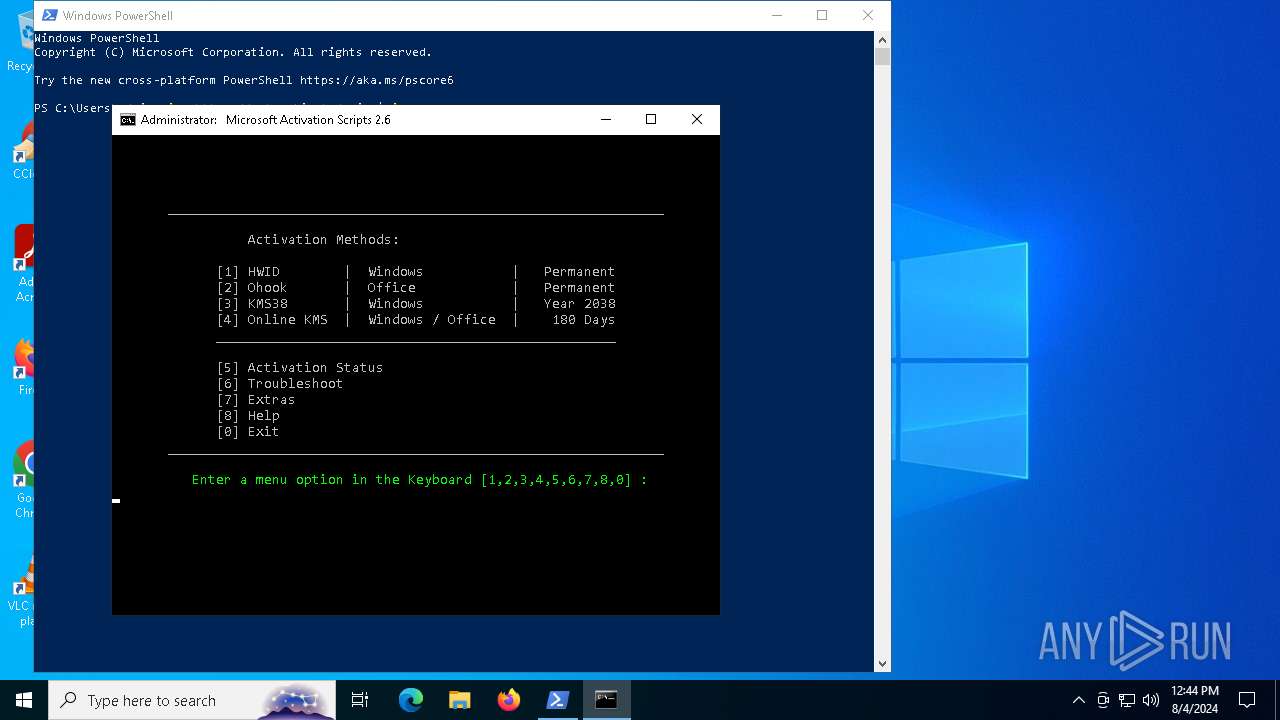
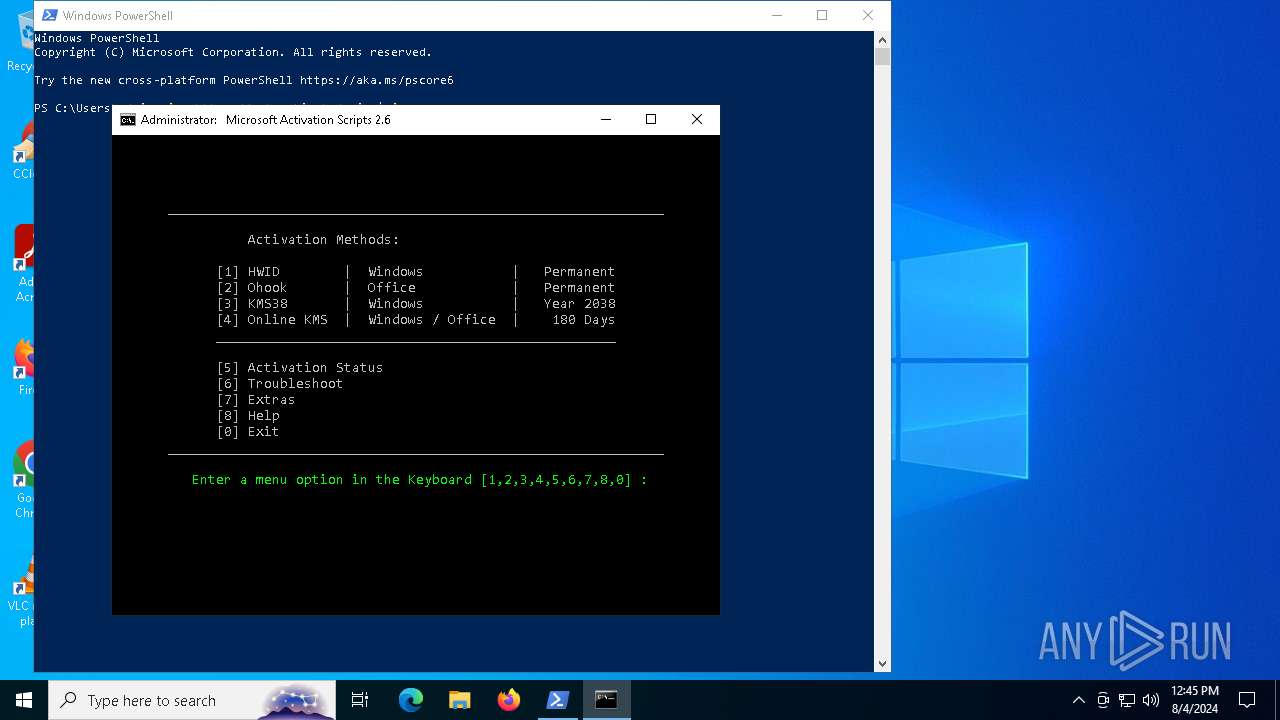
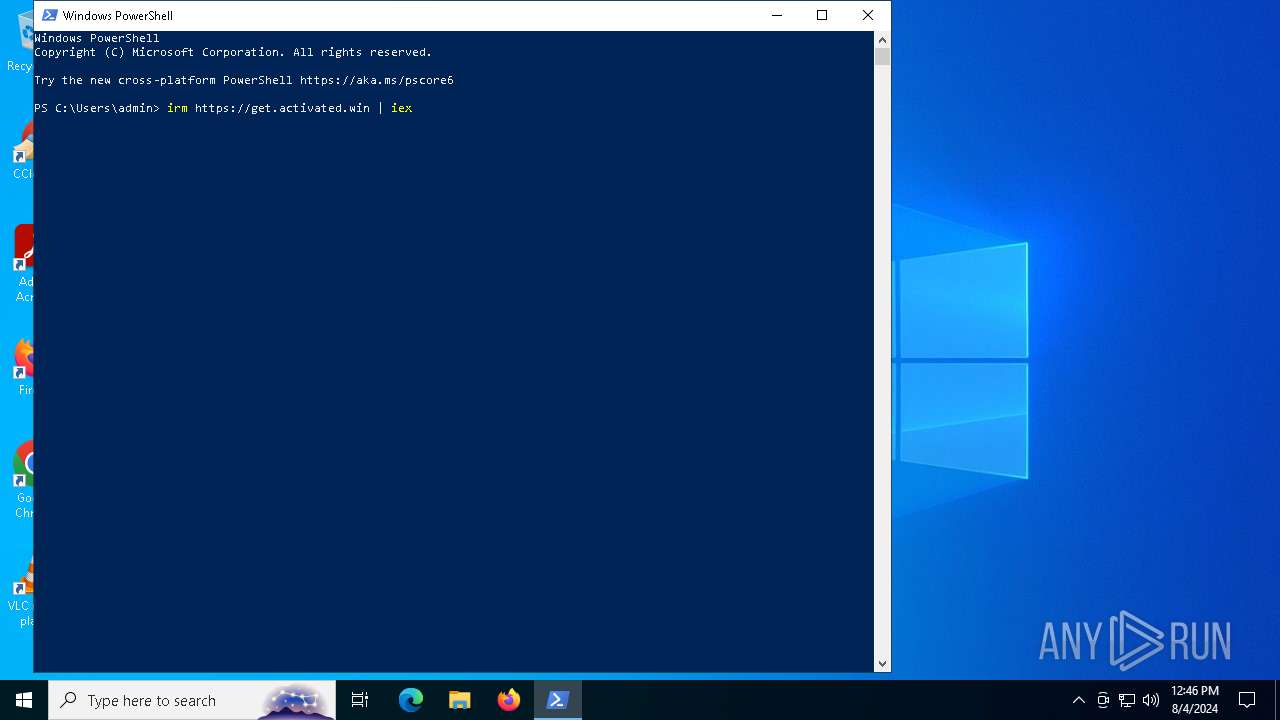
| URL: | massgrave.dev |
| Full analysis: | https://app.any.run/tasks/56f6b371-1cbd-4f75-9bd6-77deba413733 |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2024, 12:44:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C2AF0D872F2351E0C959EF559A10D748 |
| SHA1: | 00C6DCDD2CE2CDC411D076F9F2A466689FC3C33A |
| SHA256: | 78691F9EB88DF34A05D898B5E051D22EE3FCA8A7C07A720FA284765419B3925D |
| SSDEEP: | 3:5R80n:r80n |
MALICIOUS
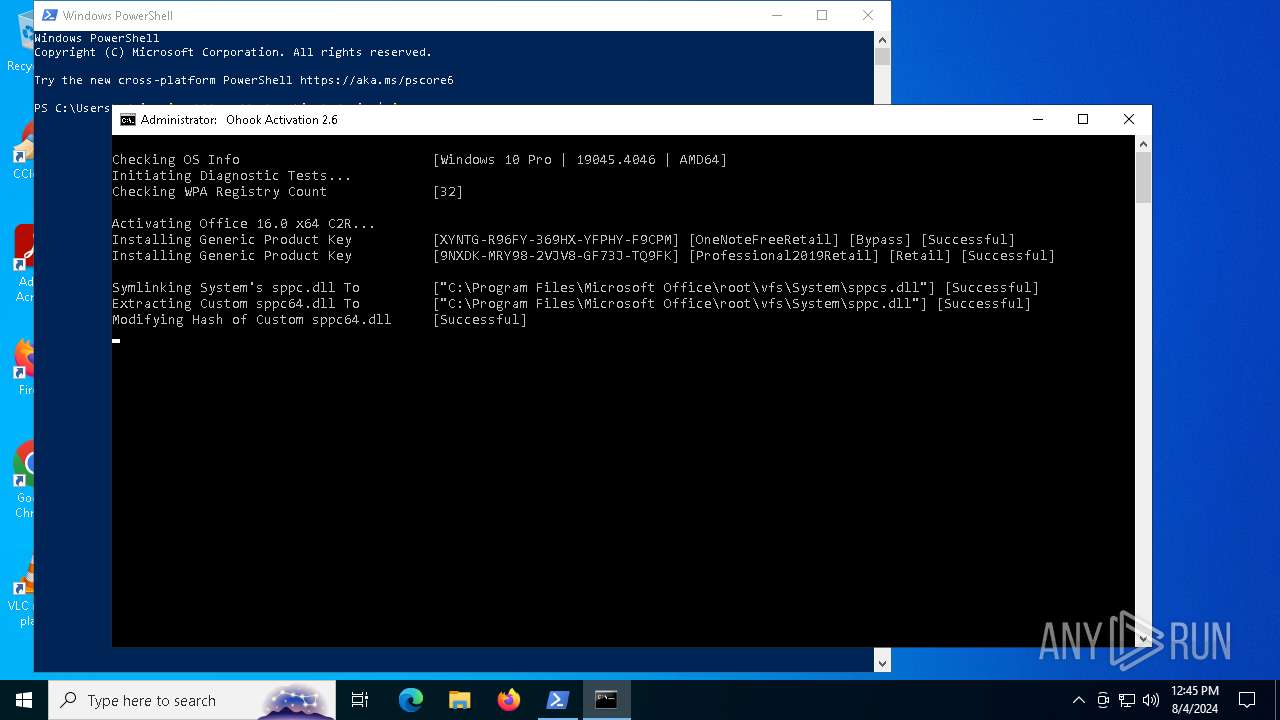
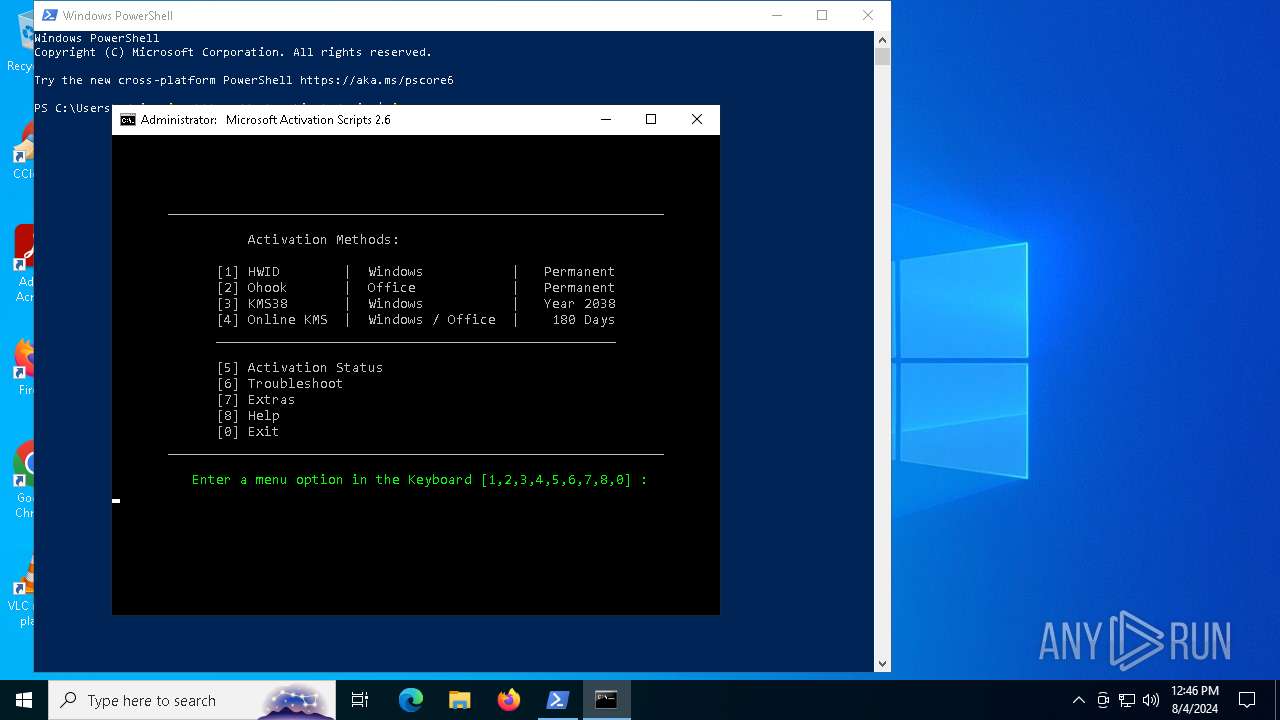
Drops the executable file immediately after the start
- powershell.exe (PID: 7696)
SUSPICIOUS
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 1044)
Creates/Modifies COM task schedule object
- POWERPNT.EXE (PID: 6432)
Starts SC.EXE for service management
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6660)
- cmd.exe (PID: 7300)
Executing commands from ".cmd" file
- powershell.exe (PID: 1044)
- cmd.exe (PID: 6296)
- powershell.exe (PID: 6888)
- cmd.exe (PID: 6660)
- cmd.exe (PID: 7300)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 1044)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 1044)
- cmd.exe (PID: 6296)
- powershell.exe (PID: 6888)
- cmd.exe (PID: 6660)
- cmd.exe (PID: 7620)
- cmd.exe (PID: 7300)
- cmd.exe (PID: 2204)
- cmd.exe (PID: 4160)
- cmd.exe (PID: 7104)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6660)
- cmd.exe (PID: 7300)
- cmd.exe (PID: 6184)
Application launched itself
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6660)
- cmd.exe (PID: 7620)
- cmd.exe (PID: 2204)
- cmd.exe (PID: 7300)
- cmd.exe (PID: 4160)
- cmd.exe (PID: 7104)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6296)
- cmd.exe (PID: 7300)
- cmd.exe (PID: 4276)
- cmd.exe (PID: 2360)
- cmd.exe (PID: 7604)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7300)
- cmd.exe (PID: 6660)
- cmd.exe (PID: 6184)
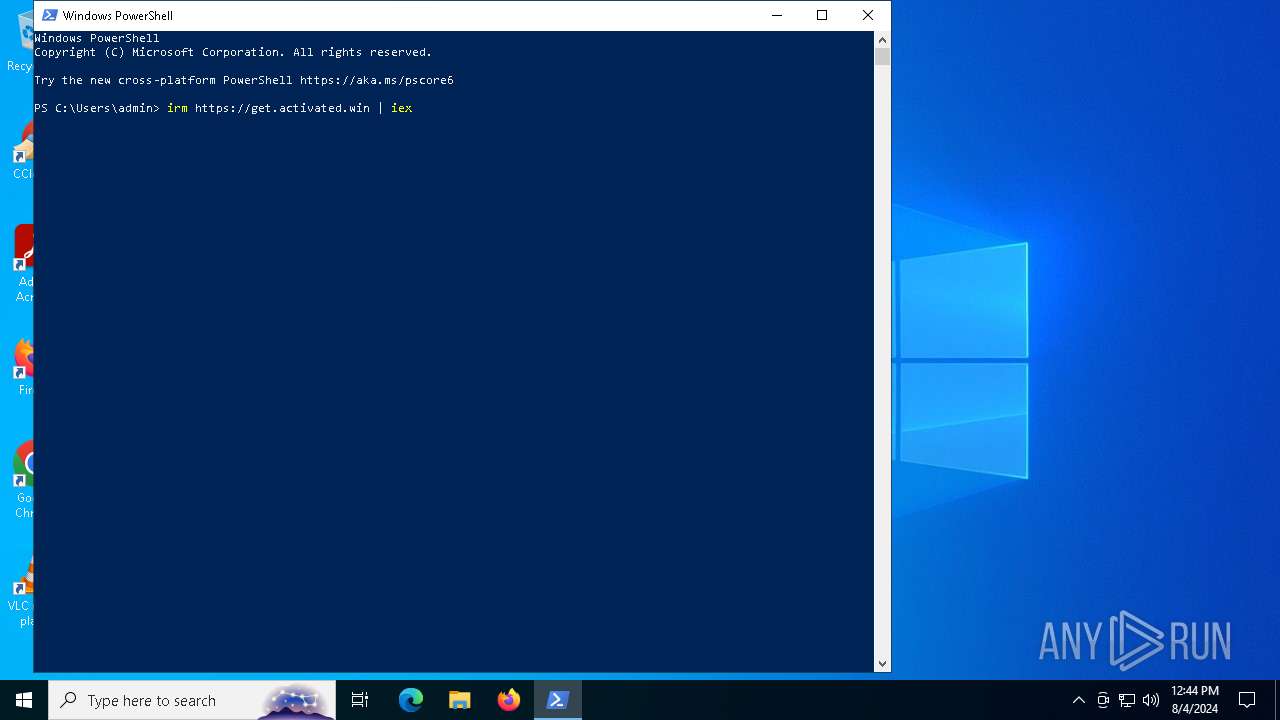
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 4276)
- cmd.exe (PID: 7300)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7300)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 4276)
- cmd.exe (PID: 7300)
- cmd.exe (PID: 7604)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 6912)
- powershell.exe (PID: 7696)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6912)
- powershell.exe (PID: 7696)
Hides command output
- cmd.exe (PID: 4276)
- cmd.exe (PID: 7304)
- cmd.exe (PID: 6600)
- cmd.exe (PID: 6952)
- cmd.exe (PID: 6872)
- cmd.exe (PID: 7872)
- cmd.exe (PID: 6940)
- cmd.exe (PID: 3696)
- cmd.exe (PID: 3660)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 7832)
- cmd.exe (PID: 888)
- cmd.exe (PID: 7852)
- cmd.exe (PID: 5904)
- cmd.exe (PID: 7864)
- cmd.exe (PID: 4308)
- cmd.exe (PID: 6468)
- cmd.exe (PID: 6184)
- cmd.exe (PID: 6732)
- cmd.exe (PID: 7604)
- cmd.exe (PID: 2464)
Process drops legitimate windows executable
- Dism.exe (PID: 5092)
The process creates files with name similar to system file names
- Dism.exe (PID: 5092)
Executable content was dropped or overwritten
- Dism.exe (PID: 5092)
- powershell.exe (PID: 7696)
The process executes VB scripts
- cmd.exe (PID: 7300)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 1128)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 3276)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7852)
- cmd.exe (PID: 5904)
- cmd.exe (PID: 2464)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 7300)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 7696)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 1128)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 1128)
INFO
Reads Microsoft Office registry keys
- firefox.exe (PID: 6560)
- firefox.exe (PID: 6672)
- reg.exe (PID: 3164)
- reg.exe (PID: 7788)
- reg.exe (PID: 7728)
- reg.exe (PID: 7984)
- reg.exe (PID: 6620)
- reg.exe (PID: 7424)
- reg.exe (PID: 376)
- reg.exe (PID: 7028)
- reg.exe (PID: 3880)
- reg.exe (PID: 5916)
- reg.exe (PID: 3548)
- reg.exe (PID: 6560)
Application launched itself
- firefox.exe (PID: 6560)
- firefox.exe (PID: 6512)
- firefox.exe (PID: 6672)
- firefox.exe (PID: 6628)
Checks supported languages
- TextInputHost.exe (PID: 4132)
- mode.com (PID: 6720)
- mode.com (PID: 2064)
- mode.com (PID: 6560)
- DismHost.exe (PID: 3276)
- mode.com (PID: 7516)
Reads the computer name
- TextInputHost.exe (PID: 4132)
- DismHost.exe (PID: 3276)
Manual execution by a user
- POWERPNT.EXE (PID: 6432)
- powershell.exe (PID: 1044)
- firefox.exe (PID: 6628)
Checks current location (POWERSHELL)
- powershell.exe (PID: 1044)
Disables trace logs
- powershell.exe (PID: 1044)
Checks proxy server information
- powershell.exe (PID: 1044)
Checks operating system version
- cmd.exe (PID: 6296)
- cmd.exe (PID: 6660)
- cmd.exe (PID: 7300)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6196)
- cscript.exe (PID: 1128)
- WMIC.exe (PID: 2680)
- WMIC.exe (PID: 3360)
- WMIC.exe (PID: 6404)
- WMIC.exe (PID: 7092)
- WMIC.exe (PID: 6860)
- WMIC.exe (PID: 7100)
- WMIC.exe (PID: 6920)
- WMIC.exe (PID: 2580)
Create files in a temporary directory
- Dism.exe (PID: 5092)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 6912)
- powershell.exe (PID: 7696)
Reads Environment values
- DismHost.exe (PID: 3276)
Drops the executable file immediately after the start
- Dism.exe (PID: 5092)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6912)
- powershell.exe (PID: 7696)
Creates files in the program directory
- cmd.exe (PID: 7300)
- powershell.exe (PID: 7696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
428
Monitored processes
283
Malicious processes
8
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | sc query Null | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | powershell.exe "$acl = Get-Acl '"C:\WINDOWS\System32\spp\store\2.0"'; if ($acl.Access.Where{ $_.IdentityReference -eq 'NT SERVICE\sppsvc' -and $_.AccessControlType -eq 'Deny' -or $acl.Access.IdentityReference -notcontains 'NT SERVICE\sppsvc'}) {Exit 2}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 376 | reg query HKU\S-1-5-21-1693682860-607145093-2874071422-1001\Software\Microsoft\Office\16.0\Common\Licensing\LicensingNext | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 888 | C:\WINDOWS\system32\cmd.exe /c reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform" /v "SkipRearm" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | reg add HKCU\Console /v QuickEdit /t REG_DWORD /d "0" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1044 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | cscript //nologo C:\WINDOWS\system32\slmgr.vbs /dlv | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1132 | reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WinPE" /v InstRoot | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | powershell.exe "&{$W=$Host.UI.RawUI.WindowSize;$B=$Host.UI.RawUI.BufferSize;$W.Height=32;$B.Height=300;$Host.UI.RawUI.WindowSize=$W;$Host.UI.RawUI.BufferSize=$B;}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1216 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo "1717c1e0-47d3-4899-a6d3-1022db7415e0 2aa09c36-3e86-4580-8e8d-e67dfc13a5a6 327dab29-b51e-4a29-9204-d83a3b353d76 3a4a2cf6-5892-484d-b3d5-fe9cc5a20d78 3e0f37cc-584b-46b1-873e-c44ad57d6605 436366de-5579-4f24-96db-3893e4400030 45c8342d-379d-4a4f-99c5-61141d3e0260 522f8458-7d49-42ff-a93b-670f6b6176ae 6379f5c8-baa4-482e-a5cc-38ade1a57348 65c693f4-3f1c-48a6-afe6-a6eb78a65ccb 72621d09-f833-4cc5-812b-2929a06dcf4f 86834d00-7896-4a38-8fae-32f20b86fa2b 91ab0c97-4cbe-4889-aca0-f0c9394046d7 ac9c8fb4-387f-4492-a919-d56577ad9861 bea06487-c54e-436a-b535-58aec833f05b da892d82-124e-444b-bd01-b109155cb2ae eb972895-440e-4863-be98-ba075b9721d0 edc83d99-c10d-4adf-8d0c-98342381820b" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
105 765
Read events
105 190
Write events
541
Delete events
34
Modification events
| (PID) Process: | (6512) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: D42FC2C700000000 | |||
| (PID) Process: | (6560) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: E5FBC3C700000000 | |||
| (PID) Process: | (6560) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Progress |
Value: 0 | |||
| (PID) Process: | (6560) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Progress |
Value: 1 | |||
| (PID) Process: | (6560) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Installer\308046B0AF4A39CB |
| Operation: | delete value | Name: | installer.taskbarpin.win10.enabled |
Value: | |||
| (PID) Process: | (6560) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (6560) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (6560) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (6560) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (6560) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
Executable files
52
Suspicious files
119
Text files
60
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6560 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6560 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:D1CAF2E0A1B0567013844C98509BFB9F | SHA256:D3EF8D4C0F9D89707E2A9350014D5C9A65E1AC531A52C1C3512F8EE680F84278 | |||
| 6560 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db-journal | binary | |
MD5:292FB262D0CC6ED3883A6CBCB371611E | SHA256:FA1E0F84F71E3A4D231493D2A9A4E8566AB5916653075AA89D70523C9F18C648 | |||
| 6560 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 6560 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6560 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6560 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6560 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | dbf | |
MD5:EF90022DF0735160DD056C0E6670E915 | SHA256:2B663C0B462A437C8DE3D9B95EE157AE181249B78BDD6F7BD73F7EB6D9E03F87 | |||
| 6560 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6560 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db | binary | |
MD5:7DE1307C945D8A8BC1860D8D7368260B | SHA256:7070AB2181EAF052C30A9DCFBD5F8FE378DC26EF11A85E83A7E0DA40C60C1AD8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
116
DNS requests
122
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6560 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6560 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6560 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6560 | firefox.exe | GET | 301 | 172.67.201.171:80 | http://massgrave.dev/ | unknown | — | — | unknown |
6560 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
6560 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
6560 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6560 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
6560 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
6560 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3140 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3720 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6560 | firefox.exe | 172.67.201.171:80 | massgrave.dev | CLOUDFLARENET | US | unknown |
6560 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
6560 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
6560 | firefox.exe | 216.58.212.170:443 | safebrowsing.googleapis.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
massgrave.dev |
| unknown |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
ipv4only.arpa |
| whitelisted |
example.org |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
Process | Message |
|---|---|
Dism.exe | PID=5092 TID=6920 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=5092 TID=6920 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=5092 TID=6920 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=5092 TID=6920 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=5092 TID=6920 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=5092 TID=6920 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=3276 TID=2572 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=3276 TID=2572 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=3276 TID=2572 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=5092 TID=6920 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |