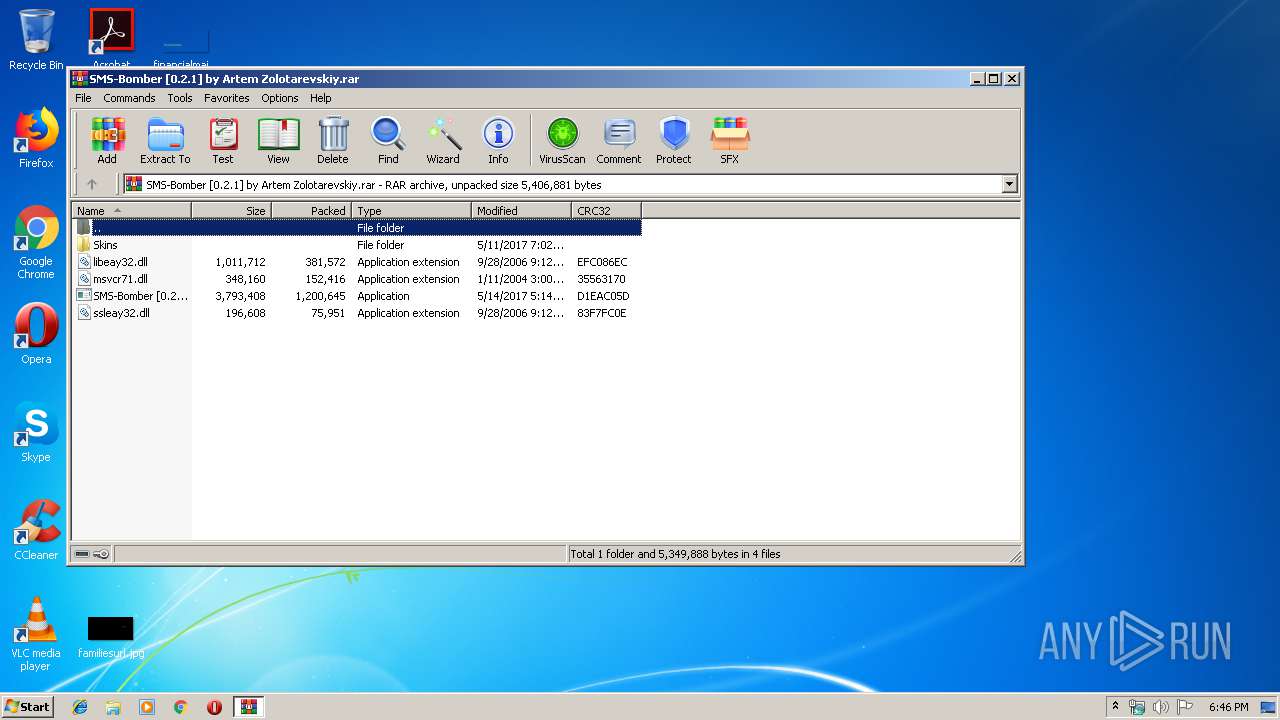
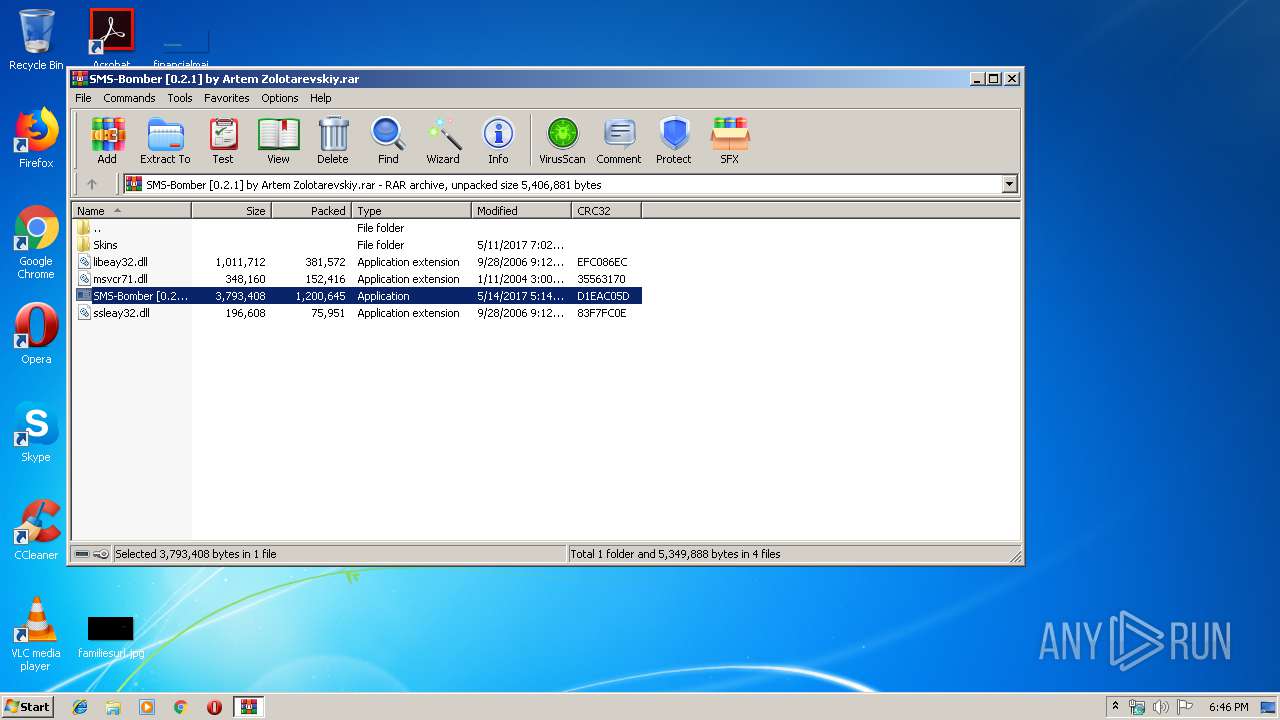
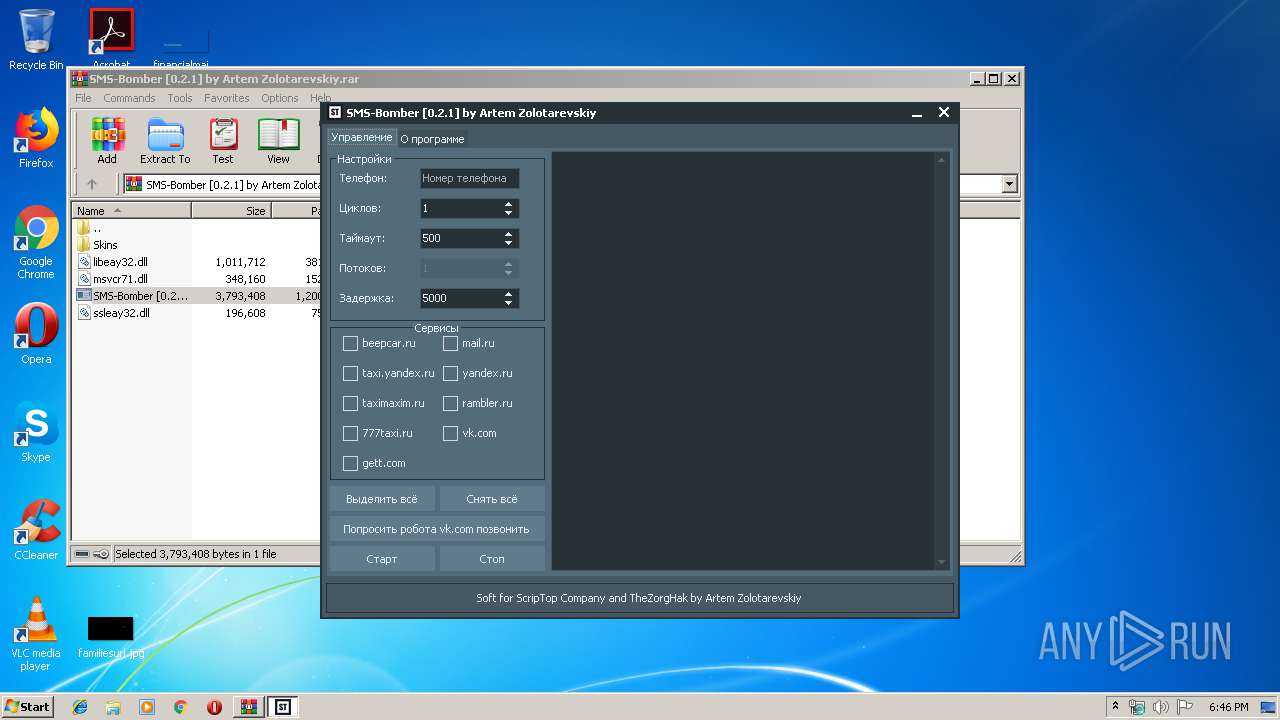
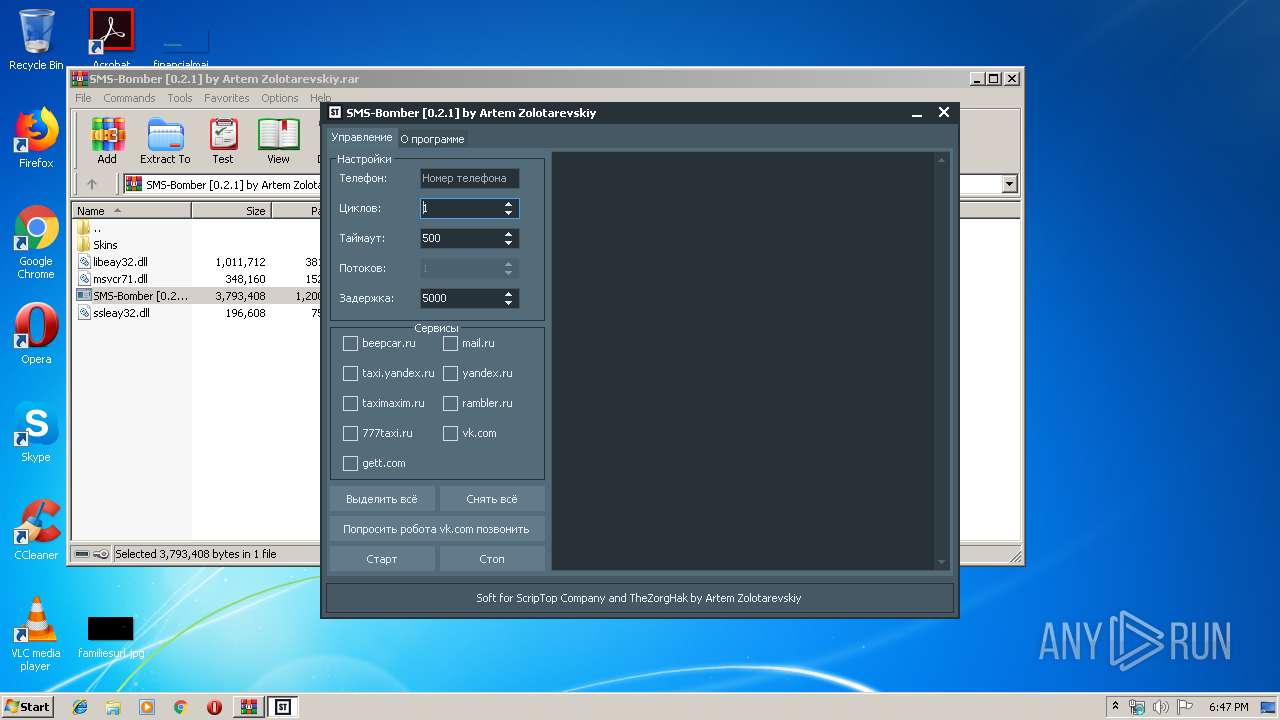
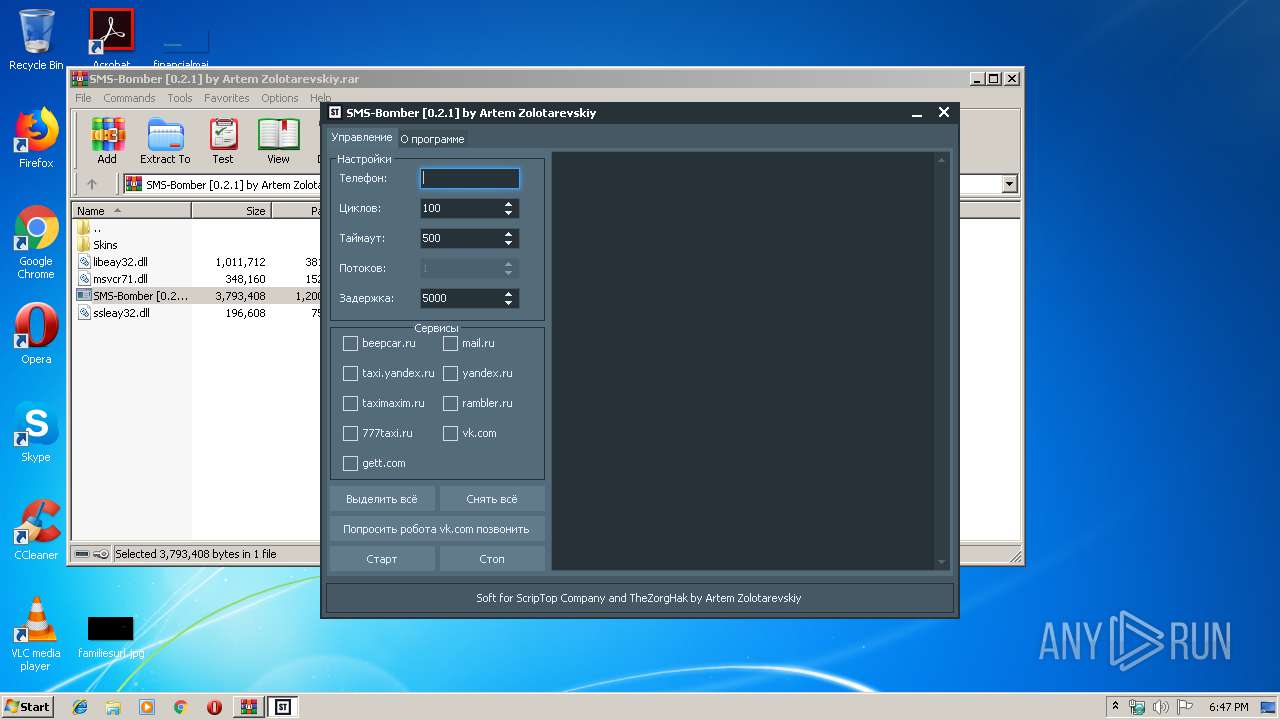
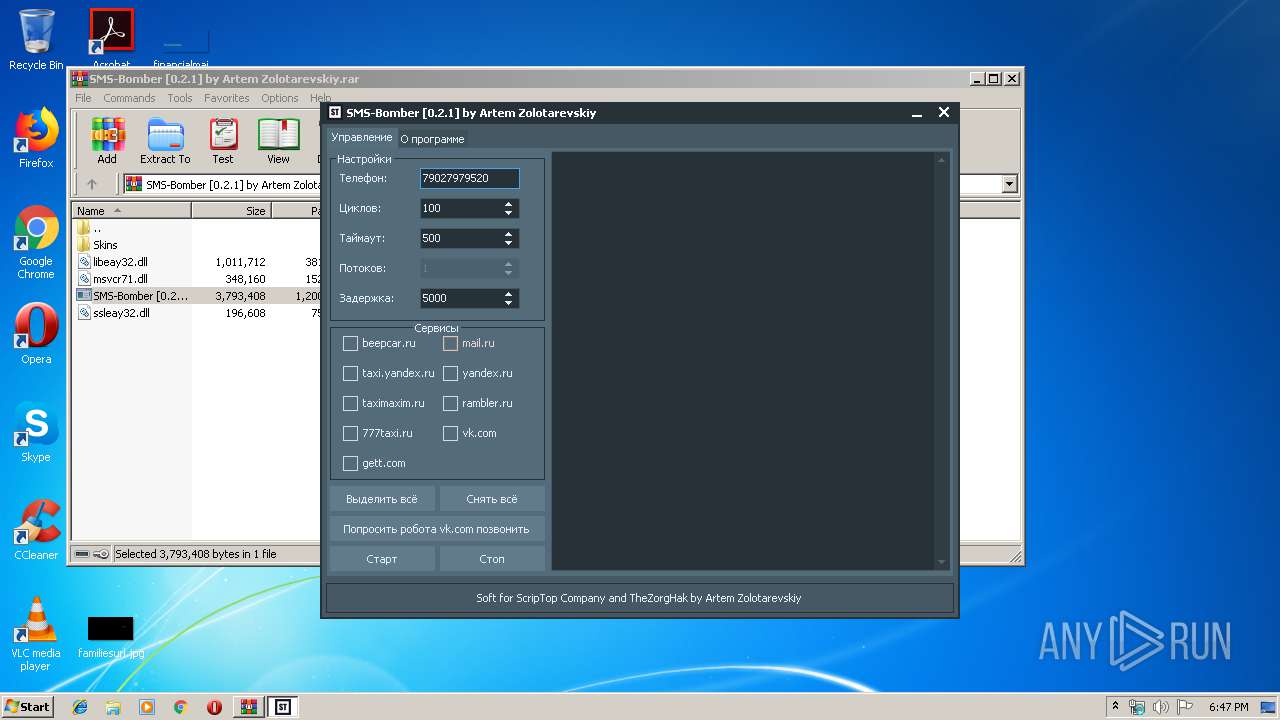
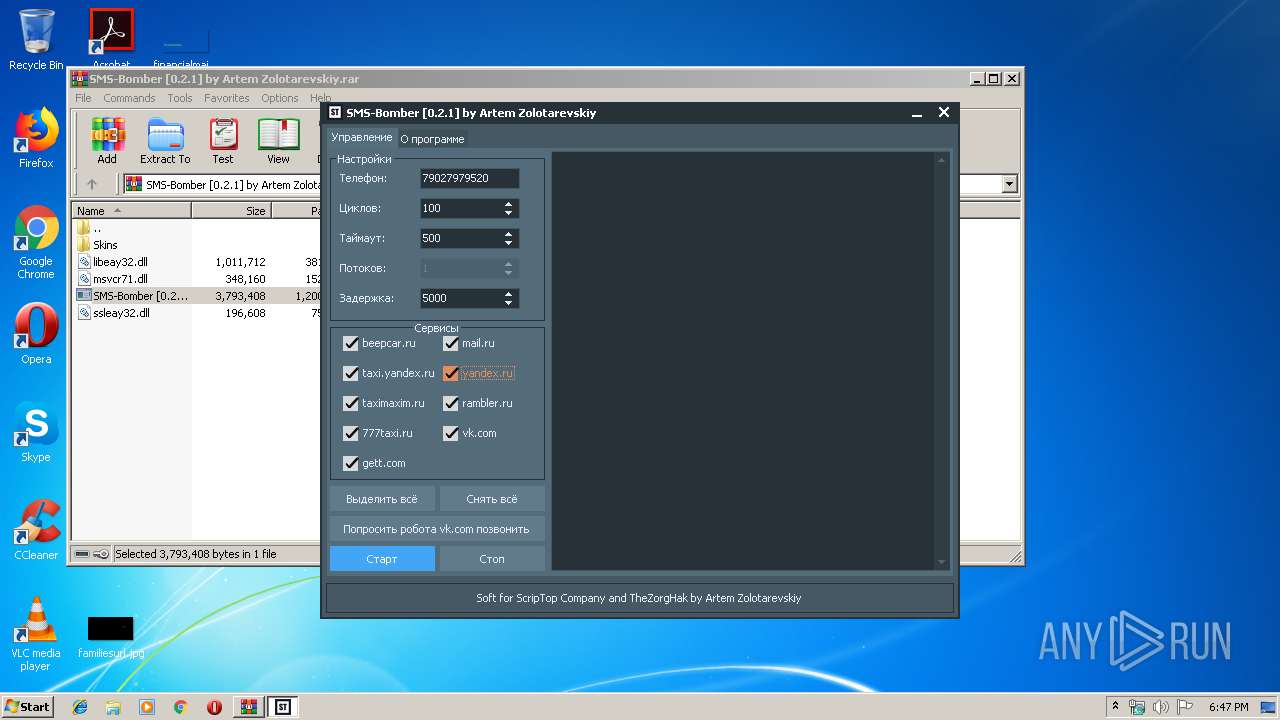
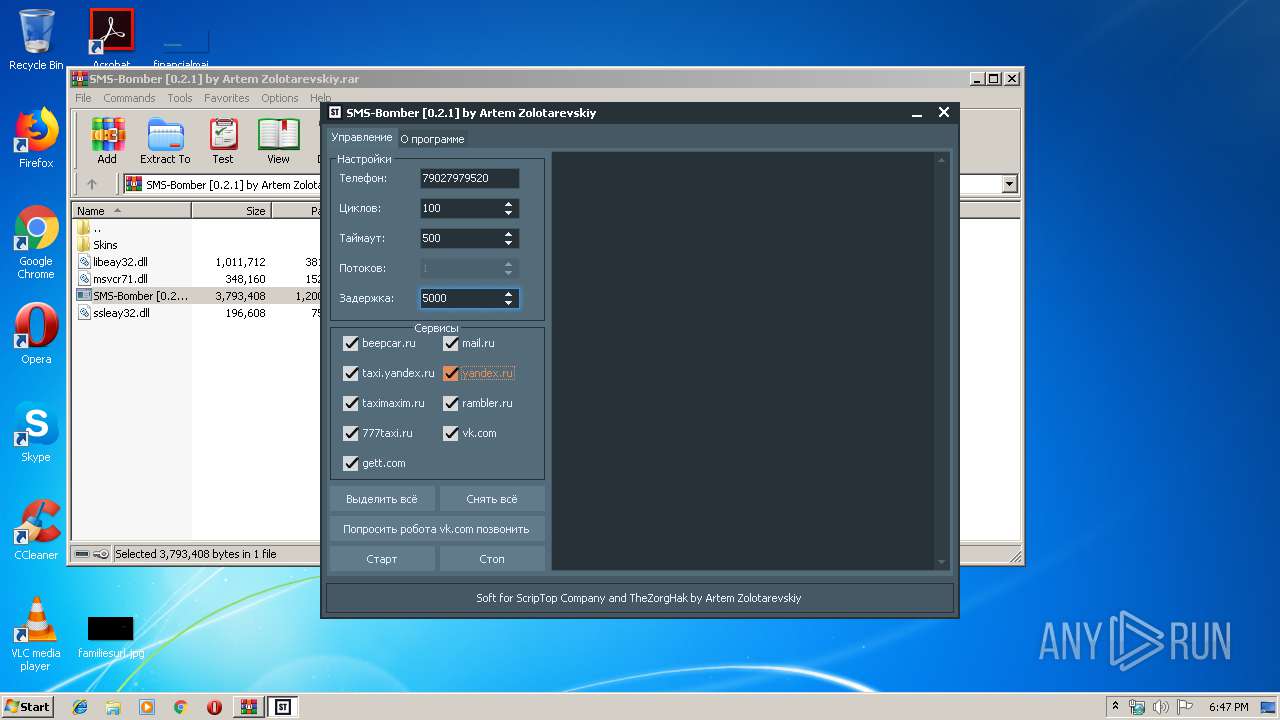
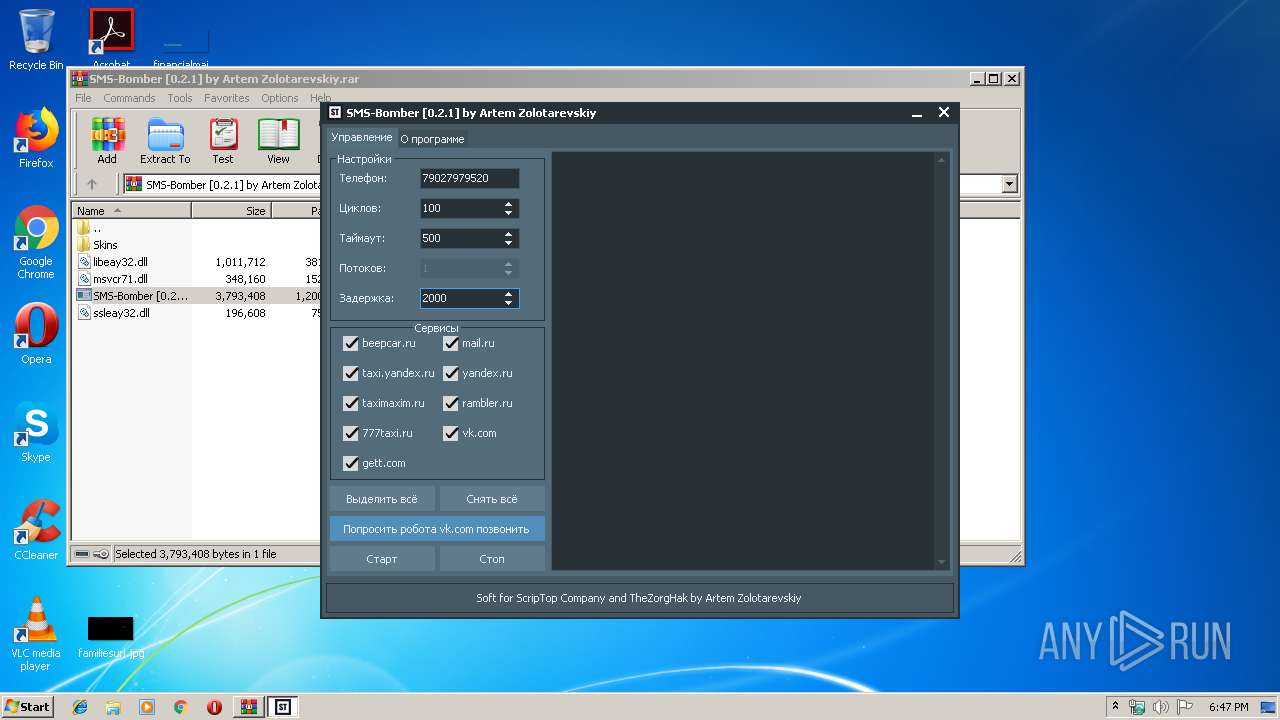
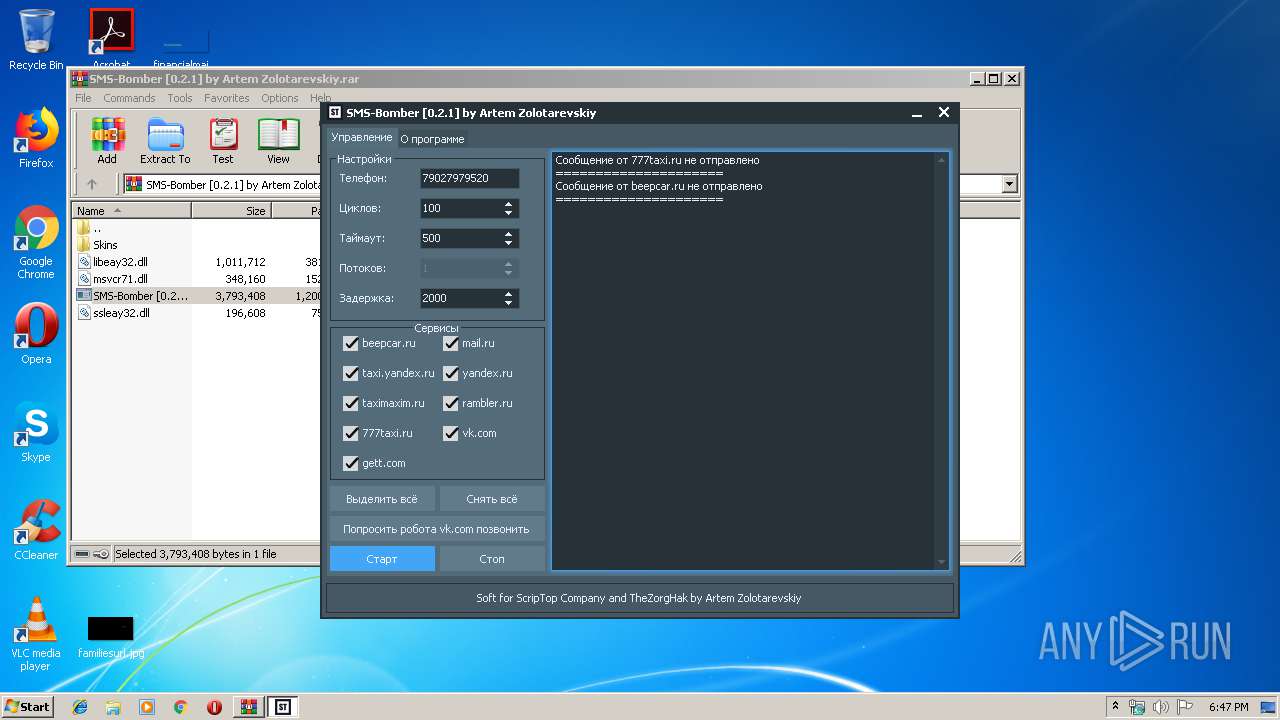
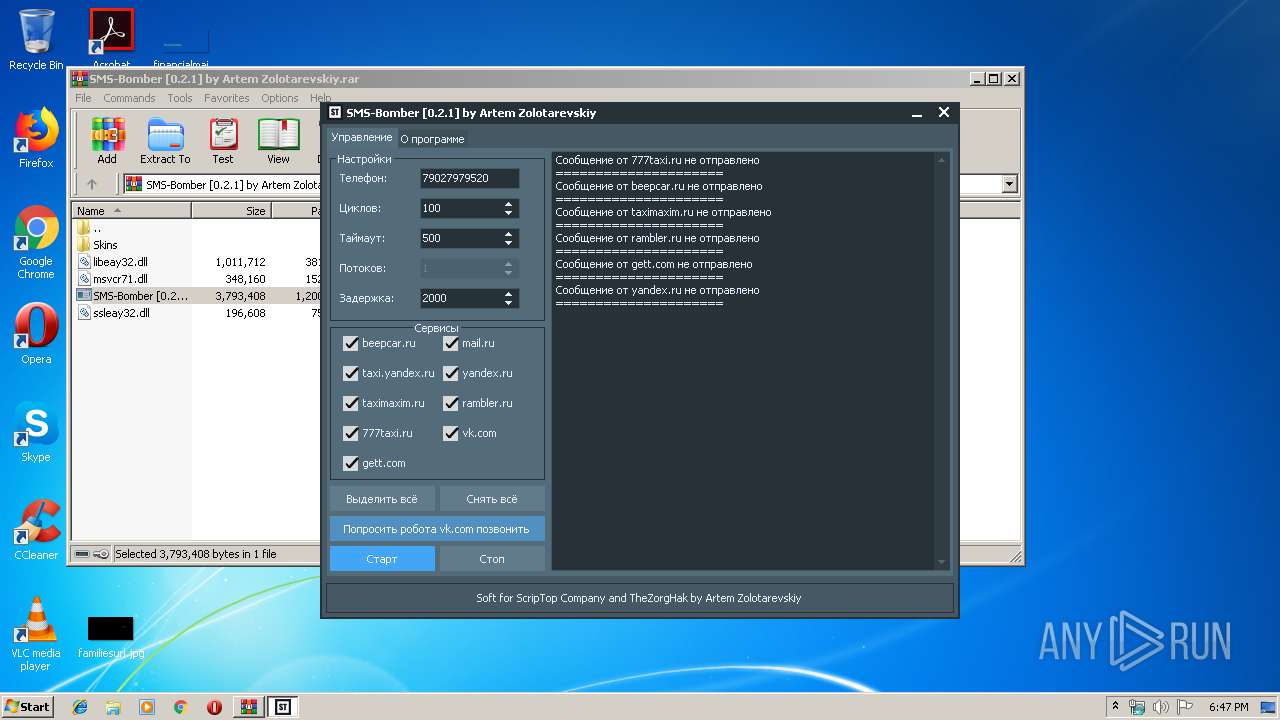
| File name: | SMS-Bomber [0.2.1] by Artem Zolotarevskiy.rar |
| Full analysis: | https://app.any.run/tasks/93df9064-aacd-4591-a2ce-835ae983557b |
| Verdict: | Malicious activity |
| Analysis date: | December 31, 2019, 18:46:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1D1220A55D65E67F30324C3708BC5FF7 |
| SHA1: | CA9AF55711A5B4CB1A56C8A2BCC55C641BB7CBB8 |
| SHA256: | 784C18E27262ECEAE8579DAB14E277C4B662FC8431960422C062C80A2C4F9E52 |
| SSDEEP: | 49152:XEZv+5wfncf63453ajuSlS0FiQRKVMUbB1EJm:Xuyw/BCayShiWGMUd1EA |
MALICIOUS
Loads dropped or rewritten executable
- SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe (PID: 1796)
Application was dropped or rewritten from another process
- SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe (PID: 1796)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2112)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1796 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2112.1895\SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2112.1895\SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe | WinRAR.exe | ||||||||||||
User: admin Company: ScripTop Company Integrity Level: MEDIUM Description: SMS-Bomber [0.2.1] by Artem Zolotarevskiy Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2112 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SMS-Bomber [0.2.1] by Artem Zolotarevskiy.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
478
Read events
452
Write events
26
Delete events
0
Modification events
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SMS-Bomber [0.2.1] by Artem Zolotarevskiy.rar | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
4
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2112.1895\Skins\default.asz | binary | |
MD5:58D2975CCB969D5C8AC1D13103139159 | SHA256:8968820FD2780710E90B861DAC7ED5870B46EED95E94011374679A659DC15BED | |||
| 2112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2112.1895\ssleay32.dll | executable | |
MD5:5023F4C4AAAA1B6E9D992D6BBDCD340B | SHA256:59B1BE1072DD4ACA5DDCF9B66D5DF8BEC327B4891925BA2339FE6AC6A1BF6D19 | |||
| 2112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2112.1895\SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe | executable | |
MD5:83F6419032487A8D15DDDC566970A8BF | SHA256:CF2D9D354909FE3C4642C104B0F6E7566713BAF466BC4FDE1208A7202CF2417E | |||
| 2112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2112.1895\libeay32.dll | executable | |
MD5:177BDA0C92482DFA2C162A3750932B9C | SHA256:17A4B75EF43A4FDEEDAEF86C39BEAD6719144E3E368B55898B79ECB371012854 | |||
| 2112 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2112.1895\msvcr71.dll | executable | |
MD5:86F1895AE8C5E8B17D99ECE768A70732 | SHA256:8094AF5EE310714CAEBCCAEEE7769FFB08048503BA478B879EDFEF5F1A24FEFE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
10
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
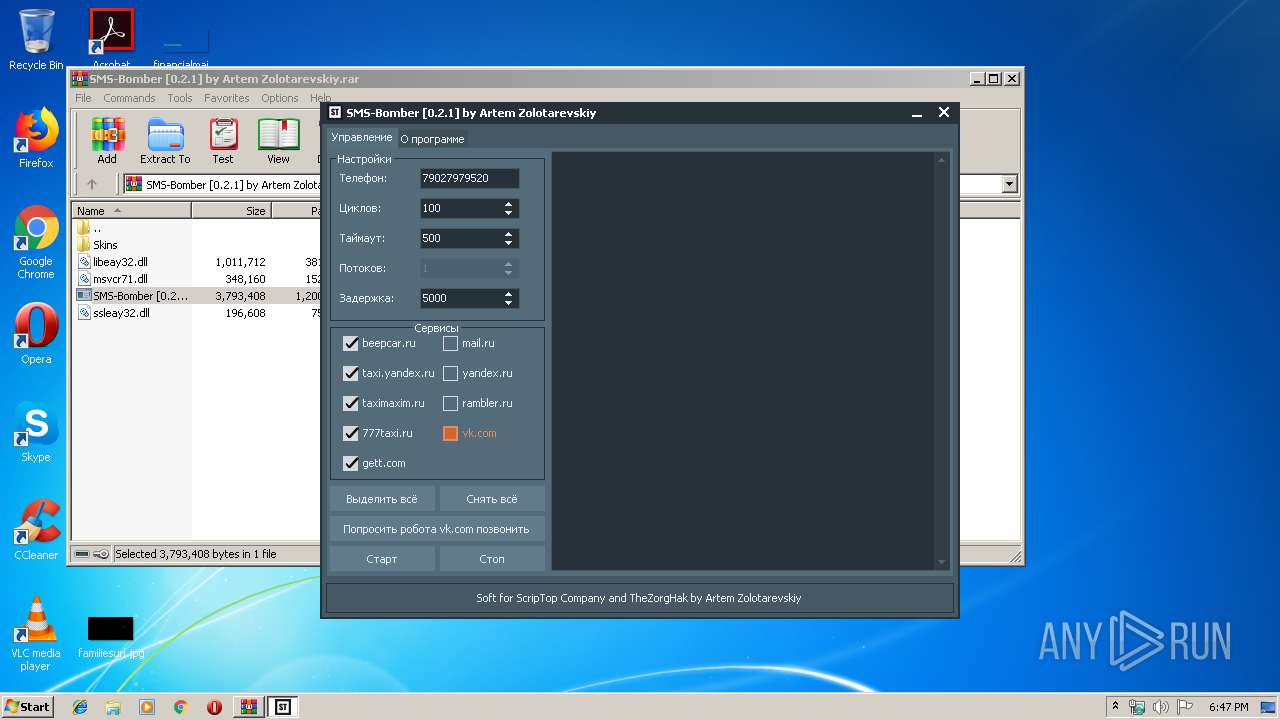
1796 | SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe | POST | 303 | 31.31.196.146:80 | http://www.777taxi.ru/swift-online/ValidateViaSms.php | RU | — | — | suspicious |
1796 | SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe | POST | 200 | 87.236.16.99:80 | http://www.theyeru.ru/api/sms-bomber/method/description.get.php | RU | text | 1.20 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1796 | SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe | 31.31.196.146:80 | www.777taxi.ru | Domain names registrar REG.RU, Ltd | RU | unknown |
1796 | SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe | 87.236.16.99:80 | www.theyeru.ru | Beget Ltd | RU | malicious |
1796 | SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe | 34.95.71.191:443 | beepcar.ru | — | US | unknown |
1796 | SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe | 178.248.237.53:443 | taximaxim.ru | HLL LLC | RU | unknown |
1796 | SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe | 81.19.78.87:443 | id.rambler.ru | Rambler Internet Holding LLC | RU | unknown |
1796 | SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe | 104.20.29.45:443 | ru.gett.com | Cloudflare Inc | US | shared |
1796 | SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe | 213.180.204.24:443 | passport.yandex.ru | YANDEX LLC | RU | whitelisted |
1796 | SMS-Bomber [0.2.1] by Artem Zolotarevskiy.exe | 87.240.137.130:443 | api.vk.com | VKontakte Ltd | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.theyeru.ru |
| malicious |
www.777taxi.ru |
| suspicious |
beepcar.ru |
| whitelisted |
taximaxim.ru |
| whitelisted |
id.rambler.ru |
| whitelisted |
ru.gett.com |
| suspicious |
passport.yandex.ru |
| whitelisted |
api.vk.com |
| whitelisted |