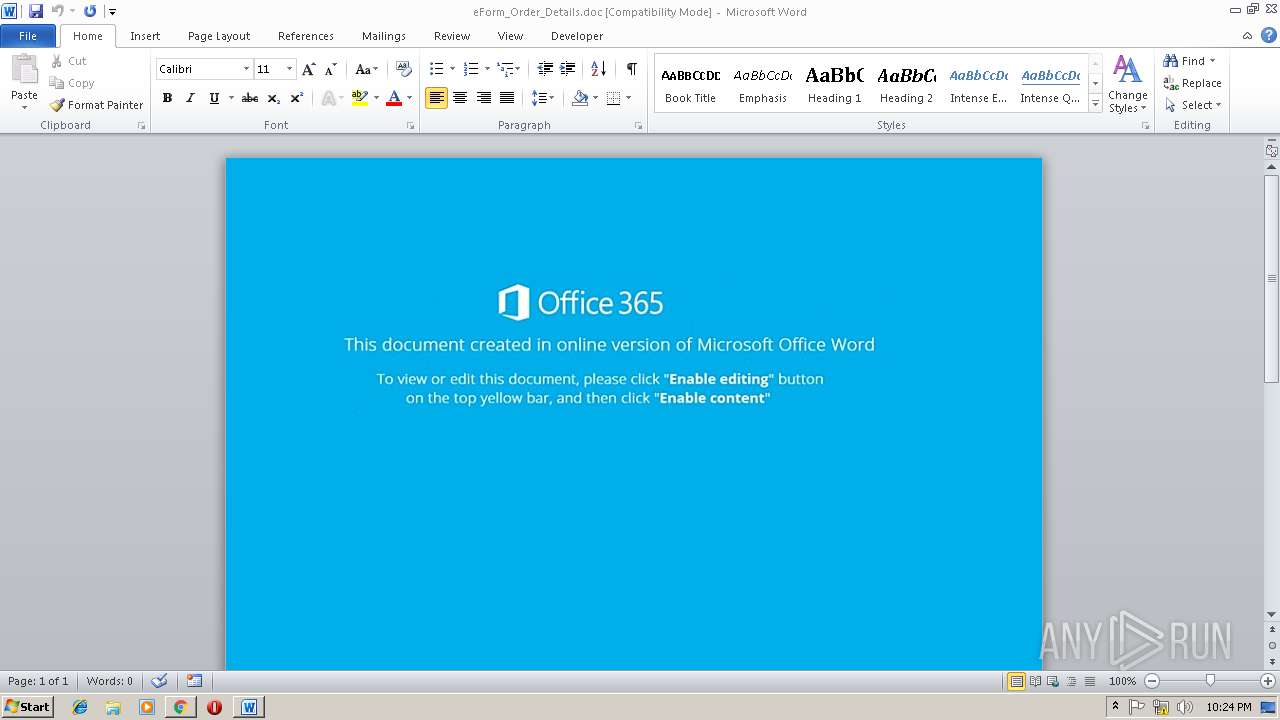
| URL: | http://themanorcentralparknguyenxien.net/Amazon/Orders_details/012019 |
| Full analysis: | https://app.any.run/tasks/45976352-b69f-499d-91d8-58578588693c |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 17, 2019, 22:22:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B751870BB780ECAD20FE5C33016C1CF9 |
| SHA1: | 984CE83EE01EFA9F04A40331DEFCD46A0DAEDF1B |
| SHA256: | 78DF928FE32E4B56050457B47B1C7F2E842B3E9646518193898C816E75338661 |
| SSDEEP: | 3:N1KKNtELMGehXkTNIKyiVRy8RNoVUc:CKNtEo/+LlRNIUc |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2460)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 4072)
Downloads executable files from the Internet
- powershell.exe (PID: 4072)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2460)
Application was dropped or rewritten from another process
- 639.exe (PID: 3960)
- 639.exe (PID: 3572)
- wabmetagen.exe (PID: 3844)
- wabmetagen.exe (PID: 2332)
Executes PowerShell scripts
- cmd.exe (PID: 3420)
EMOTET was detected
- wabmetagen.exe (PID: 2332)
Connects to CnC server
- wabmetagen.exe (PID: 2332)
SUSPICIOUS
Application launched itself
- WINWORD.EXE (PID: 2460)
Creates files in the user directory
- powershell.exe (PID: 4072)
Executable content was dropped or overwritten
- powershell.exe (PID: 4072)
- 639.exe (PID: 3572)
Starts Microsoft Office Application
- chrome.exe (PID: 3000)
- WINWORD.EXE (PID: 2460)
Starts itself from another location
- 639.exe (PID: 3572)
Connects to unusual port
- wabmetagen.exe (PID: 2332)
INFO
Reads Internet Cache Settings
- chrome.exe (PID: 3000)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2460)
- WINWORD.EXE (PID: 3396)
Application launched itself
- chrome.exe (PID: 3000)
- firefox.exe (PID: 3452)
Creates files in the user directory
- WINWORD.EXE (PID: 2460)
- firefox.exe (PID: 3452)
Reads CPU info
- firefox.exe (PID: 3452)
- firefox.exe (PID: 284)
- firefox.exe (PID: 2272)
- firefox.exe (PID: 3704)
Reads settings of System Certificates
- chrome.exe (PID: 3000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
61
Monitored processes
28
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3452.12.1411555527\126289145" -childID 3 -isForBrowser -prefsHandle 2916 -prefsLen 11808 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3452 "\\.\pipe\gecko-crash-server-pipe.3452" 3160 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 1728 | "C:\Windows\system32\notepad.exe" | C:\Windows\system32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=888,242606157672125368,8062065844879851193,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=D24AAD625AB16B6FA0E38663173B429A --mojo-platform-channel-handle=852 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2272 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3452.0.1629600764\1326540840" -childID 1 -isForBrowser -prefsHandle 928 -prefsLen 8309 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3452 "\\.\pipe\gecko-crash-server-pipe.3452" 1544 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=888,242606157672125368,8062065844879851193,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=1F087444497C84ABB32CB62E132E5B31 --mojo-platform-channel-handle=3748 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2332 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Company: Mozilla, Netscape Integrity Level: MEDIUM Exit code: 0 Version: 1.4: 2003062408 Modules
| |||||||||||||||
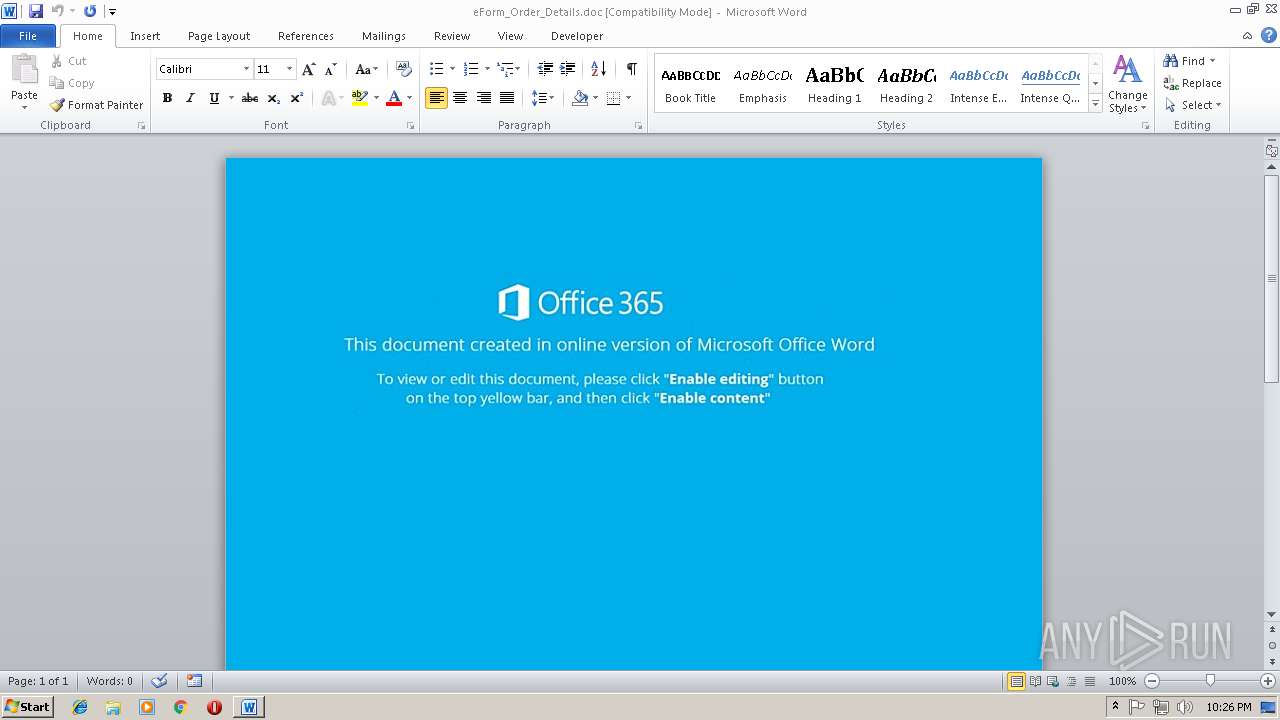
| 2460 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Downloads\eForm_Order_Details.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | chrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2652 | "C:\Program Files\Mozilla Firefox\pingsender.exe" https://incoming.telemetry.mozilla.org/submit/telemetry/9169c1d9-a866-414e-ba4b-d67b8539788b/main/Firefox/61.0.2/release/20180807170231?v=4 C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\saved-telemetry-pings\9169c1d9-a866-414e-ba4b-d67b8539788b | C:\Program Files\Mozilla Firefox\pingsender.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Foundation Integrity Level: MEDIUM Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=888,242606157672125368,8062065844879851193,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=997EF126C0B6F66D2CC35624AE922955 --mojo-platform-channel-handle=3112 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2700 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=888,242606157672125368,8062065844879851193,131072 --enable-features=PasswordImport --service-pipe-token=7D54F1FD2EBDA03F550594F9872F4BC4 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7D54F1FD2EBDA03F550594F9872F4BC4 --renderer-client-id=4 --mojo-platform-channel-handle=1892 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
3 343
Read events
2 834
Write events
495
Delete events
14
Modification events
| (PID) Process: | (3000) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3000) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3000) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2964) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3000-13192237389190250 |
Value: 259 | |||
| (PID) Process: | (3000) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3000) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3000) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (3000) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3000) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (3000) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3000-13192237389190250 |
Value: 259 | |||
Executable files
2
Suspicious files
222
Text files
179
Unknown types
100
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3000 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\1f26b8eb-87d5-4a32-b245-296b04b7c2a1.tmp | — | |
MD5:— | SHA256:— | |||
| 3000 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3000 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3000 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\214779eb-806c-45bf-bb13-586cda41c29c.tmp | — | |
MD5:— | SHA256:— | |||
| 3000 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3000 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF1999a6.TMP | text | |
MD5:— | SHA256:— | |||
| 3000 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3000 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Translate Ranker Model~RF199d21.TMP | binary | |
MD5:— | SHA256:— | |||
| 3000 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\2634581d-03e1-489f-a47f-82ba5223eb5b.tmp | — | |
MD5:— | SHA256:— | |||
| 3000 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF1999d5.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
114
DNS requests
196
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3452 | firefox.exe | GET | 301 | 104.111.233.75:80 | http://www.cibc.com/en/personal-banking.html | NL | — | — | suspicious |
3452 | firefox.exe | GET | 301 | 104.111.233.75:80 | http://www.cibc.com/ | NL | — | — | suspicious |
2332 | wabmetagen.exe | GET | — | 190.55.123.250:80 | http://190.55.123.250/ | AR | — | — | malicious |
3000 | chrome.exe | GET | 301 | 103.74.123.51:80 | http://themanorcentralparknguyenxien.net/Amazon/Orders_details/012019 | VN | html | 278 b | malicious |
4072 | powershell.exe | GET | 200 | 41.203.18.41:80 | http://refinisherstrading.com/0ccRGilOI/ | ZA | executable | 168 Kb | malicious |
3452 | firefox.exe | POST | 200 | 172.217.16.142:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
3452 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3452 | firefox.exe | POST | 200 | 172.217.16.142:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
3452 | firefox.exe | POST | 200 | 172.217.16.142:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
3452 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3000 | chrome.exe | 172.217.18.109:443 | accounts.google.com | Google Inc. | US | suspicious |
3000 | chrome.exe | 172.217.18.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3000 | chrome.exe | 172.217.16.195:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3452 | firefox.exe | 104.107.216.169:80 | detectportal.firefox.com | Akamai International B.V. | NL | whitelisted |
3452 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2332 | wabmetagen.exe | 190.55.123.250:80 | — | Telecentro S.A. | AR | malicious |
3452 | firefox.exe | 52.27.184.151:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3452 | firefox.exe | 54.187.46.234:443 | tiles.r53-2.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3452 | firefox.exe | 34.252.164.43:443 | location.services.mozilla.com | Amazon.com, Inc. | IE | unknown |
3452 | firefox.exe | 172.217.23.164:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
themanorcentralparknguyenxien.net |
| malicious |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
refinisherstrading.com |
| malicious |
detectportal.firefox.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3000 | chrome.exe | A Network Trojan was detected | ET TROJAN Possible malicious Office doc hidden in XML file |
4072 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious loader with tiny header |
4072 | powershell.exe | A Network Trojan was detected | SC TROJAN_DOWNLOADER Trojan-Downloader Emoloader Win32 |
4072 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
4072 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4072 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2332 | wabmetagen.exe | A Network Trojan was detected | SC SPYWARE Spyware Emotet Win32 |
2332 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
2332 | wabmetagen.exe | A Network Trojan was detected | SC SPYWARE Trojan-Banker.Win32.Emotet |
2332 | wabmetagen.exe | A Network Trojan was detected | SC SPYWARE Spyware Emotet Win32 |
4 ETPRO signatures available at the full report