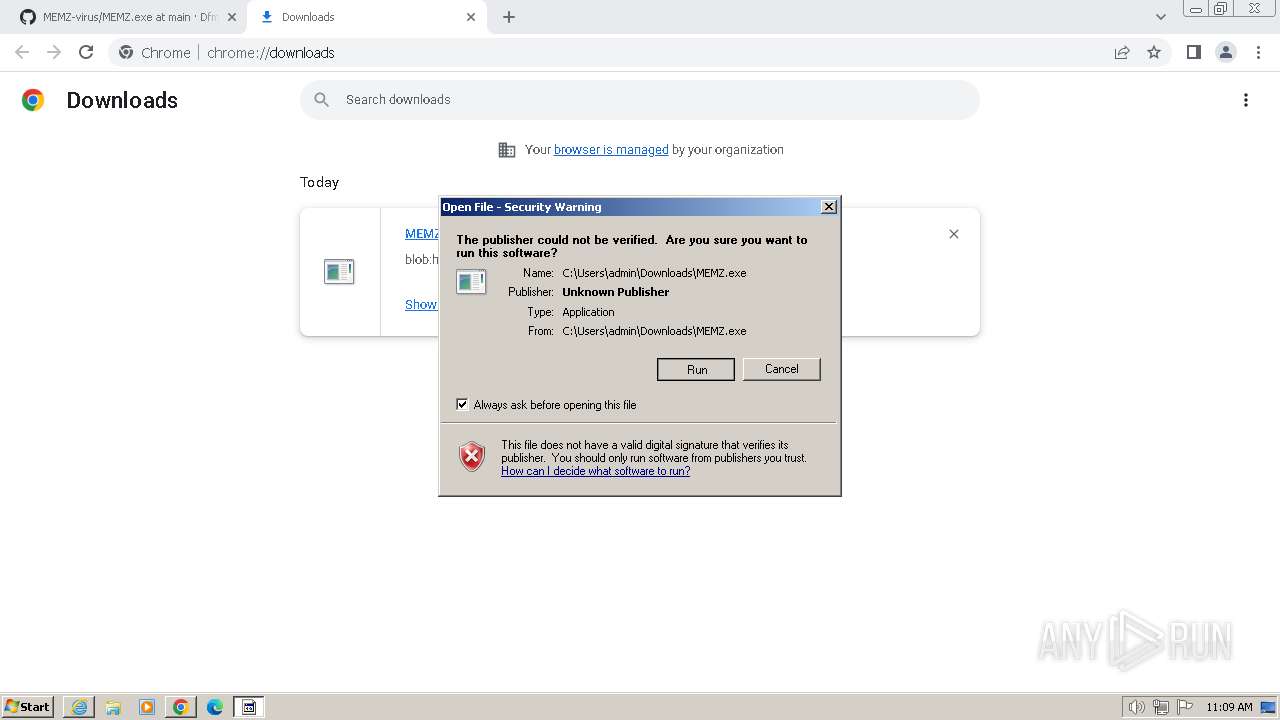
Checks Windows Trust Settings
- MEMZ.exe (PID: 3268)
- MEMZ.exe (PID: 2876)
The process executes via Task Scheduler
- sipnotify.exe (PID: 1684)
- ctfmon.exe (PID: 1792)
Reads settings of System Certificates
- sipnotify.exe (PID: 1684)
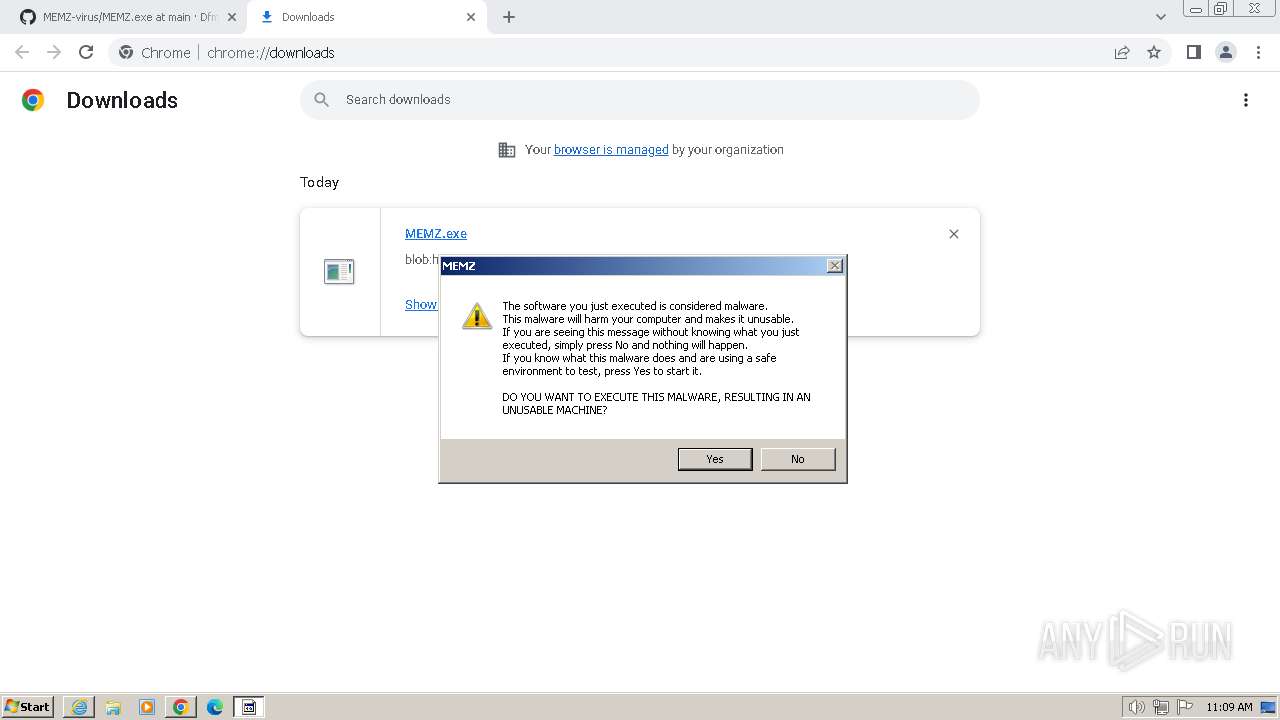
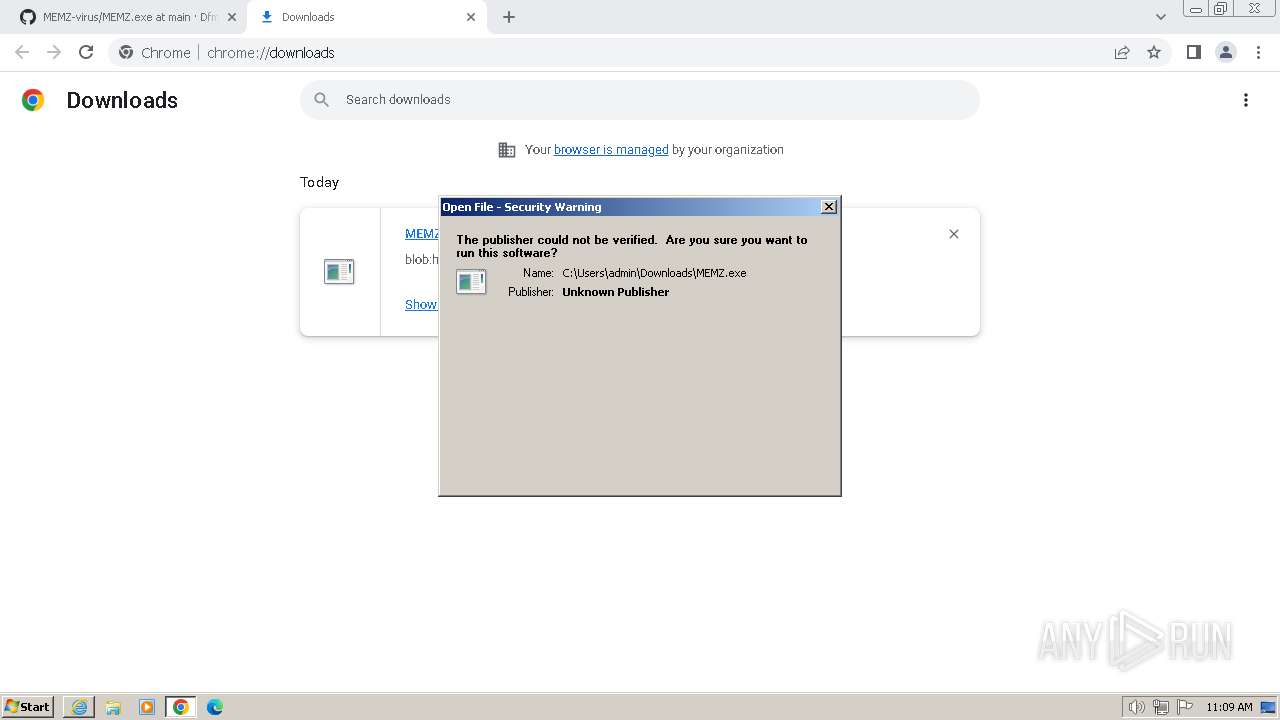
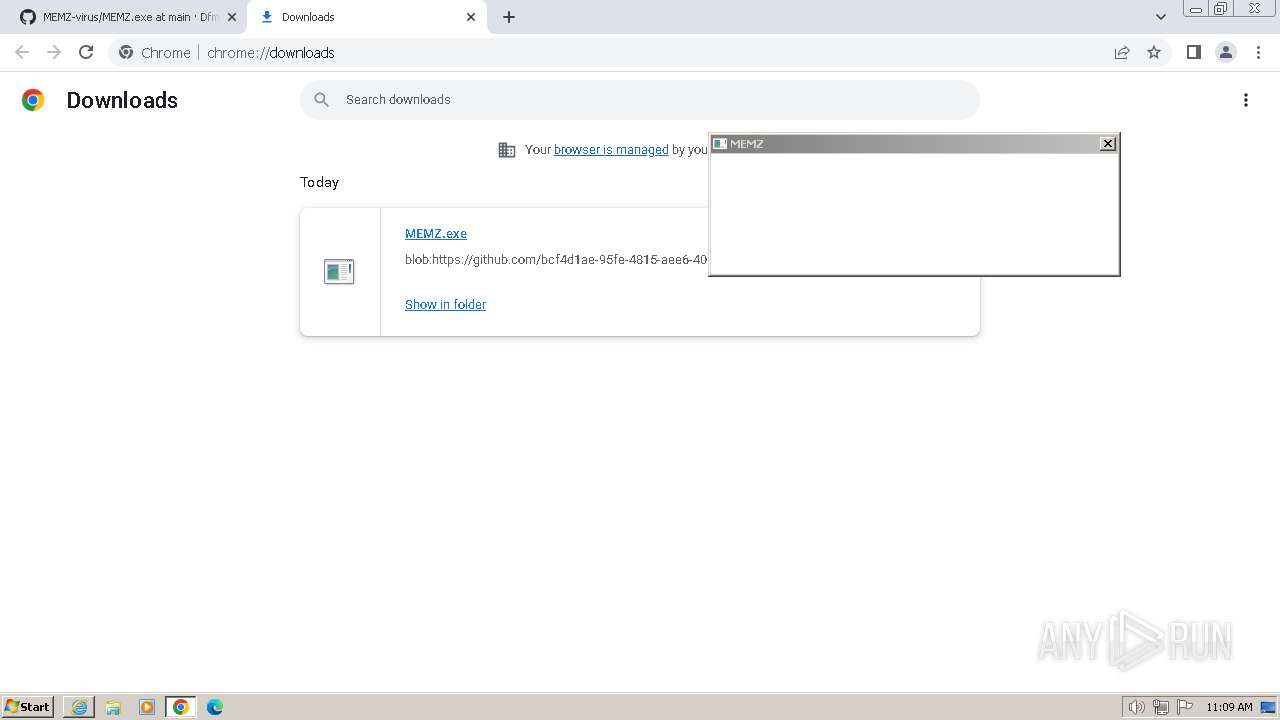
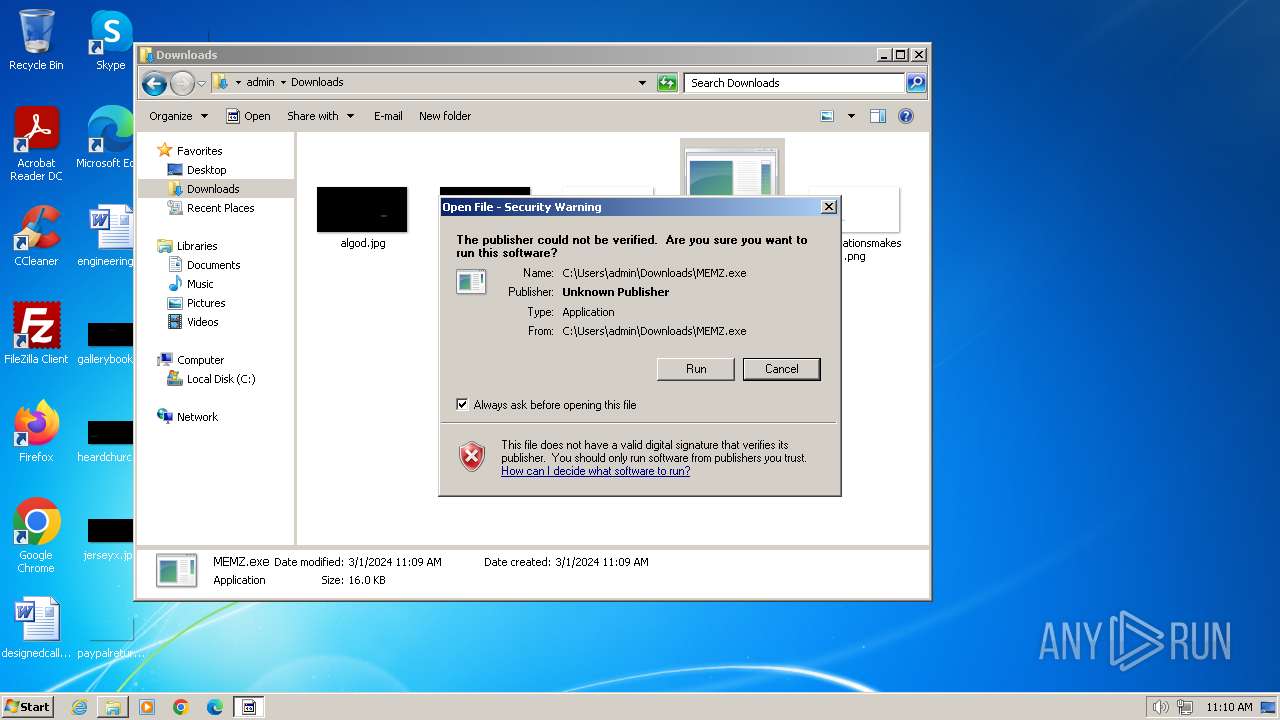
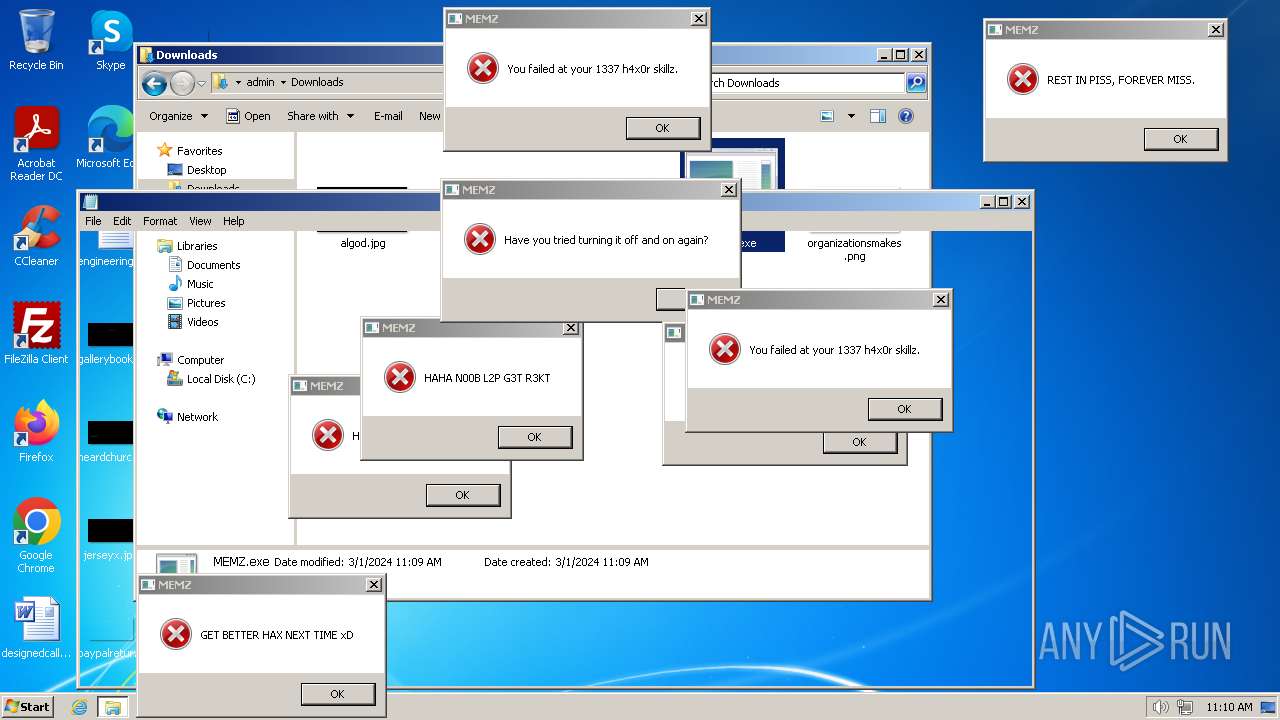
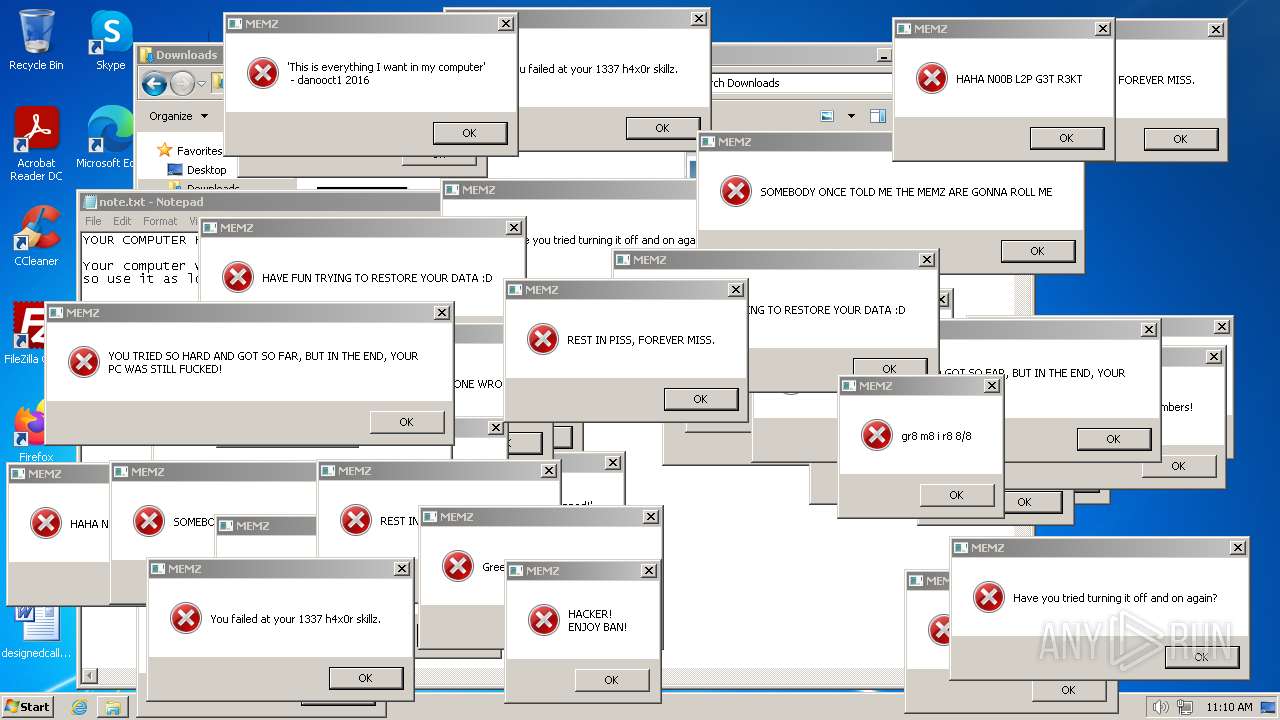
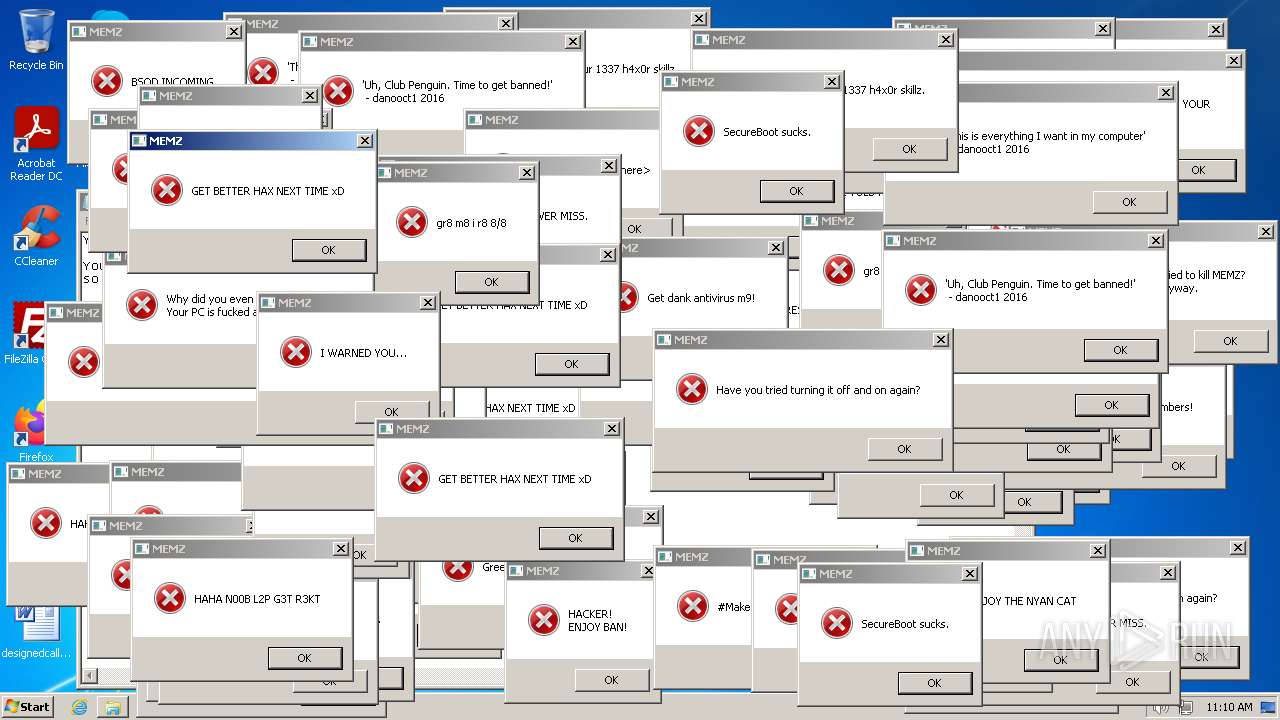
Start notepad (likely ransomware note)
- MEMZ.exe (PID: 3012)
INFO
Application launched itself
- iexplore.exe (PID: 2472)
- chrome.exe (PID: 2960)
Manual execution by a user
- chrome.exe (PID: 2960)
- runonce.exe (PID: 604)
- IMEKLMG.EXE (PID: 2148)
- IMEKLMG.EXE (PID: 2160)
- wmpnscfg.exe (PID: 2452)
- MEMZ.exe (PID: 2876)
- wmpnscfg.exe (PID: 2504)
Reads the computer name
- MEMZ.exe (PID: 3268)
- IMEKLMG.EXE (PID: 2148)
- IMEKLMG.EXE (PID: 2160)
- wmpnscfg.exe (PID: 2452)
- wmpnscfg.exe (PID: 2504)
- MEMZ.exe (PID: 2876)
- MEMZ.exe (PID: 3012)
Executable content was dropped or overwritten
- chrome.exe (PID: 2960)
The process uses the downloaded file
- chrome.exe (PID: 2960)
- chrome.exe (PID: 2868)
- MEMZ.exe (PID: 3268)
- MEMZ.exe (PID: 2876)
Drops the executable file immediately after the start
- chrome.exe (PID: 2960)
Checks supported languages
- MEMZ.exe (PID: 3268)
- MEMZ.exe (PID: 3876)
- MEMZ.exe (PID: 2136)
- MEMZ.exe (PID: 4016)
- MEMZ.exe (PID: 3916)
- MEMZ.exe (PID: 3228)
- IMEKLMG.EXE (PID: 2148)
- MEMZ.exe (PID: 3304)
- IMEKLMG.EXE (PID: 2160)
- wmpnscfg.exe (PID: 2504)
- wmpnscfg.exe (PID: 2452)
- MEMZ.exe (PID: 2876)
- MEMZ.exe (PID: 2940)
- MEMZ.exe (PID: 2924)
- MEMZ.exe (PID: 2952)
- MEMZ.exe (PID: 2964)
- MEMZ.exe (PID: 3012)
- MEMZ.exe (PID: 2992)
Reads the machine GUID from the registry
- MEMZ.exe (PID: 3268)
- MEMZ.exe (PID: 2136)
- MEMZ.exe (PID: 4016)
- MEMZ.exe (PID: 3916)
- MEMZ.exe (PID: 3876)
- MEMZ.exe (PID: 2940)
- MEMZ.exe (PID: 2964)
- MEMZ.exe (PID: 2952)
- MEMZ.exe (PID: 2924)
- MEMZ.exe (PID: 2876)
Reads the time zone
- runonce.exe (PID: 604)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1684)
- runonce.exe (PID: 604)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2148)
- IMEKLMG.EXE (PID: 2160)
Create files in a temporary directory
- WerFault.exe (PID: 2068)
Reads the software policy settings
- WerFault.exe (PID: 2068)
- sipnotify.exe (PID: 1684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
130
Monitored processes
46
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 604 | runonce.exe /Explorer | C:\Windows\System32\runonce.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3904 --field-trial-handle=1164,i,12952592246126076902,6732925541024246955,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x69cd8b38,0x69cd8b48,0x69cd8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=3772 --field-trial-handle=1164,i,12952592246126076902,6732925541024246955,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=1452 --field-trial-handle=1164,i,12952592246126076902,6732925541024246955,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1636 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3796 --field-trial-handle=1164,i,12952592246126076902,6732925541024246955,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1684 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 1792 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1808 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1620 --field-trial-handle=1164,i,12952592246126076902,6732925541024246955,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2060 | "C:\Windows\System32\WerFault.exe" -k -rq | C:\Windows\System32\WerFault.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
41 814
Read events
41 486
Write events
264
Delete events
64
Modification events
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31091656 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31091656 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
3
Suspicious files
62
Text files
123
Unknown types
94
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3348 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | der | |
MD5:31F9416110FB60BC2DAF15C8EB1514AC | SHA256:E41330297CF1BF448FF5D8918DD3F476C6A254092FD602DC2F5C7A87C0F67929 | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\5C0TP2RD.txt | text | |
MD5:993A50773A37E470E6B3A7E66249FFDA | SHA256:5E5E9773B567AAFED5E4ACEE066C8CD19C157CA2A5DC4BCE30E6510E4C209F82 | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:4F01FFCD19A45774C3DC374E08866FF8 | SHA256:955145BDD2444DED3DD24970C8F987FD2E97CAD8D1F57F37B34E99B5E43906D4 | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\light-0eace2597ca3[1].css | text | |
MD5:C98EDBDC81B370DEC6C1635959F3E6D1 | SHA256:7214039084D73A8AC3457904DCE9DBA06F30E82C1B62BF186E791502AAD5C41C | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:92CD25DFA46DF1BD0DF89F37C95D8C75 | SHA256:E1E34C4A6DC012CDFA17ED8F5BEF00F8F33AD1132F13FC1506145DA77B01F2B1 | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\vendors-node_modules_github_hydro-analytics-client_dist_analytics-client_js-node_modules_gith-6a10dd-e66ebda625fb[1].js | text | |
MD5:EA0881634AA064550AF1E9EC43BDD086 | SHA256:FF375FE79148DBE8A6FF00F2B0691DEF67955FC89F8E7AD1E9E30E46A67FF638 | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\repository-6247ca238fd4[1].css | text | |
MD5:0C6E7F9AD3D84702FE070A9DFA3E400E | SHA256:07036A0205F8314A3F5CD3EC9EEB44872B79C2418EFC20F0945B0AC5C6A83199 | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\vendors-node_modules_dompurify_dist_purify_js-6890e890956f[1].js | text | |
MD5:80FA30C00E347B5BBC8B7FF9DC2C9F44 | SHA256:BE77C75CF182F1830D0F90B8D7AEE460F0108C6E7F5A143A524F709B9023C80D | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\github-29c178bef838[1].css | text | |
MD5:32E34AE6FA7F896B0F124810B250B338 | SHA256:9A68911B28D4689283596A967BE03761A54B52BBF87877E9D6E645247808D599 | |||
| 3348 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\code-6d7b4ef0ea51[1].css | text | |
MD5:A43E8D3C18188BCB375A2D11CBFBD102 | SHA256:991E06D4A6175FD2B3E288DC647E8FA15601C55BA4B8E489913D9A0B1104841C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
59
DNS requests
56
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3348 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c9f2b763ba05a2db | unknown | — | — | unknown |
3348 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | binary | 471 b | unknown |
3348 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?14266dff8470122f | unknown | — | — | unknown |
2472 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?01f0d4b28d5ecc2d | unknown | — | — | unknown |
3348 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | binary | 471 b | unknown |
2472 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a973ebecfe8ccbeb | unknown | — | — | unknown |
3348 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAzQqL7GMs%2FmReygqbCE%2Bxw%3D | unknown | binary | 312 b | unknown |
2472 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 312 b | unknown |
2472 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6776476d79efed94 | unknown | compressed | 67.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3348 | iexplore.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
3348 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3348 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3348 | iexplore.exe | 185.199.109.154:443 | github.githubassets.com | FASTLY | US | unknown |
2472 | iexplore.exe | 185.199.109.154:443 | github.githubassets.com | FASTLY | US | unknown |
2472 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2472 | iexplore.exe | 104.126.37.168:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| shared |
user-images.githubusercontent.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |