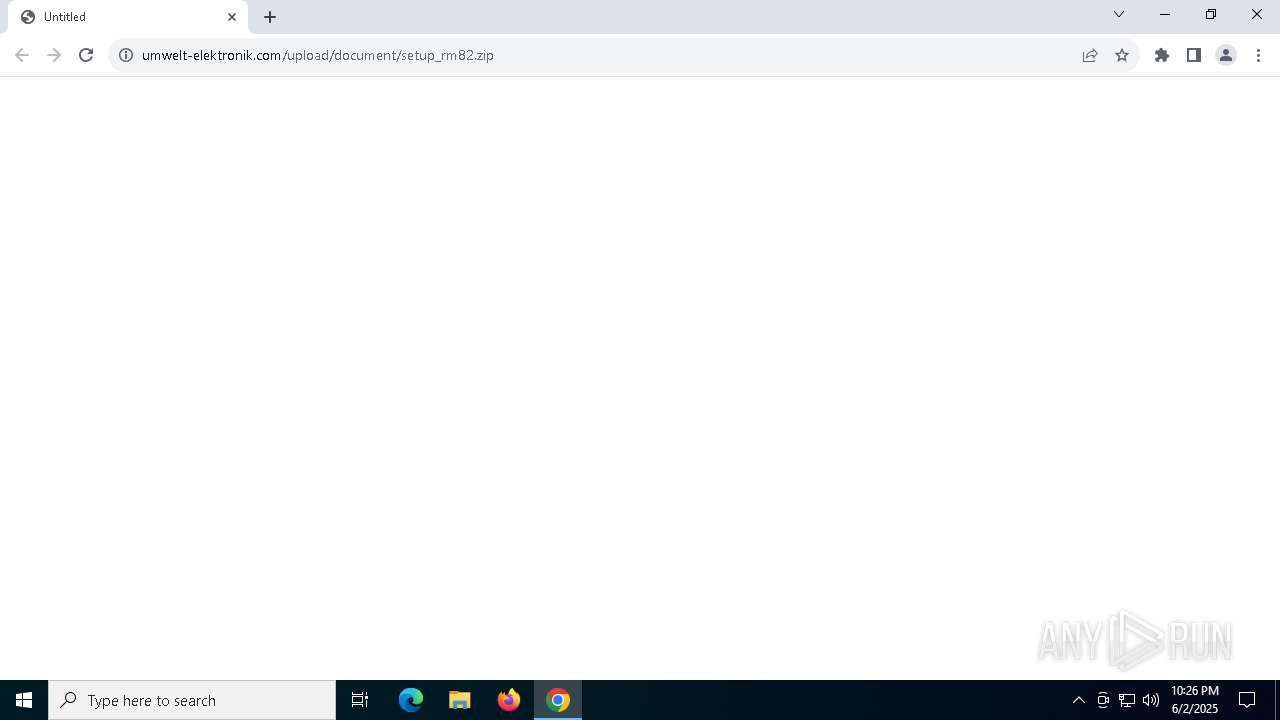
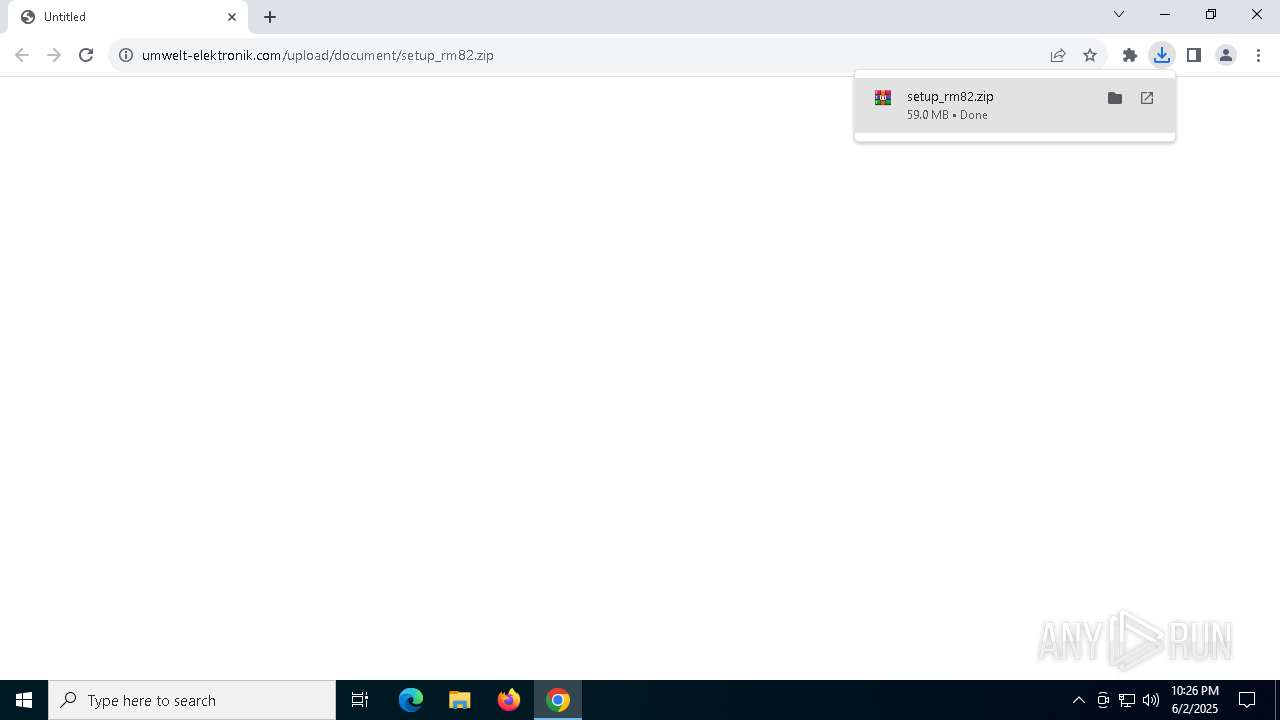
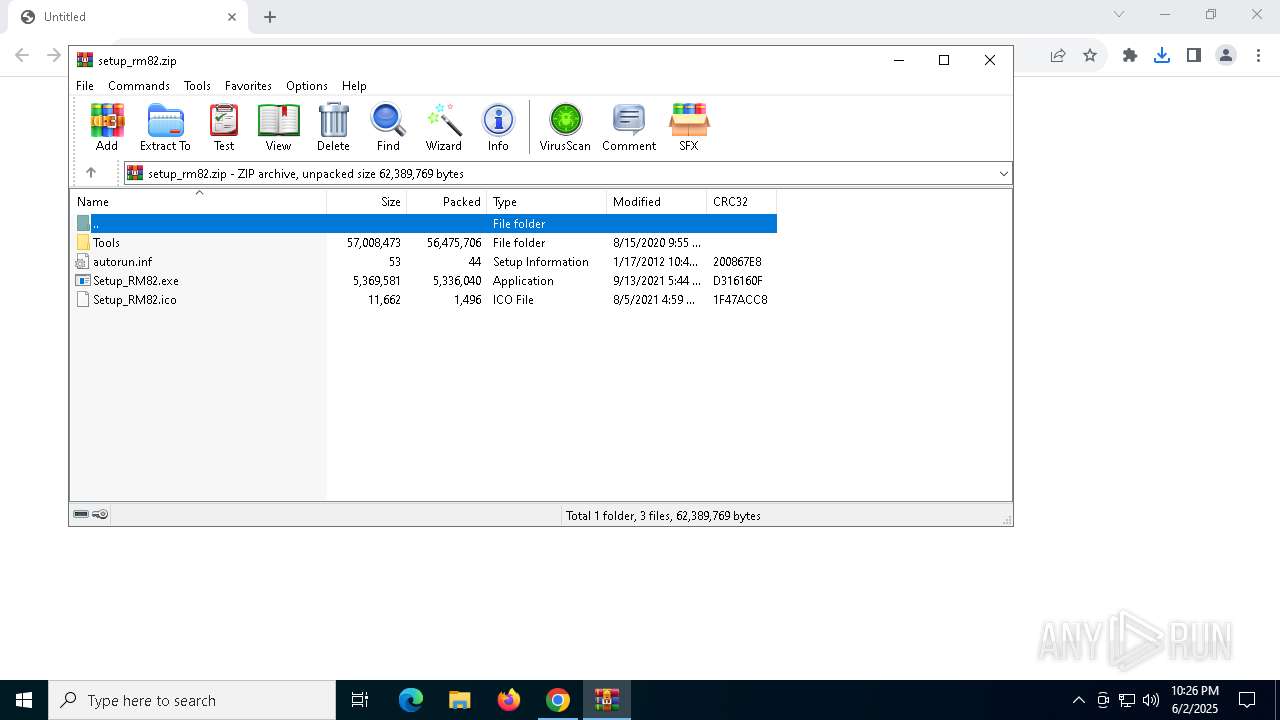
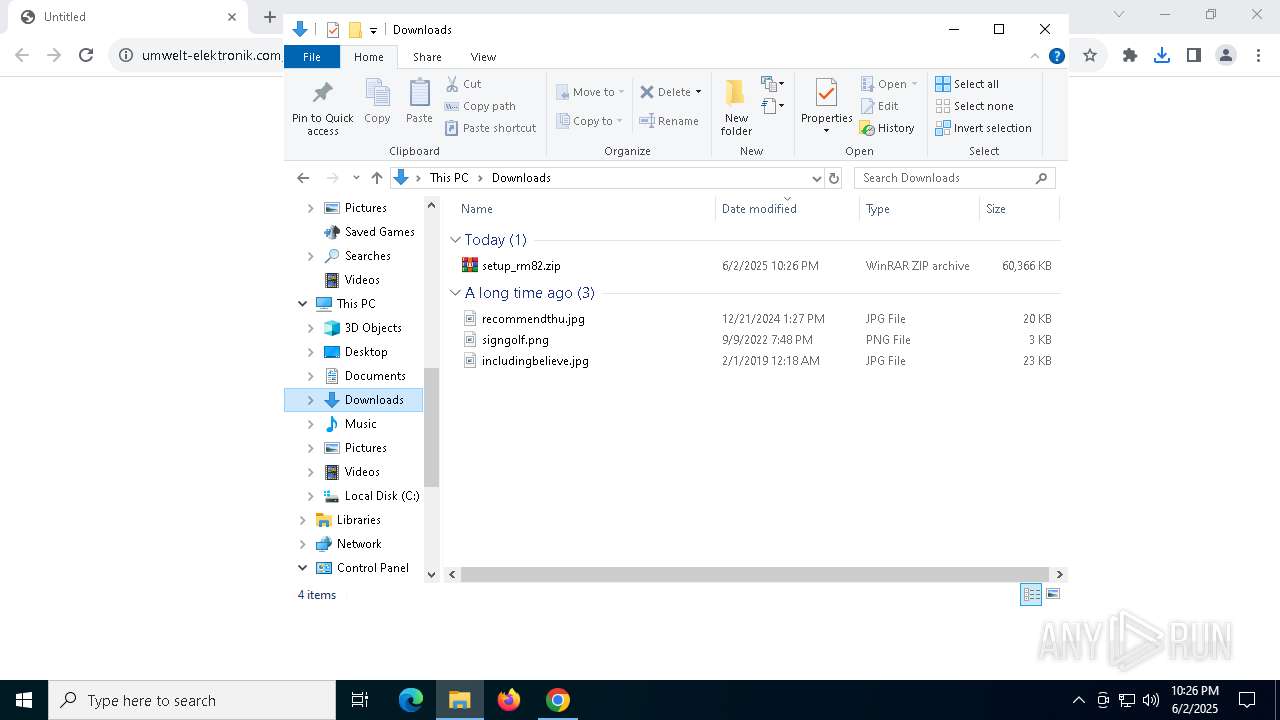
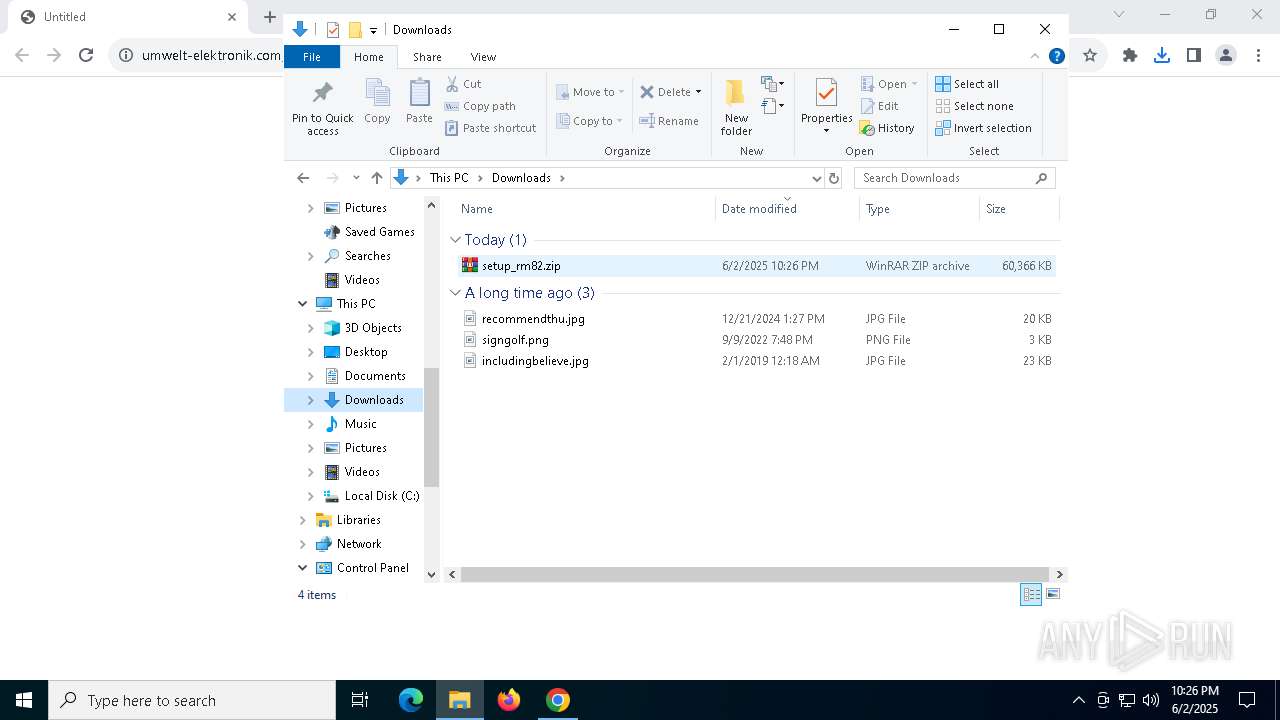
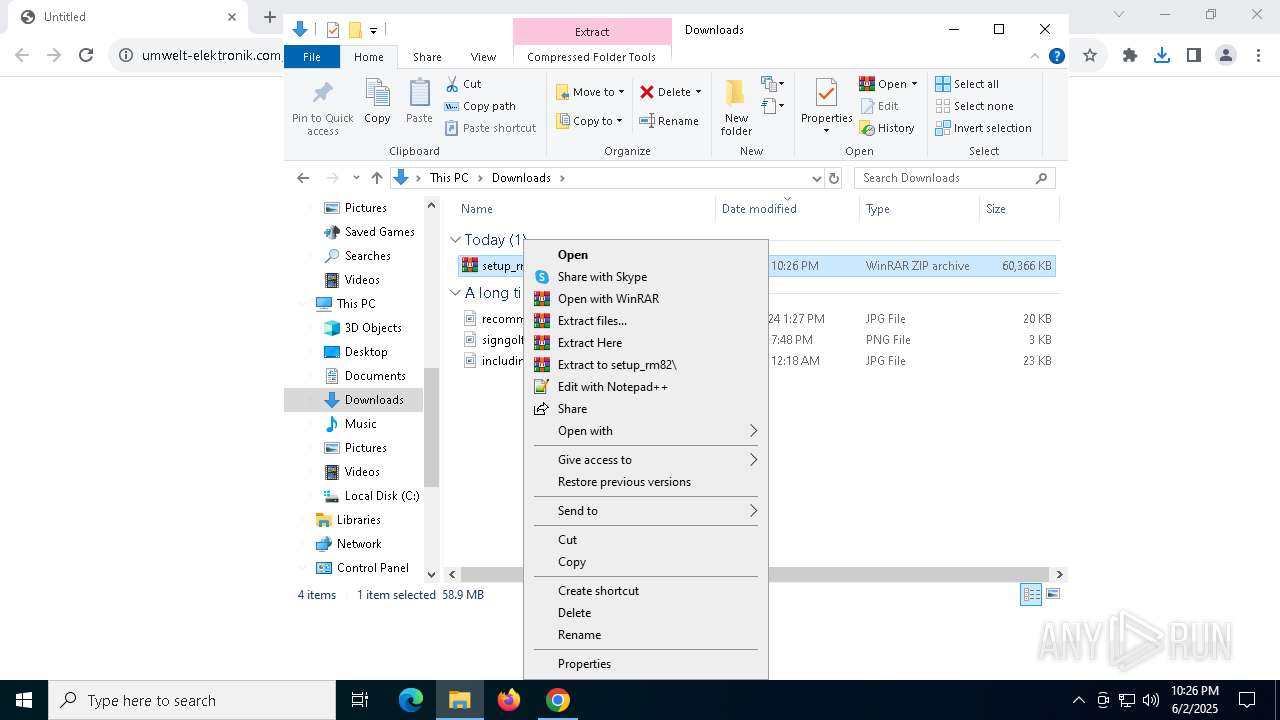
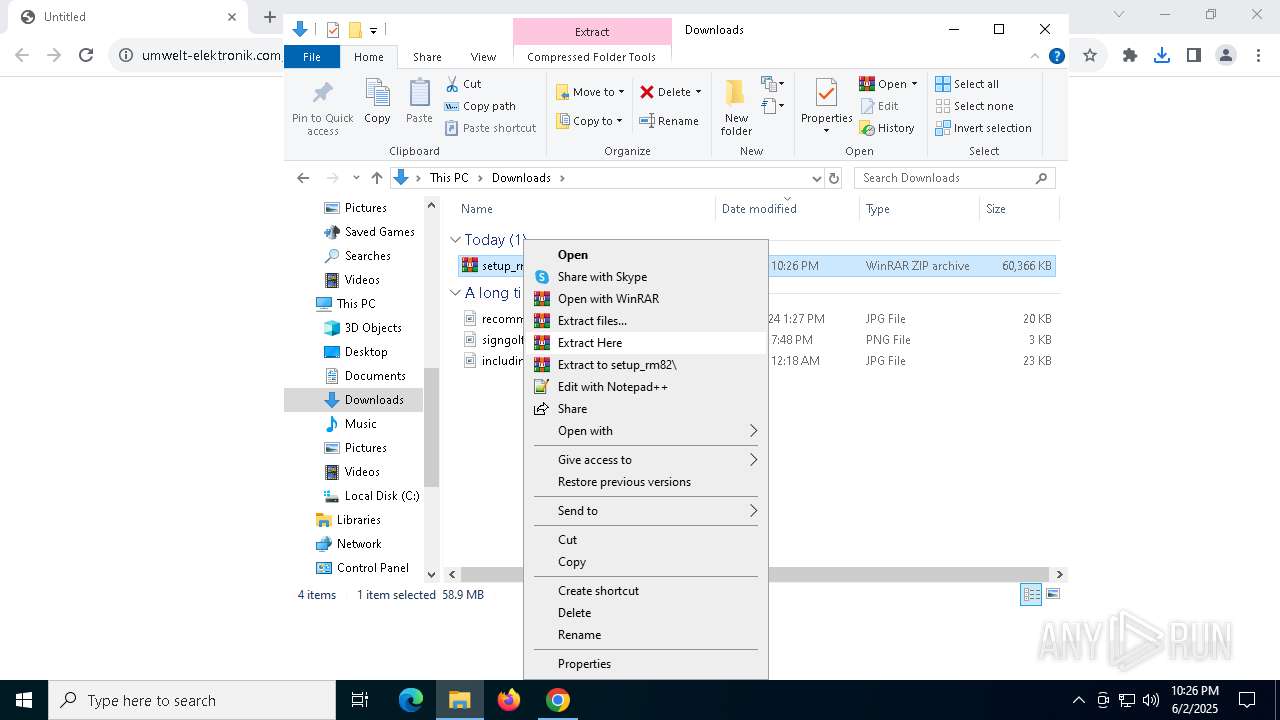
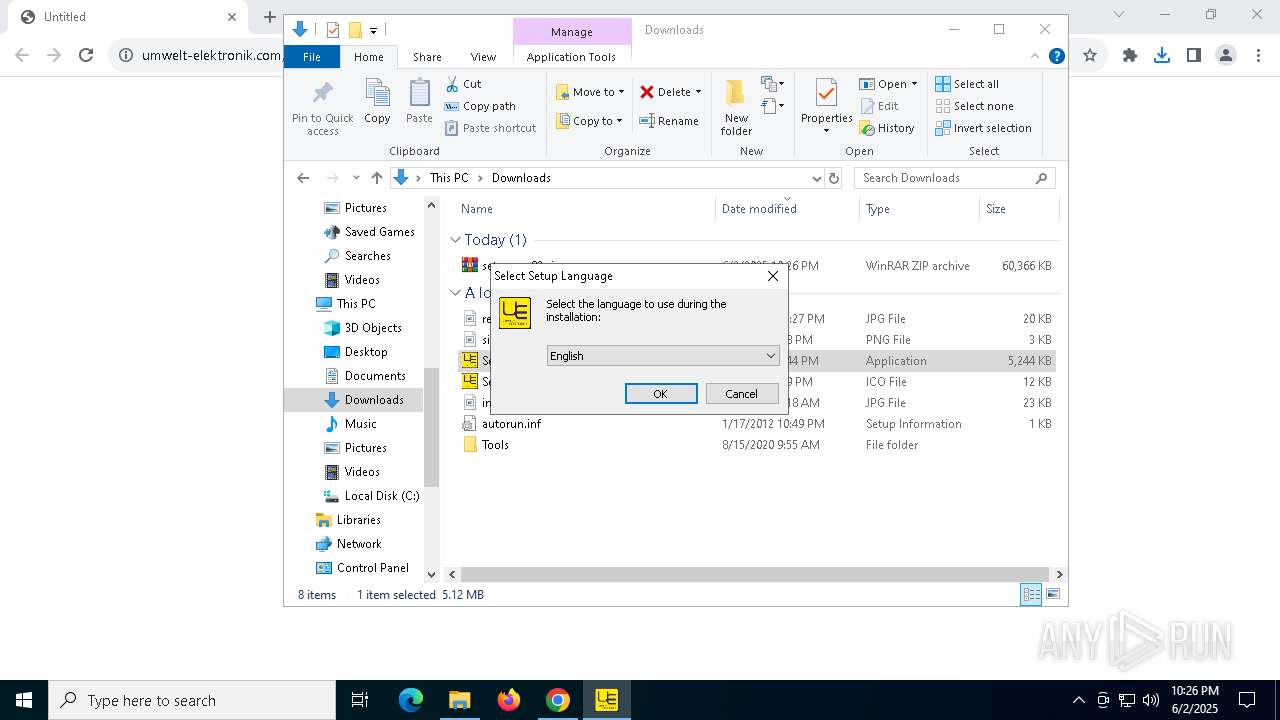
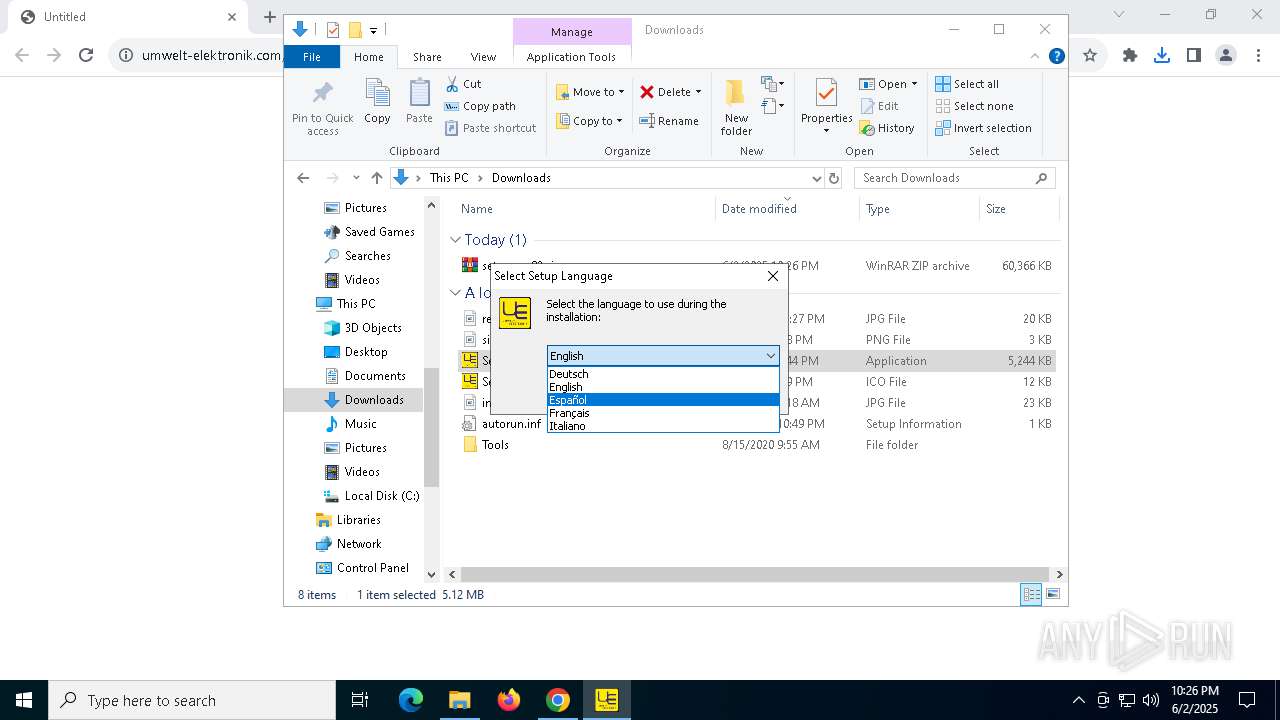
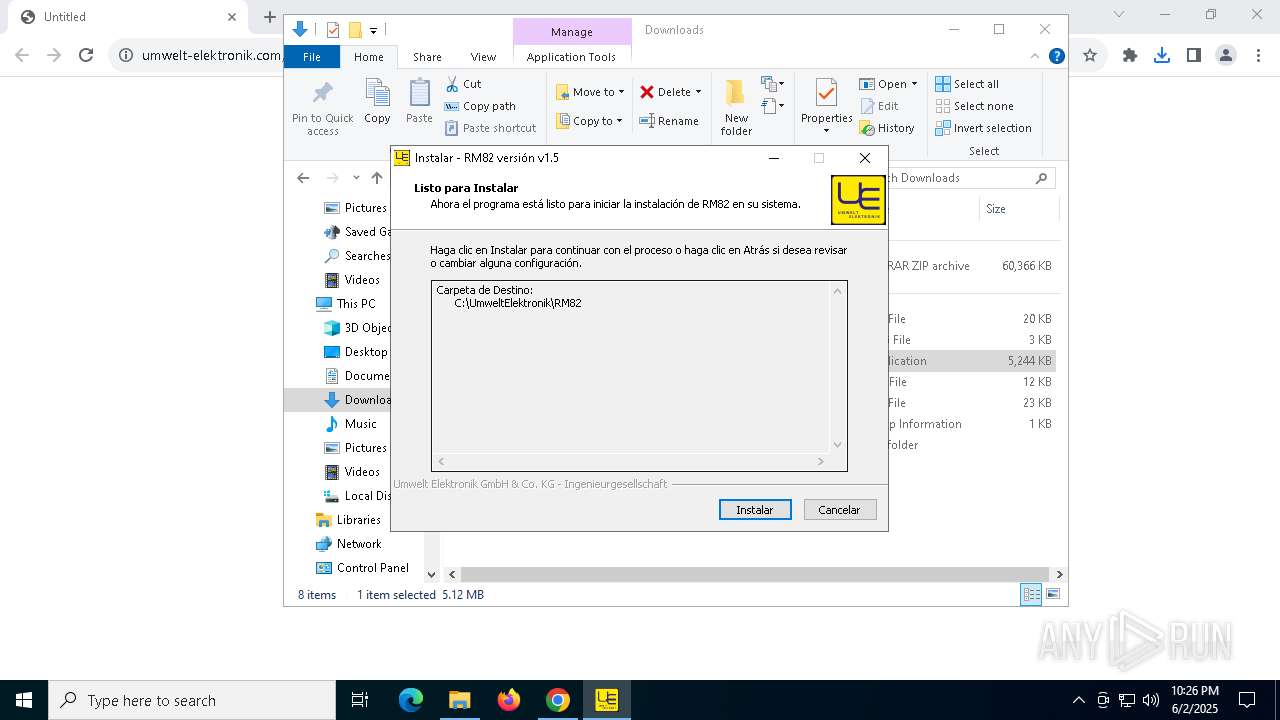
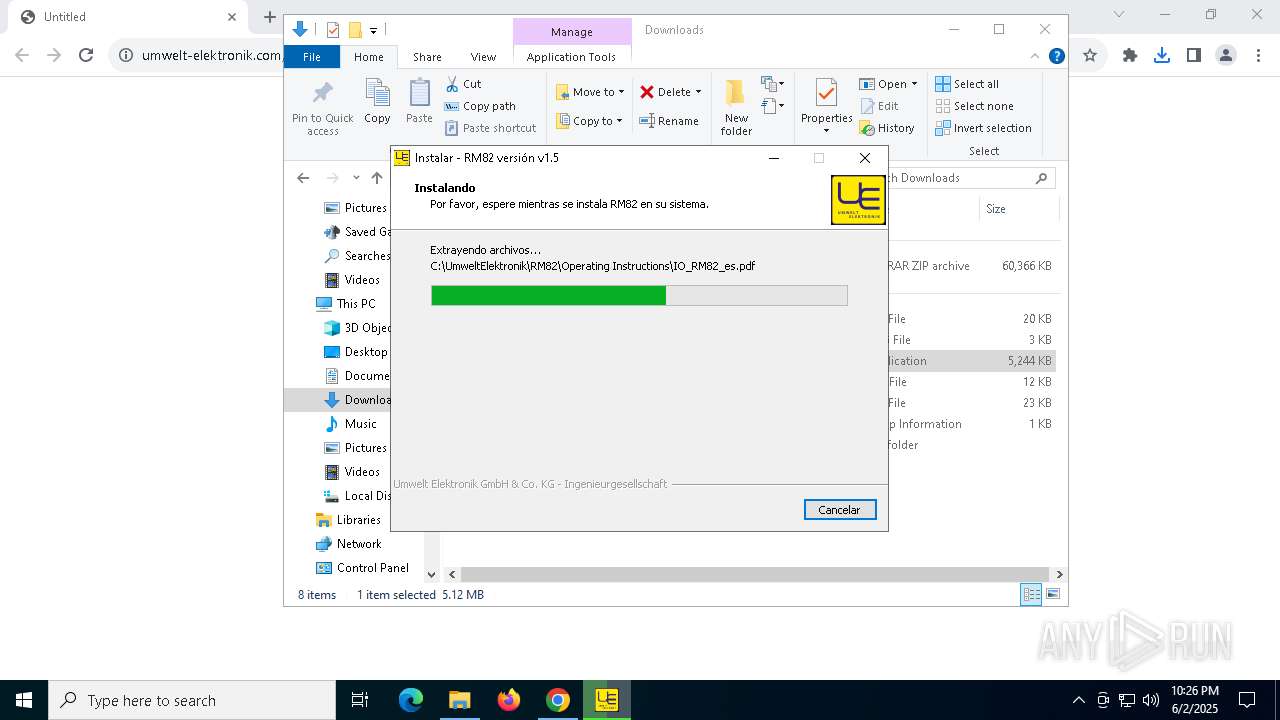
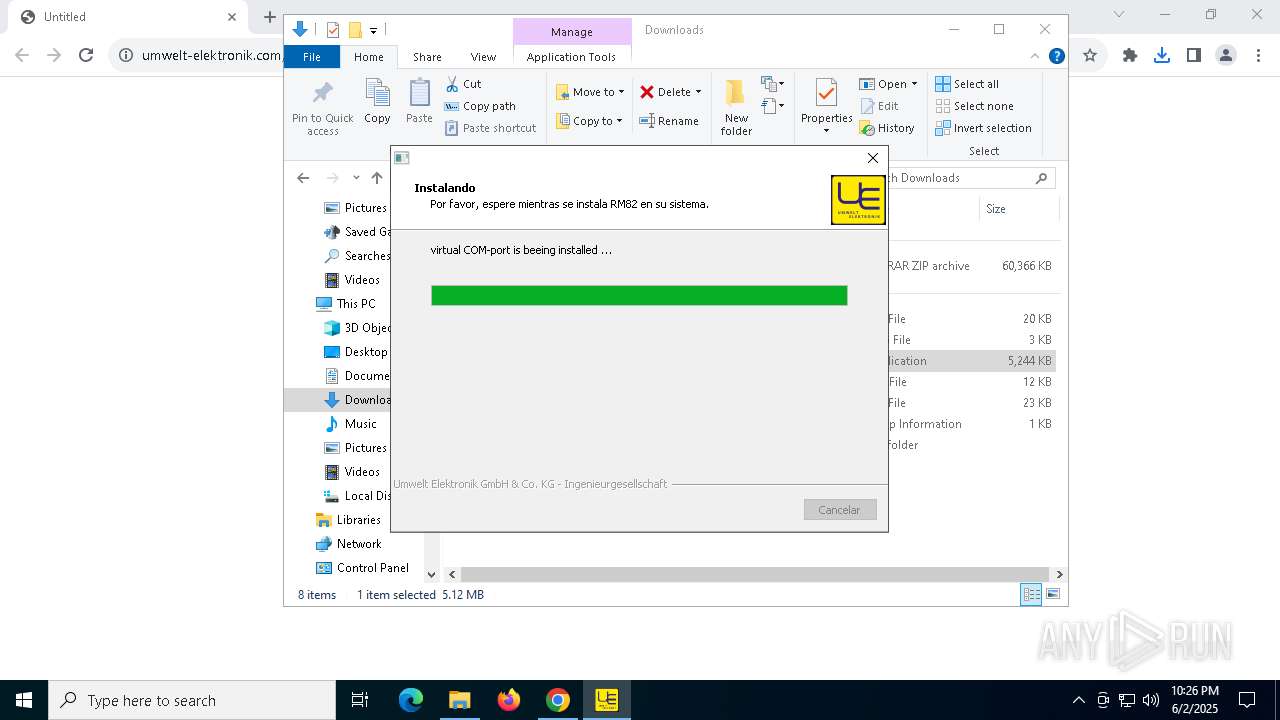
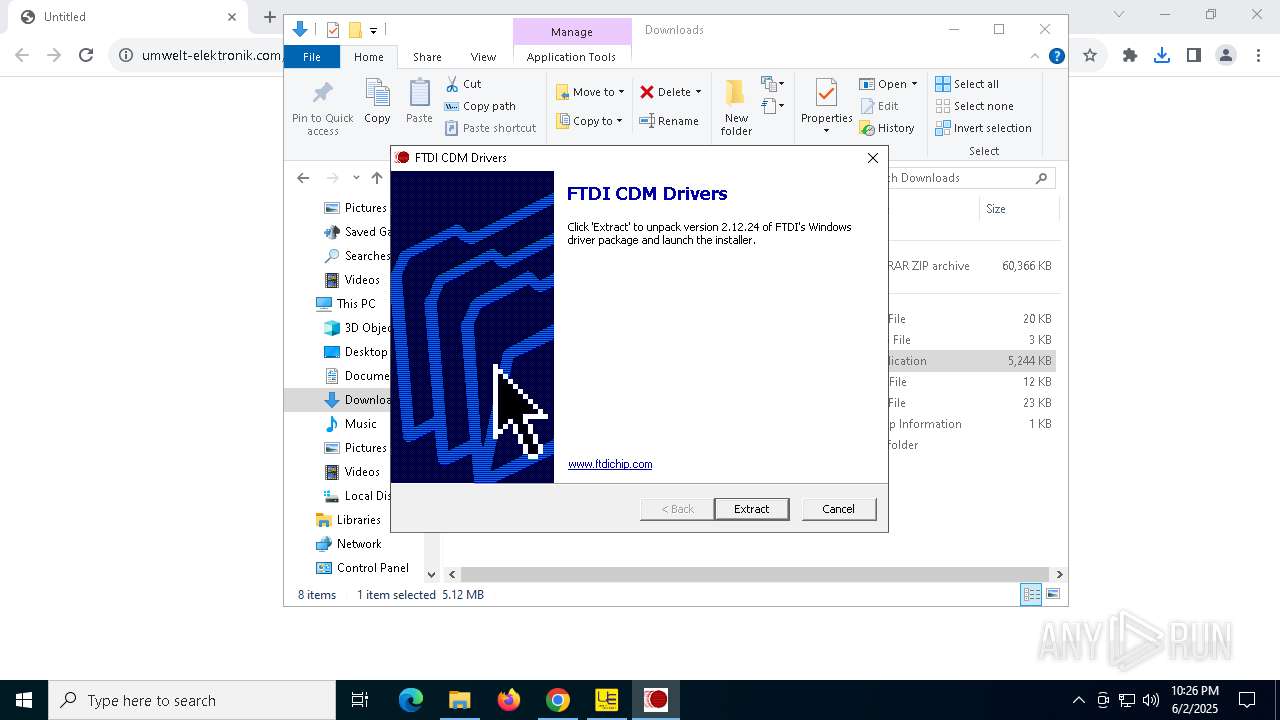
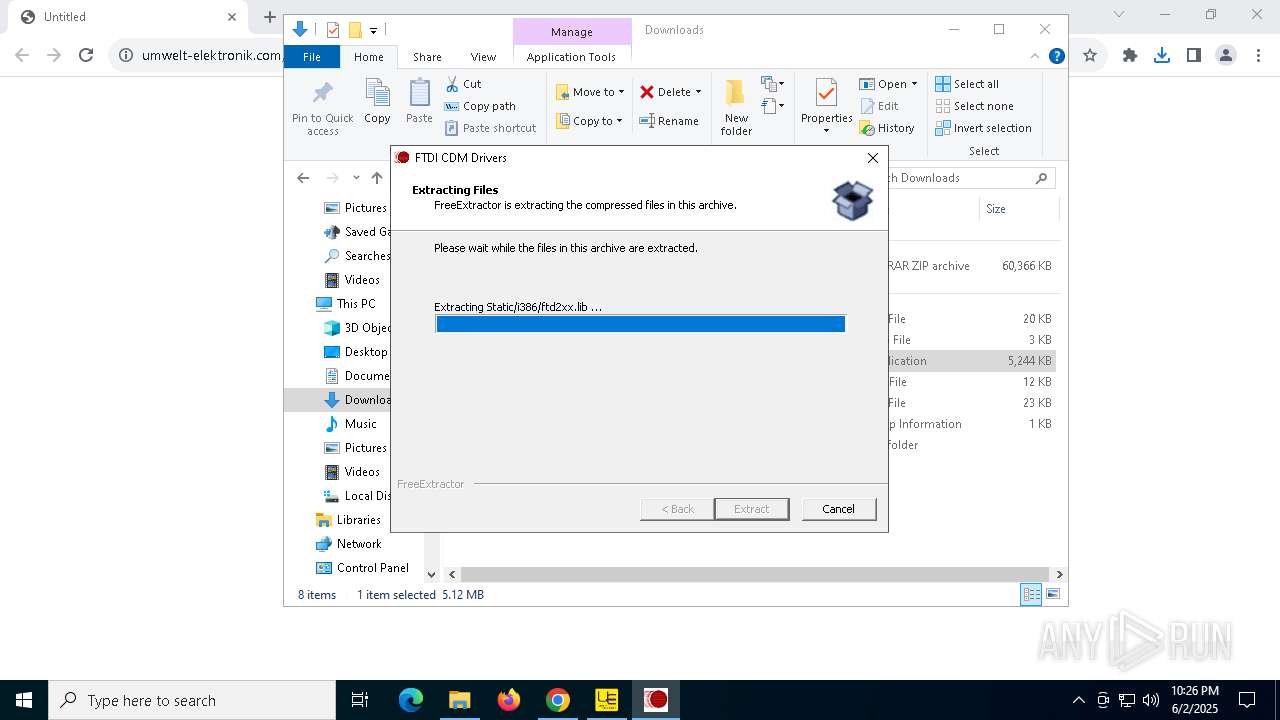
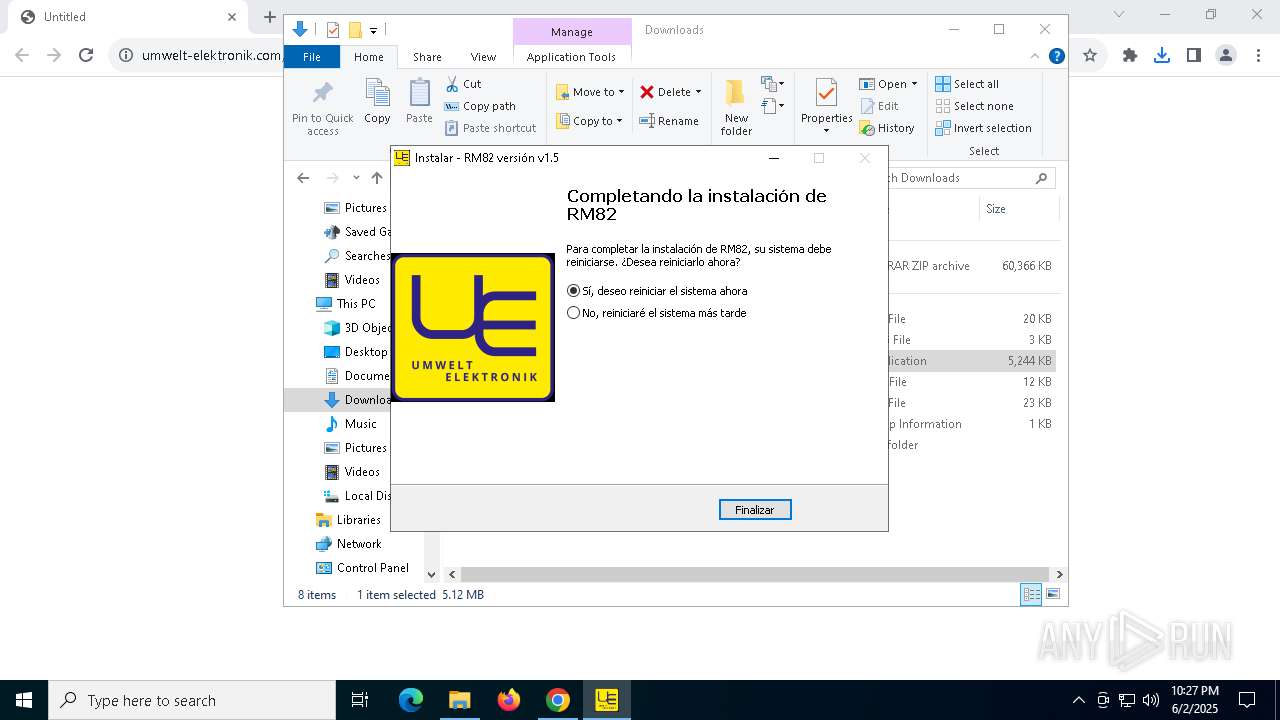
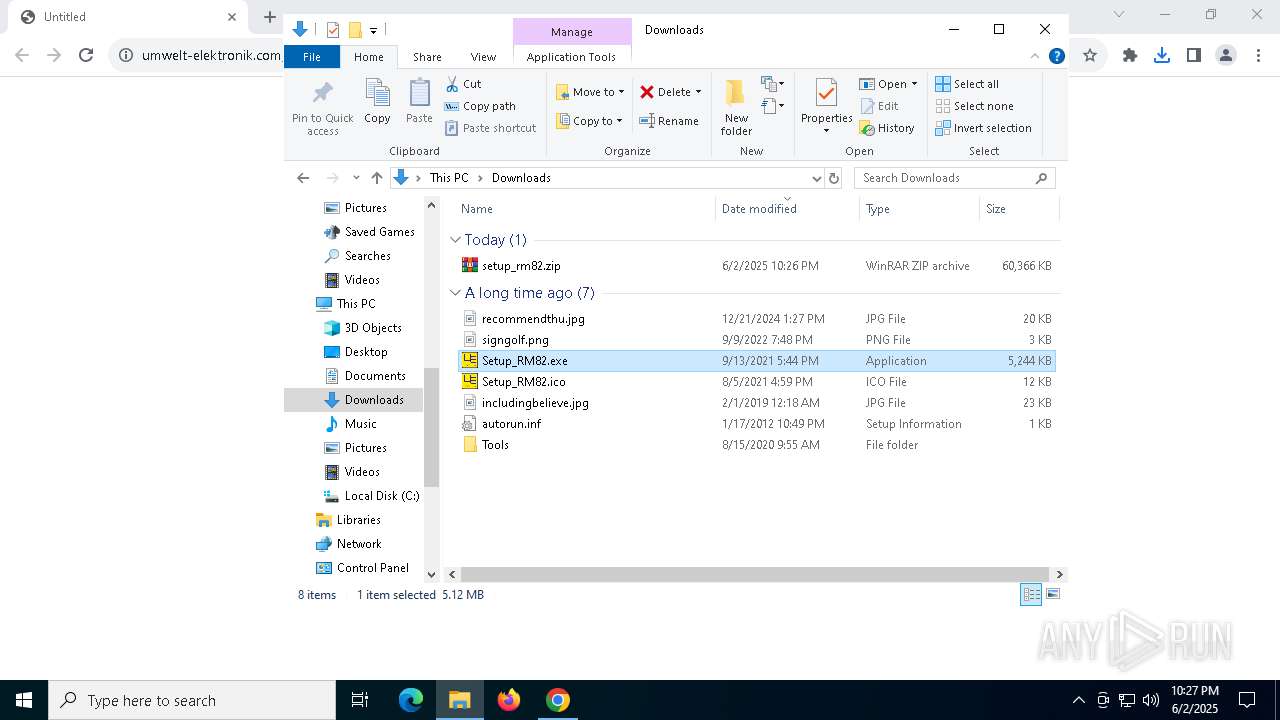
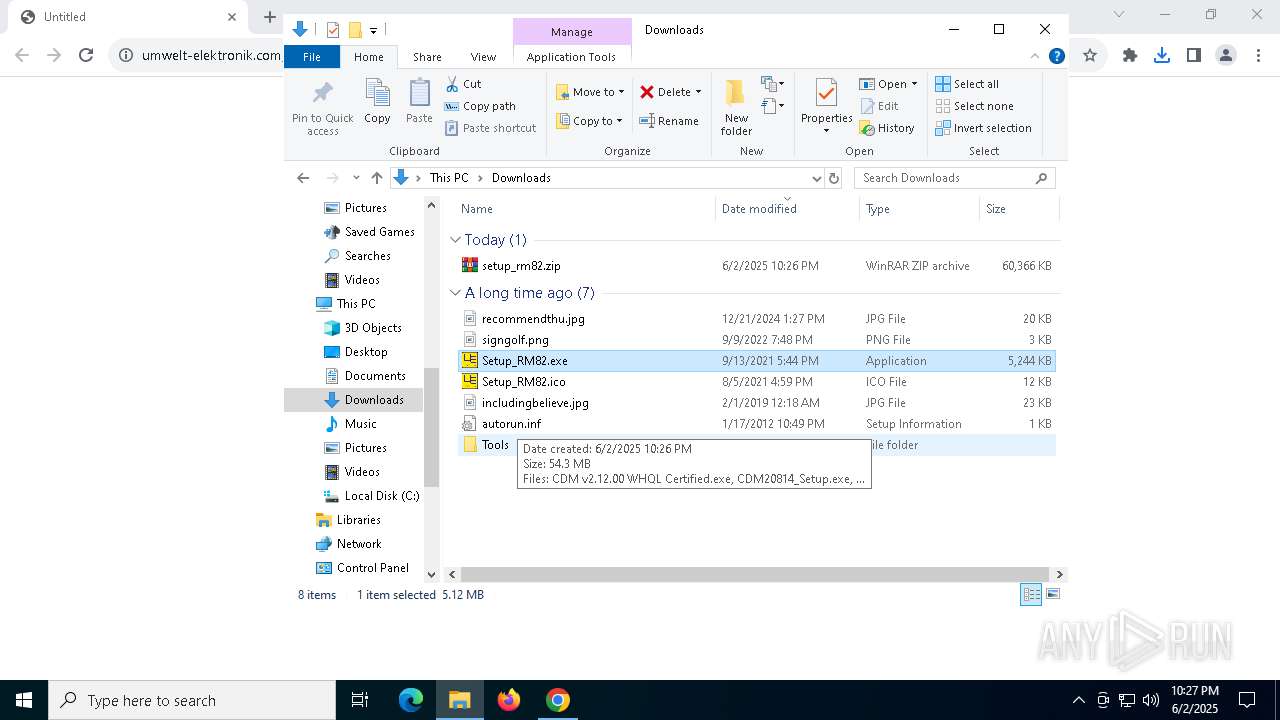
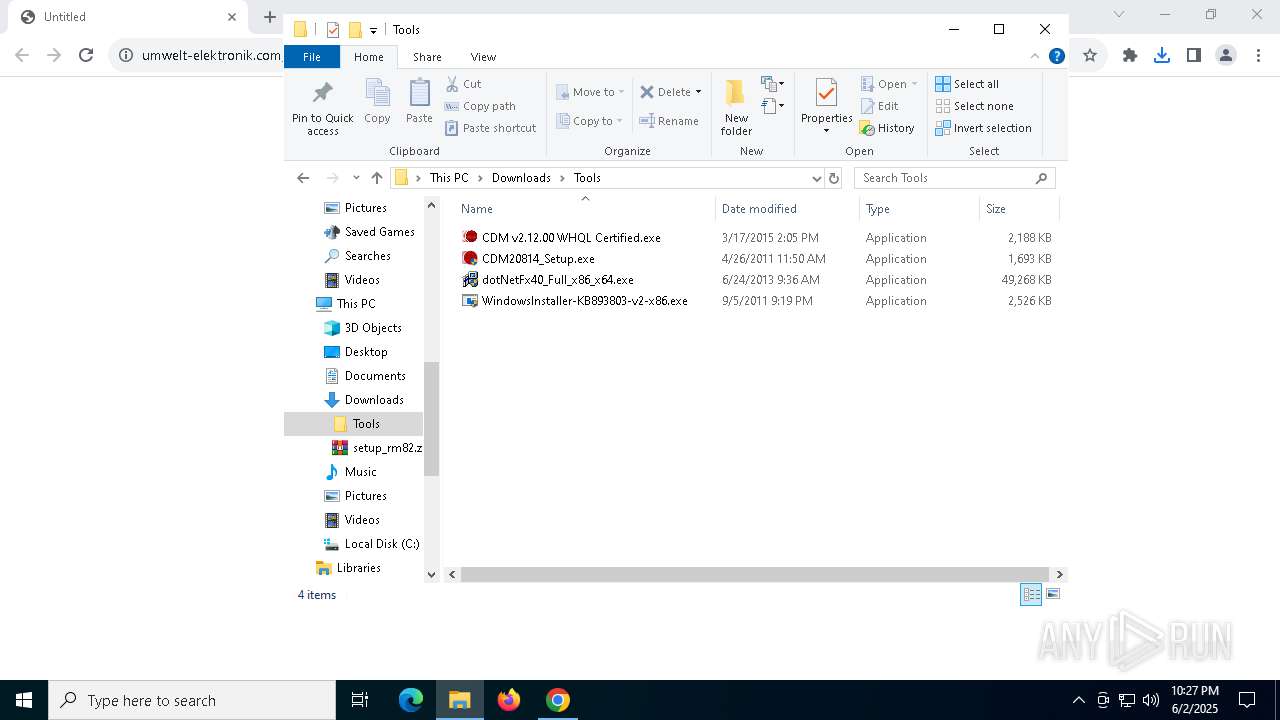
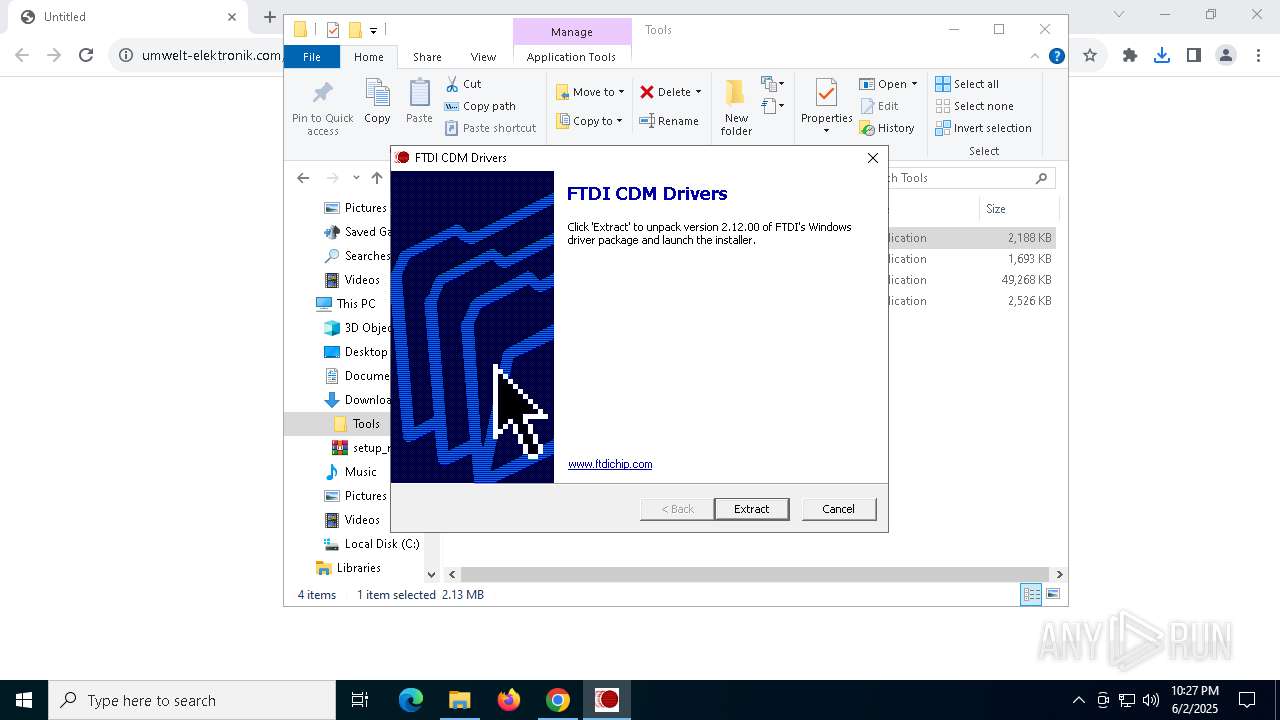
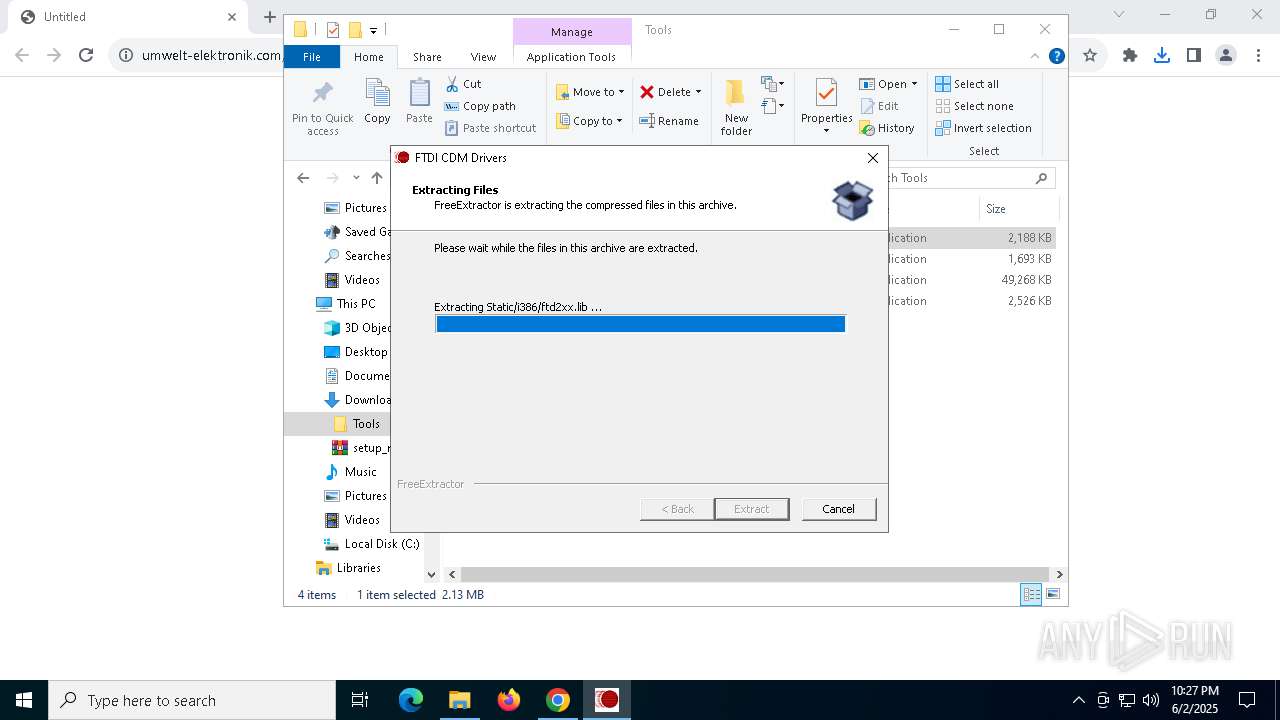
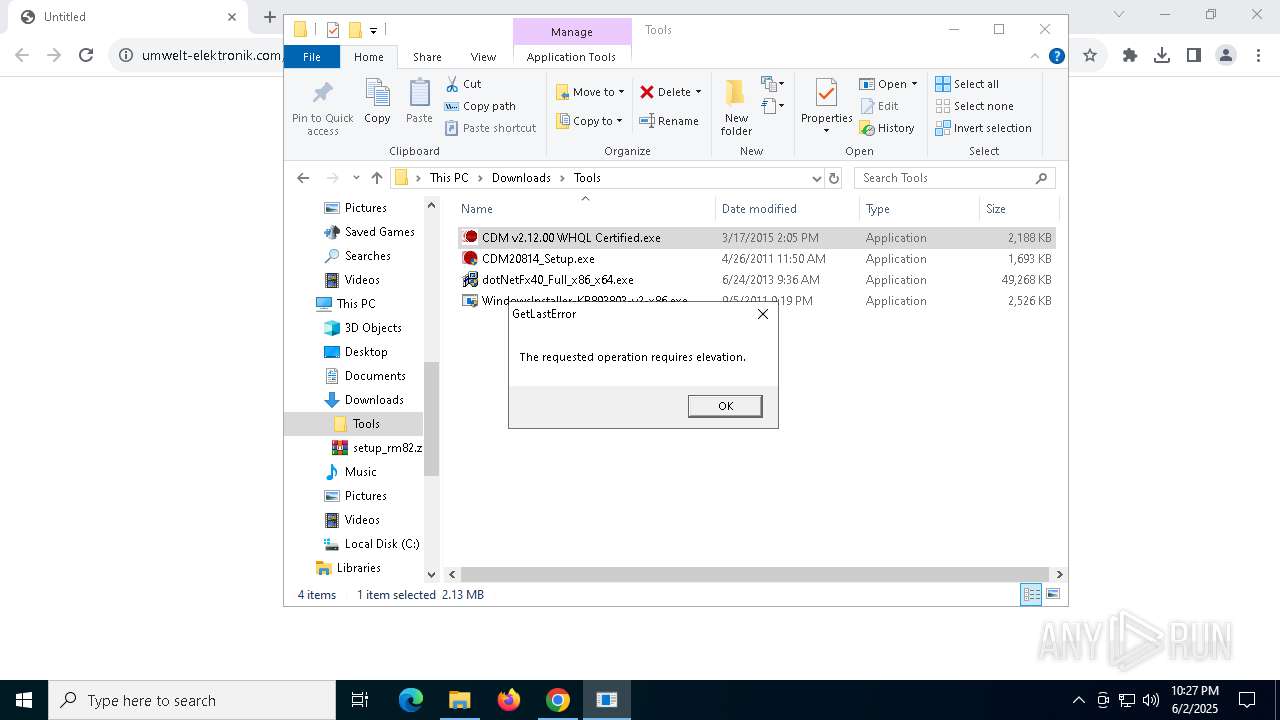
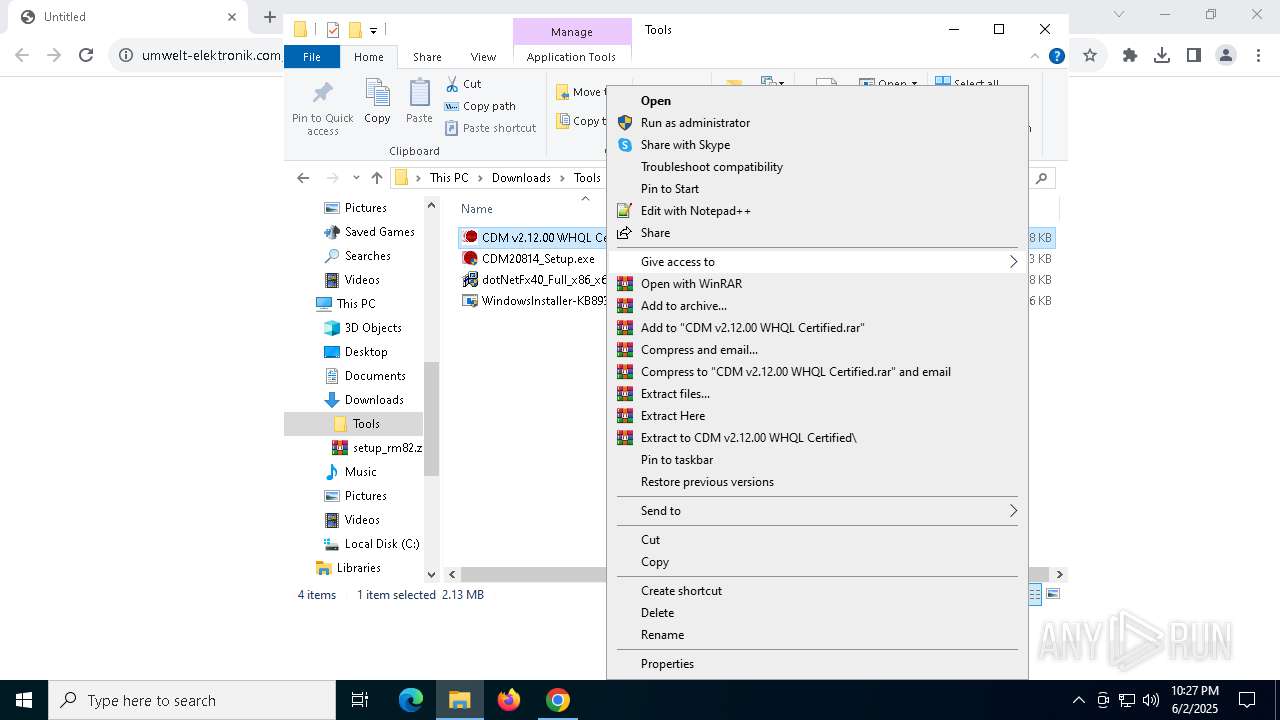
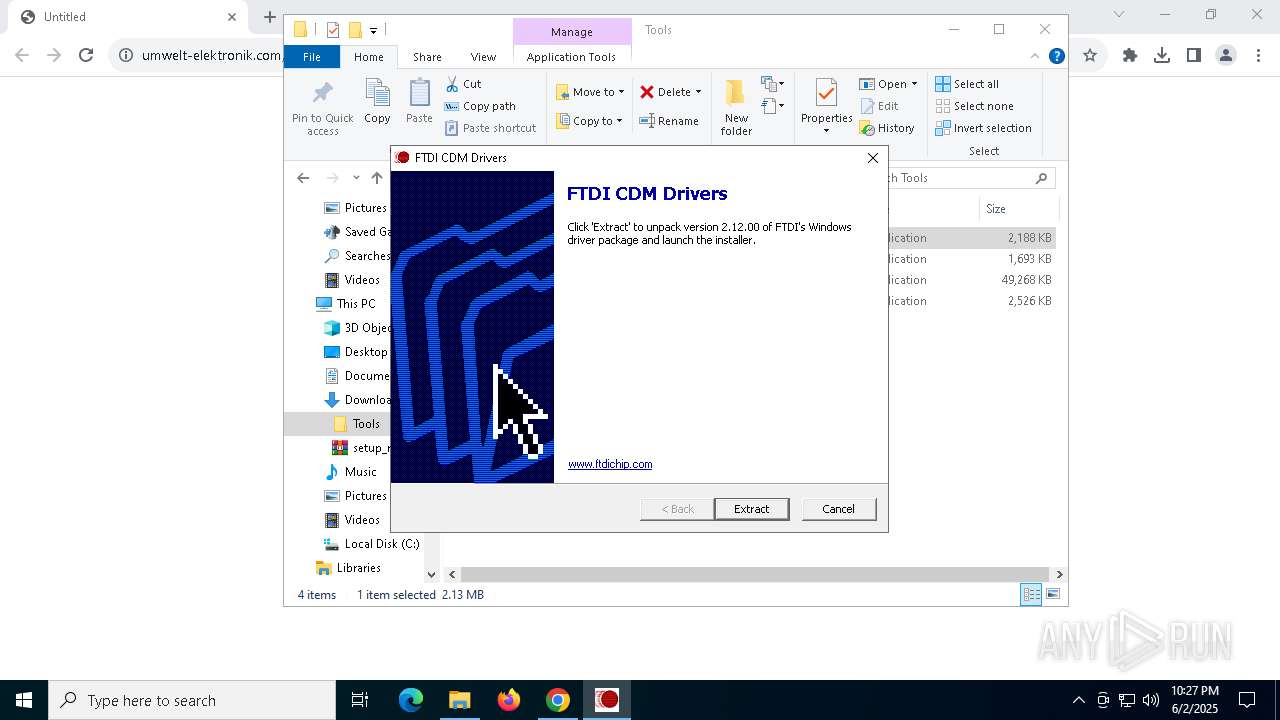
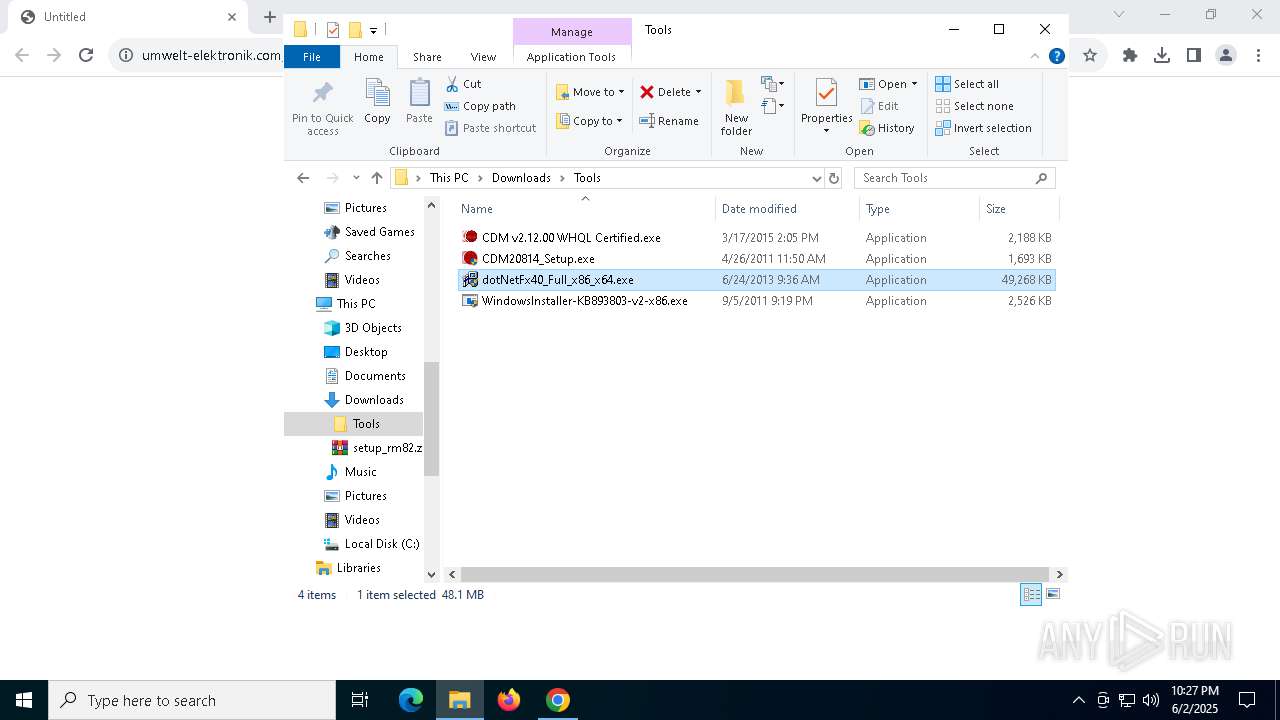
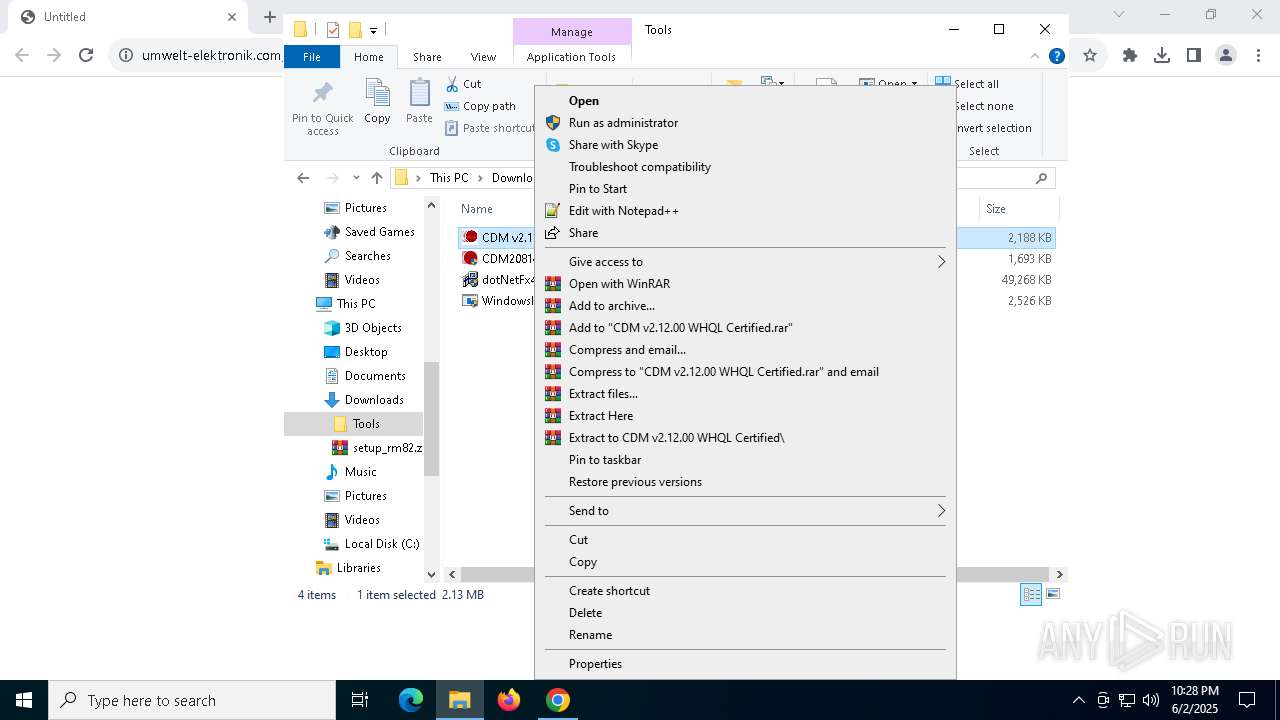
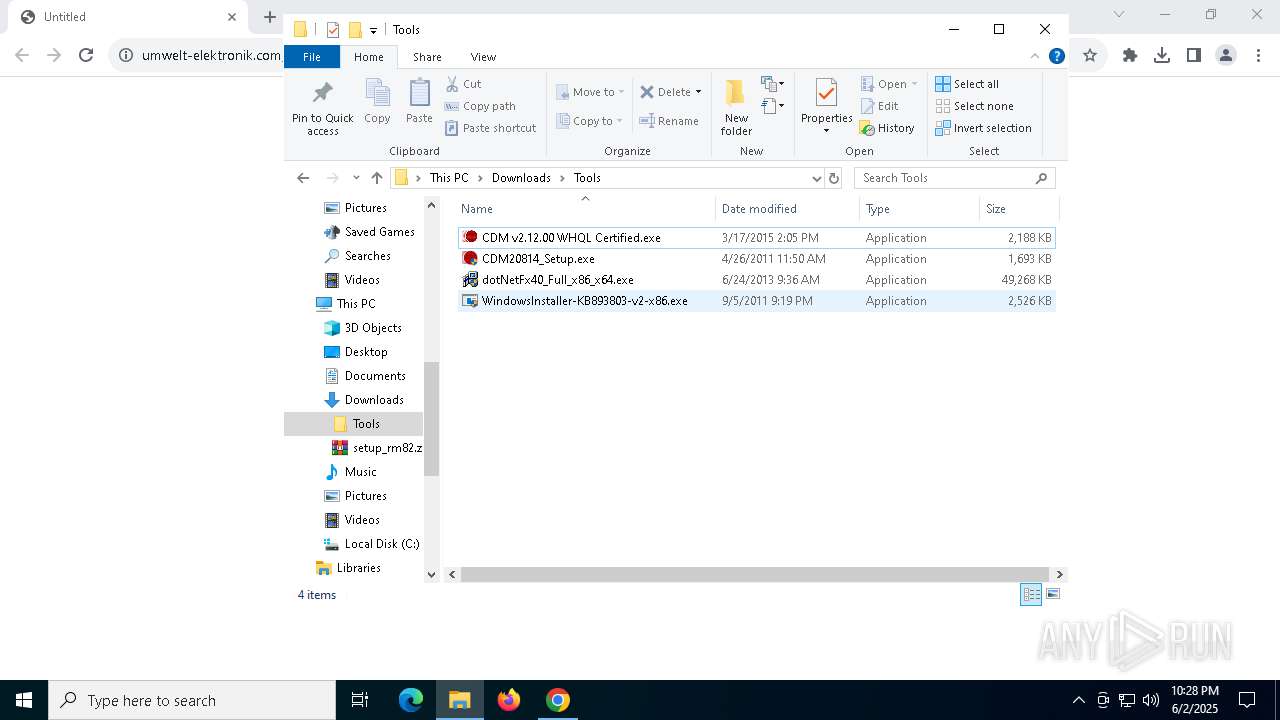
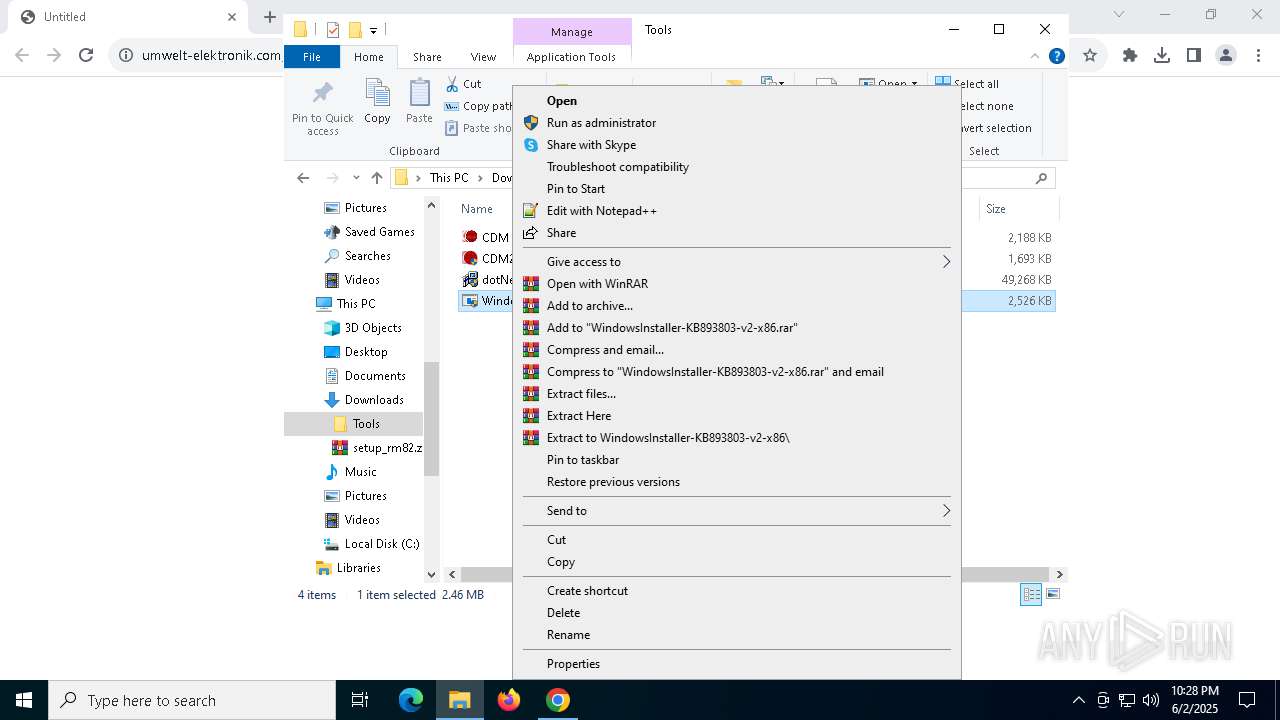
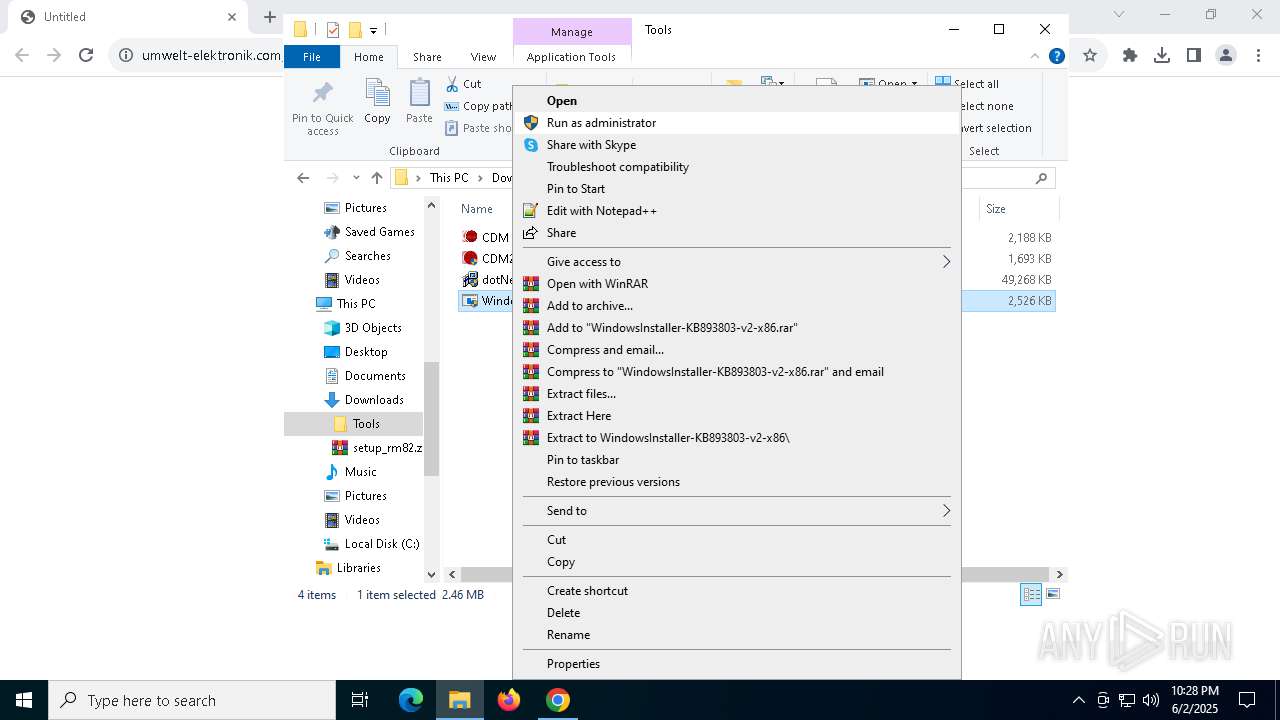
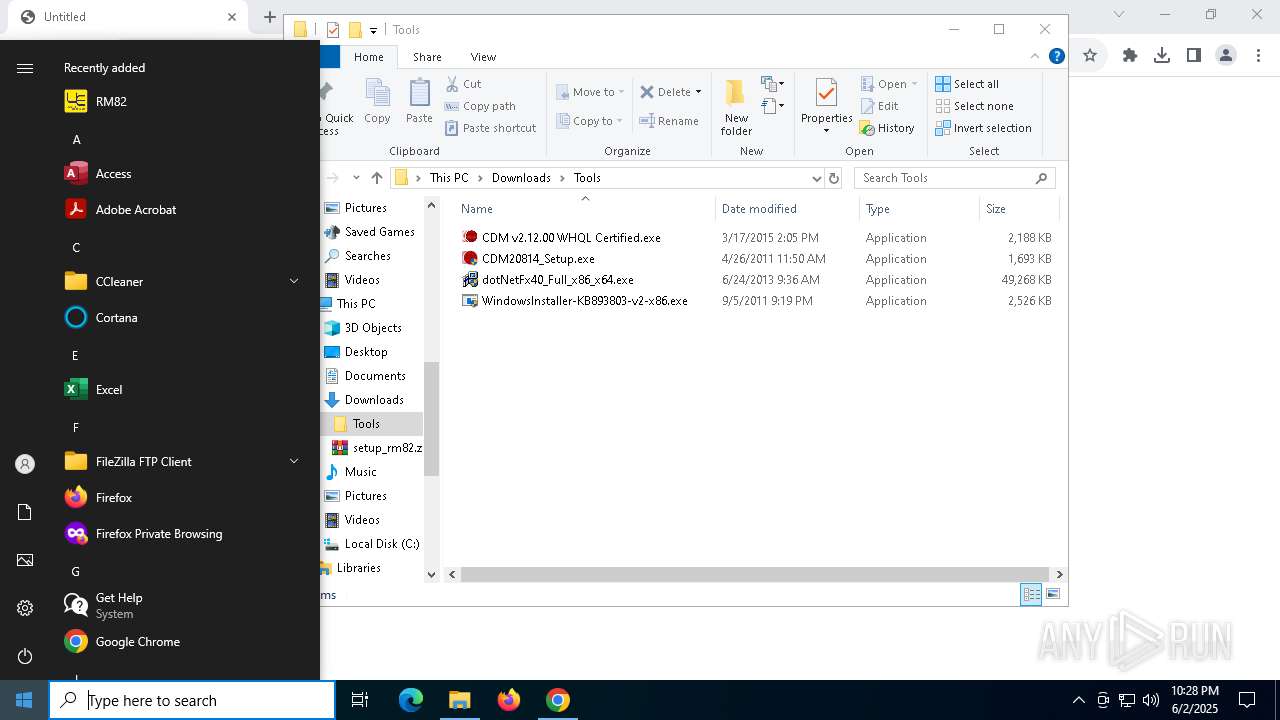
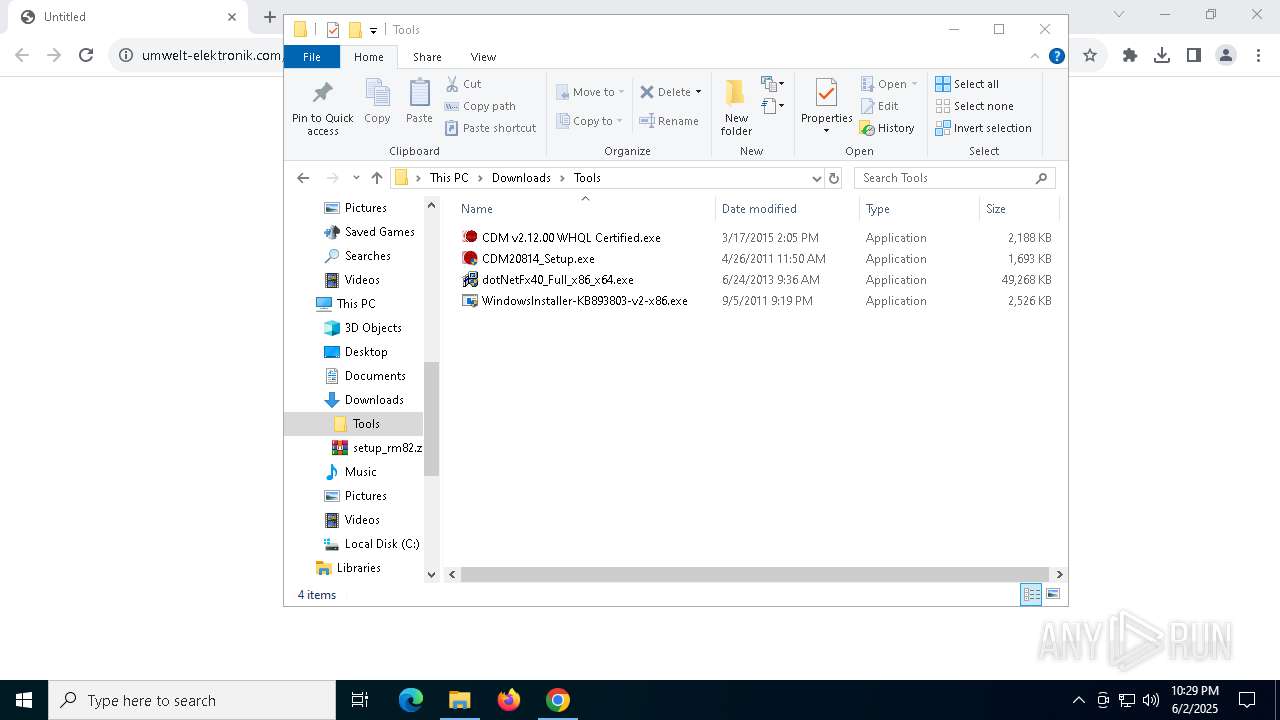
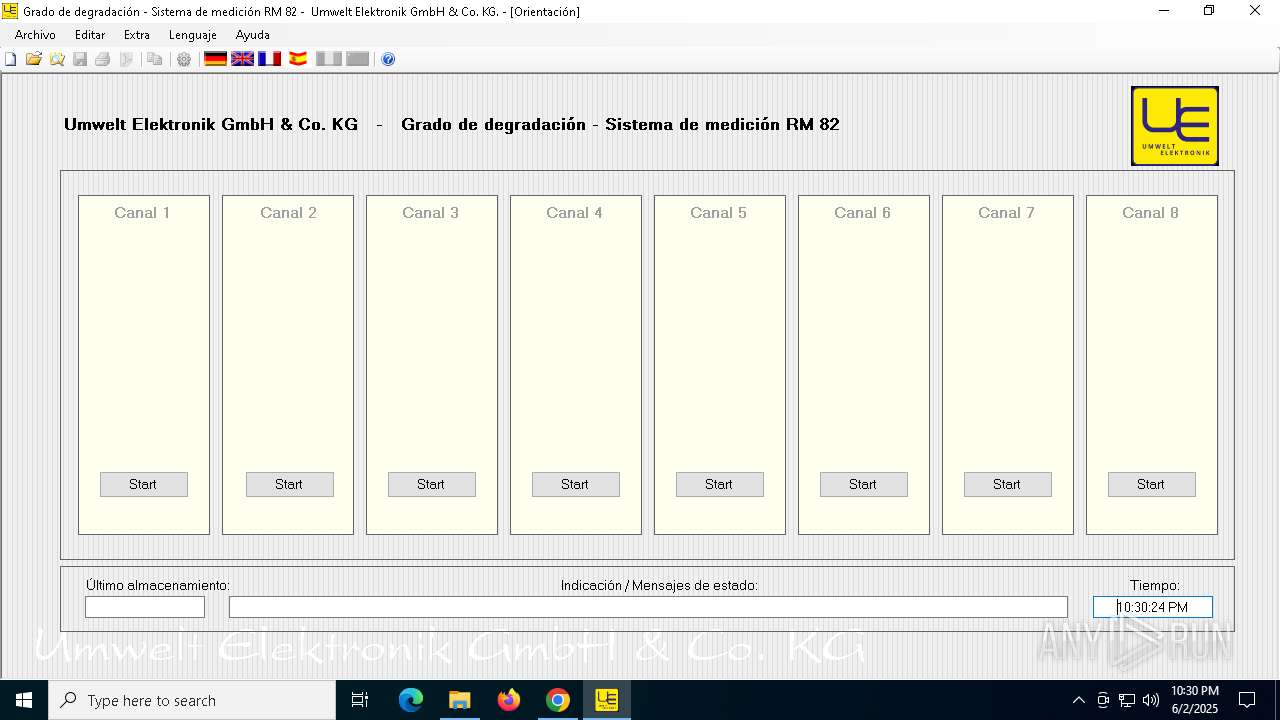
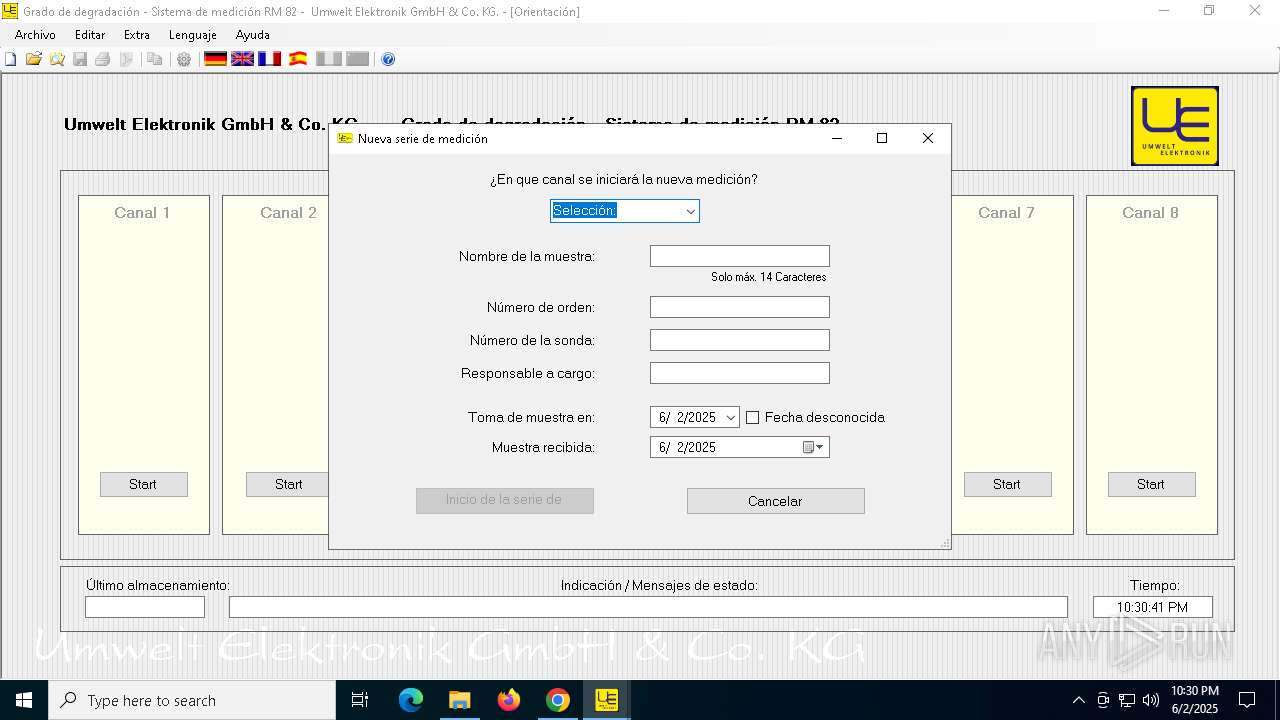
| URL: | https://www.umwelt-elektronik.com/upload/document/setup_rm82.zip |
| Full analysis: | https://app.any.run/tasks/29b2800c-0504-4c55-9775-d10e6eef09ad |
| Verdict: | Malicious activity |
| Analysis date: | June 02, 2025, 22:26:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3D13E307A9C833DD8339197D4155A272 |
| SHA1: | 3F64019C7571EF41EBB7739C638507FFA680D8AC |
| SHA256: | 787018CC71F89D147DBD01EC88567A107CF5526CC9E0C3DAC8C014D8EB1CD85F |
| SSDEEP: | 3:N8DSL6AhRXQzKKrQpRSRQQwX4n:2OL6AhUKiIwaon |
MALICIOUS
Changes the autorun value in the registry
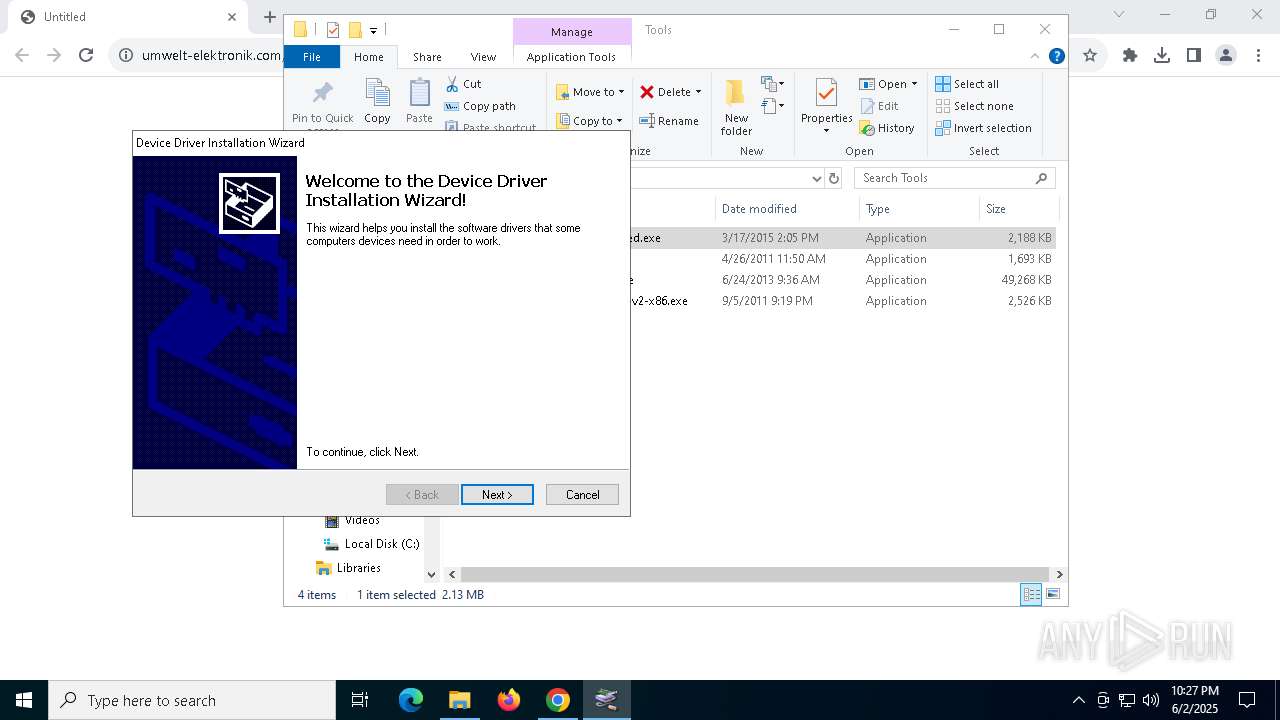
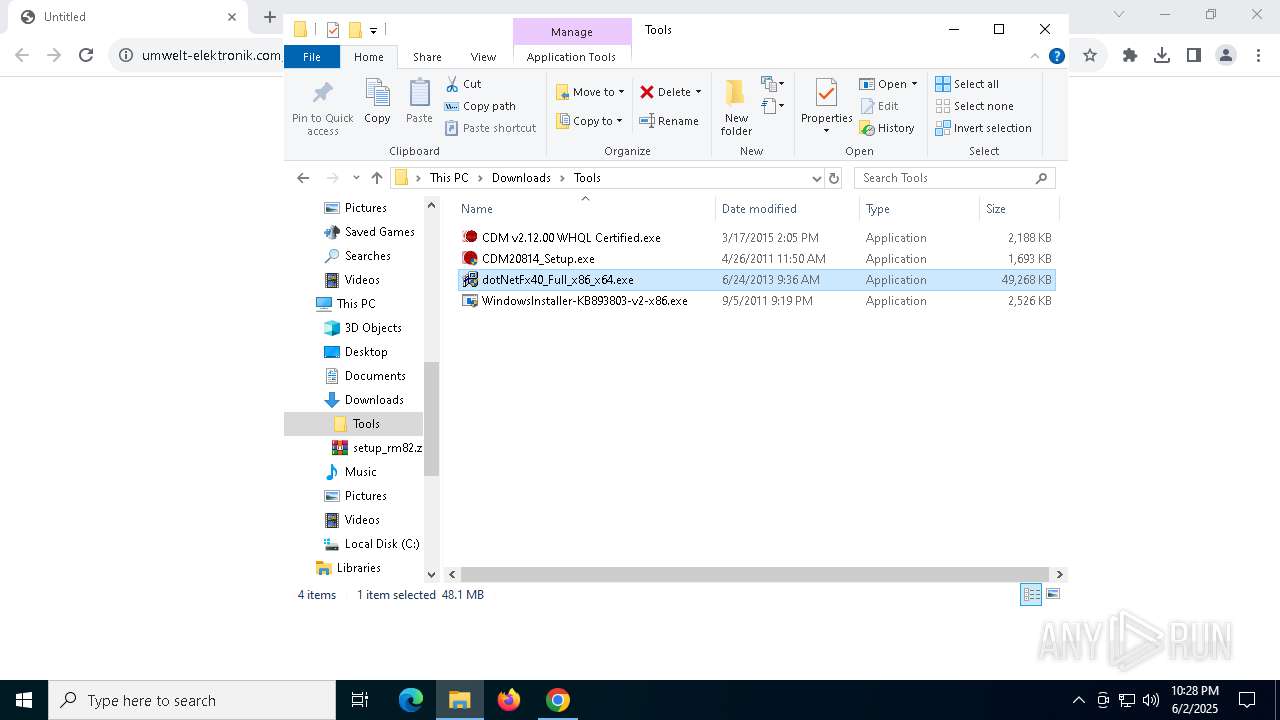
- Setup_RM82.tmp (PID: 4980)
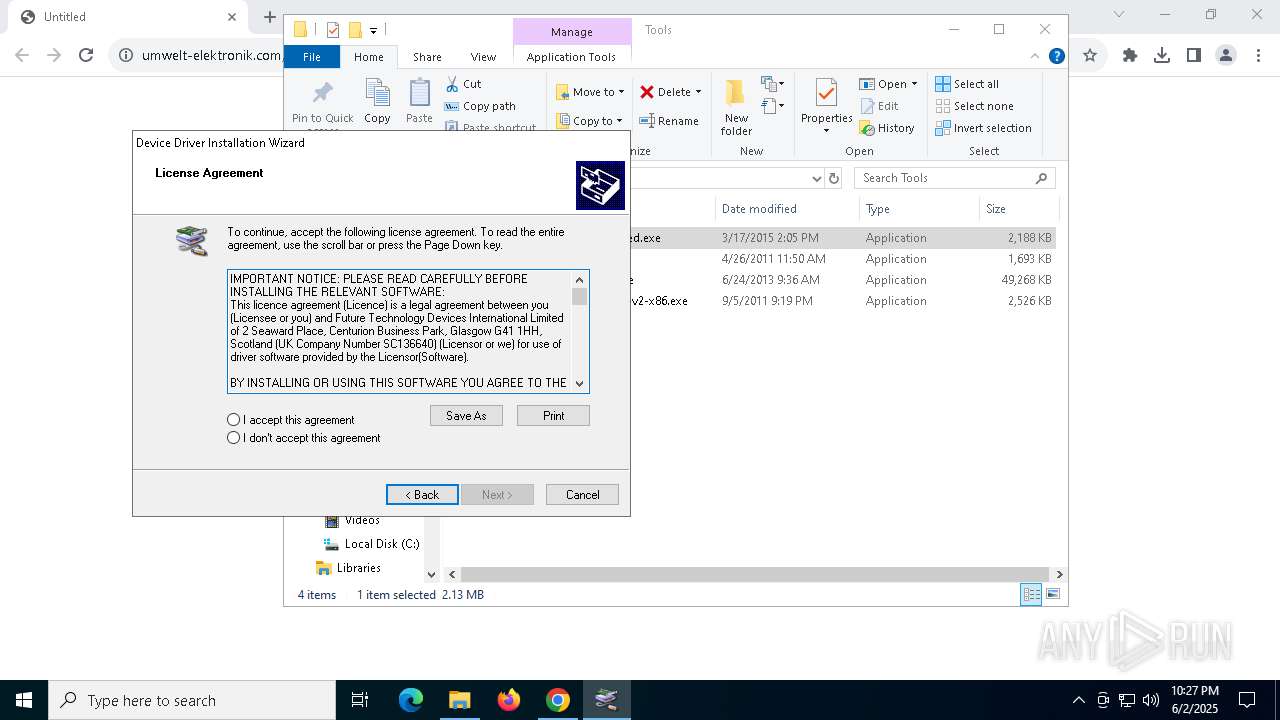
Executing a file with an untrusted certificate
- CDM21224_Setup.exe (PID: 3008)
- dp-chooser.exe (PID: 7252)
- dpinst-amd64.exe (PID: 4844)
- CDM v2.12.00 WHQL Certified.exe (PID: 2148)
- CDM v2.12.00 WHQL Certified.exe (PID: 6512)
- dp-chooser.exe (PID: 4560)
- dpinst-amd64.exe (PID: 3304)
- dp-chooser.exe (PID: 8104)
- dpinst-amd64.exe (PID: 7960)
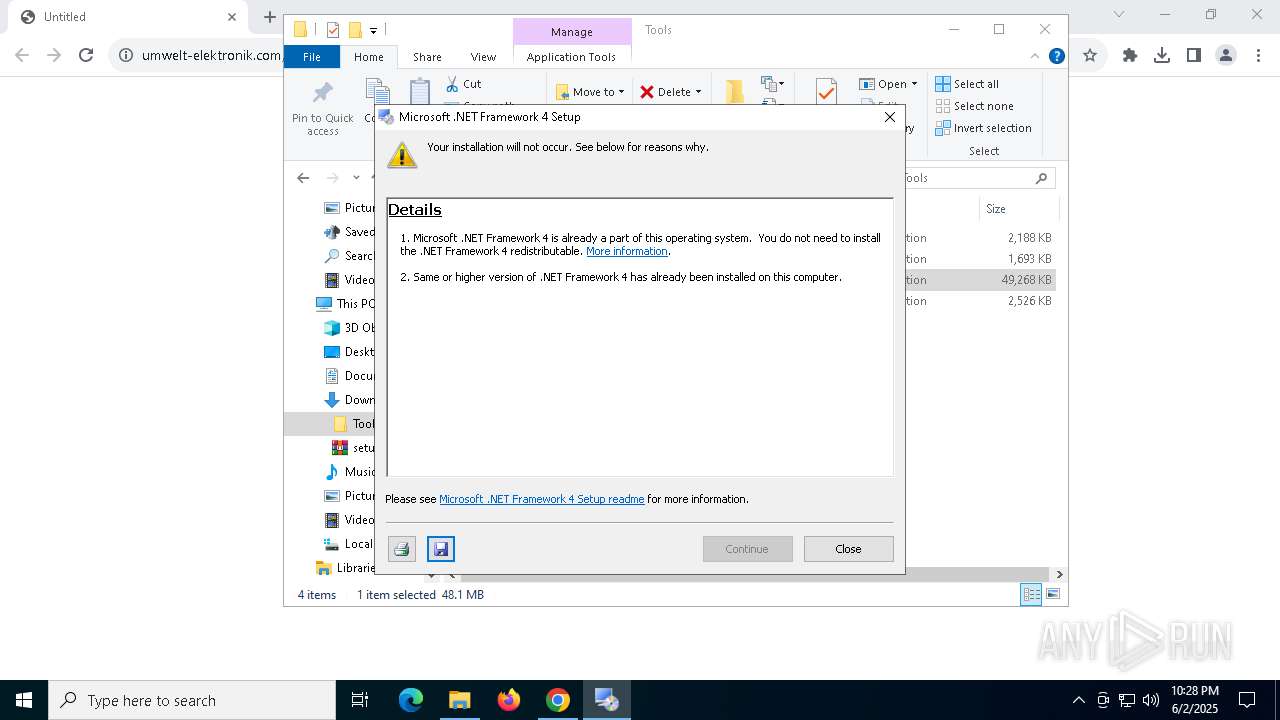
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
- Setup.exe (PID: 7684)
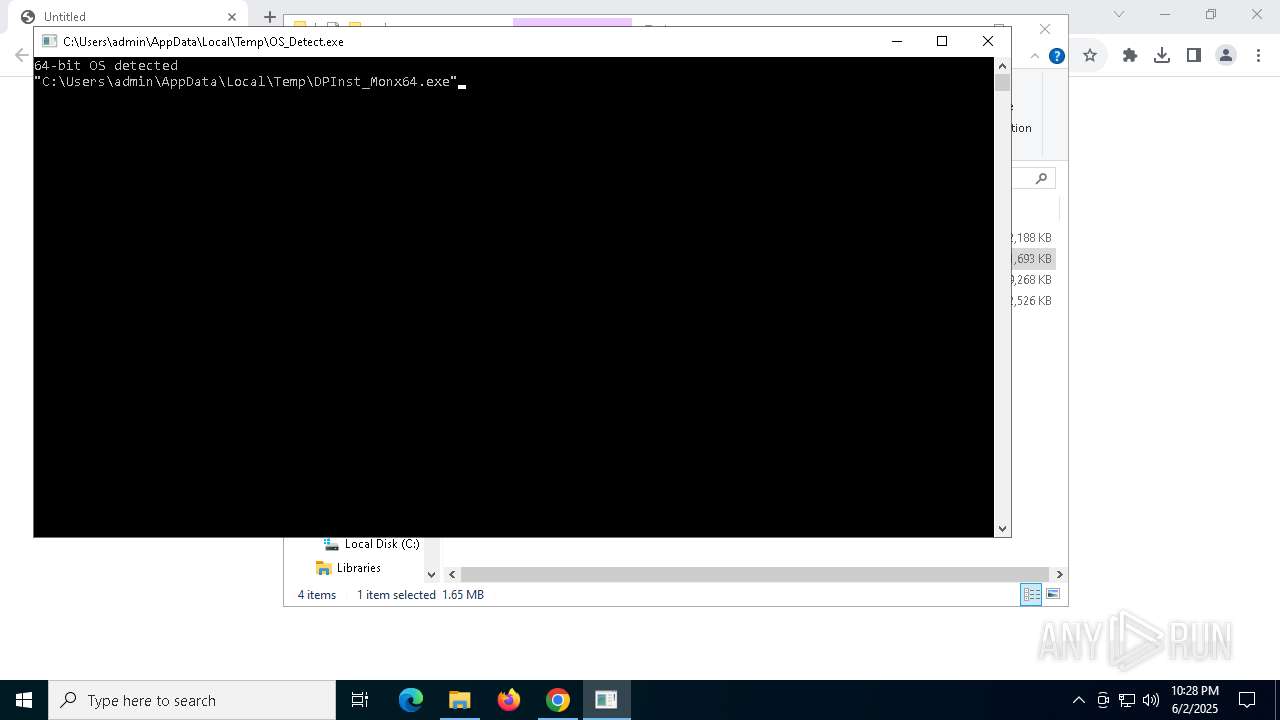
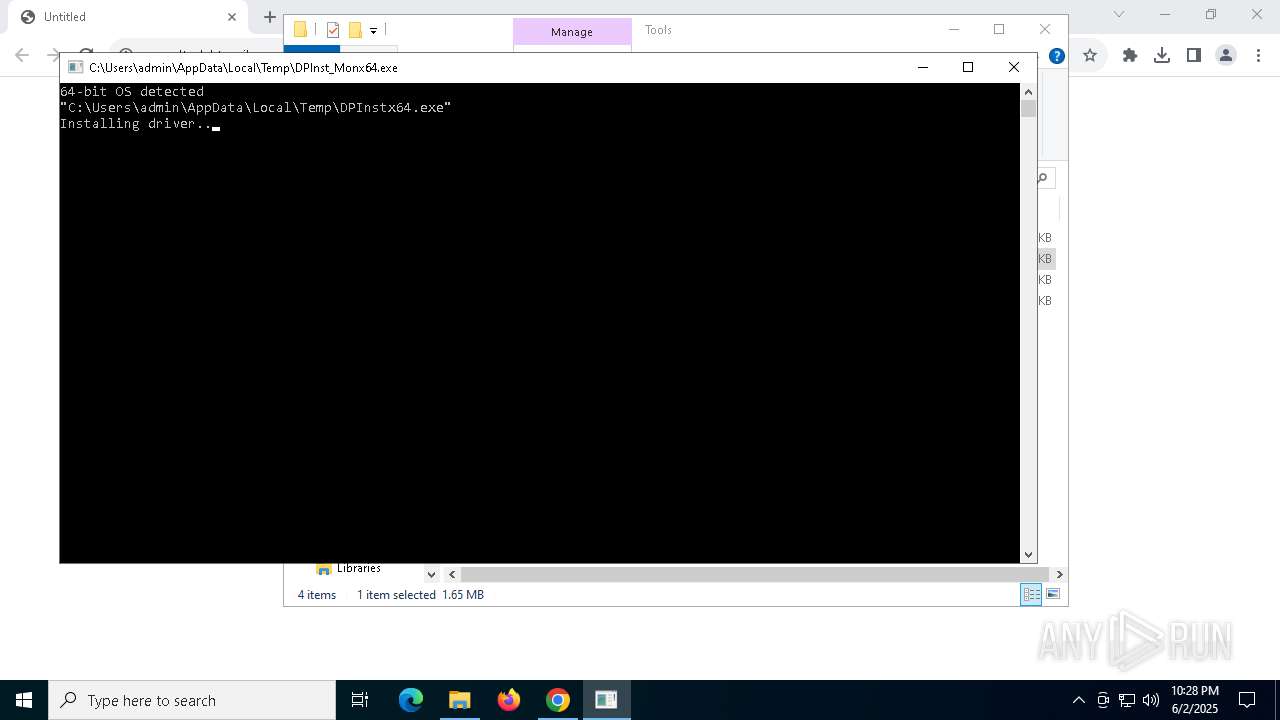
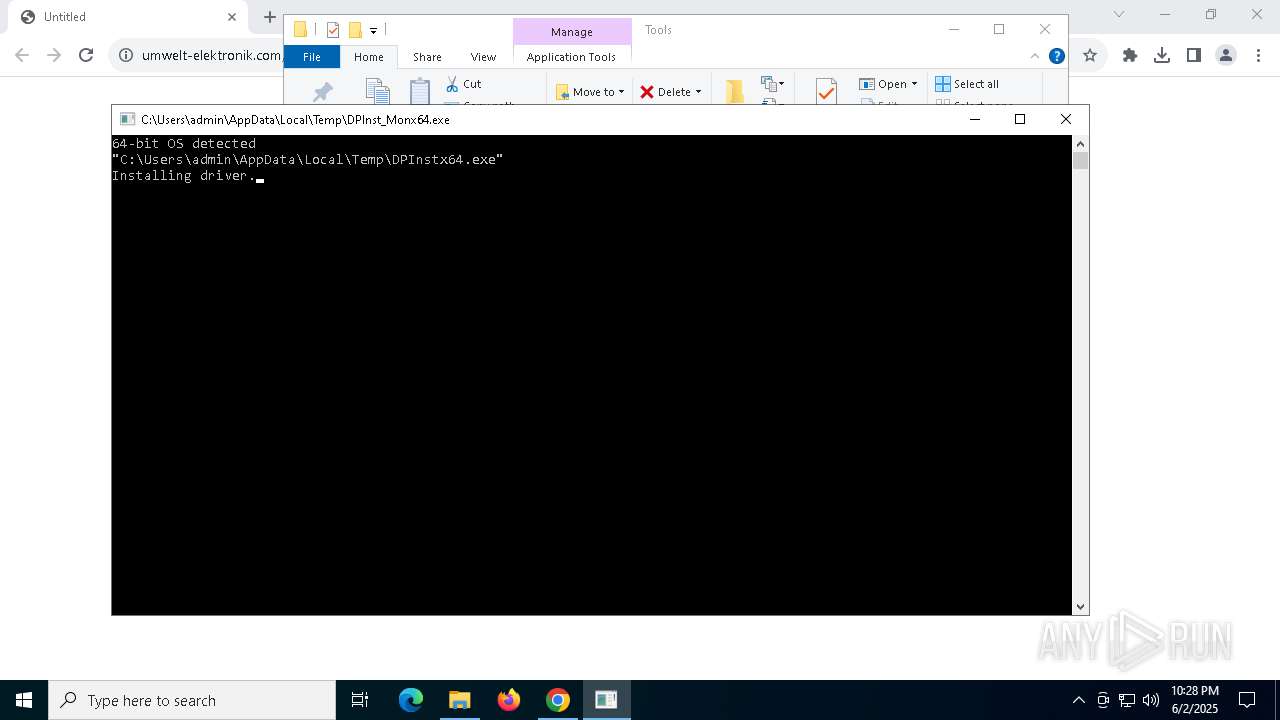
- DPInst_Monx64.exe (PID: 6892)
- OS_Detect.exe (PID: 6808)
- DPInstx64.exe (PID: 3992)
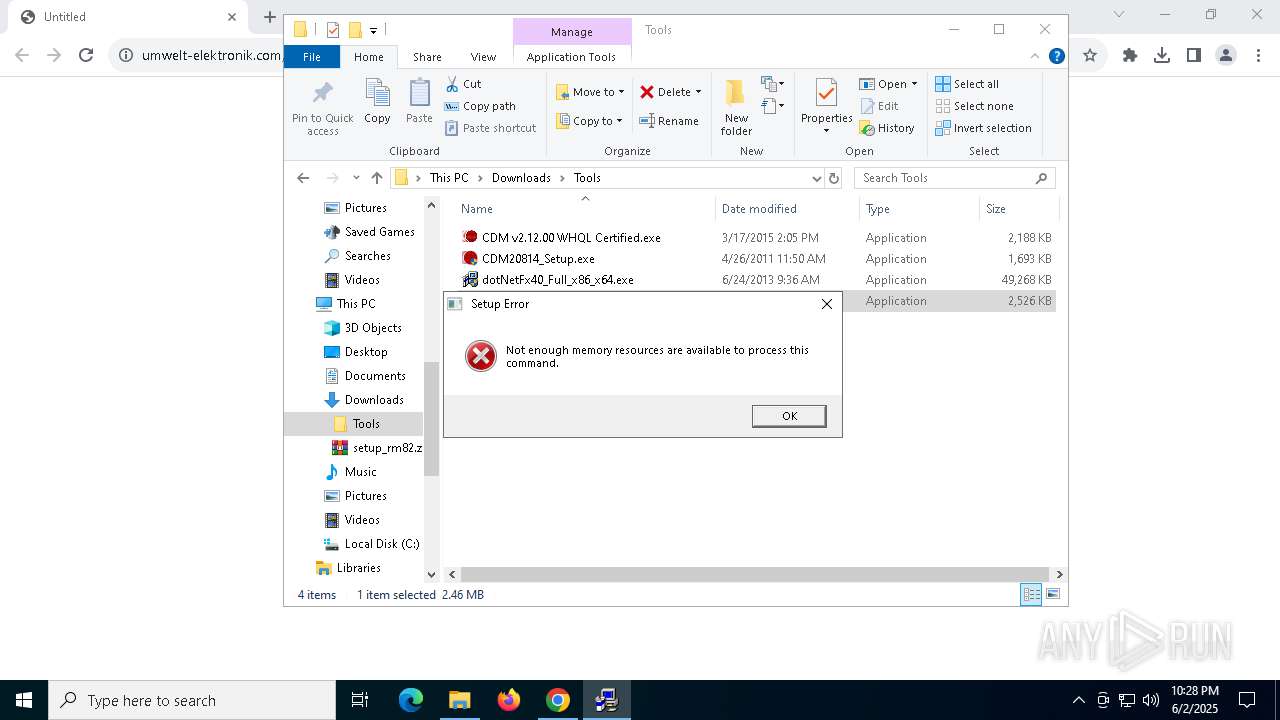
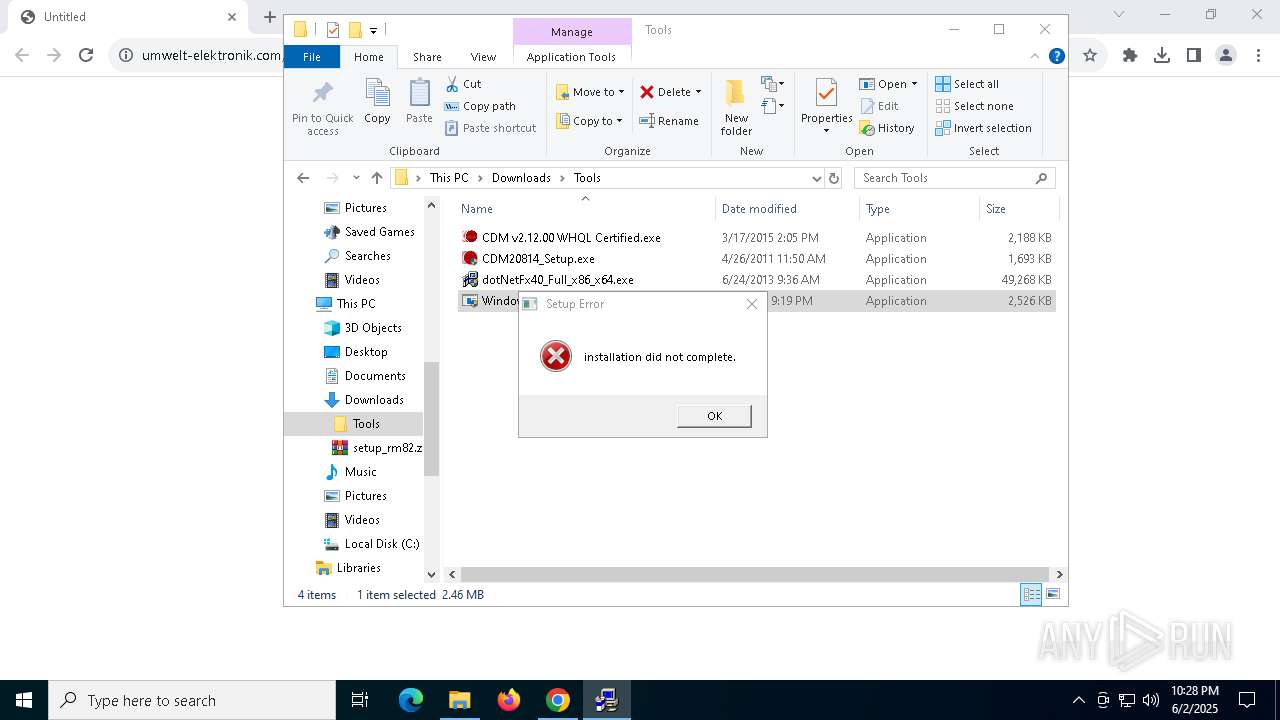
- WindowsInstaller-KB893803-v2-x86.exe (PID: 300)
- update.exe (PID: 5504)
- DPInstx64.exe (PID: 1760)
- OS_Detect.exe (PID: 7996)
- DPInst_Monx64.exe (PID: 3180)
- RM82.exe (PID: 6068)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 6436)
- CDM21224_Setup.exe (PID: 3008)
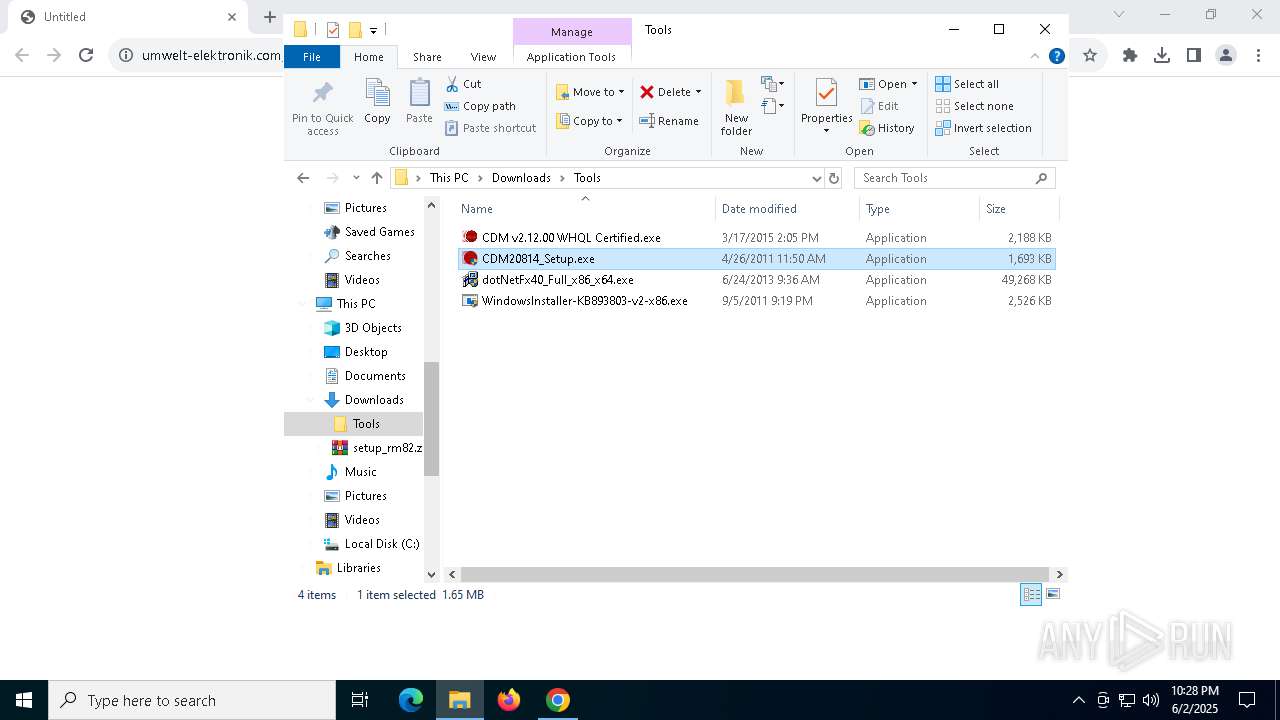
- CDM20814_Setup.exe (PID: 6644)
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 300)
Executable content was dropped or overwritten
- Setup_RM82.exe (PID: 6324)
- Setup_RM82.exe (PID: 7424)
- Setup_RM82.tmp (PID: 4980)
- CDM21224_Setup.exe (PID: 3008)
- dpinst-amd64.exe (PID: 4844)
- drvinst.exe (PID: 968)
- drvinst.exe (PID: 1532)
- drvinst.exe (PID: 6920)
- drvinst.exe (PID: 4380)
- CDM20814_Setup.exe (PID: 6644)
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
- dpinst-amd64.exe (PID: 7960)
- DPInstx64.exe (PID: 3992)
- drvinst.exe (PID: 2780)
- drvinst.exe (PID: 1660)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 300)
Reads security settings of Internet Explorer
- Setup_RM82.tmp (PID: 4244)
Reads the Windows owner or organization settings
- Setup_RM82.tmp (PID: 4980)
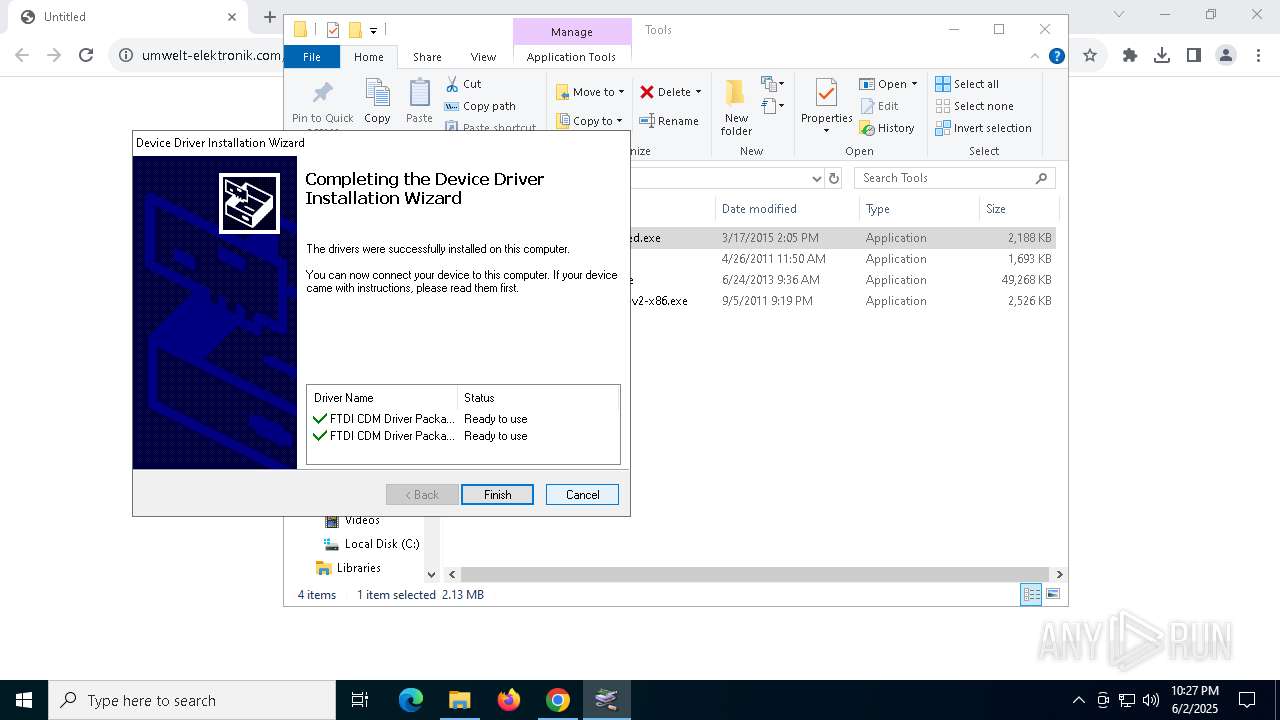
Drops a system driver (possible attempt to evade defenses)
- CDM21224_Setup.exe (PID: 3008)
- dpinst-amd64.exe (PID: 4844)
- drvinst.exe (PID: 968)
- drvinst.exe (PID: 1532)
- drvinst.exe (PID: 4380)
- CDM20814_Setup.exe (PID: 6644)
- dpinst-amd64.exe (PID: 7960)
- drvinst.exe (PID: 6920)
- DPInstx64.exe (PID: 3992)
- drvinst.exe (PID: 1660)
- drvinst.exe (PID: 2780)
Starts a Microsoft application from unusual location
- dpinst-amd64.exe (PID: 4844)
- dpinst-amd64.exe (PID: 3304)
- dpinst-amd64.exe (PID: 7960)
- DPInstx64.exe (PID: 3992)
- DPInstx64.exe (PID: 1760)
There is functionality for taking screenshot (YARA)
- CDM21224_Setup.exe (PID: 3008)
Creates files in the driver directory
- drvinst.exe (PID: 968)
- drvinst.exe (PID: 1532)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6436)
- chrome.exe (PID: 7880)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6632)
Application launched itself
- chrome.exe (PID: 6632)
Checks supported languages
- Setup_RM82.tmp (PID: 4244)
- Setup_RM82.exe (PID: 6324)
- Setup_RM82.exe (PID: 7424)
- Setup_RM82.tmp (PID: 4980)
- CDM21224_Setup.exe (PID: 3008)
- dp-chooser.exe (PID: 7252)
- dpinst-amd64.exe (PID: 4844)
- drvinst.exe (PID: 968)
- drvinst.exe (PID: 1532)
Manual execution by a user
- WinRAR.exe (PID: 6436)
- Setup_RM82.exe (PID: 6324)
- CDM v2.12.00 WHQL Certified.exe (PID: 6512)
- CDM v2.12.00 WHQL Certified.exe (PID: 2148)
- CDM20814_Setup.exe (PID: 6644)
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
- CDM20814_Setup.exe (PID: 8172)
- RM82.exe (PID: 6068)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 300)
- CDM20814_Setup.exe (PID: 7952)
Create files in a temporary directory
- Setup_RM82.exe (PID: 6324)
- Setup_RM82.exe (PID: 7424)
- Setup_RM82.tmp (PID: 4980)
- CDM21224_Setup.exe (PID: 3008)
- dpinst-amd64.exe (PID: 4844)
Process checks computer location settings
- Setup_RM82.tmp (PID: 4244)
Reads the computer name
- Setup_RM82.tmp (PID: 4244)
- Setup_RM82.tmp (PID: 4980)
- CDM21224_Setup.exe (PID: 3008)
- dpinst-amd64.exe (PID: 4844)
- drvinst.exe (PID: 968)
Detects InnoSetup installer (YARA)
- Setup_RM82.exe (PID: 6324)
- Setup_RM82.tmp (PID: 4244)
- Setup_RM82.tmp (PID: 4980)
- Setup_RM82.exe (PID: 7424)
The sample compiled with german language support
- Setup_RM82.tmp (PID: 4980)
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
Compiled with Borland Delphi (YARA)
- Setup_RM82.tmp (PID: 4244)
- Setup_RM82.tmp (PID: 4980)
Launch of the file from Registry key
- Setup_RM82.tmp (PID: 4980)
The sample compiled with arabic language support
- CDM21224_Setup.exe (PID: 3008)
- CDM20814_Setup.exe (PID: 6644)
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
The sample compiled with english language support
- CDM21224_Setup.exe (PID: 3008)
- dpinst-amd64.exe (PID: 4844)
- drvinst.exe (PID: 968)
- drvinst.exe (PID: 1532)
- drvinst.exe (PID: 6920)
- dpinst-amd64.exe (PID: 7960)
- drvinst.exe (PID: 4380)
- chrome.exe (PID: 7880)
- CDM20814_Setup.exe (PID: 6644)
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
- drvinst.exe (PID: 2780)
- DPInstx64.exe (PID: 3992)
- drvinst.exe (PID: 1660)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 300)
Creates files in the program directory
- Setup_RM82.tmp (PID: 4980)
Creates a software uninstall entry
- Setup_RM82.tmp (PID: 4980)
Reads the software policy settings
- drvinst.exe (PID: 968)
Reads the machine GUID from the registry
- drvinst.exe (PID: 968)
The sample compiled with czech language support
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
The sample compiled with french language support
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
The sample compiled with chinese language support
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
The sample compiled with swedish language support
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
The sample compiled with korean language support
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
The sample compiled with japanese language support
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
The sample compiled with Italian language support
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
The sample compiled with turkish language support
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
The sample compiled with portuguese language support
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
The sample compiled with polish language support
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
The sample compiled with spanish language support
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
The sample compiled with russian language support
- dotNetFx40_Full_x86_x64.exe (PID: 1276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
205
Monitored processes
63
Malicious processes
18
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3576 --field-trial-handle=1912,i,6642437258406540923,7783207350508677825,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
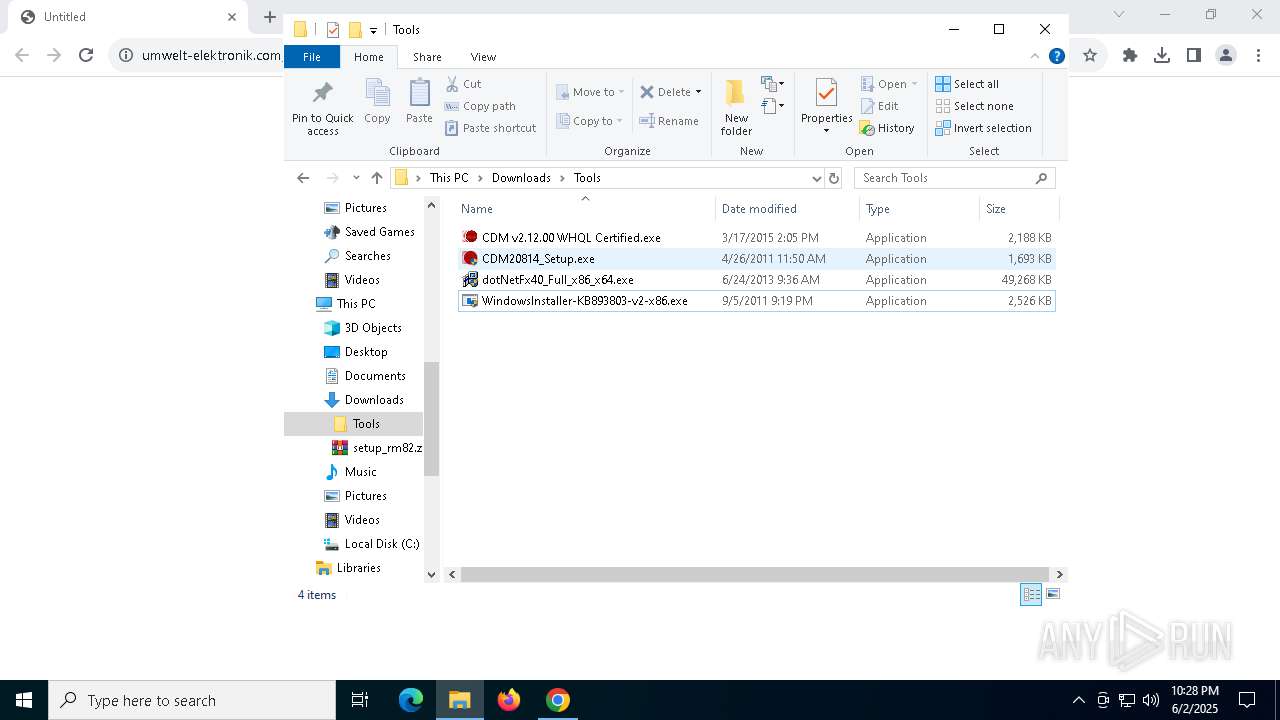
| 300 | "C:\Users\admin\Downloads\Tools\WindowsInstaller-KB893803-v2-x86.exe" | C:\Users\admin\Downloads\Tools\WindowsInstaller-KB893803-v2-x86.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Update Package Exit code: 1603 Version: 3.1 Modules
| |||||||||||||||
| 660 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3464 --field-trial-handle=1912,i,6642437258406540923,7783207350508677825,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=3536 --field-trial-handle=1912,i,6642437258406540923,7783207350508677825,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 968 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{678744bb-ac1d-4d42-82e9-2246d3e25a87}\ftdibus.inf" "9" "4a9ba6403" "00000000000001CC" "WinSta0\Default" "00000000000001EC" "208" "c:\users\admin\appdata\local\temp\ftdi-driver" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x224,0x228,0x22c,0x1fc,0x230,0x7ffc8853dc40,0x7ffc8853dc4c,0x7ffc8853dc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
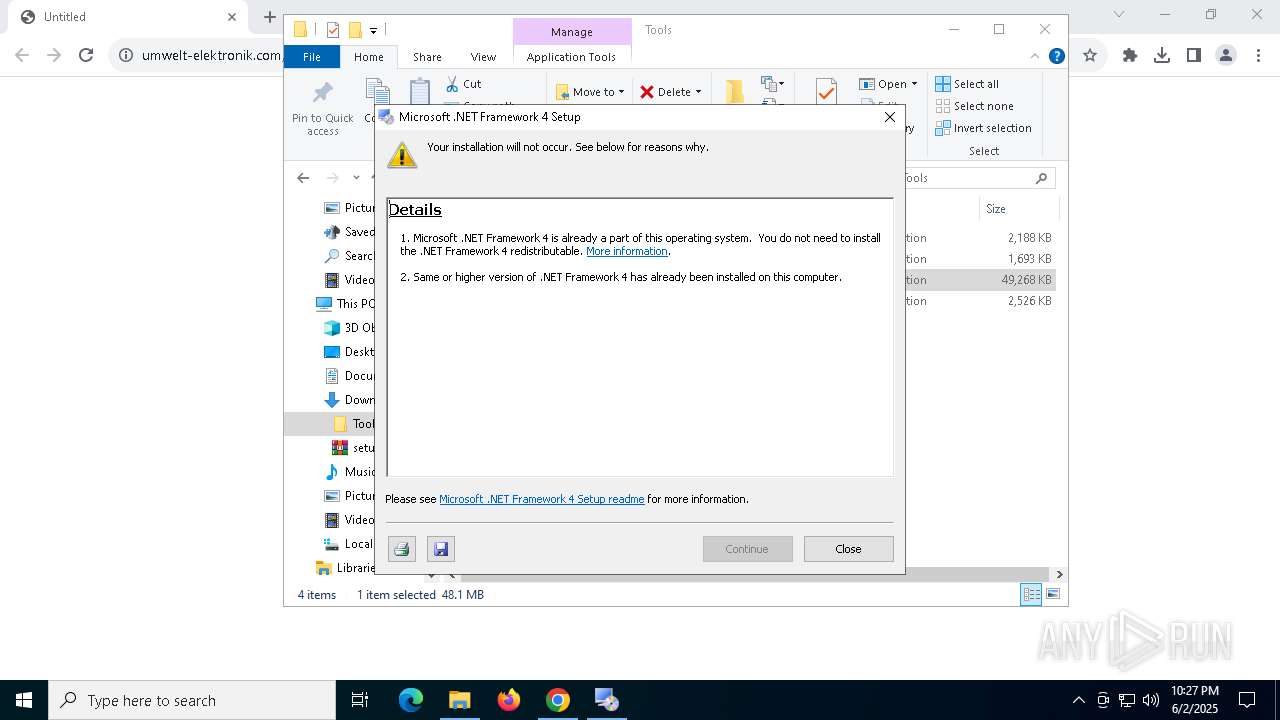
| 1276 | "C:\Users\admin\Downloads\Tools\dotNetFx40_Full_x86_x64.exe" | C:\Users\admin\Downloads\Tools\dotNetFx40_Full_x86_x64.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4 Setup Exit code: 0 Version: 4.0.30319.01 Modules
| |||||||||||||||
| 1324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2196 --field-trial-handle=1912,i,6642437258406540923,7783207350508677825,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1532 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{fd6df876-de8d-464d-a8d3-3177f6f4eb8a}\ftdiport.inf" "9" "461a5a59f" "0000000000000204" "WinSta0\Default" "0000000000000208" "208" "c:\users\admin\appdata\local\temp\ftdi-driver" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{54168286-3f4d-3d42-a6da-84c92f17d8a4}\ftdiport.inf" "9" "4a019ce6f" "0000000000000218" "WinSta0\Default" "000000000000021C" "208" "c:\users\admin\appdata\local\temp" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
36 072
Read events
35 946
Write events
116
Delete events
10
Modification events
| (PID) Process: | (6632) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6632) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6632) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6632) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6632) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (7632) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000A0E9ED5D0DD4DB01 | |||
| (PID) Process: | (6632) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
215
Suspicious files
231
Text files
163
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6632 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF12045d.TMP | — | |
MD5:— | SHA256:— | |||
| 6632 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6632 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF12046d.TMP | — | |
MD5:— | SHA256:— | |||
| 6632 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6632 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF12047c.TMP | — | |
MD5:— | SHA256:— | |||
| 6632 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6632 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF12047c.TMP | — | |
MD5:— | SHA256:— | |||
| 6632 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF12047c.TMP | — | |
MD5:— | SHA256:— | |||
| 6632 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6632 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
44
DNS requests
42
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6668 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7232 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7232 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7700 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
7700 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7700 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
7700 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/mfnf4w4aaa2rporuqgtjqv35v4_4.10.2891.0/oimompecagnajdejgnnjijobebaeigek_4.10.2891.0_win64_acwxtxt2znguar3w2o252umtomsq.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7768 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6668 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7388 | chrome.exe | 64.233.167.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6632 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.umwelt-elektronik.com |
| unknown |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |