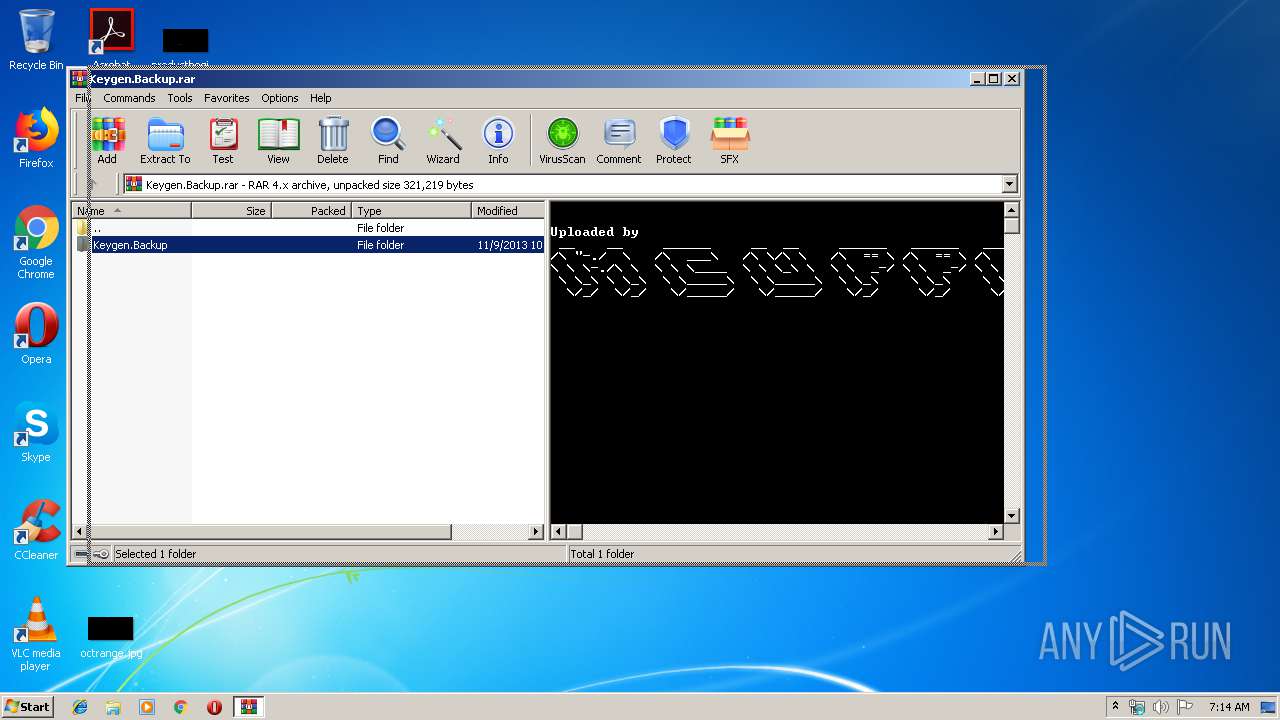
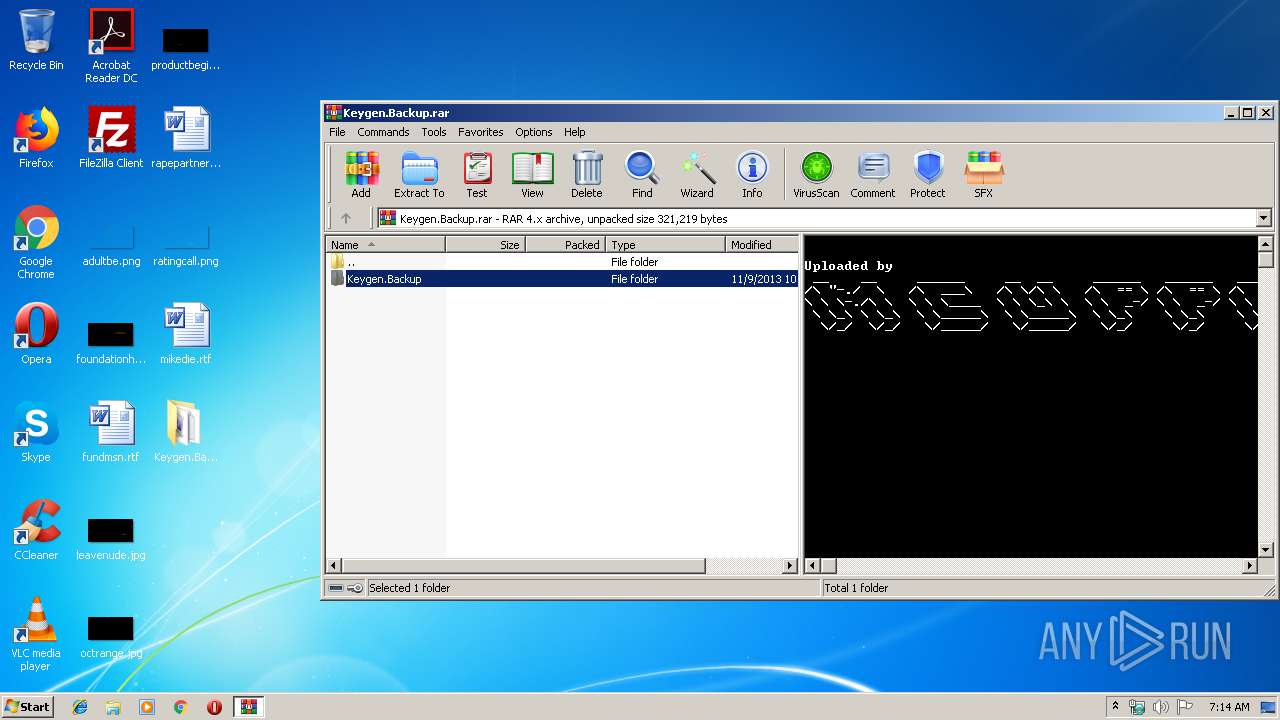
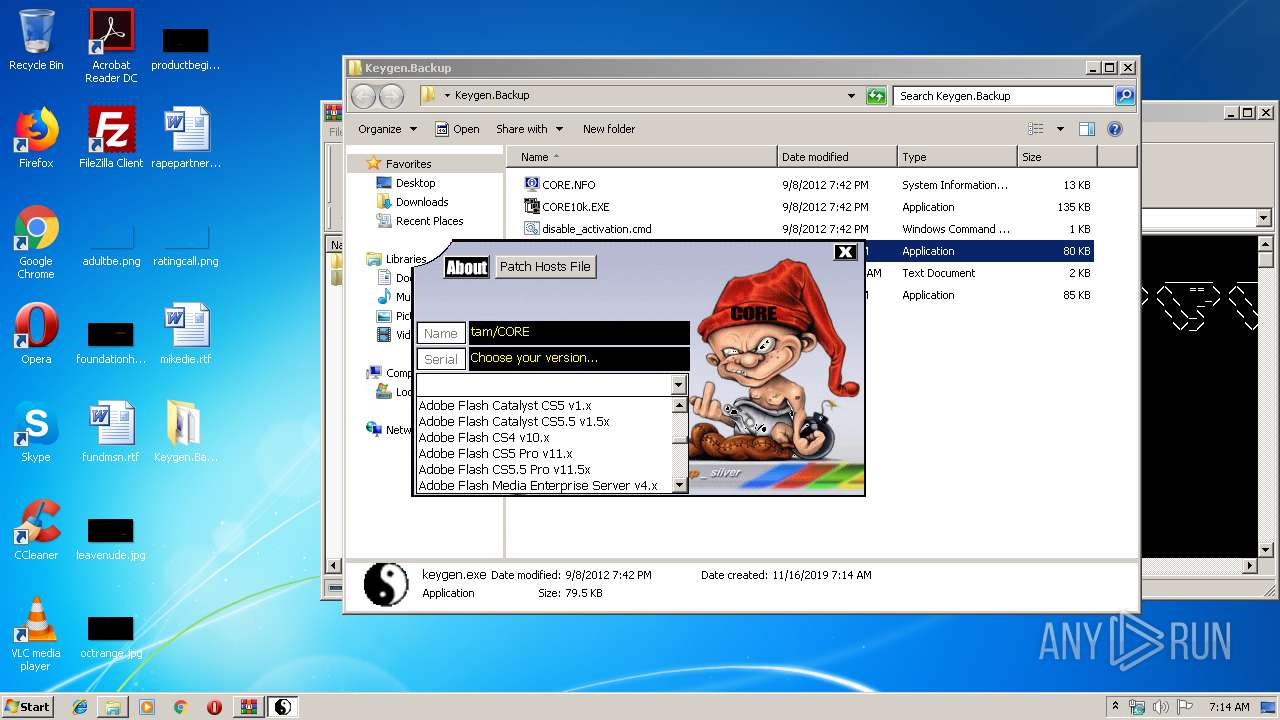
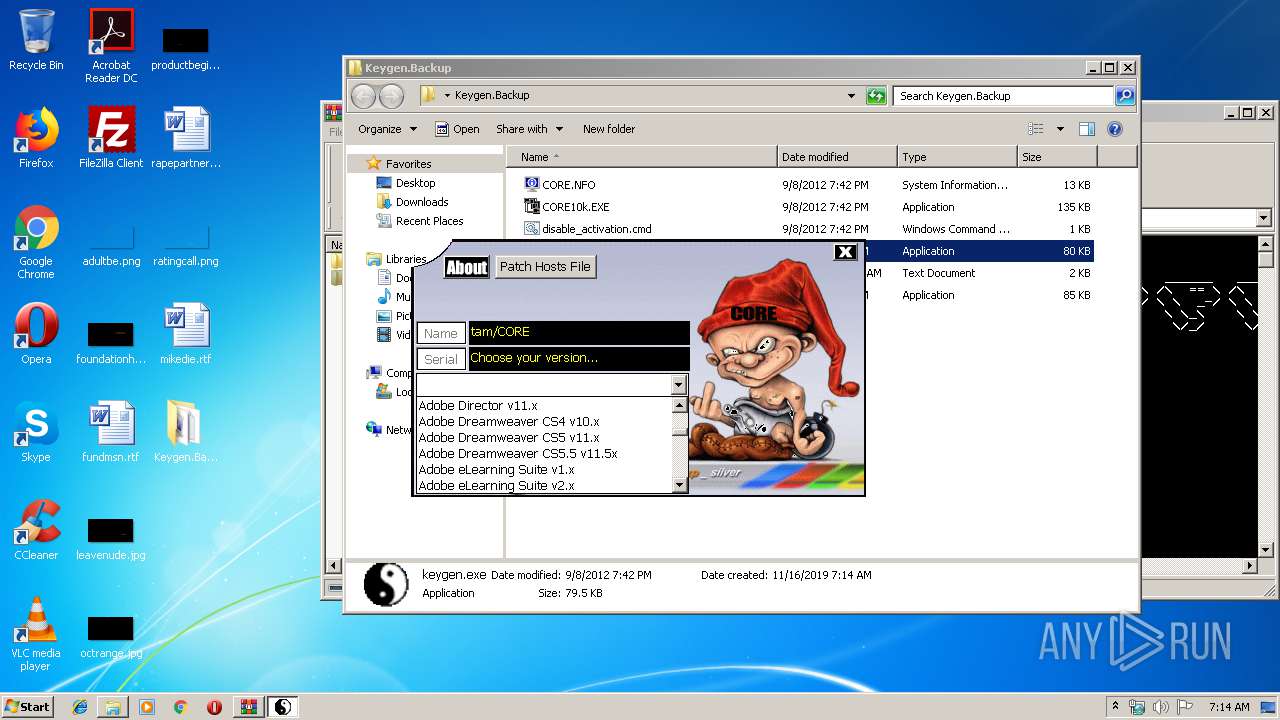
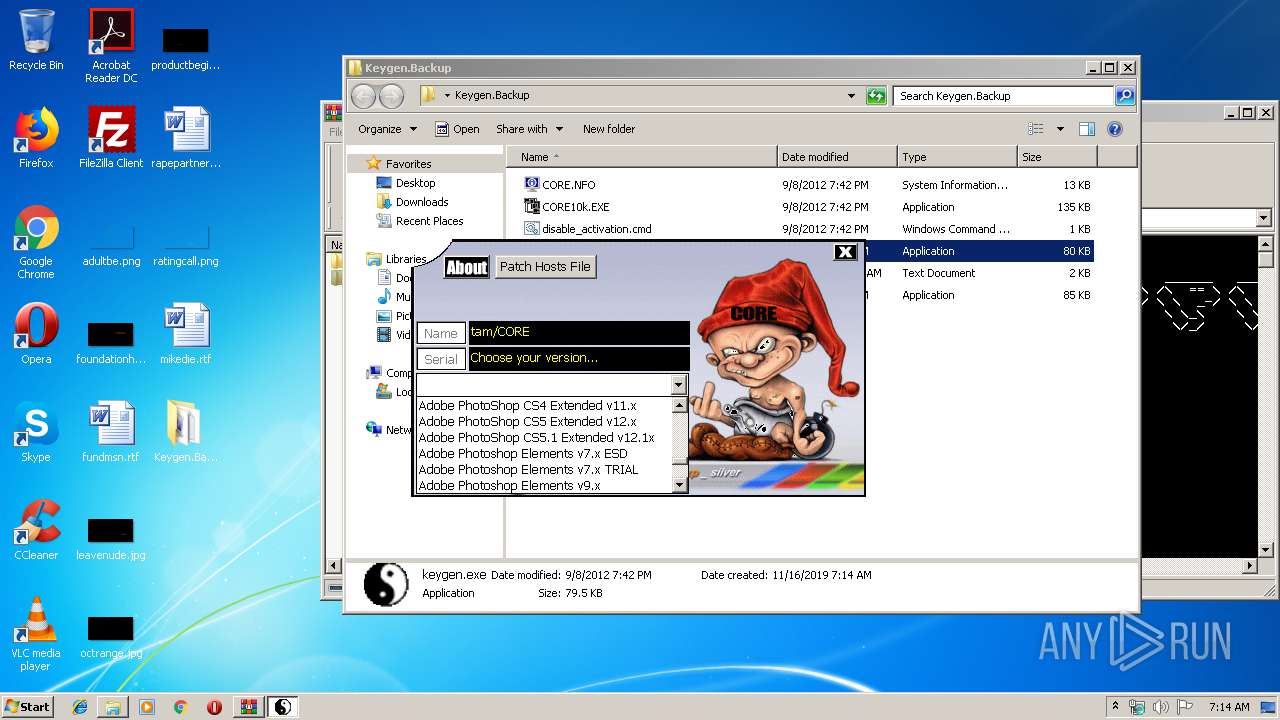
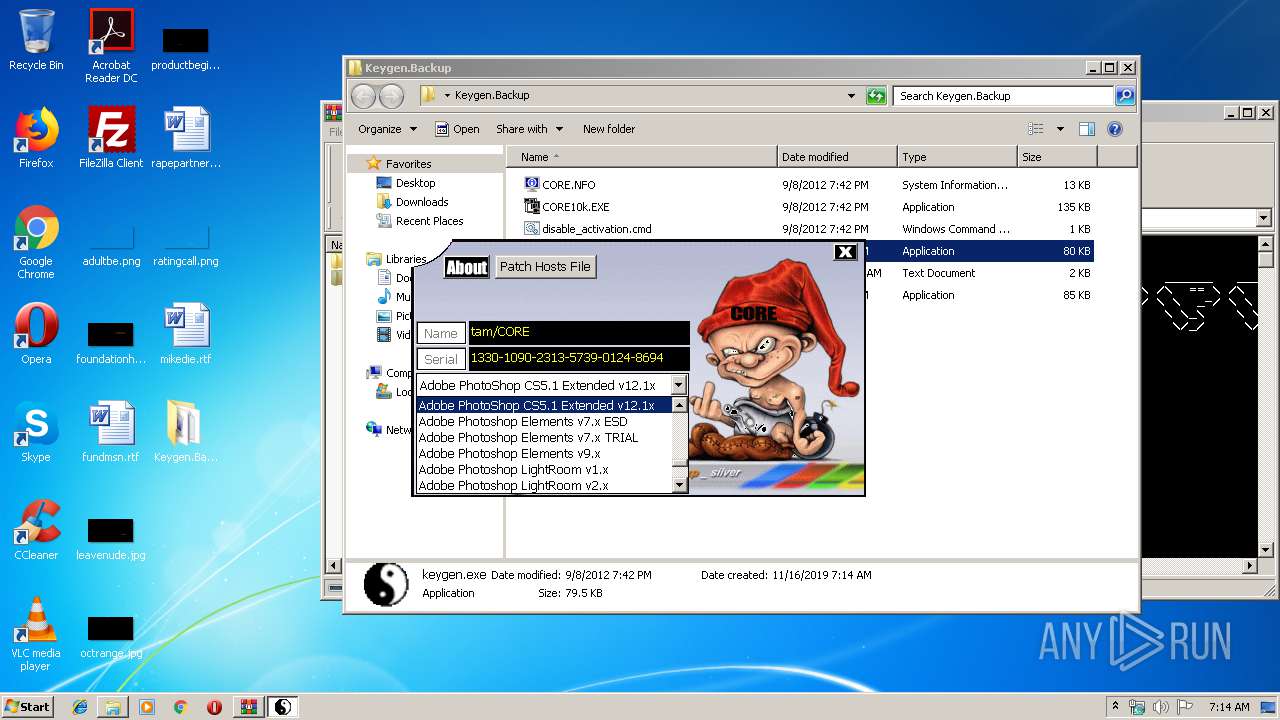
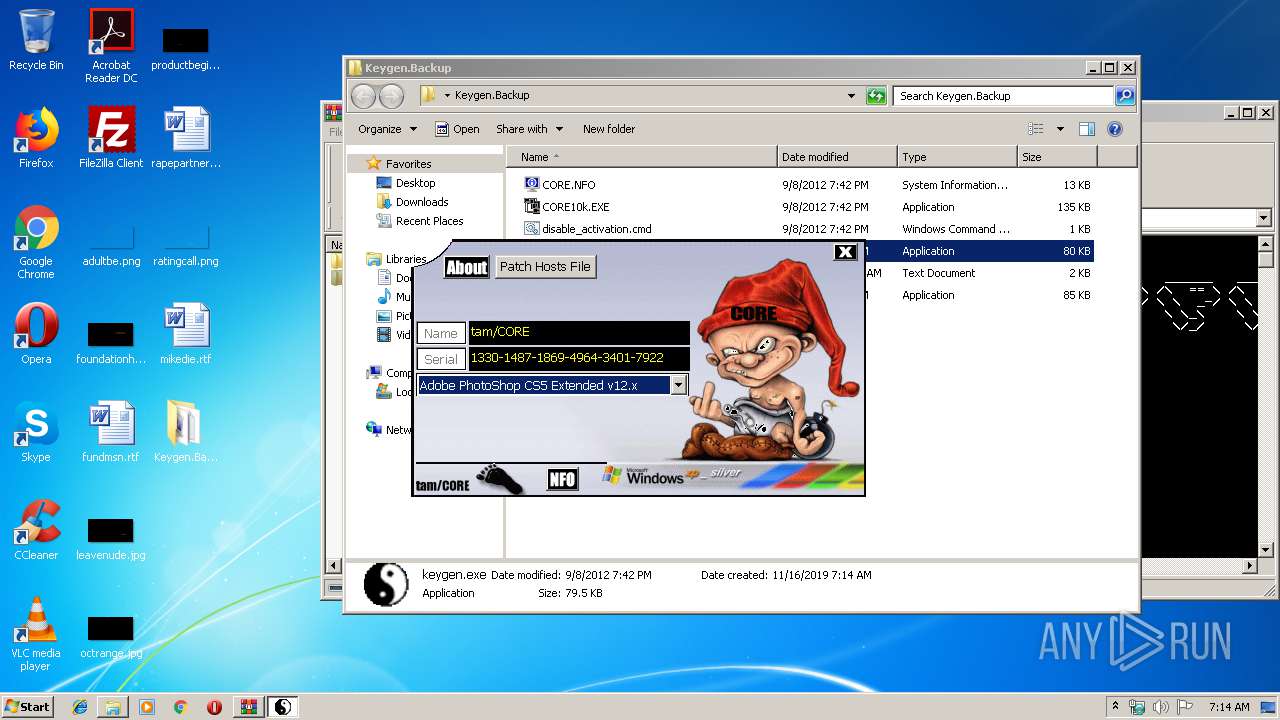
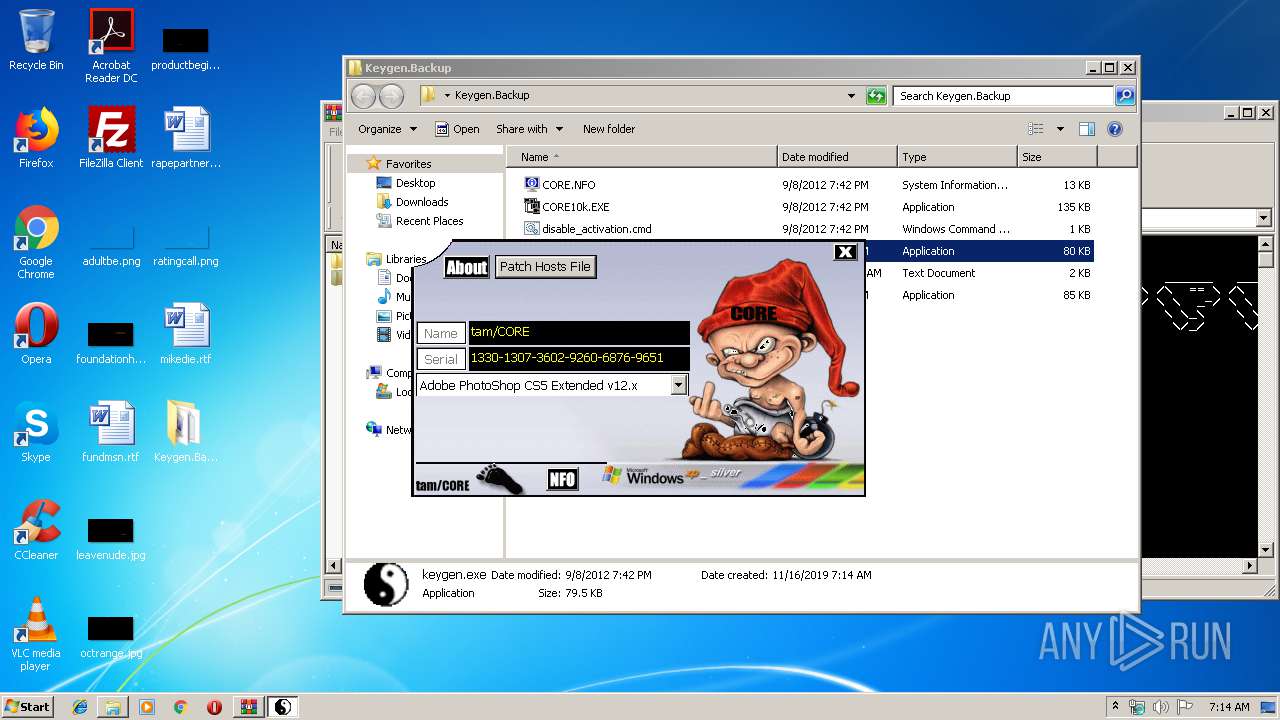
| File name: | Keygen.Backup.rar |
| Full analysis: | https://app.any.run/tasks/72485a00-1cff-4d02-85dc-a29d8c7ac2d0 |
| Verdict: | Malicious activity |
| Analysis date: | November 16, 2019, 07:13:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32, flags: RecoveryRecordPresent |
| MD5: | 546E198D77D0B1C67156536EDF02FE32 |
| SHA1: | 9F9E373583BADDCD37313F13119C194E22045791 |
| SHA256: | 78D03139ED4BA6696B0BF4A854F3EF34370BD864DBF6C549D5A785D4B546006B |
| SSDEEP: | 6144:U6fwpCkxDa609nKgHL40N1sD6ID5FTkoSIR8lNWhm:HwpPxDaogHLtIdqoSI74 |
MALICIOUS
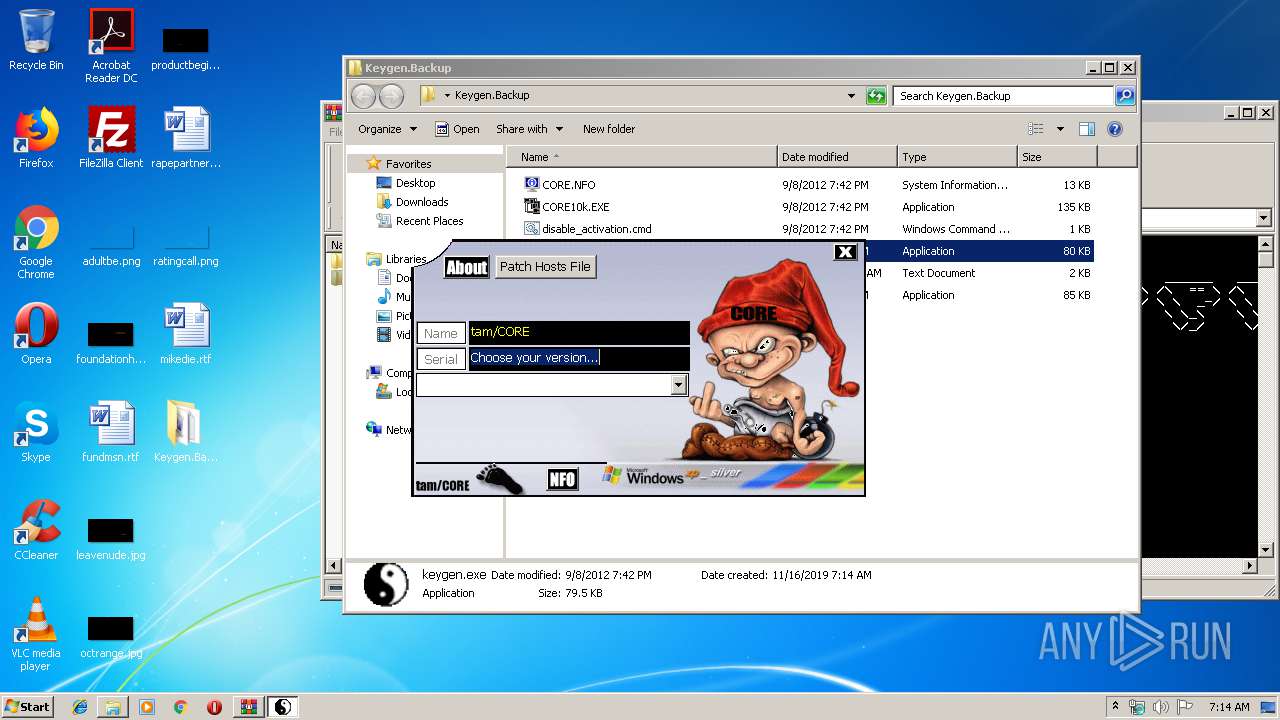
Application was dropped or rewritten from another process
- keygen.exe (PID: 2388)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3016)
INFO
Reads the hosts file
- keygen.exe (PID: 2388)
Manual execution by user
- keygen.exe (PID: 2388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 12562 |
|---|---|
| UncompressedSize: | 12519 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2012:09:08 19:42:00 |
| PackingMethod: | Stored |
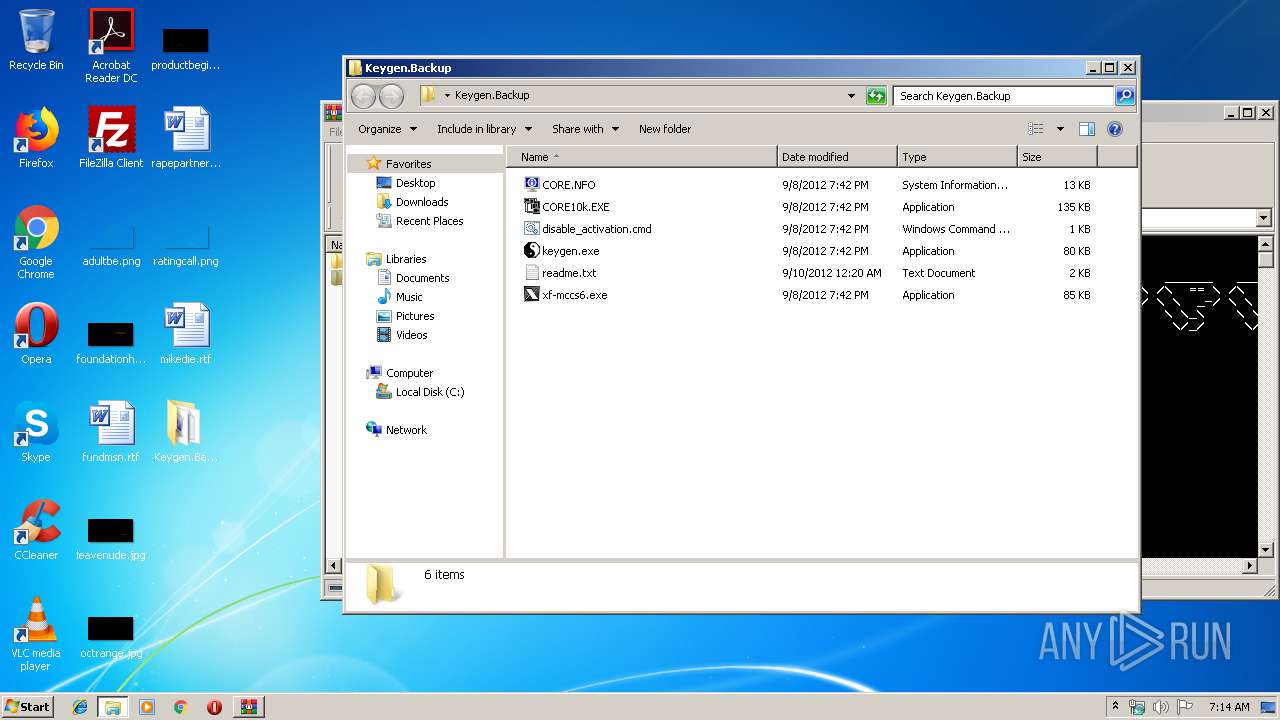
| ArchivedFileName: | Keygen.Backup\CORE.NFO |
Total processes
37
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2388 | "C:\Users\admin\Desktop\Keygen.Backup\keygen.exe" | C:\Users\admin\Desktop\Keygen.Backup\keygen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3016 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Keygen.Backup.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
434
Read events
424
Write events
10
Delete events
0
Modification events
| (PID) Process: | (3016) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3016) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3016) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3016) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Keygen.Backup.rar | |||
| (PID) Process: | (3016) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3016) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3016) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3016) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3016) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
3
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3016 | WinRAR.exe | C:\Users\admin\Desktop\Keygen.Backup\CORE.NFO | text | |
MD5:— | SHA256:— | |||
| 3016 | WinRAR.exe | C:\Users\admin\Desktop\Keygen.Backup\disable_activation.cmd | text | |
MD5:05F4F2EFF4C3A025E99233B653EDC260 | SHA256:53FF64DCDACAC89544E19E2B52DBF2FFCBB5E45614CF5D1502F5F8E77E862066 | |||
| 3016 | WinRAR.exe | C:\Users\admin\Desktop\Keygen.Backup\readme.txt | text | |
MD5:— | SHA256:— | |||
| 3016 | WinRAR.exe | C:\Users\admin\Desktop\Keygen.Backup\CORE10k.EXE | executable | |
MD5:D581068E84510083DDEA45E821EBDE36 | SHA256:FA04F7F08277B74677628A224A096D4B9FE4CAFB7EFF9F9D92E2AD776085959D | |||
| 3016 | WinRAR.exe | C:\Users\admin\Desktop\Keygen.Backup\xf-mccs6.exe | executable | |
MD5:1AF76EF8857935EB1D8E46DC9CFE3729 | SHA256:AC2D47DC2D33E6123DA1F3AB00FEA3A1659CE0F47266CC9AB004FA4B811F3B21 | |||
| 3016 | WinRAR.exe | C:\Users\admin\Desktop\Keygen.Backup\keygen.exe | executable | |
MD5:016B3F3D02B55E6729F7D363DBEA92BC | SHA256:0E89C004A33AA95AD09EFE0E22FF9D424911405E0F7E58D4CD53E4D503D03BF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report