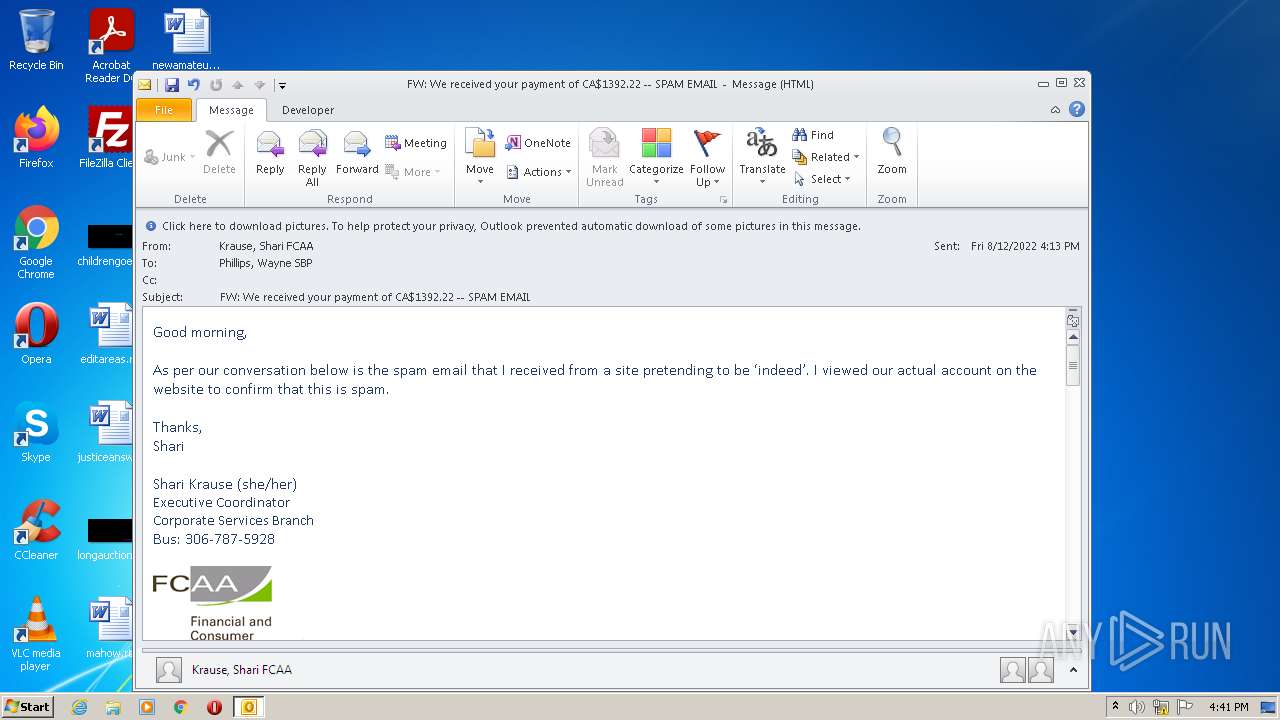
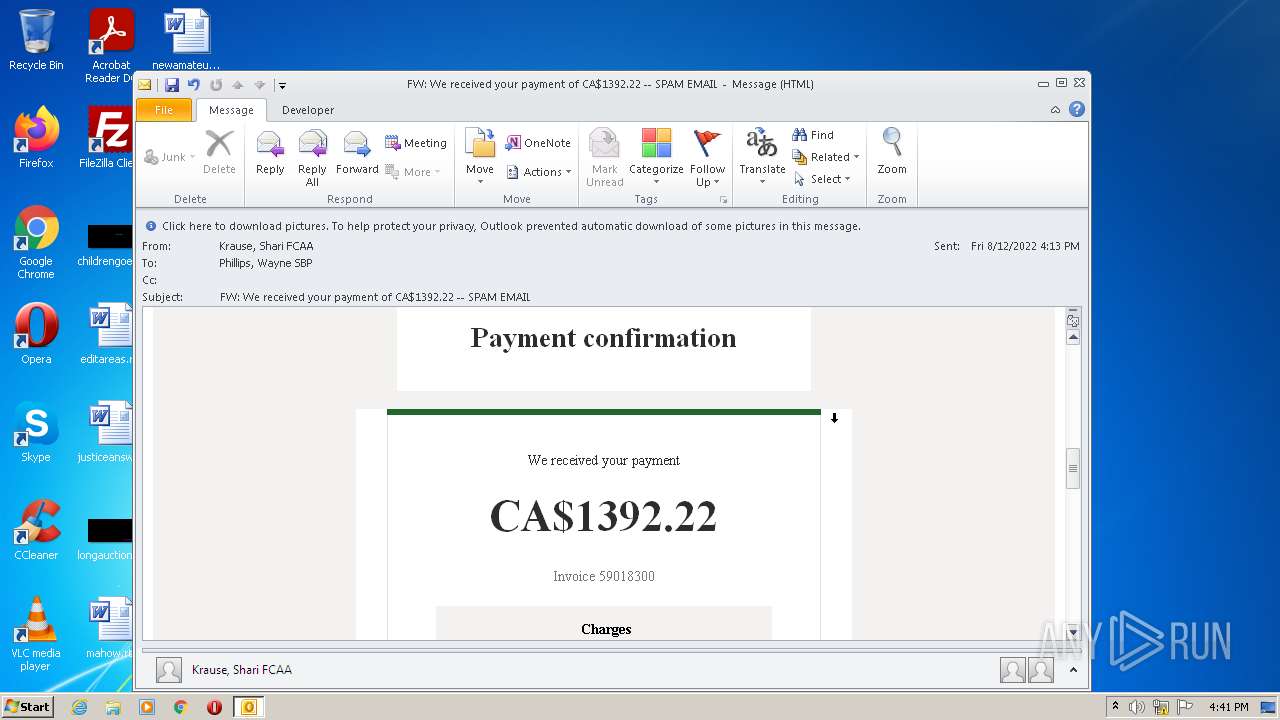
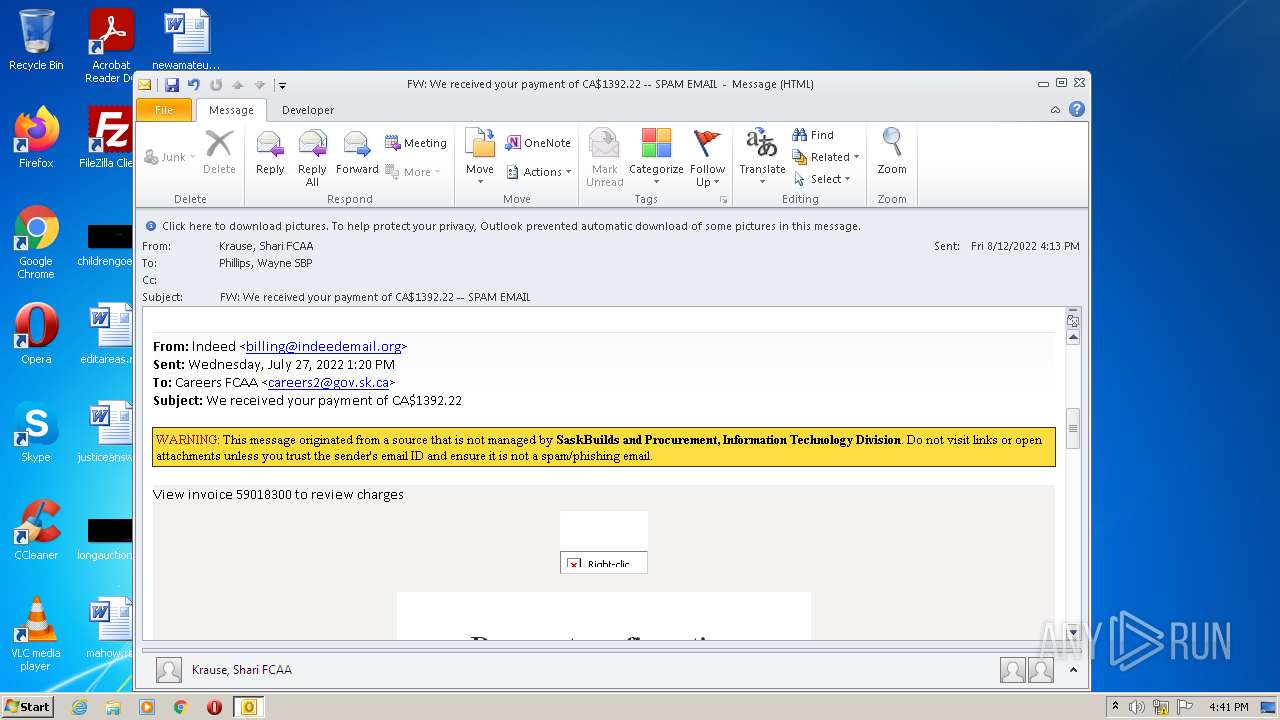
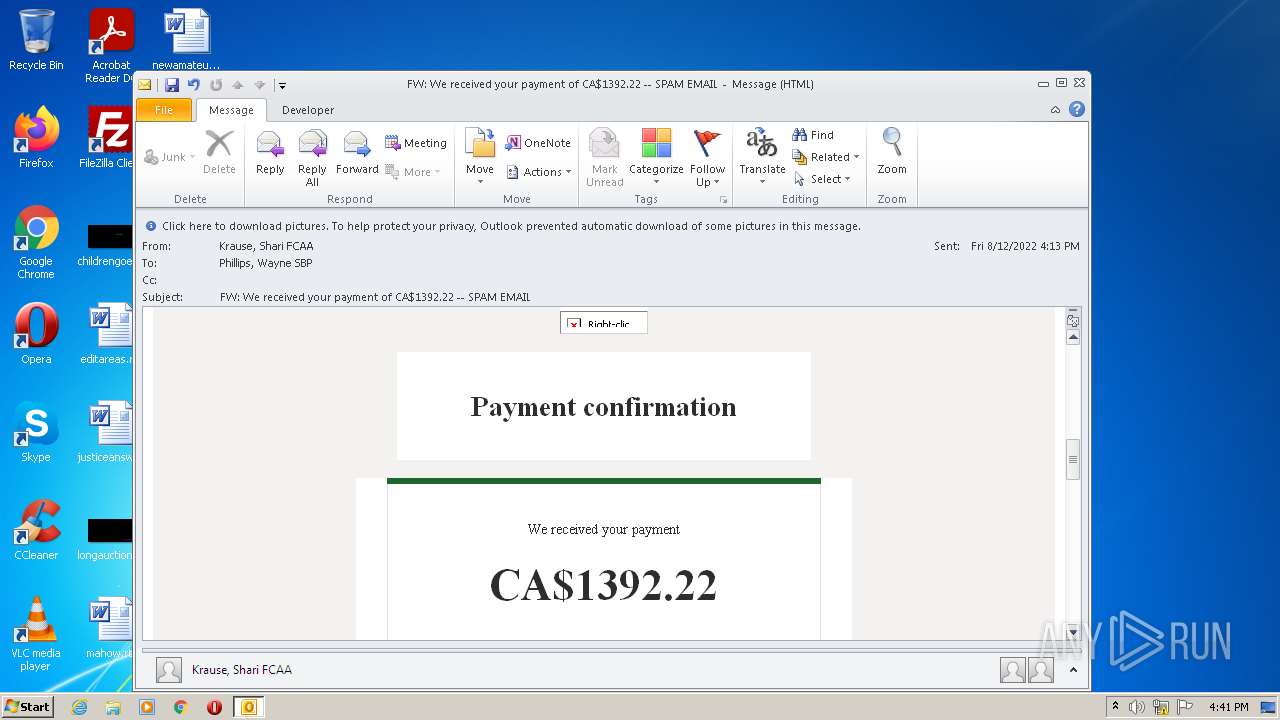
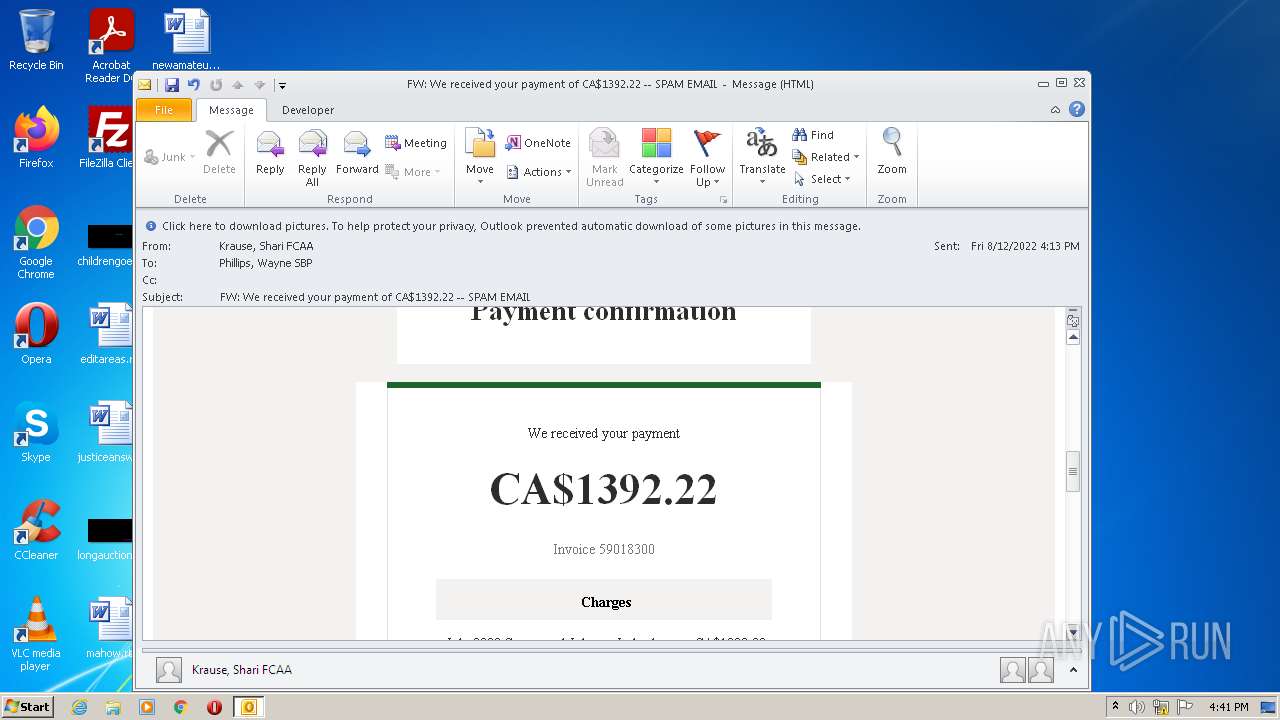
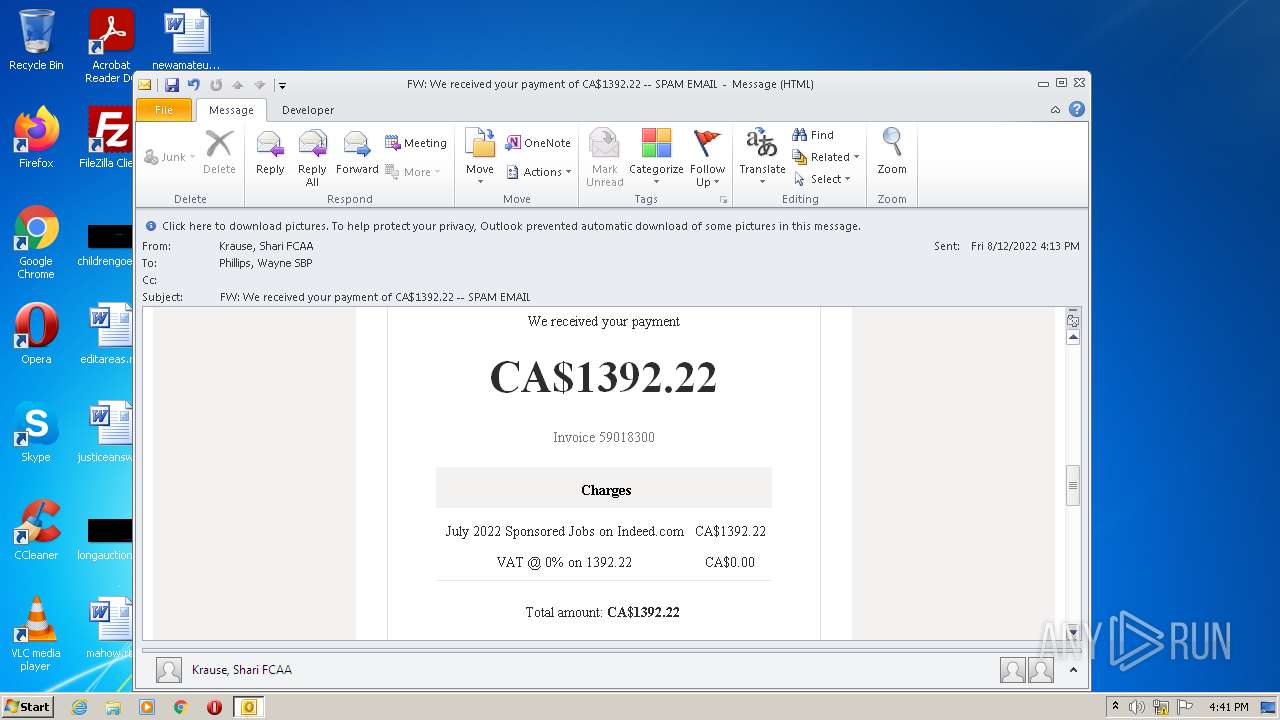
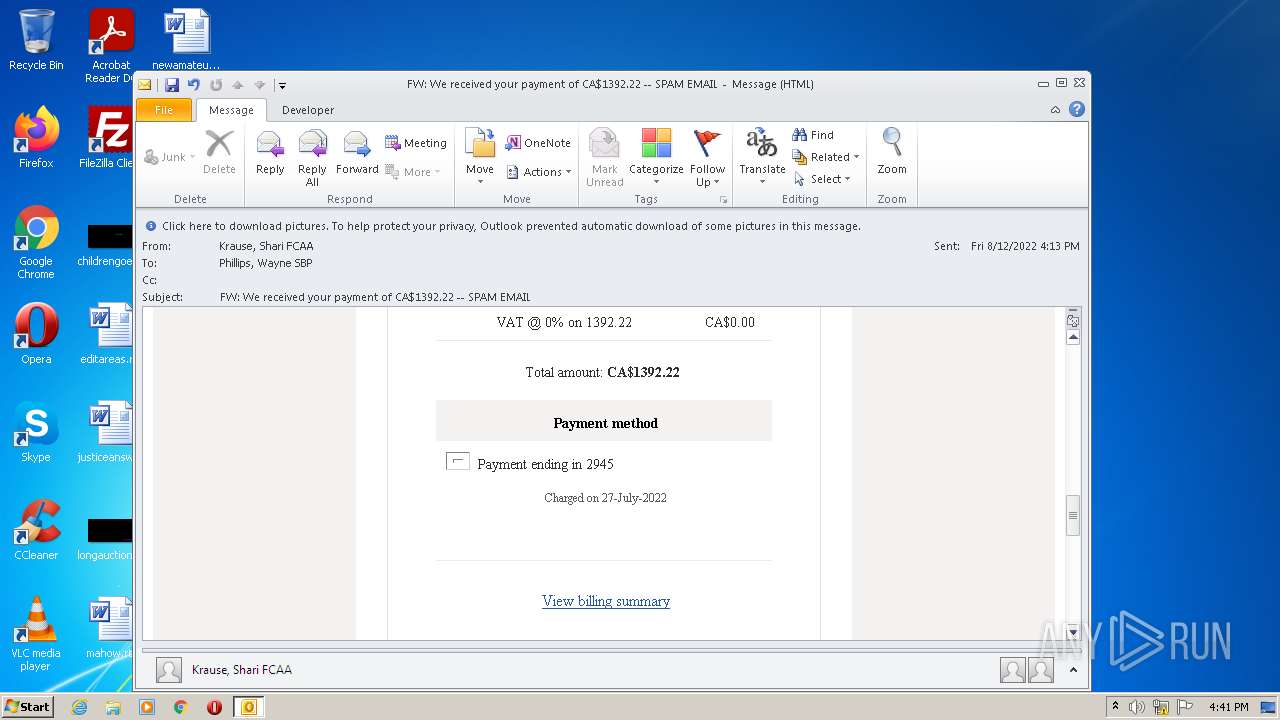
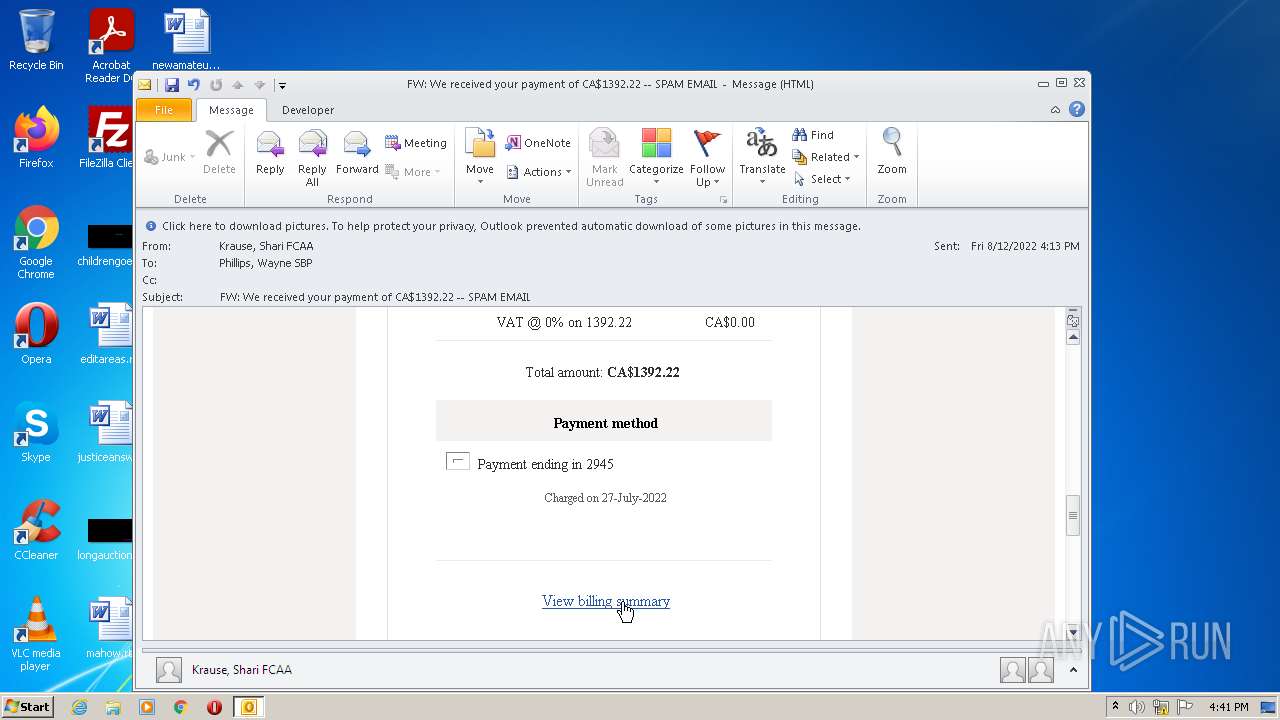
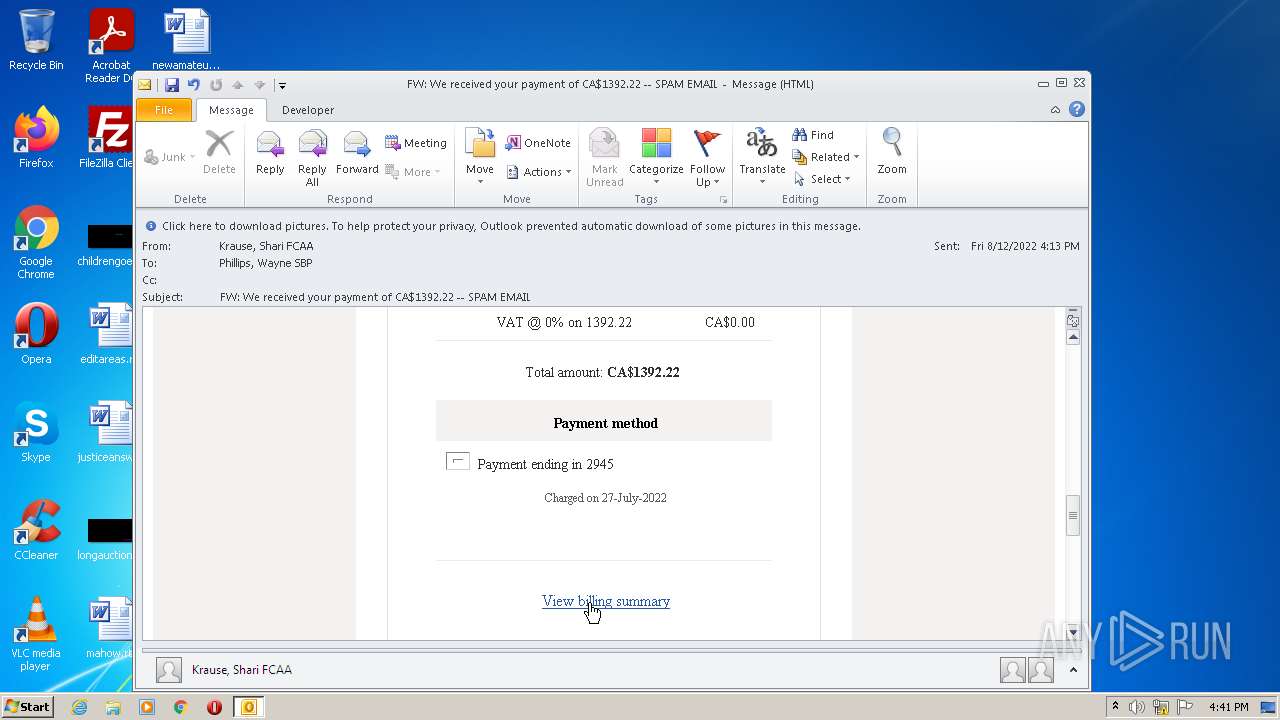
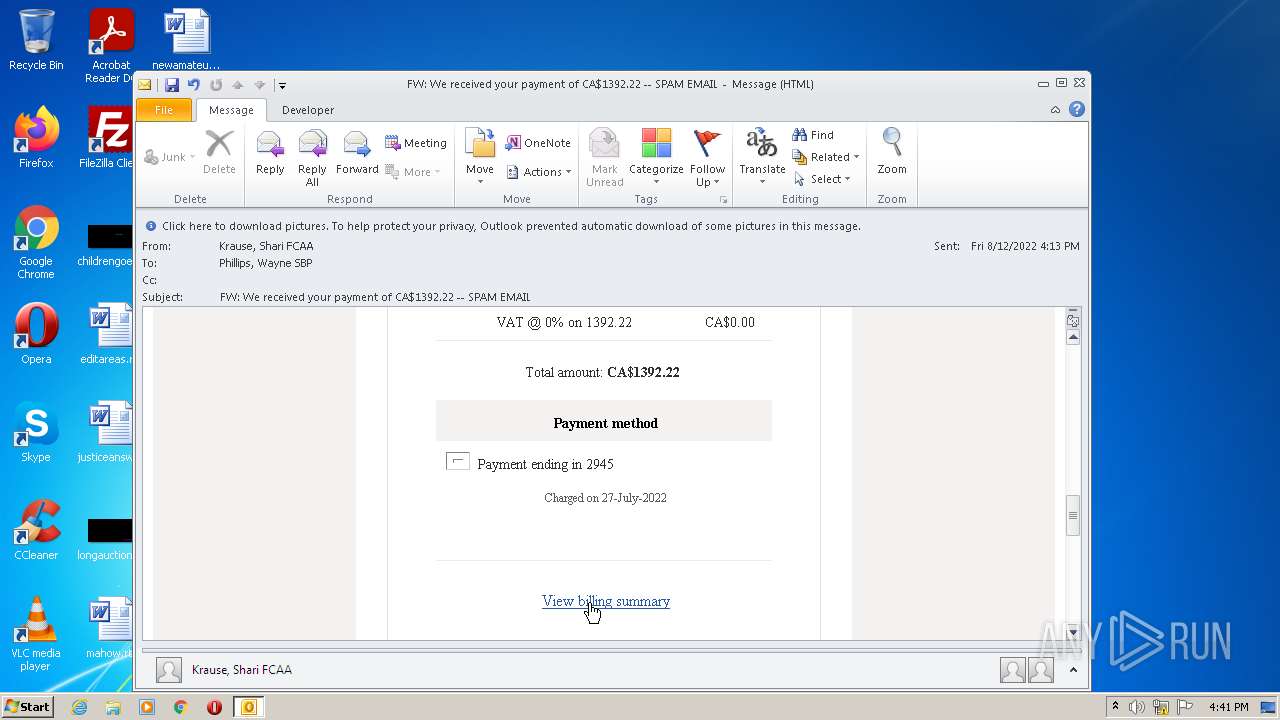
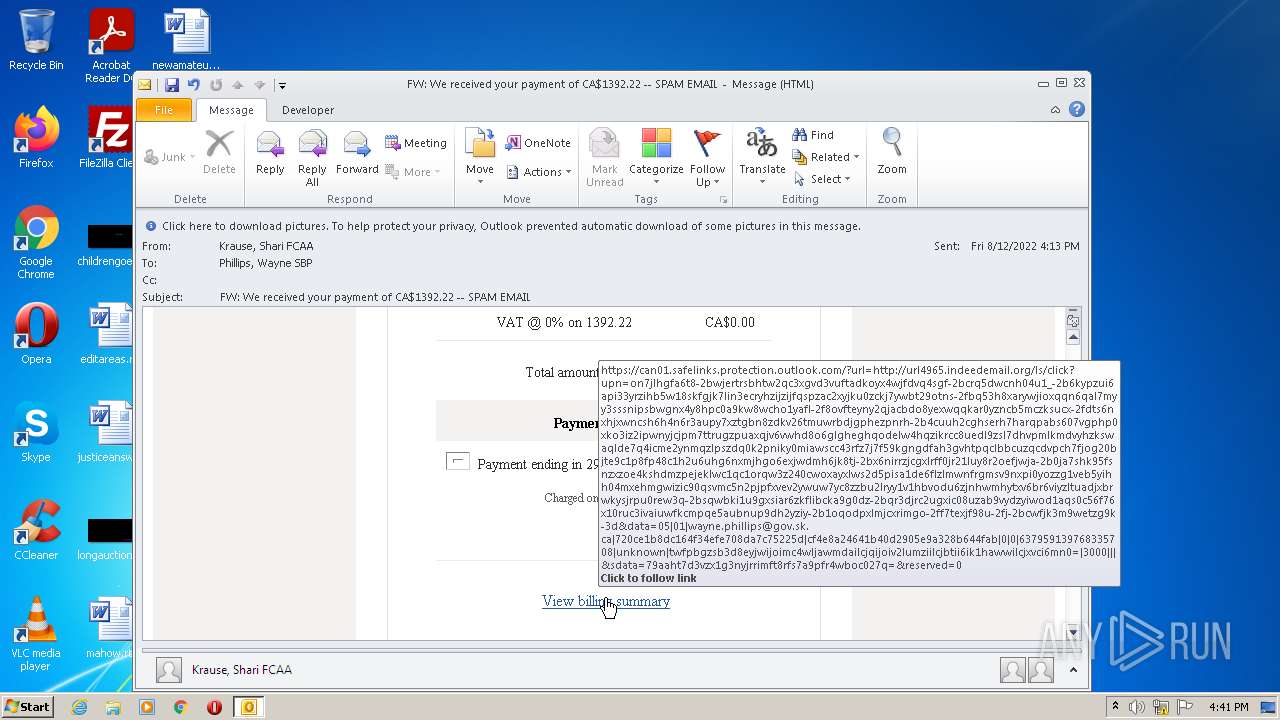
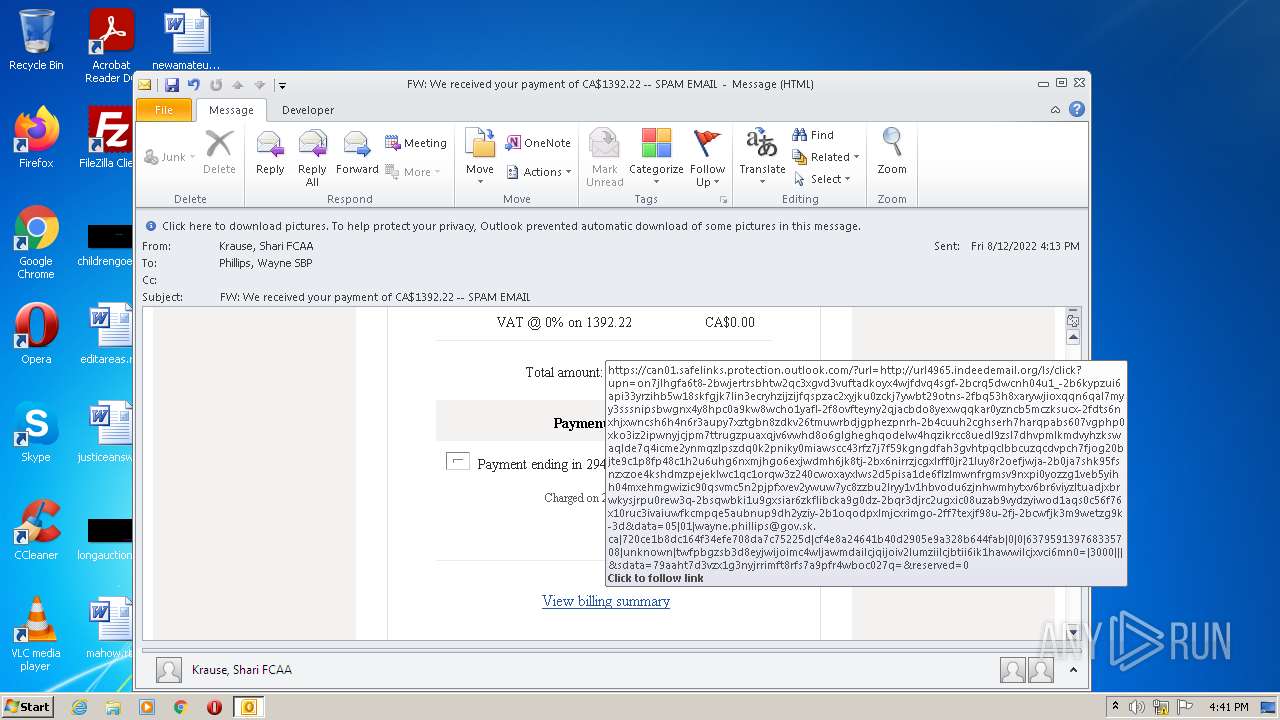
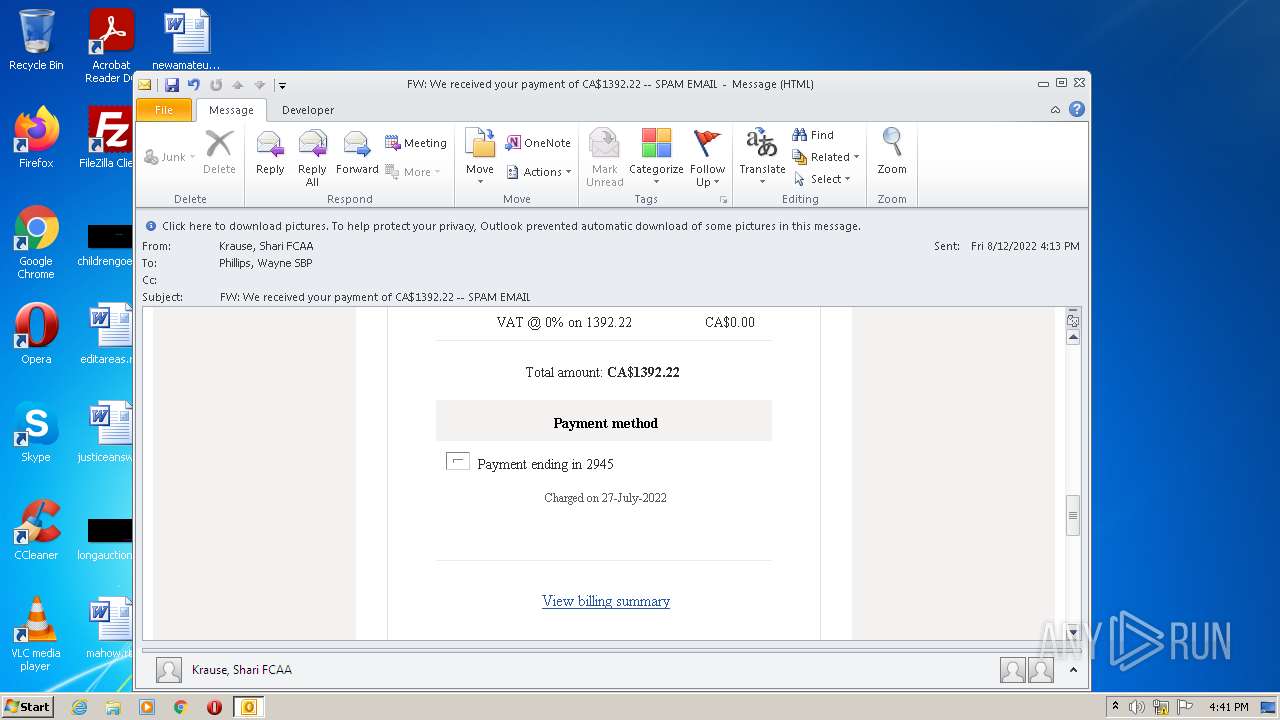
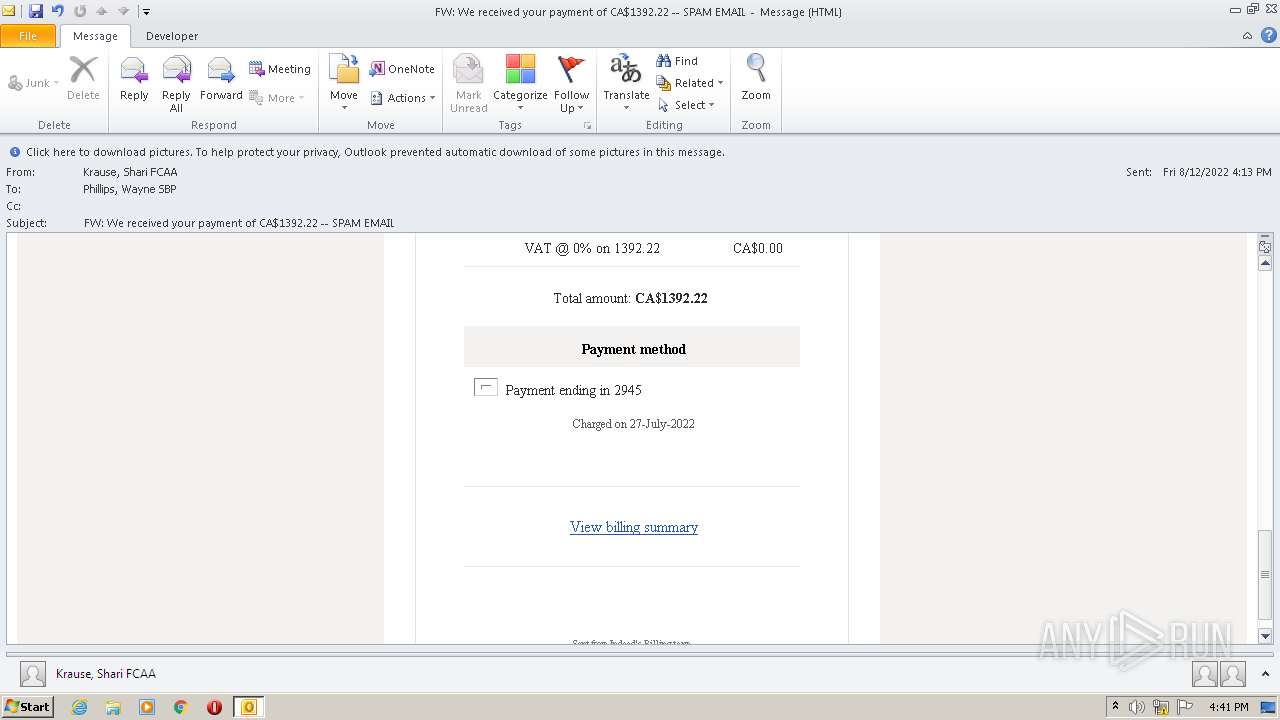
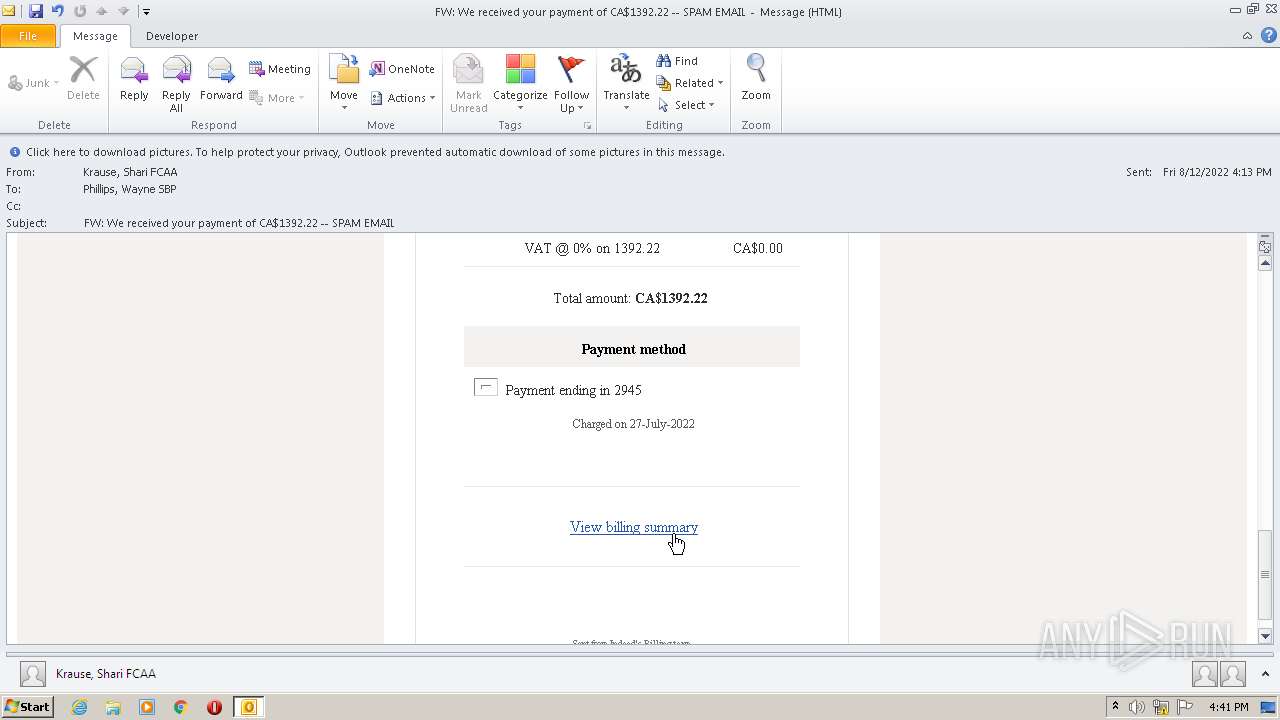
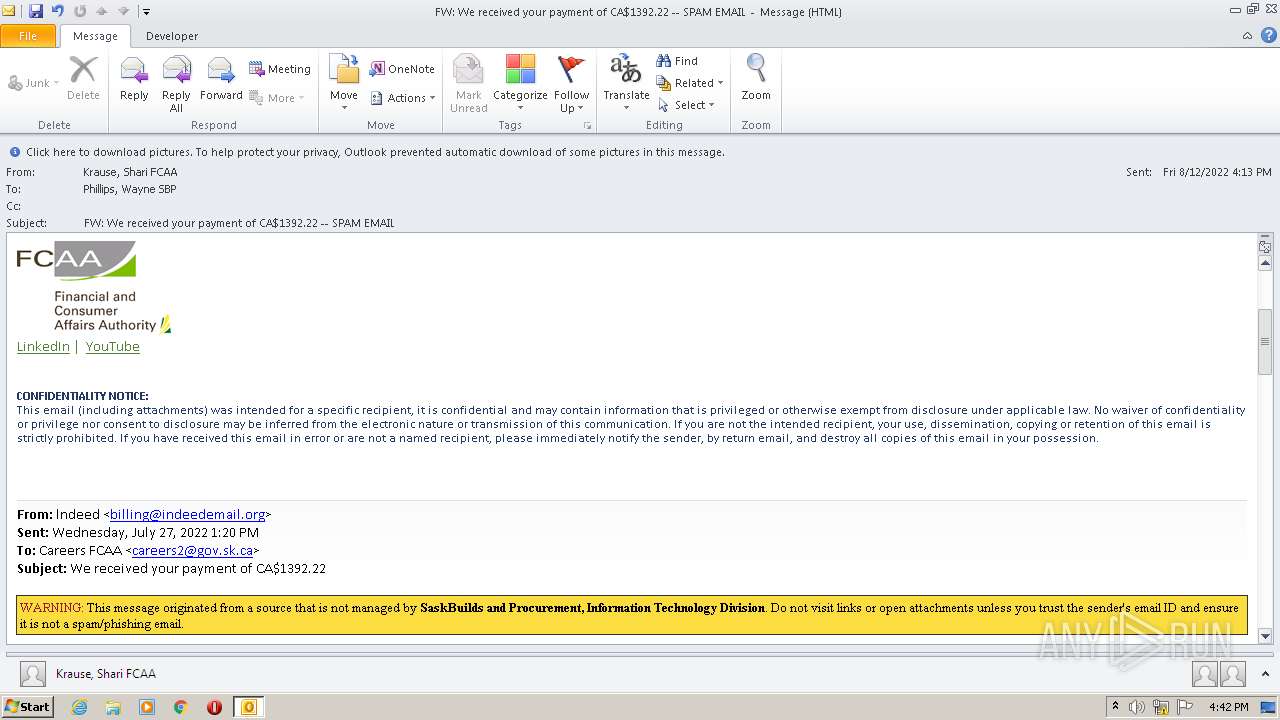
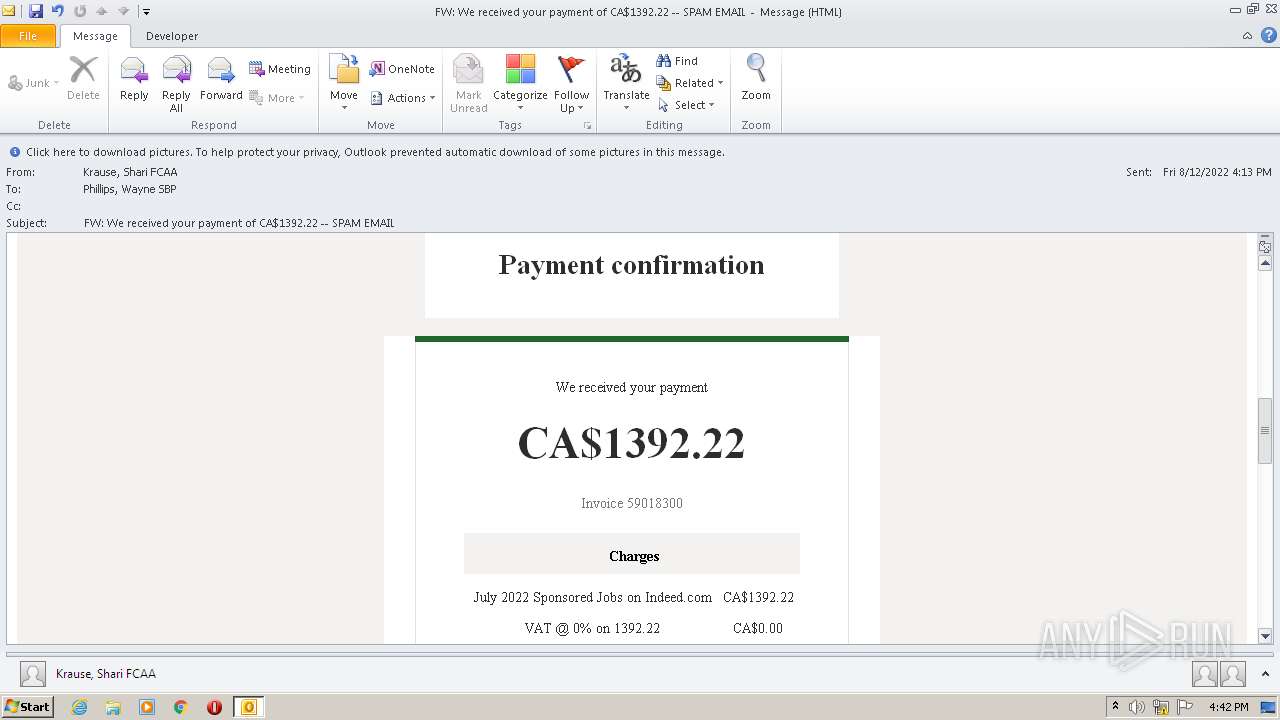
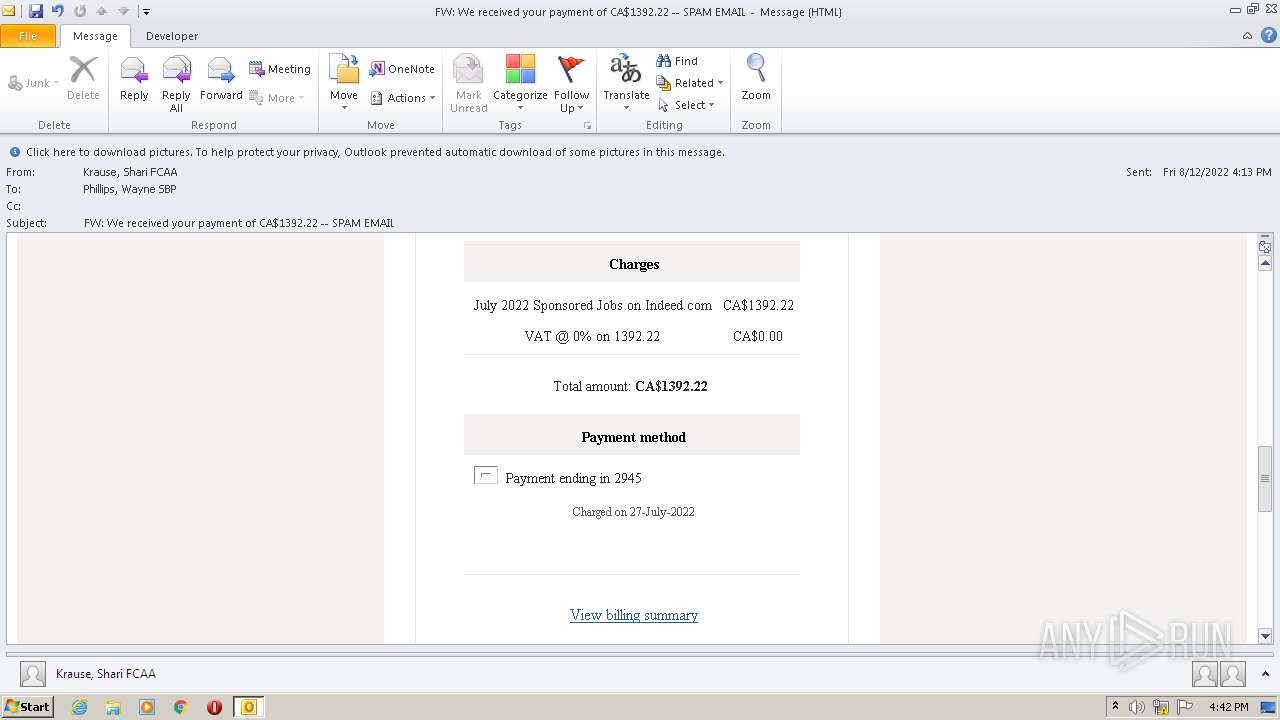
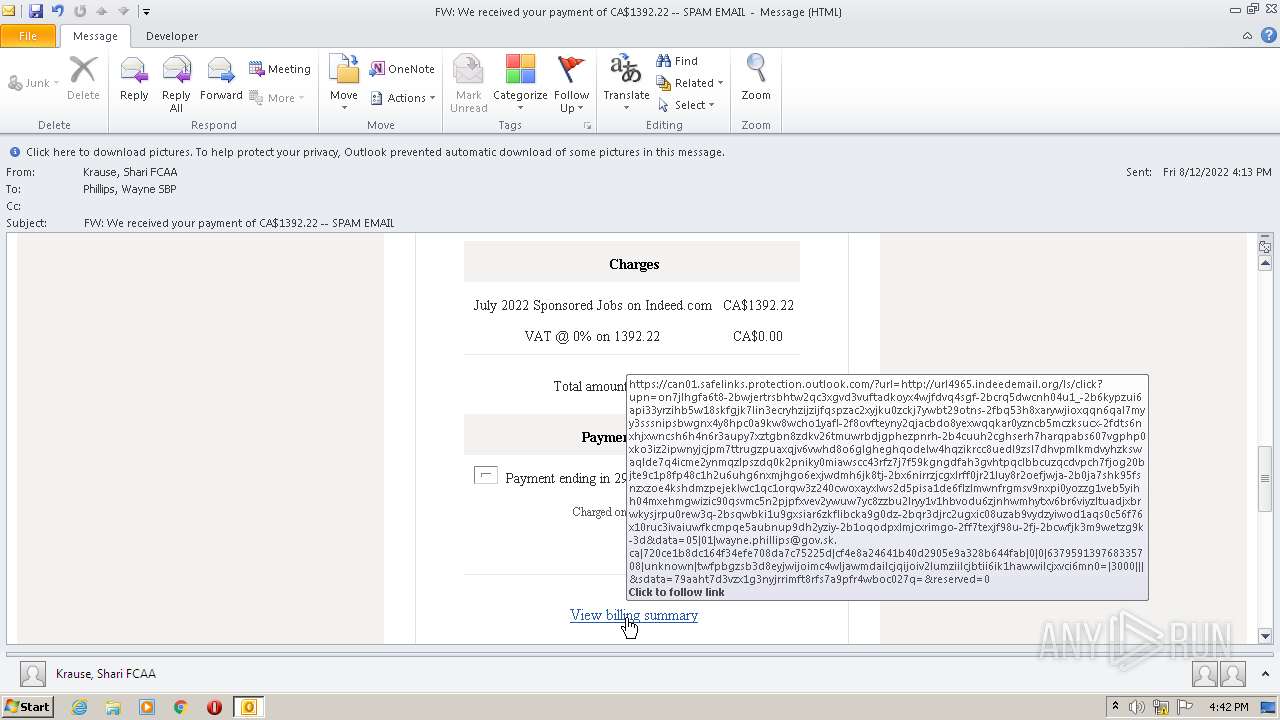
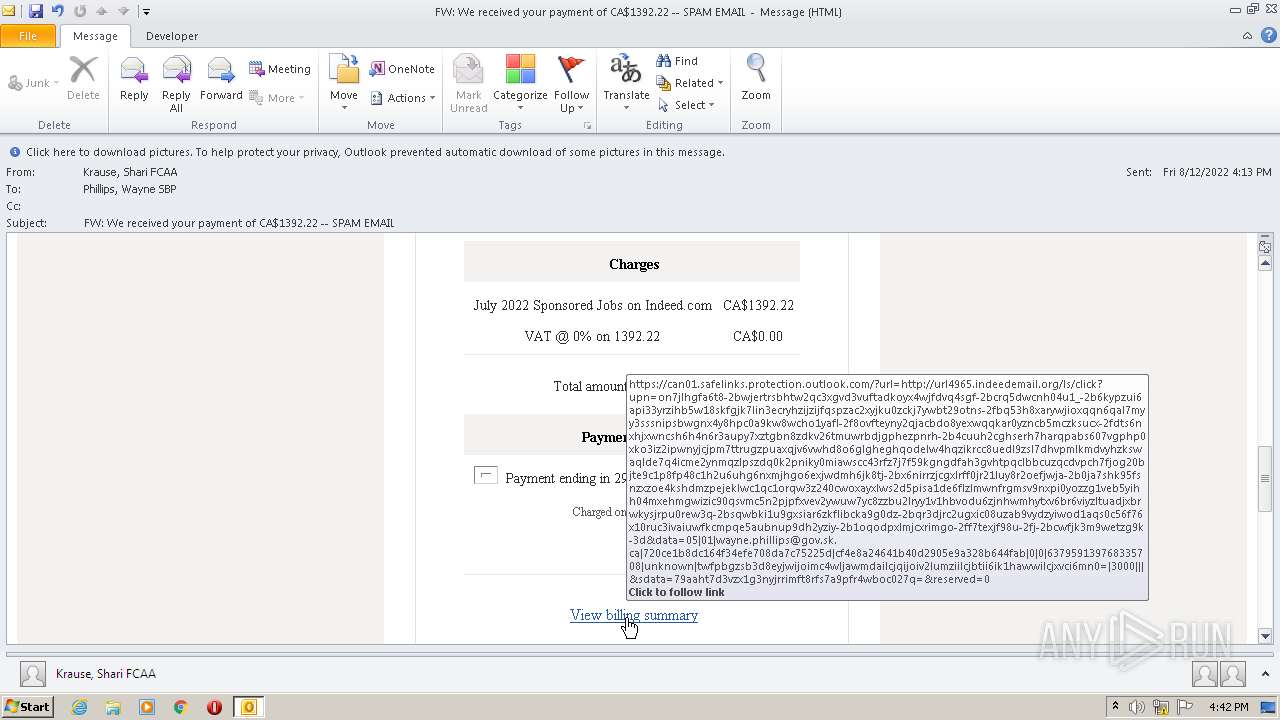
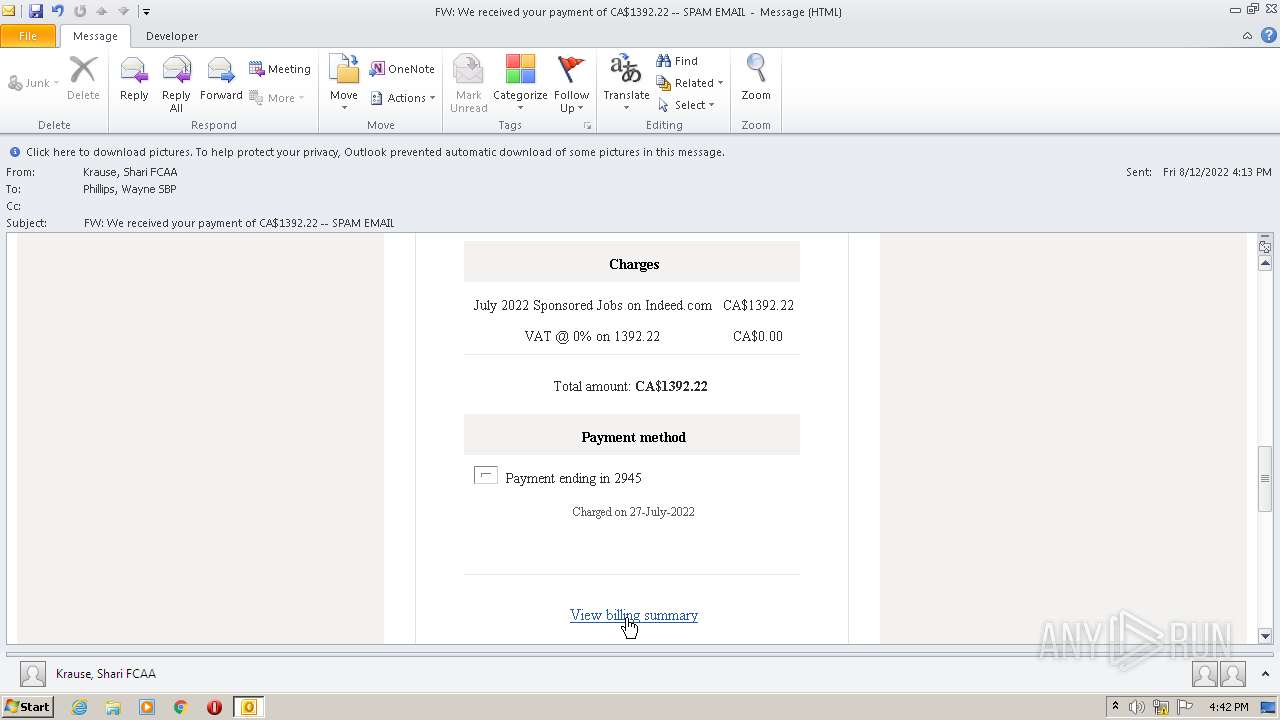
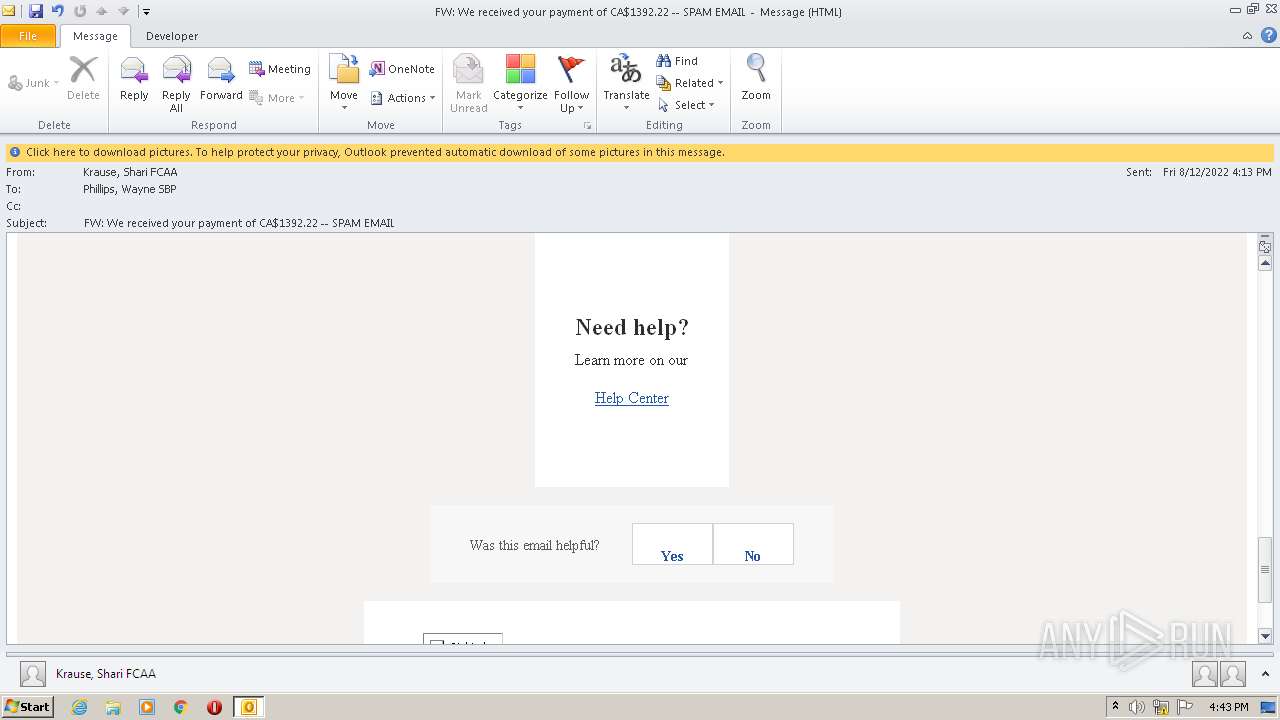
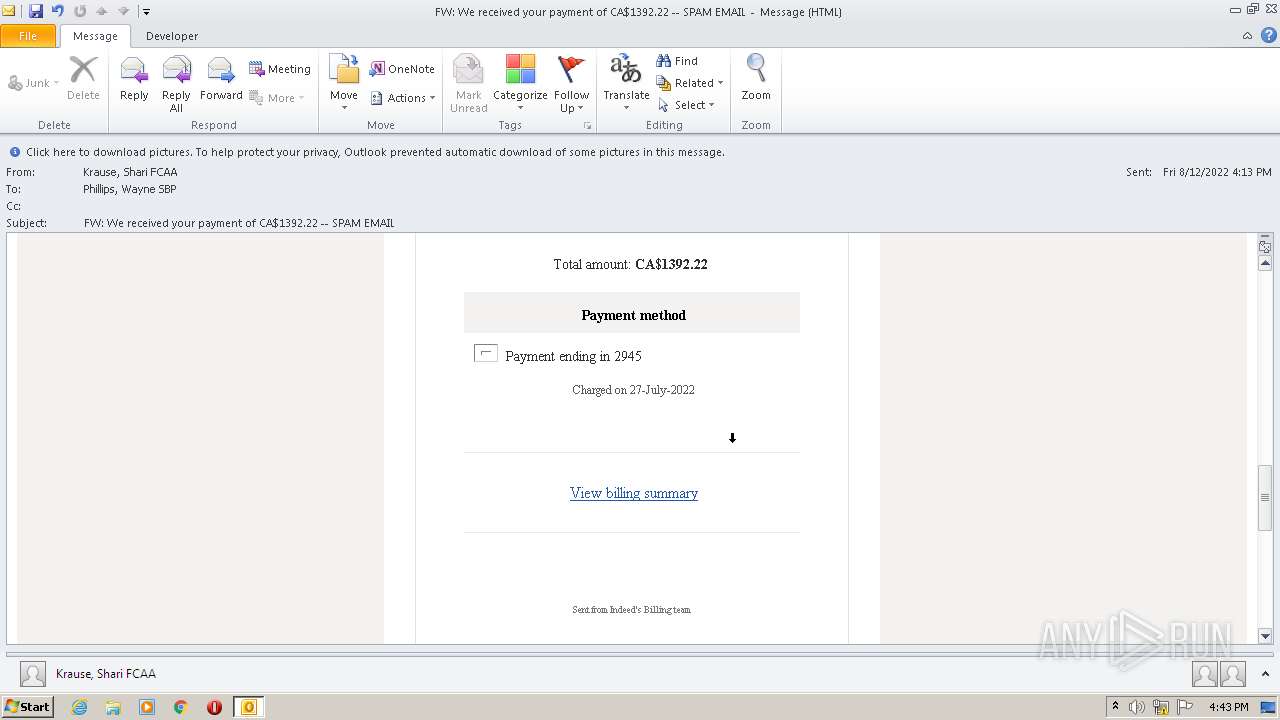
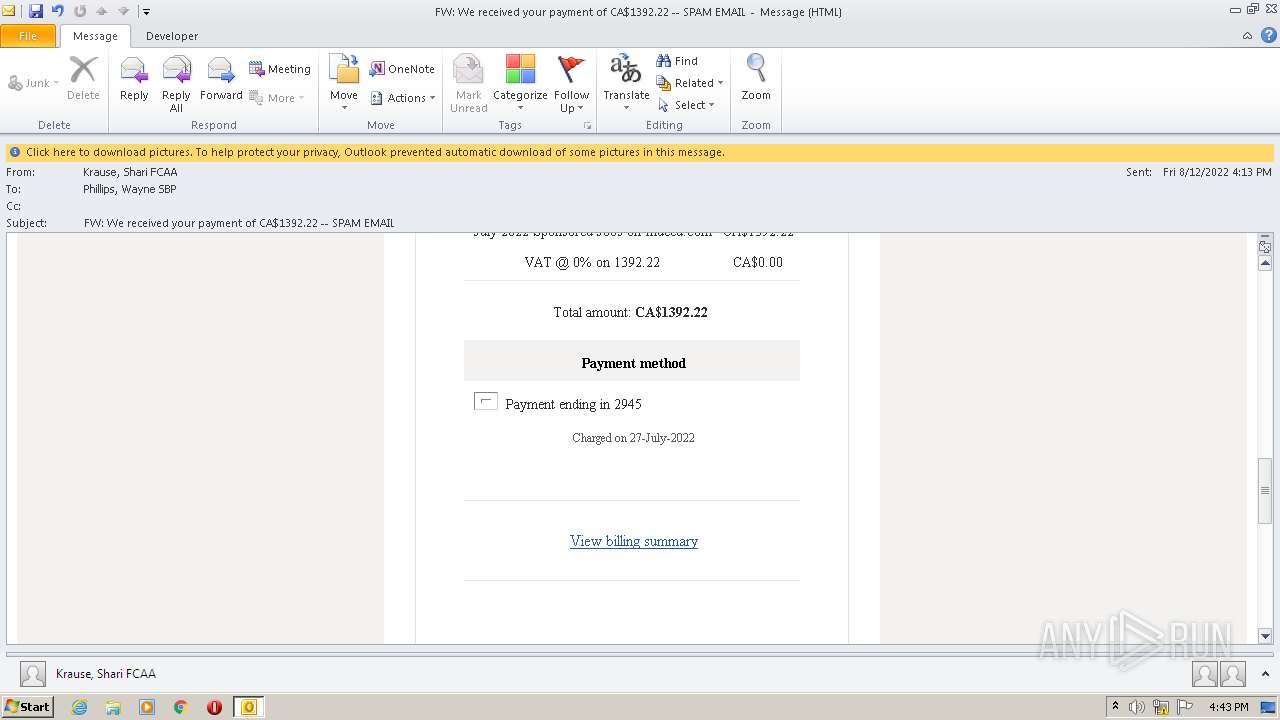
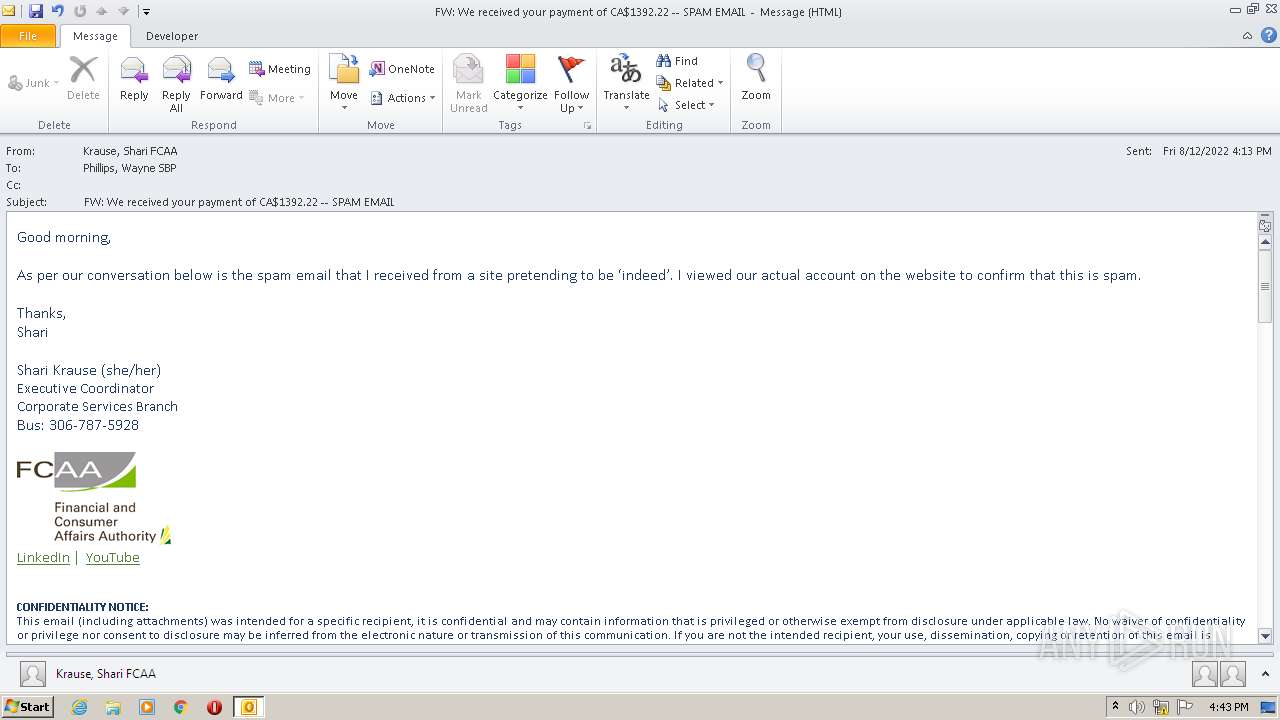
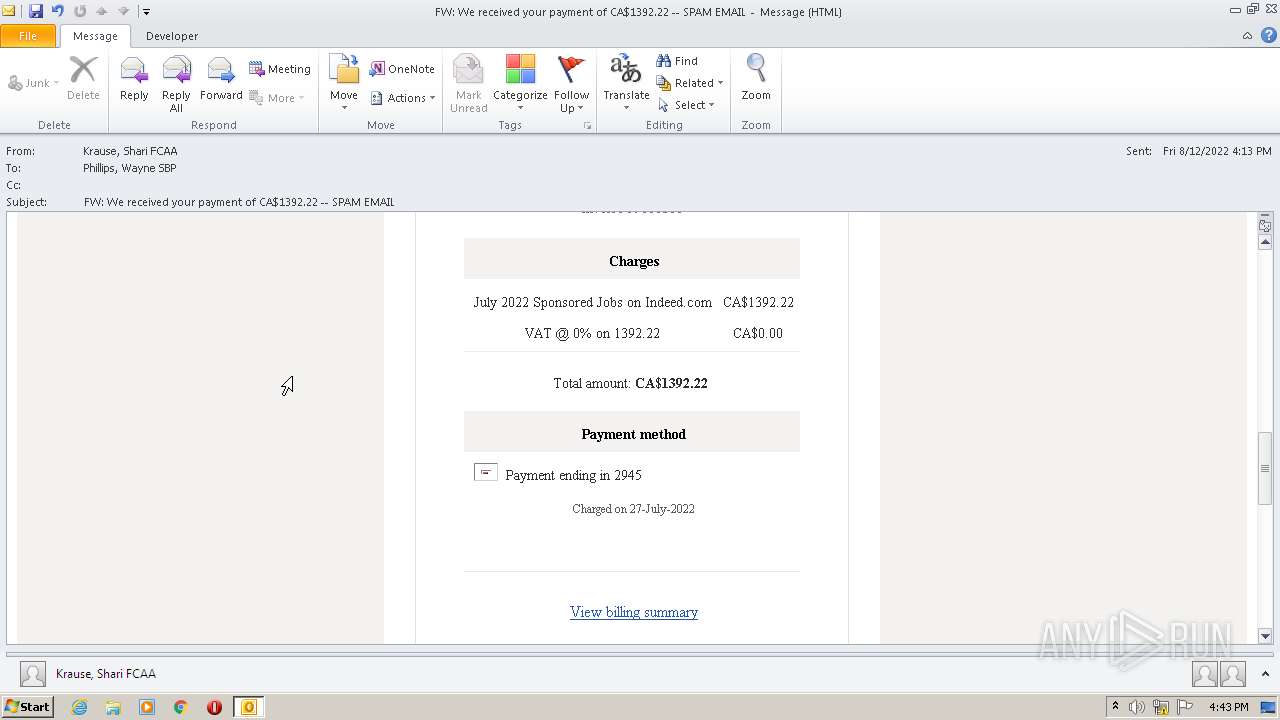
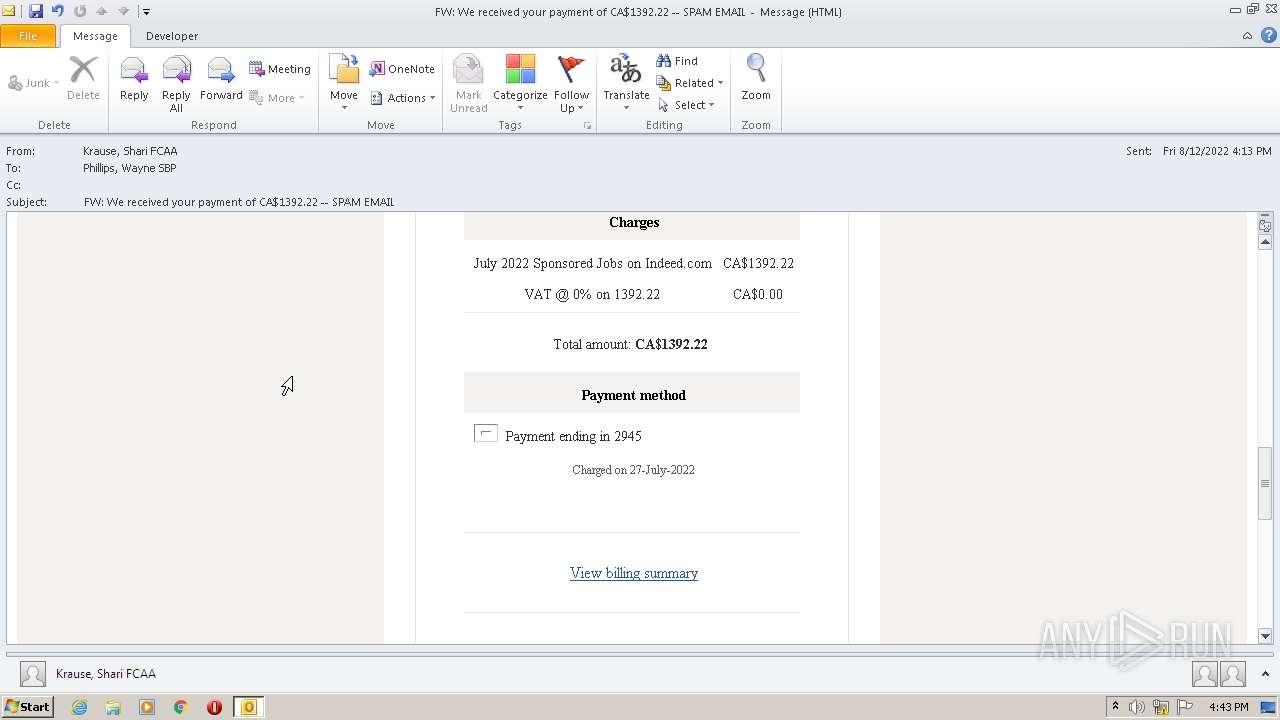
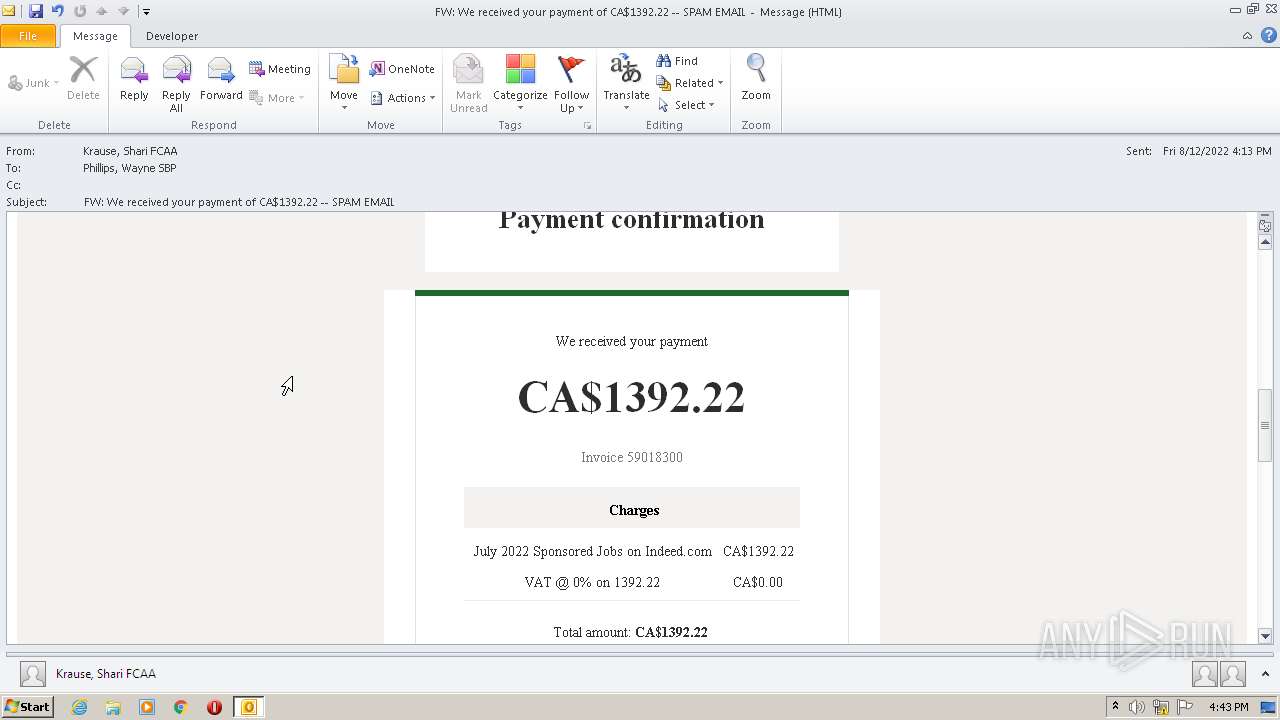
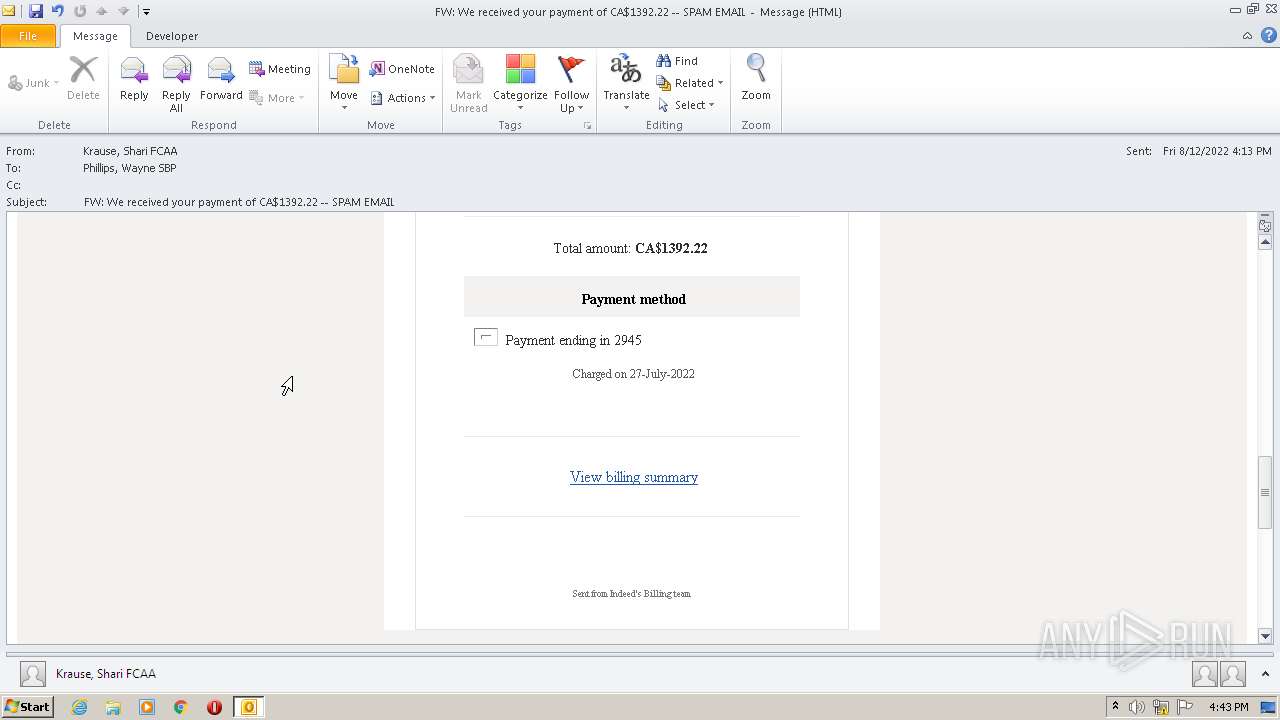
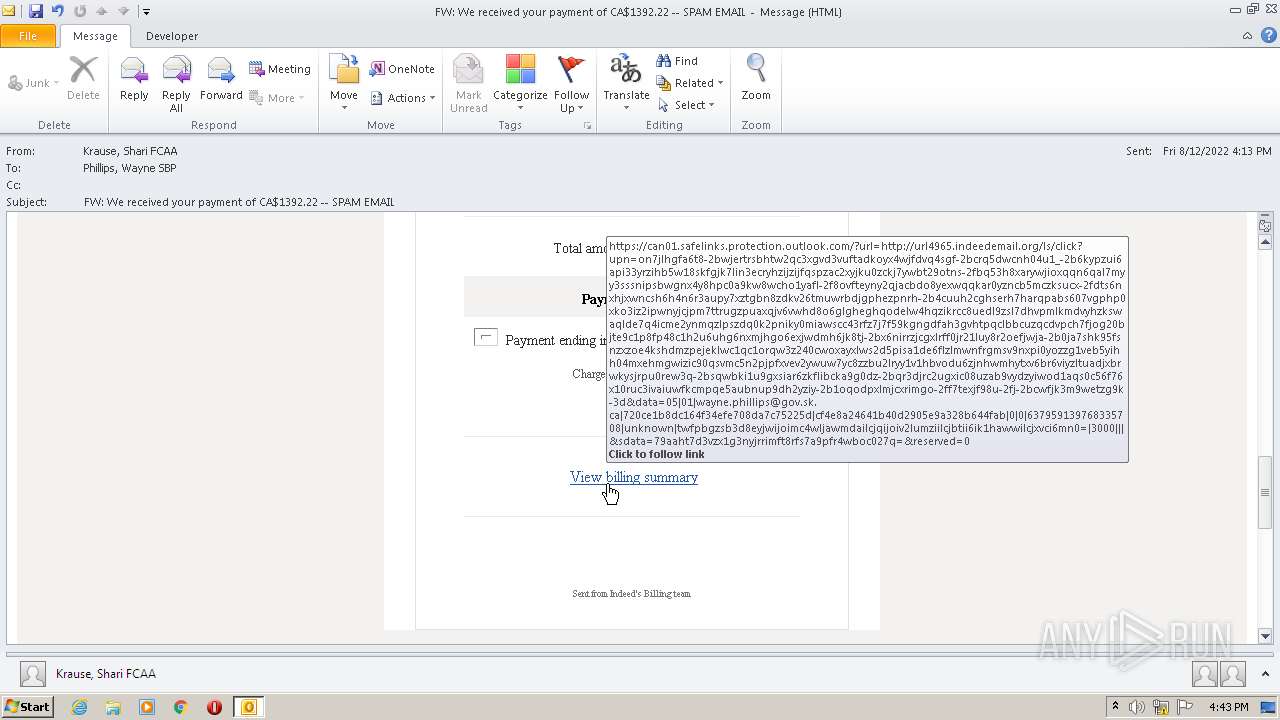
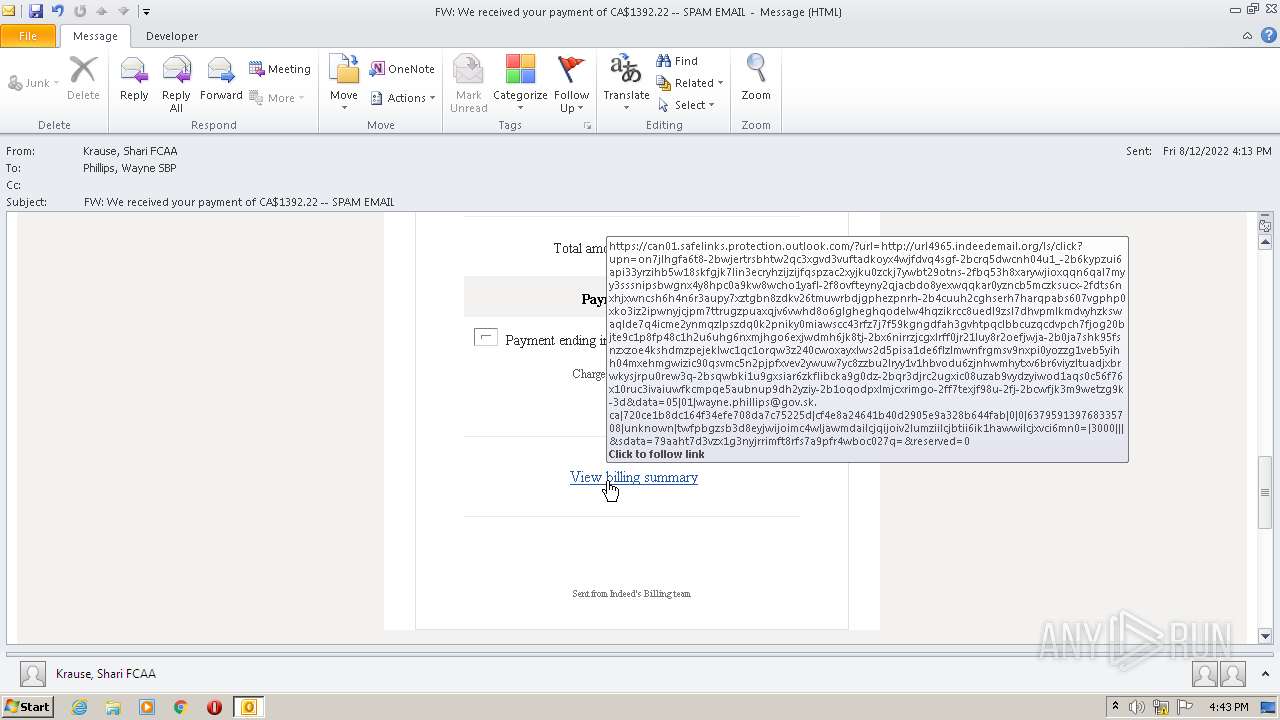
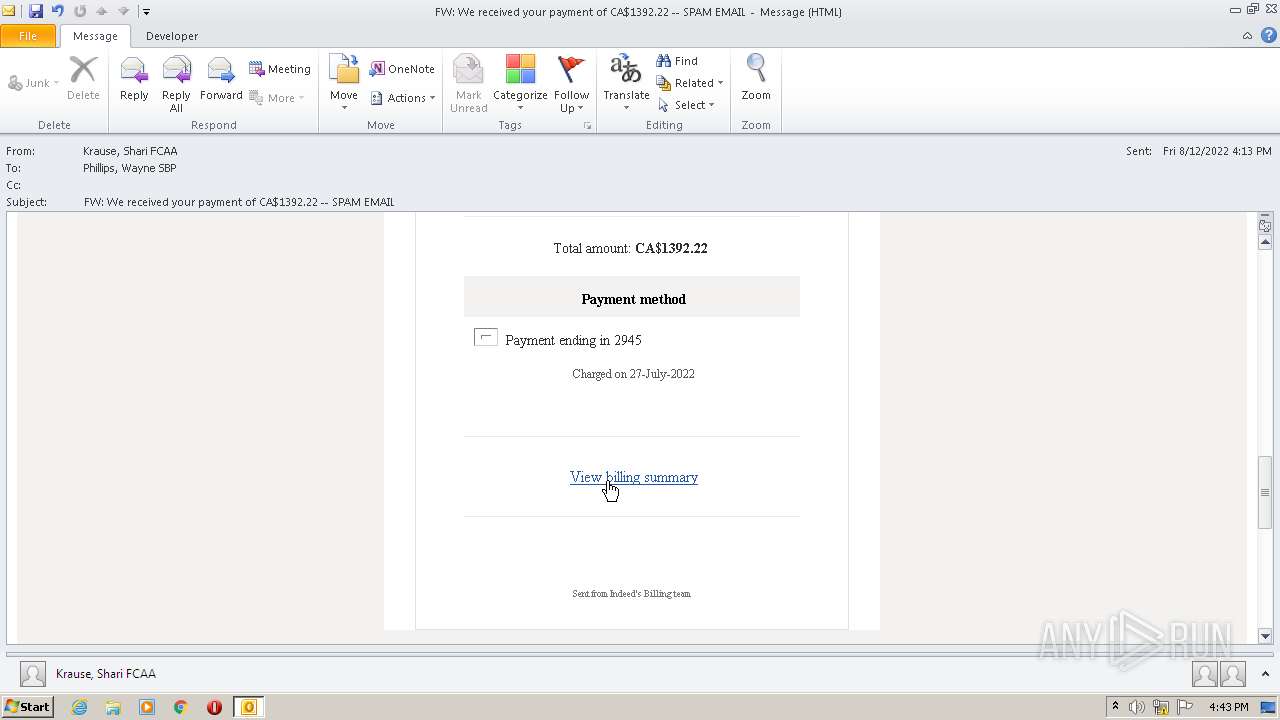
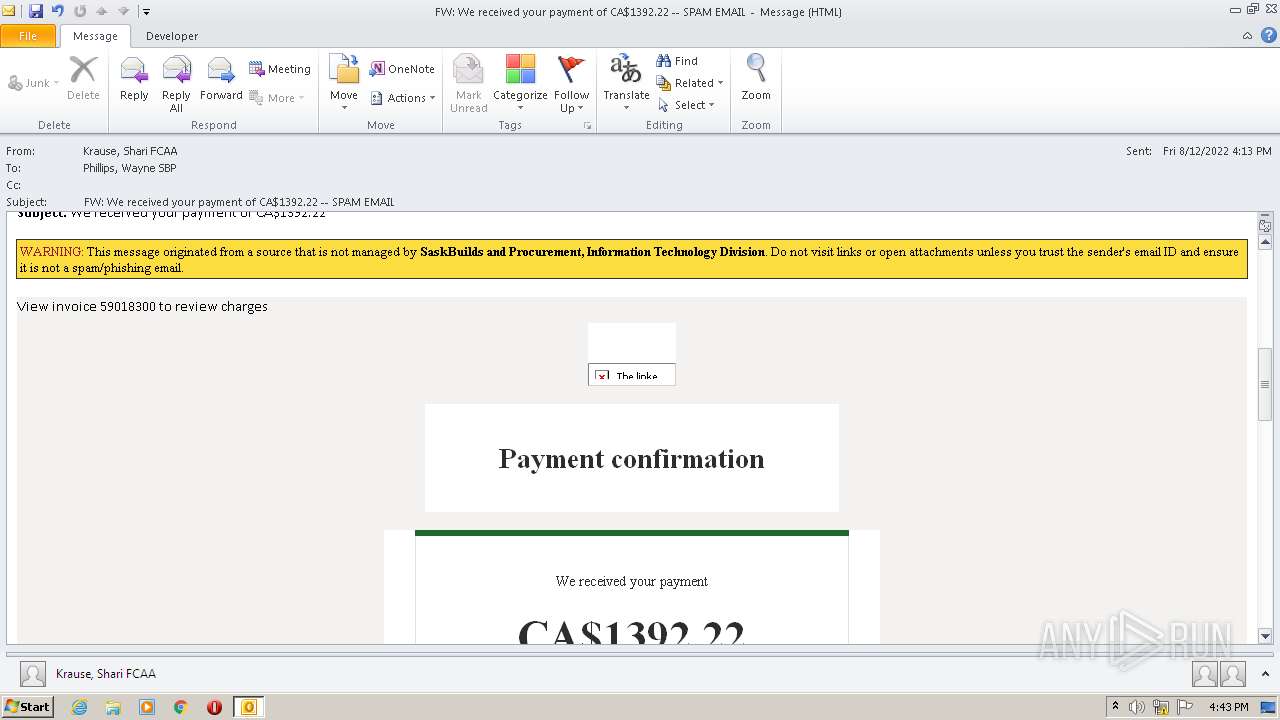
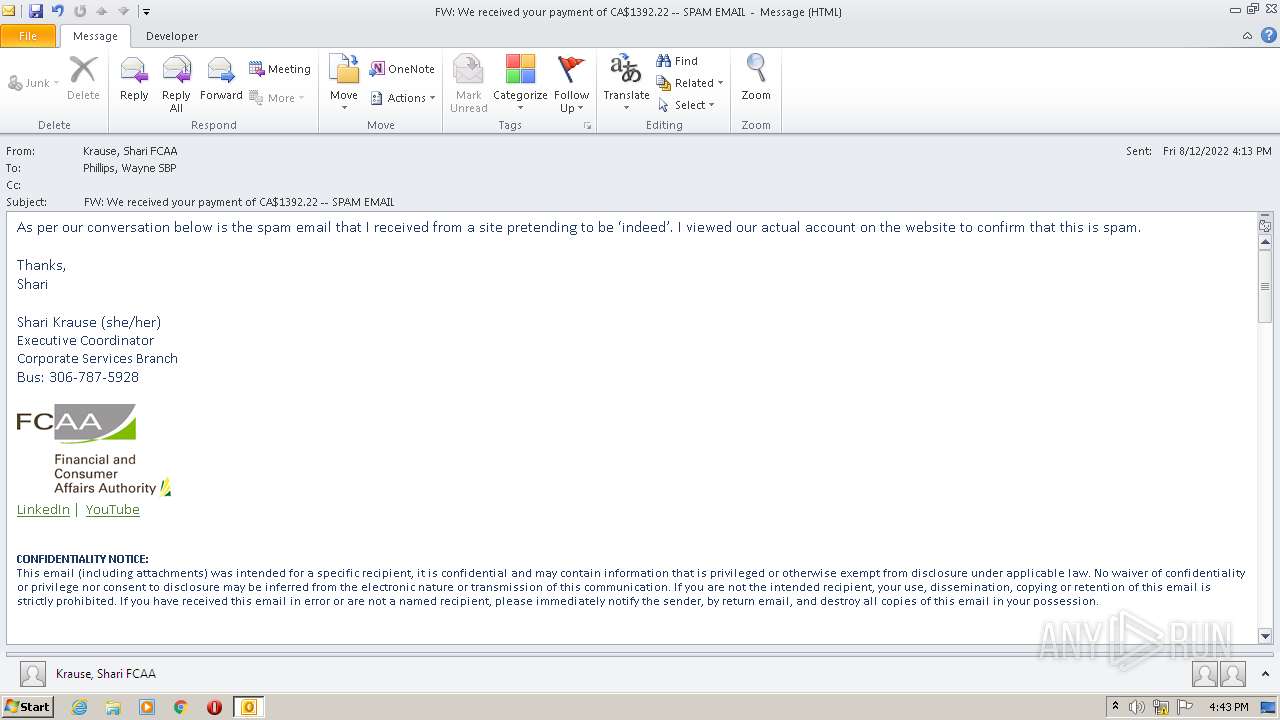
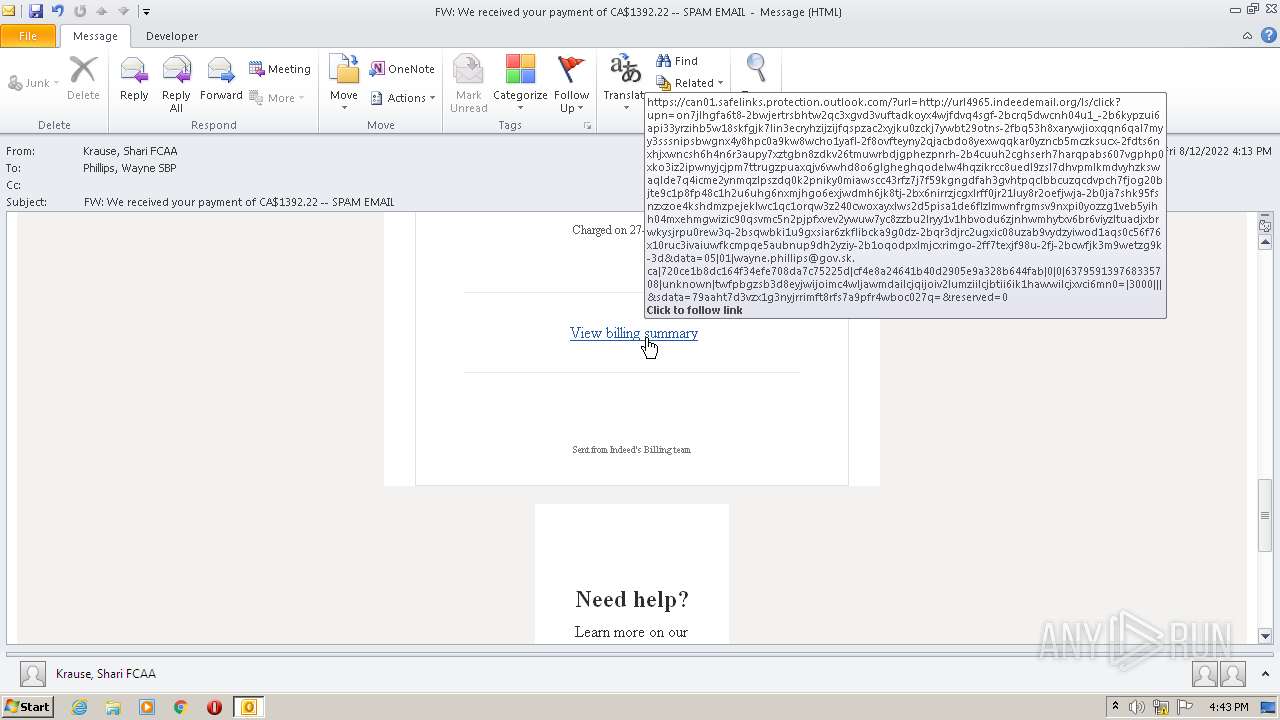
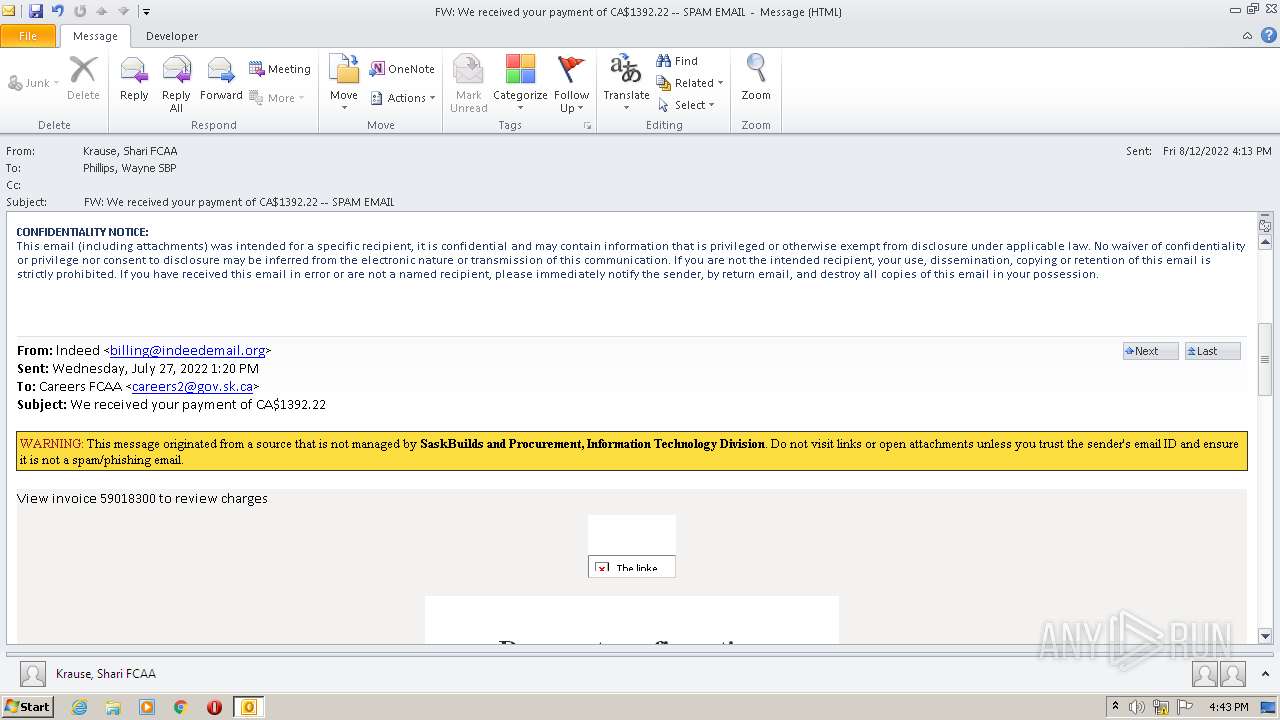
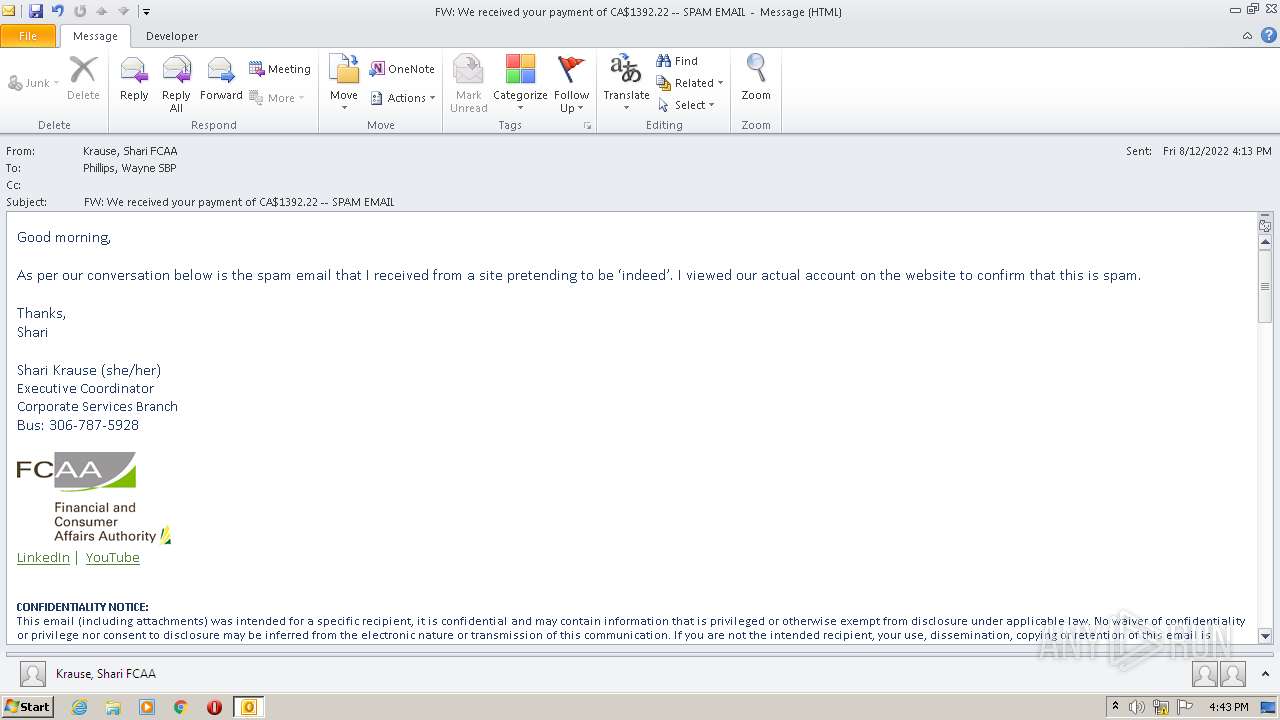
| File name: | FW_ We received your payment of CA$1392_22 -- SPAM EMAIL.msg |
| Full analysis: | https://app.any.run/tasks/279b40c4-4d18-438a-9c6a-0ac26ae54310 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 15:40:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | E4C6E7275BE5D235DED5E6B6BF9F856F |
| SHA1: | 0283FAB14D885E169F5A19C183B84867EBA2221E |
| SHA256: | 7880A8FBE7DEB62289D9B41BDA839AB316E14E837741E5BF9D5FE9F257CDCA62 |
| SSDEEP: | 3072:31wyU7AIduPq/8Iq/a7Sl6G+7QgfgKAaOq5lG7/N7/v11tk:mASGq/Xq/z6GsXtlG7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- OUTLOOK.EXE (PID: 3160)
Searches for installed software
- OUTLOOK.EXE (PID: 3160)
Checks supported languages
- OUTLOOK.EXE (PID: 3160)
Checks Windows Trust Settings
- OUTLOOK.EXE (PID: 3160)
Reads settings of System Certificates
- OUTLOOK.EXE (PID: 3160)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
38
Monitored processes
1
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3160 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\FW_ We received your payment of CA$1392_22 -- SPAM EMAIL.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
41 529
Read events
20 566
Write events
20 944
Delete events
19
Modification events
| (PID) Process: | (3160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3160) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
5
Text files
17
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9B94.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3160 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 3160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\8FE462FF.dat | image | |
MD5:— | SHA256:— | |||
| 3160 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\config14[1].xml | xml | |
MD5:— | SHA256:— | |||
| 3160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\ONetConfig\54946941a2b45a5ba7f3e1b905b42959.sig | binary | |
MD5:— | SHA256:— | |||
| 3160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_WorkHours_1_631E8C29C28D1C408A24B5BD78B761F0.dat | xml | |
MD5:807EF0FC900FEB3DA82927990083D6E7 | SHA256:4411E7DC978011222764943081500FFF0E43CBF7CCD44264BD1AB6306CA68913 | |||
| 3160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\ONetConfig\54946941a2b45a5ba7f3e1b905b42959.xml | xml | |
MD5:— | SHA256:— | |||
| 3160 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\77072380.dat | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
13
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3160 | OUTLOOK.EXE | GET | 200 | 52.109.76.141:80 | http://office14client.microsoft.com/config14?UILCID=1033&CLCID=1033&ILCID=1033&HelpLCID=1033&App={CFF13DD8-6EF2-49EB-B265-E3BFC6501C1D}&build=14.0.6023 | IE | xml | 1.96 Kb | whitelisted |
3160 | OUTLOOK.EXE | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3160 | OUTLOOK.EXE | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3160 | OUTLOOK.EXE | GET | 200 | 23.216.77.69:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?73439498480669ec | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3160 | OUTLOOK.EXE | 52.109.76.141:80 | office14client.microsoft.com | Microsoft Corporation | IE | suspicious |
3160 | OUTLOOK.EXE | 52.109.124.67:443 | rr.office.microsoft.com | Microsoft Corporation | SG | suspicious |
3160 | OUTLOOK.EXE | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3160 | OUTLOOK.EXE | 23.216.77.69:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
3160 | OUTLOOK.EXE | 143.204.89.66:443 | dpuk71x9wlmkf.cloudfront.net | — | US | suspicious |
3160 | OUTLOOK.EXE | 104.17.72.206:443 | offers.indeed.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
office14client.microsoft.com |
| whitelisted |
rr.office.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dpuk71x9wlmkf.cloudfront.net |
| malicious |
offers.indeed.com |
| malicious |
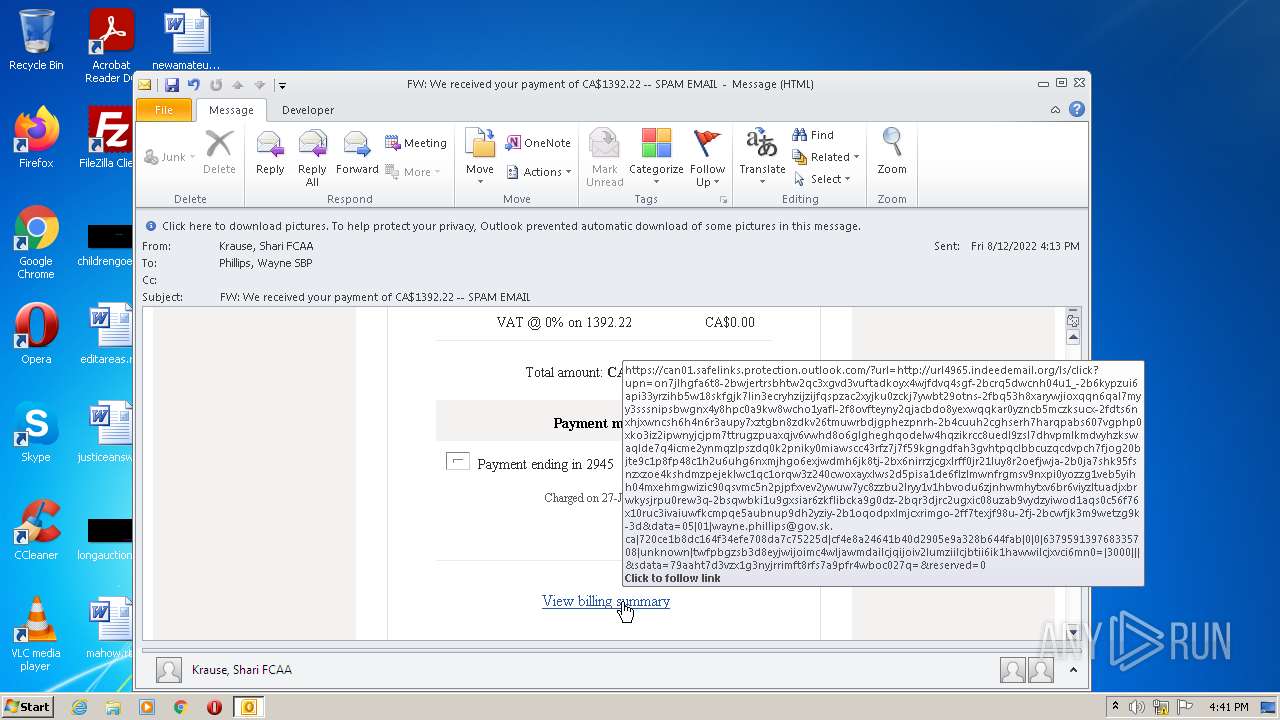
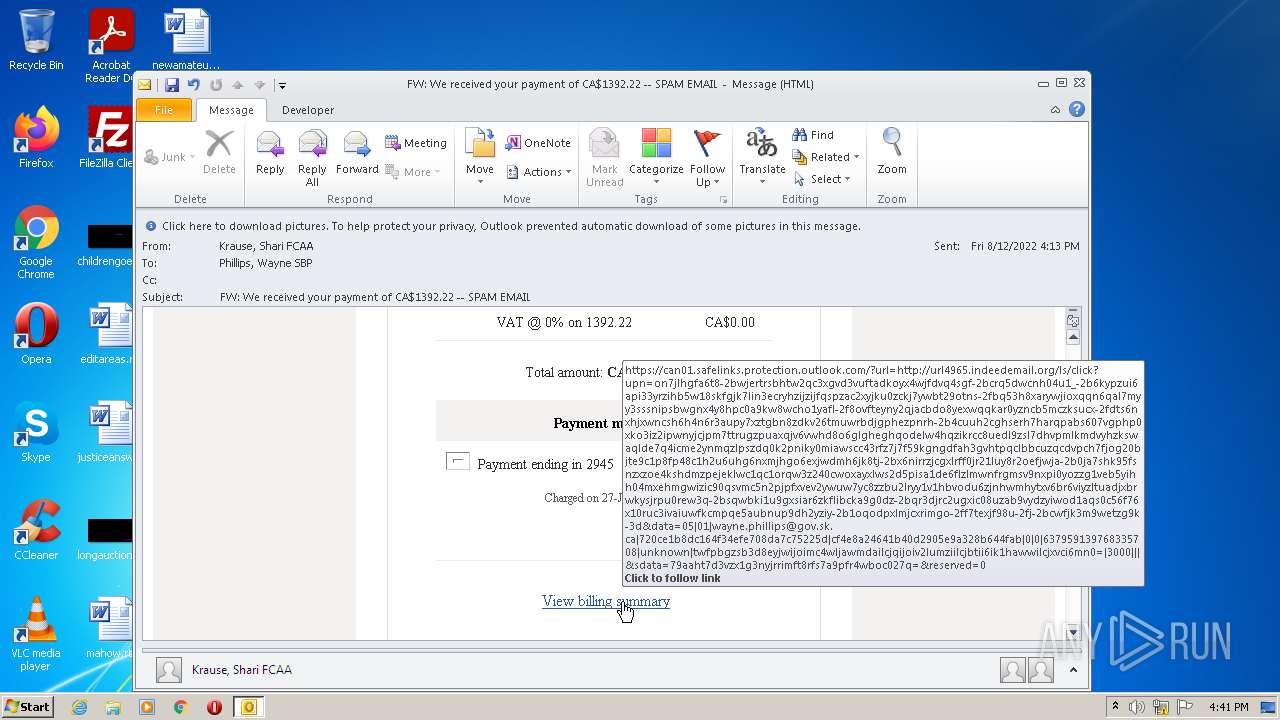
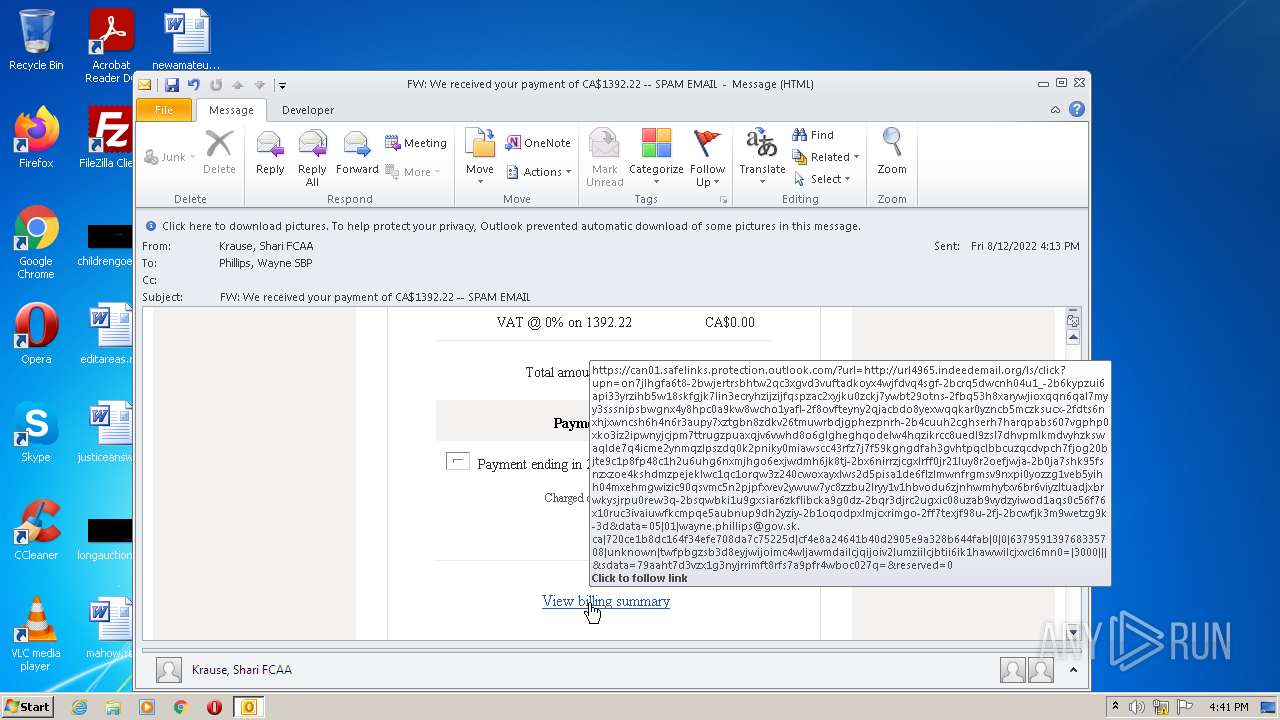
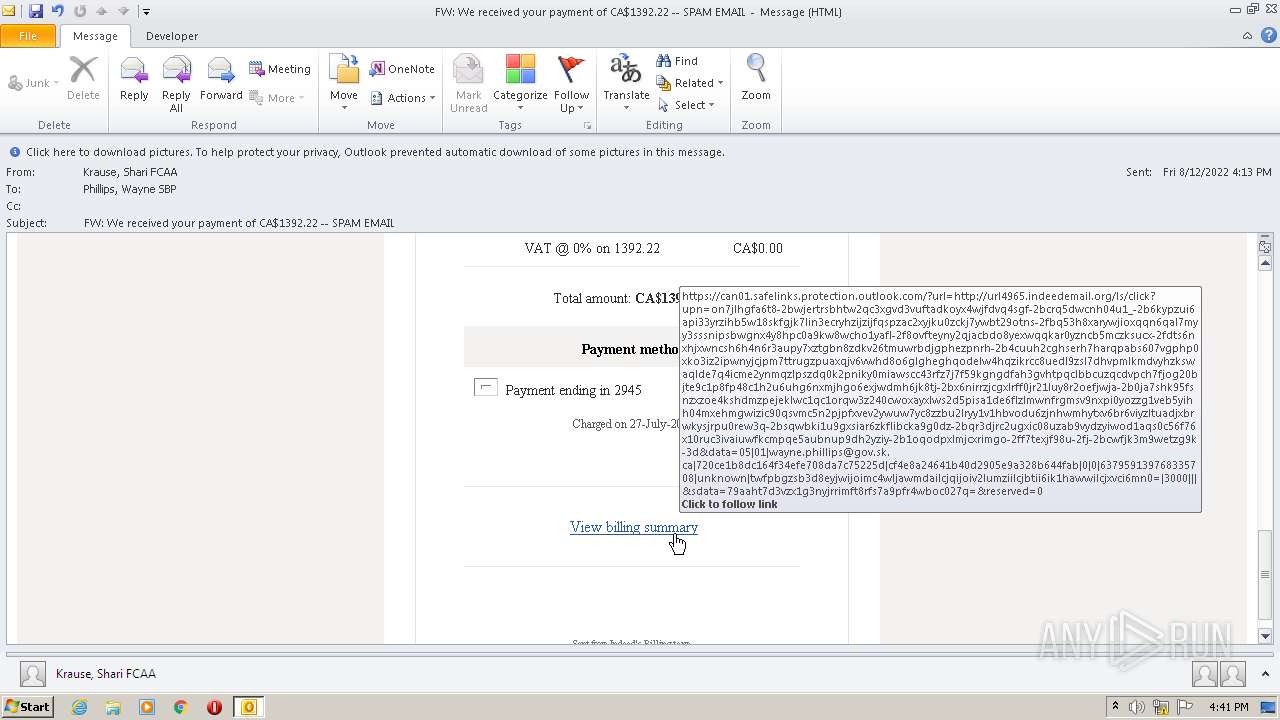
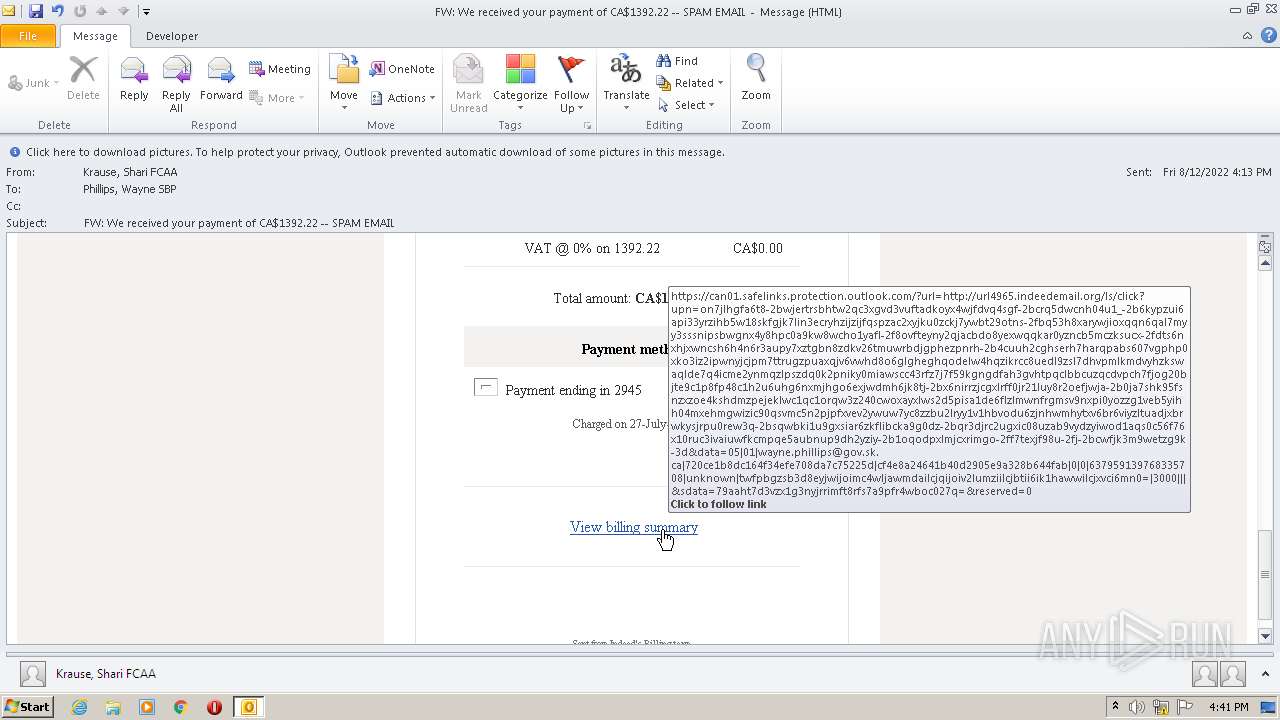
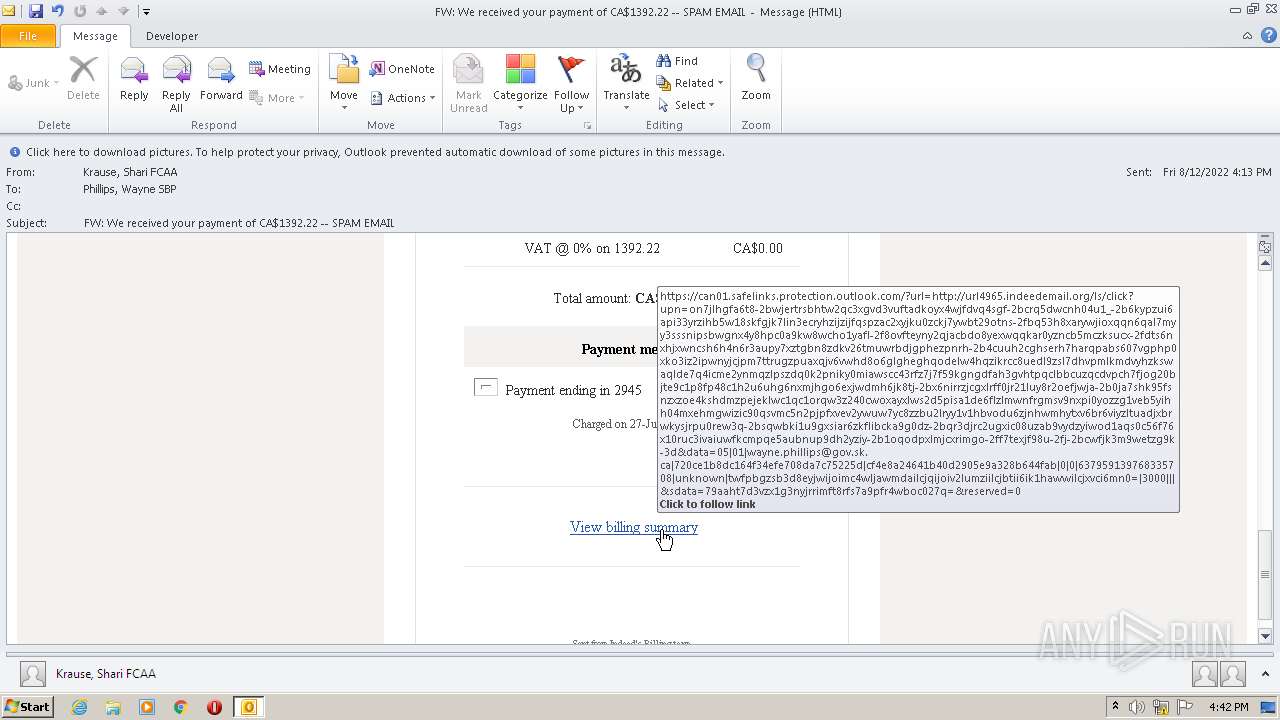
url4965.indeedemail.org |
| unknown |