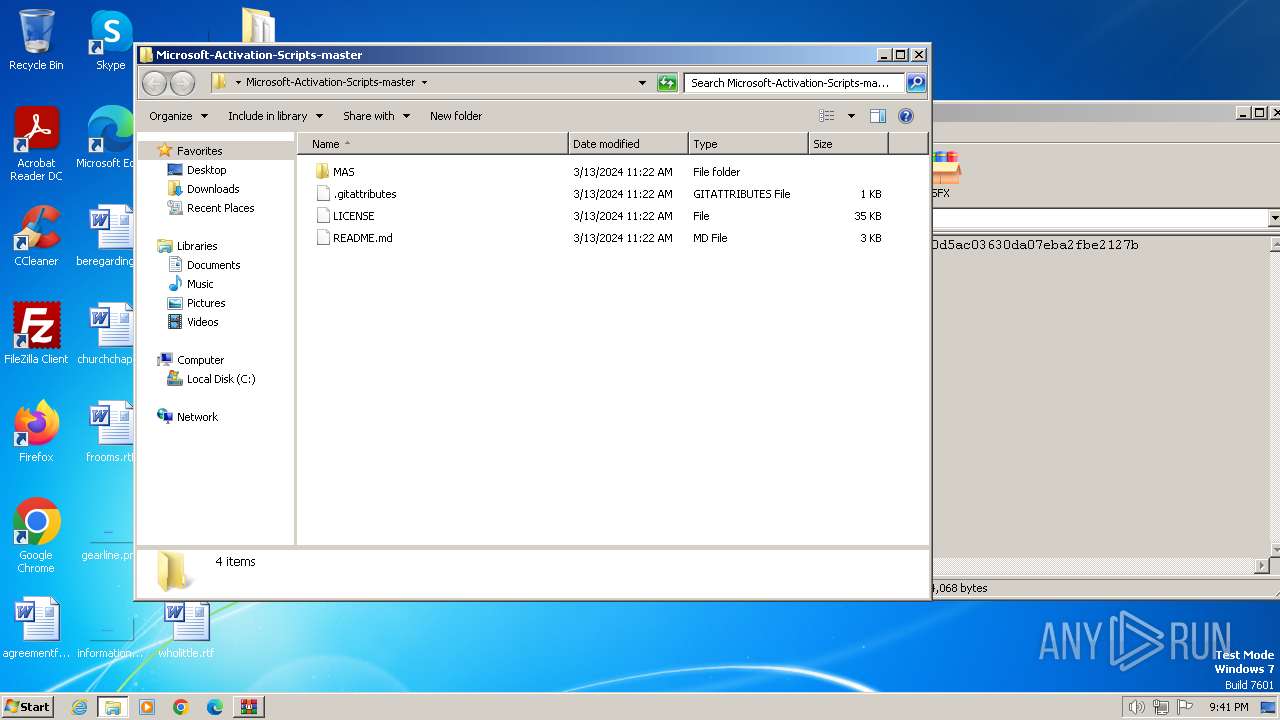
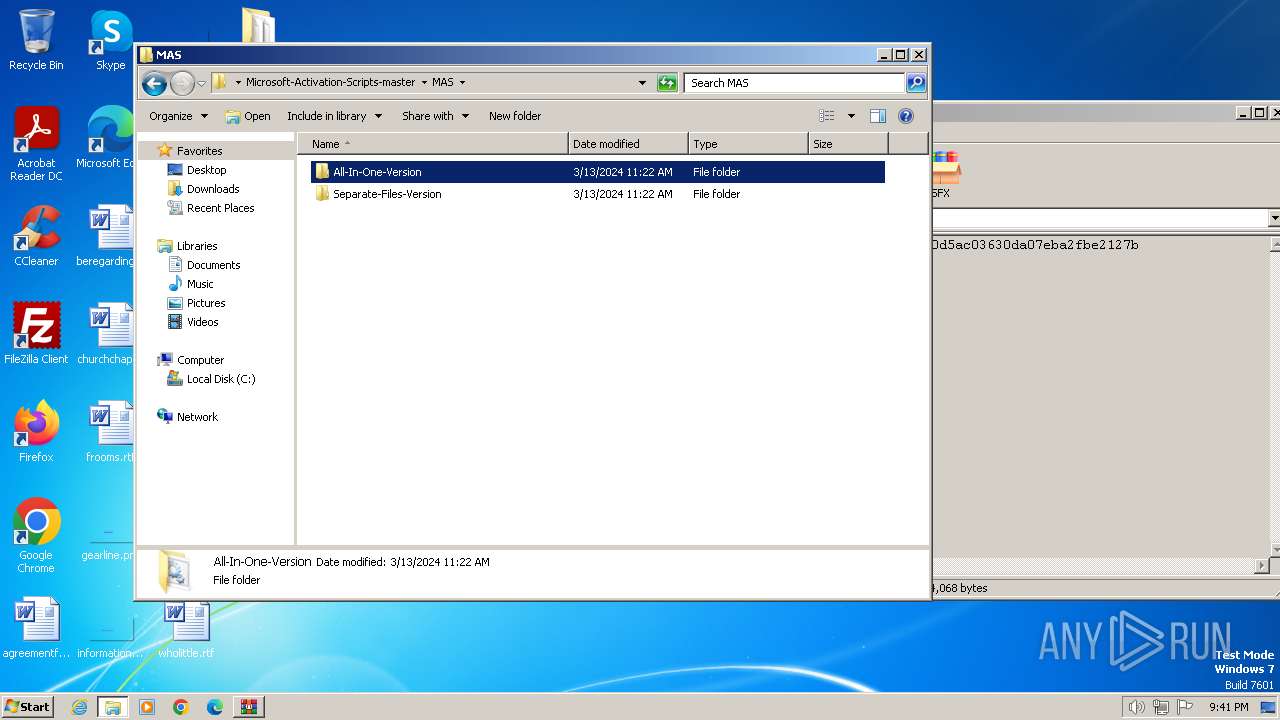
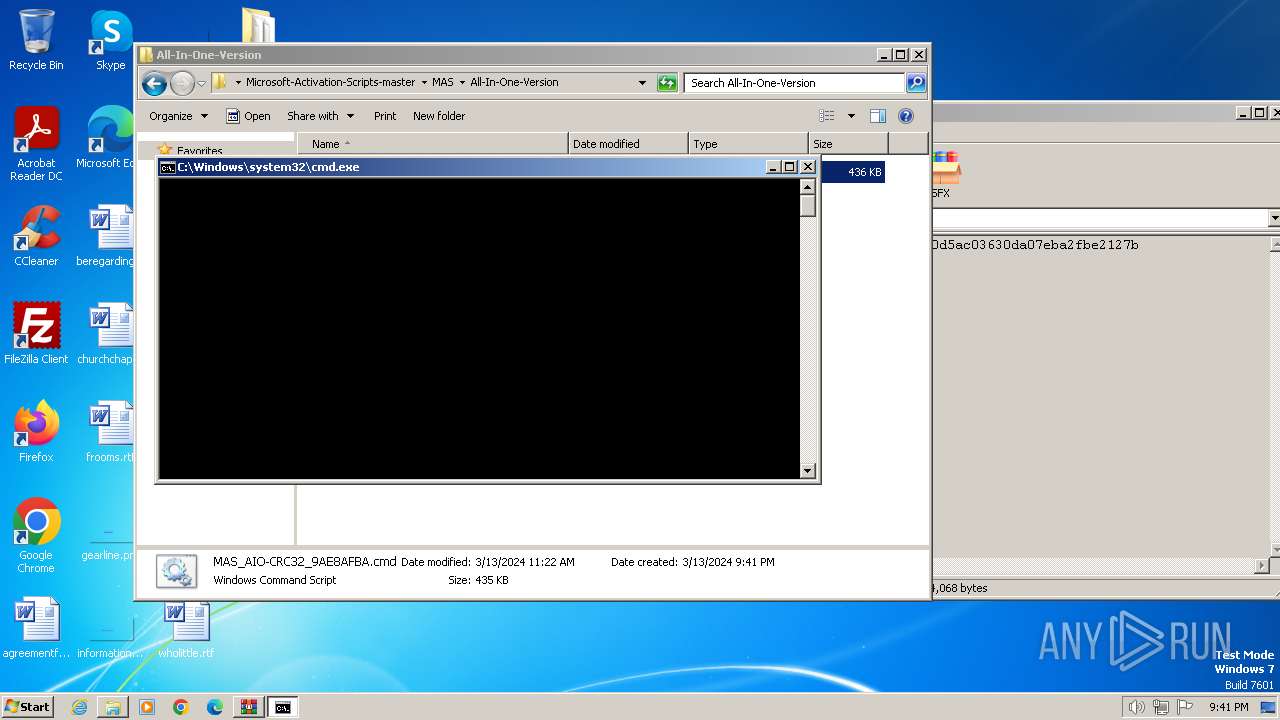
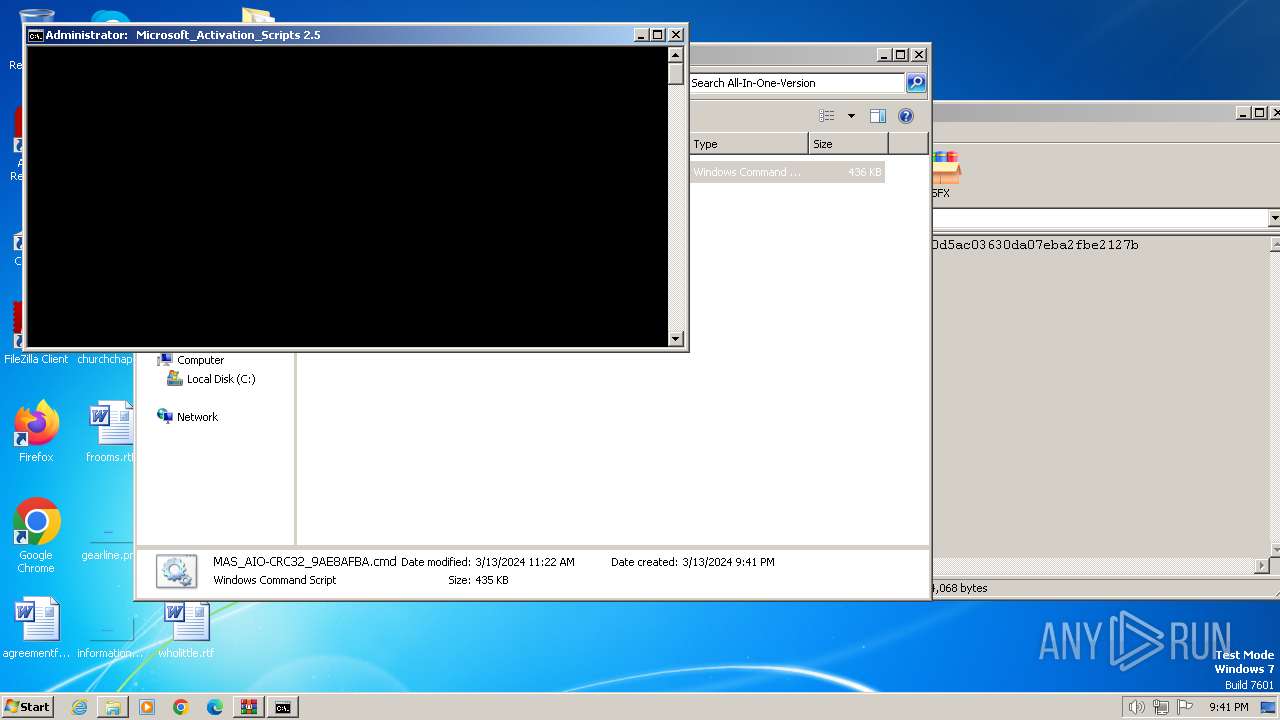
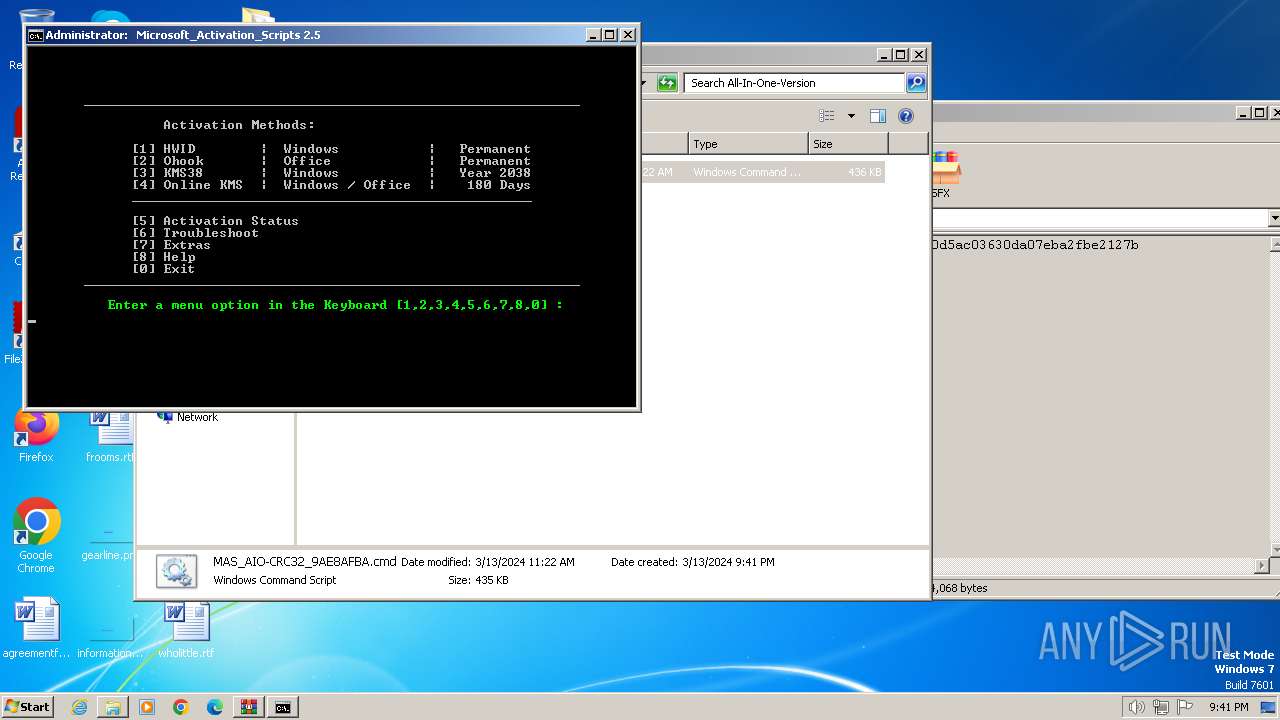
| File name: | Microsoft-Activation-Scripts-master.zip |
| Full analysis: | https://app.any.run/tasks/fba62328-6d0c-419d-b6e8-6ccbf9ac14f5 |
| Verdict: | Malicious activity |
| Analysis date: | March 13, 2024, 21:41:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | D7A74FB92A9A40D597459E86FFA12F11 |
| SHA1: | 6009E6E50EECE5B58D72976DED182E07CE221640 |
| SHA256: | 7863586F017D773B133E4CCE9814B0C8249CC629FB7265BA7C8408FA7D70A61A |
| SSDEEP: | 12288:+afOzLaRAs/u6nHcGDeXbJpFVcZiF4zYxCklr:+kOzLaRAsW6nHcGDeXbJpFVcwF4zmlr |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 3248)
- cmd.exe (PID: 2148)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2624)
- powershell.exe (PID: 116)
- cmd.exe (PID: 2148)
Starts SC.EXE for service management
- cmd.exe (PID: 2624)
- cmd.exe (PID: 2148)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2624)
- cmd.exe (PID: 2148)
Executing commands from ".cmd" file
- cmd.exe (PID: 2624)
- powershell.exe (PID: 116)
- cmd.exe (PID: 2148)
Reads the Internet Settings
- powershell.exe (PID: 116)
- WMIC.exe (PID: 3056)
- WMIC.exe (PID: 3940)
- WMIC.exe (PID: 552)
- WMIC.exe (PID: 2584)
- WMIC.exe (PID: 2068)
- WMIC.exe (PID: 3312)
- WMIC.exe (PID: 4064)
- WMIC.exe (PID: 3564)
- WMIC.exe (PID: 2024)
- WMIC.exe (PID: 1264)
Application launched itself
- cmd.exe (PID: 2624)
- cmd.exe (PID: 2148)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2624)
- cmd.exe (PID: 2148)
Hides command output
- cmd.exe (PID: 2672)
- cmd.exe (PID: 2744)
- cmd.exe (PID: 3976)
- cmd.exe (PID: 2992)
- cmd.exe (PID: 316)
- cmd.exe (PID: 2128)
- cmd.exe (PID: 448)
- cmd.exe (PID: 2808)
- cmd.exe (PID: 2588)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2148)
Starts NET.EXE to map network drives
- cmd.exe (PID: 2148)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 2148)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2148)
- cmd.exe (PID: 2308)
- cmd.exe (PID: 896)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 1928)
INFO
Manual execution by a user
- cmd.exe (PID: 2624)
Checks operating system version
- cmd.exe (PID: 2624)
- cmd.exe (PID: 2148)
Checks supported languages
- mode.com (PID: 2772)
- mode.com (PID: 3504)
- mode.com (PID: 1652)
- mode.com (PID: 3048)
- mode.com (PID: 2652)
- mode.com (PID: 1348)
Reads Microsoft Office registry keys
- reg.exe (PID: 1892)
- reg.exe (PID: 840)
- reg.exe (PID: 1484)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:03:13 04:22:44 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Microsoft-Activation-Scripts-master/ |
Total processes
229
Monitored processes
185
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | powershell.exe "start cmd.exe -arg '/c \""""C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\All-In-One-Version\MAS_AIO-CRC32_9AE8AFBA.cmd""" -el \"' -verb runas" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 116 | powershell.exe "&{$W=$Host.UI.RawUI.WindowSize;$B=$Host.UI.RawUI.BufferSize;$W.Height=31;$B.Height=300;$Host.UI.RawUI.WindowSize=$W;$Host.UI.RawUI.BufferSize=$B;}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 120 | sc query Null | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 120 | reg delete "HKLM\SOFTWARE\Microsoft\OfficeSoftwareProtectionPlatform" /f /v KeyManagementServiceName | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 316 | C:\Windows\system32\cmd.exe /c "reg query HKLM\SOFTWARE\Microsoft\Office\14.0\Common\InstallRoot /v Path" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 448 | C:\Windows\system32\cmd.exe /c "reg query HKLM\SOFTWARE\Wow6432Node\Microsoft\Office\14.0\Common\InstallRoot /v Path" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 548 | powershell.exe write-host -back '"Red"' -fore '"white"' '"==== ERROR ===="' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 548 | C:\Windows\system32\net1 stop sppsvc /y | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 552 | wmic path SoftwareLicensingProduct where (Description like '%KMSCLIENT%' ) get Name /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | powershell.exe write-host -back '"Black"' -fore '"Yellow"' '"Press any key to Go back..."' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
23 680
Read events
23 637
Write events
25
Delete events
18
Modification events
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Microsoft-Activation-Scripts-master.zip | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2472) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
18
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Activators\HWID_Activation.cmd | text | |
MD5:13D4E68079965EB95B2DFCCE5456D9C8 | SHA256:2B87C097866023B7A46FF200859A89F4AFD225CFBC8F7D9EBDEFAC1DA1619DEE | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Activators\KMS38_Activation.cmd | text | |
MD5:BEF5B180D317FB7713C5B4BA9BF00BBB | SHA256:9C9B7D7ABA4CE7B0D5B30CF278DB1A1DEBD76857A6C37982D25C61BB82CF0B1D | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\.gitattributes | text | |
MD5:87EB06393A7628EA5CE171C620ECB45E | SHA256:0AD46C92E5970CD411D921177BCBE77FB73A14901EE619312D6445E03E74C47F | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Extract_OEM_Folder.cmd | text | |
MD5:37A2205CAF8DC4386761BDFC150997C6 | SHA256:2013EDA675C560A377753CE2AE69F2BDCDC13D17D1E1B484393FA548F8AC0C68 | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Change_Edition.cmd | text | |
MD5:36BFEB7DC64507ADB806E8124D211EA2 | SHA256:551F2550A48BBB4DD1BC436EEBF5D337FA9C003FC42EE9D20E09F5DAB181E3D3 | |||
| 116 | powershell.exe | C:\Users\admin\AppData\Local\Temp\fmc3jrm5.mw2.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\_ReadMe.html | html | |
MD5:574E18C1F9B32A47F988AC91588901BA | SHA256:8932BACD828C0716B136AF6AA15011AED0015E7838006F2CFF7A64954A5696B0 | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Check-Activation-Status-vbs.cmd | text | |
MD5:97B92ADBE161D5A5731719E18585CFF0 | SHA256:839B7EEFB255A5B53EFBA8980193854B4ABFB472939DDEC0EB248428F08B6C57 | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\LICENSE | text | |
MD5:5B4473596678D62D9D83096273422C8C | SHA256:E57F1C320B8CF8798A7D2FF83A6F9E06A33A03585F6E065FEA97F1D86DB84052 | |||
| 2472 | WinRAR.exe | C:\Users\admin\Desktop\Microsoft-Activation-Scripts-master\MAS\Separate-Files-Version\Check-Activation-Status-wmi.cmd | text | |
MD5:FC7DFD4ABBD167E7303301FA7F593CC2 | SHA256:DE2A3F3016732D6C46CEFA13BA70889EDEDA8FAE3A244DD1C507F1B80D4579F3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
updatecheck.massgrave.dev |
| unknown |
kms.zhuxiaole.org |
| unknown |
xincheng213618.cn |
| unknown |