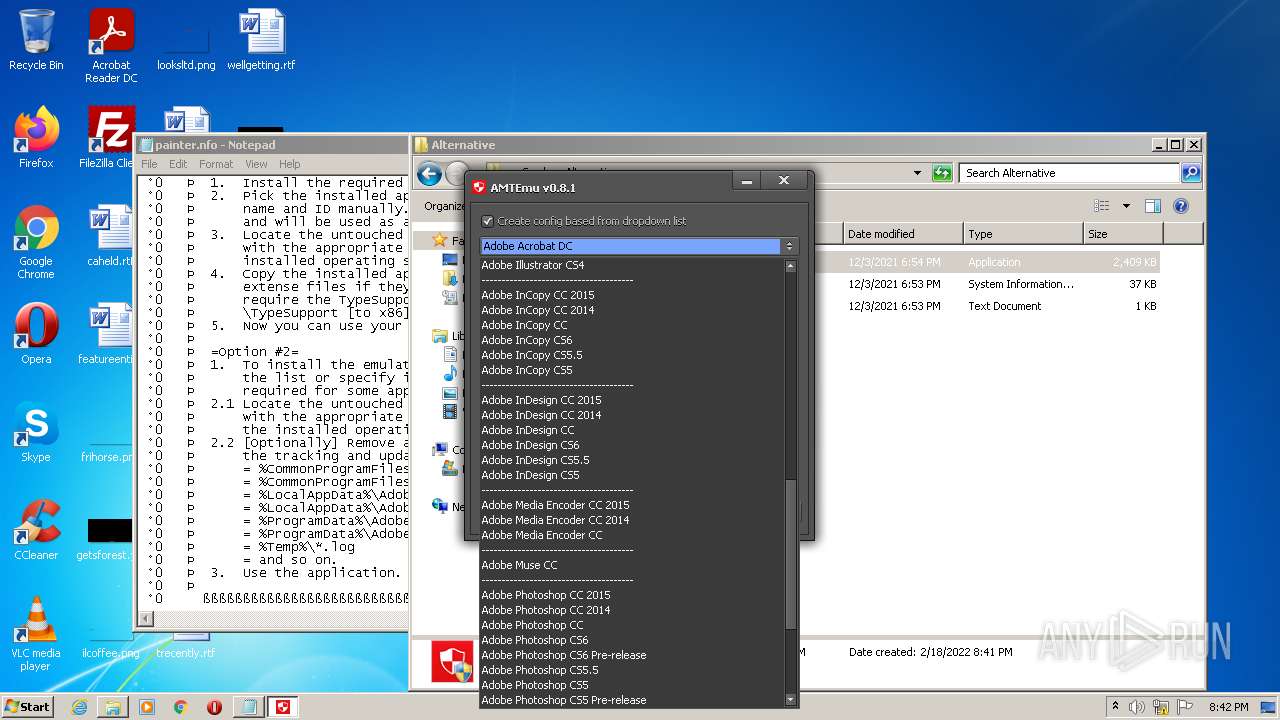
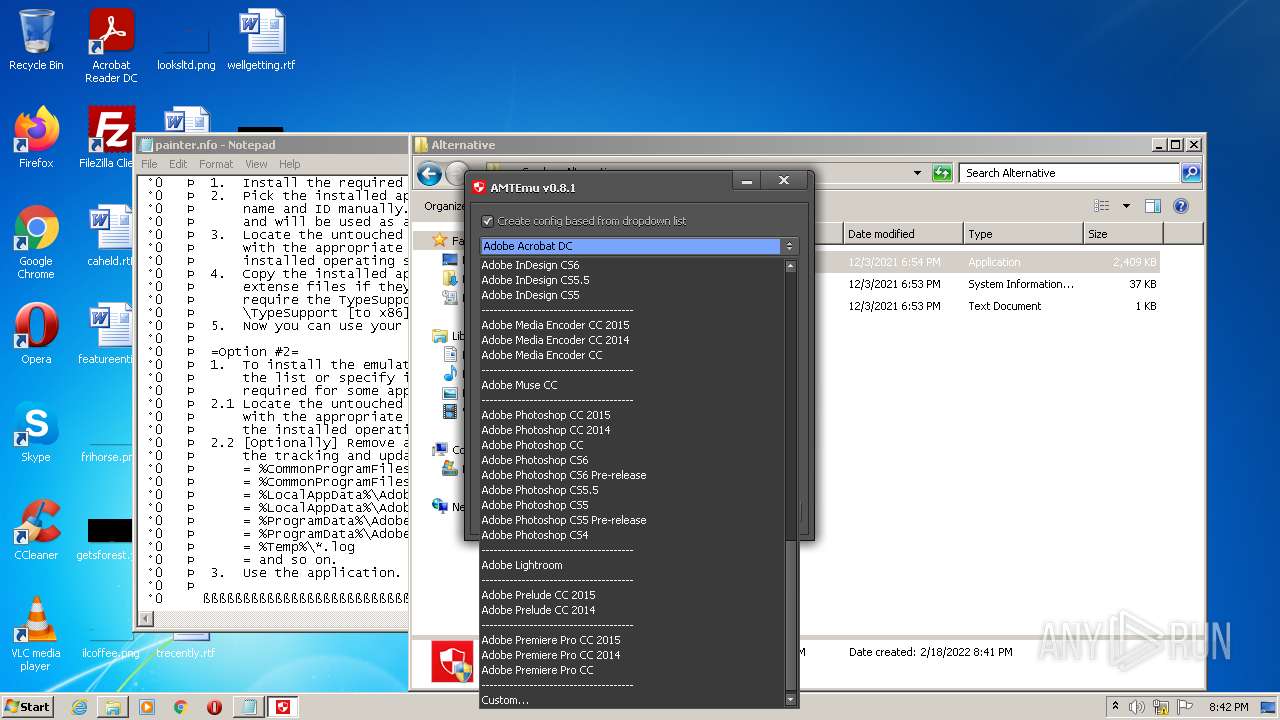
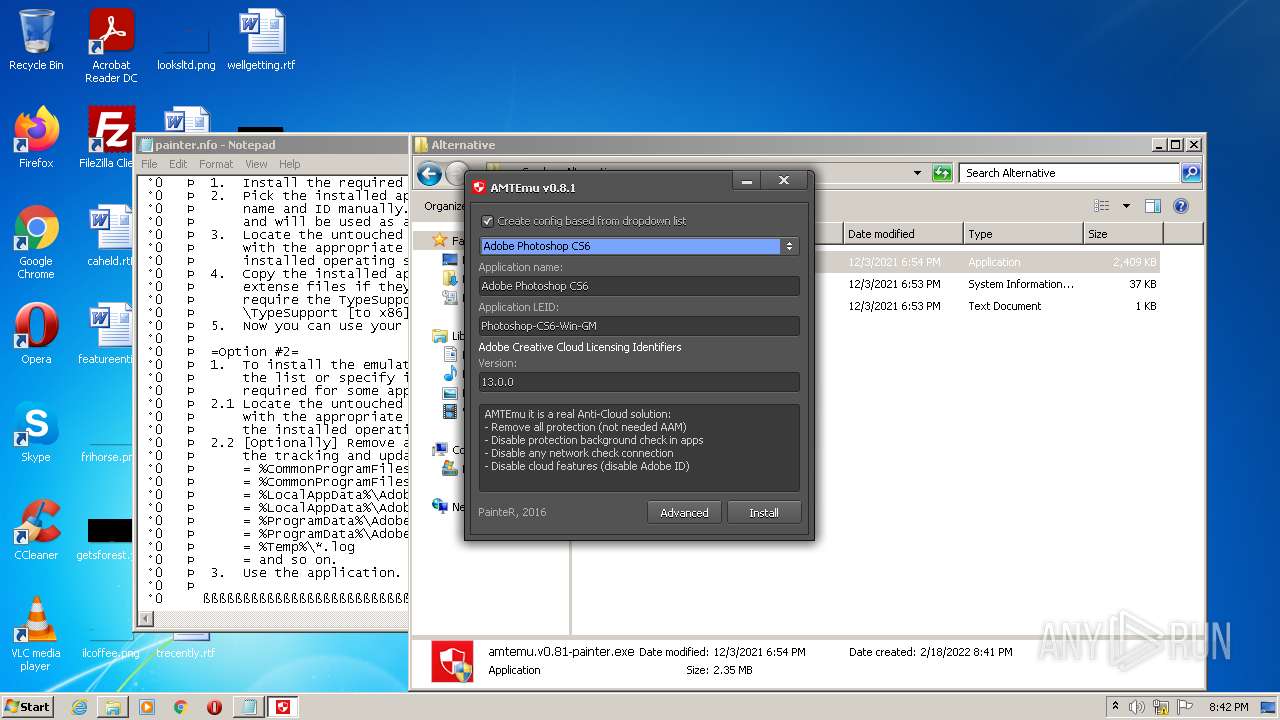
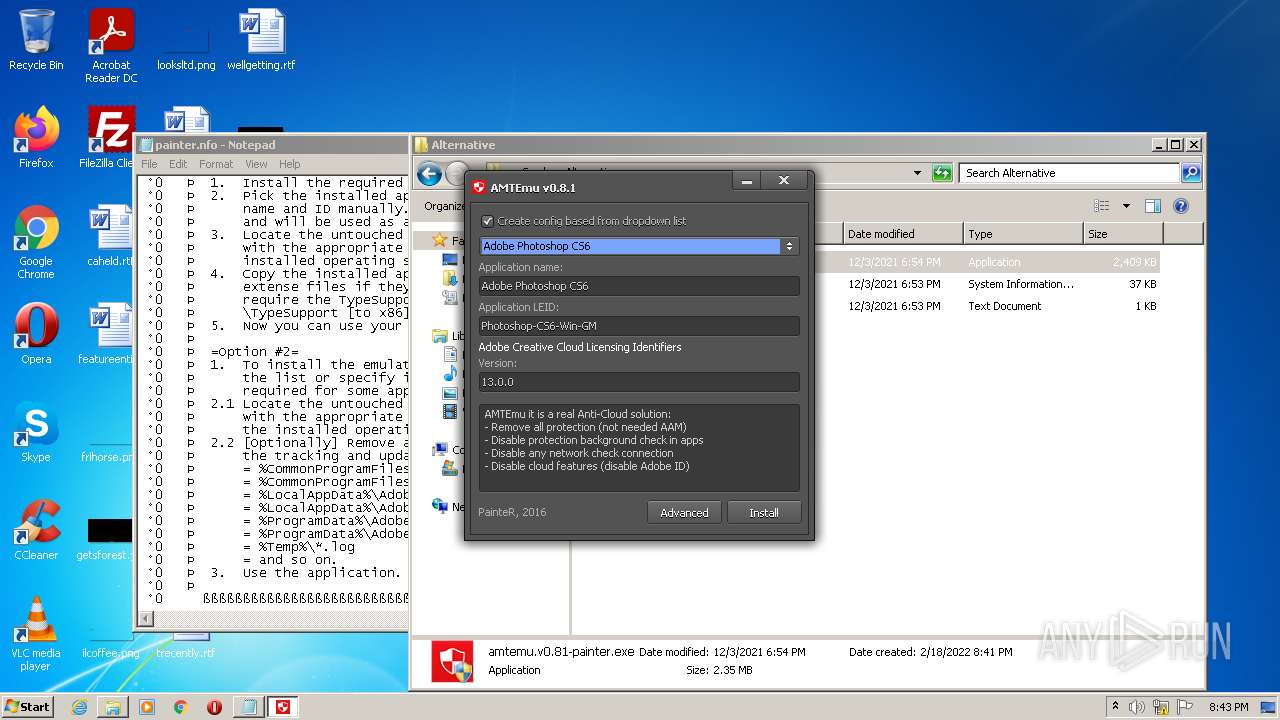
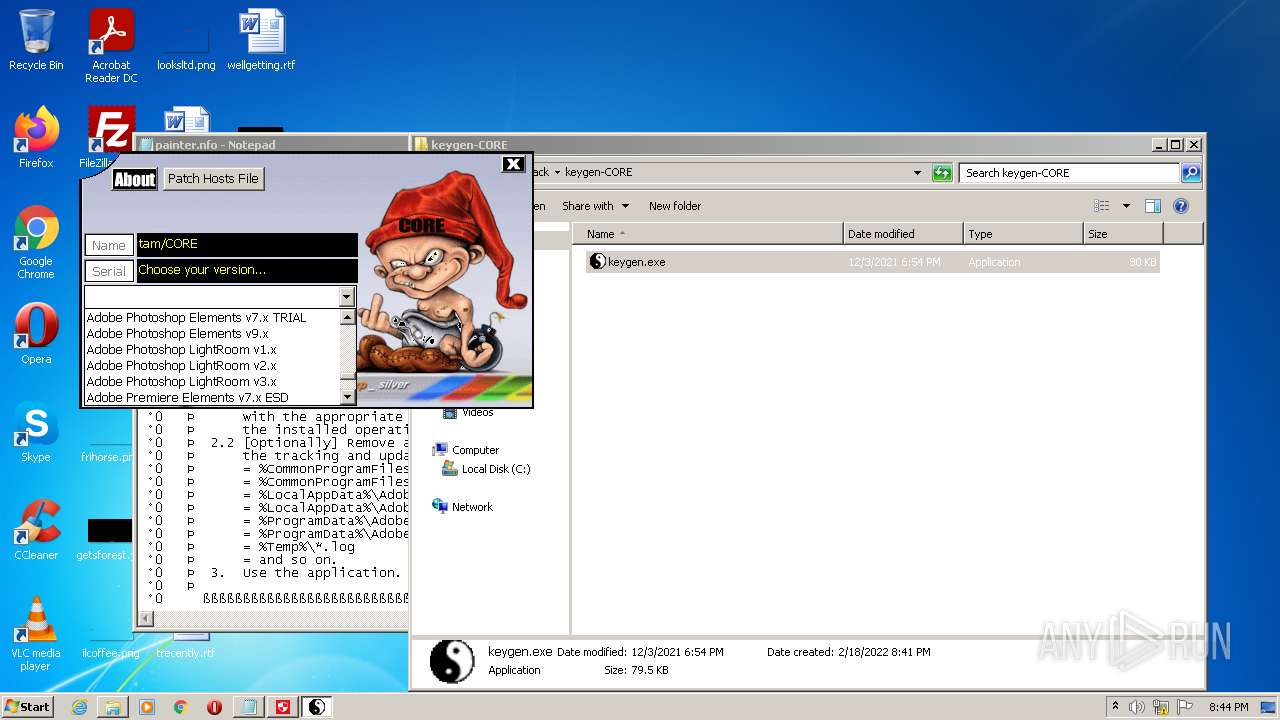
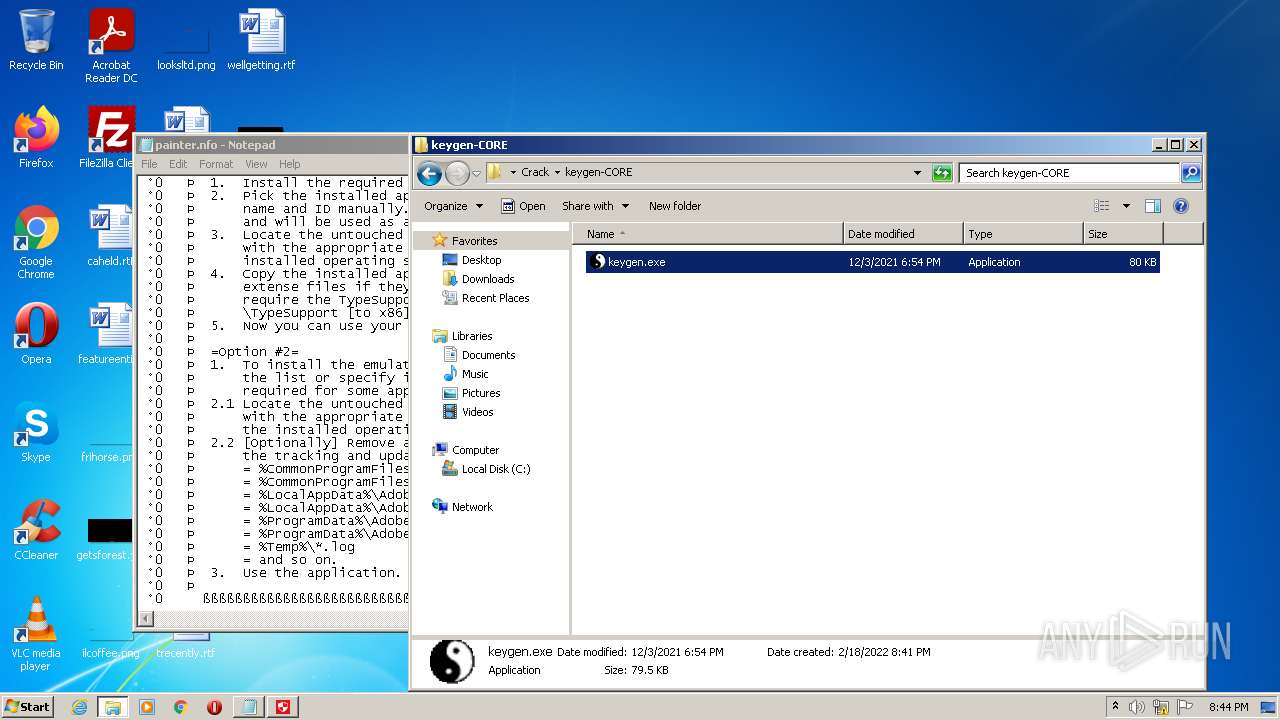
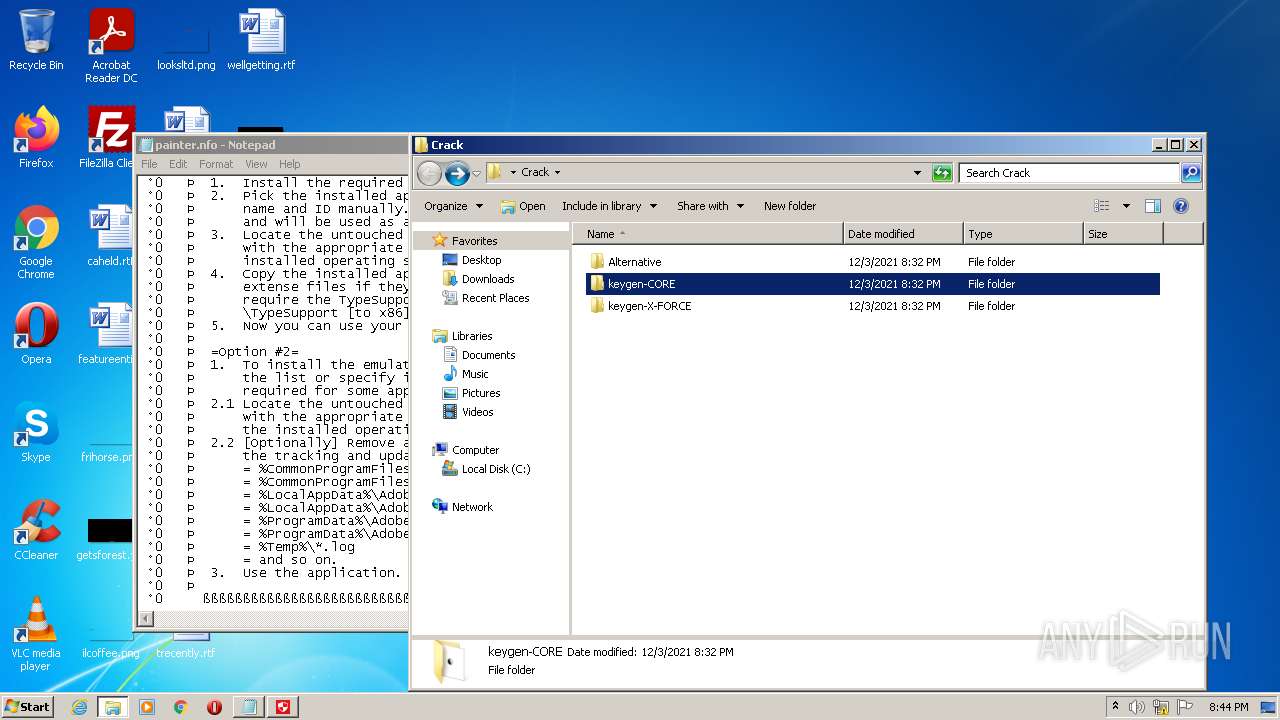
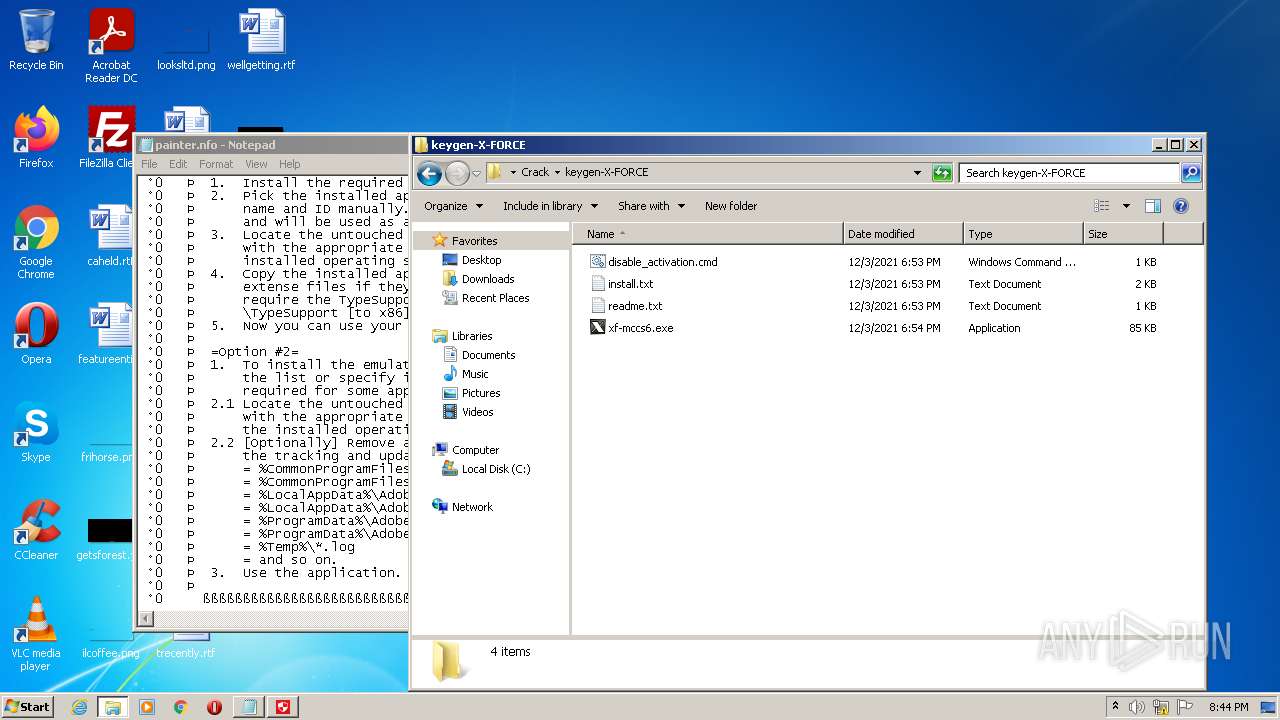
| File name: | Crack.7z |
| Full analysis: | https://app.any.run/tasks/1781eb8d-8f5b-4b23-8710-df74cec0d575 |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2022, 20:41:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 2940999FA6FB8335D51D7D9A4B995BEC |
| SHA1: | 7E92F7AB59B83DD2D91EEBA6CB3E7F3624BC207D |
| SHA256: | 78763B8978ECFED9FF89605AF36BF04AAE17FEC25DCB87B9DC01ED7480CD1BA9 |
| SSDEEP: | 24576:21pIvvCjNO/c2RgBb9V/AA49Gt/bWaLN31exrjvN9wNP2Du9Dh/ChAV697sztdN:2WqxOW/GGt/bWEen9wA4/CRcb |
MALICIOUS
Application was dropped or rewritten from another process
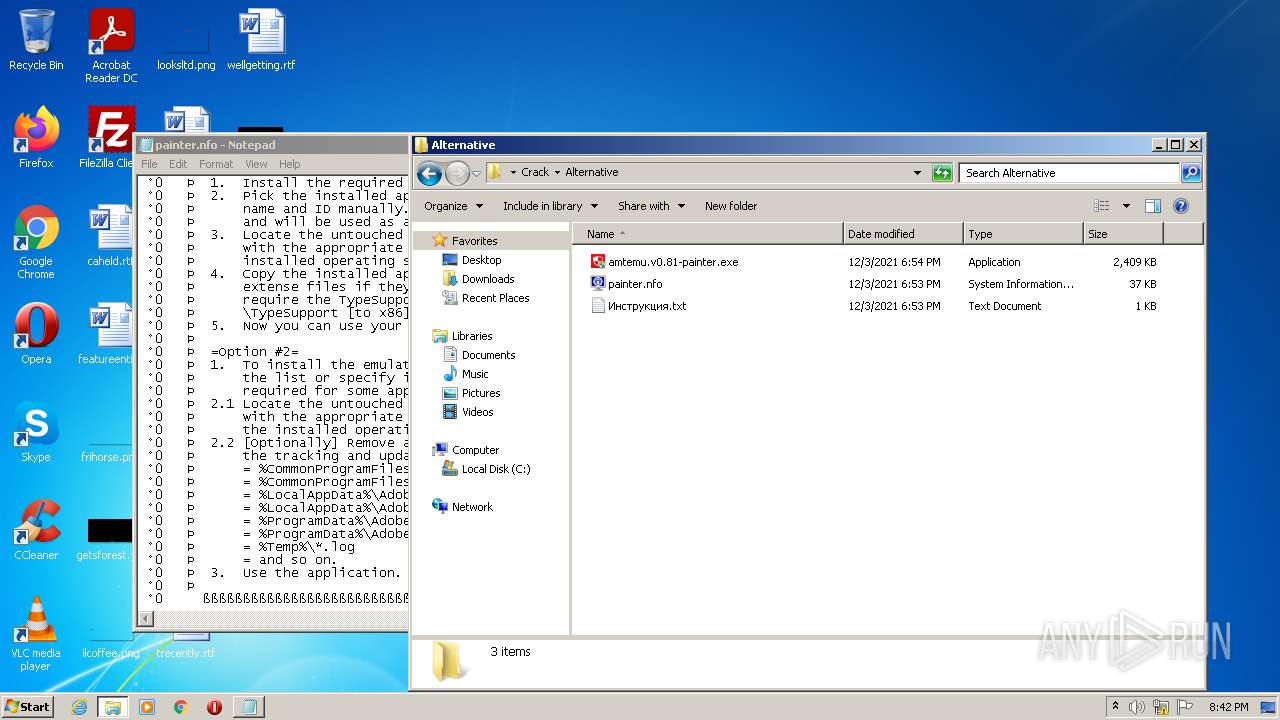
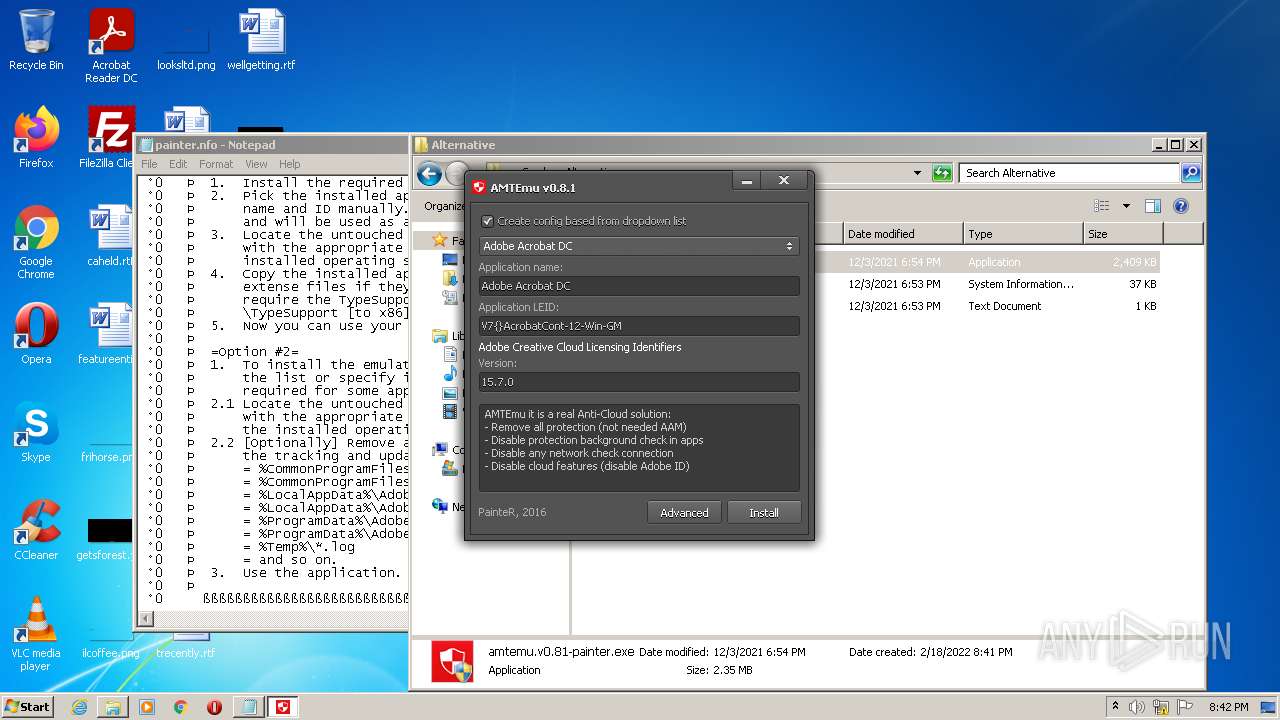
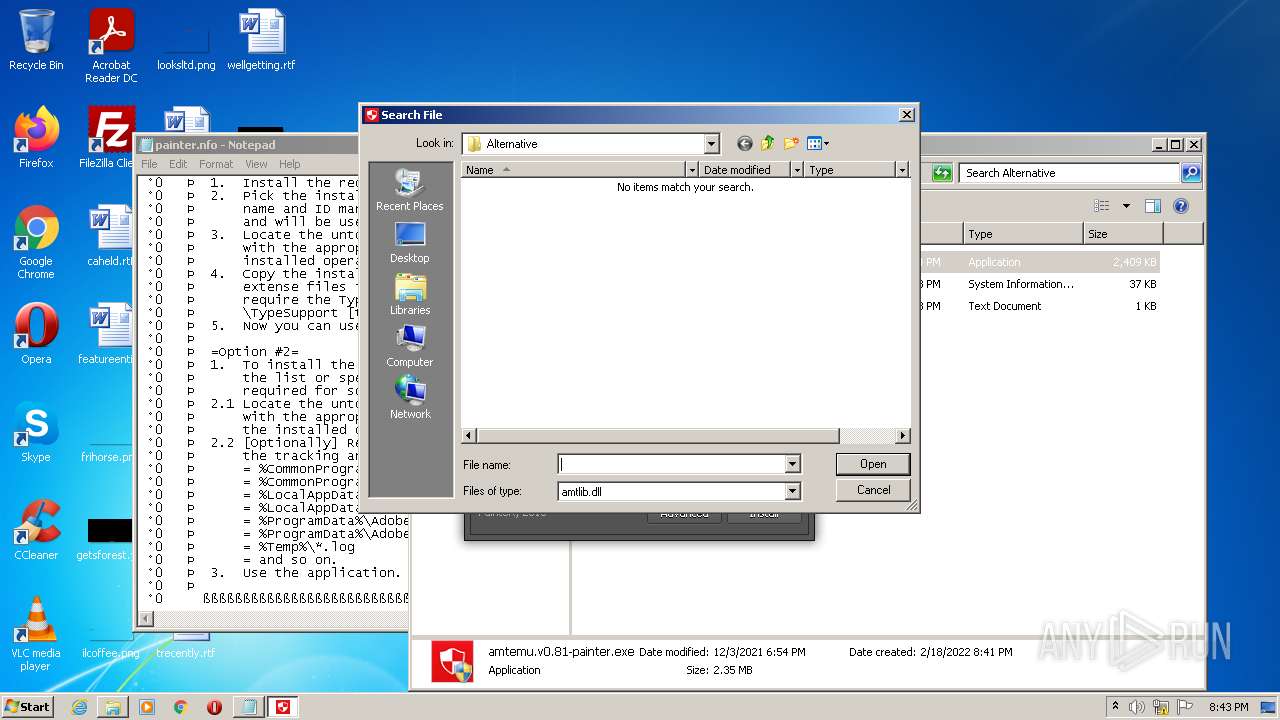
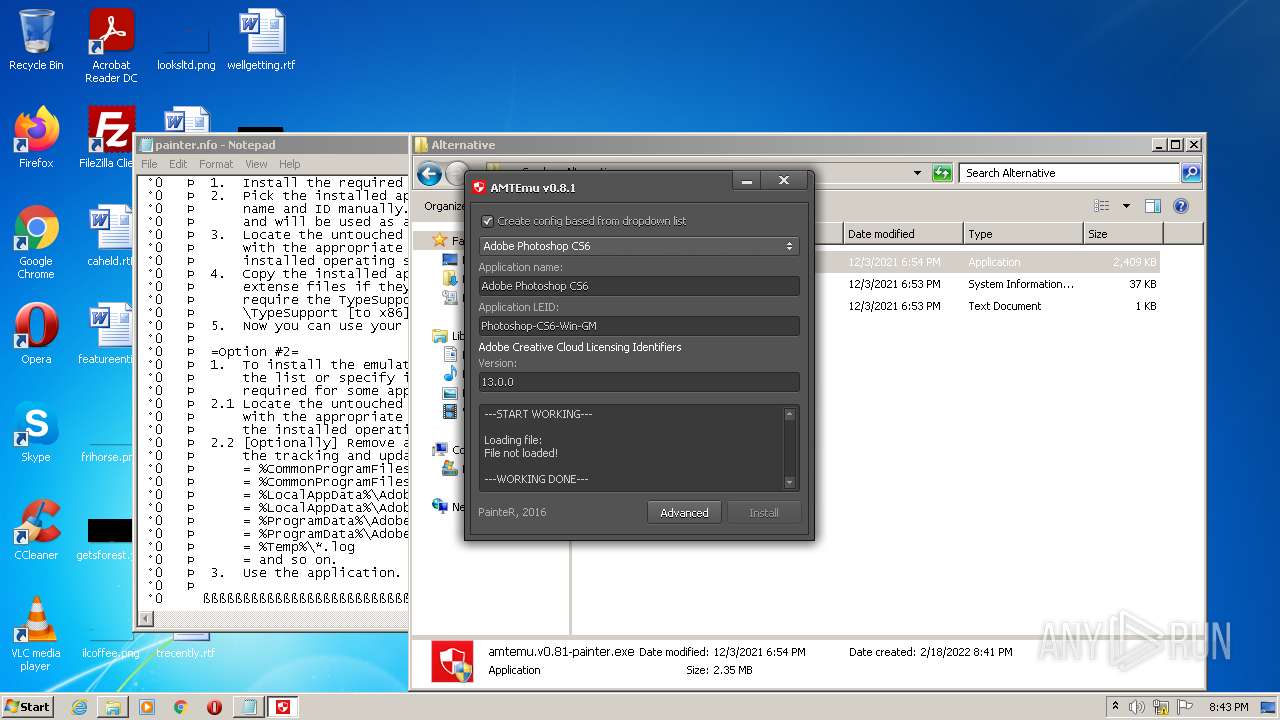
- amtemu.v0.81-painter.exe (PID: 3156)
- amtemu.v0.81-painter.exe (PID: 4048)
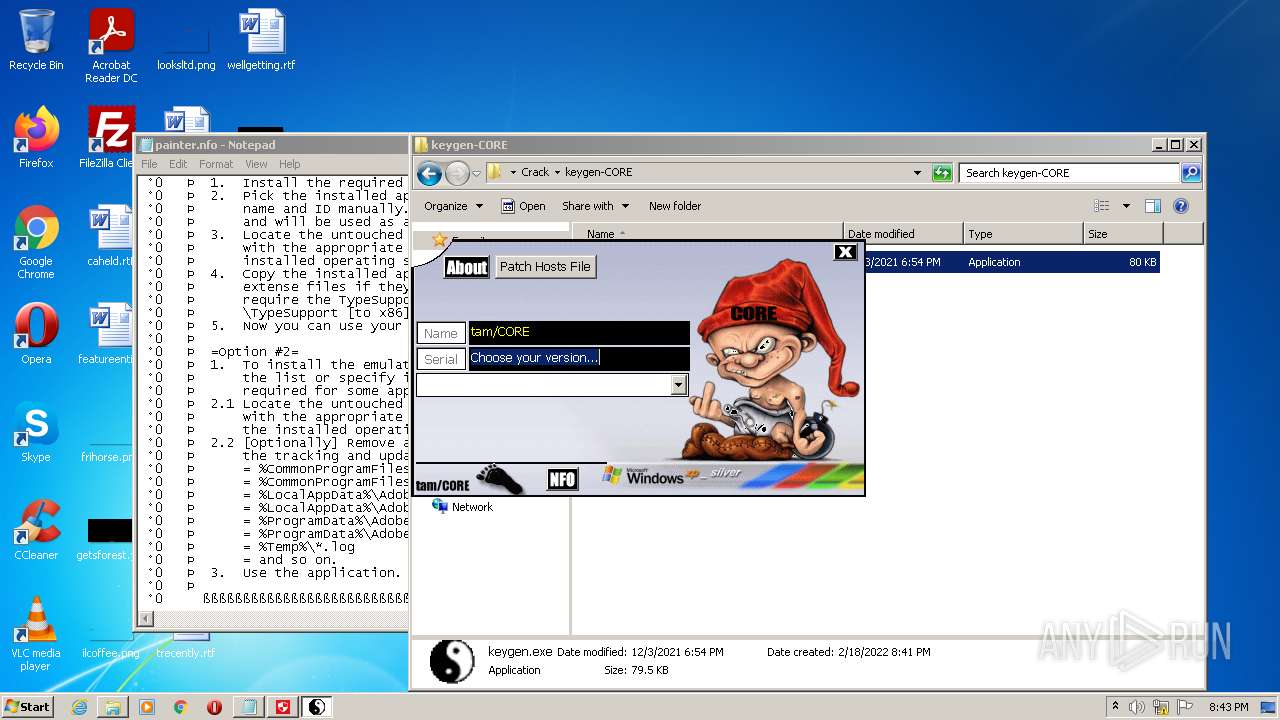
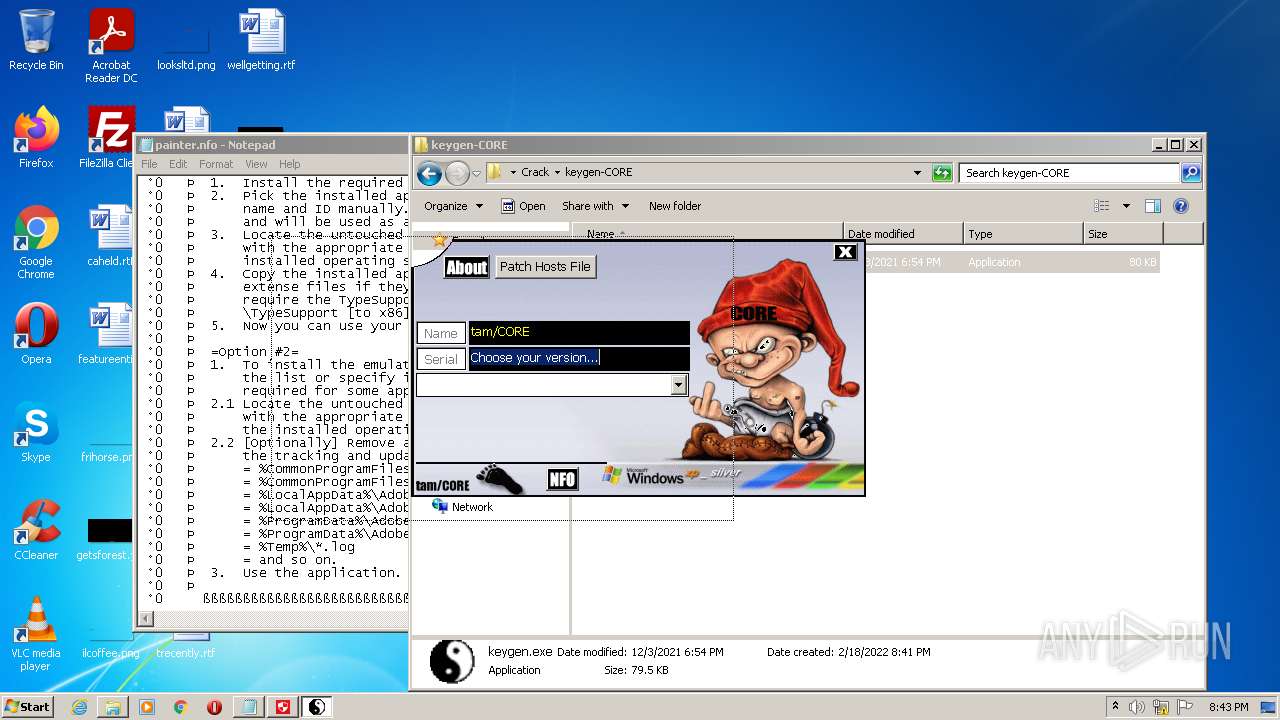
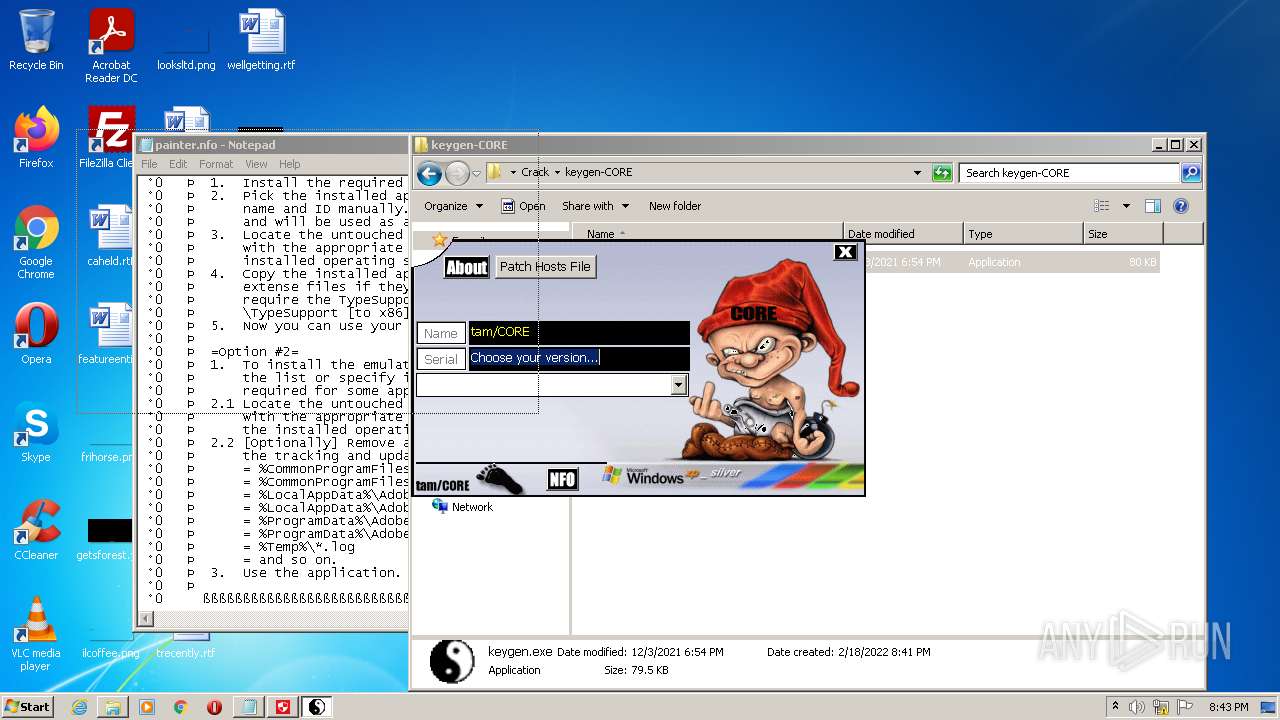
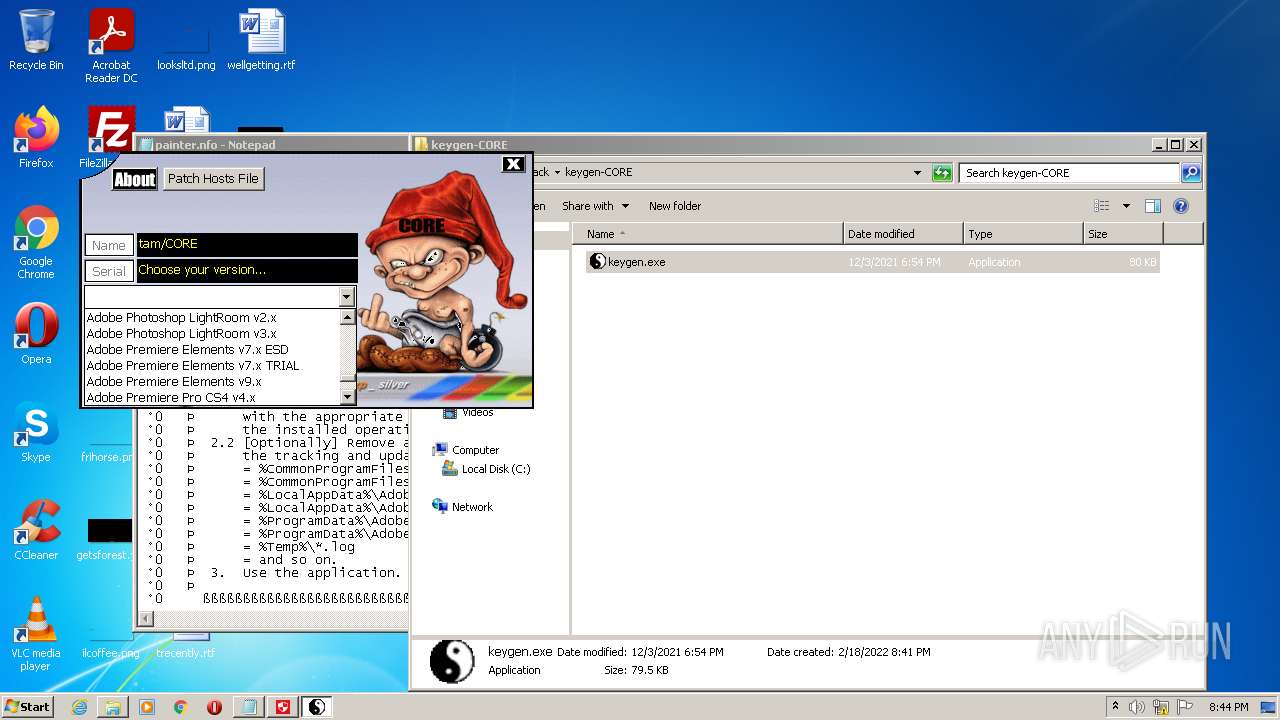
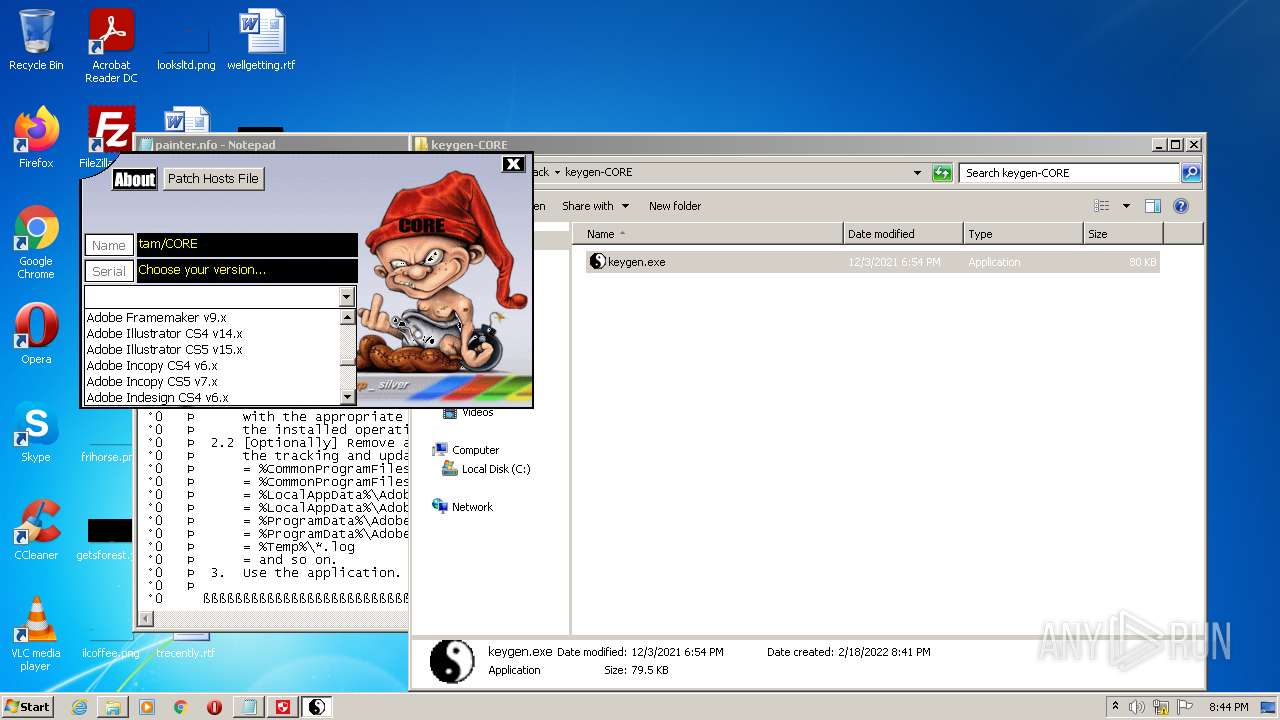
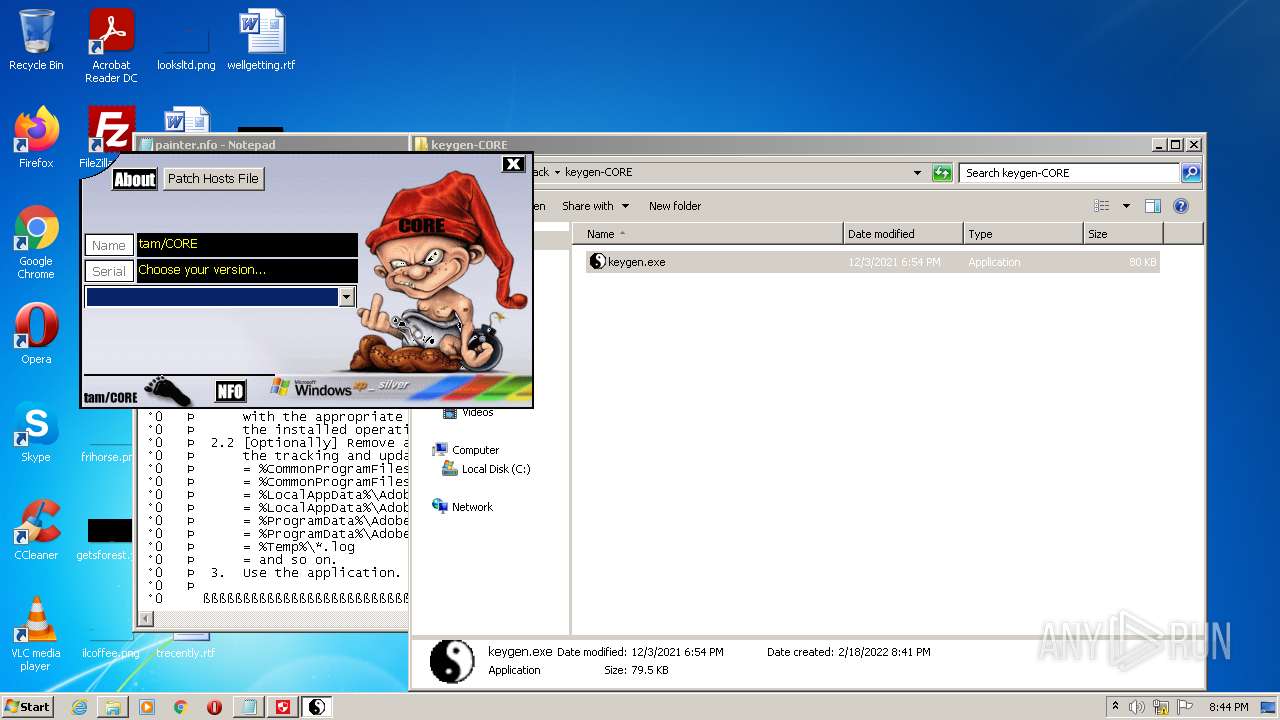
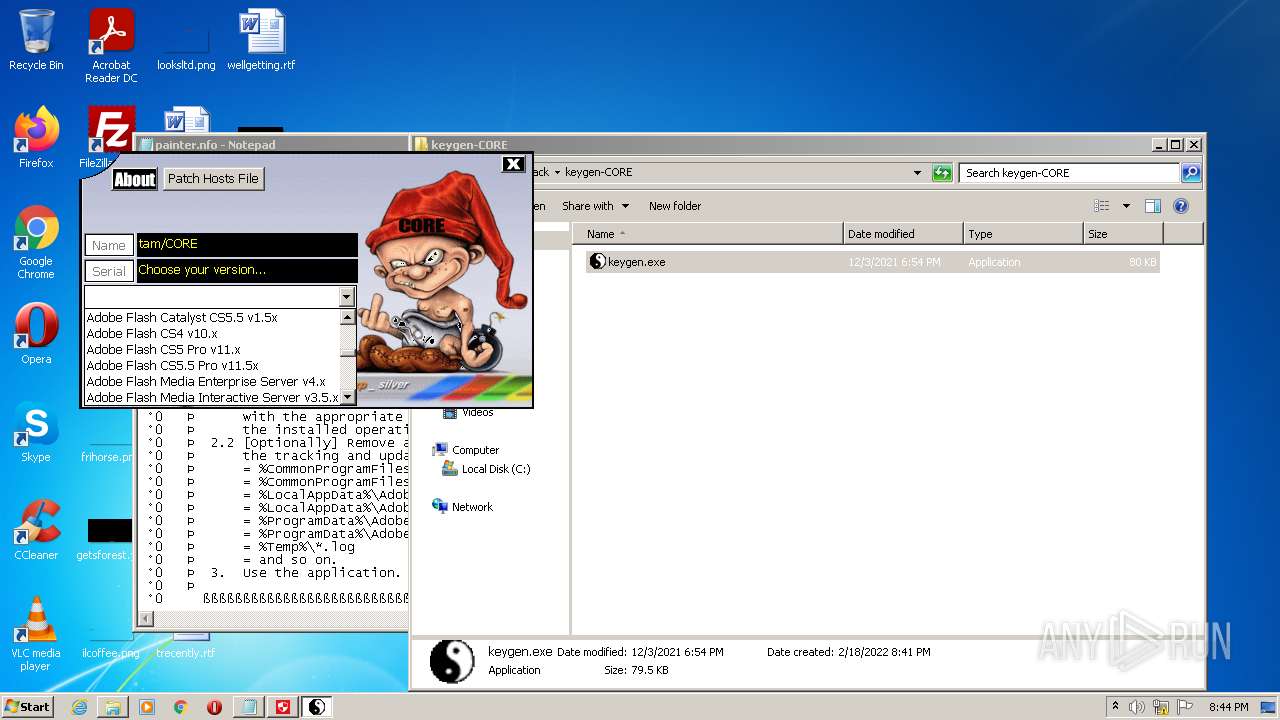
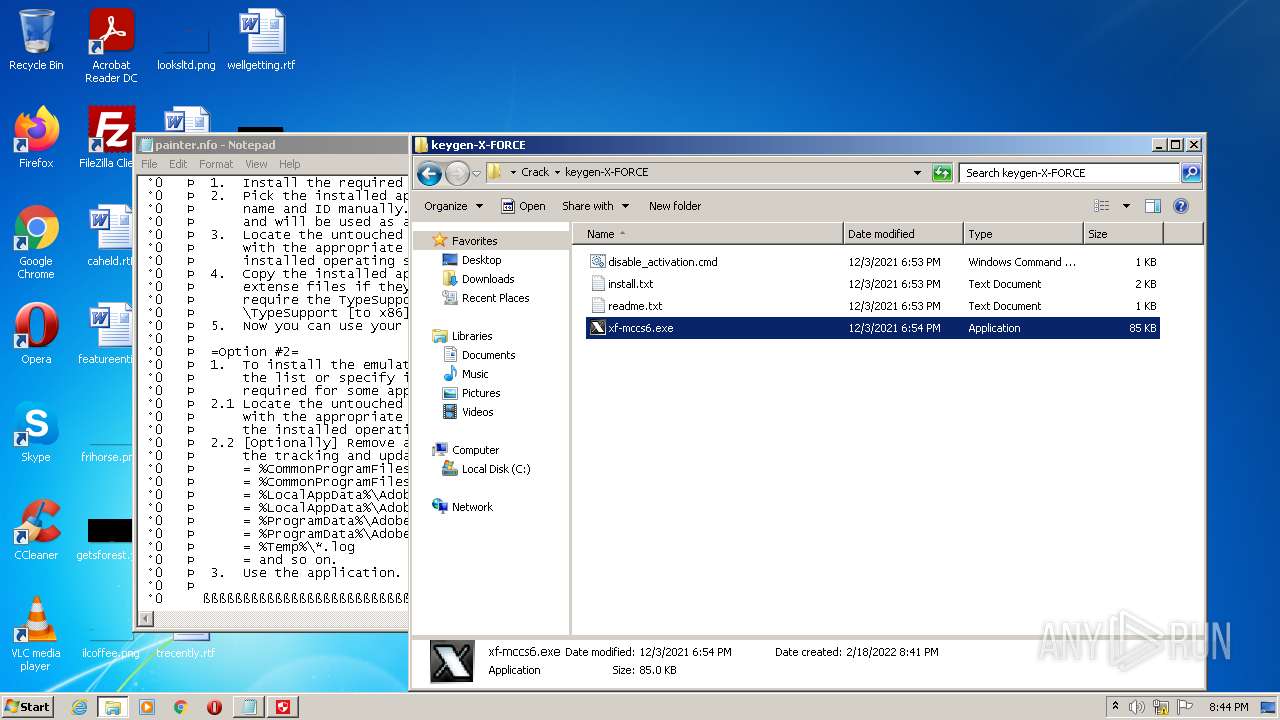
- keygen.exe (PID: 2952)
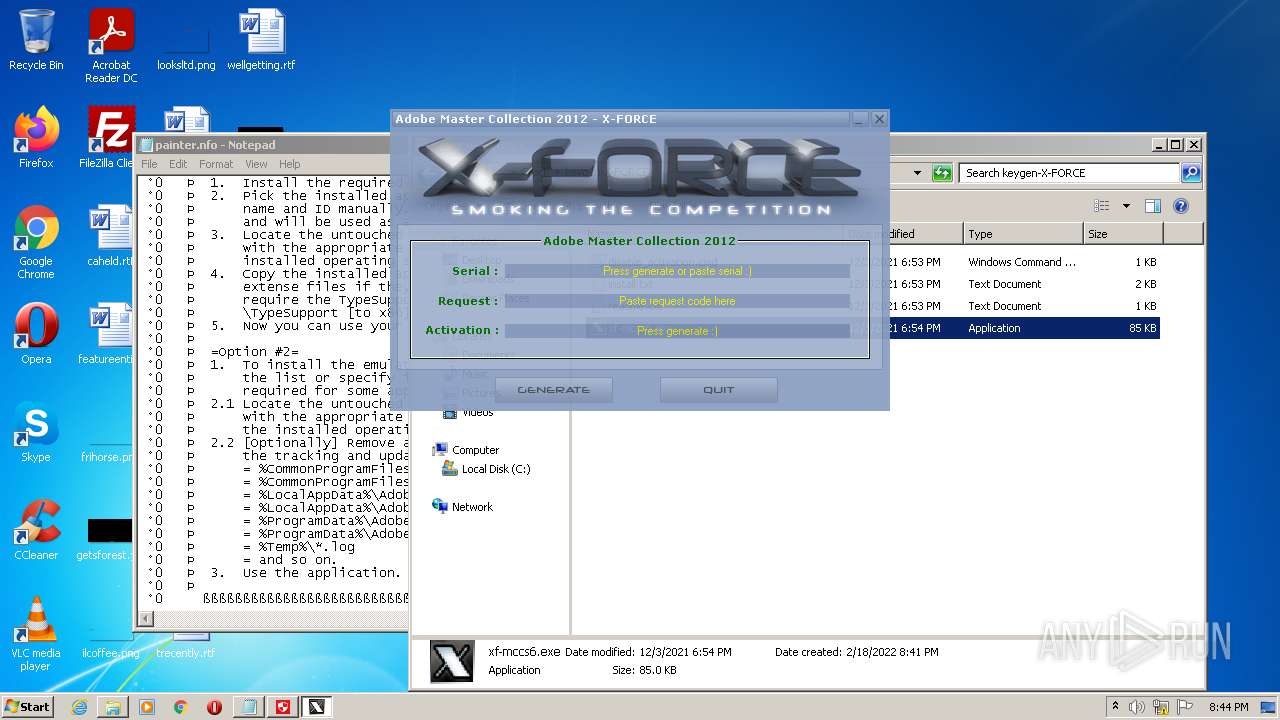
- xf-mccs6.exe (PID: 2528)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3724)
- amtemu.v0.81-painter.exe (PID: 4048)
- keygen.exe (PID: 2952)
- xf-mccs6.exe (PID: 2528)
Checks supported languages
- WinRAR.exe (PID: 3724)
- amtemu.v0.81-painter.exe (PID: 4048)
- keygen.exe (PID: 2952)
- xf-mccs6.exe (PID: 2528)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3724)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3724)
Drops a file with too old compile date
- WinRAR.exe (PID: 3724)
INFO
Checks supported languages
- notepad.exe (PID: 1884)
Reads the computer name
- notepad.exe (PID: 1884)
Manual execution by user
- notepad.exe (PID: 1884)
- amtemu.v0.81-painter.exe (PID: 3156)
- amtemu.v0.81-painter.exe (PID: 4048)
- keygen.exe (PID: 2952)
- xf-mccs6.exe (PID: 2528)
Reads the hosts file
- keygen.exe (PID: 2952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
46
Monitored processes
6
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1884 | "C:\Windows\system32\notepad.exe" | C:\Windows\system32\notepad.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2528 | "C:\Users\admin\Desktop\Crack\keygen-X-FORCE\xf-mccs6.exe" | C:\Users\admin\Desktop\Crack\keygen-X-FORCE\xf-mccs6.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225547 Modules
| |||||||||||||||
| 2952 | "C:\Users\admin\Desktop\Crack\keygen-CORE\keygen.exe" | C:\Users\admin\Desktop\Crack\keygen-CORE\keygen.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
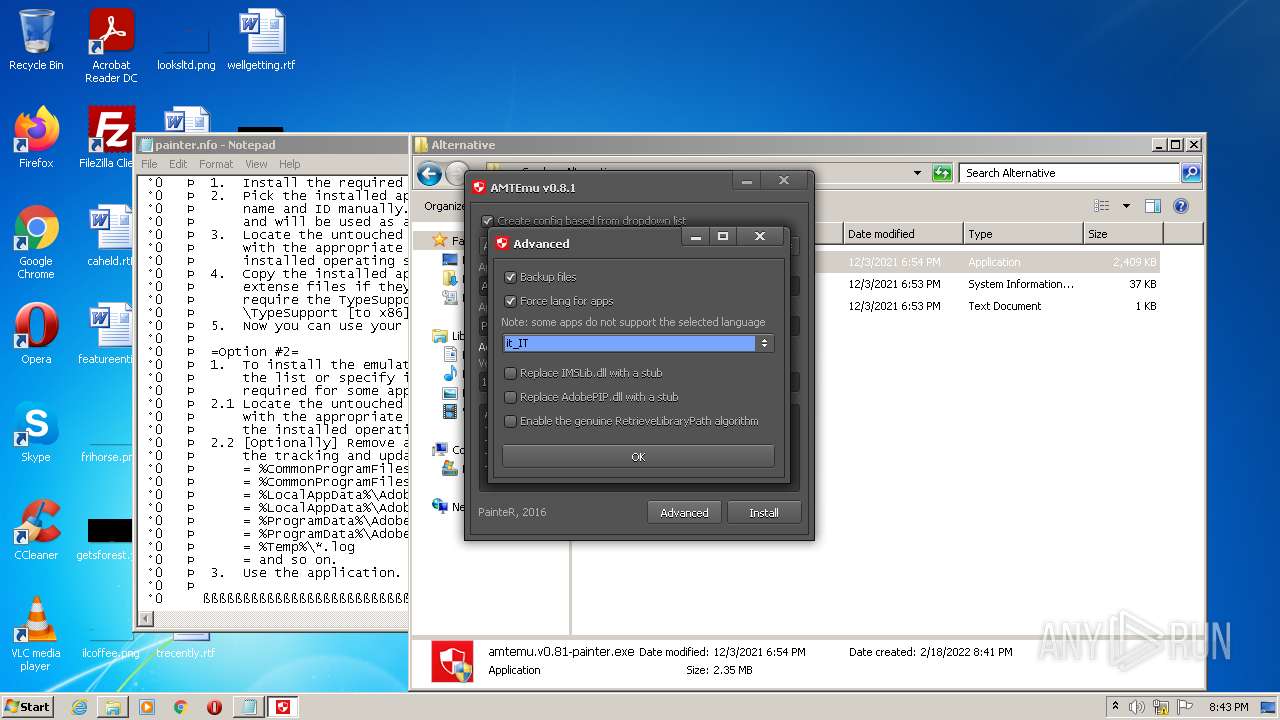
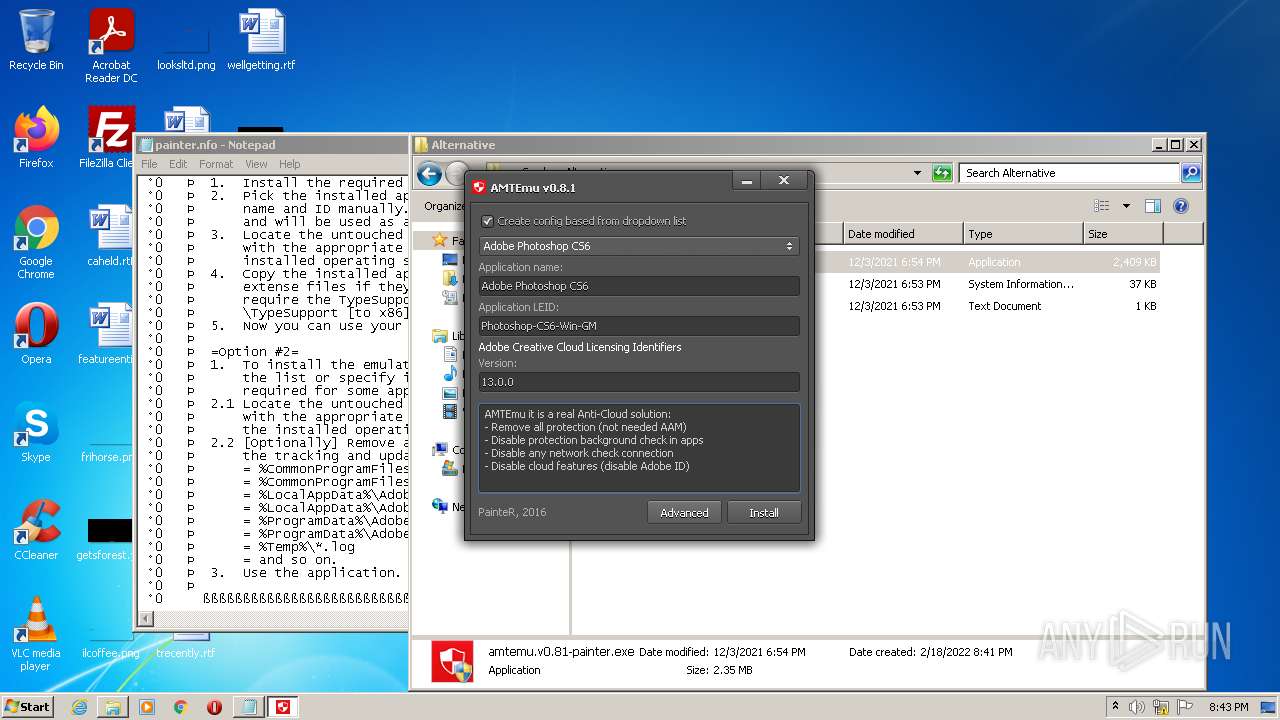
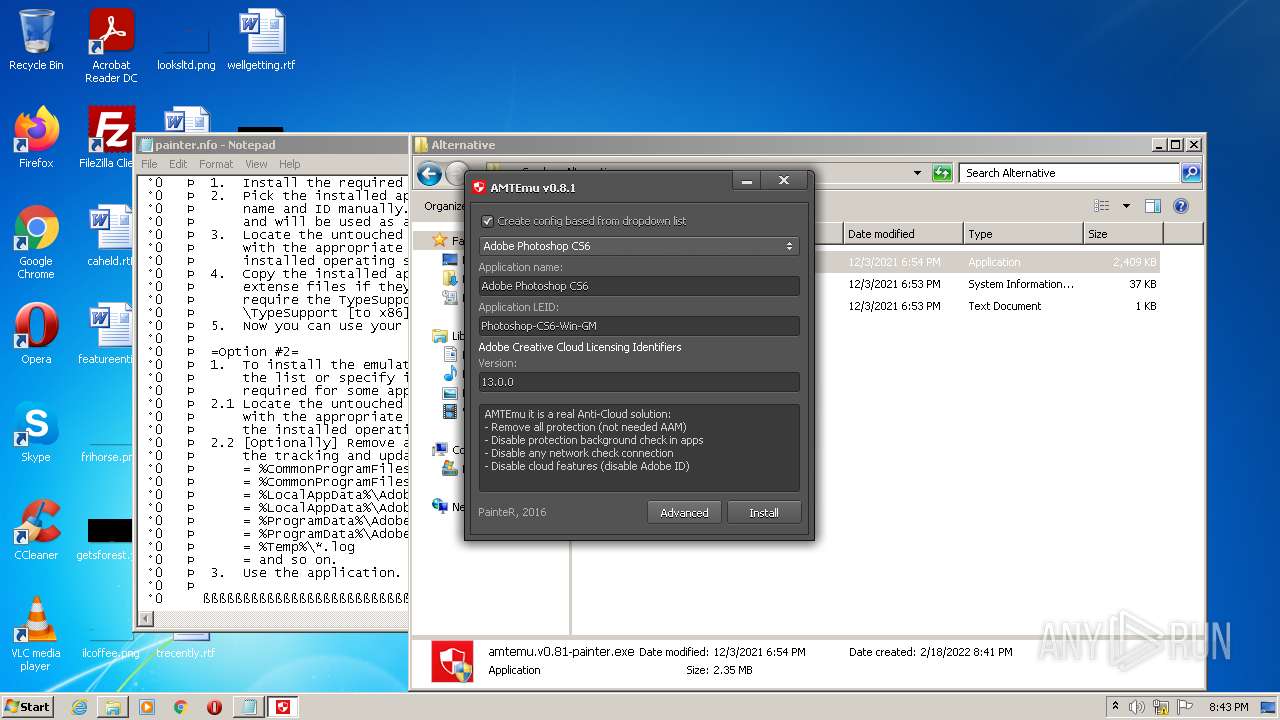
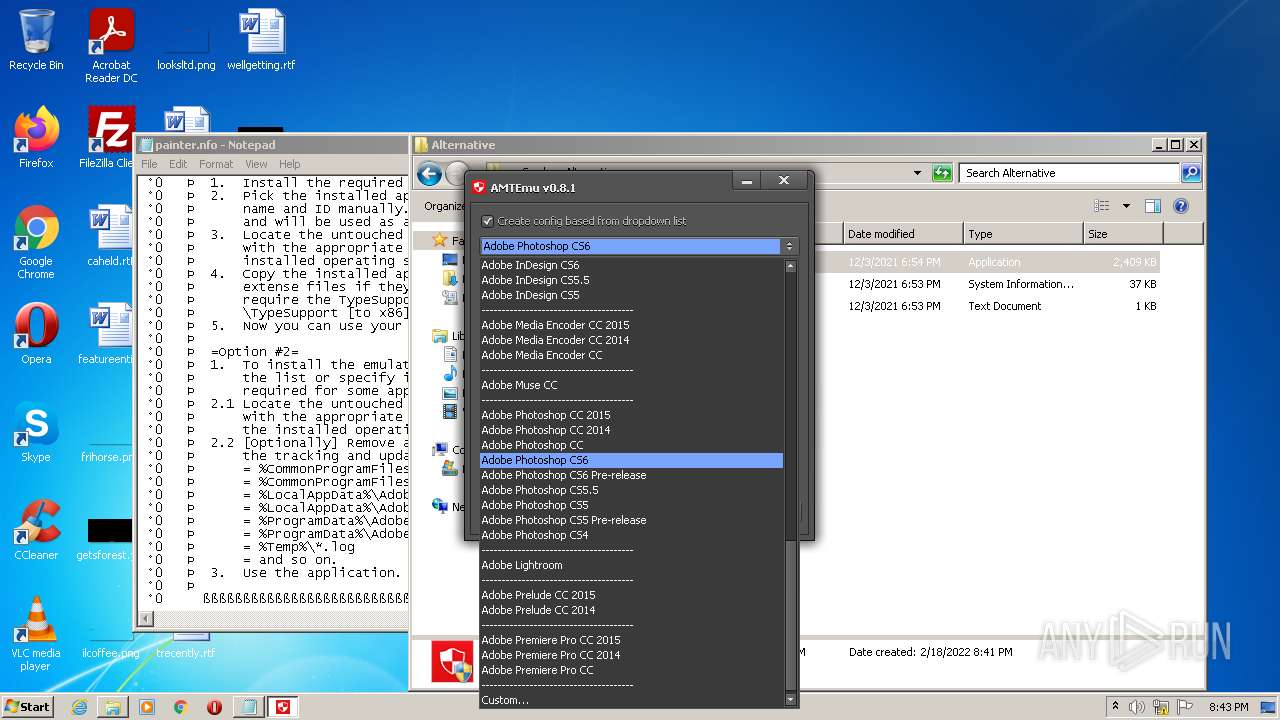
| 3156 | "C:\Users\admin\Desktop\Crack\Alternative\amtemu.v0.81-painter.exe" | C:\Users\admin\Desktop\Crack\Alternative\amtemu.v0.81-painter.exe | — | Explorer.EXE | |||||||||||
User: admin Company: PainteR Integrity Level: MEDIUM Description: ProxyEmu Exit code: 3221226540 Version: 0.8.1.0 Modules
| |||||||||||||||
| 3724 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Crack.7z" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4048 | "C:\Users\admin\Desktop\Crack\Alternative\amtemu.v0.81-painter.exe" | C:\Users\admin\Desktop\Crack\Alternative\amtemu.v0.81-painter.exe | Explorer.EXE | ||||||||||||
User: admin Company: PainteR Integrity Level: HIGH Description: ProxyEmu Exit code: 0 Version: 0.8.1.0 Modules
| |||||||||||||||
Total events
4 925
Read events
4 872
Write events
52
Delete events
1
Modification events
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Crack.7z | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
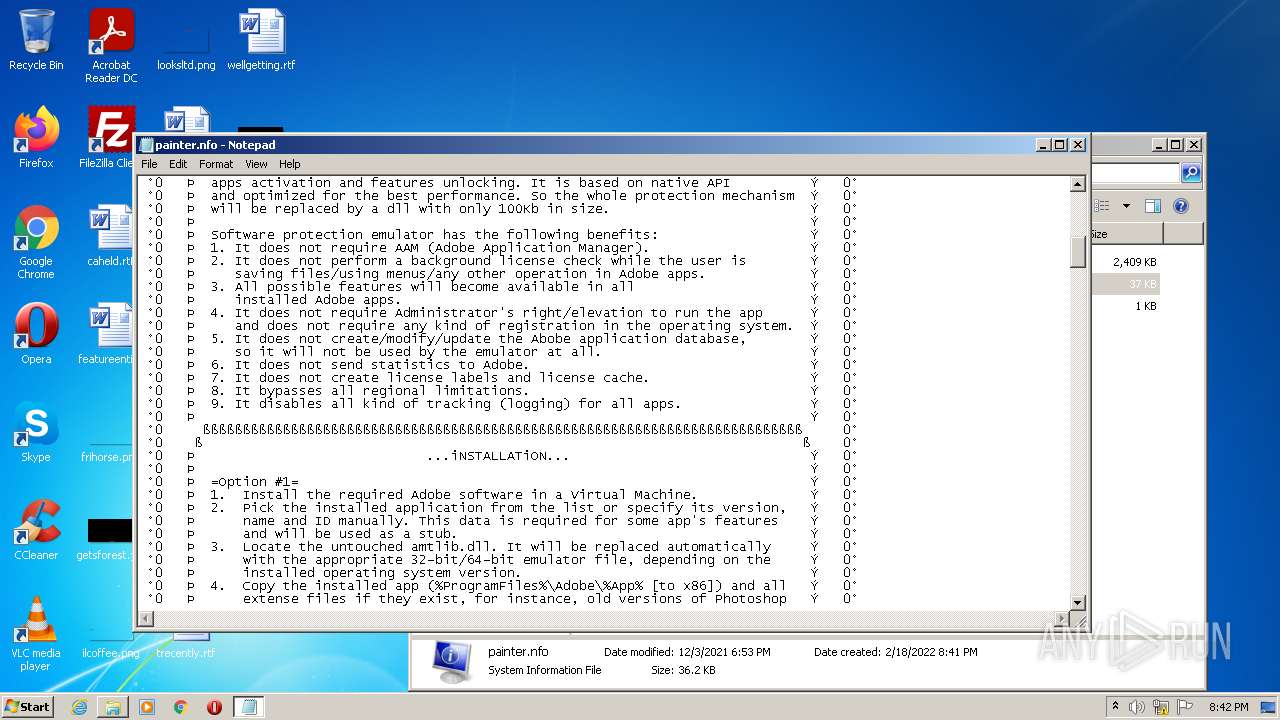
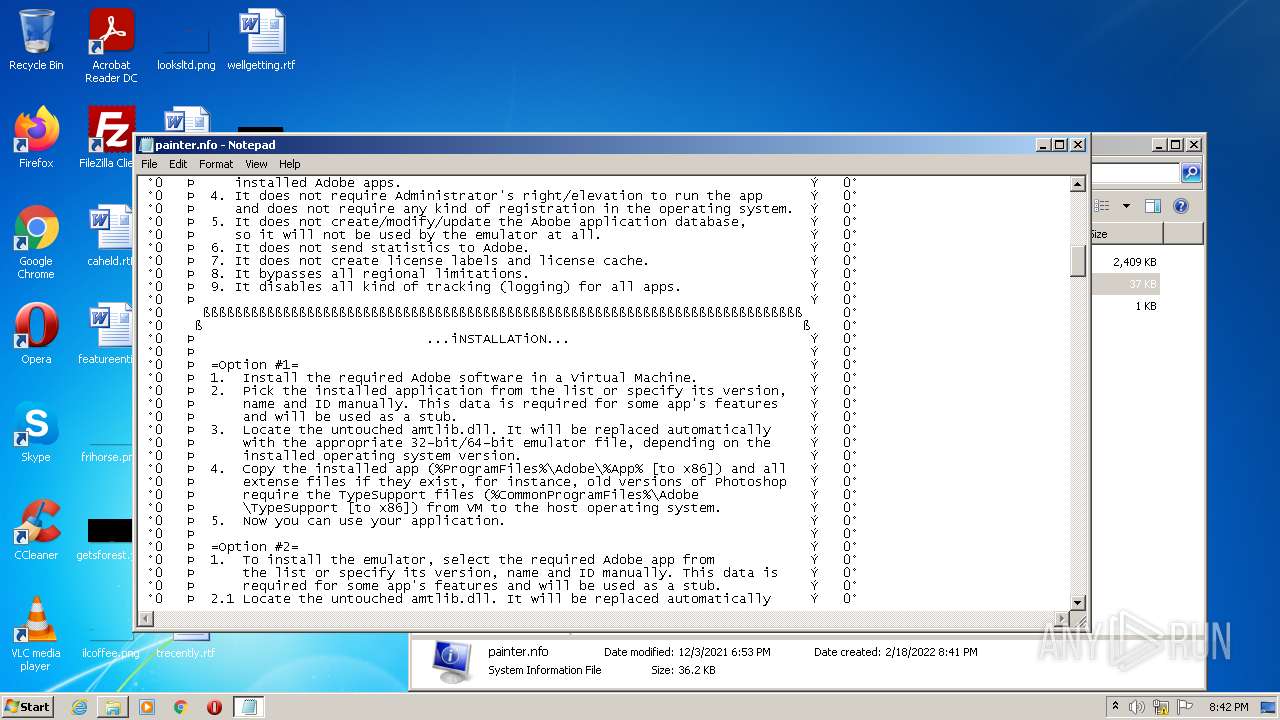
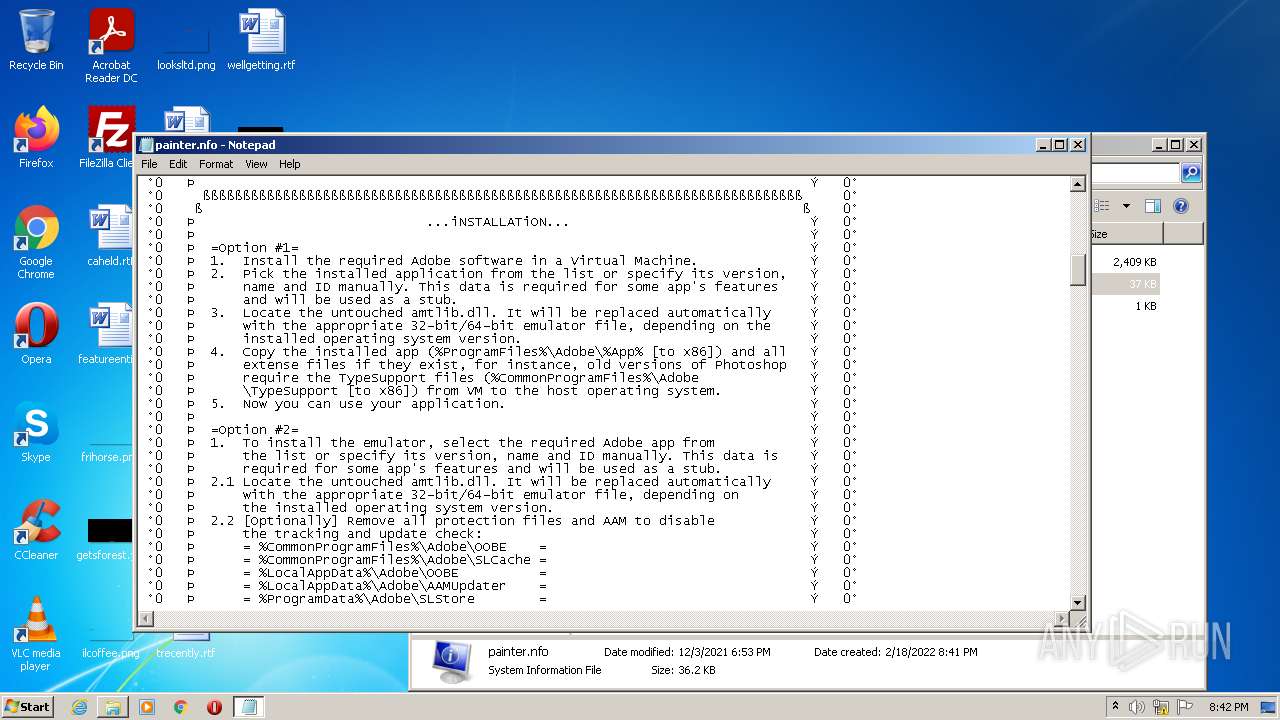
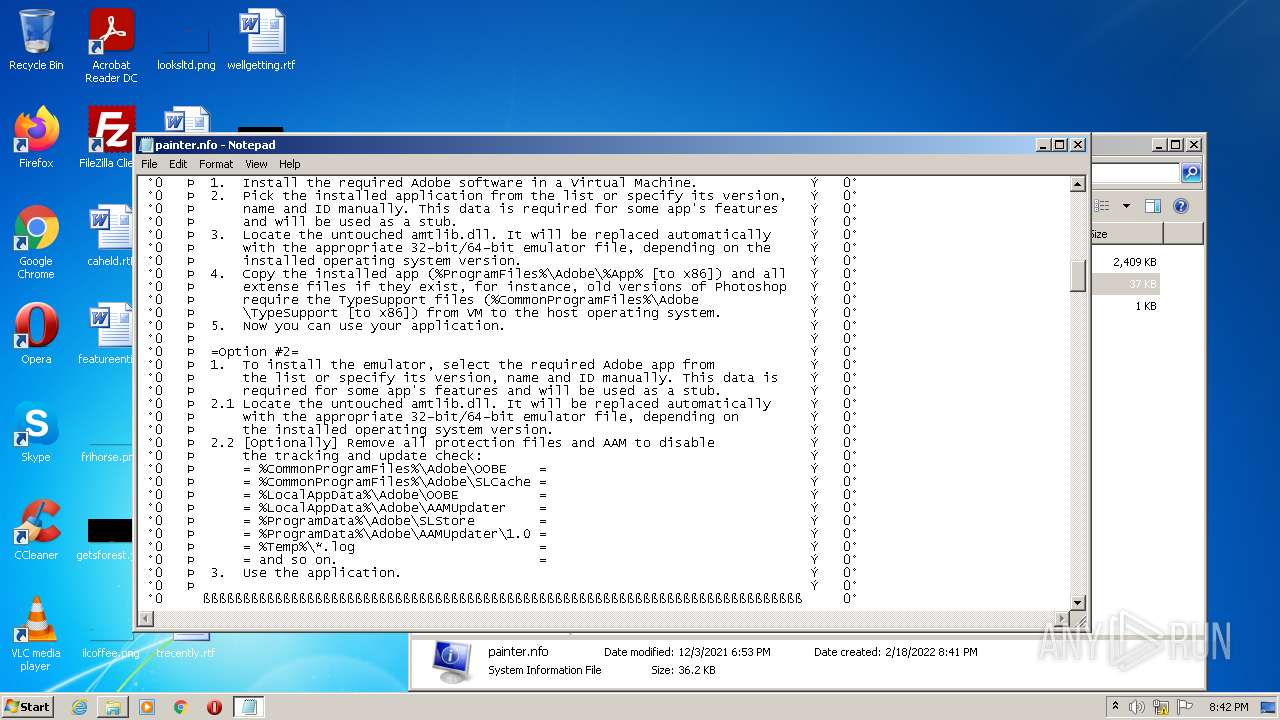
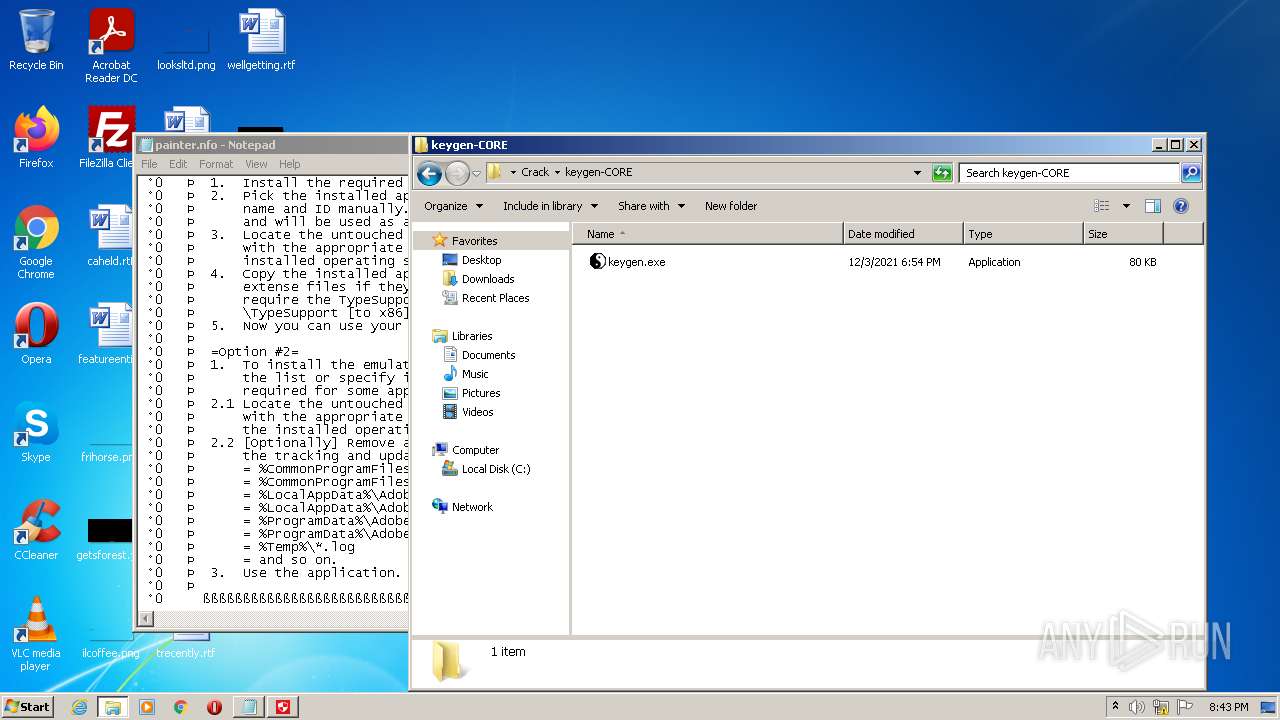
| 3724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3724.5649\Crack\Alternative\painter.nfo | text | |
MD5:4542380B402A369E4B42B5943FE2921F | SHA256:EC9EB36C1569FA8919F05528DE8057A2D2E6D01CDCDFEC9829DF7EF2971419FF | |||
| 3724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3724.5649\Crack\keygen-X-FORCE\disable_activation.cmd | text | |
MD5:05F4F2EFF4C3A025E99233B653EDC260 | SHA256:53FF64DCDACAC89544E19E2B52DBF2FFCBB5E45614CF5D1502F5F8E77E862066 | |||
| 3724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3724.5649\Crack\keygen-X-FORCE\readme.txt | text | |
MD5:3CB036961DB1F7F2644C22669829FAA8 | SHA256:131DACC9DB28D7104DBE374D12E12B3E1CE7C0230AC5FD9CBCCCE9C18B63C008 | |||
| 3724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3724.5649\Crack\Alternative\amtemu.v0.81-painter.exe | executable | |
MD5:033560EC0C5FB31D80728875D6EA0CB4 | SHA256:AA291205F0831A4544495B8B143D279BF2D3604BC9C080D5D6627FAE7D7D29B5 | |||
| 3724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3724.5649\Crack\Alternative\??????????.txt | text | |
MD5:C78278204978B5149331253E9780D140 | SHA256:5A8A90A0CCDCE96AB54F630F165B594B8CB89931797C449D7523557E66A4343A | |||
| 3724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3724.5649\Crack\keygen-X-FORCE\xf-mccs6.exe | executable | |
MD5:1AF76EF8857935EB1D8E46DC9CFE3729 | SHA256:AC2D47DC2D33E6123DA1F3AB00FEA3A1659CE0F47266CC9AB004FA4B811F3B21 | |||
| 3724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3724.5649\Crack\keygen-CORE\keygen.exe | executable | |
MD5:016B3F3D02B55E6729F7D363DBEA92BC | SHA256:0E89C004A33AA95AD09EFE0E22FF9D424911405E0F7E58D4CD53E4D503D03BF7 | |||
| 3724 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3724.5649\Crack\keygen-X-FORCE\install.txt | text | |
MD5:BE8F4A32D6CB53D517DE0C4BDDC17671 | SHA256:257A797799C933E84ACEA47AF84F618EB7763F710ECD850D58D62CFFDFB4CE52 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report