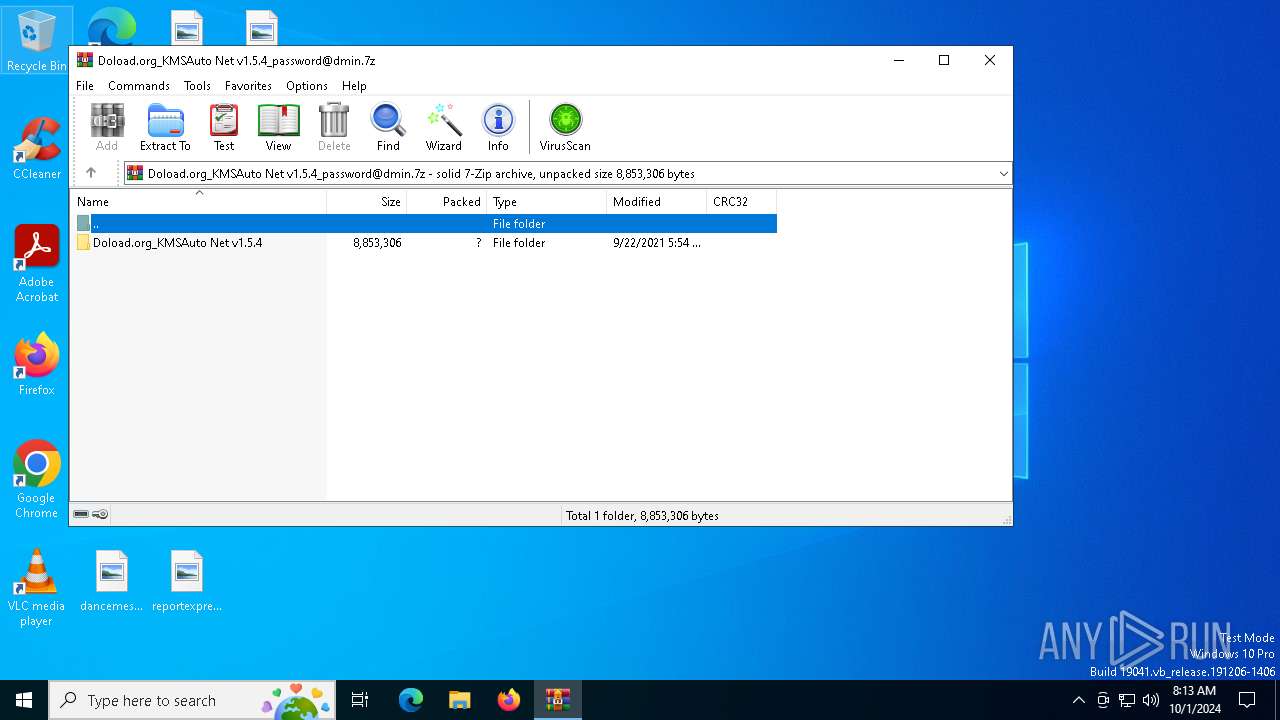
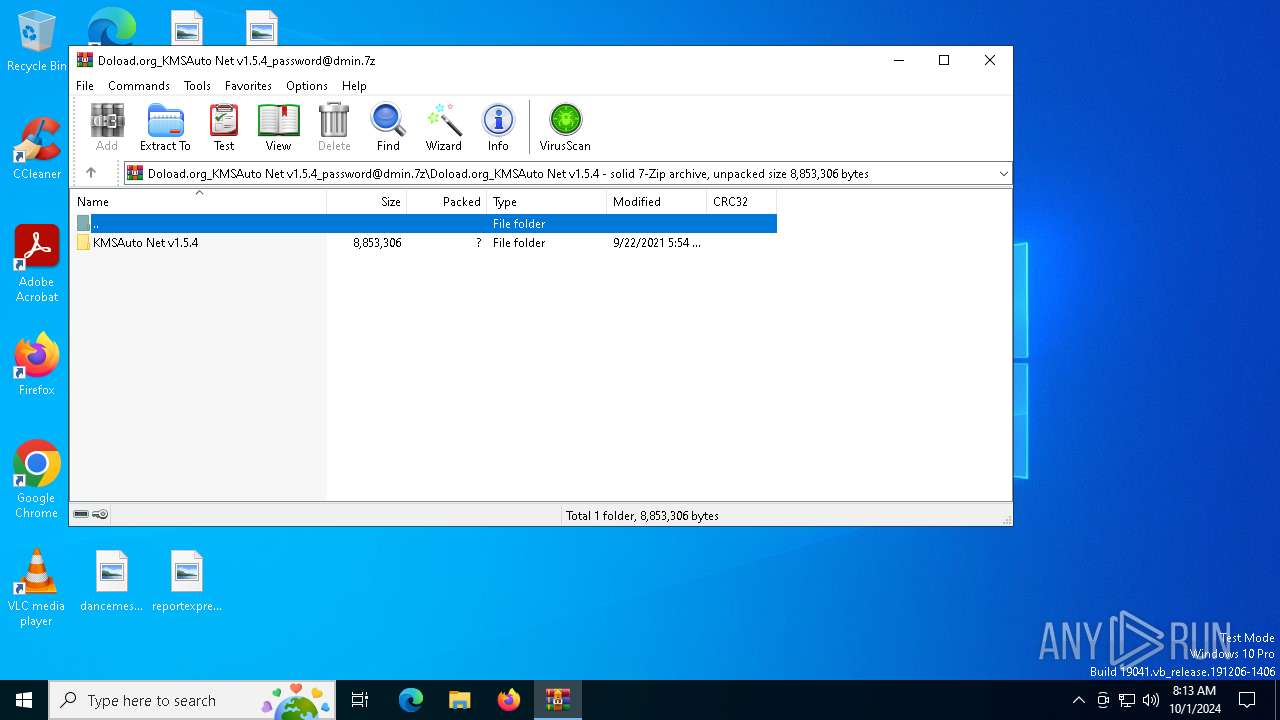
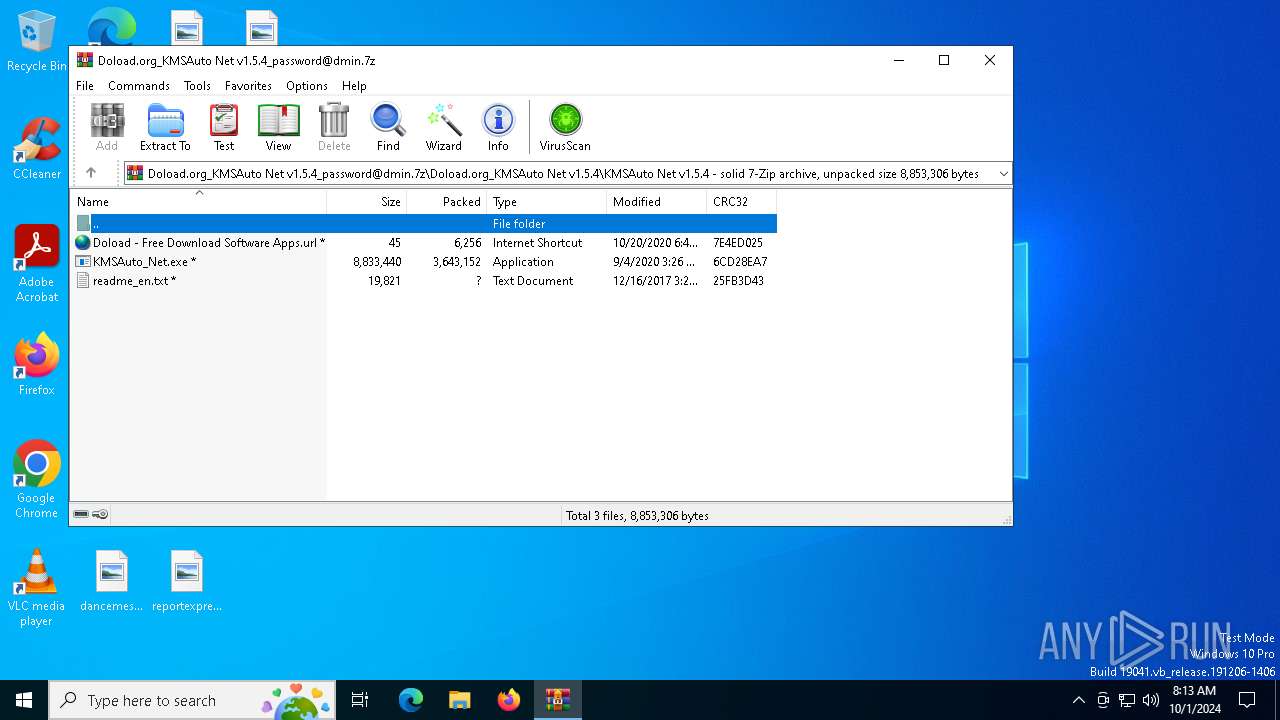
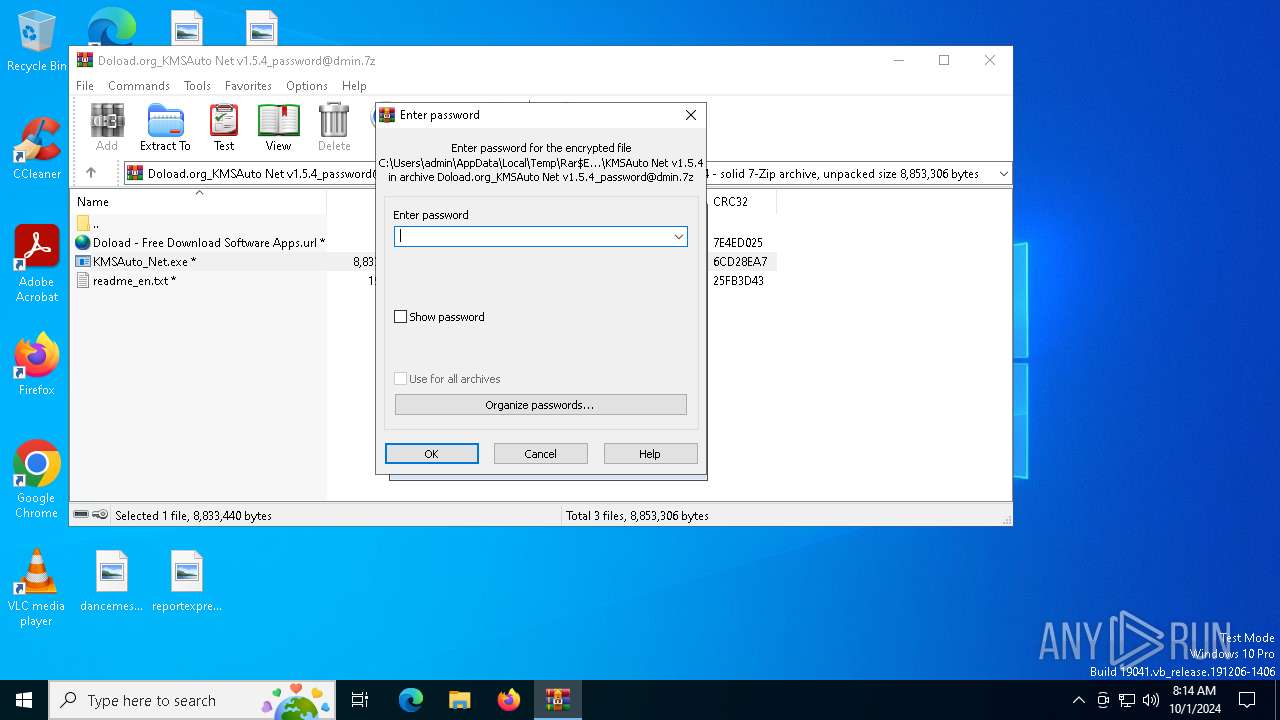
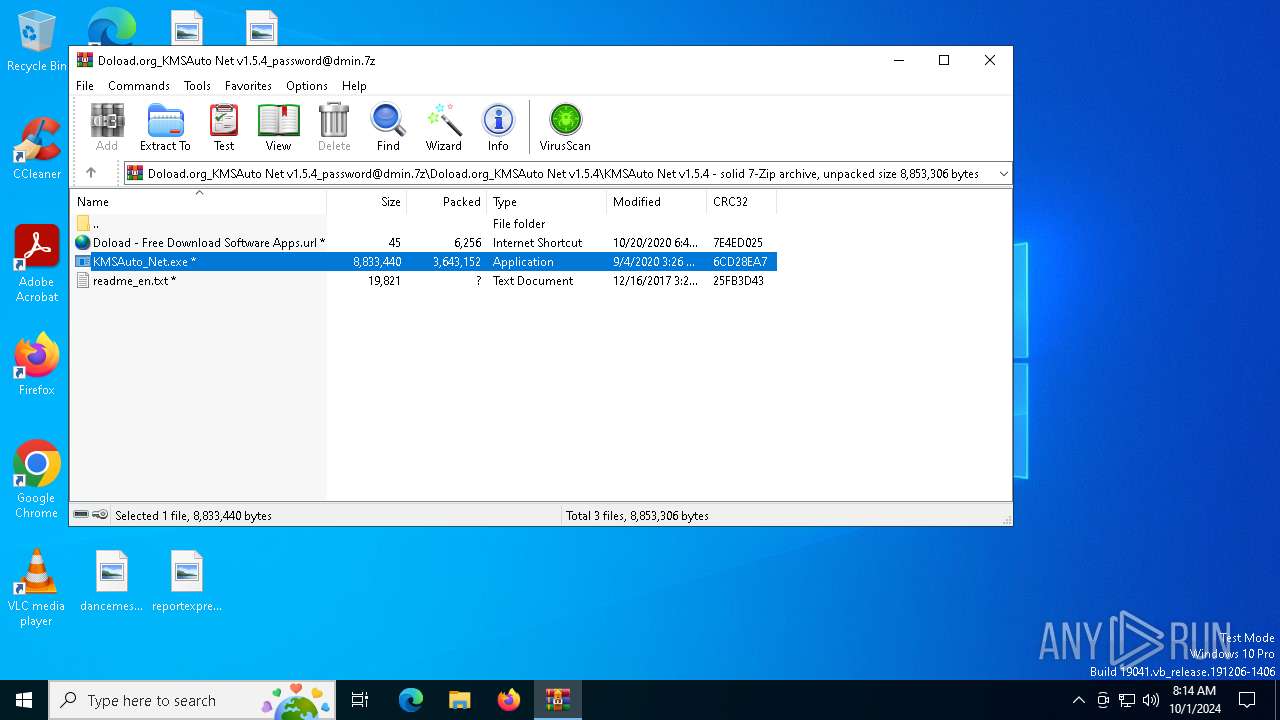
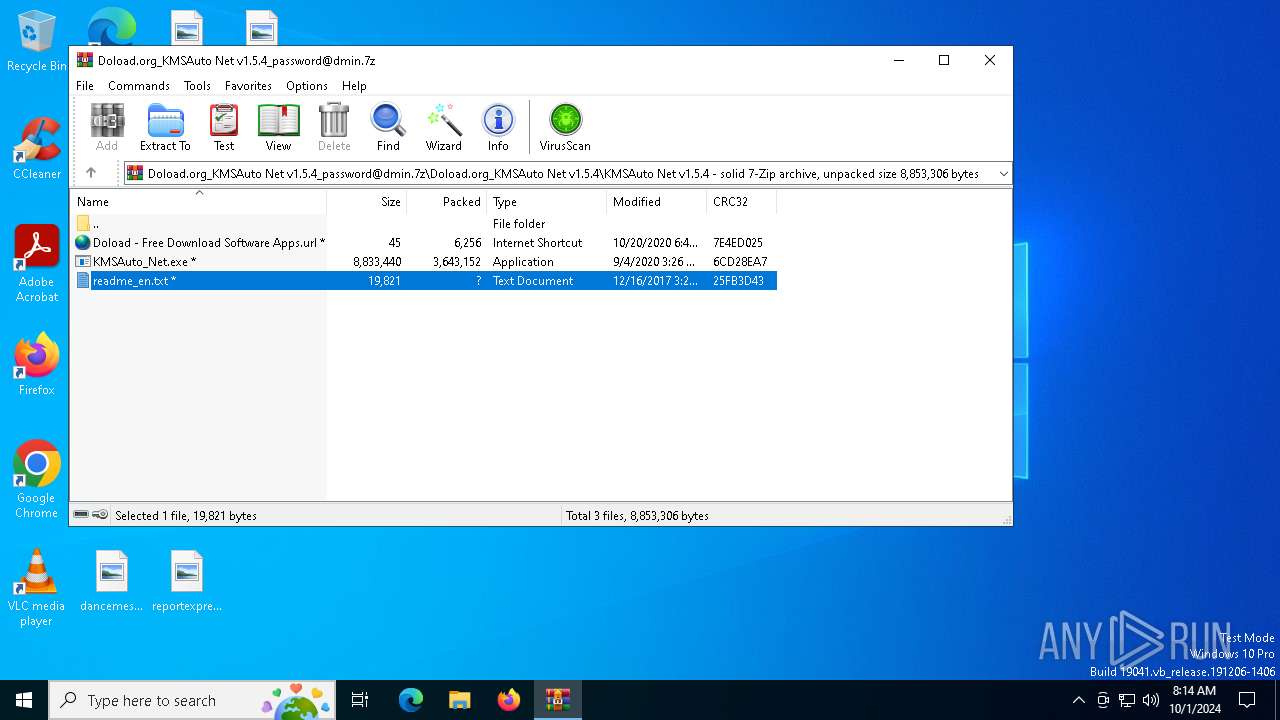
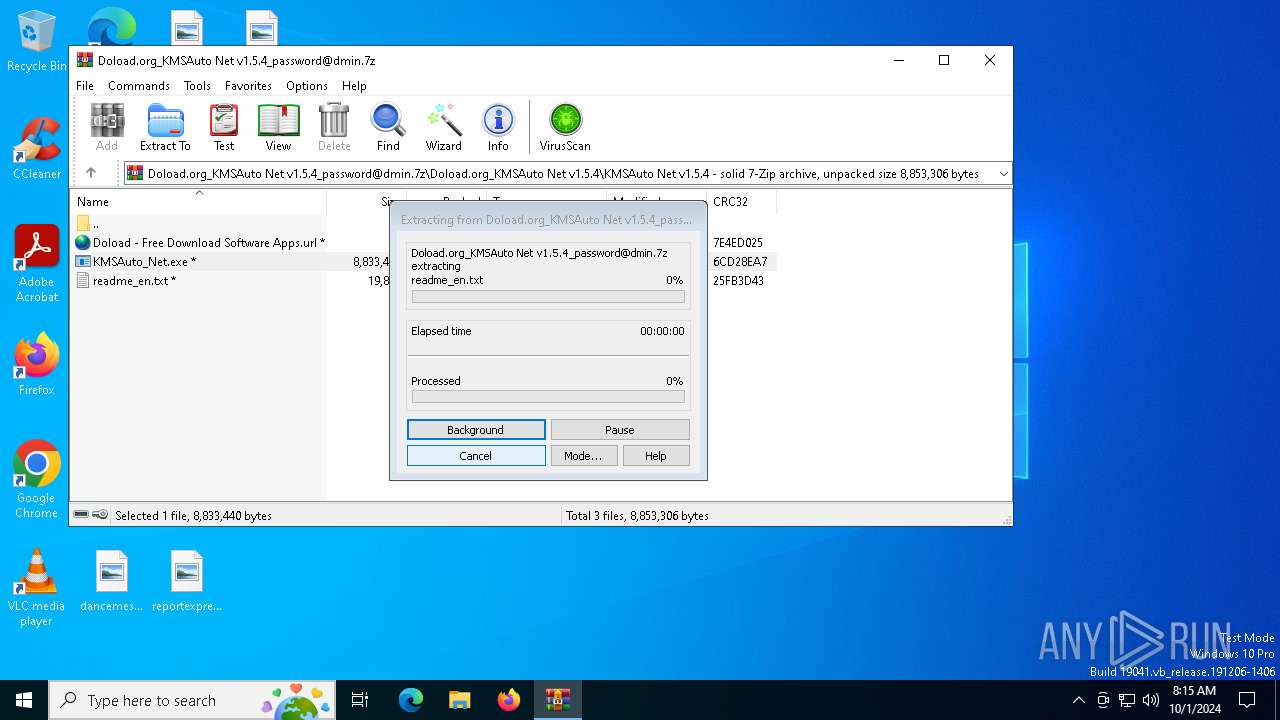
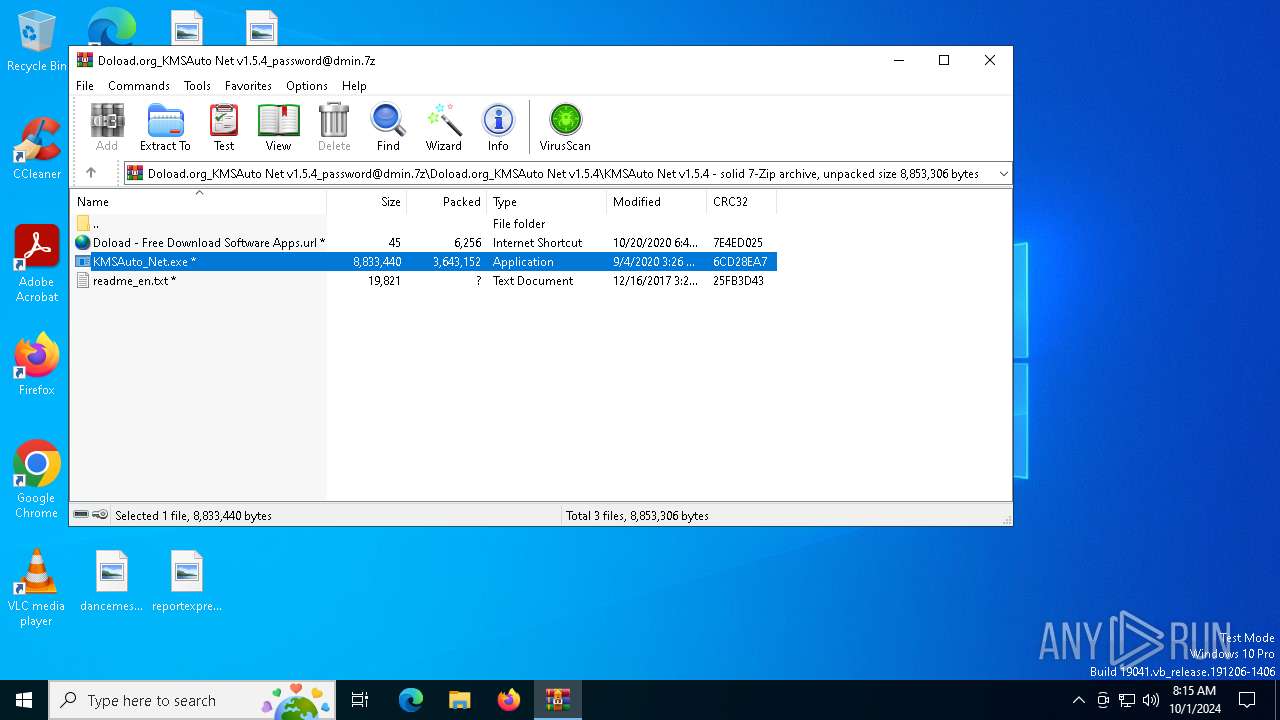
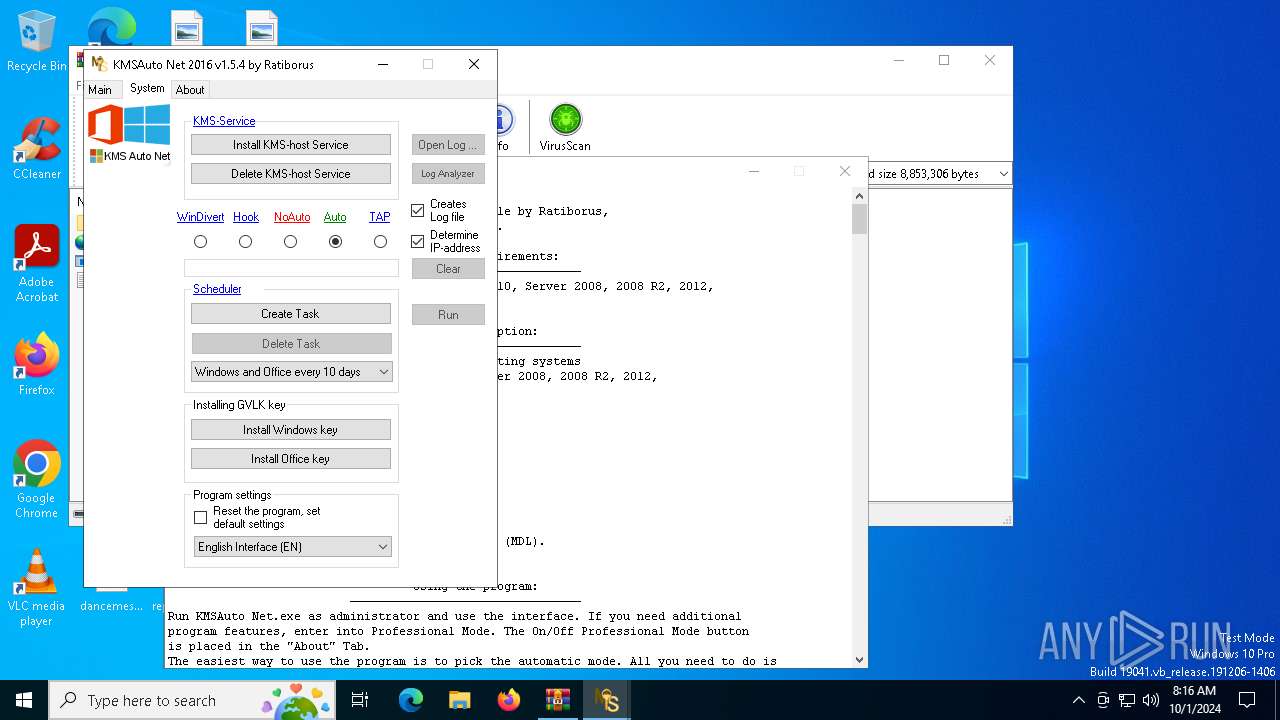
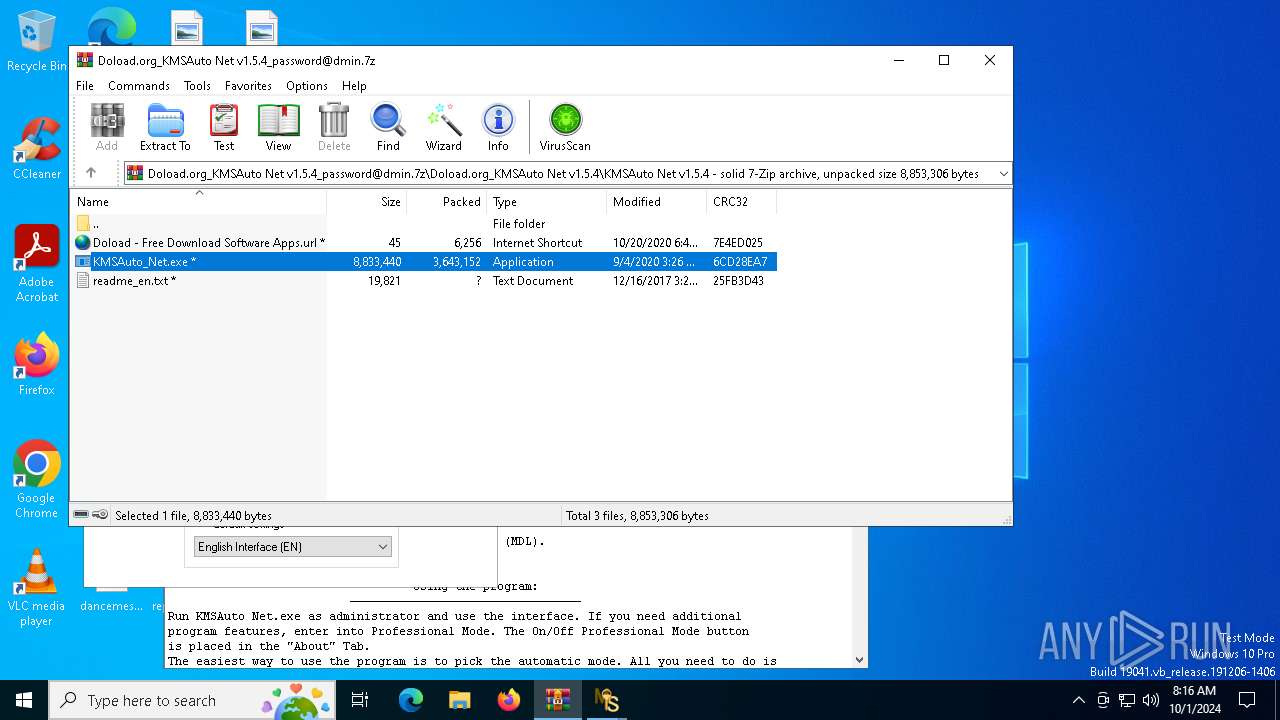
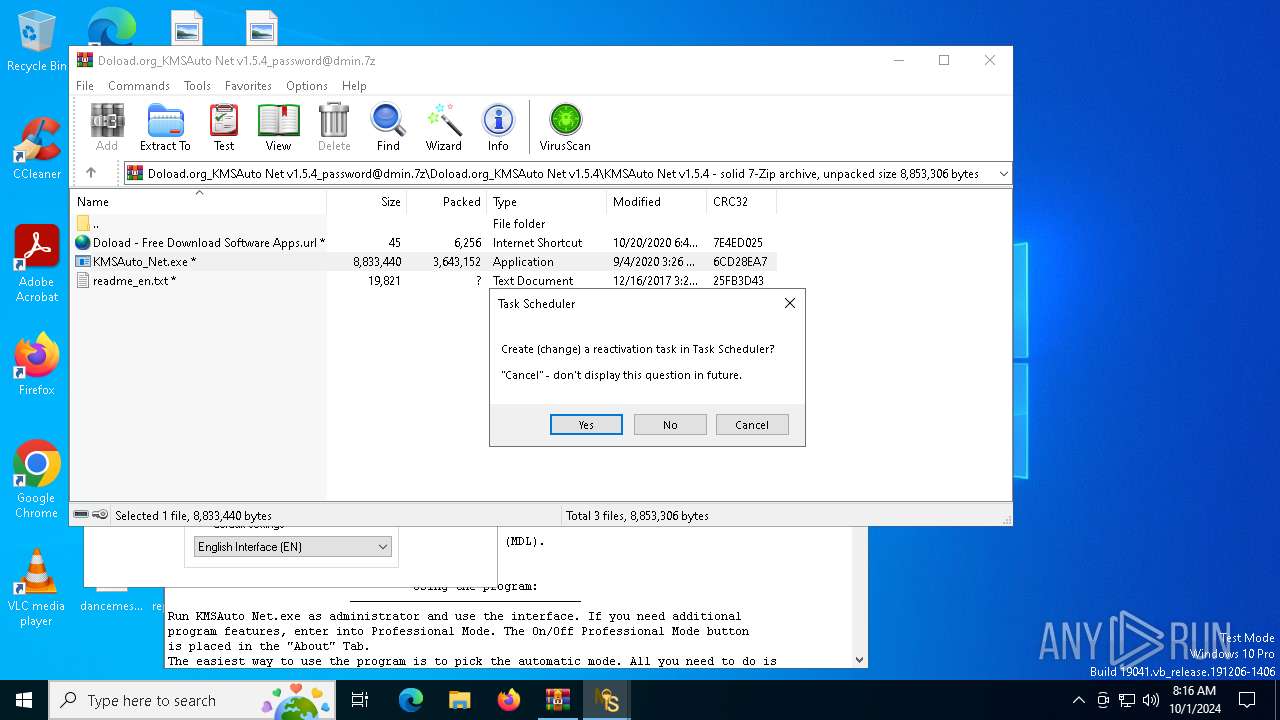
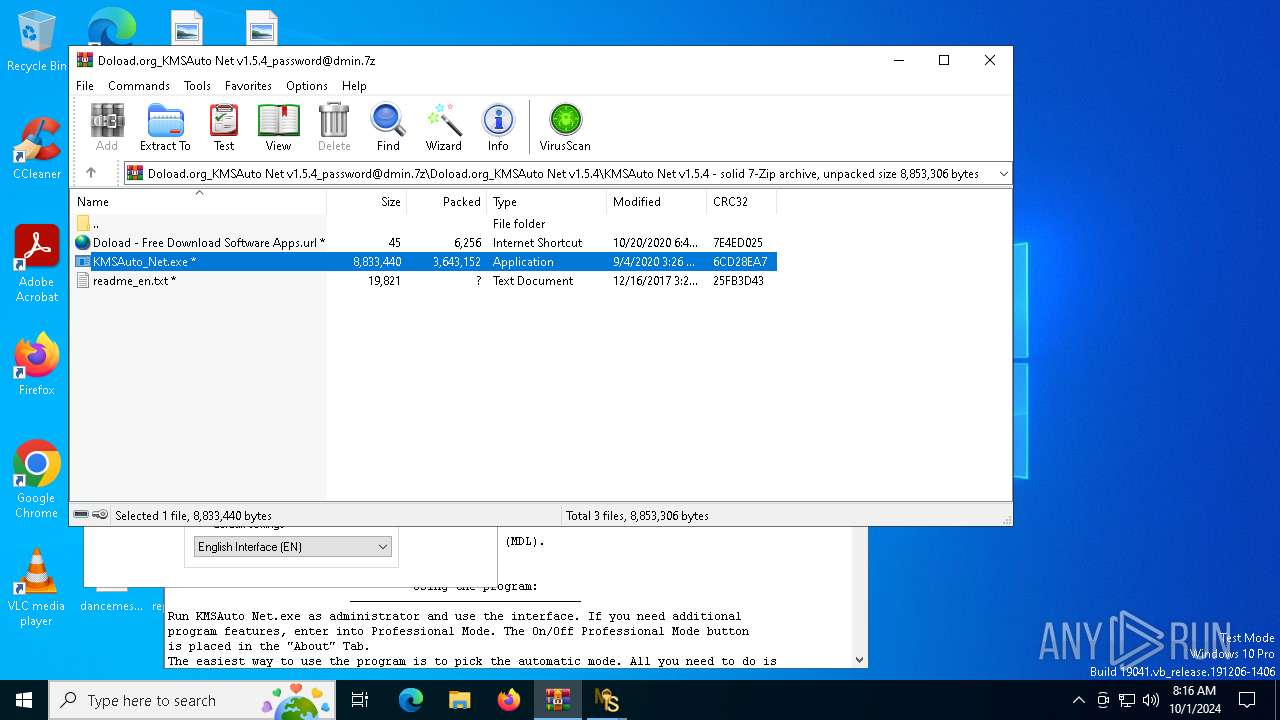
| File name: | Doload.org_KMSAuto Net v1.5.4_password@dmin.7z |
| Full analysis: | https://app.any.run/tasks/1a9a21c5-4dc5-411d-b4ef-e5fd3d372e9e |
| Verdict: | Malicious activity |
| Analysis date: | October 01, 2024, 08:13:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 9B918593836FE81D4181E369C012BB4C |
| SHA1: | B1592818C26A7BFA2A5DD187771A0F46FDA7C809 |
| SHA256: | 786B8AE977C529A527983DC21F3B93CDD188AA20EA8C6E0D7BDC26B35A3AA8F8 |
| SSDEEP: | 98304:TGQ0GOuXYJ4pIMxjOeDB4IiB6qt4KMz5szJ2XCSHkOJnpnJWof/S7YkFXZt/Se9S:mq6mKTykxbtHy |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6696)
SUSPICIOUS
Reads security settings of Internet Explorer
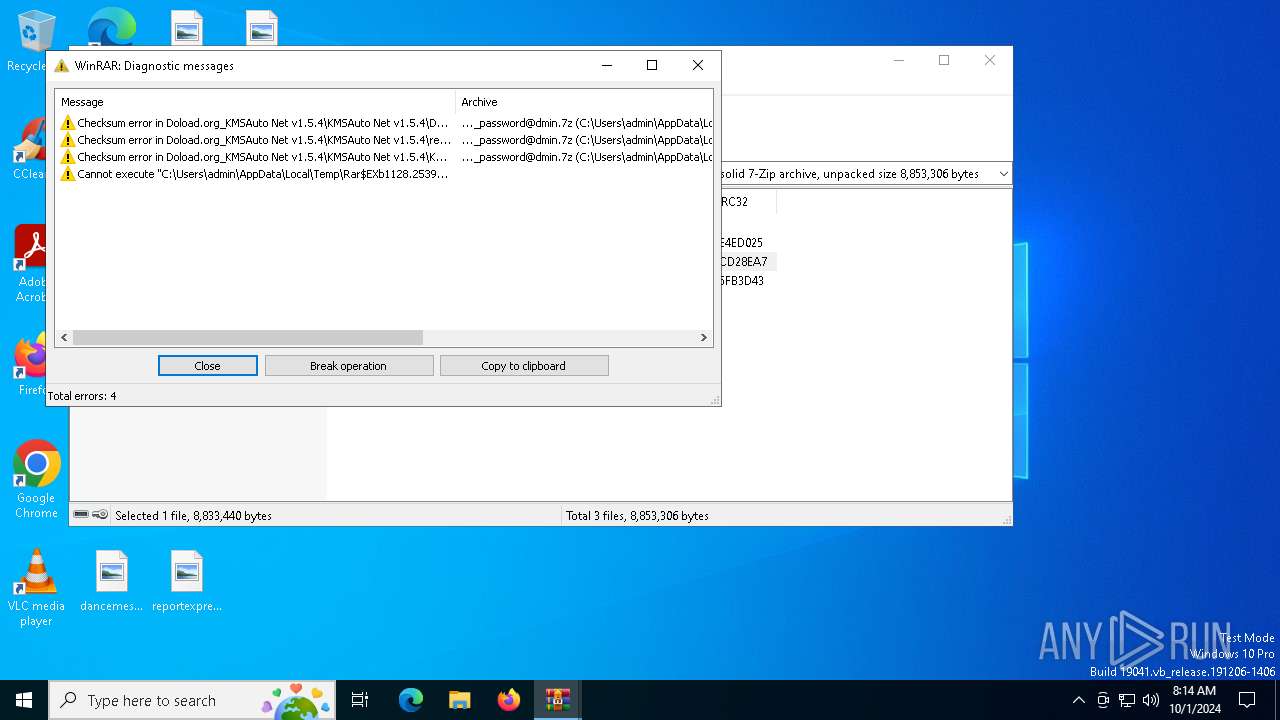
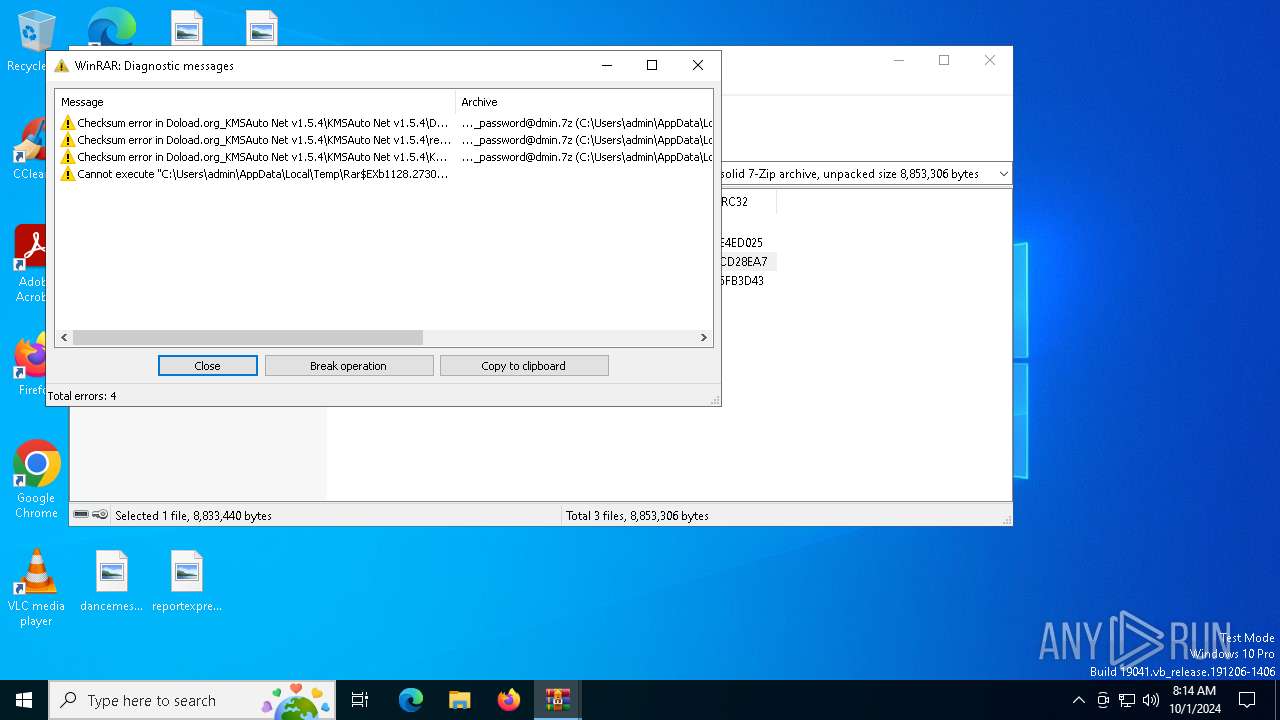
- WinRAR.exe (PID: 1128)
Drops 7-zip archiver for unpacking
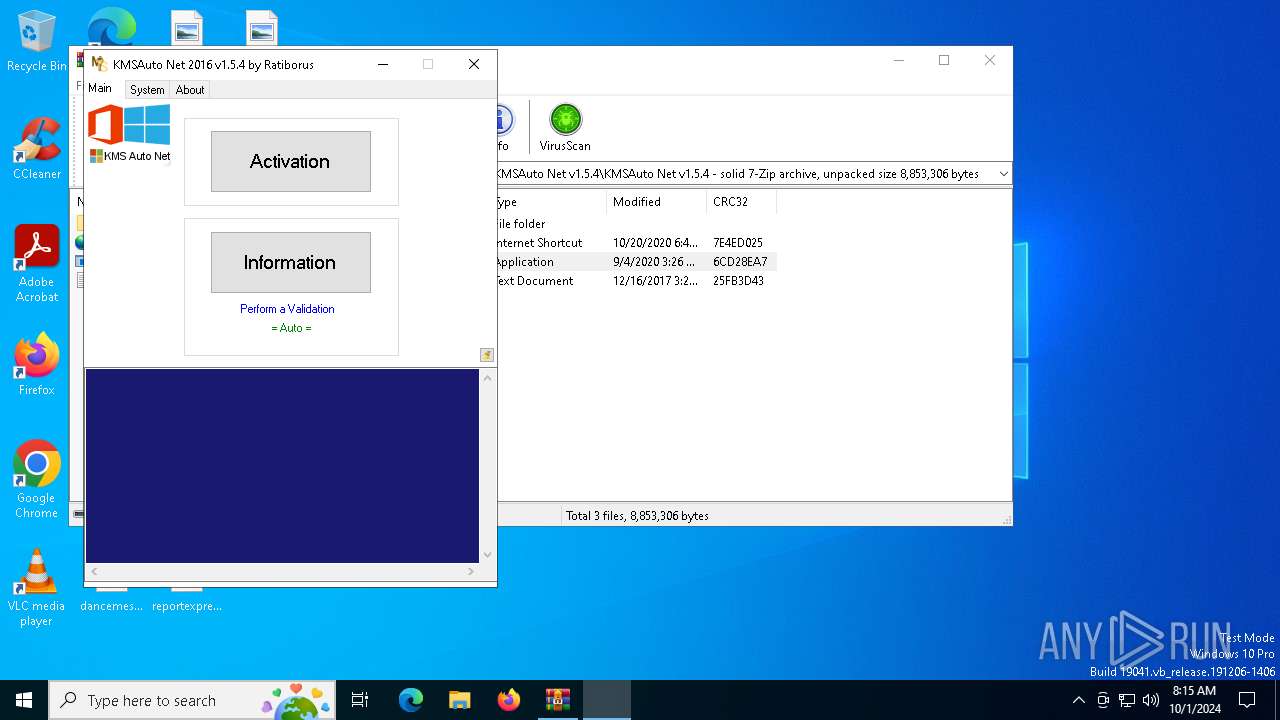
- kmsauto net.exe (PID: 4932)
Executable content was dropped or overwritten
- kmsauto net_v.exe (PID: 6264)
- wzt.dat (PID: 2580)
- kmsauto net.exe (PID: 4932)
- bin.dat (PID: 5772)
- bin_x64.dat (PID: 2836)
- AESDecoder.exe (PID: 1780)
- bin_x64.dat (PID: 2192)
- wzt.dat (PID: 2816)
- bin.dat (PID: 2192)
- AESDecoder.exe (PID: 6832)
- bin_x64.dat (PID: 2368)
- KMSAuto_Net.exe (PID: 2708)
Starts application with an unusual extension
- cmd.exe (PID: 2092)
- cmd.exe (PID: 7164)
- cmd.exe (PID: 5080)
- cmd.exe (PID: 2956)
- cmd.exe (PID: 7124)
- cmd.exe (PID: 3712)
- cmd.exe (PID: 6912)
Starts CMD.EXE for commands execution
- kmsauto net.exe (PID: 4932)
- cmd.exe (PID: 1776)
Process drops legitimate windows executable
- wzt.dat (PID: 2580)
- bin_x64.dat (PID: 2836)
- bin_x64.dat (PID: 2192)
- wzt.dat (PID: 2816)
- bin_x64.dat (PID: 2368)
Uses NETSH.EXE to add a firewall rule or allowed programs
- kmsauto net.exe (PID: 4932)
Executes as Windows Service
- KMSSS.exe (PID: 304)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- kmsauto net.exe (PID: 4932)
Found regular expressions for crypto-addresses (YARA)
- svchost32.exe (PID: 4716)
Uses REG/REGEDIT.EXE to modify registry
- kmsauto net.exe (PID: 4932)
- cmd.exe (PID: 1716)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 3992)
Starts POWERSHELL.EXE for commands execution
- svchost32.exe (PID: 4716)
Drops a system driver (possible attempt to evade defenses)
- bin_x64.dat (PID: 2192)
- bin_x64.dat (PID: 2836)
- bin_x64.dat (PID: 2368)
Uses ROUTE.EXE to modify routing table
- cmd.exe (PID: 6844)
Application launched itself
- cmd.exe (PID: 1776)
Starts itself from another location
- svchost32.exe (PID: 4716)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2208)
Executes application which crashes
- system32.exe (PID: 2212)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 6868)
Modifies existing scheduled task
- schtasks.exe (PID: 6968)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 1128)
UPX packer has been detected
- kmsauto net.exe (PID: 4932)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
315
Monitored processes
175
Malicious processes
8
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 304 | "C:\ProgramData\KMSAuto\bin\KMSSS.exe" -Port 1688 -PWin RandomKMSPID -PO14 RandomKMSPID -PO15 RandomKMSPID -PO16 RandomKMSPID -AI 43200 -RI 43200 -Log -IP | C:\ProgramData\KMSAuto\bin\KMSSS.exe | — | services.exe | |||||||||||
User: SYSTEM Company: MSFree Inc. Integrity Level: SYSTEM Description: KMS emulator by Ratiborus. Exit code: 0 Version: 2.0.7.0 Modules
| |||||||||||||||
| 400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | svchost.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | C:\WINDOWS\Sysnative\cmd.exe /D /c AESDecoder.exe | C:\Windows\System32\cmd.exe | — | kmsauto net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | C:\WINDOWS\Sysnative\cmd.exe /D /c certmgr.exe -add wzteam.cer -n wzteam -s -r localMachine ROOT | C:\Windows\System32\cmd.exe | — | kmsauto net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1008 | C:\WINDOWS\Sysnative\cmd.exe /D /c del /F /Q "bin.dat" | C:\Windows\System32\cmd.exe | — | kmsauto net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 765
Read events
29 730
Write events
27
Delete events
8
Modification events
| (PID) Process: | (1128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
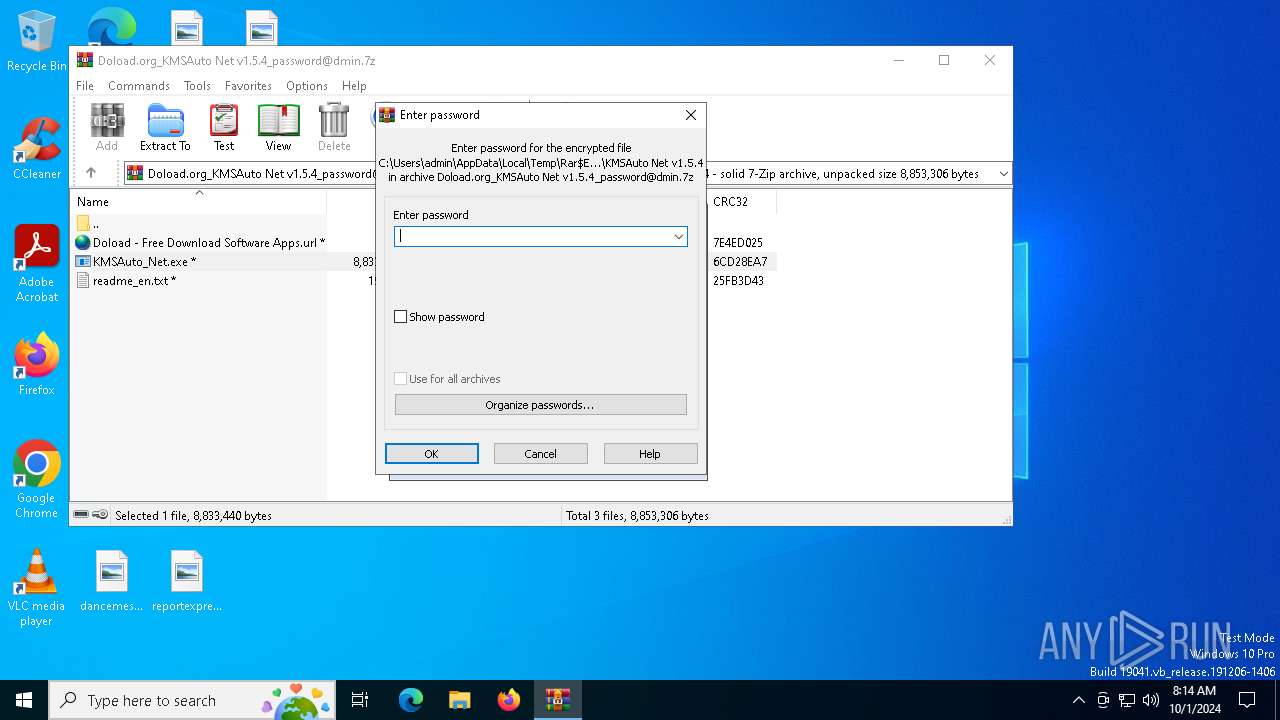
Value: C:\Users\admin\AppData\Local\Temp\Doload.org_KMSAuto Net v1.5.4_password@dmin.7z | |||
| (PID) Process: | (1128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
| (PID) Process: | (2708) KMSAuto_Net.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: A8AFFB6600000000 | |||
| (PID) Process: | (2708) KMSAuto_Net.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
49
Suspicious files
26
Text files
18
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1128.33732\Doload.org_KMSAuto Net v1.5.4\KMSAuto Net v1.5.4\readme_en.txt | text | |
MD5:F928E511DE690CD342B631B5C16A355A | SHA256:11367EF9FD35DDABBE9A04CC3AEB0AAEDBE6DB8FE3D41892E2AACBEB79F001E1 | |||
| 2708 | KMSAuto_Net.exe | C:\Users\admin\kmsauto net_v.exe | executable | |
MD5:A5F81D33DC9F0C07DBCE908B90D7AB5A | SHA256:FA1B9D992DE7C5849C8EB2F51E991A3899CE0735C1D5DA9D270271D5412ABAE6 | |||
| 2708 | KMSAuto_Net.exe | C:\Users\admin\system32.exe | executable | |
MD5:1461068E84322CF7AF19A938E9CF9B24 | SHA256:D3D508BDDC6DA73AE8585C0DD7A14E781F55E4DDAF6A55CF6F6EE4A6D0EB1039 | |||
| 4932 | kmsauto net.exe | C:\Users\admin\AppData\Local\MSfree Inc\kmsauto.ini | text | |
MD5:AF6A20FD7DFADCD582CCF2B1BFAAF82B | SHA256:0BEE97833A70AA9BA271E93226DACE849836C64919FBFE15543D694E219D4AF2 | |||
| 6264 | kmsauto net_v.exe | C:\Users\admin\kmsauto net.exe | executable | |
MD5:C44B78898B8D24BC78ACFC47516A3287 | SHA256:896388E05507979E3EB8C445D2475EF2B57A5519F6EDB3ABA8AC92C573E11A1A | |||
| 1128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1128.33732\Doload.org_KMSAuto Net v1.5.4\KMSAuto Net v1.5.4\KMSAuto_Net.exe | executable | |
MD5:3145750685F2D676880374160CE207C9 | SHA256:81C6DEF81E9D5CA2D92510DFF8FD55B0FFE11515314BED55C552CF1802065FA8 | |||
| 1336 | kmsservice.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bc2t5oxr.jk0.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2580 | wzt.dat | C:\ProgramData\KMSAuto\wzt\certmgr.exe | executable | |
MD5:9D4F1124B2D870583268D19317D564AE | SHA256:EBAD2237B3E7CDF65385CCCE5099E82C7EC5080E737C97CE4E542CDBEA8D418D | |||
| 2580 | wzt.dat | C:\ProgramData\KMSAuto\wzt\wzteam.cer | der | |
MD5:76B56D90E6F1DA030A8B85E64579F25A | SHA256:FD2D7DF0220DD65EE23D0090299DFCC356F6F8F7167BAE9ADF7D08CEFAF39D02 | |||
| 6264 | kmsauto net_v.exe | C:\Users\admin\svchost32.exe | executable | |
MD5:AD011D1E3FB8B21F20A75CD52067B3D4 | SHA256:1566DDA7D16618AD75CCF6514676DCFC0D18F7EED0E1AD93E4A5C99C202A8AB0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
61
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1328 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1504 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1504 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1336 | kmsservice.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
2116 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1116 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2952 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2952 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1328 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1328 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
Process | Message |
|---|---|
FakeClient.exe | WdfCoInstaller: [10/01/2024 08:15.54.899] ReadComponents: WdfSection for Driver Service windivert using KMDF lib version Major 0x1, minor 0x9
|
FakeClient.exe | WdfCoInstaller: [10/01/2024 08:15.54.915] BootApplication: could not open service windivert, error error(1060) The specified service does not exist as an installed service.
|
FakeClient.exe | WdfCoInstaller: [10/01/2024 08:15.54.915] BootApplication: GetStartType error error(87) The parameter is incorrect.
Driver Service name windivert
|