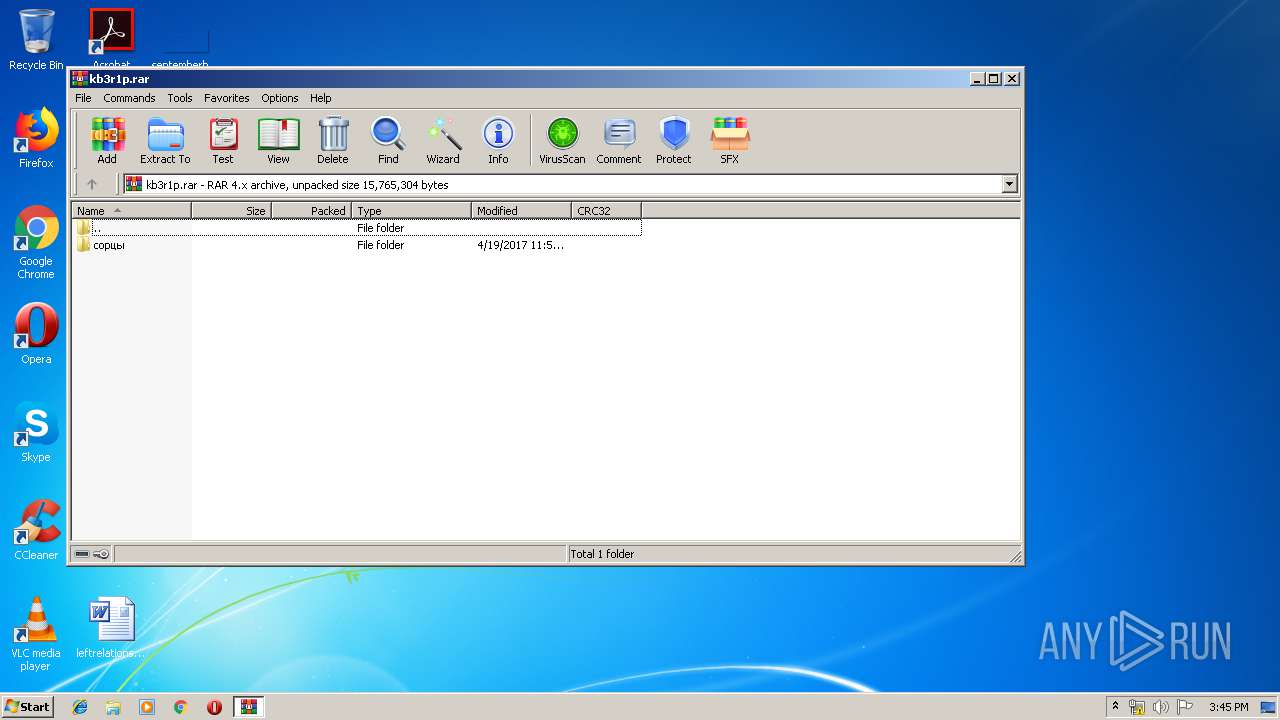
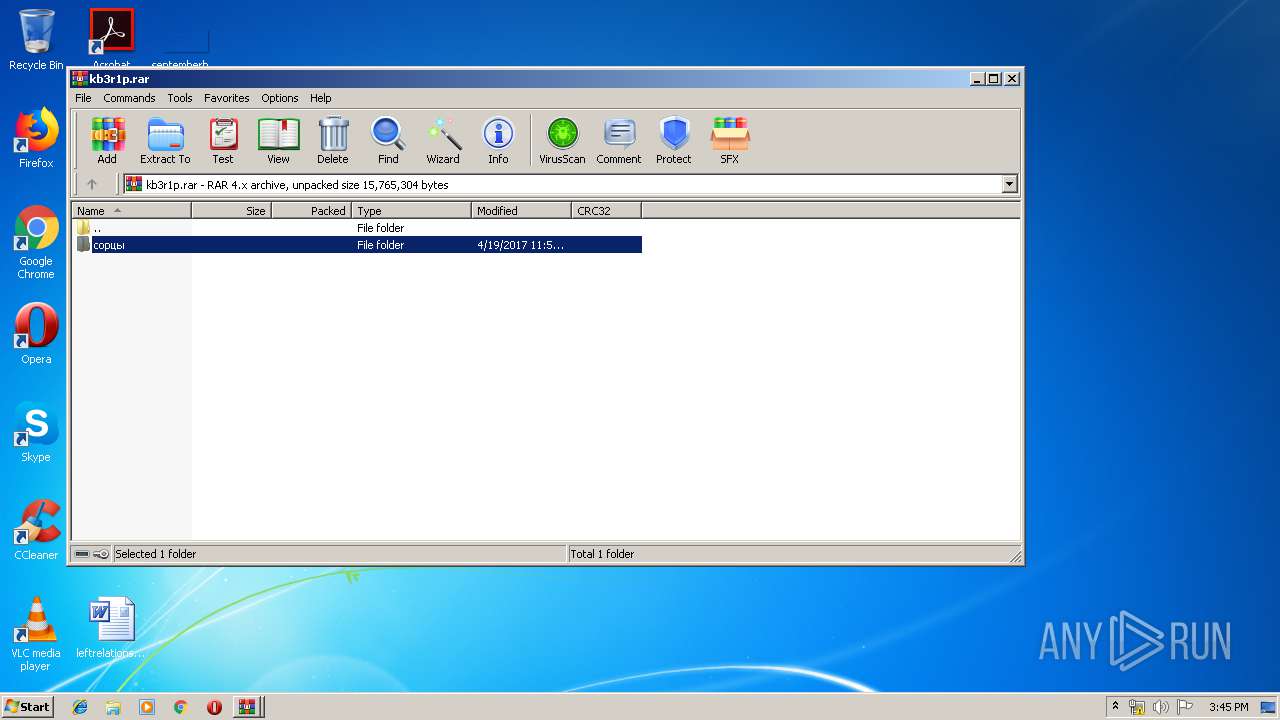
| File name: | kb3r1p.rar |
| Full analysis: | https://app.any.run/tasks/bfc8d8ce-bd6d-436c-9b6b-833843f12151 |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2019, 14:44:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 06EFD1354B7418198C66A78FF3E68E59 |
| SHA1: | 666C0EF12715E0D554FF4080CCDC6AF8898CBC65 |
| SHA256: | 783B2EEFDB90EB78CFDA475073422EE86476ACA65D67FF2C9CF6A6F9067BA5FA |
| SSDEEP: | 98304:1TyTT2A10WTUnbxQiJbTYQjhvAFl+MVCPmNh8:60WobxQUbEQjJwdri |
MALICIOUS
Application was dropped or rewritten from another process
- makecert.exe (PID: 1732)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2564)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1492)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 390 |
|---|---|
| UncompressedSize: | 957 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2016:03:24 11:20:17 |
| PackingMethod: | Normal |
| ArchivedFileName: | ?????\botep\.gitignore |
Total processes
39
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1492 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\kb3r1p.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
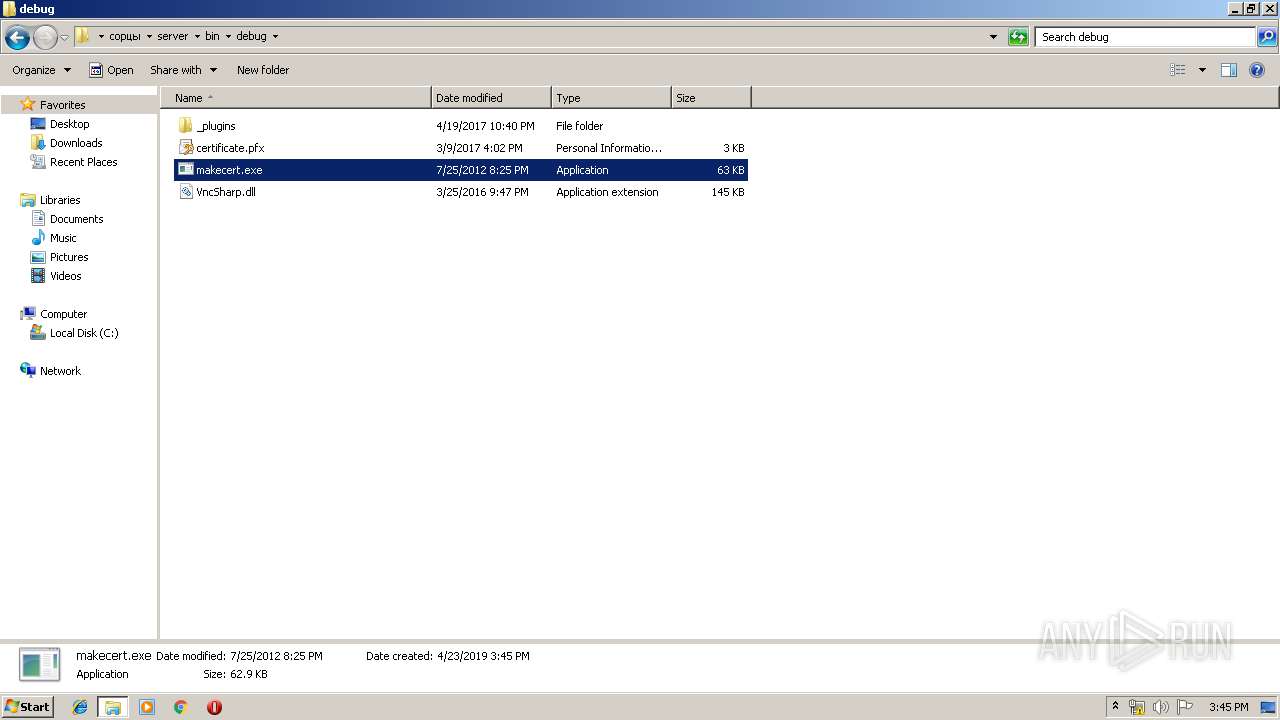
| 1732 | "C:\Users\admin\Desktop\сорцы\server\bin\debug\makecert.exe" | C:\Users\admin\Desktop\сорцы\server\bin\debug\makecert.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ECM MakeCert Exit code: 4294967295 Version: 6.2.9200.16384 (win8_rtm.120725-1247) Modules
| |||||||||||||||
| 2564 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3496 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\kb3r1p.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
982
Read events
940
Write events
42
Delete events
0
Modification events
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3496) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\kb3r1p.rar | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
22
Suspicious files
2
Text files
718
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1492.21489\сорцы\botep\bot\include\MonitoringProcesses.h | text | |
MD5:32E83DD834E61D9E4464C412078C8C80 | SHA256:BF9CB2C74D068CDC5E19233EE1165BA333524521BC77AAD4473DA8314AE89DCD | |||
| 1492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1492.21489\сорцы\botep\bot\config\debug\config.h | text | |
MD5:18351D1BACFC40A9240505000E786179 | SHA256:69F249020B1DFDF0AC9279A35D23D332A53603E6BBB2D635789098DA1D7BA9E0 | |||
| 1492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1492.21489\сорцы\botep\bot\bot.vcxproj | xml | |
MD5:4B5C1457E3259653324DD2D573EB242D | SHA256:8C509AAE196FC0114337193AC38F8A1D530A215448E213D9CDBFF9884BF547A6 | |||
| 1492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1492.21489\сорцы\botep\bot\include\AdminPanel.h | text | |
MD5:D1AC9655A0C90D987F449460534E40A6 | SHA256:75013301F443C2F9FBC717479338BC70B6E22CE3D6DB770B3D113396859E9BB1 | |||
| 1492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1492.21489\сорцы\botep\bot\include\errors.h | text | |
MD5:8C0FB8555357CABBB27C8168233D9341 | SHA256:2C41A93944DA3FD087114C9D018D5C9E6B269E6460EC485836AD3C95D45B83C9 | |||
| 1492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1492.21489\сорцы\botep\bot\config\builder.h | text | |
MD5:70768D071747A40F60BA18A69A2C9CE8 | SHA256:2C8D06C3EC10688D2CC9A2DA8928D2637513B226BF31376E4F996A879BFC0C83 | |||
| 1492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1492.21489\сорцы\botep\bot\include\system.h | text | |
MD5:62B8F70195DE5B9505C67080C74A8A4C | SHA256:A2196BC92003BB6629CACBFB33B8A57342A168B968E961209FA50B857925F3BF | |||
| 1492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1492.21489\сорцы\botep\bot\include\other.h | text | |
MD5:1CCBCA4961DC4C18C84761D6535D39EE | SHA256:10D252E3EBBEE0661520AB91F46432EF2AE3E259572E9DD4314DC0E1AF5ED753 | |||
| 1492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1492.21489\сорцы\botep\.gitignore | text | |
MD5:B0DFC2552001501660AE4D91D49FD414 | SHA256:1901AC02CC9DBE96CEF516107F127EE767197B7DA8807457AFE095E662032BAE | |||
| 1492 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1492.21489\сорцы\botep\bot\include\info.h | text | |
MD5:B501C41939C8BE0944D330FD4031AE41 | SHA256:206F5E7251BF10B6DAC0B29D48859F7FAE7A3D680A965E68EF1318043A2A9D70 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report