| File name: | R2R.rar |
| Full analysis: | https://app.any.run/tasks/ad02e7e5-6bef-48a6-96a3-62fd18c0d787 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2023, 19:51:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C458550A3B602194BB60BC035B2786E3 |
| SHA1: | 8BAD2F16C46A2529FC616CE7B84AD5ADB25683AC |
| SHA256: | 790A9226740D404949FDA1C03D19406A9EA051A0A975B6479B25B4B91FEF5017 |
| SSDEEP: | 49152:LVSUpV36lA94bZEVWziXCnbdJbI56FVL2qLm6J5l3yWEmUpWwnIwL+bxLF/a9Tax:LV9Vqldag9BJB3L27eny/6bxLFUmwpSx |
MALICIOUS
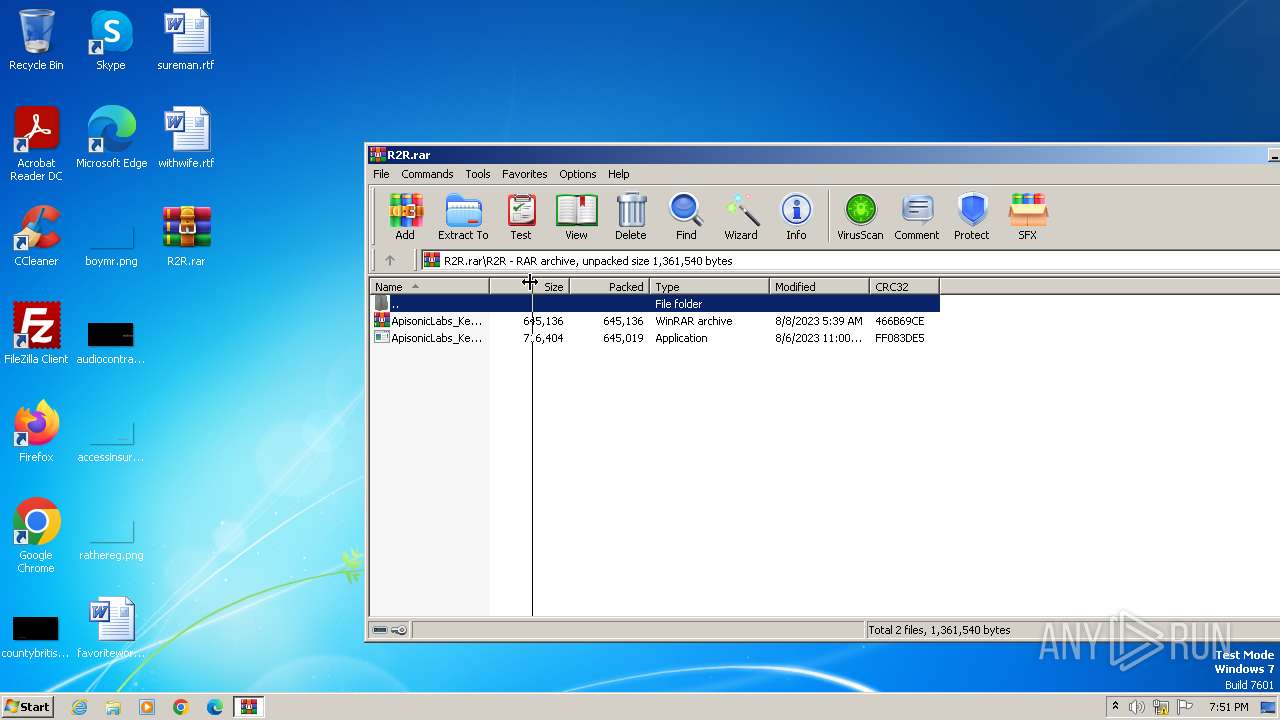
Drops the executable file immediately after the start
- ApisonicLabs_KeyGen.exe (PID: 3652)
SUSPICIOUS
No suspicious indicators.INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3436)
Checks supported languages
- ApisonicLabs_KeyGen.exe (PID: 3652)
- keygen.exe (PID: 3756)
- wmpnscfg.exe (PID: 3840)
- wmpnscfg.exe (PID: 4080)
Reads the computer name
- ApisonicLabs_KeyGen.exe (PID: 3652)
- keygen.exe (PID: 3756)
- wmpnscfg.exe (PID: 3840)
- wmpnscfg.exe (PID: 4080)
Manual execution by a user
- ApisonicLabs_KeyGen.exe (PID: 3652)
- ApisonicLabs_KeyGen.exe (PID: 3608)
- wmpnscfg.exe (PID: 3840)
- wmpnscfg.exe (PID: 4080)
Create files in a temporary directory
- ApisonicLabs_KeyGen.exe (PID: 3652)
- keygen.exe (PID: 3756)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3840)
- keygen.exe (PID: 3756)
- wmpnscfg.exe (PID: 4080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
45
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3436 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\R2R.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3608 | "C:\Users\admin\Desktop\ApisonicLabs_KeyGen.exe" | C:\Users\admin\Desktop\ApisonicLabs_KeyGen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3652 | "C:\Users\admin\Desktop\ApisonicLabs_KeyGen.exe" | C:\Users\admin\Desktop\ApisonicLabs_KeyGen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3756 | C:\Users\admin\AppData\Local\Temp\keygen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | — | ApisonicLabs_KeyGen.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3840 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4080 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 045
Read events
1 029
Write events
8
Delete events
8
Modification events
| (PID) Process: | (3436) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3436) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3840) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{AD7BE65D-315B-4DA1-BE82-1D0658D31DB5}\{C90EB22E-B9DB-4D66-BB6B-947DCC727BC4} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3840) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{AD7BE65D-315B-4DA1-BE82-1D0658D31DB5} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
4
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3652 | ApisonicLabs_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\BASSMOD.dll | executable | |
MD5:E4EC57E8508C5C4040383EBE6D367928 | SHA256:8AD9E47693E292F381DA42DDC13724A3063040E51C26F4CA8E1F8E2F1DDD547F | |||
| 3436 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3436.9336\R2R\ApisonicLabs_KeyGen.exe | executable | |
MD5:5C49257298E7C0B31519361815B8DCCE | SHA256:484FAEEF317AE761D2E24FC54AE4E6934509344BEA9E1F4A20739BFB173DBDAA | |||
| 3652 | ApisonicLabs_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\R2RAPISNC.dll | executable | |
MD5:5B691D4232876AF1CF7BF16B717FA5F1 | SHA256:197EAD845EB6366E6152D8CBD6579D3CCE689609433CC64CD4C7F6A30BEB7FCB | |||
| 3652 | ApisonicLabs_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\bgm.xm | binary | |
MD5:C817D3DFFD16F30FD40A51A71750B660 | SHA256:DFE9AB47EB98135EA1BAB0B73F57EE5A3E7C930E16369E8D48A8A4A1AC4B3F5B | |||
| 3652 | ApisonicLabs_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | executable | |
MD5:AFA202B319750B4207EE776626FFC95C | SHA256:F70E9F2EFD57A722C306B585D32D05D6E82B189A8E040DFA4431184B93408EBC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 69.192.160.136:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |