| download: | /attachments/1305713667681288284/1380874971378749541/matcha-e1da58b32b1c4d64.rar |
| Full analysis: | https://app.any.run/tasks/6c4d88c7-3c77-4e47-bf91-3f64b97051fa |
| Verdict: | Malicious activity |
| Analysis date: | June 07, 2025, 12:02:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 63834A858FB6342EFF5911DCF37CD70D |
| SHA1: | D9861B804E9A37B144637080B3CBECD7ADA7D983 |
| SHA256: | 7847CD10E0EE3AFA13E343591FC09F10FB99C99D64BCFFCB5EBAE9DDB5700C47 |
| SSDEEP: | 393216:B7guLwksHFLonVeSEqgKvpmYkppsjYbe4EiA9l11:JguLywV5DvcYkpPbe4EBv/ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7776)
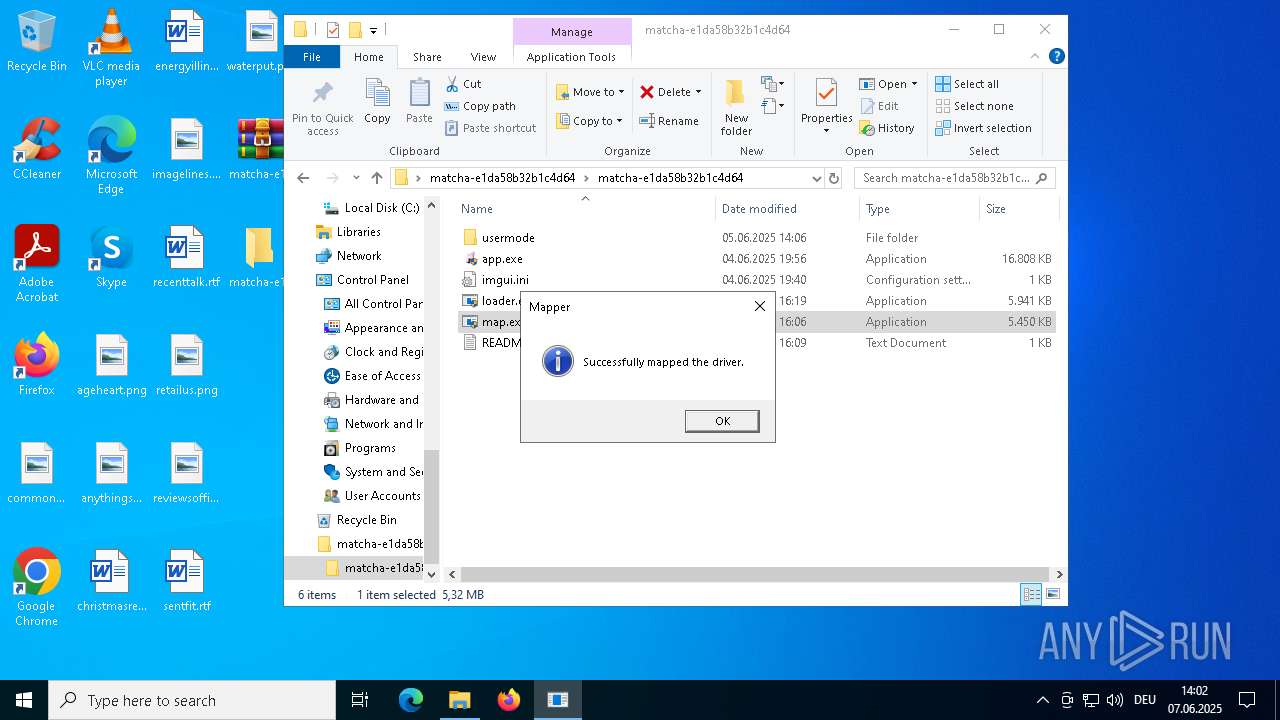
Vulnerable driver has been detected
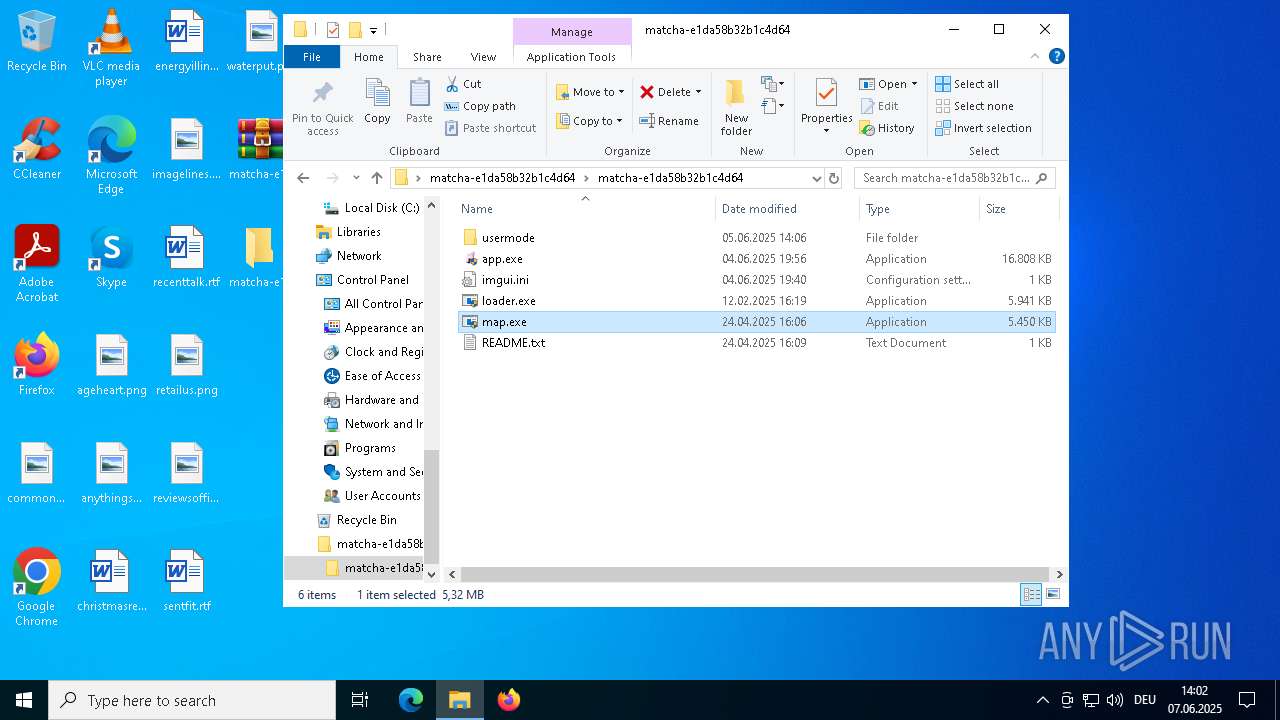
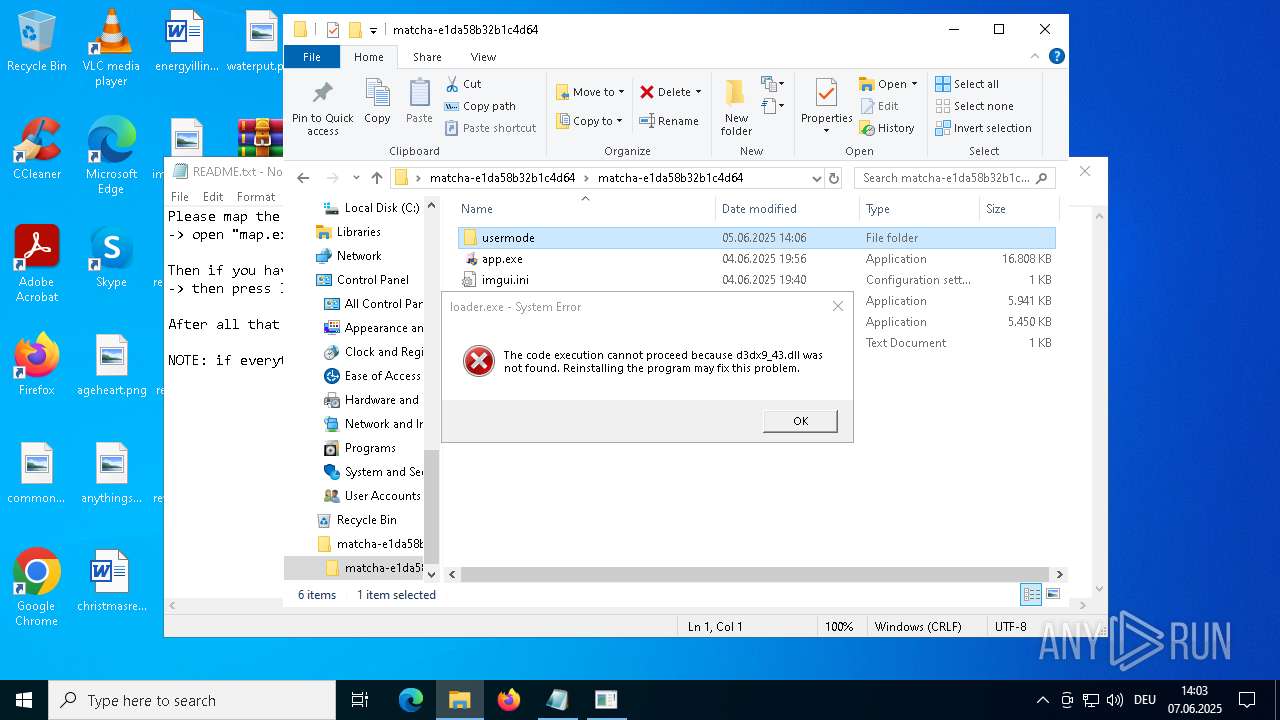
- map.exe (PID: 7948)
SUSPICIOUS
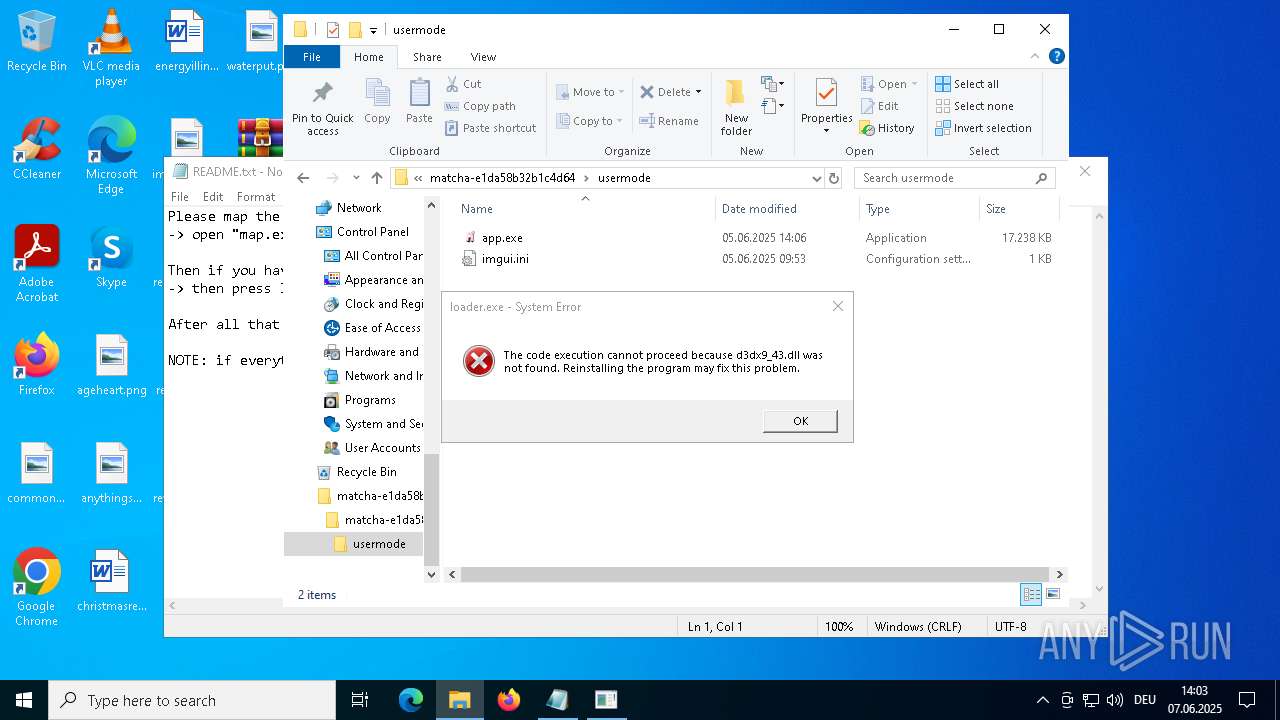
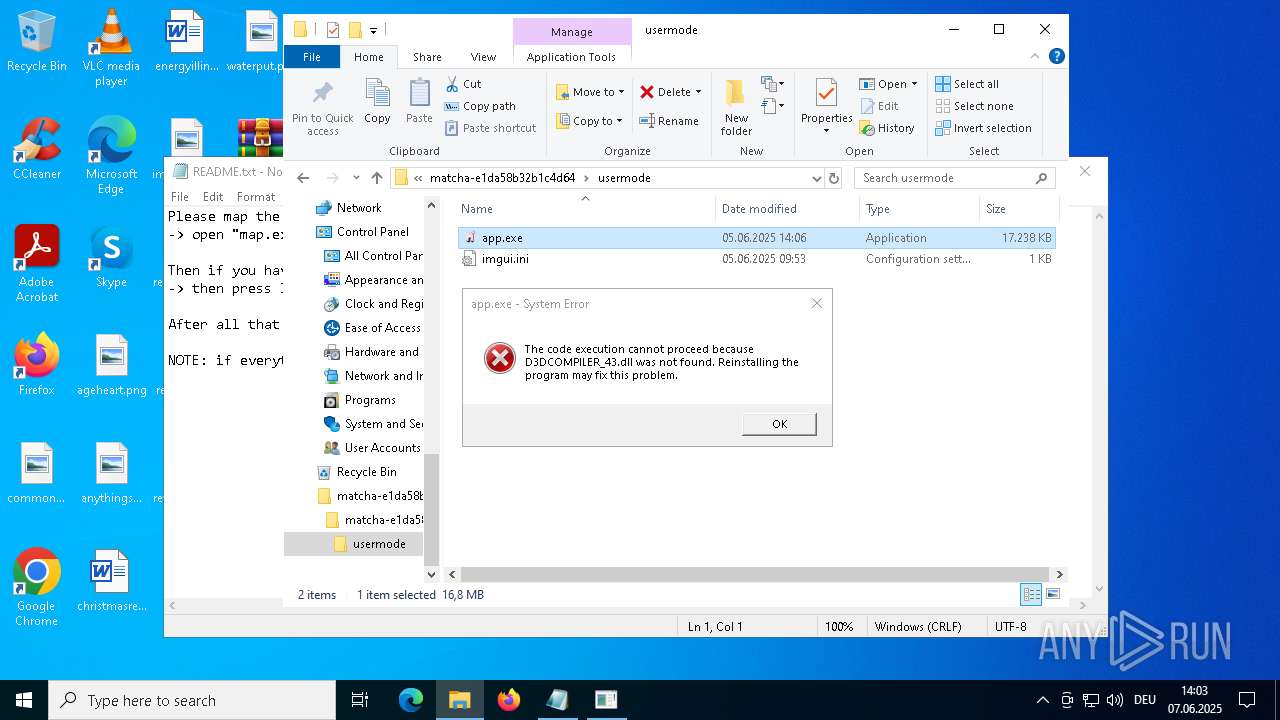
Executable content was dropped or overwritten
- map.exe (PID: 7948)
Creates or modifies Windows services
- map.exe (PID: 7948)
INFO
Manual execution by a user
- WinRAR.exe (PID: 1164)
- app.exe (PID: 6852)
- loader.exe (PID: 2136)
- loader.exe (PID: 3760)
- app.exe (PID: 5612)
- notepad.exe (PID: 4400)
- app.exe (PID: 4020)
- app.exe (PID: 404)
- app.exe (PID: 6028)
- map.exe (PID: 7948)
- loader.exe (PID: 8132)
- loader.exe (PID: 7456)
- map.exe (PID: 7836)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1164)
The sample compiled with english language support
- map.exe (PID: 7948)
Create files in a temporary directory
- map.exe (PID: 7948)
Reads the computer name
- map.exe (PID: 7948)
Reads security settings of Internet Explorer
- notepad.exe (PID: 4400)
Checks supported languages
- map.exe (PID: 7948)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 14896301 |
| UncompressedSize: | 17210880 |
| OperatingSystem: | Win32 |
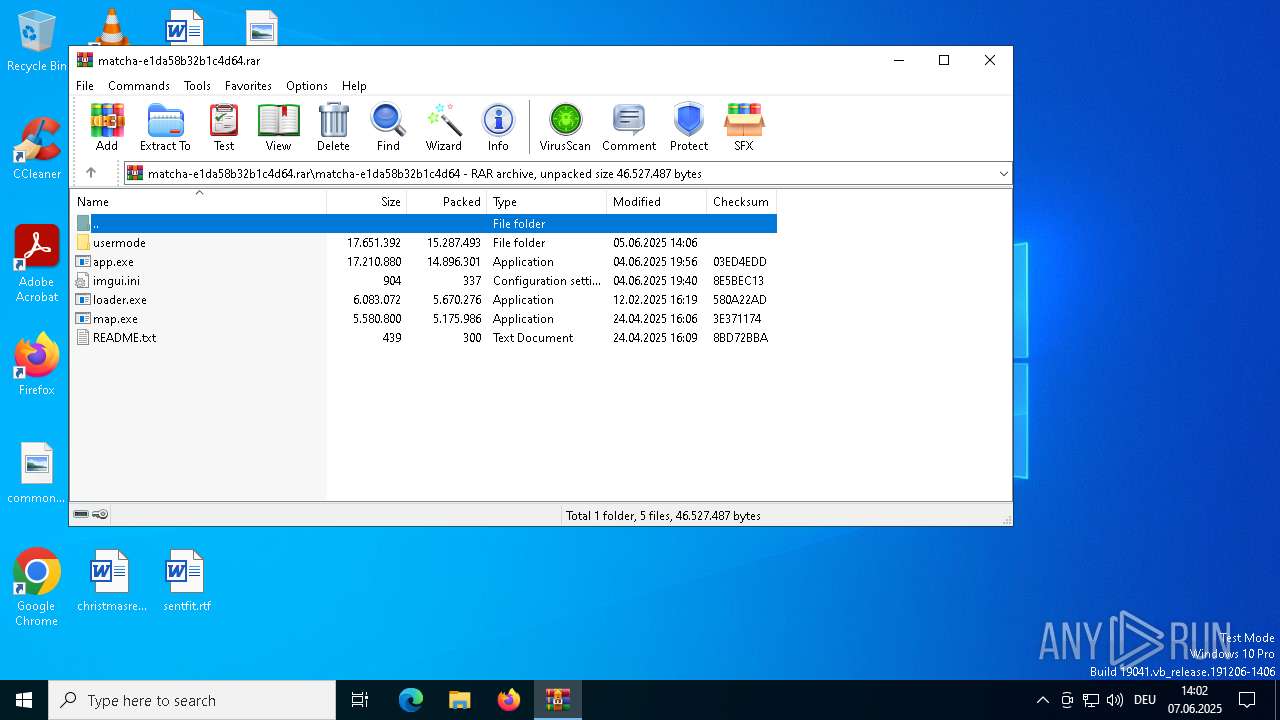
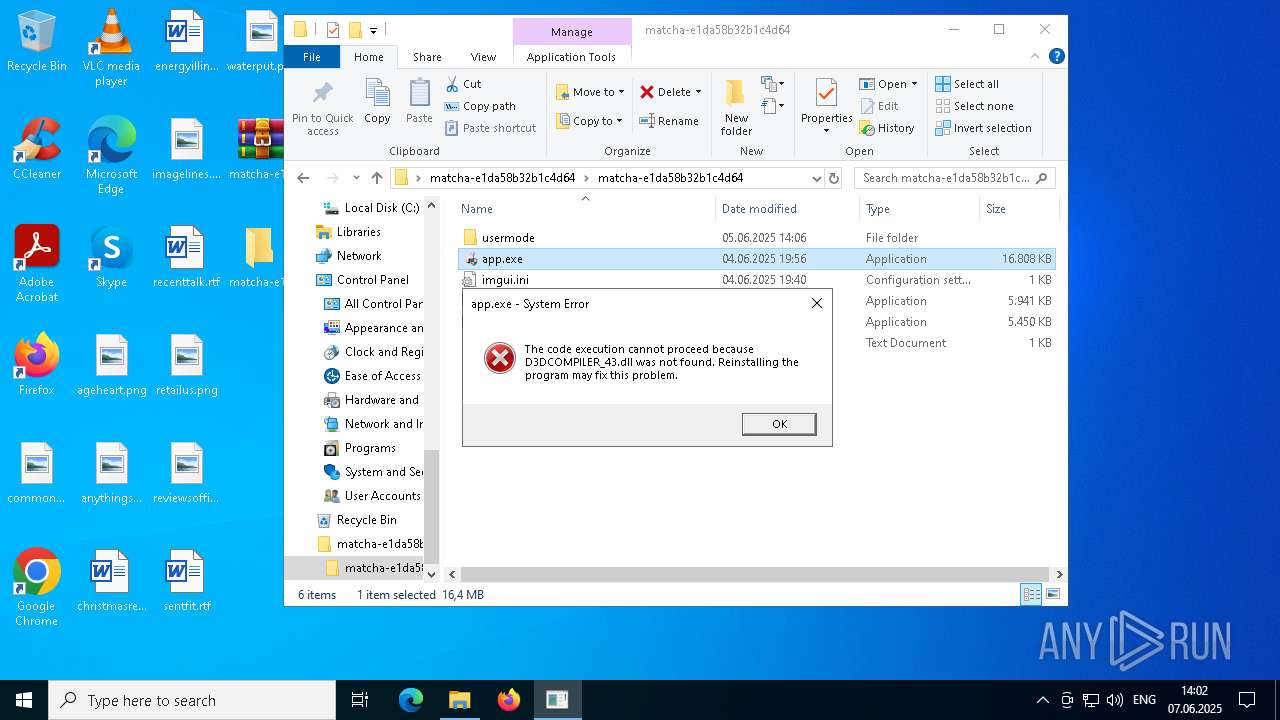
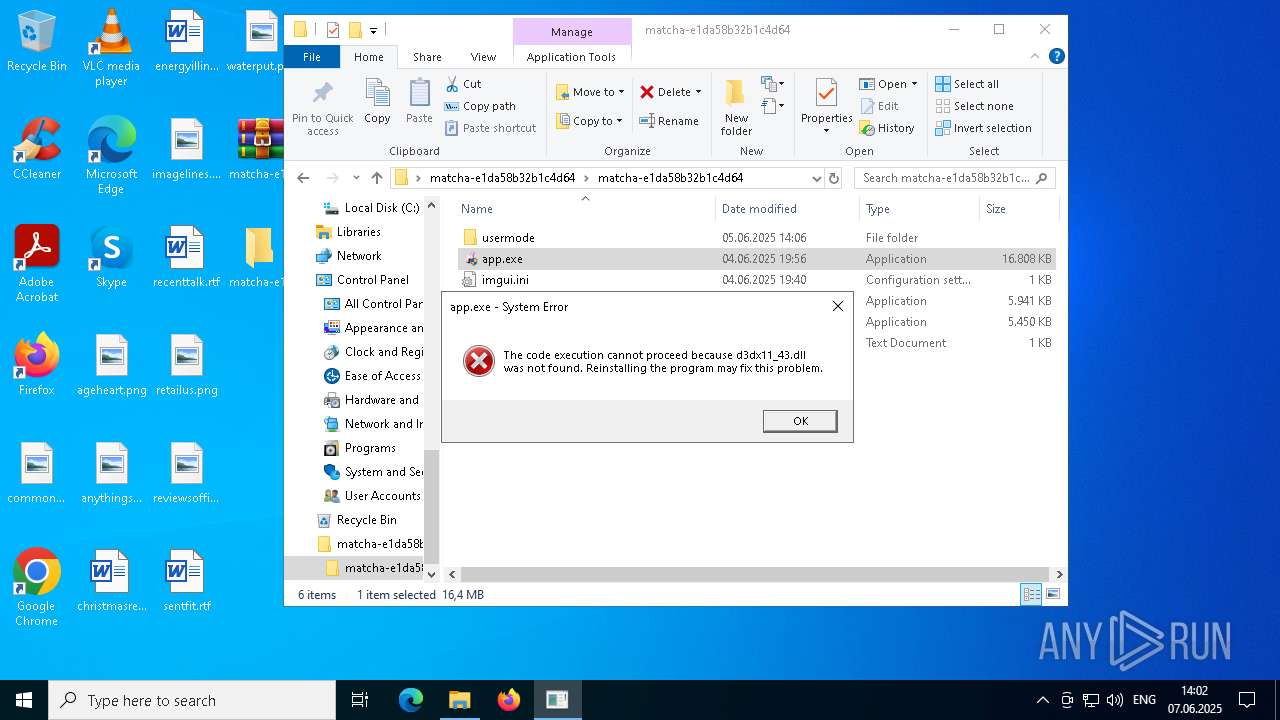
| ArchivedFileName: | matcha-e1da58b32b1c4d64/app.exe |
Total processes
136
Monitored processes
16
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 404 | "C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\app.exe" | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\app.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225781 Modules
| |||||||||||||||
| 1164 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64.rar" C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
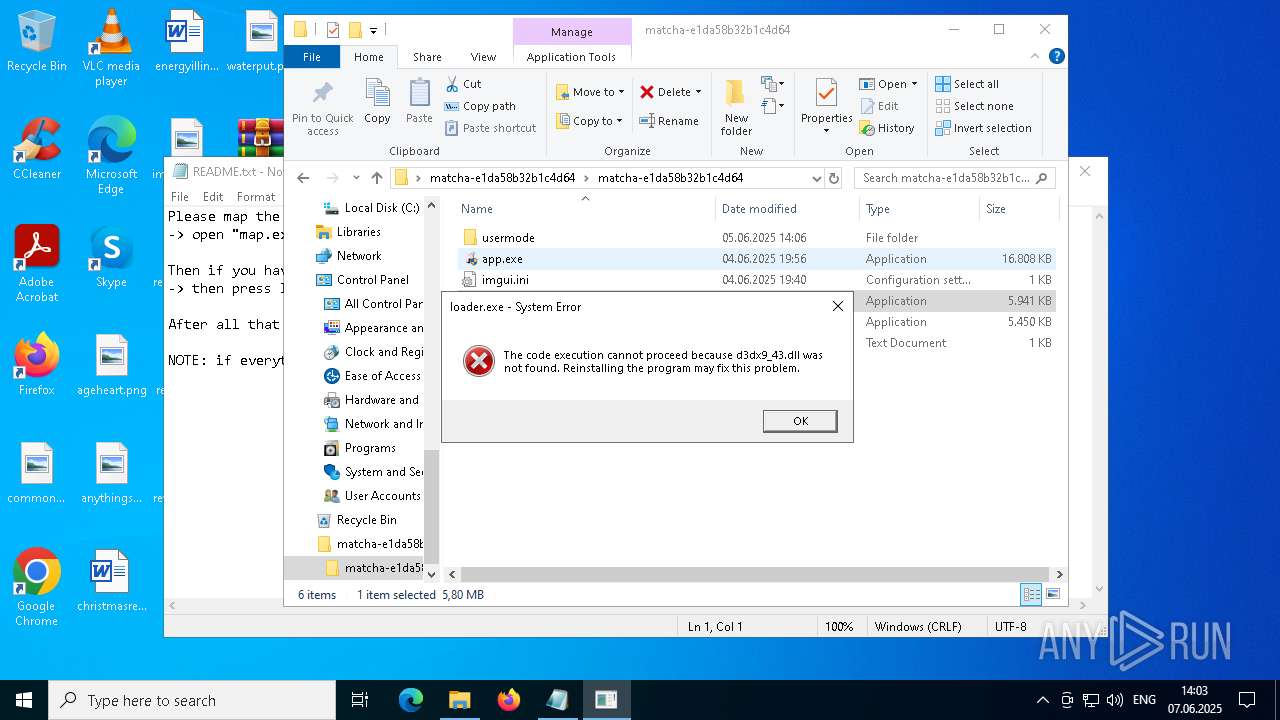
| 2136 | "C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\loader.exe" | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\loader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3760 | "C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\loader.exe" | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\loader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225781 Modules
| |||||||||||||||
| 4020 | "C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\app.exe" | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\app.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225781 Modules
| |||||||||||||||
| 4400 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5612 | "C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\app.exe" | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\app.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6028 | "C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\usermode\app.exe" | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\usermode\app.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225781 Modules
| |||||||||||||||
| 6048 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6852 | "C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\app.exe" | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\app.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
3 953
Read events
3 926
Write events
26
Delete events
1
Modification events
| (PID) Process: | (7776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64.rar | |||
| (PID) Process: | (7776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
5
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
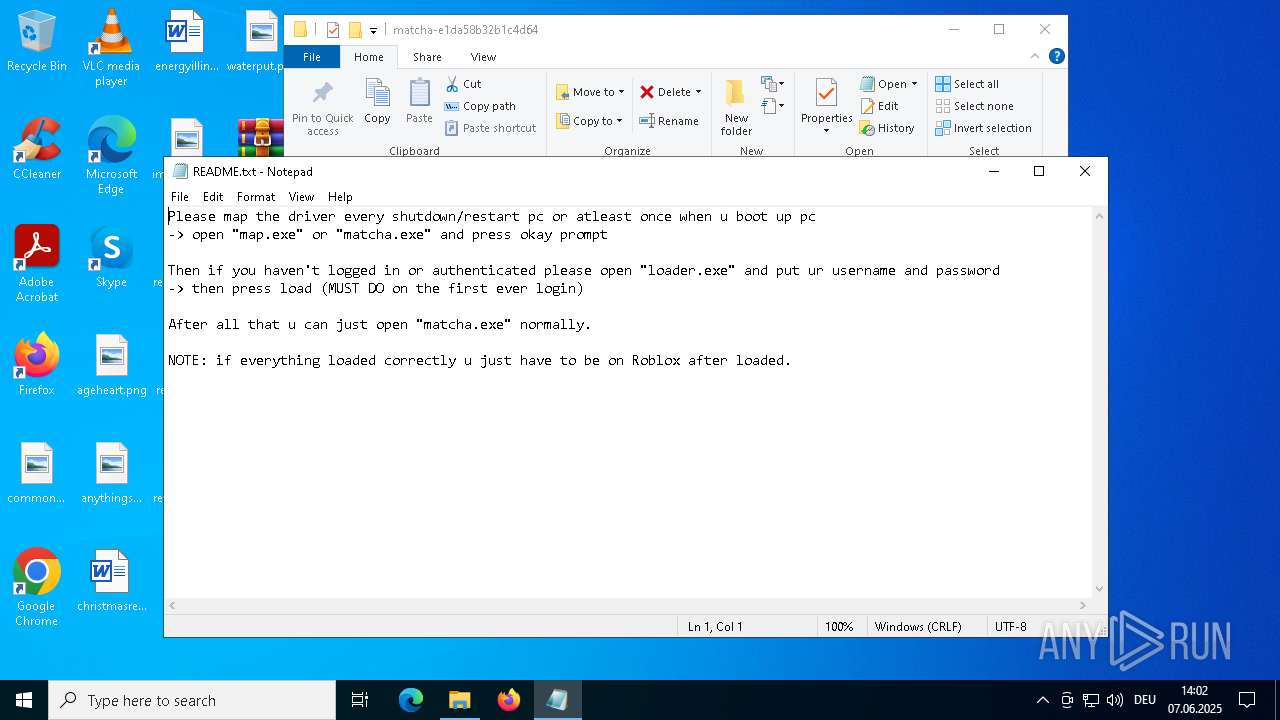
| 1164 | WinRAR.exe | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\README.txt | text | |
MD5:210B224F0F3251F218EE41C148E1B9CA | SHA256:17D21A88C4A89035F4477268F3CE4193F4A1092563AD2F8AD605703F64025776 | |||
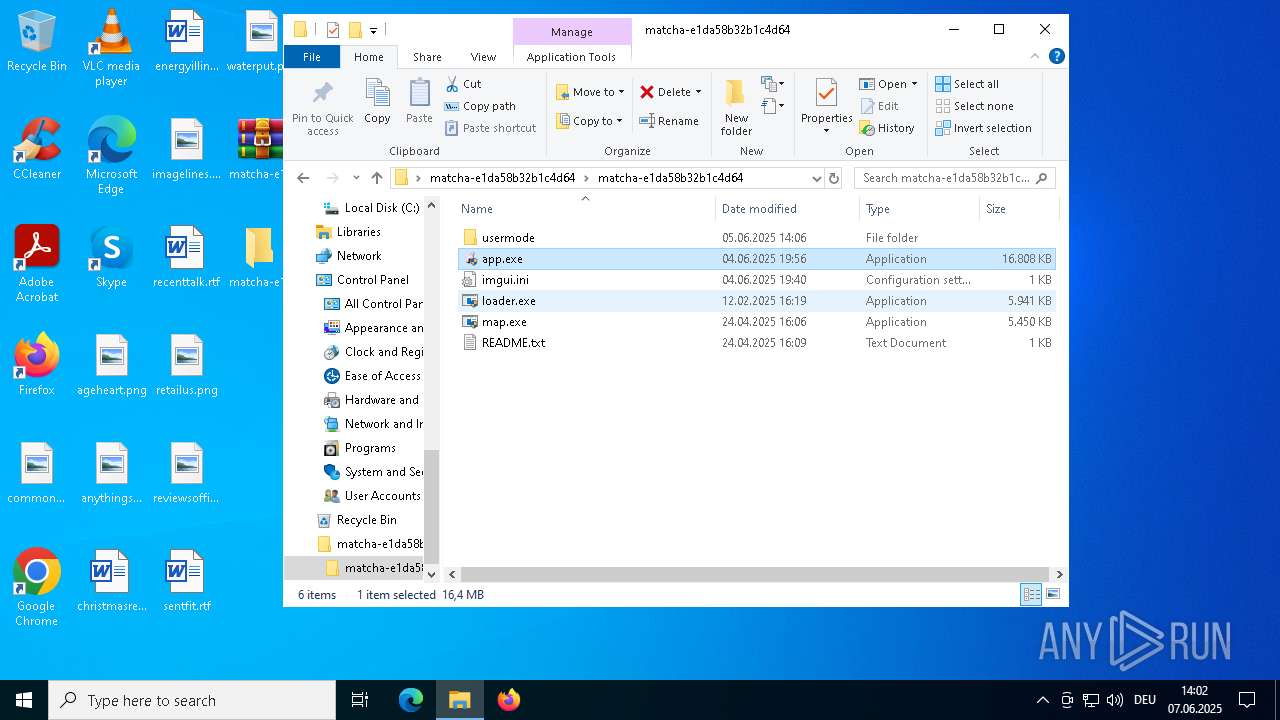
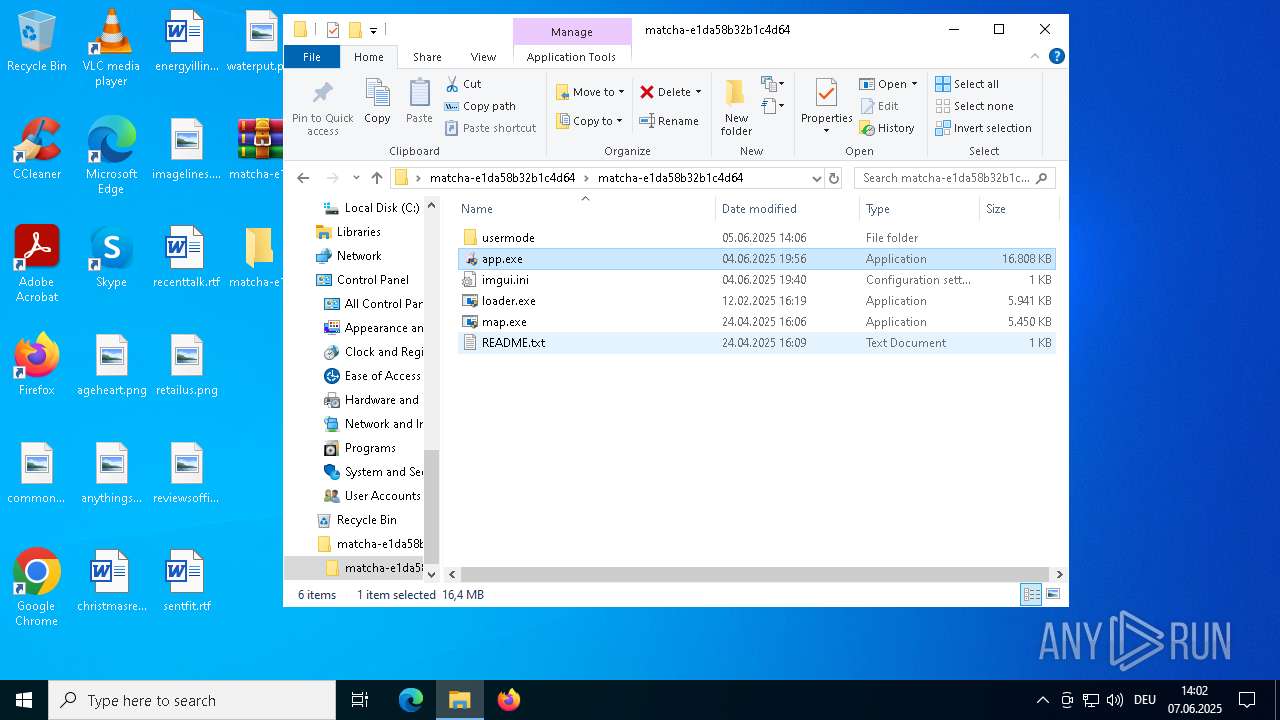
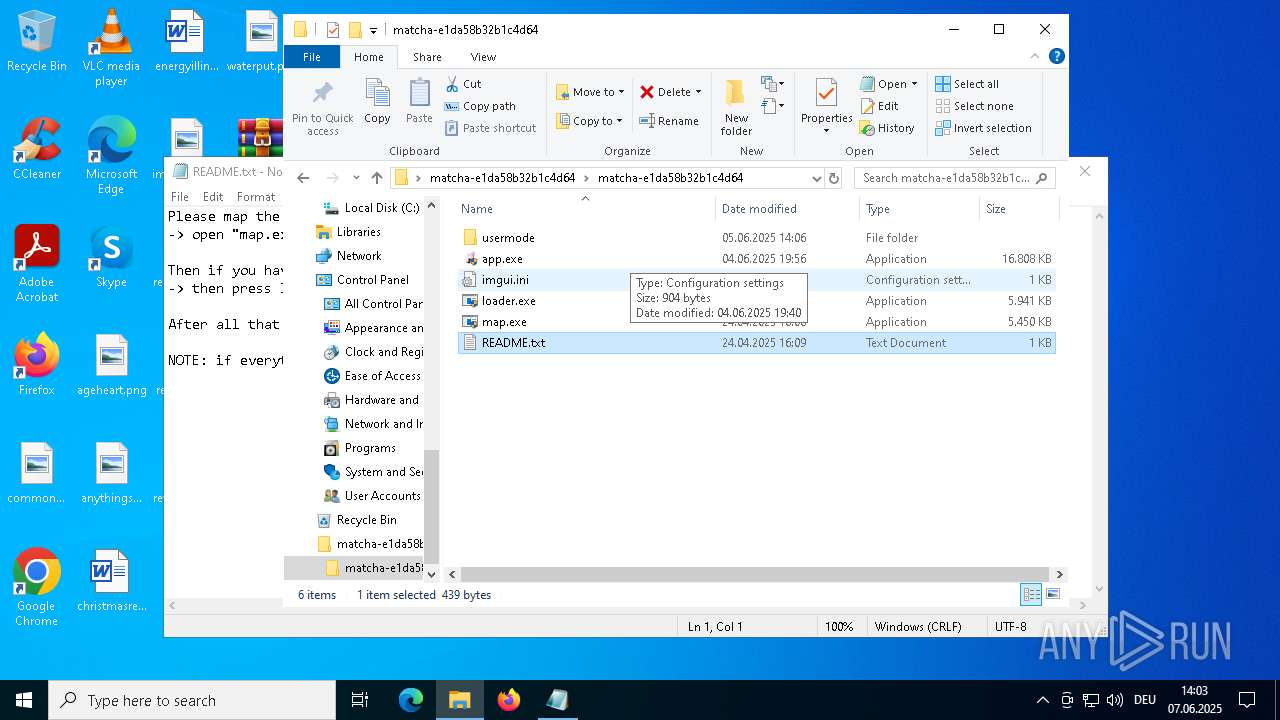
| 1164 | WinRAR.exe | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\usermode\app.exe | executable | |
MD5:816C697602486CD742A130DC8F3BAF07 | SHA256:DD61C9621A941615E3DBCD9262C23FBB02881F60F2B22608B575BEF710496D43 | |||
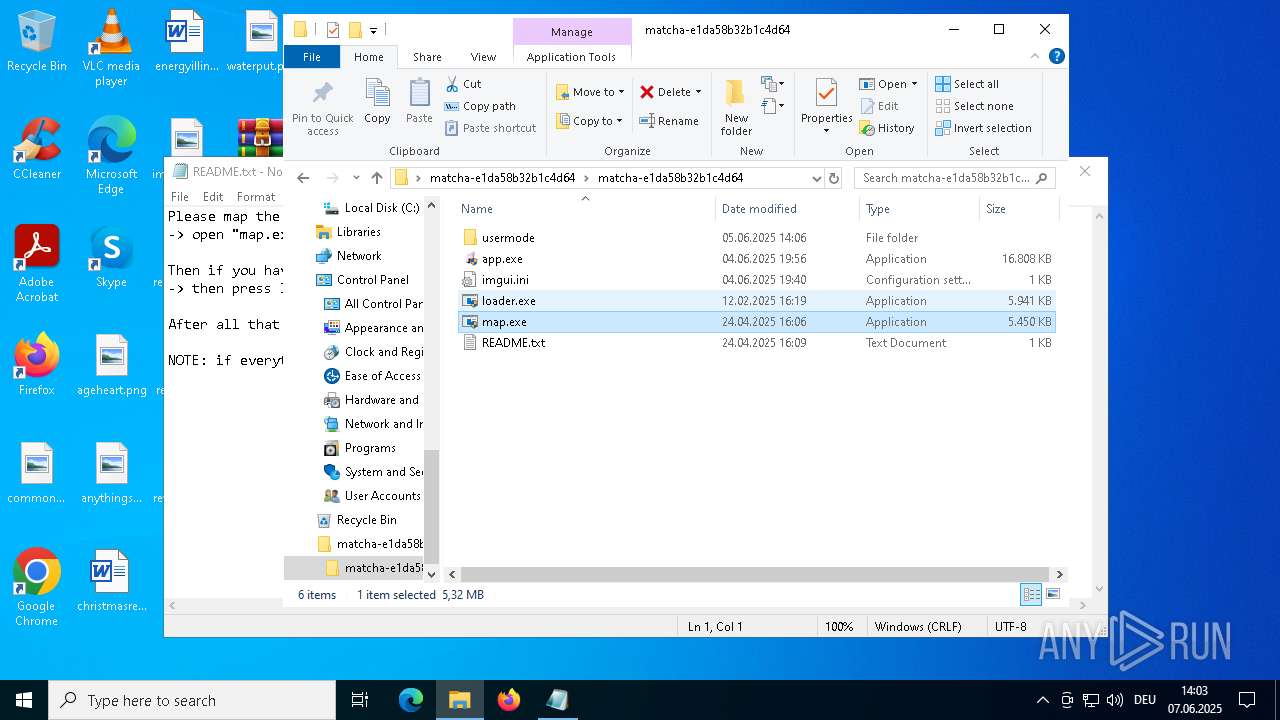
| 1164 | WinRAR.exe | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\map.exe | executable | |
MD5:0918732E8E201A578B4388250F4C79D8 | SHA256:26F1D7F187BBE3D5ED4A31CD618AAB2341465E24395963C7FF906249193E9DAE | |||
| 1164 | WinRAR.exe | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\app.exe | executable | |
MD5:C85D84E96EE9481141EDE69CDE4E220E | SHA256:398DB4942A60B392757A01B73913D74BBC9E244EC46FFFE6EEC5011ED17B7761 | |||
| 1164 | WinRAR.exe | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\usermode\imgui.ini | text | |
MD5:04115F0E0A9FFF8C762AA1B3C9D6C6B4 | SHA256:42F2E1030CE6A4970B8244AD55B59933961D19F2D9E3992EB6F04AE69F9DD7CE | |||
| 7948 | map.exe | C:\Users\admin\AppData\Local\Temp\TDxXdzRlmQ | executable | |
MD5:1898CEDA3247213C084F43637EF163B3 | SHA256:4429F32DB1CC70567919D7D47B844A91CF1329A6CD116F582305F3B7B60CD60B | |||
| 1164 | WinRAR.exe | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\loader.exe | executable | |
MD5:179220FA399C407FB4F625F9B9B113E3 | SHA256:F387640B8A8D28F2902768DBC2F66DCE7DFC98503483BEFD74FE31B3A41C6A10 | |||
| 1164 | WinRAR.exe | C:\Users\admin\Desktop\matcha-e1da58b32b1c4d64\matcha-e1da58b32b1c4d64\imgui.ini | text | |
MD5:B5BC12A23D0E1FAA41F73FBC3B54D341 | SHA256:A20CB51A124511EBC2C9D21E5D3AD1DEE87816E364C9B400491D3E293B31A514 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
19
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
7812 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |